A RISC-V Test Sequences Generation Method Based on Instruction Generation Constraints
-
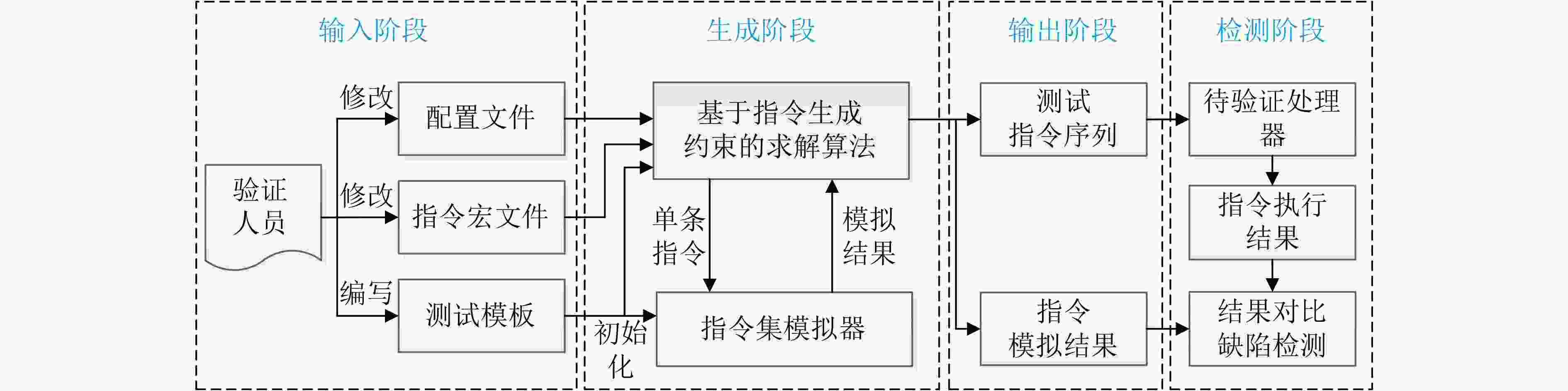
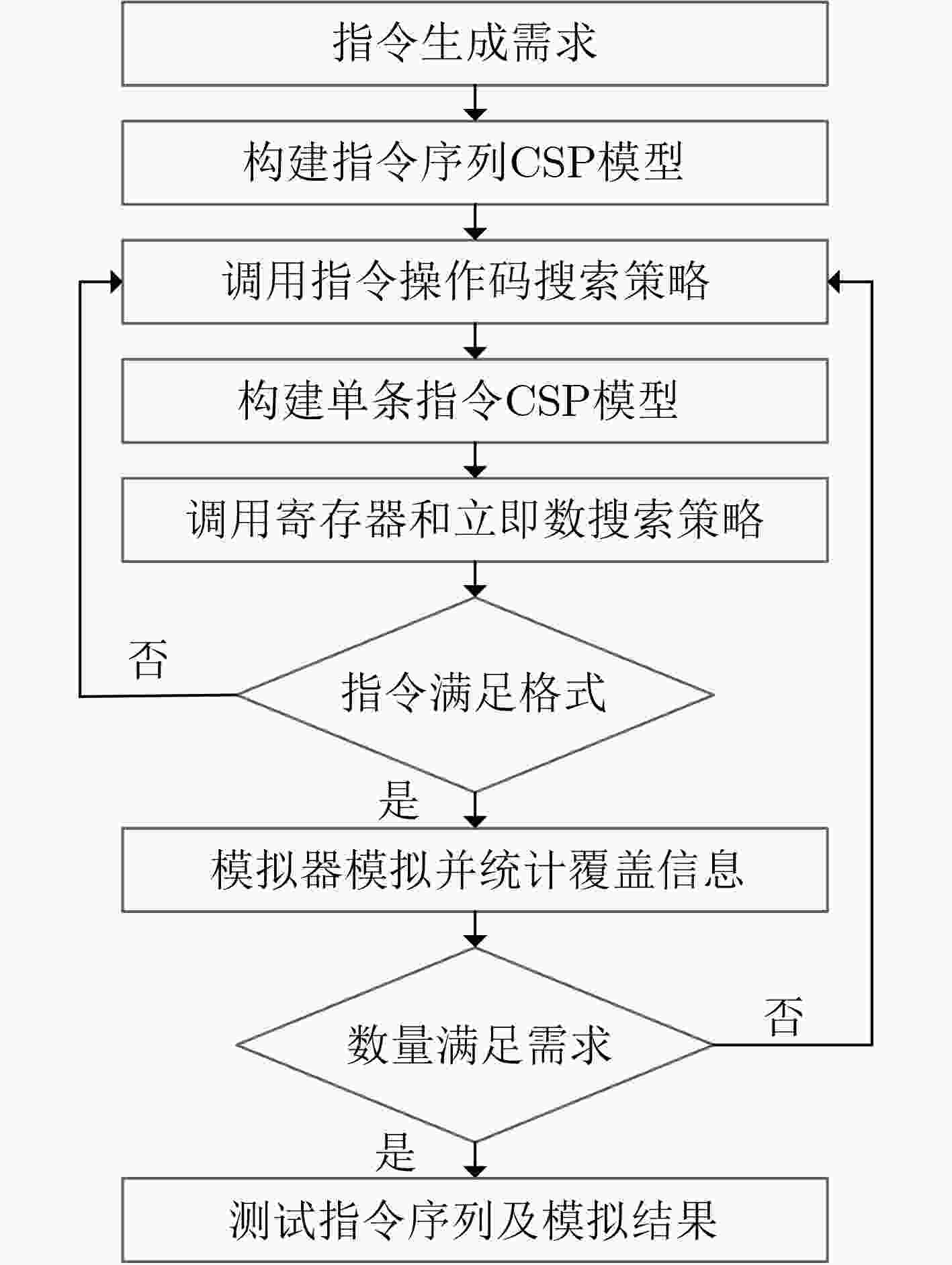
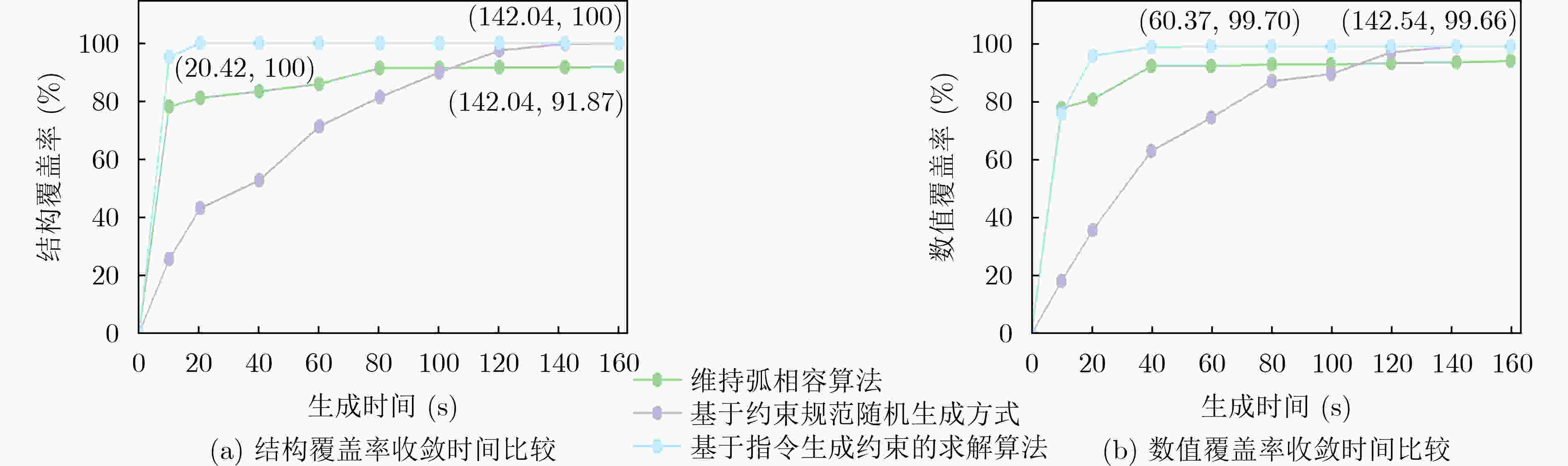
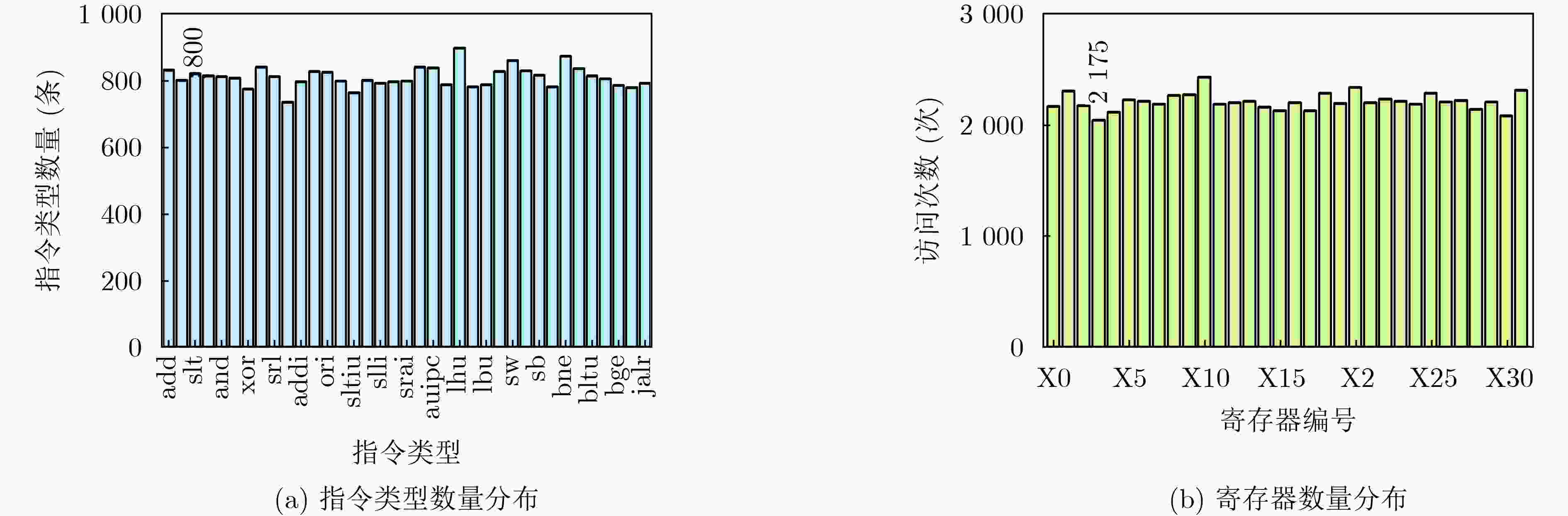
摘要: 为了避免处理器受到指令缺陷的威胁,该文提出基于指令生成约束的RISC-V测试序列生成方法,构建测试指令序列生成框架,实现测试指令生成及指令缺陷检测,解决现有测试指令序列生成方法约束定义困难和收敛速度慢的问题。在该方法中,首先,根据指令集架构规范和指令验证需求定义指令生成约束,包括指令格式约束、通用功能覆盖约束和特殊功能覆盖约束,以解决随着指令数量增多约束定义的困难,提高可复用性;然后,定义启发式搜索策略,通过统计覆盖信息,加快覆盖率收敛速度;最后,基于启发式搜索策略构造求解算法,实现满足指令生成约束的测试序列生成。实验结果表明,与现有方法相比,在覆盖所有指令验证需求的前提下,结构覆盖率和数值覆盖率的收敛时间分别减少了85.62%和57.64%。利用该框架对开源处理器进行检测,可以定位到在处理器译码和执行阶段引入的指令缺陷,为处理器指令缺陷检测提供了有效的方法。Abstract: In order to avoid the threat of instruction defects to the processor, this paper proposes a RISC-V test sequence generation method based on instruction generation constraints. A test instruction sequence generation framework is constructed based on this method to achieve test instruction generation and instruction defect detection, while addressing the challenges in defining constraints and slow convergence speed in existing test instruction sequence generation methods. Firstly, the instruction generation constraints are defined according to the instruction set architecture specification and instruction verification requirements. These constraints include instruction format constraints, general coverage constraints, and particular coverage constraints, aiming to solve the challenges in defining constraints as the number of instructions increases and improve reusability. Then, a heuristic search strategy is applied to accelerating the convergence rate of coverage by utilizing statistical coverage information. Finally, a solving algorithm is constructed based on the heuristic search strategies to generate test sequences that satisfy the instruction generation constraints. The experimental results show that, compared with the state-of-the-art methods, the convergence time of structural coverage is reduced by 85.62% and numerical coverage is reduced by 57.64%, under the premise of covering all instruction verification requirements. By using this framework to detect open-source processor, instruction defects introduced in the processor decoding and execution stages can be located, providing an efficient method for detecting processor instruction defects.
-
Key words:
- Processor /
- RISC-V /
- Instruction defect detection /
- Constrained instruction generation
-
表 1 RV32I指令格式约束
约束变量 数值约束 指令操作码 add, sub等37种已定义操作码 寄存器 X0 ~ X31,32个整数通用寄存器 立即数 根据不同比特数确定,如5-bit无符号数
立即数范围0 ~ 31访存指令 访存粒度为字节/半字/字,偏移地址约束
为1/2/4的倍数 -
[1] WANG Yuze, LIU Peng, WANG Weidong, et al. On a consistency testing model and strategy for revealing RISC processor's dark instructions and vulnerabilities[J]. IEEE Transactions on Computers, 2022, 71(7): 1586–1597. doi: 10.1109/TC.2021.3097174 [2] HUANG Yu, AHMAD H, FORREST S, et al. Applying automated program repair to dataflow programming languages[C]. 2021 IEEE/ACM International Workshop on Genetic Improvement (GI), Madrid, Spain, 2021: 21–22. [3] PATTERSON D A and HENNESSY J L. Computer Organization and Design RISC-V Edition: The Hardware Software Interface[M]. China Machine Press, 2019: v–vii. [4] KAMKIN A S and KOTSYNYAK A M. Specification-based test program generation for MIPS64 memory management units[J]. Proceedings of the Institute for System Programming of the RAS, 2016, 28(4): 99–114. doi: 10.15514/ISPRAS-2016-28(4)-6 [5] AHMADI-POUR S, HERDT V, and DRECHSLER R. Constrained random verification for RISC-V: Overview, evaluation and discussion[C/OL]. MBMV 2021; 24th Workshop, 2021: 1–8. [6] BRUNS N, HERDT V, JENTZSCH E, et al. Cross-level processor verification via endless randomized instruction stream generation with coverage-guided aging[C]. 2022 Design, Automation & Test in Europe Conference & Exhibition (DATE), Antwerp, Belgium, 2022: 1123–1126. [7] HERDT V, GROßE D, and DRECHSLER R. Towards specification and testing of RISC-V ISA compliance[C]. 2020 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 2020: 995–998. [8] CHUPILKO M, KAMKIN A, and PROTSENKO A. Open-source validation suite for RISC-V[C]. 2019 20th International Workshop on Microprocessor/SoC Test, Security and Verification (MTV), Austin, USA, 2019: 7–12. [9] 谭坚, 罗巧玲, 王丽一, 等. 基于SMT求解器的微处理器指令验证数据约束生成技术[J]. 计算机研究与发展, 2020, 57(12): 2694–2702. doi: 10.7544/issn1000-1239.2020.20190718TAN Jian, LUO Qiaoling, WANG Liyi, et al. Data constraint generation technology for microprocessor instruction verification based on SMT solver[J]. Journal of Computer Research and Development, 2020, 57(12): 2694–2702. doi: 10.7544/issn1000-1239.2020.20190718 [10] ADIR A, ALMOG E, FOURNIER L, et al. Genesys-Pro: Innovations in test program generation for functional processor verification[J]. IEEE Design & Test of Computers, 2004, 21(2): 84–93. doi: 10.1109/MDT.2004.1277900 [11] BRAUN M, FINE S, and ZIV A. Enhancing the efficiency of Bayesian network based coverage directed test generation[C]. Proceedings Ninth IEEE International High-Level Design Validation and Test Workshop, Sonoma, USA, 2004: 75–80. [12] PFEIFER N, ZIMPEL B V, ANDRADE G A G, et al. A reinforcement learning approach to directed test generation for shared memory verification[C]. 2020 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 2020: 538–543. [13] HERDT V, GROßE D, and DRECHSLER R. Closing the RISC-V compliance gap: Looking from the negative testing side[C]. 2020 57th ACM/IEEE Design Automation Conference (DAC), San Francisco, USA, 2020: 1–6. [14] WATERMAN A, LEE Y, PATTERSON D A, et al. The RISC-V instruction set manual. Volume I: User-level ISA, version 2.0[R]. Technical Report No. UCB/EECS-2014-54, 2014: 9–26. [15] AYADI Z, BOULILA W, FARAH I R, et al. Resolution methods for constraint satisfaction problem in remote sensing field: A survey of static and dynamic algorithms[J]. Ecological Informatics, 2022, 69: 101607. doi: 10.1016/j.ecoinf.2022.101607 [16] UC Berkeley Architecture Research, RISC-V ISA Tests[EB/OL]. https://github.com/riscv/riscv-tests, 2022. [17] BIN E, EMEK R, SHUREK G, et al. Using a constraint satisfaction formulation and solution techniques for random test program generation[J]. IBM Systems Journal, 2002, 41(3): 386–402. doi: 10.1147/sj.413.0386 [18] HERDT V, GROßE D, LE H M, et al. Verifying instruction set simulators using coverage-guided fuzzing[C]. 2019 Design, Automation & Test in Europe Conference & Exhibition (DATE), Florence, Italy, 2019: 360–365. [19] XI Yuhao, ZHANG Zhendong, WANG Yuze, et al. A heterogeneous RISC-V SoC for confidential computing and password recovery[C]. 2022 7th International Conference on Integrated Circuits and Microsystems (ICICM), Xi’an, China, 2022: 500–504. -





 下载:
下载:





 下载:
下载:
