A Traffic Anomaly Detection Method Based on the Joint Model of Attention Mechanism and One-Dimensional Convolutional Neural Network-Bidirectional Long Short Term Memory
-
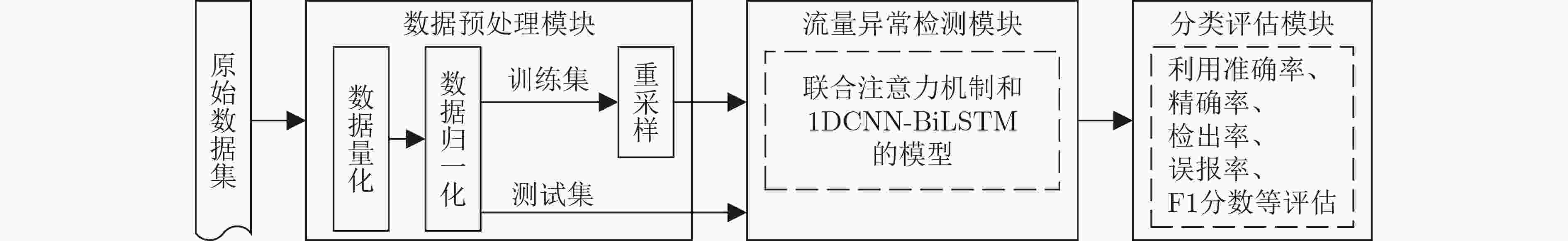
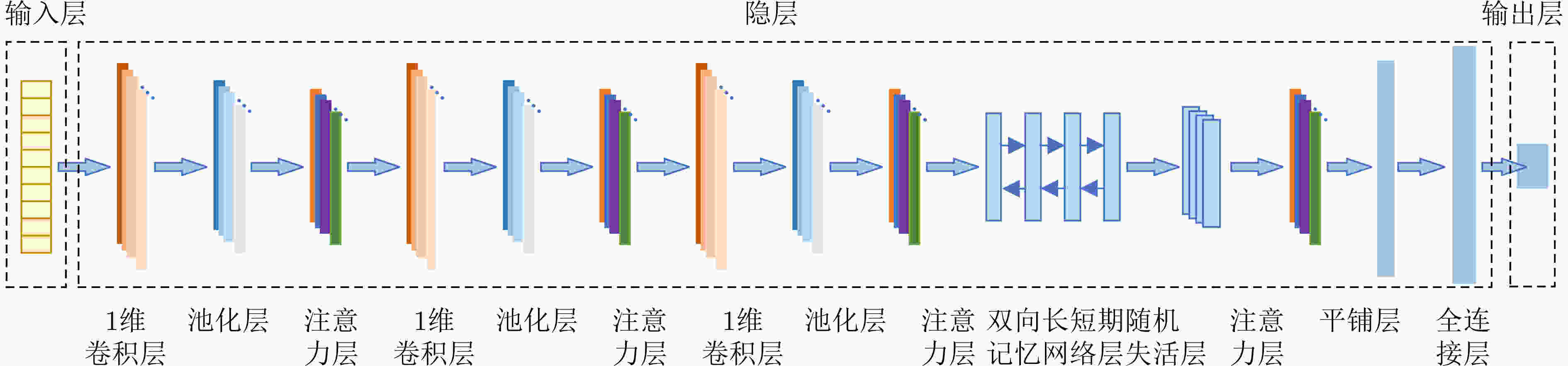
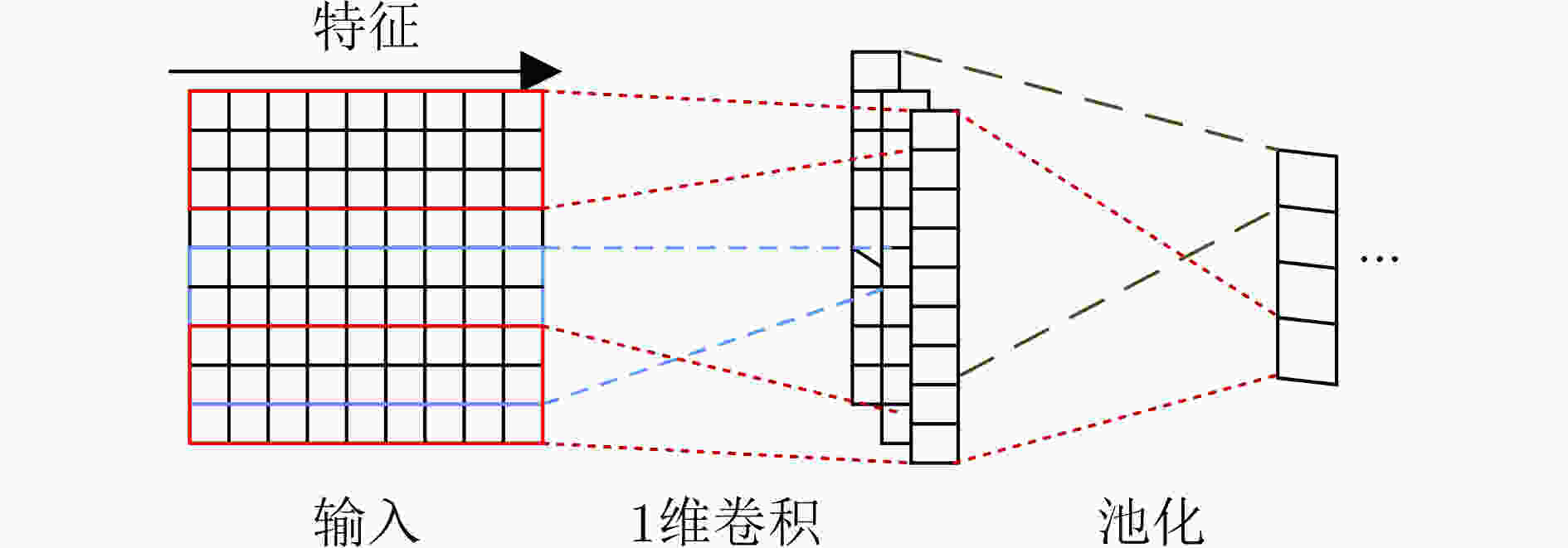
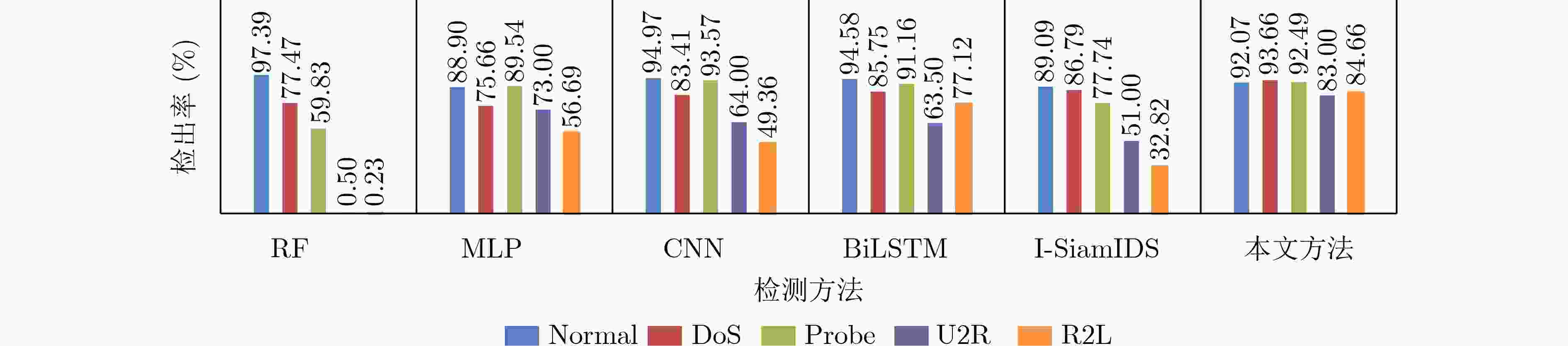
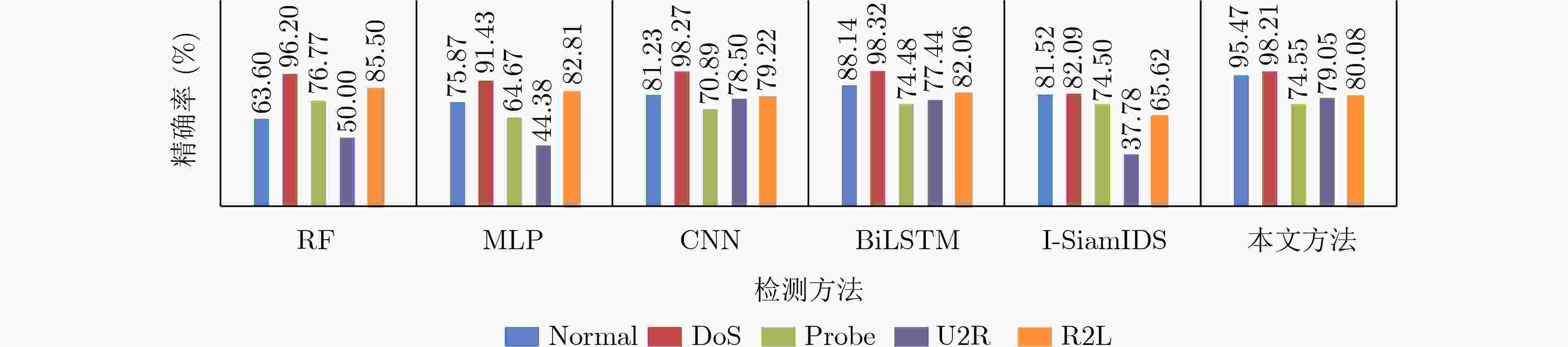
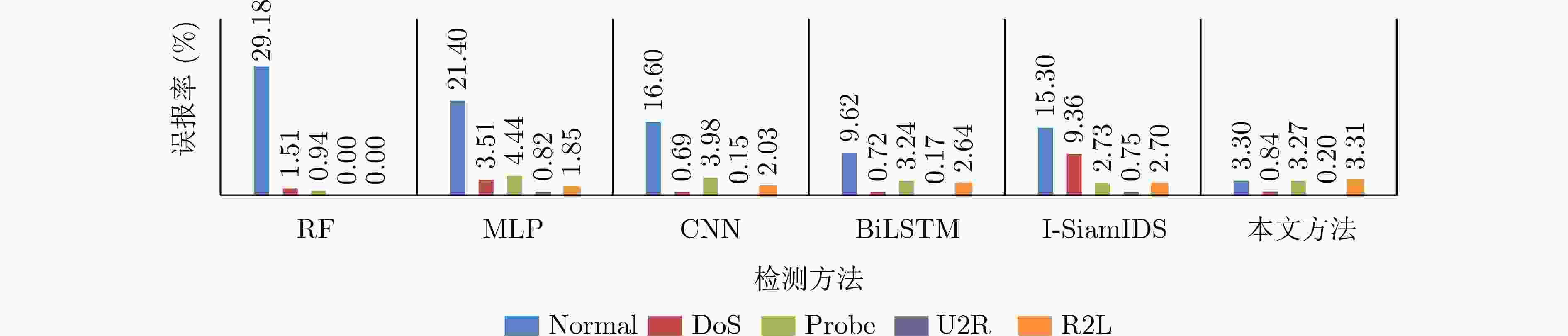
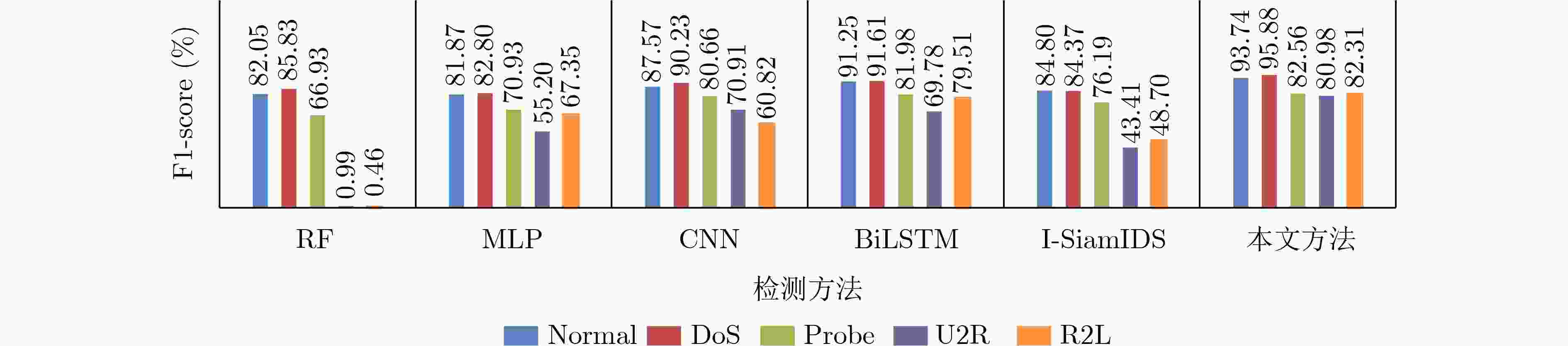
摘要: 针对流量数据集中类别不平衡限制了分类模型对少数类攻击流量的检测性能这一问题,该文提出一种基于联合注意力机制和1维卷积神经网络-双向长短期记忆网络(1DCNN-BiLSTM)模型的流量异常检测方法。首先在数据预处理过程中利用BorderlineSMOTE方法对流量数据不平衡训练样本预处理,使得各类流量数据均衡,有助于后续模型对各类数据的充分训练。然后设计联合注意力机制和1DCNN-BiLSTM的模型对流量数据进行训练,提取流量数据的局部和长距离序列特征并进行分类,通过注意力机制将对分类有用的特征按其重要性赋予权值,提高对少数攻击类的检出率。实验结果表明,同几种现有方法相比,该文方法对NSL-KDD和CICIDS2017数据集的检测准确率最高(可达93.17%和98.65%),对NSL-KDD数据集中的提权攻击(U2R)攻击流量的检出率至少提升13.70%,证明了该文方法提升少数类攻击流量检出率的有效性。
-
关键词:
- 流量异常检测 /
- 类别不平衡 /
- 一维卷积神经网络-双向长短期记忆网络 /
- 注意力机制
Abstract: Considering the problem that the class imbalance of traffic dataset limits the performance of the model to the minority class attack traffic, a traffic anomaly detection method based on the joint model of attention mechanism and One-Dimensional Convolutional Neural Network - Bidirectional Long Short Term Memory (1DCNN-BiLSTM) is proposed. First, in the data preprocessing, the BorderlineSMOTE method is used to preprocess the imbalanced traffic training data, so that the quantities of different categories are balanced, which is helpful for the model to train various types fully. Then, the joint model of attention mechanism and 1DCNN-BiLSTM is designed to extract the local and long-distance sequence features of the traffic data. The features useful for classification are assigned weights according to their importance through the attention mechanism, which makes the model improve the detection rate of attack classes. Experimental results show that the proposed method has the highest accuracy for NSL-KDD and CICIDS2017 datasets (up to 93.17% and 98.65%). The proposed method improves the detection rate of User to Root(U2R) attack traffic in NSL-KDD dataset by at least 13.70%, which proves the effectiveness of the proposed method in improving the detection rate of minority attack traffic. -
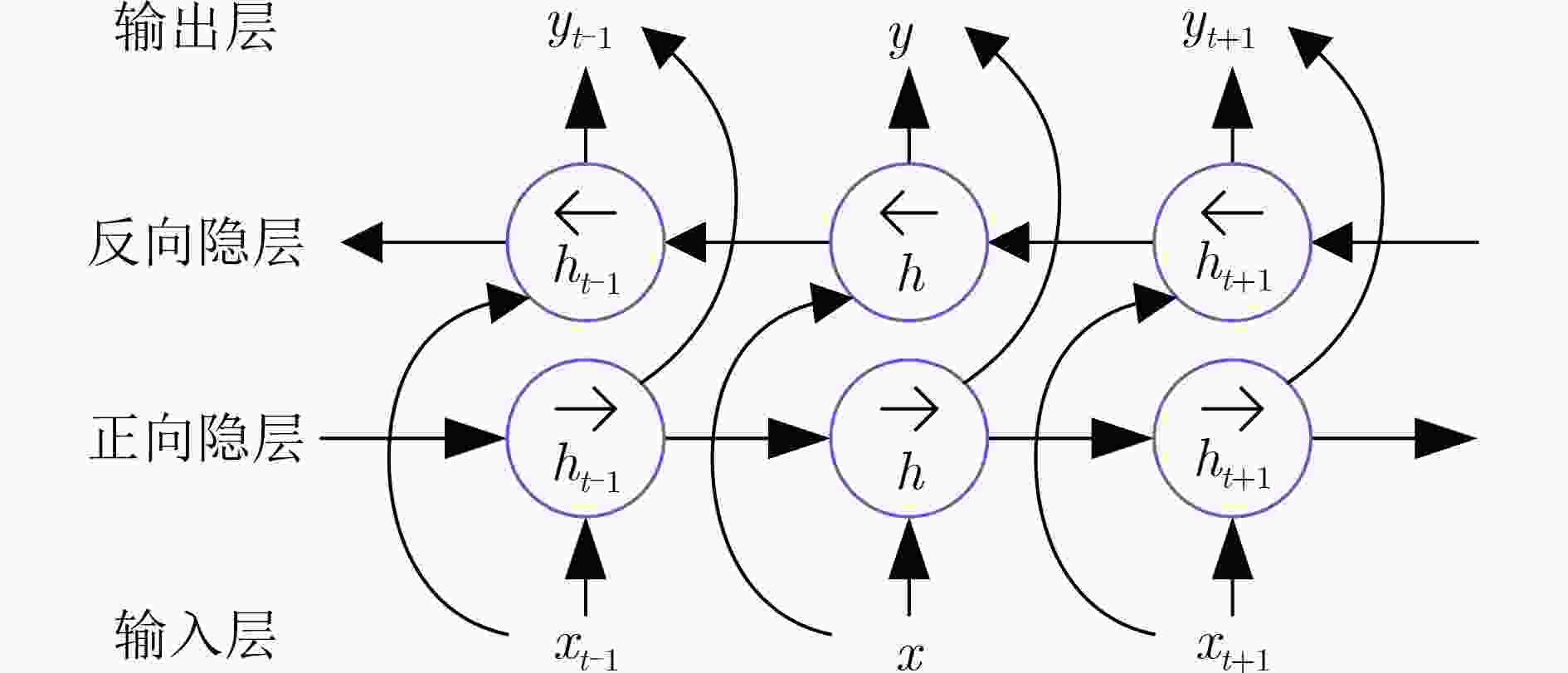
算法1 正向LSTM和反向LSTM计算 正向LSTM 反向LSTM $ {{\mathbf{i}}_t} = \sigma ({{\mathbf{W}}_i}[{{\mathbf{h}}_{t - 1}},{{\mathbf{x}}_t}] + {{\mathbf{b}}_i}) $ $ {{\boldsymbol{i}}_t} = \sigma ({{\boldsymbol{W}}_i}[{{\boldsymbol{h}}_{t + 1}},{{\boldsymbol{x}}_t}] + {{\boldsymbol{b}}_i}) $ $ {{\boldsymbol{f}}_t} = \sigma ({{\boldsymbol{W}}_f}[{{\boldsymbol{h}}_{t - 1}},{{\boldsymbol{x}}_t}] + {{\boldsymbol{b}}_f}) $ $ {{\boldsymbol{f}}_t} = \sigma ({{\boldsymbol{W}}_f}[{{\boldsymbol{h}}_{t + 1}},{{\boldsymbol{x}}_t}] + {{\boldsymbol{b}}_f}) $ $ {{\boldsymbol{g}}_t} = \tanh ({{\boldsymbol{W}}_c}[{{\boldsymbol{h}}_{t - 1}},{{\boldsymbol{x}}_t}] + {{\boldsymbol{b}}_c}) $ $ {{\boldsymbol{g}}_t} = \tanh ({{\boldsymbol{W}}_c}[{{\boldsymbol{h}}_{t + 1}},{{\boldsymbol{x}}_t}] + {{\boldsymbol{b}}_c}) $ $ {{\boldsymbol{C}}_t} = {{\boldsymbol{i}}_t} \odot {{\boldsymbol{g}}_t} + {{\boldsymbol{f}}_t} \odot {{\boldsymbol{C}}_{t - 1}} $ $ {{\boldsymbol{C}}_t} = {{\boldsymbol{i}}_t} \odot {{\boldsymbol{g}}_t} + {{\boldsymbol{f}}_t} \odot {{\boldsymbol{C}}_{t + 1}} $ $ {{\boldsymbol{o}}_t} = \sigma ({{\boldsymbol{W}}_o}[{{\boldsymbol{h}}_{t - 1}},{{\boldsymbol{x}}_t}] + {{\boldsymbol{b}}_o}) $ $ {{\boldsymbol{o}}_t} = \sigma ({{\boldsymbol{W}}_o}[{{\boldsymbol{h}}_{t + 1}},{{\boldsymbol{x}}_t}] + {{\boldsymbol{b}}_o}) $ ${{\boldsymbol{h'}}_t} = {{\boldsymbol{o}}_t} \odot \tanh ({{\boldsymbol{C}}_t})$ ${{\boldsymbol{h''}}_t} = {{\boldsymbol{o}}_t} \odot \tanh ({{\boldsymbol{C}}_t})$ 表 1 NSL-KDD数据集数据分布
类别 正常流量 DoS Probe U2R R2L 总计 KDDTrain+_20Percent 13 449 9 234 2 289 11 209 25 192 KDDTest+ 9 711 7 458 2 116 200 3 059 22 544 表 2 CICIDS2017数据集数据分布
类别 正常流量 Bot DDoS DoS GoldenEye DoS Hulk DoS Slowhttptest DoS Slowloris FTP-Patator 数量 2 271 320 1 956 128 025 10 293 230 124 5 499 5 796 7 935 类别 Heartbleed Infiltration PortScan SSH-Patator Web Attack Brute Force Web Attack-SQL Injection Web Attack-XSS 总计 数量 11 36 158 804 2 897 1 507 21 652 2 824 876 表 3 基于NSL-KDD数据集的二分类检测结果(%)
模型 采样方法 准确率 精确率 检出率 误报率 F1-score MLP 78.73 90.58 69.97 9.69 78.92 ROS 79.08 92.03 69.34 8.04 79.04 BorderlineSMOTE 79.92 93.26 71.02 6.72 79.82 RF 80.17 90.84 72.46 9.65 80.62 ROS 80.52 90.79 73.21 9.81 81.06 BorderlineSMOTE 80.88 90.18 74.53 10.73 81.61 CNN[19] 81.43 89.04 76.91 12.58 82.38 ROS 82.17 90.65 76.55 9.95 83.07 BorderlineSMOTE 84.20 91.69 78.96 8.87 84.91 BiLSTM[14] 85.18 80.16 89.03 17.73 84.36 ROS 86.73 92.49 83.46 8.96 87.74 BorderlineSMOTE 87.01 92.54 83.96 7.95 88.04 DTNB+MOEFS[23] 83.04 82.79 82.29 16.73 82.54 ROS 85.96 86.02 85.14 14.09 85.58 BorderlineSMOTE 87.57 88.49 86.20 13.30 87.33 1DCNN-BiLSTM 84.37 82.16 85.05 13.56 83.58 ROS 86.13 84.92 86.23 12.74 85.57 BorderlineSMOTE 89.06 88.42 88.92 10.34 88.67 本文模型 88.94 90.90 89.53 11.84 90.20 ROS 89.54 91.66 89.78 10.79 90.71 BorderlineSMOTE 93.17 93.52 94.55 8.64 94.03 -
[1] Statista Research Department. Number of internet of things (IoT) connected devices worldwide from 2019 to 2021, with forecasts from 2022 to 2030[EB/OL]. https://www.statista.com/statistics/1183457/iot-connected-devices-worldwide/, 2022. [2] SU Yu, QI Kaiyue, DI Chong, et al. Learning automata based feature selection for network traffic intrusion detection[C]. 2018 IEEE Third International Conference on Data Science in Cyberspace, Guangzhou, China, 2018: 622–627. [3] SYARIF I, PRUGEL-BENNETT A, and WILLS G. Unsupervised clustering approach for network anomaly detection[C]. 4th International Conference on Networked Digital Technologies, Berlin, Germany, 2012: 135–145. [4] BO Li and YUAN Chenyuan. The research of intrusion detection based on support vector machine[C]. 2009 International Conference on Computer and Communications Security, Hong Kong, China, 2009: 21–23. [5] TENGL S, ZHANG Zhenhua, TENG Luyao, et al. A collaborative intrusion detection model using a novel optimal weight strategy based on genetic algorithm for ensemble classifier[C]. 2018 IEEE 22nd International Conference on Computer Supported Cooperative Work in Design. Nanjing, China, 2018: 761–766. [6] SORNSUWIT P and JAIYEN S. Intrusion detection model based on ensemble learning for U2R and R2L attacks[C]. 2015 7th International Conference on Information Technology and Electrical Engineering, Chiang Mai, Thailand, 2015: 354–359. [7] NEGANDHI P, TRIVEDI Y, and MANGRULKAR R. Intrusion detection system using random forest on the NSL-KDD dataset[C]. Emerging Research in Computing, Information, Communication and Applications, Singapore, 2019: 519–531. [8] KORONIOTIS N, MOUSTAFA N, SITNIKOVA E, et al. Towards developing network forensic mechanism for botnet activities in the IoT based on machine learning techniques[C]. International Conference on Mobile Networks and Management, Cham, Switzerland, 2018: 30–44. [9] D'HOOGE L, WAUTERS T, VOLCKAERT B, et al. Inter-dataset generalization strength of supervised machine learning methods for intrusion detection[J]. Journal of Information Security and Applications, 2020, 54: 102564. doi: 10.1016/j.jisa.2020.102564 [10] TANG T A, MHAMDI L, MCLERNON D, et al. Deep learning approach for network intrusion detection in software defined networking[C]. 2016 International Conference on Wireless Networks and Mobile Communications, Fez, Morocco, 2016: 258–263. [11] SHONE N, NGOC T N, PHAI V D, et al. A deep learning approach to network intrusion detection[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2018, 2(1): 41–50. doi: 10.1109/TETCI.2017.2772792 [12] 董书琴, 张斌. 基于深度特征学习的网络流量异常检测方法[J]. 电子与信息学报, 2020, 42(3): 695–703. doi: 10.11999/JEIT190266DONG Shuqin and ZHANG Bin. Network traffic anomaly detection method based on deep features learning[J]. Journal of Electronics &Information Technology, 2020, 42(3): 695–703. doi: 10.11999/JEIT190266 [13] 缪祥华, 单小撤. 基于密集连接卷积神经网络的入侵检测技术研究[J]. 电子与信息学报, 2020, 42(11): 2706–2712. doi: 10.11999/JEIT190655MIAO Xianghua and SHAN Xiaoche. Research on intrusion detection technology based on densely connected convolutional neural networks[J]. Journal of Electronics &Information Technology, 2020, 42(11): 2706–2712. doi: 10.11999/JEIT190655 [14] SIVAMOHAN S, SRIDHAR S S, and KRISHNAVENI S. An effective recurrent neural network (RNN) based intrusion detection via bi-directional long short-term memory[C]. 2021 International Conference on Intelligent Technologies (CONIT), Hubli, India, 2021: 1–5. [15] EBENUWA S H, SHARIF M S, ALAZAB M, et al. Variance ranking attributes selection techniques for binary classification problem in imbalance data[J]. IEEE Access, 2019, 7: 24649–24666. doi: 10.1109/ACCESS.2019.2899578 [16] CHAWLA N V, BOWYER K W, HALL L O, et al. SMOTE: Synthetic minority over-sampling technique[J]. Journal of Artificial Intelligence Research, 2002, 16: 321–357. doi: 10.1613/jair.953 [17] HE Haibo, BAI Yang, GARCIA E A, et al. ADASYN: Adaptive synthetic sampling approach for imbalanced learning[C]. 2008 IEEE International Joint Conference on Neural Networks (IEEE World Congress on Computational Intelligence), Hong Kong, China, 2008: 1322–1328. [18] HE Haibo and GARCIA E A. Learning from imbalanced data[J]. IEEE Transactions on Knowledge and Data Engineering, 2009, 21(9): 1263–1284. doi: 10.1109/TKDE.2008.239 [19] YU Yingwei and BIAN Naizheng. An intrusion detection method using few-shot learning[J]. IEEE Access, 2020, 8: 49730–49740. doi: 10.1109/ACCESS.2020.2980136 [20] CHOWDHURY M M U, HAMMOND F, KONOWICZ G, et al. A few-shot deep learning approach for improved intrusion detection[C]. 2017 IEEE 8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON), New York, USA, 2017: 456–462. [21] CHORAŚ M and PAWLICKI M. Intrusion detection approach based on optimised artificial neural network[J]. Neurocomputing, 2021, 452: 705–715. doi: 10.1016/j.neucom.2020.07.138 [22] BEDI P, GUPTA N, and JINDAL V. I-SiamIDS: An improved Siam-IDS for handling class imbalance in network-based intrusion detection systems[J]. Applied Intelligence, 2021, 51(2): 1133–1151. doi: 10.1007/s10489-020-01886-y [23] PANIGRAHI R, BORAH S, PRAMANIK M, et al. Intrusion detection in cyber-physical environment using hybrid Naïve Bayes-Decision table and multi-objective evolutionary feature selection[J]. Computer Communications, 2022, 188: 133–144. doi: 10.1016/j.comcom.2022.03.009 -





 下载:
下载:


 下载:
下载:
