Provably Secure Distributed Efficient Edge Authentication Protocol with Anonymity in Internet of Vehicles
-
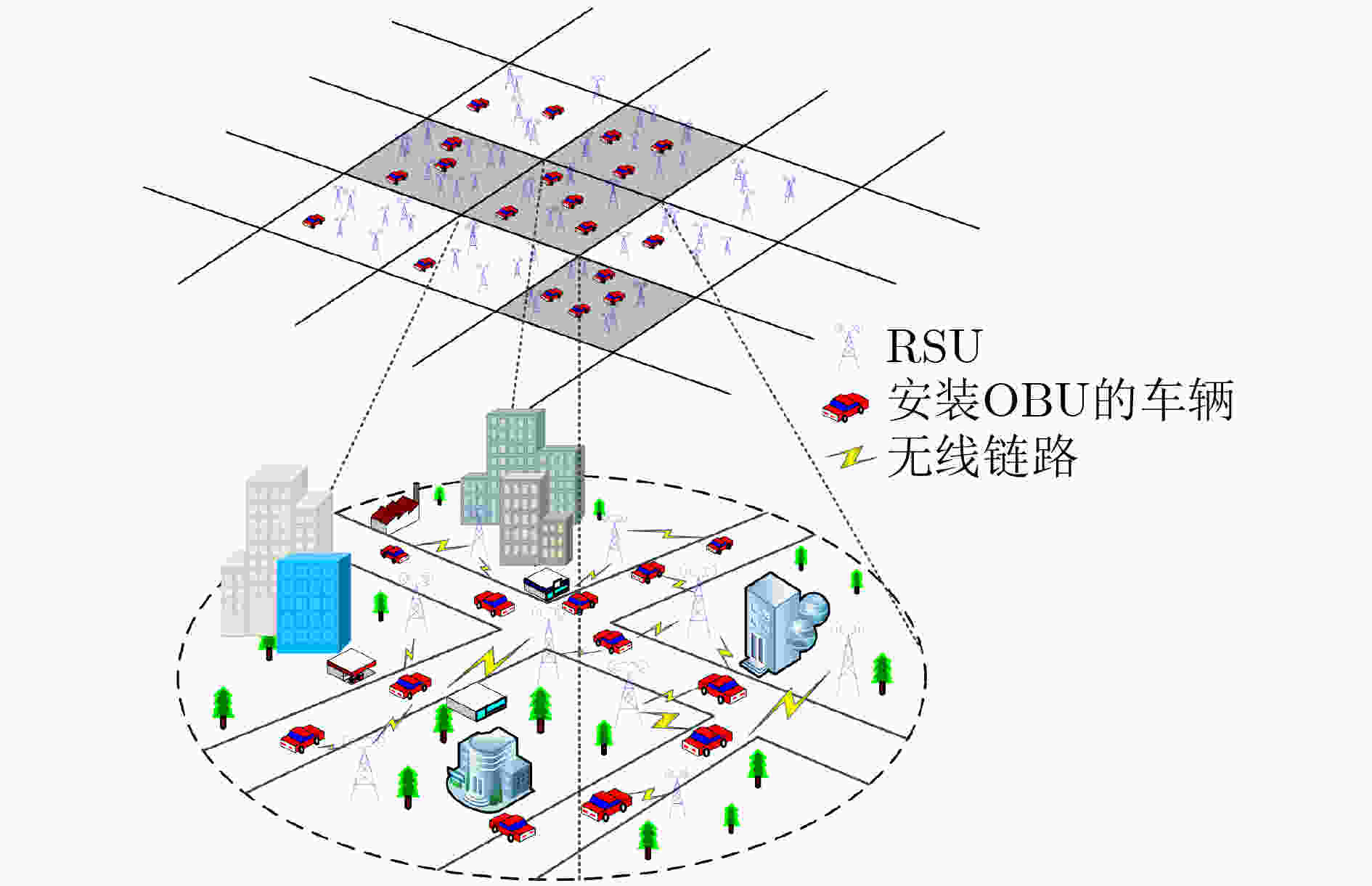
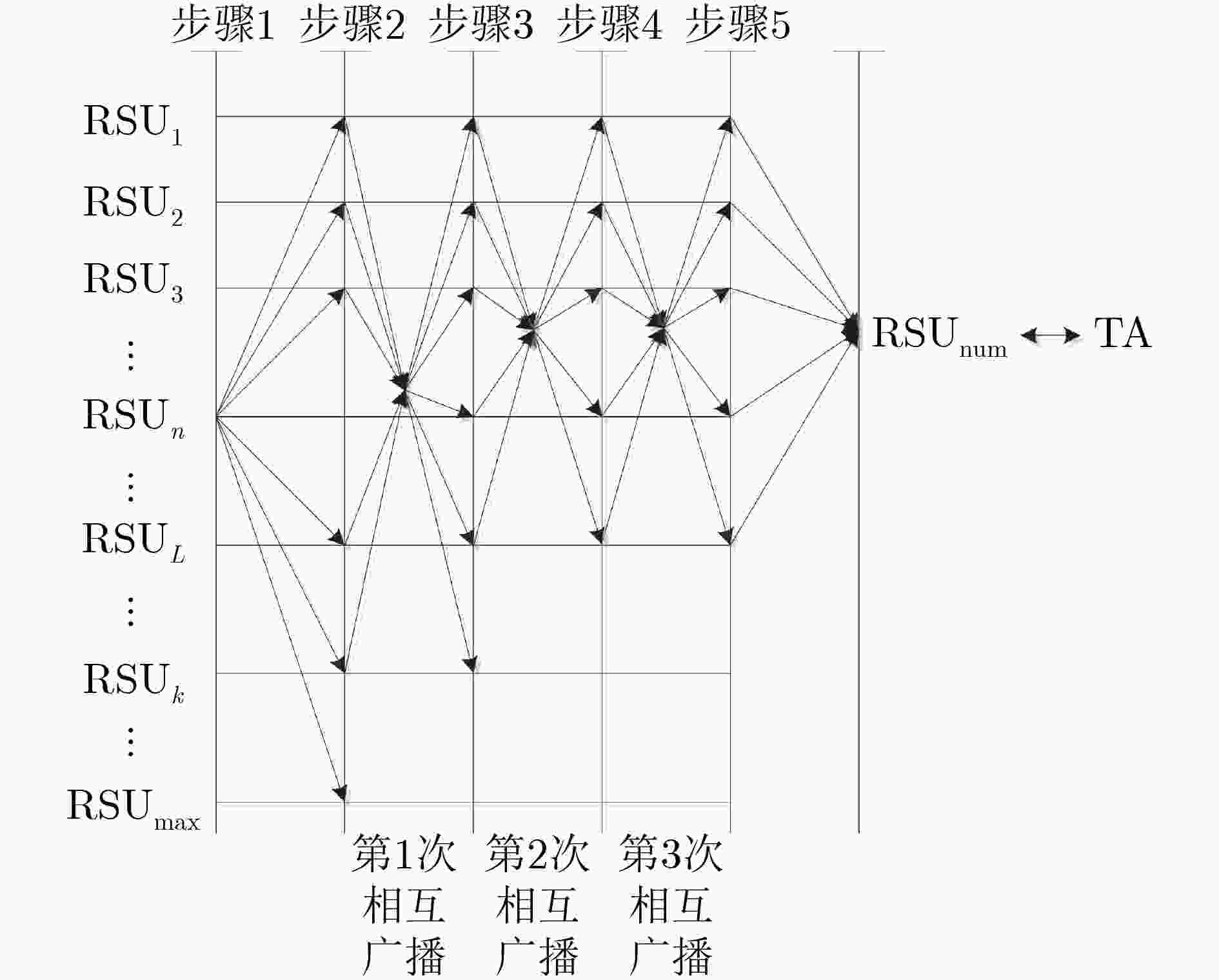
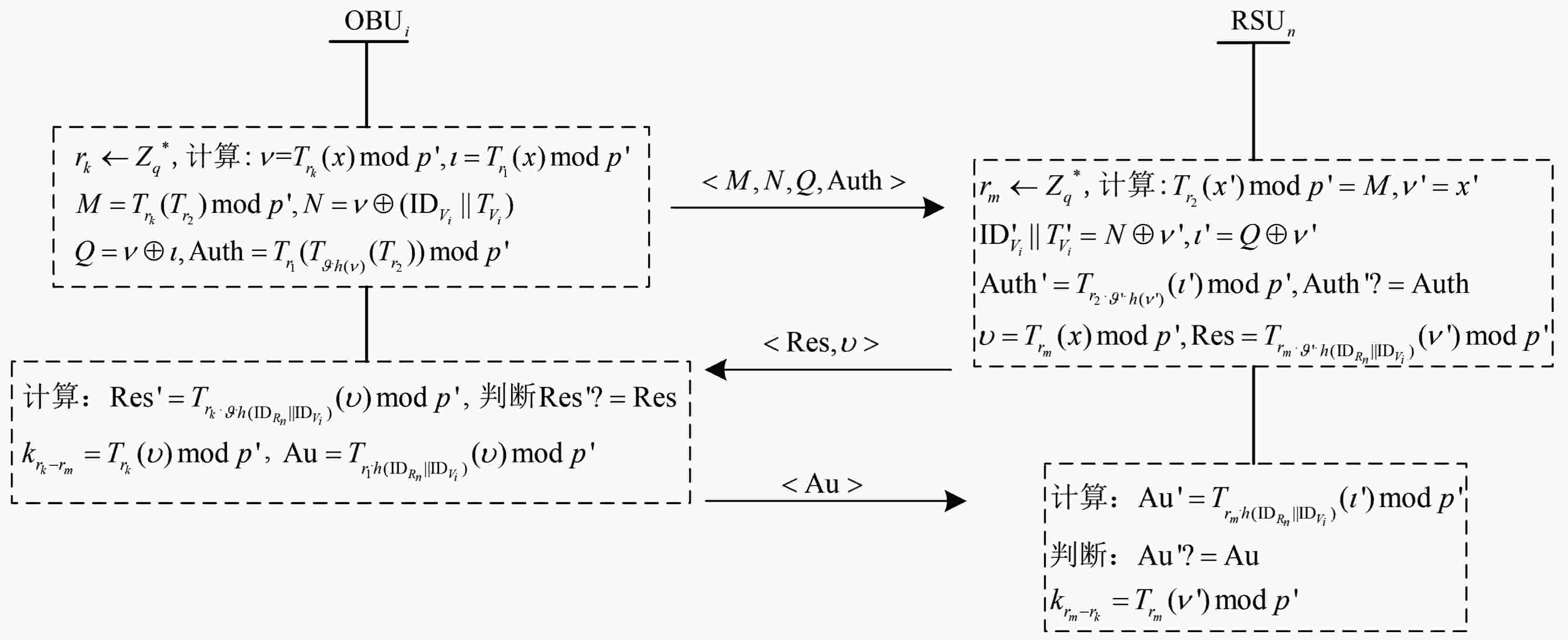
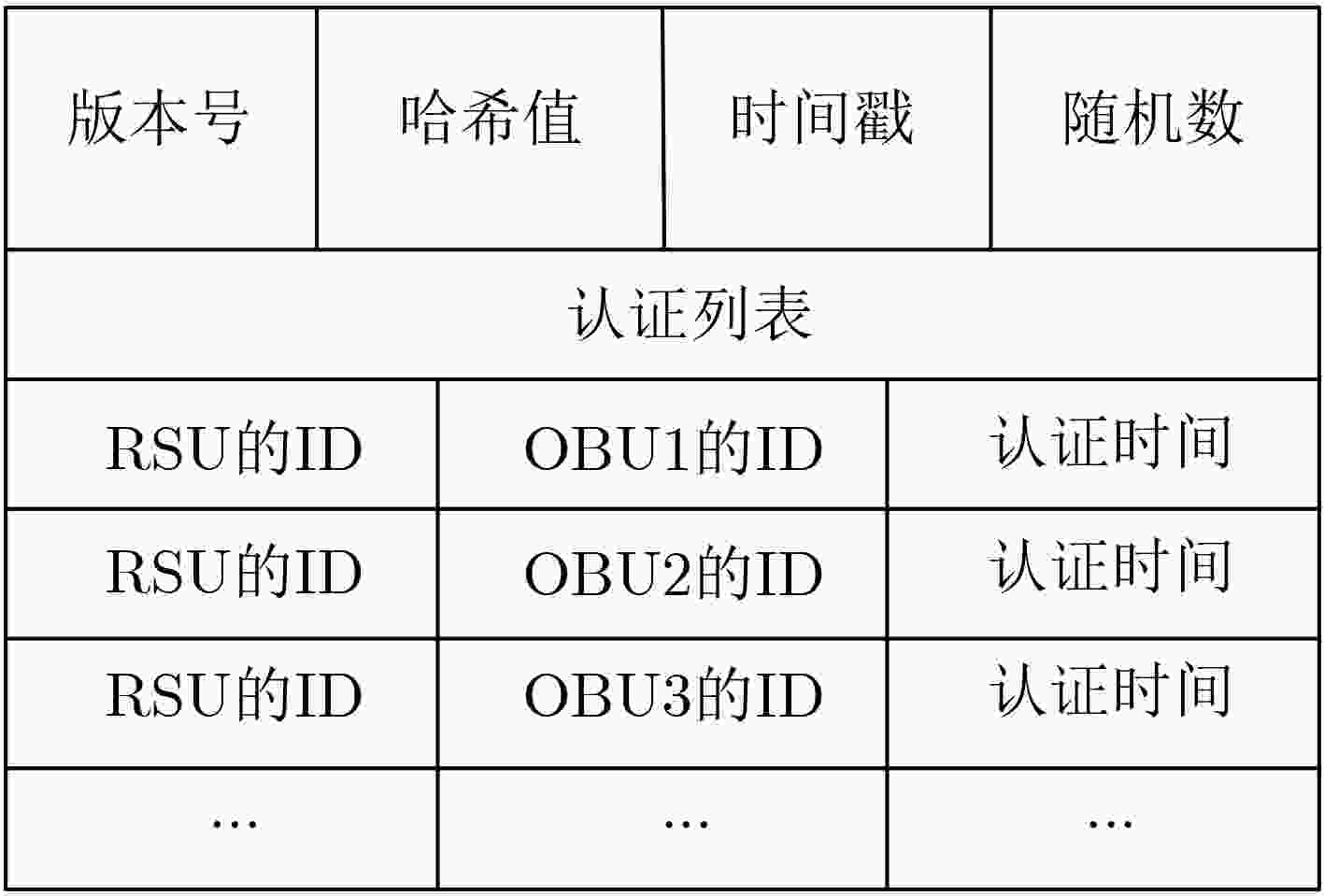
摘要: 针对当前车联网(IoV)中的分布式认证协议直接依赖于半可信路边单元(RSU)的问题,该文提出一种新的分布式认证模型。该模型中的RSU通过3阶段广播自发建立边缘认证区,利用区域内的RSU同步保存车辆的认证记录,RSU可以通过校验节点同步保存的认证记录来防止恶意RSU的异常认证行为。然后,利用切比雪夫混沌映射设计了IoV中的分布式匿名认证协议,通过车辆发送消息不直接携带身份信息的方式来避免假名机制所带来的存储负担。最后,利用随机预言机对协议安全性进行了证明。仿真结果表明所提方案具有更低的认证时延和通信成本。Abstract: Considering the problem that the current distributed authentication protocols in the Internet of Vehicles (IoV) directly depend on semi-trusted Road Side Units (RSU), a new distributed authentication model is proposed. The RSUs in this model establish automatically the edge authentication area through a three-stage broadcast, and these RSUs in the area save synchronously the vehicle certification records. RSU can prevent abnormal authentication behavior of malicious RSU by verifying the authentication records saved synchronously by nodes. Then, a distributed anonymous authentication protocol in IoV is designed by using Chebyshev chaotic mapping, to avoid the storage burden caused by the pseudonym mechanism, the vehicle sends messages without directly carrying identity information. Finally, the security of the protocol is proved by using random oracle. The simulation results show that the proposed scheme has lower authentication delay and communication cost.
-
Key words:
- Internet of Vehicles (IoV) /
- Distributed authentication /
- Chaotic mapping /
- Random oracle
-
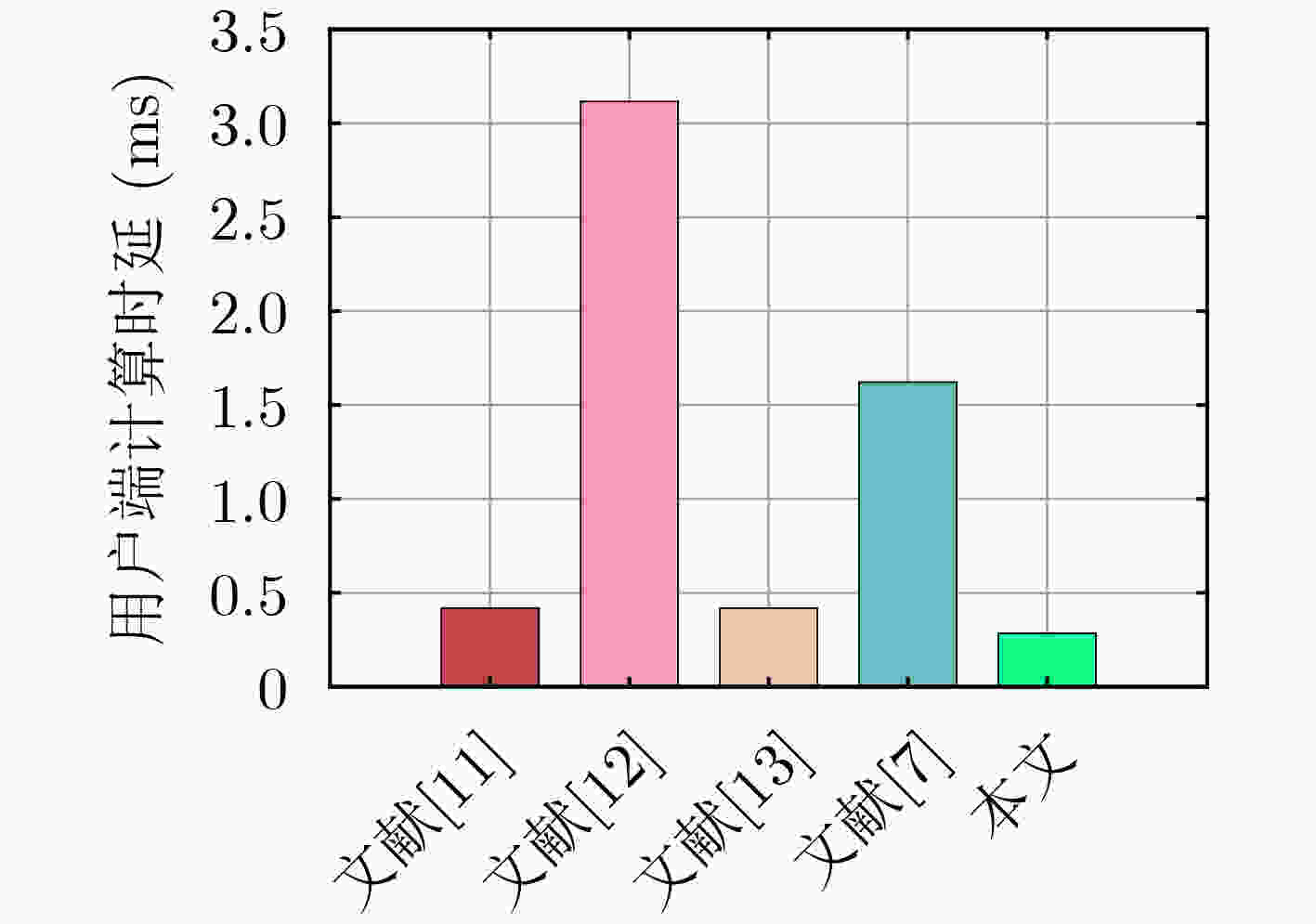
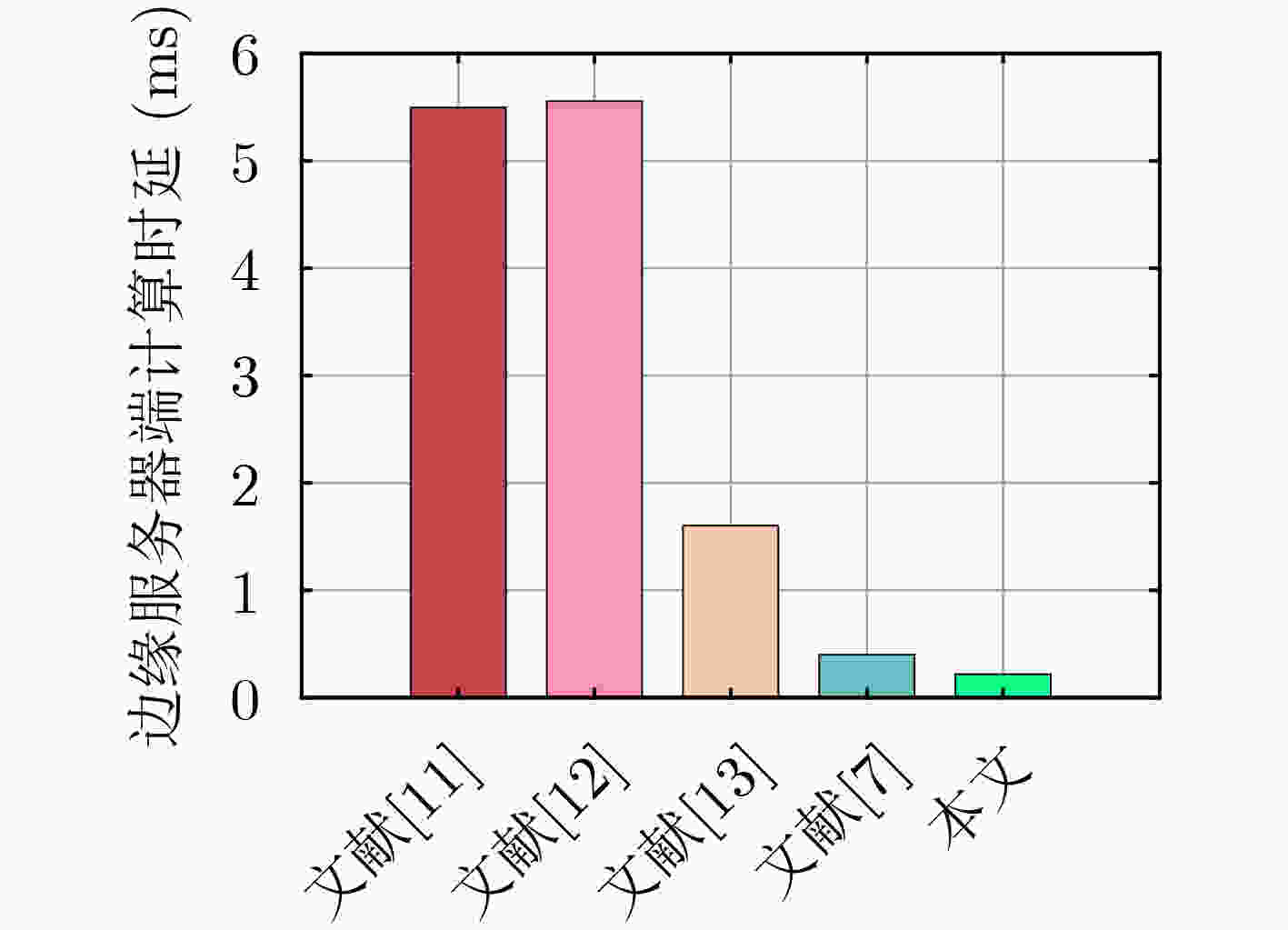
表 1 认证时延对比(ms)
方案 用户端 边缘服务器端 文献[11] ${\text{5} }{ { {T} }_{\text{h} } }{\text{ + } }{ { {T} }_{\text{e} } }{\text{ + 4} }{ { {T} }_{ {\text{mul} } } } \approx 0.418\;8$ ${\text{4} }{ { {T} }_{\text{h} } }{\text{ + 2} }{ { {T} }_{\text{e} } }{\text{ + 4} }{ { {T} }_{\text{p} } }{\text{ + 2} }{ { {T} }_{ {\text{mul} } } } \approx 5.497\;6$ 文献[12] ${\text{7} }{ { {T} }_{\text{h} } }{\text{ + 2} }{ { {T} }_{\text{e} } }{\text{ + 2} }{ { {T} }_{\text{p} } }{\text{ + 4} }{ { {T} }_{ {\text{mul} } } } \approx 3.116\;2$ ${\text{5} }{ { {T} }_{\text{h} } }{\text{ + 2} }{ { {T} }_{\text{e} } }{\text{ + 4} }{ { {T} }_{\text{p} } }{\text{ + 3} }{ { {T} }_{ {\text{mul} } } } \approx 5.557\;0$ 文献[13] ${\text{5} }{ { {T} }_{\text{h} } }{\text{ + } }{ { {T} }_{\text{e} } }{\text{ + 4} }{ { {T} }_{ {\text{mul} } } } \approx 0.418\;8$ ${\text{5} }{ { {T} }_{\text{h} } }{\text{ + } }{ { {T} }_{\text{p} } }{\text{ + 6} }{ { {T} }_{ {\text{mul} } } } \approx 1.602\;5$ 文献[7] ${\text{10} }{ { {T} }_{\text{h} } }{\text{ + 30} }{ { {T} }_{ {\text{mul} } } } \approx 1.622\;0$ ${\text{5} }{ { {T} }_{\text{h} } }{\text{ + 7} }{ { {T} }_{ {\text{mul} } } } \approx 0.399\;8$ 本文 ${\text{2} }{ { {T} }_{\text{h} } }{\text{ + 8} }{ { {T} }_{ {\text{chev} } } } \approx 0.284\;8$ ${\text{2} }{ { {T} }_{\text{h} } }{\text{ + 6} }{ { {T} }_{ {\text{chev} } } } \approx 0.217\;6$ 表 2 通信轮数及通信开销对比
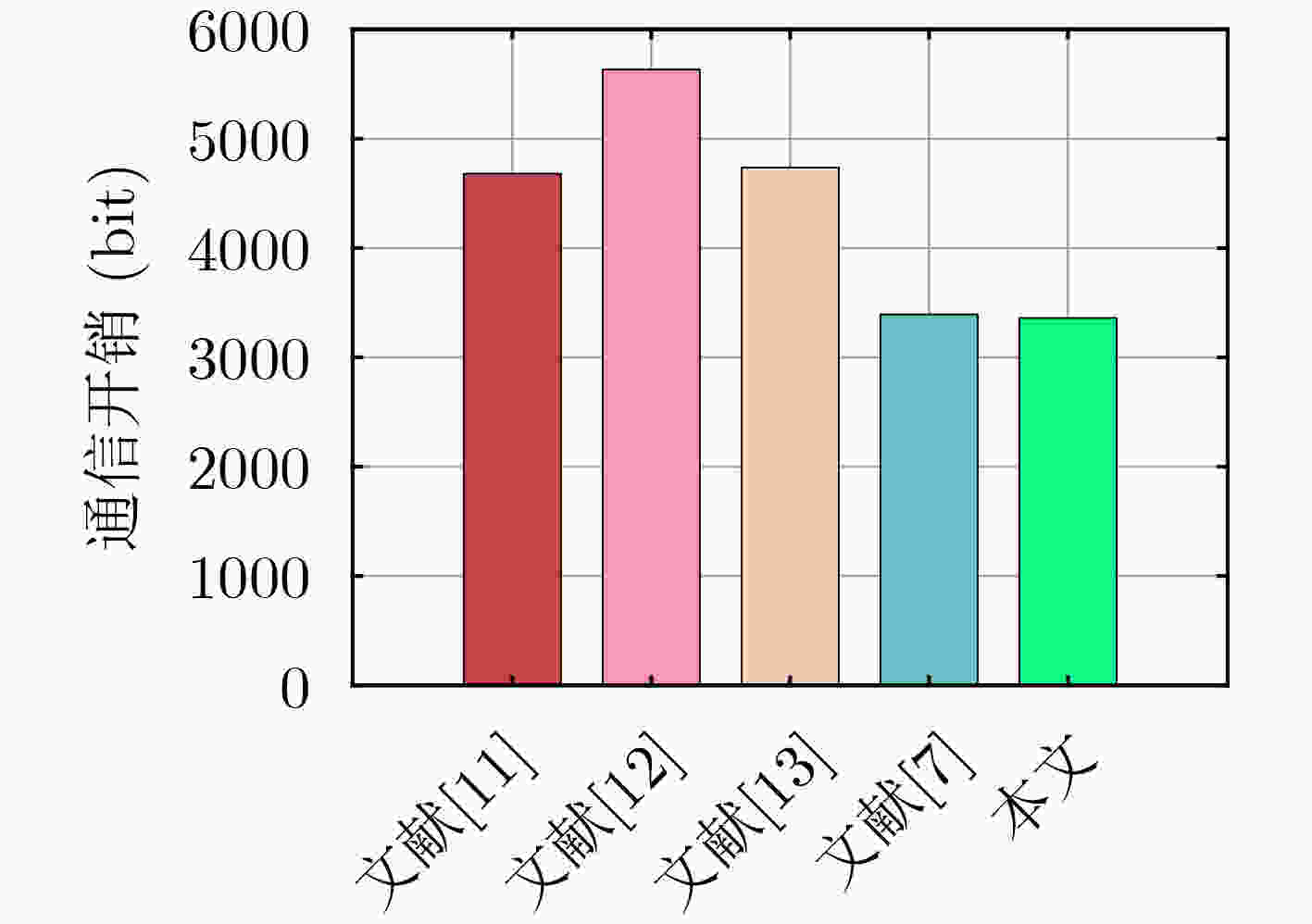
方案 通信轮数 通信开销(bit) 文献[11] 4 $3|{ { {W} }_{ {\text{mul} } } }| + |{ { {W} }_{\text{p} } }| + |{ { {W} }_{\text{H} } }| + |{ { {W} }_{ {\text{ID} } } }| = 4\;608$ 文献[12] 4 $4|{ { {W} }_{ {\text{mul} } } }| + |{ { {W} }_{\text{p} } }{\text{|} } + |{ { {W} }_{\text{H} } }| + |{ { {W} }_{ {\text{ID} } } }| = 5\;632$ 文献[13] 2 $4|{ { {W} }_{ {\text{mul} } } }| + 2|{ { {W} }_{\text{T} } }| + 2|{ { {W} }_{ { {\text{Z} }_{\text{q} } } }}| + |{ { {W} }_{ {\text{ID} } } }| = 4\;736$ 文献[7] 2 $2|{ { {W} }_{ {\text{mul} } } }| + 2|{ { {W} }_{\text{T} } }| + 4|{ { {W} }_{ {\text{ID} } } }| + 2|{ { {W} }_{\text{R} } }| = 3\;392$ 本文 3 $7|{ { {W} }_{ {\text{chev} } } }| = 3\;360$ -
[1] SUN Yunchuan, WU Lei, WU Shizhong, et al. Security and privacy in the internet of vehicles[C]. Proceedings of 2015 International Conference on Identification, Information, and Knowledge in the Internet of Things (IIKI), Beijing, China, 2015: 116–121. [2] YING Bidi and NAYAK A. Anonymous and lightweight authentication for secure vehicular networks[J]. IEEE Transactions on Vehicular Technology, 2017, 66(12): 10626–10636. doi: 10.1109/TVT.2017.2744182 [3] CHEN C M, XIANG Bin, LIU Yining, et al. A secure authentication protocol for internet of vehicles[J]. IEEE Access, 2019, 7: 12047–12057. doi: 10.1109/ACCESS.2019.2891105 [4] CUI Jie, WANG Yali, ZHANG Jing, et al. Full session key agreement scheme based on chaotic map in vehicular Ad hoc networks[J]. IEEE Transactions on Vehicular Technology, 2020, 69(8): 8914–8924. doi: 10.1109/TVT.2020.2997694 [5] WEI Lu, CUI Jie, ZHONG Hong, et al. Proven secure tree-based authenticated key agreement for securing V2V and V2I communications in VANETs[J]. IEEE Transactions on Mobile Computing, 2022, 21(9): 3280–3297. doi: 10.1109/TMC.2021.3056712 [6] CHUANG M C and LEE J F. TEAM: Trust-extended authentication mechanism for vehicular Ad hoc networks[J]. IEEE Systems Journal, 2014, 8(3): 749–758. doi: 10.1109/JSYST.2012.2231792 [7] YAO Yingying, CHANG Xiaolin, MIŠIĆ J, et al. BLA: Blockchain-assisted lightweight anonymous authentication for distributed vehicular fog services[J]. IEEE Internet of Things Journal, 2019, 6(2): 3775–3784. doi: 10.1109/JIOT.2019.2892009 [8] 刘雪艳, 王力, 郇丽娟, 等. 车联网环境下无证书匿名认证方案[J]. 电子与信息学报, 2022, 44(1): 295–304. doi: 10.11999/JEIT201069LIU Xueyan, WANG Li, HUAN Lijuan, et al. Certificateless anonymous authentication scheme for internet of vehicles[J]. Journal of Electronics &Information Technology, 2022, 44(1): 295–304. doi: 10.11999/JEIT201069 [9] LI Jiangtao, LI Yufeng, CAO Chenhong, et al. Conditional anonymous authentication with abuse-resistant tracing and distributed trust for internet of vehicles[J]. IEEE Internet of Things Journal, 2022, 9(11): 8749–8762. doi: 10.1109/JIOT.2021.3116422 [10] VIJAYAKUMAR P, AZEES M, KOZLOV S A, et al. An anonymous batch authentication and key exchange protocols for 6G enabled VANETs[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(2): 1630–1638. doi: 10.1109/TITS.2021.3099488 [11] TSAI J L and LO N W. A privacy-aware authentication scheme for distributed mobile cloud computing services[J]. IEEE Systems Journal, 2015, 9(3): 805–815. doi: 10.1109/JSYST.2014.2322973 [12] IRSHAD A, SHER M, AHMAD H F, et al. An improved multi-server authentication scheme for distributed mobile cloud computing services[J]. KSII Transactions on Internet and Information Systems, 2016, 10(12): 6092–6115. doi: 10.3837/TIIS.2016.12.021 [13] JIA Xiaoying, HE Debiao, KUMAR N, et al. A provably secure and efficient identity-based anonymous authentication scheme for mobile edge computing[J]. IEEE Systems Journal, 2020, 14(1): 560–571. doi: 10.1109/JSYST.2019.2896064 [14] KUMAR A and OM H. An enhanced and provably secure authentication protocol using Chebyshev chaotic maps for multi-server environment[J]. Multimedia Tools and Applications, 2021, 80(9): 14163–14189. doi: 10.1007/s11042-020-10320-x [15] BAGGA P, DAS A K, WAZID M, et al. Authentication protocols in Internet of vehicles: Taxonomy, analysis, and challenges[J]. IEEE Access, 2020, 8: 54314–54344. doi: 10.1109/ACCESS.2020.2981397 [16] LAI Chengzhe, ZHANG Min, CAO Jie, et al. SPIR: A secure and privacy-preserving incentive scheme for reliable real-time map updates[J]. IEEE Internet of Things Journal, 2020, 7(1): 416–428. doi: 10.1109/JIOT.2019.2953188 -





 下载:
下载:



 下载:
下载:
