| [1] |
ALTINEL D and KURT G K. Modeling of hybrid energy harvesting communication systems[J]. IEEE Transactions on Green Communications and Networking, 2019, 3(2): 523–534. doi: 10.1109/TGCN.2019.2908086
|
| [2] |
OZEL O and ULUKUS S. Achieving AWGN capacity under stochastic energy harvesting[J]. IEEE Transactions on Information Theory, 2012, 58(10): 6471–6483. doi: 10.1109/TIT.2012.2204389
|
| [3] |
HUANG Chuan, ZHANG Rui, and CUI Shuguang. Throughput maximization for the Gaussian relay channel with energy harvesting constraints[J]. IEEE Journal on Selected Areas in Communications, 2013, 31(8): 1469–1479. doi: 10.1109/JSAC.2013.130811
|
| [4] |
HO C K and ZHANG Rui. Optimal energy allocation for wireless communications with energy harvesting constraints[J]. IEEE Transactions on Signal Processing, 2012, 60(9): 4808–4818. doi: 10.1109/TSP.2012.2199984
|
| [5] |
李云, 唐英, 刘涵霄. 基于Q-Learning算法的毫微微小区功率控制算法[J]. 电子与信息学报, 2019, 41(11): 2557–2564. doi: 10.11999/JEIT181191LI Yun, TANG Ying, and LIU Hanxiao. Power control algorithm based on Q-Learning in femtocell[J]. Journal of Electronics &Information Technology, 2019, 41(11): 2557–2564. doi: 10.11999/JEIT181191
|
| [6] |
NEELY M J. Stochastic Network Optimization with Application to Communication and Queueing Systems[M]. Williston, USA: Morgan & Claypool, 2010: 45–62.
|
| [7] |
LI Yun, XIA Shichao, ZHENG Mengyan, et al. Lyapunov optimization based trade-off policy for mobile cloud offloading in heterogeneous wireless networks[J]. IEEE Transactions on Cloud Computing, To be publised. doi: 10.1109/TCC.2019.2938504
|
| [8] |
AMIRNAVAEI F and DONG Min. Online power control optimization for wireless transmission with energy harvesting and storage[J]. IEEE Transactions on Wireless Communications, 2016, 15(7): 4888–4901. doi: 10.1109/TWC.2016.2548459
|
| [9] |
DONG Min, LI Wen, and AMIRNAVAEI F. Online joint power control for two-hop wireless relay networks with energy harvesting[J]. IEEE Transactions on Signal Processing, 2018, 66(2): 463–478. doi: 10.1109/TSP.2017.2768040
|
| [10] |
ZHU Fengchao and YAO Minli. Improving physical-layer security for CRNs using SINR-based cooperative beamforming[J]. IEEE Transactions on Vehicular Technology, 2016, 65(3): 1835–1841. doi: 10.1109/TVT.2015.2412152
|
| [11] |
张波, 黄开枝. 异构携能通信网络中基于人工噪声辅助的鲁棒安全传输方案[J]. 电子与信息学报, 2019, 41(1): 1–8. doi: 10.11999/JEIT180269ZHANG Bo and HUANG Kaizhi. Robust secure transmission scheme based on artificial noise-aided for heterogeneous networks with simultaneous wireless information and power transfer[J]. Journal of Electronics &Information Technology, 2019, 41(1): 1–8. doi: 10.11999/JEIT180269
|
| [12] |
JAMEEL F, WYNE S, KADDOUM G, et al. A comprehensive survey on cooperative relaying and jamming strategies for physical layer security[J]. IEEE Communications Surveys & Tutorials, 2019, 21(3): 2734–2771. doi: 10.1109/COMST.2018.2865607
|
| [13] |
HOANG T M, DUONG T Q, VO N S, et al. Physical layer security in cooperative energy harvesting networks with a friendly jammer[J]. IEEE Wireless Communications Letters, 2017, 6(2): 174–177. doi: 10.1109/LWC.2017.2650224
|
| [14] |
谢国芳. 一般实系数四次方程的谢国芳求根公式[EB/OL]. https://wenku.baidu.com/view/2ac910223169a4517723a39a.html, 2013.XIE Guofang. Formula for finding roots of quartic equations with general real coefficients[EB/OL]. https://wenku.baidu.com/view/2ac910223169a4517723a39a.html, 2013.
|
| [15] |
BENNER P and BYERS R. An exact line search method for solving generalized continuous-time algebraic Riccati equations[J]. IEEE Transactions on Automatic Control, 1998, 43(1): 101–107. doi: 10.1109/9.654908
|





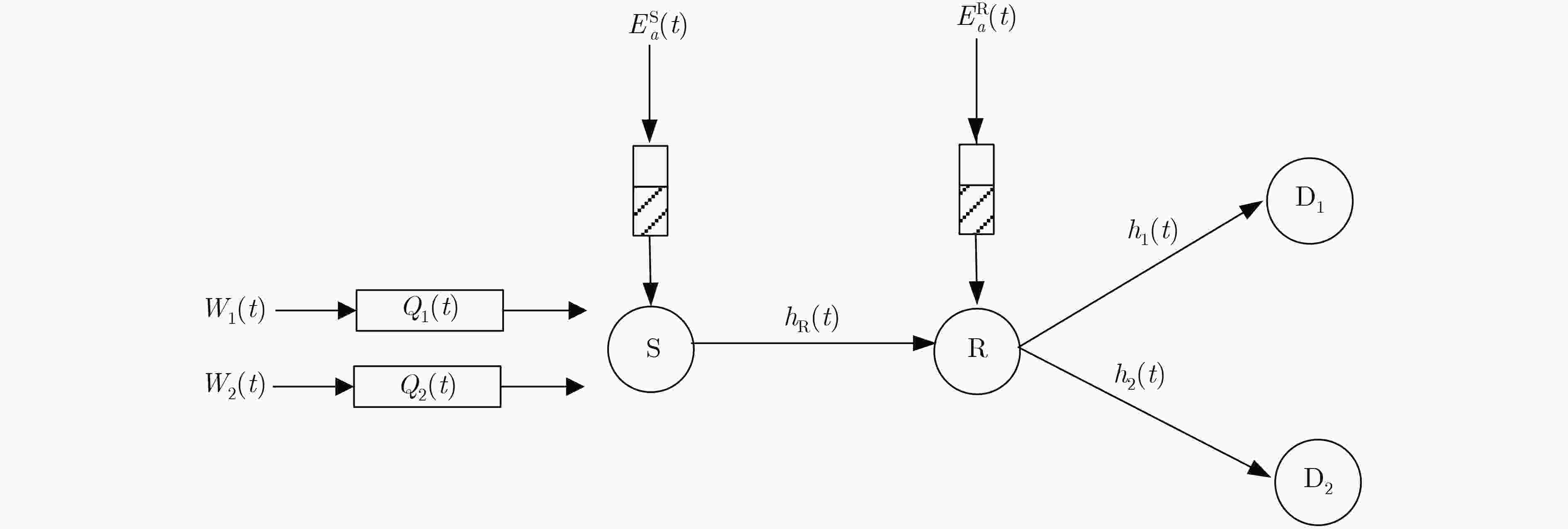
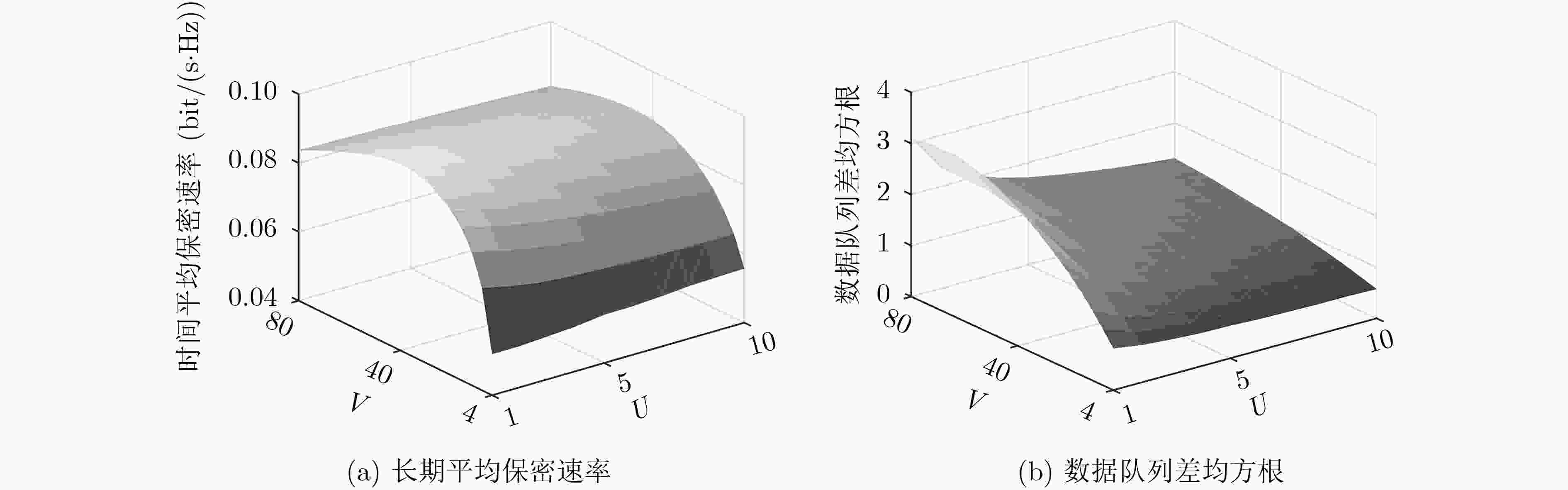
 下载:
下载:
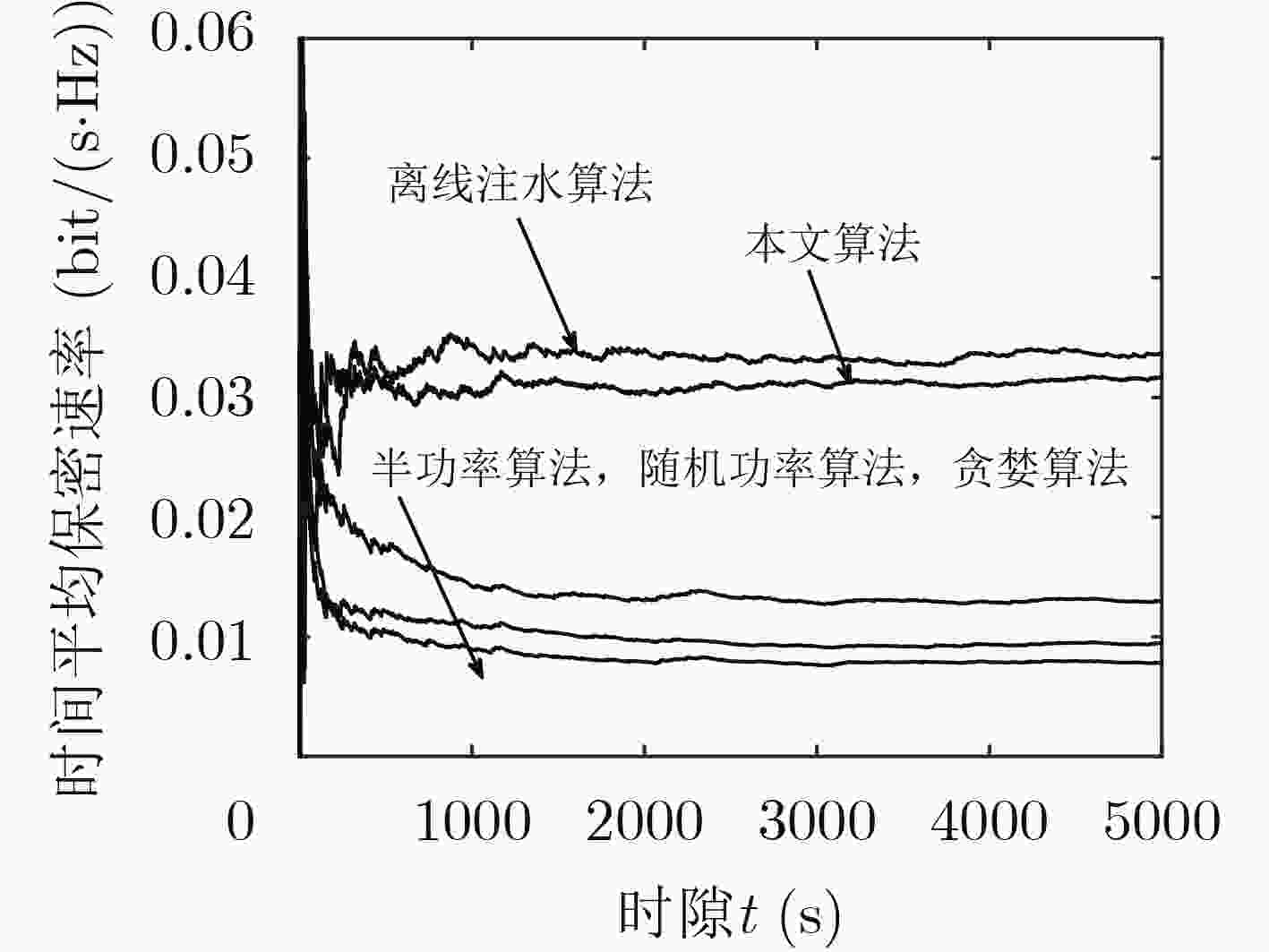
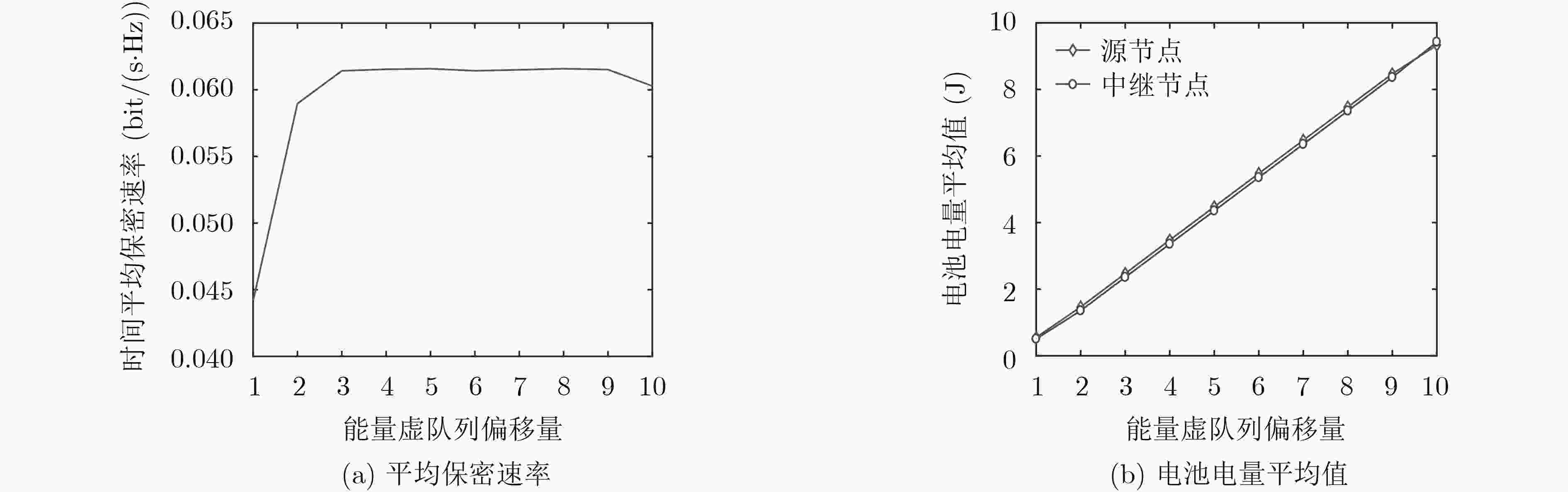
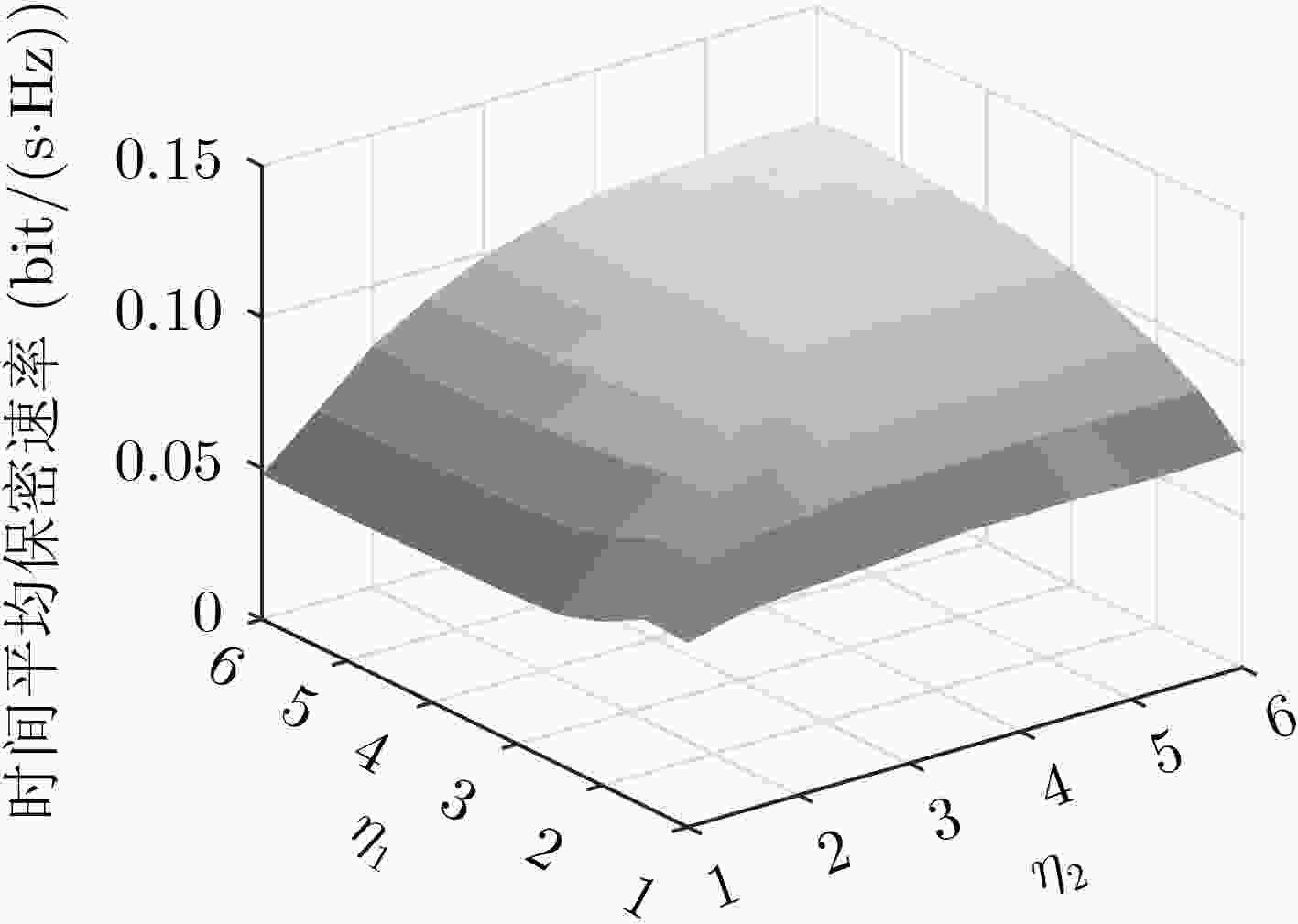
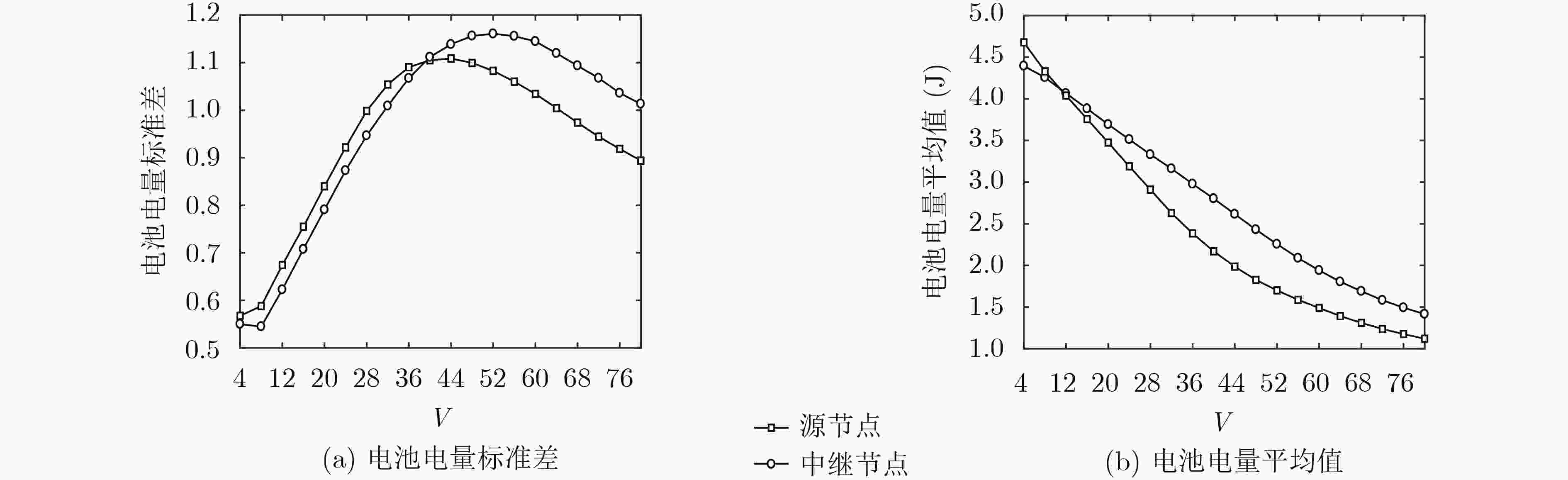


 下载:
下载:
