Performance Analysis of Physical Layer Security for Cognitive Radio Non-Orthogonal Multiple Access Random Network
-
摘要:
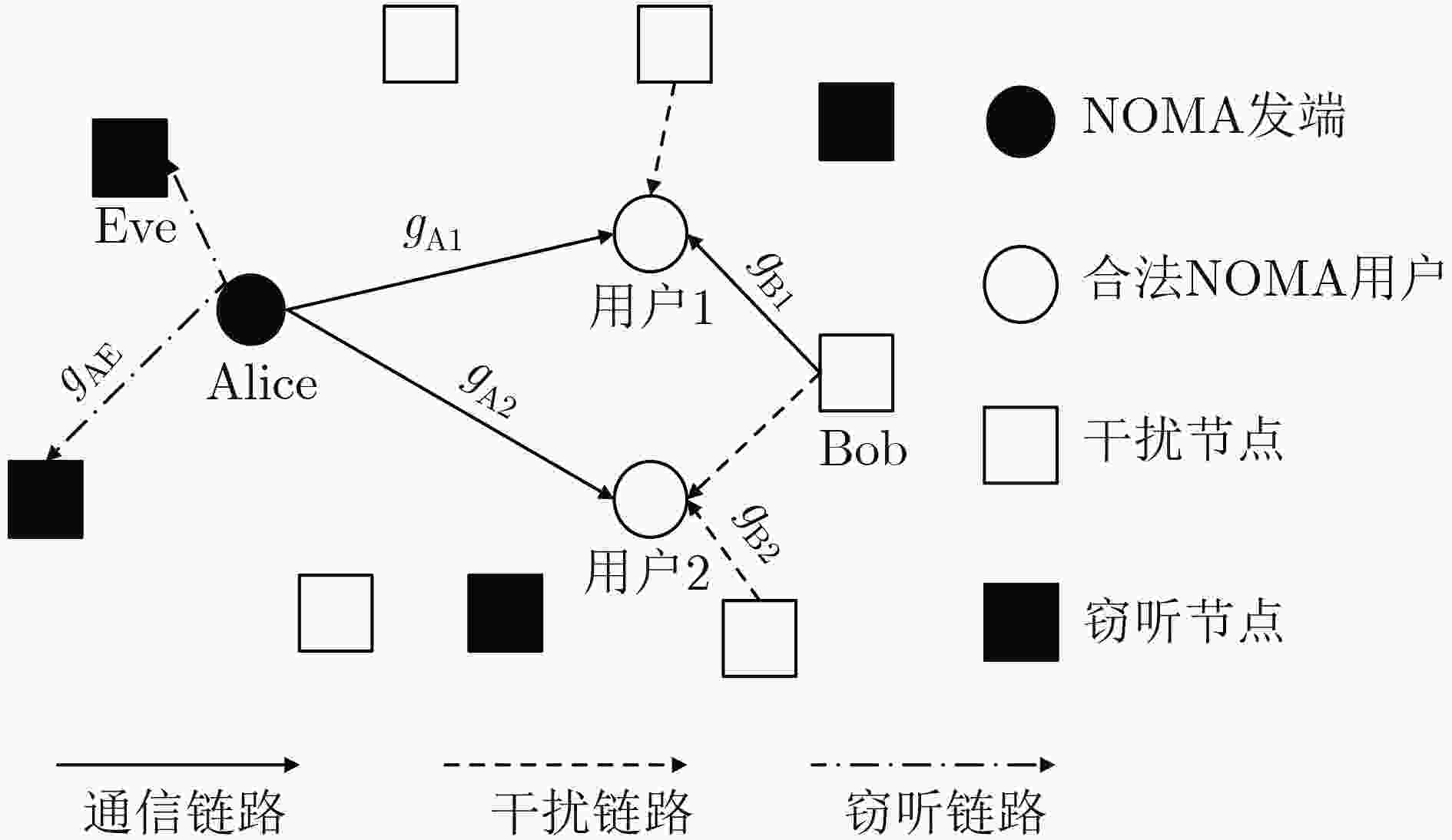
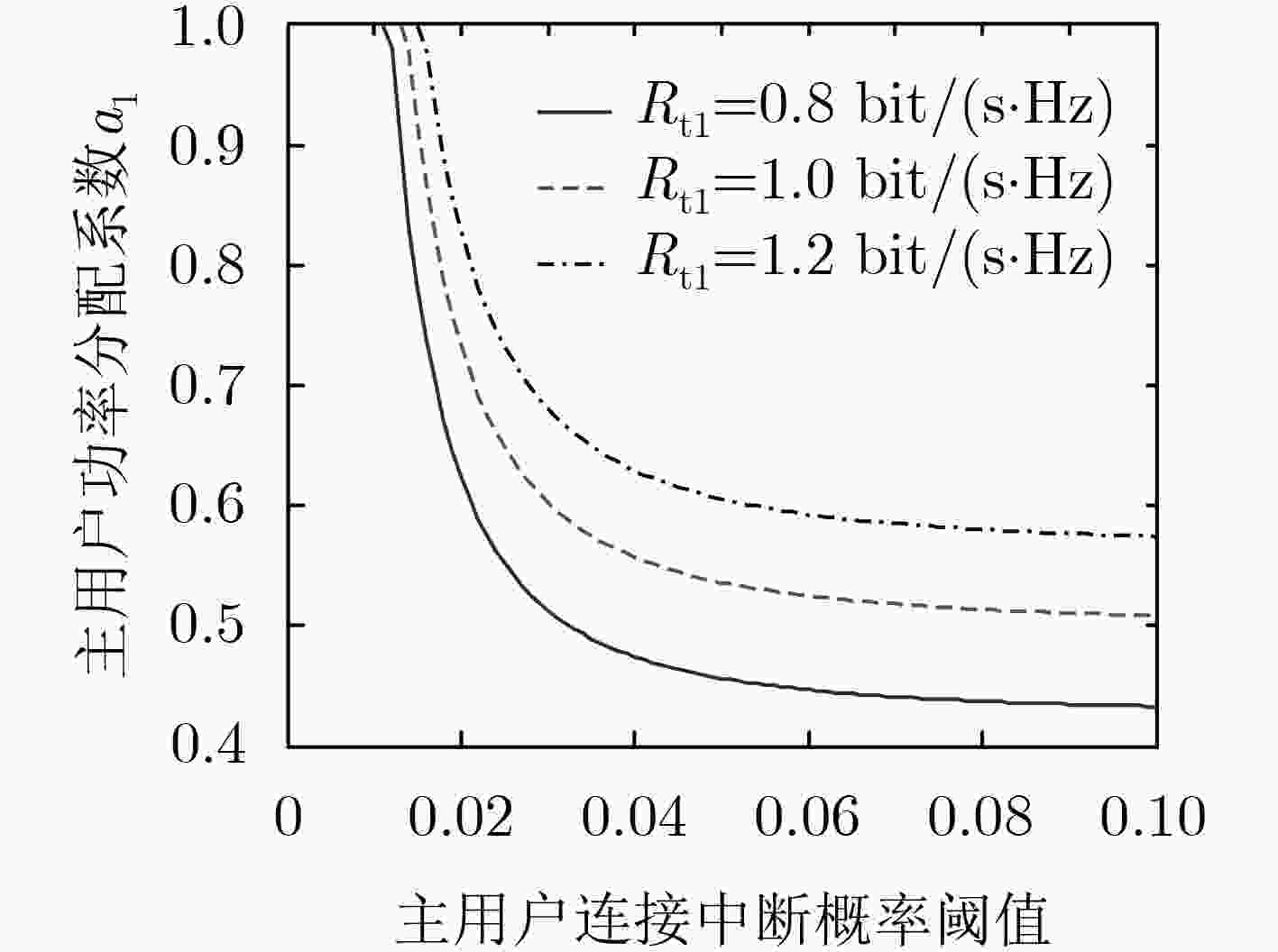
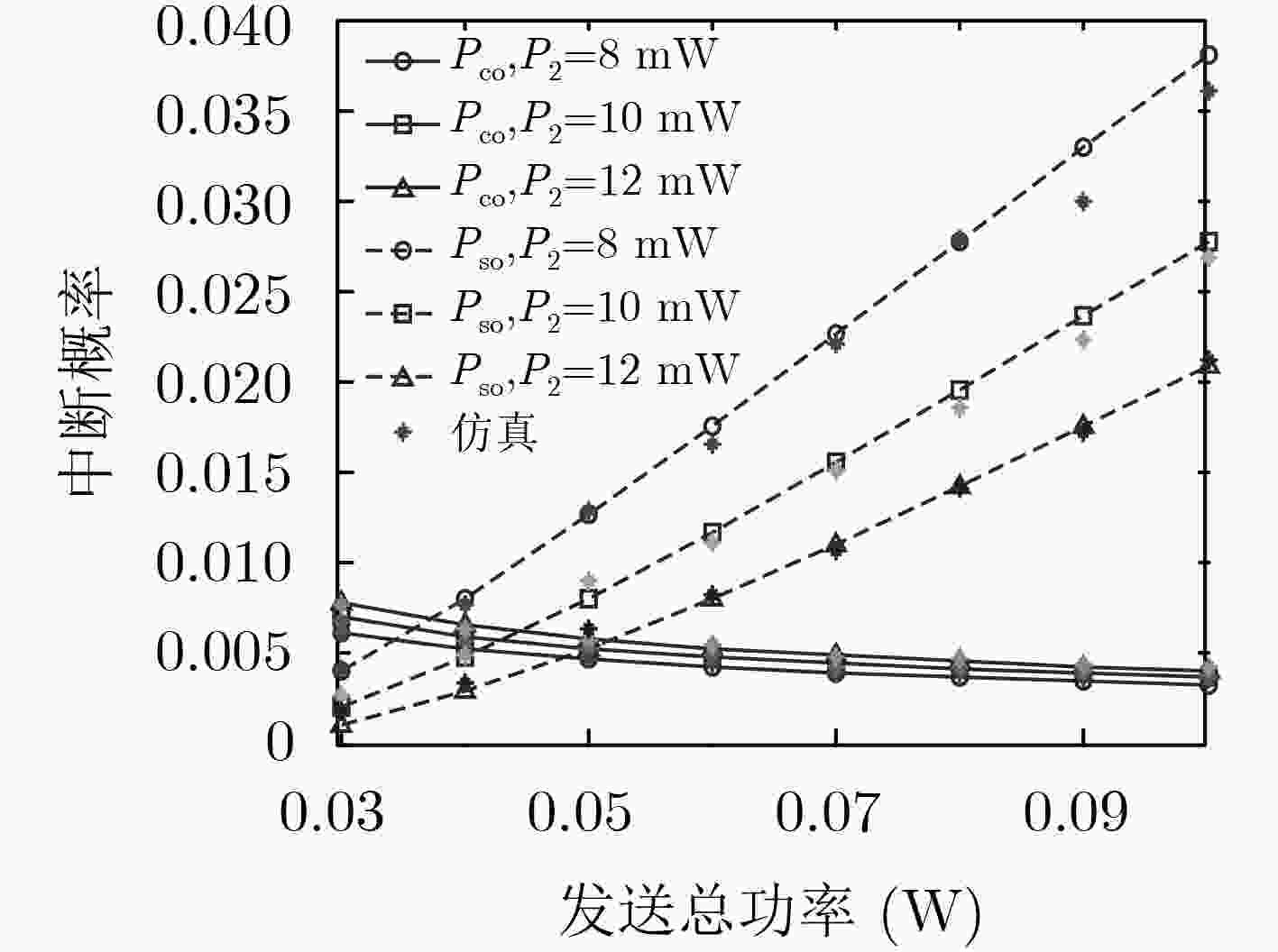
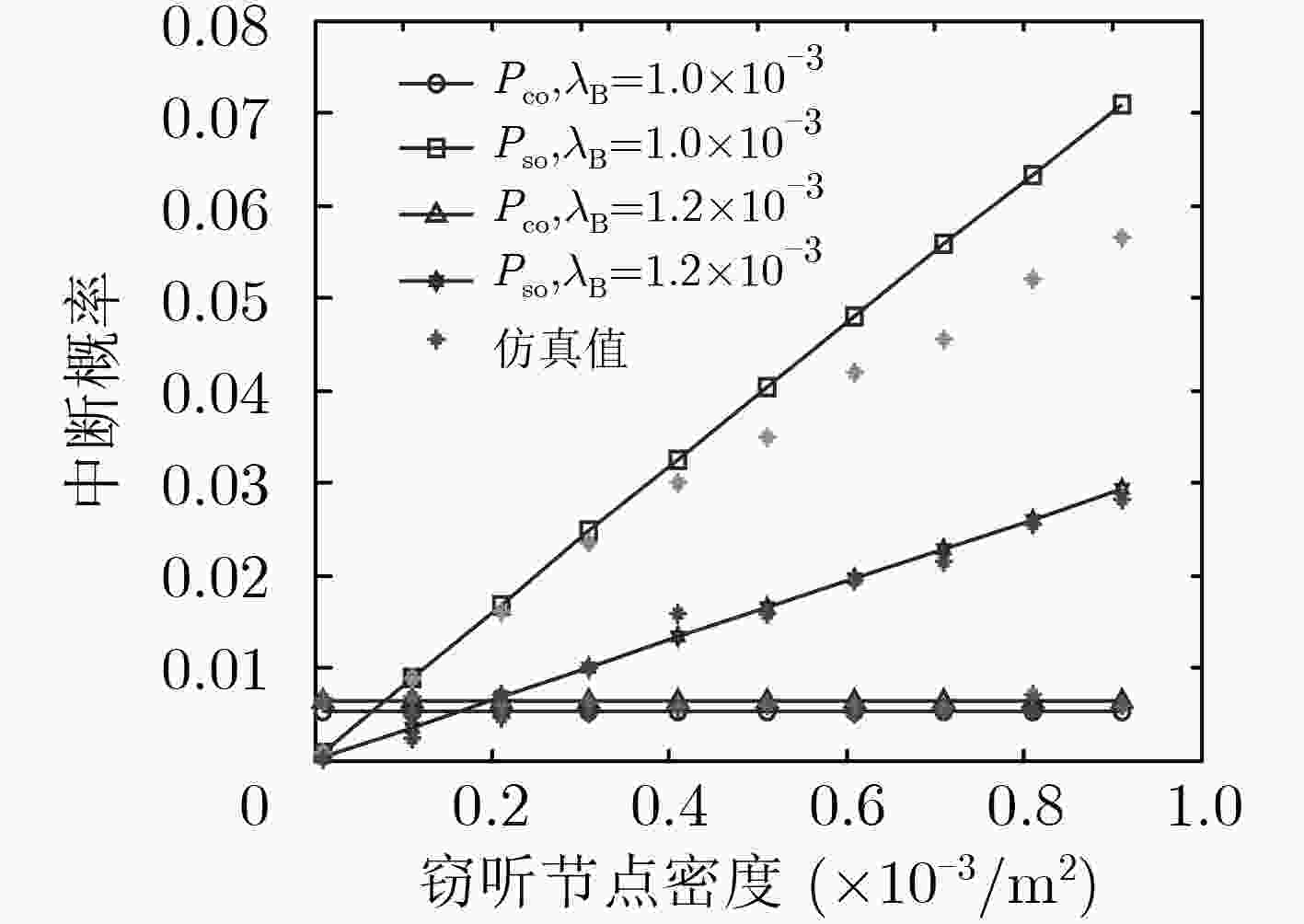
该文针对干扰源以及窃听节点均随机分布的通信场景,分析了认知无线电启发式非正交多址接入(CR-NOMA)网络中次用户通信对的安全通信性能。采用随机几何理论,将窃听节点和干扰节点建模为服从特定分布的齐次泊松点过程(PPP)。首先,在保证主用户通信对通信可靠性的前提下,得到了发端设定的功率分配系数,进一步得到了次用户通信对的连接中断概率和安全中断概率的闭式表达式。随后,得到了功率分配系数随主用户可靠性能约束的变化规律。最后,研究了次用户对的中断概率随着窃听节点密度、发端发送功率的变化情况,结果表明干扰信号的增强在降低网络可靠性能的同时,换来了安全性能的提高。仿真结果验证了理论分析的正确性。
-
关键词:
- 认知无线电 /
- 物理层安全 /
- 启发式非正交多址接入 /
- 随机分布 /
- 功率分配
Abstract:This paper analyzes the security communication performance of secondary user communication pairs in Cognitive Radio Non-Orthogonal Multiple Access (CR-NOMA) networks, where interference sources and eavesdropping nodes are randomly distributed. The stochastic geometry theory is used to model the eavesdropping nodes and the interfering nodes as a homogeneous Poisson Point Processes (PPP). Firstly, to ensure the reliability of the primary user communication pairs, the power allocation coefficient set of the sender is obtained, and the closed expressions of the connection outage probability and the secrecy outage probability of the secondary user are further obtained. Then, the variation of the power distribution coefficient with the constraint of the primary user’s reliability is analyzed. Finally, the relationship between outage probability of secondary user communication pairs and the density of the eavesdropping nodes and the transmission power is studied. The research shows that the enhancement of interfering signal reduces the reliability of the system, but brings about a significant improvement of security performance. The simulation results verify the correctness of the theoretical analysis.
-
YANG Nan, WANG Lifeng, GERACI G, et al. Safeguarding 5G wireless communication networks using physical layer security[J]. IEEE Communications Magazine, 2015, 53(4): 20–27. doi: 10.1109/MCOM.2015.7081071 MARZBAN M F, KASHEF M, ABDALLAH M, et al. Beamforming and power allocation for physical-layer security in hybrid RF/VLC wireless networks[C]. The 13th International Wireless Communications and Mobile Computing Conference, Valencia, Spain, 2017: 258–263. doi: 10.1109/IWCMC.2017.7986296. WANG Huiming, WANG Chao, NG D W K, et al. Artificial noise assisted secure transmission for distributed antenna systems[J]. IEEE Transactions on Signal Processing, 2016, 64(15): 4050–4064. doi: 10.1109/TSP.2016.2558164 DAI Linglong, WANG Bichai, YUAN Yifei, et al. Non-orthogonal multiple access for 5G: Solutions, challenges, opportunities, and future research trends[J]. IEEE Communications Magazine, 2105, 53(9): 74–81. doi: 10.1109/MCOM.2015.7263349 HE Biao, LIU An, YANG Nan, et al. On the design of secure non-orthogonal multiple access systems[J]. IEEE Journal on Selected Areas in Communications, 2017, 35(10): 2196–2206. doi: 10.1109/JSAC.2017.2725698 李钊, 戴晓琴, 陈柯宇, 等. 非正交多址接入下行链路用户匹配与功率优化算法[J]. 电子与信息学报, 2017, 39(8): 1804–1811. doi: 10.11999/JEIT161197LI Zhao, DAI Xiaoqin, CHEN Keyu, et al. User matching and power optimization algorithm for downlink NOMA[J]. Journal of Electronics &Information Technology, 2017, 39(8): 1804–1811. doi: 10.11999/JEIT161197 CHANDWANI N, JAIN A, and VYAVAHARE P D. Throughput comparison for cognitive radio network under various conditions of primary user and channel noise signals[C]. 2015 Radio and Antenna Days of the Indian Ocean, Belle Mare, 2015: 1–2. doi: 10.1109/RADIO.2015.7323379. CICIOĞLU M, CICIOĞLU S, and ÇALHAN A. Performance analysis of software-defined network approach for wireless cognitive radio networks[C]. The 26th Signal Processing and Communications Applications Conference, Izmir, Turkey, 2018: 1–4. doi: 10.1109/SIU.2018.8404691. DING Zhiguo, FAN Pingzhi, and POOR H V. Impact of user pairing on 5G nonorthogonal multiple-access downlink transmissions[J]. IEEE Transactions on Vehicular Technology, 2016, 65(8): 6010–6023. doi: 10.1109/TVT.2015.2480766 LIU Yuanwei, DING Zhiguo, ELKASHLAN M, et al. Nonorthogonal multiple access in large-scale underlay cognitive radio networks[J]. IEEE Transactions on Vehicular Technology, 2016, 65(12): 10152–10157. doi: 10.1109/TVT.2016.2524694 LÜ Lu, CHEN Jian, and NI Qiang. Cooperative non-orthogonal multiple access in cognitive radio[J]. IEEE Communications Letters, 2016, 20(10): 2059–2062. doi: 10.1109/LCOMM.2016.2596763 ARZYKULOV S, TSIFTSIS T A, NAURYZBAYEV G, et al. Outage performance of cooperative underlay CR-NOMA with imperfect CSI[J]. IEEE Communications Letters, 2019, 23(1): 176–179. doi: 10.1109/LCOMM.2018.2878730 CHEN Yingyang, WANG Li, and JIAO Bingli. Cooperative multicast non-orthogonal multiple access in cognitive radio[C]. 2017 IEEE International Conference on Communications, Paris, France, 2017: 1–6. LÜ Lu, CHEN Jian, NI Qiang, et al. Design of cooperative non-orthogonal multicast cognitive multiple access for 5G systems: User scheduling and performance analysis[J]. IEEE Transactions on Communications, 2017, 65(6): 2641–2656. doi: 10.1109/TCOMM.2017.2677942 WANG Huiming, WANG Chao, ZHENG Tongxing, et al. Impact of artificial noise on cellular networks: A stochastic geometry approach[J]. IEEE Transactions on Wireless Communications, 2016, 15(11): 7390–7404. doi: 10.1109/TWC.2016.2601903 HU Xiang, ZHANG Xing, HUANG Haozhou, et al. Secure transmission via jamming in cognitive radio networks with possion spatially distributed eavesdroppers[C]. The 27th IEEE Annual International Symposium on Personal, Indoor, and Mobile Radio Communications, Valencia, Spain, 2016: 1–6. doi: 10.1109/PIMRC.2016.7794918. CHEN Hui, TAO Xiaofeng, LI Na, et al. Secrecy performance analysis of hybrid eavesdroppers system using stochastic geometry and random matrix theory[C]. 2017 IEEE International Conference on Communications, Paris, France, 2017: 1–6. doi: 10.1109/ICC.2017.7996465. DENG Yansha, WANG Lifeng, ELKASHLAN M, et al. Physical layer security in three-tier wireless sensor networks: A stochastic geometry approach[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(6): 1128–1138. doi: 10.1109/TIFS.2016.2516917 CAI Yueming, XU Xiaoming, and YANG Weiwei. Secure transmission in the random cognitive radio networks with secrecy guard zone and artificial noise[J]. IET Communications, 2016, 10(15): 1904–1913. doi: 10.1049/iet-com.2016.0117 黄开枝, 王兵, 许晓明, 等. 基于安全保护域的增强型多点协作传输机制[J]. 电子与信息学报, 2018, 40(1): 108–115. doi: 10.11999/JEIT170478HUANG Kaizhi, WANG Bing, XU Xiaoming, et al. An enhanced coordinated multipoint transmission policy based on secrecy guard zone[J]. Journal of Electronics &Information Technology, 2018, 40(1): 108–115. doi: 10.11999/JEIT170478 -





 下载:
下载:


 下载:
下载:
