Resilient Average Consensus for Second-Order Multi-Agent Systems: Algorithms and Application
-
摘要: 多智能体系统是实现协同协作的重要途径,而弹性一致性则是其安全支撑技术之一。该文针对二阶多智能体系统,研究在存在异常行为节点(包括恶意攻击和意外故障)情况下保证系统协同性能的弹性平均一致性问题。该问题面临双重挑战:如何实现分布式异常检测,以及如何通过一维加速度输入精确补偿二维状态误差。为解决该问题,该文首先推导了二阶平均一致性实现的充分条件。基于此,通过引入两跳通信信息设计了分布式检测机制,并提出能够精确补偿有限控制输入误差的方案。针对输入、速度、位置维度可能遭受的持续攻击,进一步提出具有容错机制的扩展算法。理论证明表明,所提算法能使节点在存在异常节点情况下渐近实现二阶平均一致性。最后,通过大量数值仿真和实验验证了所提方法的有效性。Abstract:
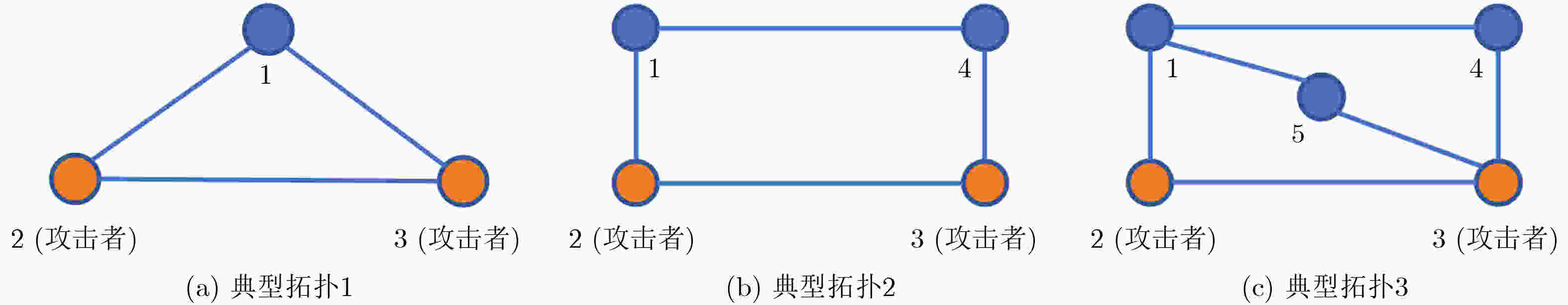
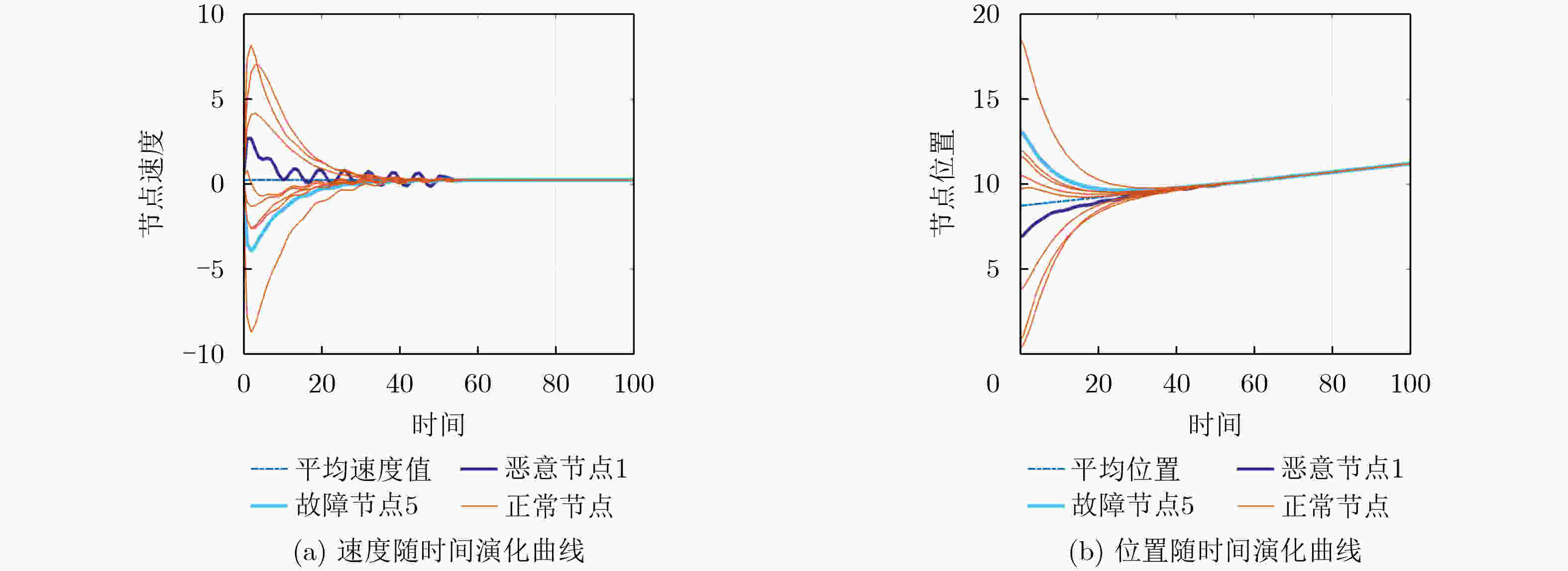
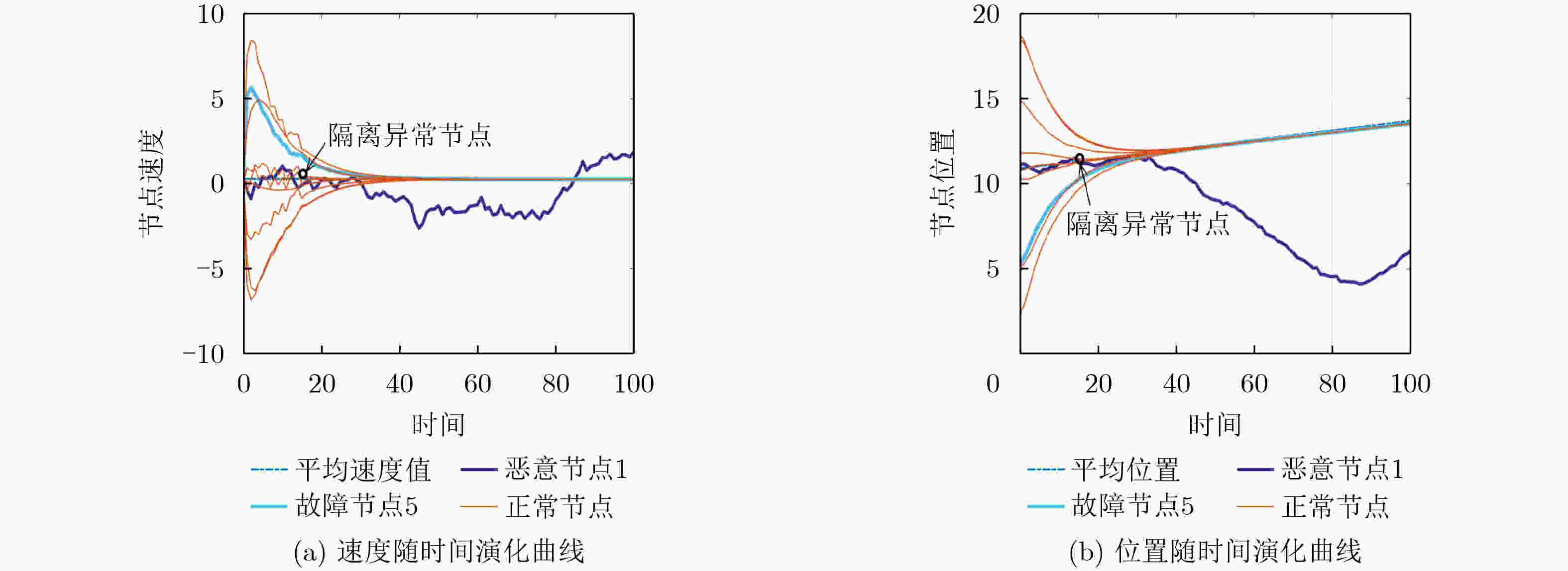
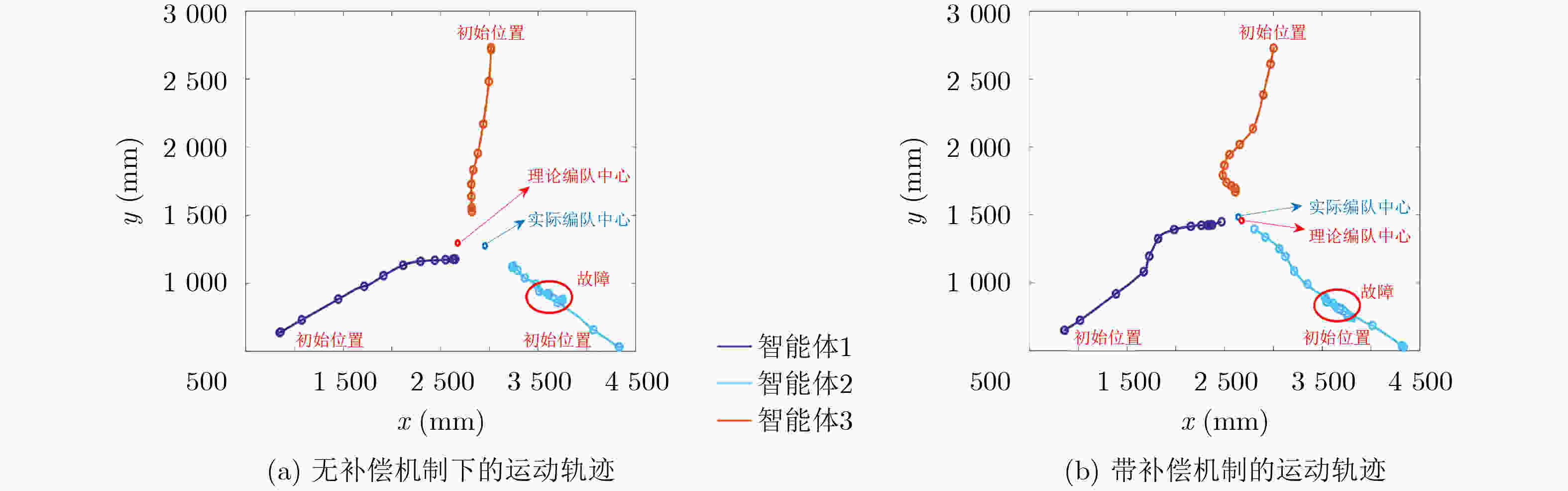
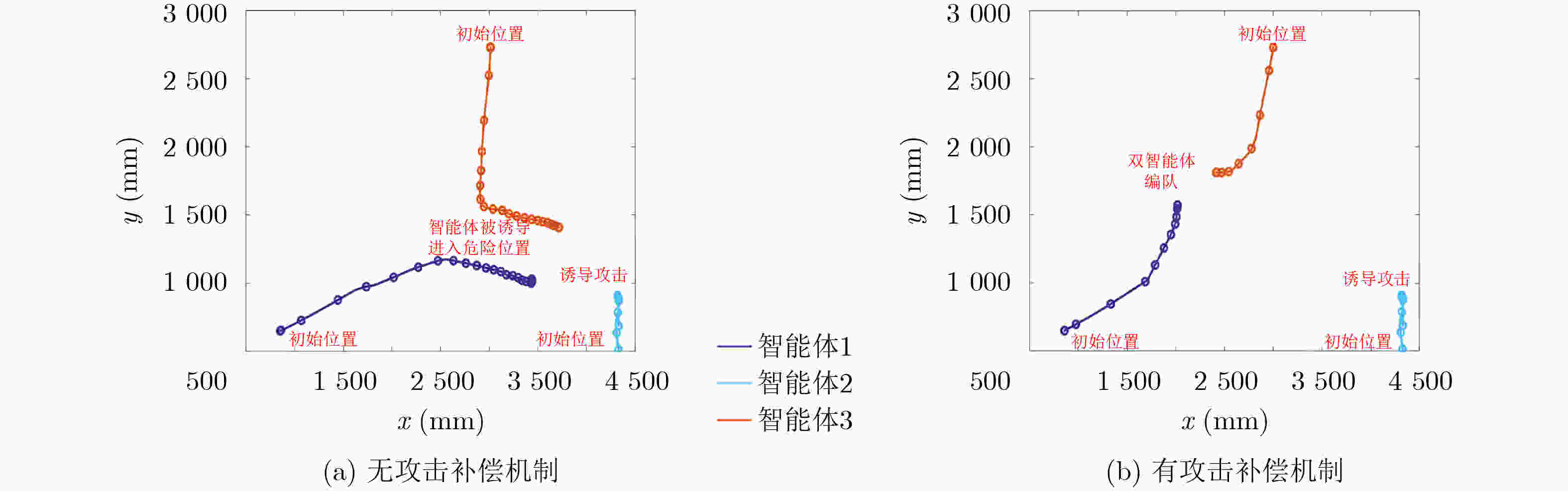
Objective Multi-agent systems (MASs) are pivotal for collaborative tasks in dynamic environments, with consensus algorithms serving as a cornerstone for applications like formation control. However, MASs are vulnerable to misbehaviors (e.g., malicious attacks or accidental faults), which can disrupt consensus and compromise system performance. While resilient consensus methods exist for first-order systems, they are inadequate for second-order MASs, where agents’ dynamics involve both position and velocity. This work addresses the gap by developing a resilient average consensus framework for second-order MASs that ensures accurate collaboration under misbehaviors. The primary challenges include distributed error detection and compensating two-dimensional state errors (position and velocity) using one-dimensional acceleration inputs. Methods The study first derives sufficient conditions for second-order average consensus under misbehaviors, leveraging graph theory and Lyapunov stability analysis. The system is modeled as an undirected graph $ \mathcal{G}=(\mathcal{V},\mathcal{E}) $, where agents follow double-integrator dynamics. Two algorithms are proposed: Finite Input-Errors Detection-Compensation (FIDC): For finite control input errors, detection strategies (1 and 2) use two-hop communication information to identify discrepancies in neighbors’ states or control inputs. Compensation Scheme I designs input sequences to satisfy consensus conditions (Corollary 1). Infinite Attack Detection-Compensation (IADC): For infinite errors in control input, velocity, and position, detection strategies are extended to identify falsified data. Compensation Schemes 2 and 3 mitigate errors, while an exponentially decaying error bound isolates persistent attackers. The algorithms are distributed and require no global knowledge. Results and Discussions Simulations on a 10-agent network validate the algorithms’ efficacy. Under FIDC, agents achieve exact average consensus despite finite input errors from malicious and faulty agents ( Fig. 5 ). IADC ensures consensus among normal agents after isolating malicious ones exceeding the error bound (Fig. 6 ). Experimental evaluations on a multi-robot platform demonstrate resilience against real-world faults (e.g., actuator failures) and attacks (e.g., false data injection). In fault scenarios, FIDC reduces formation center deviation from 180mm to 34mm (Fig. 8 ). For attacks, IADC isolates malicious robots, allowing normal agents to converge correctly (Fig. 9 ). Discussions on relaxing Assumption 1 (non-adjacent misbehaving agents) reveal that Detection Strategy 3 and majority voting can handle certain connected malicious topologies (Fig. 3 –Fig. 4 ), though complex cases require further study.Conclusions This work proposes a novel resilient average consensus framework for second-order MASs. Theoretically, sufficient conditions ensure consensus under misbehaviors, while FIDC and IADC algorithms enable distributed detection, compensation, and isolation of errors. Simulations and physical experiments confirm that the methods achieve accurate average consensus against both finite and infinite errors. Future work will explore extensions to directed networks, time-varying topologies, and higher-dimensional systems. -
Key words:
- Second-order multi-agent system /
- resilient consensus /
- attack detection /
- compensation
-
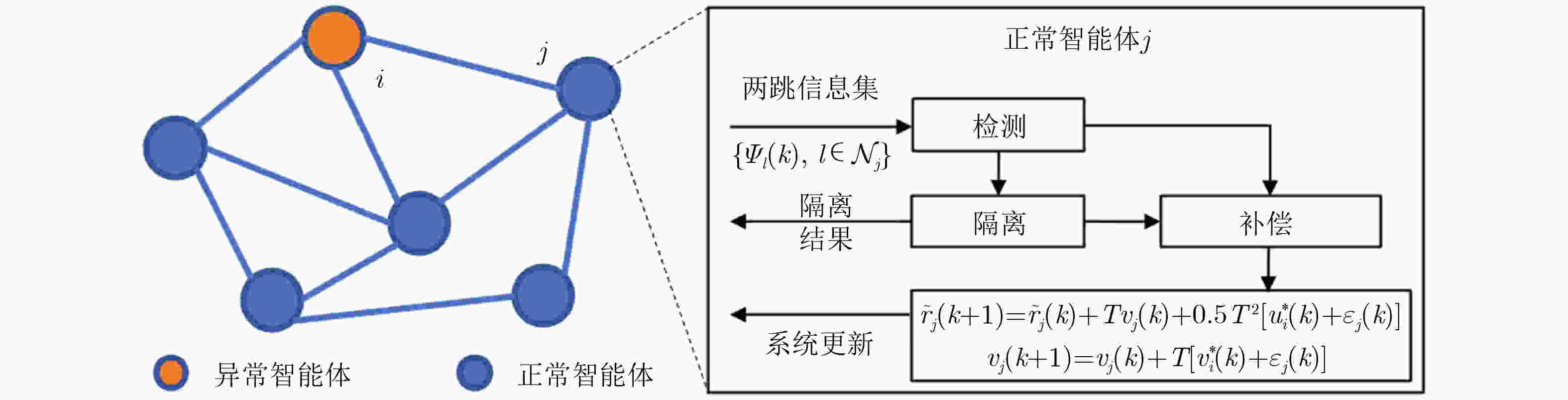
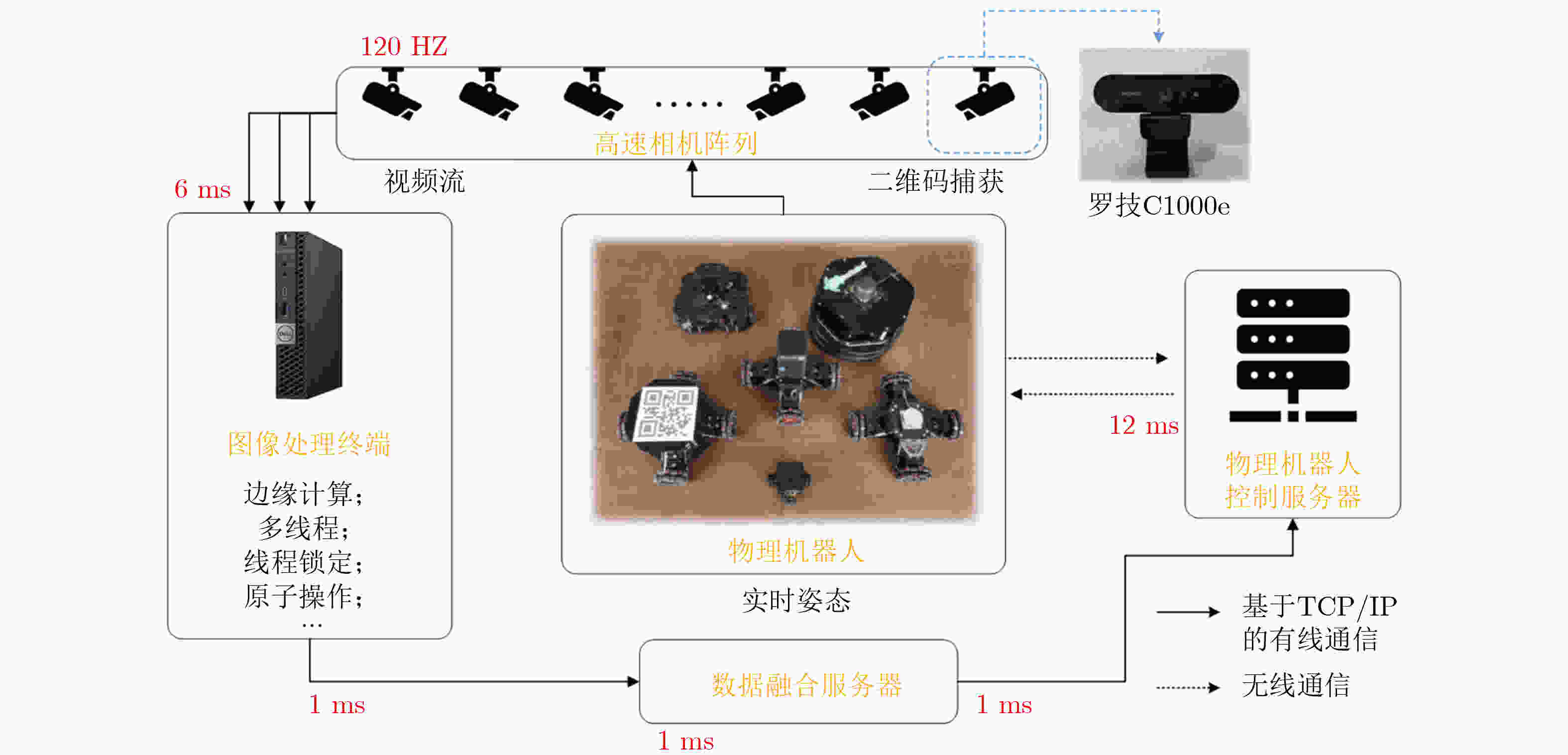
图 5 多机器人平台架构[23]
1 FIDC
1:初始化:设置补偿周期$ {T}_{c} $,并交换各节点的邻居数量$ |{\mathcal{N}}_{j}| $信息 2:$ \rm{f}\rm{o}\rm{r} $$ k=0\colon {\mathrm{Max}}\_ {\mathrm{time}} $ $ \rm{d}\rm{o} $ 3: $ \rm{f}\rm{o}\rm{r} $ $ i\in {\mathcal{N}}_{j} $ $ \rm{d}\rm{o} $ 4: 节点$ j $基于公式计算节点$ i $引起的误差 5: $ \rm{i}\rm{f} $ $ \varepsilon _{i}^{j}(k)\neq 0 $ 6: 通过公式计算补偿序列$ {\varepsilon }_{j}(k+l|k),l=1,2,\cdots ,{T}_{c} $ 7: $ \rm{e}\rm{n}\rm{d} $ $ \rm{i}\rm{f} $ 8: $ \rm{e}\rm{n}\rm{d} $$ \boldsymbol{f}\boldsymbol{o}\boldsymbol{r} $ 9: 通过公式和公式(6)分别计算$ {\varepsilon }_{j}(k+1) $和控制输入并施加 10: 更新$ {v}_{j}(k+2) $和$ {\tilde{r}}_{j}(k+2) $状态值 11:$ \rm{e}\rm{n}\rm{d} $ $ \rm{f}\rm{o}\rm{r} $ 2 IADC
1:初始化:设置补偿周期$ {T}_{c} $,并交换各节点的邻居数量$ |{\mathcal{N}}_{j}| $信息 2:$ \rm{f}\rm{o}\rm{r} $$ k=0\colon {\mathrm{Max}}\_ {\mathrm{time}} $ $ \rm{d}\rm{o} $ 3: $ \rm{f}\rm{o}\rm{r} $ $ i\in {\mathcal{N}}_{j} $ $ \rm{d}\rm{o} $ 4: 通过公式计算$ i $在控制输入、速度和位置上的误差。 5: $ \rm{i}\rm{f} $ $ {\omega }_{i}(k)\neq 0 $或$ {\delta }_{i}(k)\neq 0 $或$ \varepsilon _{i}^{j}(k)\neq 0 $ 6: 根据公式和获取补偿序列。 7: $ \rm{e}\rm{n}\rm{d} $ $ \rm{i}\rm{f} $ 8: $ \rm{i}\rm{f} $ $ \varepsilon _{i}^{j}(k)\geq {\alpha }_{j}\rho _{j}^{k} $或$ {\omega }_{i}(k)\geq {\alpha }_{j}\rho _{j}^{k} $或$ {\delta }_{i}(k)\geq {\alpha }_{j}\rho _{j}^{k} $ 9: 节点$ j $隔离节点$ i $,通过公式计算补偿序列。 10: $ \rm{e}\rm{n}\rm{d} $ $ \rm{i}\rm{f} $ 11: $ \rm{e}\rm{n}\rm{d} $$ \rm{f}\rm{o}\rm{r} $ 12: 通过公式计算$ {\varepsilon }_{j}(k+1) $,基于公式计算控制输入并施加 13: 更新$ {v}_{j}(k+2) $和$ {\tilde{r}}_{j}(k+2) $状态值 14:$ \rm{e}\rm{n}\rm{d} $ $ \rm{f}\rm{o}\rm{r} $ -
[1] OLFATI-SABER R, FAX J A, and MURRAY R M. Consensus and cooperation in networked multi-agent systems[J]. Proceedings of the IEEE, 2007, 95(1): 215–233. doi: 10.1109/JPROC.2006.887293. [2] WANG Xin, HE Jianping, CHENG Peng, et al. Differentially private maximum consensus: Design, analysis and impossibility result[J]. IEEE Transactions on Network Science and Engineering, 2019, 6(4): 928–939. doi: 10.1109/TNSE.2018.2879795. [3] LIU Mengxiang, ZHAO Chengcheng, DENG Ruilong, et al. False data injection attacks and the distributed countermeasure in DC microgrids[J]. IEEE Transactions on Control of Network Systems, 2022, 9(4): 1962–1974. doi: 10.1109/TCNS.2022.3181483. [4] WU Yanfang, GUO Peng, WANG Ying, et al. Attack-defense game modeling framework from a vulnerability perspective to protect critical infrastructure systems[J]. Reliability Engineering & System Safety, 2025, 256: 110740. doi: 10.1016/j.ress.2024.110740. [5] KIECKHAFER R M and AZADMANESH M H. Low cost approximate agreement in partially connected networks[J]. Journal of Computing and Information, 1993, 3(2). (查阅网上资料, 未找到页码信息, 请补充). [6] KIECKHAFER R M and AZADMANESH M H. Reaching approximate agreement with mixed-mode faults[J]. IEEE Transactions on Parallel and Distributed Systems, 1994, 5(1): 53–63. doi: 10.1109/71.262588. [7] LEBLANC H J, ZHANG Haotian, KOUTSOUKOS X, et al. Resilient asymptotic consensus in robust networks[J]. IEEE Journal on Selected Areas in Communications, 2013, 31(4): 766–781. doi: 10.1109/JSAC.2013.130413. [8] DIBAJI S M and ISHII H. Consensus of second-order multi-agent systems in the presence of locally bounded faults[J]. Systems & Control Letters, 2015, 79: 23–29. doi: 10.1016/j.sysconle.2015.02.005. [9] SUNDARAM S and HADJICOSTIS C N. Distributed function calculation via linear iterative strategies in the presence of malicious agents[J]. IEEE Transactions on Automatic Control, 2011, 56(7): 1495–1508. doi: 10.1109/TAC.2010.2088690. [10] WU Hanyu, LIU Qingshan, and PARK J H. Observer-based secure consensus for multiagent systems under multimode DoS attacks with application to power system[J]. IEEE Transactions on Cybernetics, 2025, 55(3): 1032–1044. doi: 10.1109/TCYB.2025.3528200. [11] PASQUALETTI F, BICCHI A, and BULLO F. Consensus computation in unreliable networks: A system theoretic approach[J]. IEEE Transactions on Automatic Control, 2012, 57(1): 90–104. doi: 10.1109/TAC.2011.2158130. [12] SHAMES I, TEIXEIRA A M H, SANDBERG H, et al. Distributed fault detection for interconnected second-order systems[J]. Automatica, 2011, 47(12): 2757–2764. doi: 10.1016/j.automatica.2011.09.011. [13] GUO Meng, DIMAROGONAS D V, and JOHANSSON K H. Distributed real-time fault detection and isolation for cooperative multi-agent systems[C]. 2012 American Control Conference, Montreal, Canada, 2012: 5270–5275. doi: 10.1109/ACC.2012.6315178. [14] FANG Chongrong, ZHENG Wenzhe, HE Zhiyu, et al. Towards resilient average consensus in multi-agent systems: A detection and compensation approach[J]. Frontiers of Information Technology & Electronic Engineering, 2024, 25(2): 182–196. doi: 10.1631/FITEE.2300467. [15] YUAN Liwei and ISHII H. Resilient average consensus with adversaries via distributed detection and recovery[J]. IEEE Transactions on Automatic Control, 2025, 70(1): 415–430. doi: 10.1109/TAC.2024.3426387. [16] LIU Zeqiang, LIU Zhiwei, HE Dingxin, et al. Dynamic resilient consensus of second-order multiagent networks with a time-varying malicious agent set[J]. IEEE Transactions on Automatic Control, 2025, 70(5): 3308–3315. doi: 10.1109/TAC.2024.3507672. [17] XIAO Lin, BOYD S, and KIM S J. Distributed average consensus with least-mean-square deviation[J]. Journal of Parallel and Distributed Computing, 2007, 67(1): 33–46. doi: 10.1016/j.jpdc.2006.08.010. [18] ZHENG Wenzhe, FANG Chongrong, HE Jianping, et al. Resilient average consensus of second-order multi-agent systems[C]. 2022 American Control Conference, Atlanta, USA, 2022: 1466–1471. doi: 10.23919/ACC53348.2022.9867735. [19] CAO Yongcan and REN Wei. Sampled-data discrete-time coordination algorithms for double-integrator dynamics under dynamic directed interaction[J]. International Journal of Control, 2010, 83(3): 506–515. doi: 10.1080/00207170903214338. [20] HE Jianping, CHENG Peng, SHI Ling, et al. SATS: Secure average-consensus-based time synchronization in wireless sensor networks[J]. IEEE Transactions on Signal Processing, 2013, 61(24): 6387–6400. doi: 10.1109/TSP.2013.2286102. [21] ZHAO Chengcheng, HE Jianping, and CHEN Jiming. Resilient consensus with mobile detectors against malicious attacks[J]. IEEE Transactions on Signal and Information Processing over Networks, 2018, 4(1): 60–69. doi: 10.1109/TSIPN.2017.2742859. [22] E-ISAC. Analysis of the Cyber Attack on the Ukrainian Power Grid[M]. Washington, USA: E-ISAC, 2016: 3. (查阅网上资料, 未能确认作者信息, 请确认). [23] DING Xuda, WANG Han, LI Hongbo, et al. Robopheus: A virtual-physical interactive mobile robotic testbed[J]. arXiv: 2103.04391, 2021. doi: 10.48550/arXiv.2103.04391.(查阅网上资料,未能确认文献类型,请确认). [24] LI Yushan, HE Jianping, CHEN Cailian, et al. Intelligent physical attack against mobile robots with obstacle-avoidance[J]. IEEE Transactions on Robotics, 2023, 39(1): 253–272. doi: 10.1109/TRO.2022.3201394. -





 下载:
下载:


 下载:
下载:
