Privacy-Preserving Computation in Trustworthy Face Recognition: A Comprehensive Survey
-
摘要: 论文聚焦人脸识别生态,系统梳理了面向人脸识别可信应用的隐私保护计算研究进展。首先,概述了人脸识别系统的基本架构与流程,剖析非授权采集、信息泄露、梯度泄露、成员推理、人脸重建及非授权识别等关键隐私风险。随后,围绕数据变换、分布式、图像合成和对抗扰动四类主流隐私保护范式,解析加密计算、联邦学习、频域学习、特征模板保护、合成图像训练、身份保持匿名化、虚拟身份识别、差分隐私、重建攻击防御与对抗性隐私保护等十类代表性技术。最后,展望未来研究方向,包括隐私保护计算的效率提升、生成式大模型带来的新机遇与挑战、新型识别范式的构建以及标准化评估体系的建立。论文旨在为可信人脸识别研究提供系统性参考,推动其在信息物理系统中的安全与可信应用,进一步强化个人信息保护。Abstract:
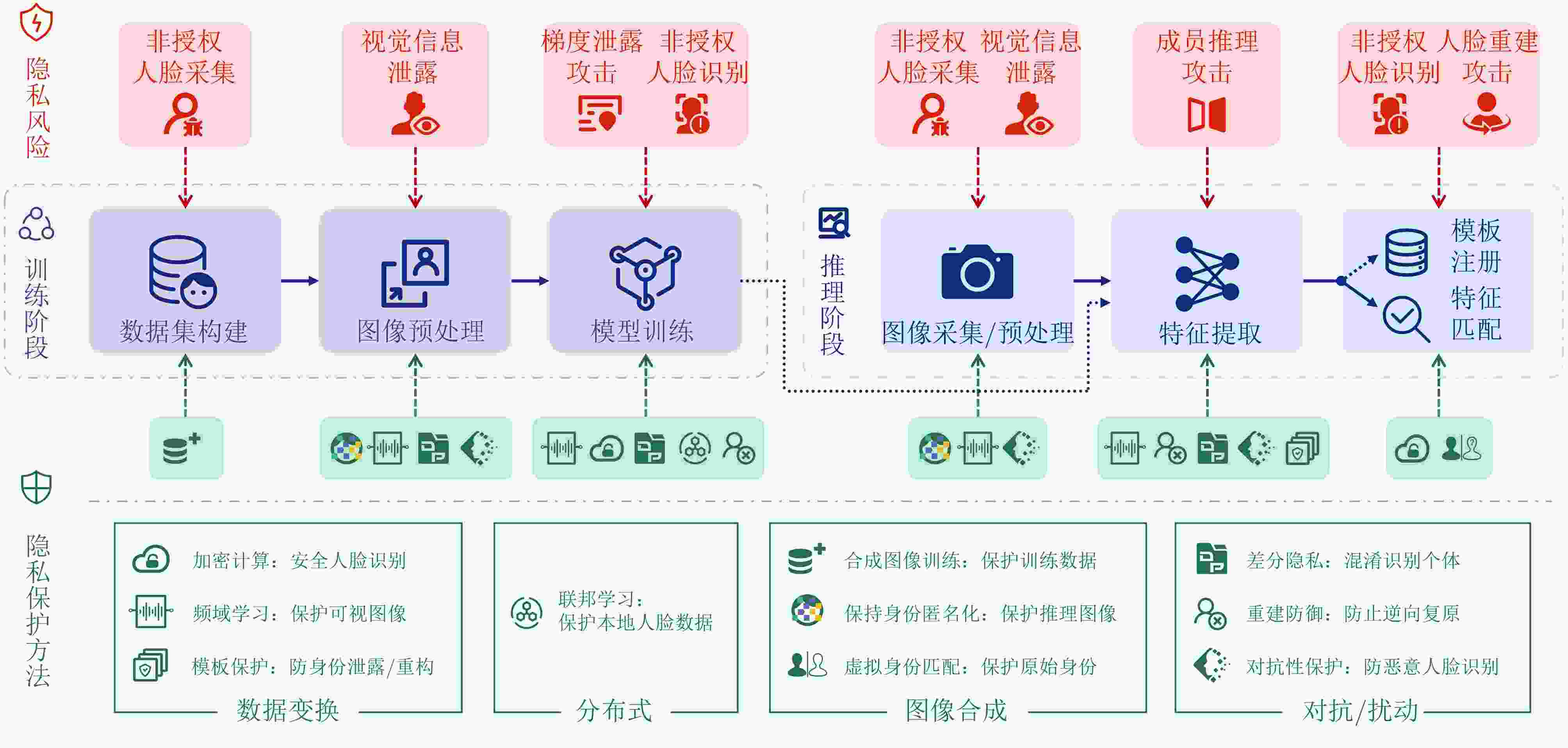
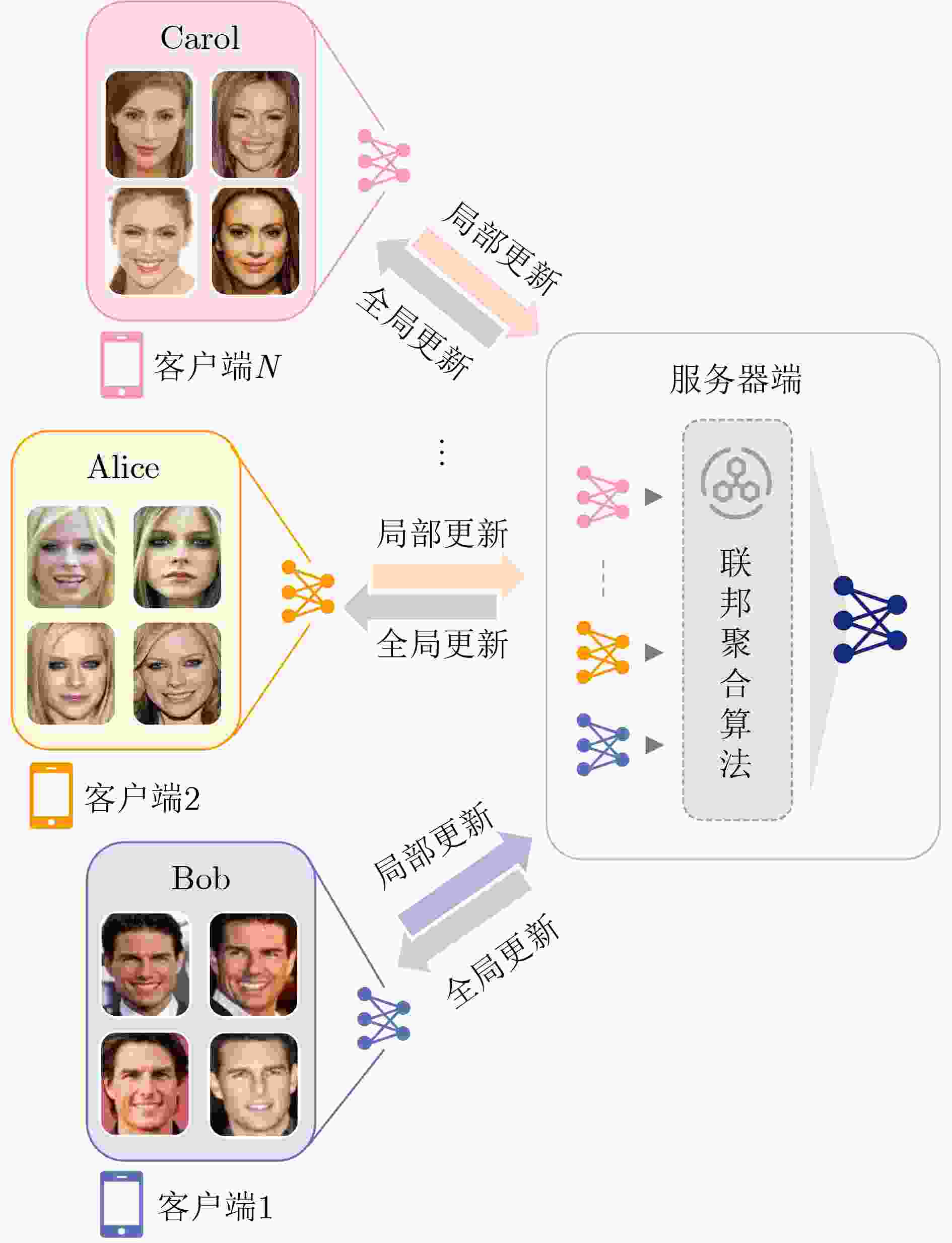
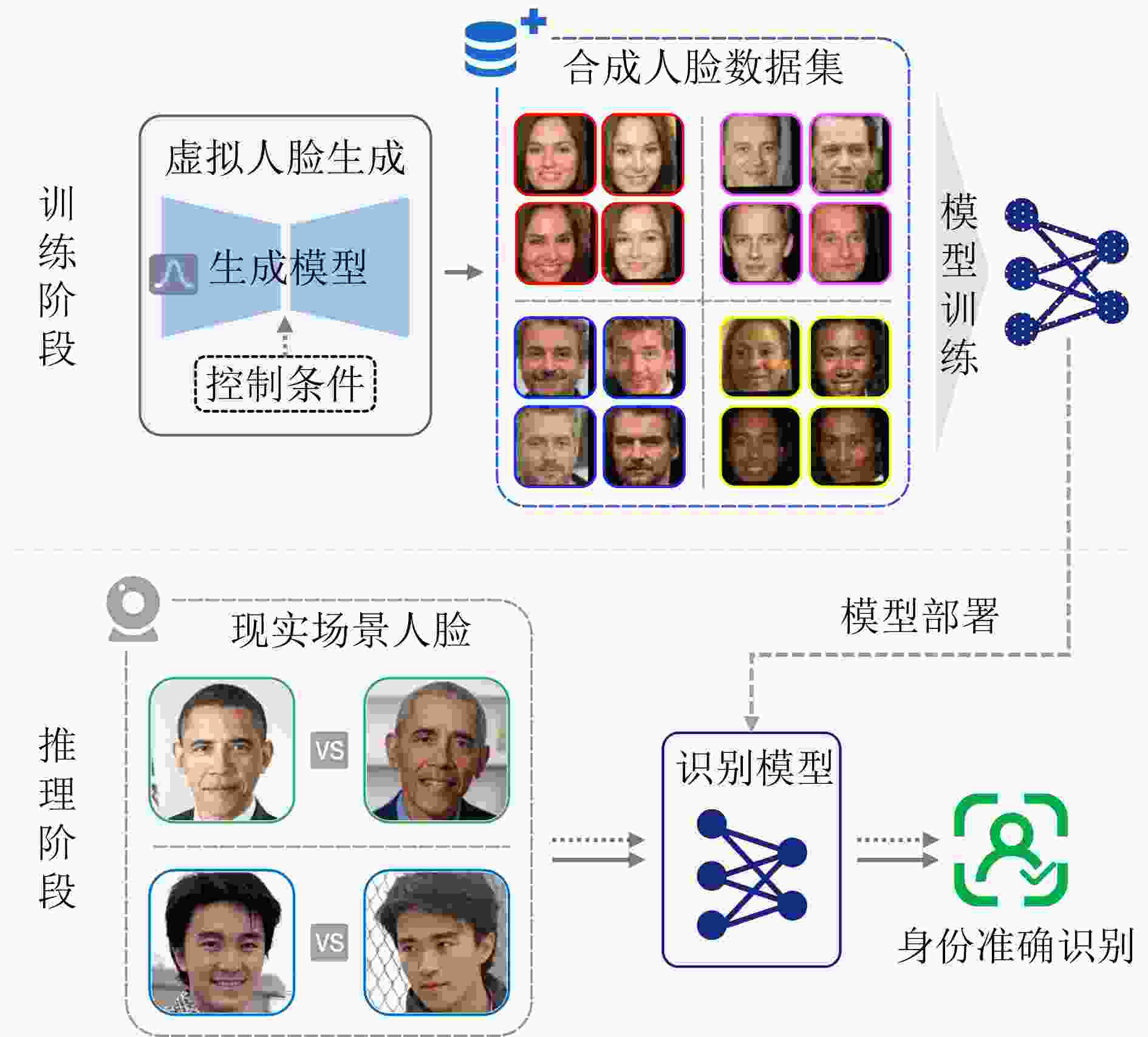
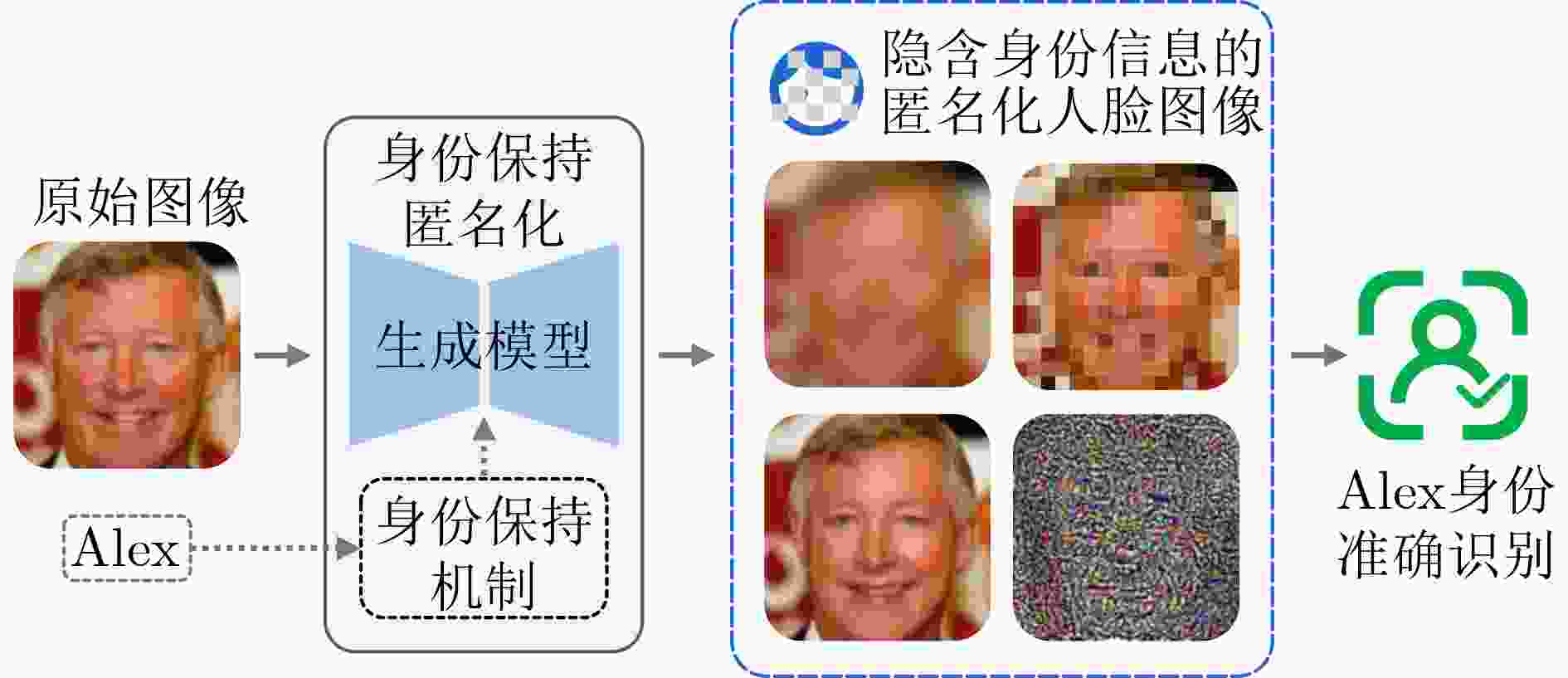
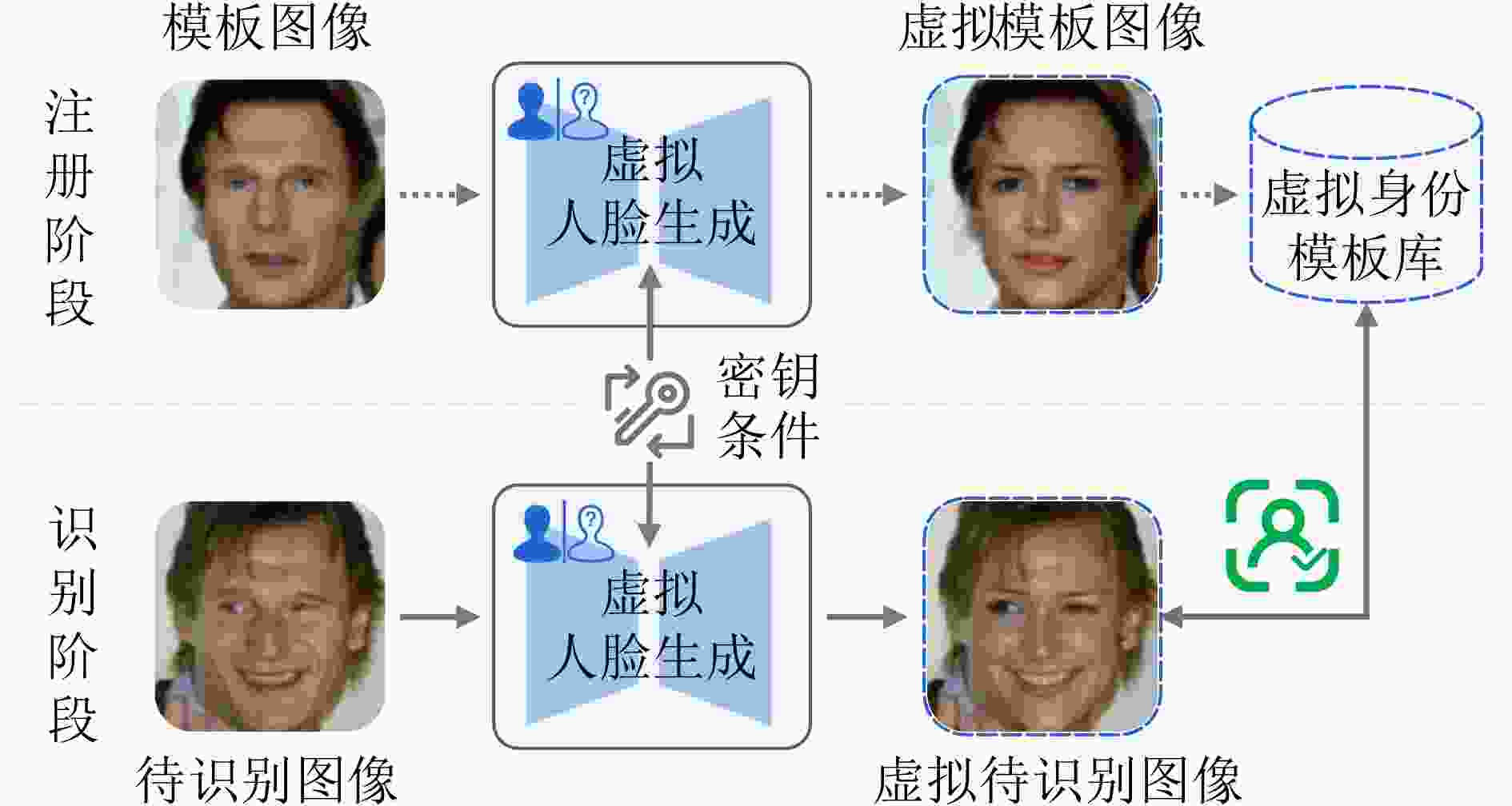
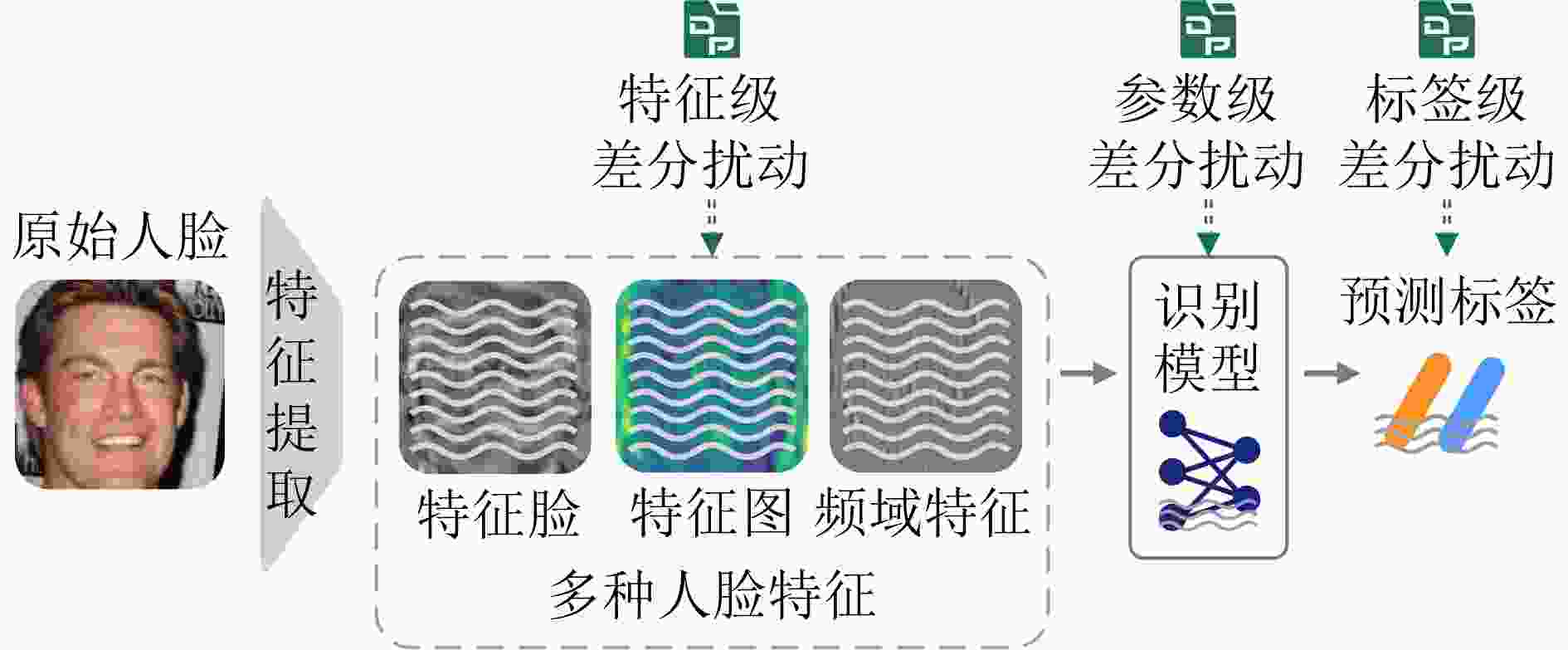
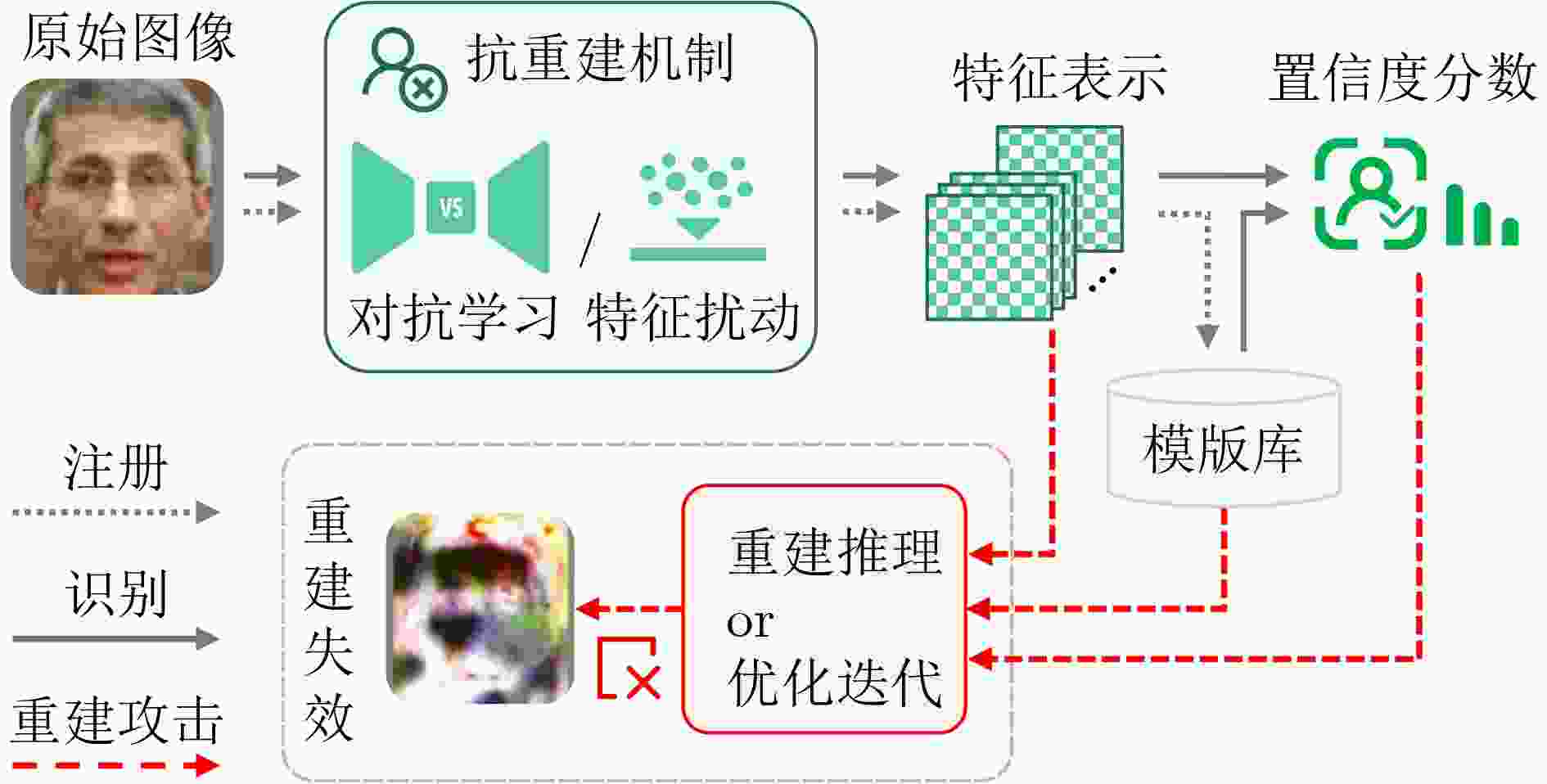
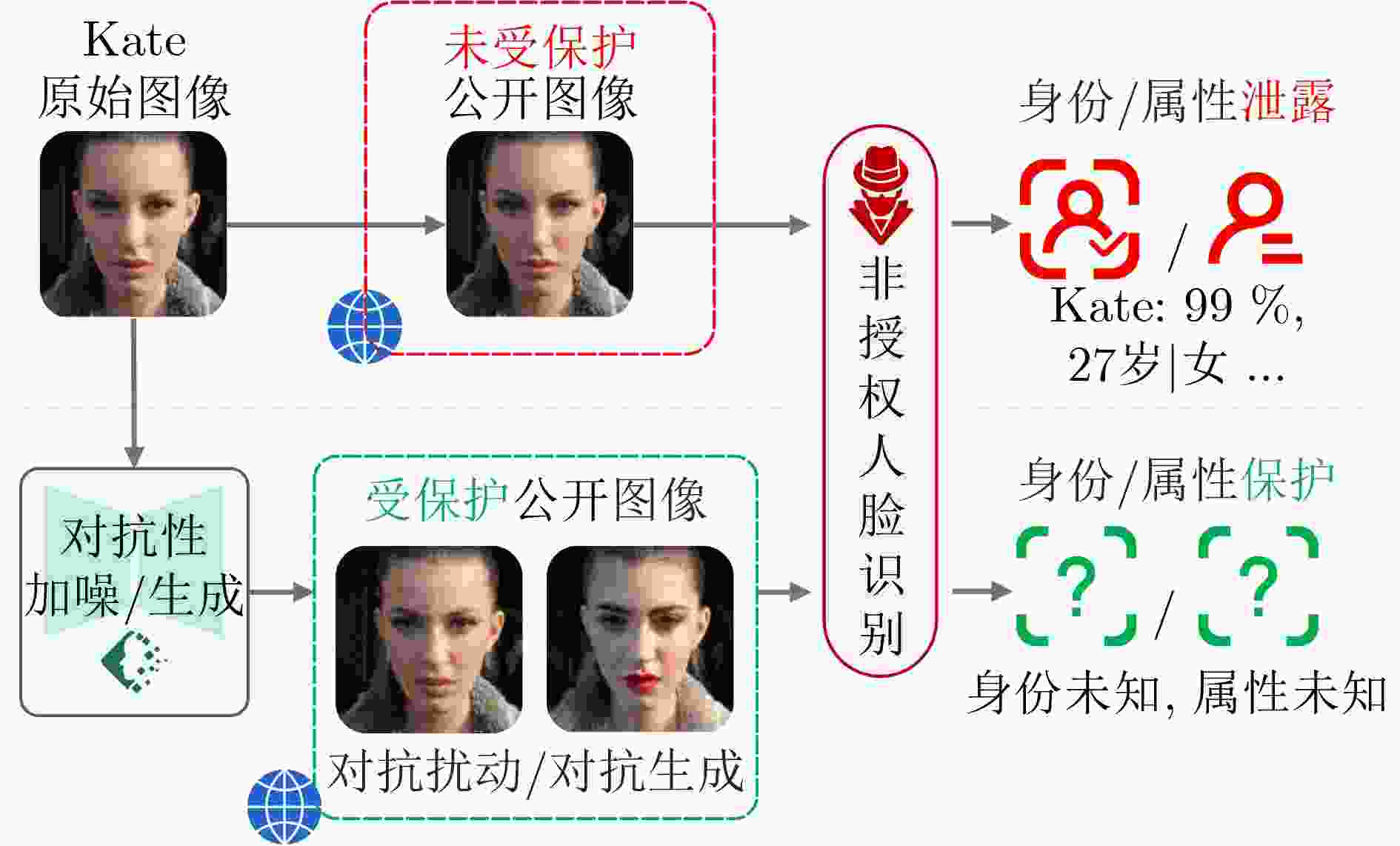
Significance With the widespread deployment of face recognition in Cyber-Physical Systems (CPS), including smart cities, intelligent transportation, and public safety infrastructures, privacy leakage has become a central concern for both academia and industry. Unlike many biometric modalities, face recognition operates in highly visible and loosely controlled environments such as public spaces, consumer devices, and online platforms, where facial image acquisition is effortless and pervasive. This exposure makes facial data especially vulnerable to unauthorized collection and misuse. Insufficient protection may lead to identity theft, unauthorized tracking, and deepfake generation, undermining individual rights and eroding trust in digital systems. Consequently, facial data protection is not merely a technical problem but a critical societal and ethical challenge. This work is significant in that it integrates fragmented research efforts across computer vision, cryptography, and privacy-preserving computation, providing a unified perspective to guide the development of trustworthy face recognition ecosystems that balance usability, compliance, and public trust. Contributions This paper systematically reviews recent advances in privacy-preserving computation for face recognition, covering both theoretical foundations and practical implementations. It begins by examining the core architecture and application pipeline of face recognition systems, identifying privacy risks at each stage. At the data collection stage, unauthorized or covert capture of facial images introduces immediate risks of misuse. During model training and deployment, gradient leakage, membership inference, and overfitting can expose sensitive information about individuals included in training data. At the inference stage, adversaries may reconstruct facial images, perform unauthorized recognition, or link identities across datasets, compromising anonymity.To address these threats, the paper categorizes existing approaches into four major privacy-preserving paradigms: data transformation, distributed collaboration, image generation, and adversarial perturbation. Within these categories, ten representative techniques are analyzed. Cryptographic computation, including homomorphic encryption and secure multiparty computation, enables recognition without revealing raw data but often incurs high computational overhead. Frequency-domain learning transforms images into spectral representations to suppress identifiable details while retaining discriminative features. Federated learning decentralizes training to reduce centralized data exposure, though it remains vulnerable to gradient inversion attacks. Image generation techniques, such as face synthesis and virtual identity modeling, reduce reliance on real facial data for training and testing. Differential privacy introduces calibrated noise to provide statistical privacy guarantees, while face anonymization obscures identifiable traits to protect visual privacy. Template protection and anti-reconstruction mechanisms defend stored features against reverse engineering, and adversarial privacy protection introduces imperceptible perturbations that disrupt machine recognition while preserving human perception.In addition, several representative studies from each category are examined in depth. The commonly used evaluation datasets are summarized, and a comparative analysis is conducted across multiple dimensions, including face recognition performance, privacy protection effectiveness, and practical usability, thereby systematically outlining the strengths and limitations of different types of methods. Prospects Looking forward, several research directions are identified. A primary challenge is achieving a dynamic balance between privacy protection and system utility, as excessive protection can degrade recognition performance while insufficient safeguards expose users to unacceptable risks. Adaptive mechanisms that adjust privacy levels based on context, task requirements, and user consent are therefore essential. Another promising direction is the development of inherently privacy-aware recognition paradigms, such as representations designed to minimize identity leakage by construction.Equally important is the establishment of standardized evaluation frameworks for privacy risk and usability, enabling reproducible benchmarking and facilitating real-world adoption. The emergence of generative foundation models, including diffusion and large multimodal models, further reshapes the landscape. While such models enable synthetic data generation and controllable identity representations, they also empower more sophisticated attacks such as high-fidelity face reconstruction and impersonation. Addressing these dual effects will require interdisciplinary collaboration spanning computer vision, cryptography, law, and ethics, alongside regulatory support and continuous methodological innovation. Conclusions This paper provides a comprehensive reference for researchers and practitioners working on trustworthy face recognition. By integrating advances across multiple disciplines, it aims to promote the development of effective facial privacy protection technologies and support the secure, reliable, and ethically responsible deployment of face recognition in real-world scenarios. Ultimately, the goal is to establish face recognition as a trustworthy component of Cyber-Physical Systems, balancing functionality, privacy, and societal trust. -
表 1 代表性研究工作的实验方法与性能对比
类别 应对
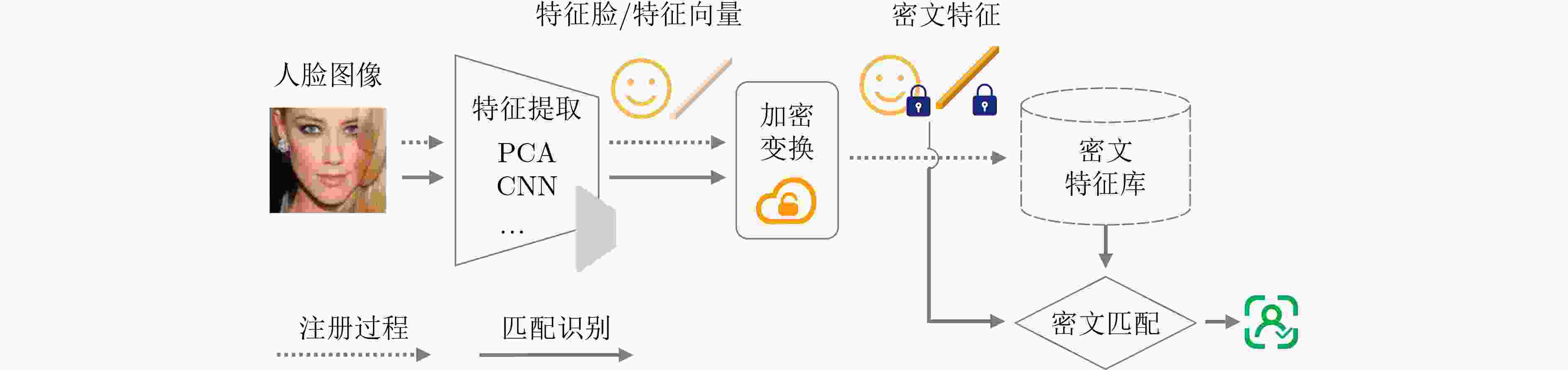
风险代表性研究 测试数据集 人脸识别性能(%) 隐私保护性能 可用性评估 加密
计算(r4)
(r5)Secure Face-FH[18] LFW, IJB-A, IJB-B,
CASIA-WebFaceTAR↑ (67.89-99.11) 理论性隐私保证 匹配耗时(2.45 ms)
存储开销(16 KB)Efficient-PPFR[37] LFW TAR↑ (97.72) 注册耗时(2.614 s)
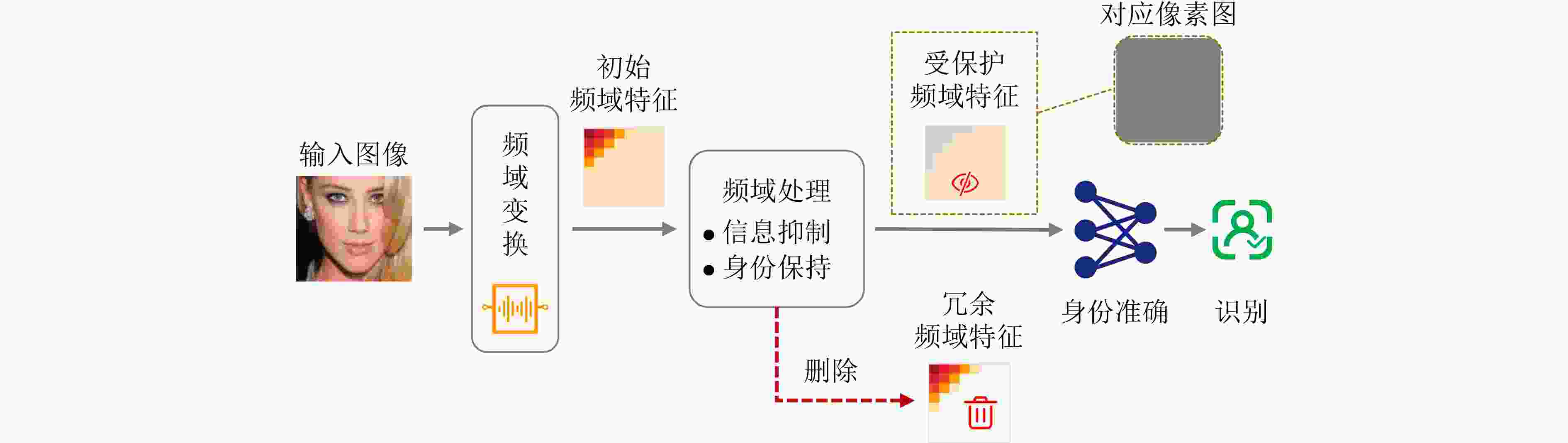
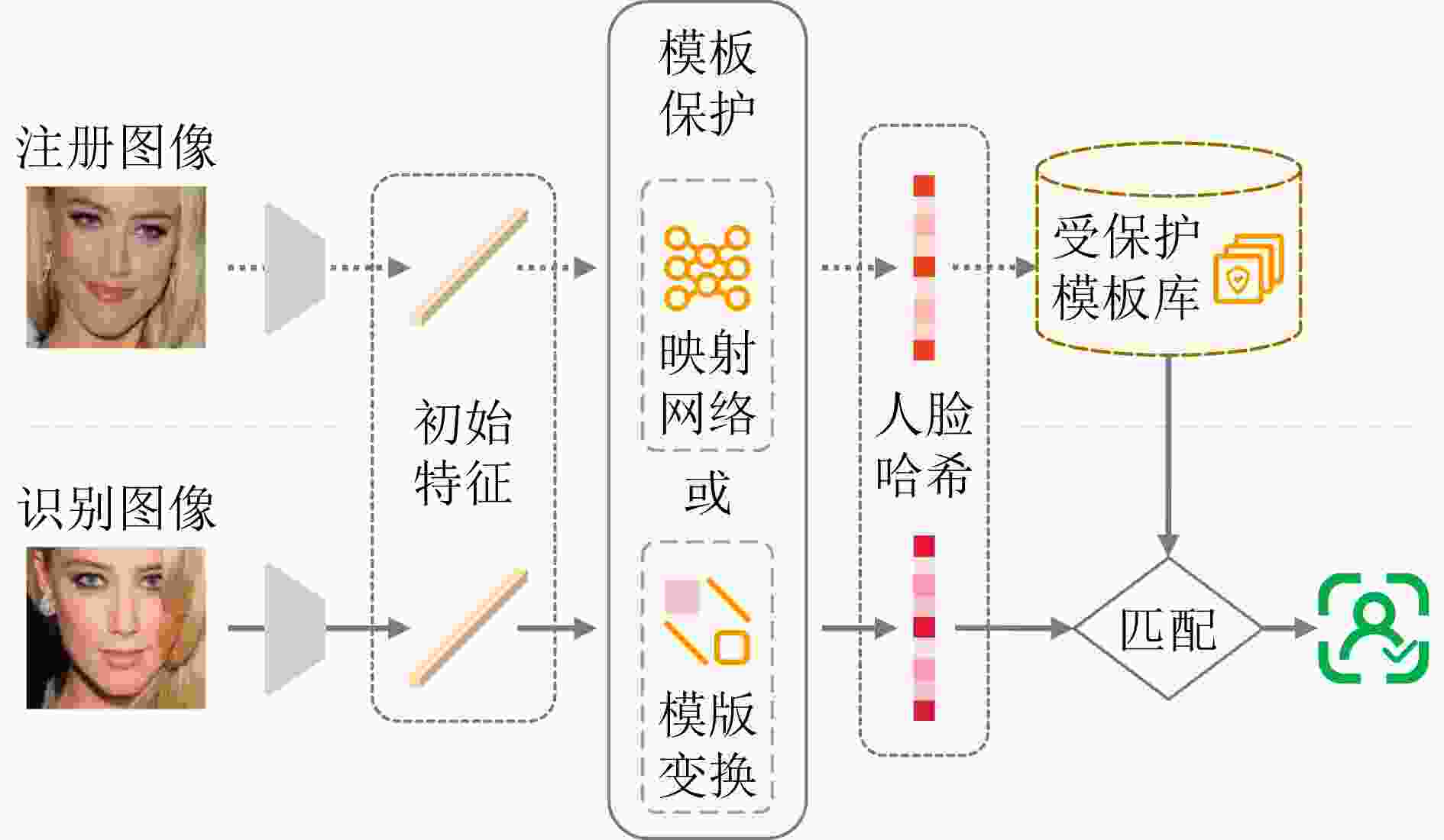
匹配耗时(2.718 s)Gao[38] Yale, ORL ACC↑ (89.29-96.15) 识别总耗时(2.467 s) 频域学习 (r2) PPFR-FD[9] LFW, CFP-FP, AgeDB, CPLFW, CALFW, VGGFace2 ACC↑ (90.78-99.68) SSIM↓ (0.713), PSNR↓ (15.66) N/A DuetFace[10] LFW, CFP-FP, AgeDB, CPLFW, CALFW, IJB-B, IJB-C ACC↑ (92.10-99.82) SSIM↓ (0.866), PSNR↓ (19.88) PartialFace[40] ACC↑ (92.03-99.80) SSIM↓ (0.591), PSNR↓ (13.70) 模板保护 (r5) MLP-Hash[21] LFW, MOBIO TAR↑ (90.90-100) 不可链接性↓(0.01)
不可逆性↑(9.05)保护执行时间↓(62 μs) Simhash[49] FEI, CASIA-WebFace,
LFWTAR↑ (94.06-100) 字典攻击复杂度↑(2411-2430次)
不可连接性↓(0.039-0.043)
不可逆性↓(0.04-0.08)注册耗时↓(10.1-10.8 ms)
匹配耗时↓(69-72 μs)SlerpFace[19] LFW, CFP-FP, AgeDB, CALFW, CPLFW, IJB-B, IJB-C ACC↑ (88.90-99.42) 不可链接性↓(0.05)
暴力破解次数↑(3.649次)注册耗时↓(0.35 s)
匹配耗时↓(0.17 s)联邦学习 (r3) FedFace[54] LFW, IJB-A, IJB-C ACC↑ (83.79-99.28) 经验性隐私保证 N/A FedFR[59] IJB-C ACC↑ (85.21) 合成图像训练 (r1)
(r3)HyperFace[73] LFW, CFP-FP, AgeDB, CPLFW, CALFW ACC↑ (87.07-98.67) 经验性隐私保证 N/A CemiFace[5] ACC↑ (88.86-99.22) MorphFace[74] ACC↑ (90.07-99.35) 保持身份匿名化 (r2) PRO-Face[79] LFW, CelebA, VGGFace2 TAR↑ (88.4-94.7) SSIM↓ (0.527-0.875)
LPIPS↑ (0.111-0.638)N/A Li[78] CelebA, VGGFace2 TAR↑ (61-89) 属性识别准确率↓,如
年龄23-49 %,性别13-41 %,
种族10-35 %FID↓ (41.64-54.04) Wang[82] CelebA, VGGFace2 AUC↑ (88.5-96.9) SSIM↓ (0.306-0.315)
LPIPS↑ (0.559-0.588)
MAE↑ (0.251-0.256)HPS↓ (2.315-3.831)
EDR↑ (69.2-73 %)虚拟身份匹配 (r2)
(r5)IVFG[84] LFW, CelebA AUC↑ (99.4-99.9)
EER↓ (1.8-3.5)PSR↑ (98.8 %) FDR↑ (100 %), FID↓ (6.17) CanFG[87] CelebA, VGGFace2 AUC↑ (95.1-98.8), EER↓ (4.5-10.1) PSR↑(98.2-99.2 %) FID↓ (9.43), SSIM↑ (0.823) KFAAR[88] LFW, CelebA AUC↑ (97.3-99.2), EER↓ (8.9-9.2) PSR↑ (92.2-96.2 %) FDR↑ (100 %), EDR↑ (80.5-83.3 %), FID↓ (6.82-7.29) 差分隐私 (r2)
(r3)
(r4)
(r5)Mao[91] LFW ACC↑ (82) 理论性隐私保证 N/A PEEP[22] LFW, CFP-FP, AgeDB, CPLFW, CALFW, IJB-B, IJB-C ACC↑ (5.82-98.41) Ji[39] ACC↑ (89.33-99.48) PSNR↓ (14.28), COS↓ (0.214) 重建攻击防御 (r5) AdvFace[20] LFW, CFP-FP, AgeDB-30 ACC↑ (86.35-97.78) SSIM↓ (0.28), PSNR↓ (6.97),
MSE↑ (0.206), SRRA↓ (4.03%)N/A MinusFace[43] LFW, CFP-FP, AgeDB, CPLFW, CALFW, IJB-B, IJB-C ACC↑ (91.90-99.78) SSIM↓ (0.50), PSNR↓ (10.98) FaceObfuscator[97] ACC↑ (88.48-99.68) SSIM↓ (0.471), PSNR↓ (12.71),
MSE↑ (0.057), COS↓ (0.004)存储开销:98 KB/pic
推理耗时:1.18 ms/pic对抗性隐私保护 (r2)
(r6)OPOM[101] Celeb-1M, LFW N/A PSR (1:N)↑ (78-86.6 %@R-1-U,
69.4-79.3 %@R-5-U)N/A CLIP2Protect[105] CelebA, LFW PSR (1:1)↑ (64.9 %),
PSR (1:N)↑ (82.2 %@R-1-U, 23.4 %@R-1-T)PSNR↑ (19.31),
SSIM↑ (0.75),
FID↓ (26.5)Salar[107] CelebA PSR (1:1)↑ (79.17 %) PSNR↑ (27.72),
SSIM↑ (0.84), FID↓ (26.5) -
[1] TURK M A and PENTLAND A P. Face recognition using eigenfaces[C]. Proceedings. 1991 IEEE Computer Society Conference on Computer Vision and Pattern Recognition, Maui, USA, 1991: 586–591. doi: 10.1109/CVPR.1991.139758. [2] SCHROFF F, KALENICHENKO D, and PHILBIN J. FaceNet: A unified embedding for face recognition and clustering[C]. Proceedings of the 2015 IEEE Conference on Computer Vision and Pattern Recognition, Boston, USA, 2015: 815–823. doi: 10.1109/CVPR.2015.7298682. [3] DENG Jiankang, GUO Jia, YANG Jing, et al. ArcFace: Additive angular margin loss for deep face recognition[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2022, 44(10): 5962–5979. doi: 10.1109/TPAMI.2021.3087709. [4] KIM M, JAIN A K, and LIU Xiaoming. AdaFace: Quality adaptive margin for face recognition[C]. IEEE/CVF Conference on Computer Vision and Pattern Recognition, New Orleans, USA, 2022: 18729–18738. doi: 10.1109/CVPR52688.2022.01819. [5] SUN Zhonglin, SONG Siyang, PATRAS I, et al. CemiFace: Center-based semi-hard synthetic face generation for face recognition[C]. Proceedings of the 37th International Conference on Neural Information Processing Systems, Vancouver, Canada, 2024: 35612–35638. doi: 10.52202/079017-1123. [6] BOUTROS F, HUBER M, SIEBKE P, et al. SFace: Privacy-friendly and accurate face recognition using synthetic data[C]. 2022 IEEE International Joint Conference on Biometrics, Abu Dhabi, United Arab Emirates, 2022: 1–11. doi: 10.1109/IJCB54206.2022.10007961. [7] QIU Haibo, YU Baosheng, GONG Dihong, et al. SynFace: Face recognition with synthetic data[C]. 2021 IEEE/CVF International Conference on Computer Vision, Montreal, Canada, 2021: 10860–10870. doi: 10.1109/ICCV48922.2021.01070. [8] KIM M, LIU Feng, JAIN A, et al. DCFace: Synthetic face generation with dual condition diffusion model[C]. Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Vancouver, Canada, 2023: 12715–12725. doi: 10.1109/CVPR52729.2023.01223. [9] WANG Yinggui, LIU Jian, LUO Man, et al. Privacy-preserving face recognition in the frequency domain[C]. Proceedings of the 36th AAAI Conference on Artificial Intelligence, Vancouver, Canada, 2022: 2558–2566. doi: 10.1609/aaai.v36i3.20157. (查阅网上资料,未找到本条文献出版地信息,请确认). [10] MI Yuxi, HUANG Yuge, JI Jiazhen, et al. DuetFace: Collaborative privacy-preserving face recognition via channel splitting in the frequency domain[C]. Proceedings of the 30th ACM International Conference on Multimedia, Lisboa, Portugal, 2022: 6755–6764. doi: 10.1145/3503161.3548303. [11] SHOKRI R, STRONATI M, SONG Congzheng, et al. Membership inference attacks against machine learning models[C]. 2017 IEEE Symposium on Security and Privacy, San Jose, USA, 2017: 3–18. doi: 10.1109/sp.2017.41. [12] SHAHREZA H O and MARCEL S. Unveiling synthetic faces: How synthetic datasets can expose real identities[C]. Proceedings of the Third Workshop on New Frontiers in Adversarial Machine Learning, Vancouver, Canada, 2024. [13] ZHU Ligeng, LIU Zhijian, and HAN Song. Deep leakage from gradients[C]. Proceedings of the 33rd International Conference on Neural Information Processing Systems, Vancouver, Canada, 2019: 1323. [14] LIU Yufan, ZHANG Wanqian, WU Dayan, et al. Prediction exposes your face: Black-box model inversion via prediction alignment[C]. Proceedings of the 18th European Conference on Computer Vision, Milan, Italy, 2025: 288–306. doi: 10.1007/978-3-031-72764-1_17. [15] ZHANG Hui, DONG Xingbo, LAI Y, et al. Validating privacy-preserving face recognition under a minimum assumption[C]. 2024 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Seattle, USA, 2024: 12205–12214. doi: 10.1109/CVPR52733.2024.01160. [16] SHAHREZA H O and MARCEL S. Template inversion attack against face recognition systems using 3D face reconstruction[C]. 2023 IEEE/CVF International Conference on Computer Vision, Paris, France, 2023: 19605–19615. doi: 10.1109/ICCV51070.2023.01801. [17] SHAHREZA H O and MARCEL S. Face reconstruction from facial templates by learning latent space of a generator network[C]. Proceedings of the 37th International Conference on Neural Information Processing Systems, New Orleans, USA, 2023: 557. [18] BODDETI V N. Secure face matching using fully homomorphic encryption[C]. 2018 IEEE 9th International Conference on Biometrics Theory, Applications and Systems, Redondo Beach, USA, 2018: 1–10. doi: 10.1109/BTAS.2018.8698601. [19] ZHONG Zhizhou, MI Yuxi, HUANG Yuge, et al. SlerpFace: Face template protection via spherical linear interpolation[C]. Proceedings of the 39th AAAI Conference on Artificial Intelligence, Philadelphia, USA, 2025: 10698–10706. doi: 10.1609/aaai.v39i10.33162. [20] WANG Zhibo, WANG He, JIN Shuaifan, et al. Privacy-preserving adversarial facial features[C]. 2023 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Vancouver, Canada, 2023: 8212–8221. doi: 10.1109/CVPR52729.2023.00794. [21] SHAHREZA H O, HAHN V K, and MARCEL S. MLP-hash: Protecting face templates via hashing of randomized multi-layer perceptron[C]. 2023 31st European Signal Processing Conference, Helsinki, Finland, 2023: 605–609. doi: 10.23919/EUSIPCO58844.2023.10289780. [22] CHAMIKARA M A P, BERTOK P, KHALIL I, et al. Privacy preserving face recognition utilizing differential privacy[J]. Computers & Security, 2020, 97: 101951. doi: 10.1016/j.cose.2020.101951. [23] TANG Long, YE Dengpan, LV Yunna, et al. Once and for all: Universal transferable adversarial perturbation against deep hashing-based facial image retrieval[C]. Proceedings of the 38th AAAI Conference on Artificial Intelligence, Vancouver, Canada, 2024: 5136–5144. doi: 10.1609/aaai.v38i6.28319. [24] HU Shengshan, LIU Xiaogeng, ZHANG Yechao, et al. Protecting facial privacy: Generating adversarial identity masks via style-robust makeup transfer[C]. Proceedings of the 2022 IEEE/CVF Conference on Computer Vision and Pattern Recognition, New Orleans, USA, 2022: 14994–15003. doi: 10.1109/CVPR52688.2022.01459. [25] YANG Xiao, LIU Chang, XU Longlong, et al. Towards effective adversarial textured 3D meshes on physical face recognition[C]. 2023 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Vancouver, Canada, 2023: 4119–4128. doi: 10.1109/CVPR52729.2023.00401. [26] ERKIN Z, FRANZ M, GUAJARDO J, et al. Privacy-preserving face recognition[C]. The 9th International Symposium on Privacy Enhancing Technologies, Seattle, USA, 2009: 235–253. doi: 10.1007/978-3-642-03168-7_14. [27] PAILLIER P. Public-key cryptosystems based on composite degree residuosity classes[M]. STERN J. Advances in Cryptology–EUROCRYPT ’99. Berlin: Springer, 1999: 223–238. doi: 10.1007/3-540-48910-X_16. [28] DAMGÅRD I, GEISLER M, and KRØIGAARD M. Efficient and secure comparison for on-line auctions[C]. 12th Australasian Conference on Information Security and Privacy, Townsville, Australia, 2007: 416–430. doi: 10.1007/978-3-540-73458-1_30. [29] MA Zhuo, LIU Yang, LIU Ximeng, et al. Lightweight privacy-preserving ensemble classification for face recognition[J]. IEEE Internet of Things Journal, 2019, 6(3): 5778–5790. doi: 10.1109/JIOT.2019.2905555. [30] ZHANG Pengbo and YANG Zhixin. A novel AdaBoost framework with robust threshold and structural optimization[J]. IEEE Transactions on Cybernetics, 2018, 48(1): 64–76. doi: 10.1109/TCYB.2016.2623900. [31] OSADCHY M, PINKAS B, JARROUS A, et al. SCiFI - A system for secure face identification[C]. 2010 IEEE Symposium on Security and Privacy, Oakland, USA, 2010: 239–254. doi: 10.1109/SP.2010.39. [32] TRONCOSO-PASTORIZA J R, GONZALEZ-JIMENEZ D, and PEREZ-GONZALEZ F. Fully private noninteractive face verification[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(7): 1101–1114. doi: 10.1109/TIFS.2013.2262273. [33] JIN Xin, LIU Yan, LI Xiaodong, et al. Privacy preserving face identification in the cloud through sparse representation[C]. Proceedings of the 10th Chinese Conference on Biometric Recognition, Tianjin, China, 2015: 160–167. doi: 10.1007/978-3-319-25417-3_20. [34] IBARRONDO A, CHABANNE H, DESPIEGEL V, et al. Grote: Group testing for privacy-preserving face identification[C]. Proceedings of the Thirteenth ACM Conference on Data and Application Security and Privacy, Charlotte, USA, 2023: 117–128. doi: 10.1145/3577923.3583656. [35] CHEON J H, KIM A, KIM M, et al. Homomorphic encryption for arithmetic of approximate numbers[C]. 23rd International Conference on the Theory and Applications of Cryptology and Information Security, Hong Kong, China, 2017: 409–437. doi: 10.1007/978-3-319-70694-8_15. [36] GUO Shangwei, XIANG Tao, and LI Xiaoguo. Towards efficient privacy-preserving face recognition in the cloud[J]. Signal Processing, 2019, 164: 320–328. doi: 10.1016/j.sigpro.2019.06.024. [37] KOU Xiaoyu, ZHANG Ziling, ZHANG Yuelei, et al. Efficient and privacy-preserving distributed face recognition scheme via FaceNet[C]. Proceedings of the ACM Turing Award Celebration Conference, Hefei, China, 2021: 110–115. doi: 10.1145/3472634.3472661. [38] GAO Wenjing, YU Jia, HAO Rong, et al. Privacy-preserving face recognition with multi-edge assistance for intelligent security systems[J]. IEEE Internet of Things Journal, 2023, 10(12): 10948–10958. doi: 10.1109/JIOT.2023.3240166. [39] JI Jiazhen, WANG Huan, HUANG Yuge, et al. Privacy-preserving face recognition with learnable privacy budgets in frequency domain[C]. 17th European Conference on Computer Vision, Tel Aviv, Israel, 2022: 475–491. doi: 10.1007/978-3-031-19775-8_28. [40] MI Yuxi, HUANG Yuge, JI Jiazhen, et al. Privacy-preserving face recognition using random frequency components[C]. Proceedings of the IEEE/CVF International Conference on Computer Vision, Paris, France, 2023: 19616–19627. doi: 10.1109/ICCV51070.2023.01802. [41] HENRY C, ASIF M S, and LI Zhu. Privacy preserving face recognition with lensless camera[C]. 2023 IEEE International Conference on Acoustics, Speech and Signal Processing, Rhodes Island, Greece, 2023: 1–5. doi: 10.1109/ICASSP49357.2023.10096627. [42] ASIF M S, AYREMLOU A, SANKARANARAYANAN A, et al. Flatcam: Thin, lensless cameras using coded aperture and computation[J]. IEEE Transactions on Computational Imaging, 2017, 3(3): 384–397. doi: 10.1109/TCI.2016.2593662. [43] MI Yuxi, ZHONG Zhizhou, HUANG Yuge, et al. Privacy-preserving face recognition using trainable feature subtraction[C]. Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Seattle, USA, 2024: 297–307. doi: 10.1109/CVPR52733.2024.00036. [44] PANDEY R K, ZHOU Yingbo, KOTA B U, et al. Deep secure encoding for face template protection[C]. 2016 IEEE Conference on Computer Vision and Pattern Recognition Workshops, Las Vegas, USA, 2016: 77–83. doi: 10.1109/CVPRW.2016.17. [45] TALREJA V, VALENTI M C, and NASRABADI N M. Zero-shot deep hashing and neural network based error correction for face template protection[C]. 2019 IEEE 10th International Conference on Biometrics Theory, Applications and Systems, Tampa, USA, 2019: 1–10. doi: 10.1109/BTAS46853.2019.9185979. [46] 赵铖辉, 李勇, 张振江. BinaryFace: 基于深层卷积神经网络的人脸模板保护模型[J]. 信息安全学报, 2020, 5(5): 43–55. doi: 10.19363/J.cnki.cn10-1380/tn.2020.09.04.ZHAO Chenghui, LI Yong, and ZHANG Zhenjiang. BinaryFace: The model of face template protection based on CNN[J]. Journal of Cyber Security, 2020, 5(5): 43–55. doi: 10.19363/J.cnki.cn10-1380/tn.2020.09.04. [47] ZHOU Junwei, SHANG Delong, LANG Huile, et al. Face template protection through residual learning based error-correcting codes[C]. Proceedings of the 4th International Conference on Control and Computer Vision, Macau, China, 2021: 112–118. doi: 10.1145/3484274.3484292. [48] MAI Guangcan, CAO Kai, LAN Xiangyuan, et al. SecureFace: Face template protection[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 262–277. doi: 10.1109/TIFS.2020.3009590. [49] GAO Ce, ZHANG Kang, WANG Weiwei, et al. Protected face templates generation based on multiple partial Walsh transformations and Simhash[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 4100–4113. doi: 10.1109/TIFS.2024.3369322. [50] SWICK D. Walsh function generation (Corresp. )[J]. IEEE Transactions on Information Theory, 1969, 15(1): 167–167. doi: 10.1109/TIT.1969.1054251. [51] CHARIKAR M S. Similarity estimation techniques from rounding algorithms[C]. Proceedings of the Thiry-Fourth Annual ACM Symposium on Theory of Computing, Montreal, Canada, 2002: 380–388. doi: 10.1145/509907.509965. [52] 李亚红, 李一婧, 杨小东, 等. 基于同态加密和群签名的可验证联邦学习方案[J]. 电子与信息学报, 2025, 47(3): 758–768. doi: 10.11999/JEIT240796.LI Yahong, LI Yijing, YANG Xiaodong, et al. A verifiable federated learning scheme based on homomorphic encryption and group signature[J]. Journal of Electronics & Information Technology, 2025, 47(3): 758–768. doi: 10.11999/JEIT240796. [53] 郭显, 王典冬, 冯涛, 等. 基于同态加密的可验证隐私保护联邦学习方案[J]. 电子与信息学报, 2025, 47(4): 1113–1125. doi: 10.11999/JEIT240390.GUO Xian, WANG Diandong, FENG Tao, et al. A verifiable privacy protection federated learning scheme based on homomorphic encryption[J]. Journal of Electronics & Information Technology, 2025, 47(4): 1113–1125. doi: 10.11999/JEIT240390. [54] AGGARWAL D, ZHOU Jiayu, and JAIN A K. FedFace: Collaborative learning of face recognition model[C]. 2021 IEEE International Joint Conference on Biometrics, Shenzhen, China, 2021: 1–8. doi: 10.1109/IJCB52358.2021.9484386. [55] MARTÍNEZ BELTRÁN E T, PERALES GÓMEZ Á L, FENG Chao, et al. Fedstellar: A platform for decentralized federated learning[J]. Expert Systems with Applications, 2024, 242: 122861. doi: 10.1016/j.eswa.2023.122861. [56] GAO Liang, LI Li, CHEN Yingwen, et al. FIFL: A fair incentive mechanism for federated learning[C]. Proceedings of the 50th International Conference on Parallel Processing, Lemont, USA, 2021: 82. doi: 10.1145/3472456.3472469. [57] ZHENG Haipeng, LI Bing, LIU Guozhu, et al. Blockchain-based federated learning framework applied in face recognition[C]. 2022 7th International Conference on Signal and Image Processing, Suzhou, China, 2022: 265–269. doi: 10.1109/ICSIP55141.2022.9886171. [58] NIU Yifan and DENG Weihong. Federated learning for face recognition with gradient correction[C]. Proceedings of the 36th AAAI Conference on Artificial Intelligence, 2022: 1999–2007. doi: 10.1609/aaai.v36i2.20095. (查阅网上资料,未找到本条文献出版地信息,请确认). [59] LIU C T, WANG C Y, CHIEN S Y, et al. FedFR: Joint optimization federated framework for generic and personalized face recognition[C]. Proceedings of the 36th AAAI Conference on Artificial Intelligence, 2022: 1656–1664. doi: 10.1609/aaai.v36i2.20057. [60] WOUBIE A, SOLOMON E, and ATTIEH J. Maintaining privacy in face recognition using federated learning method[J]. IEEE Access, 2024, 12: 39603–39613. doi: 10.1109/ACCESS.2024.3373691. [61] KIM J, PARK T, KIM H, et al. Federated learning for face recognition[C]. 2021 IEEE International Conference on Consumer Electronics, Las Vegas, USA, 2021: 1–2. doi: 10.1109/ICCE50685.2021.9427748. [62] DENG Yu, YANG Jiaolong, CHEN Dong, et al. Disentangled and controllable face image generation via 3D imitative-contrastive learning[C]. Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Seattle, USA, 2020: 5153–5162. doi: 10.1109/CVPR42600.2020.00520. [63] LI Yuancheng, WANG Yimeng, and LI Daoxing. Privacy-preserving lightweight face recognition[J]. Neurocomputing, 2019, 363: 212–222. doi: 10.1016/j.neucom.2019.07.039. [64] SAATCHI Y and WILSON A G. Bayesian GAN[C]. Proceedings of the 31st International Conference on Neural Information Processing Systems, Long Beach, USA, 2017. 2017: 3625–3634. [65] KARRAS T, AITTALA M, HELLSTEN J, et al. Training generative adversarial networks with limited data[C]. Proceedings of the 34th International Conference on Neural Information Processing Systems, Vancouver, Canada, 2020: 1015. [66] BAE G, DE LA GORCE M, BALTRUŠAITIS T, et al. DigiFace-1M: 1 million digital face images for face recognition[C]. Proceedings of the IEEE/CVF Winter Conference on Applications of Computer Vision, Waikoloa, USA, 2023: 3515–3524. doi: 10.1109/WACV56688.2023.00352. [67] BLANZ V and VETTER T. A morphable model for the synthesis of 3D faces[C]. Proceedings of the 26th Annual Conference on Computer Graphics and Interactive Techniques, Los Angeles, USA, 1999: 187–194. doi: 10.1145/311535.311556. [68] WOOD E, BALTRUŠAITIS T, HEWITT C, et al. Fake it till you make it: Face analysis in the wild using synthetic data alone[C]. Proceedings of the IEEE/CVF International Conference on Computer Vision, Montreal, Canada, 2021: 3661–3671. doi: 10.1109/ICCV48922.2021.00366. [69] KOLF J N, RIEBER T, ELLIESEN J, et al. Identity-driven three-player generative adversarial network for synthetic-based face recognition[C]. 2023 IEEE/CVF Conference on Computer Vision and Pattern Recognition Workshops, Vancouver, Canada, 2023: 806–816. doi: 10.1109/CVPRW59228.2023.00088. [70] BOUTROS F, GREBE J H, KUIJPER A, et al. IDiff-Face: Synthetic-based face recognition through fizzy identity-conditioned diffusion model[C]. Proceedings of the IEEE/CVF International Conference on Computer Vision, Paris, France, 2023: 19593–19604. doi: 10.1109/ICCV51070.2023.01800. [71] MELZI P, RATHGEB C, TOLOSANA R, et al. GANDiffFace: Controllable generation of synthetic datasets for face recognition with realistic variations[C]. Proceedings of the 2023 IEEE/CVF International Conference on Computer Vision Workshops, Paris, France, 2023: 3078–3087. doi: 10.1109/ICCVW60793.2023.00333. [72] XU Jianqing, LI Shen, WU Jiaying, et al. ID3: Identity-preserving-yet-diversified diffusion models for synthetic face recognition[C]. Proceedings of the 38th International Conference on Neural Information Processing Systems, Vancouver, Canada, 2024: 77777–77798. [73] SHAHREZA H O and MARCEL S. HyperFace: Generating synthetic face recognition datasets by exploring face embedding hypersphere[C]. The Thirteenth International Conference on Learning Representations, Singapore, Singapore, 2025: 478–491. (查阅网上资料, 未找到本条文献页码信息, 请确认). [74] MI Yuxi, ZHONG Zhizhou, HUANG Yuge, et al. Data synthesis with diverse styles for face recognition via 3DMM-guided diffusion[C]. Proceedings of the 2025 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Nashville, USA, 2025: 21203–21214. doi: 10.1109/CVPR52734.2025.01975. [75] 彭春蕾, 苗紫民, 刘德成, 等. 视觉身份隐私保护: 人脸匿名化研究方法[J]. 计算机学报, 2023, 46(11): 2431–2452. doi: 10.11897/SP.J.1016.2023.02431.PENG Chunlei, MIAO Zimin, LIU Decheng, et al. Visual identity privacy protection: Research methods of face anonymization[J]. Chinese Journal of Computers, 2023, 46(11): 2431–2452. doi: 10.11897/SP.J.1016.2023.02431. [76] LI Jingzhi, HAN Lutong, ZHANG Hua, et al. Learning disentangled representations for identity preserving surveillance face camouflage[C]. 2020 25th International Conference on Pattern Recognition, Milan, Italy, 2021: 9748–9755. doi: 10.1109/ICPR48806.2021.9412636. [77] LI Jingzhi, HAN Lutong, CHEN Ruoyu, et al. Identity-preserving face anonymization via adaptively facial attributes obfuscation[C]. Proceedings of the 29th ACM International Conference on Multimedia, Chengdu, China, 2021: 3891–3899. doi: 10.1145/3474085.3475367. (查阅网上资料,未找到本条文献出版地信息,请确认). [78] LI Jingzhi, ZHANG Hua, LIANG Siyuan, et al. Privacy-enhancing face obfuscation guided by semantic-aware attribution maps[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 3632–3646. doi: 10.1109/TIFS.2023.3282384. [79] YUAN Lin, LIU Linguo, PU Xiao, et al. PRO-face: A generic framework for privacy-preserving recognizable obfuscation of face images[C]. Proceedings of the 30th ACM International Conference on Multimedia, Lisboa, Portugal, 2022: 1661–1669. doi: 10.1145/3503161.3548202. [80] YUAN Lin, CHEN Wu, PU Xiao, et al. PRO-face C: Privacy-preserving recognition of obfuscated face via feature compensation[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 4930–4944. doi: 10.1109/TIFS.2024.3388976. [81] SU Zhigang, ZHOU Dawei, WANG Nannan, et al. Hiding visual information via obfuscating adversarial perturbations[C]. Proceedings of the IEEE/CVF International Conference on Computer Vision, Paris, France, 2023: 4333–4343. doi: 10.1109/ICCV51070.2023.00402. [82] WANG Tao, ZHANG Yushu, YANG Zixuan, et al. Seeing is not believing: An identity hider for human vision privacy protection[J]. IEEE Transactions on Biometrics, Behavior, and Identity Science, 2025, 7(2): 170–181. doi: 10.1109/TBIOM.2024.3449849. [83] 任坤, 李峥瑱, 桂源泽, 等. 低分辨率随机遮挡人脸图像的超分辨率修复[J]. 电子与信息学报, 2024, 46(8): 3343–3352. doi: 10.11999/JEIT231262.REN Kun, LI Zhengzhen, GUI Yuanze, et al. Super-resolution inpainting of low-resolution randomly occluded face images[J]. Journal of Electronics & Information Technology, 2024, 46(8): 3343–3352. doi: 10.11999/JEIT231262. [84] YUAN Zhuowen, YOU Zhengxin, LI Sheng, et al. On generating identifiable virtual faces[C]. Proceedings of the 30th ACM International Conference on Multimedia, Lisboa, Portugal, 2022: 1465–1473. doi: 10.1145/3503161.3548110. [85] KARRAS T, LAINE S, and AILA T. A style-based generator architecture for generative adversarial networks[C]. 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Long Beach, USA, 2019: 4396–4405. doi: 10.1109/CVPR.2019.00453. [86] WANG Tao, ZHANG Yushu, ZHAO Ruoyu, et al. Identifiable face privacy protection via virtual identity transformation[J]. IEEE Signal Processing Letters, 2023, 30: 773–777. doi: 10.1109/LSP.2023.3289392. [87] WANG Tao, ZHANG Yushu, XIAO Xiangli, et al. Make privacy renewable! Generating privacy-preserving faces supporting cancelable biometric recognition[C]. Proceedings of the 32nd ACM International Conference on Multimedia, Melbourne, Australia, 2024: 10268–10276. doi: 10.1145/3664647.3680704. [88] WANG Miaomiao, HUA Guang, LI Sheng, et al. A key-driven framework for identity-preserving face anonymization[C]. 32nd Annual Network and Distributed System Security Symposium, San Diego, USA, 2025: 10168–10176. doi: 10.14722/ndss.2025.23729. (查阅网上资料,未找到本条文献页码和doi信息,请确认). [89] DWORK C and LEI Jing. Differential privacy and robust statistics[C]. Proceedings of the Forty-First Annual ACM Symposium on Theory of Computing, Bethesda, USA, 2009: 371–380. doi: 10.1145/1536414.1536466. [90] MAHAWAGA ARACHCHIGE P C, BERTOK P, KHALIL I, et al. Local differential privacy for deep learning[J]. IEEE Internet of Things Journal, 2020, 7(7): 5827–5842. doi: 10.1109/JIOT.2019.2952146. [91] MAO Yunlong, YI Shanhe, LI Qun, et al. A privacy-preserving deep learning approach for face recognition with edge computing[C]. Proceedings of the USENIX Workshop on Hot Topics in Edge Computing, Boston, USA, 2018: 1–6. doi: 10.5555/3342665.3342676. (查阅网上资料,未找到本条文献页码和doi信息,请确认). [92] MENG Qiang, ZHOU Feng, REN Hainan, et al. Improving federated learning face recognition via privacy-agnostic clusters[C]. The Tenth International Conference on Learning Representations, 2022: 237–245. (查阅网上资料, 未找到本条文献页码和出版地信息, 请确认). [93] WEN Yunqian, LIU Bo, DING Ming, et al. IdentityDP: Differential private identification protection for face images[J]. Neurocomputing, 2022, 501: 197–211. doi: 10.1016/j.neucom.2022.06.039. [94] 张啸剑, 付聪聪, 孟小峰. 结合矩阵分解与差分隐私的人脸图像发布[J]. 中国图象图形学报, 2020, 25(4): 655–668. doi: 10.11834/jig.190308.ZHANG Xiaojian, FU Congcong, and MENG Xiaofeng. Private facial image publication through matrix decomposition[J]. Journal of Image and Graphics, 2020, 25(4): 655–668. doi: 10.11834/jig.190308. [95] XIAO Taihong, TSAI Y H, SOHN K, et al. Adversarial learning of privacy-preserving and task-oriented representations[C]. Proceedings of the 34th AAAI Conference on Artificial Intelligence, New York, USA, 2020: 12434–12441. doi: 10.1609/aaai.v34i07.6930. [96] LI Ang, GUO Jiayi, YANG Huanrui, et al. DeepObfuscator: Obfuscating intermediate representations with privacy-preserving adversarial learning on smartphones[C]. Proceedings of the International Conference on Internet-of-Things Design and Implementation, Charlottesvle, USA, 2021: 28–39. doi: 10.1145/3450268.3453519. [97] JIN Shuaifan, WANG He, WANG Zhibo, et al. FaceObfuscator: Defending deep learning-based privacy attacks with gradient descent-resistant features in face recognition[C]. Proceedings of the 33rd USENIX Conference on Security Symposium, Philadelphia, USA, 2024: 383. [98] WEI Chenda, WANG Haoyue, QIAN Zhenxing, et al. Learning discrepant transformations for face privacy protection[C]. Proceedings of the 33rd ACM International Conference on Multimedia, Dublin, Ireland, 2025: 7672–7680. doi: 10.1145/3746027.3754881. [99] SHAN S, WENGER Emily, ZHANG Jiayun, et al. Fawkes: Protecting privacy against unauthorized deep learning models[C]. Proceedings of the 29th USENIX Conference on Security Symposium, Santa Clara, USA, 2020: 90. (查阅网上资料, 未找到本条文献出版地信息, 请确认). [100] YANG Xiao, DONG Yinpeng, PANG Tianyu, et al. Towards face encryption by generating adversarial identity masks[C]. 2021 IEEE/CVF International Conference on Computer Vision, Montreal, Canada, 2021: 3877–3887. doi: 10.1109/ICCV48922.2021.00387. [101] ZHONG Yaoyao and DENG Weihong. OPOM: Customized invisible cloak towards face privacy protection[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2023, 45(3): 3590–3603. doi: 10.1109/TPAMI.2022.3175602. [102] LIU Xuannan, ZHONG Yaoyao, CUI Xing, et al. AdvCloak: Customized adversarial cloak for privacy protection[J]. Pattern Recognition, 2025, 158: 111050. doi: 10.1016/j.patcog.2024.111050. [103] DONG Xin, WANG Rui, LIANG Siyuan, et al. Face encryption via frequency-restricted identity-agnostic attacks[C]. Proceedings of the 31st ACM International Conference on Multimedia, Ottawa, Canada, 2023: 579–588. doi: 10.1145/3581783.3612233. [104] YIN Bangjie, WANG Wenxuan, YAO Taiping, et al. Adv-makeup: A new imperceptible and transferable attack on face recognition[C]. Proceedings of the Thirtieth International Joint Conference on Artificial Intelligence, Montreal, Canada, 2021: 1252–1258. doi: 10.24963/ijcai.2021/173. [105] SHAMSHAD F, NASEER M, and NANDAKUMAR K. CLIP2Protect: Protecting facial privacy using text-guided makeup via adversarial latent search[C]. 2023 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Vancouver, Canada, 2023: 20595–20605. doi: 10.1109/CVPR52729.2023.01973. [106] SUN Yuhao, YU Lingyun, XIE Hongtao, et al. DiffAM: Diffusion-based adversarial makeup transfer for facial privacy protection[C]. 2024 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Seattle, USA, 2024: 24584–24594. doi: 10.1109/CVPR52733.2024.02321. [107] SALAR A, LIU Qing, TIAN Yingli, et al. Enhancing facial privacy protection via weakening diffusion purification[C]. Proceedings of the 2025 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Nashville, USA, 2025: 8235–8244. doi: 10.1109/CVPR52734.2025.00771. [108] 孙军梅, 潘振雄, 李秀梅, 等. 面向人脸验证的可迁移对抗样本生成方法[J]. 电子与信息学报, 2023, 45(5): 1842–1851. doi: 10.11999/JEIT220358.SUN Junmei, PAN Zhenxiong, LI Xiumei, et al. Transferable adversarial example generation method for face verification[J]. Journal of Electronics & Information Technology, 2023, 45(5): 1842–1851. doi: 10.11999/JEIT220358. [109] ZHANG Yushu, WANG Tao, ZHAO Ruoyu, et al. RAPP: Reversible privacy preservation for various face attributes[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 3074–3087. doi: 10.1109/TIFS.2023.3274359. [110] MIRJALILI V, RASCHKA S, and ROSS A. PrivacyNet: Semi-adversarial networks for multi-attribute face privacy[J]. IEEE Transactions on Image Processing, 2020, 29: 9400–9412. doi: 10.1109/TIP.2020.3024026. [111] MORALES A, FIERREZ J, VERA-RODRIGUEZ R, et al. SensitiveNets: Learning agnostic representations with application to face images[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2021, 43(6): 2158–2164. doi: 10.1109/TPAMI.2020.3015420. [112] WANG Zhou, BOVIK A C, SHEIKH H R, et al. Image quality assessment: From error visibility to structural similarity[J]. IEEE Transactions on Image Processing, 2004, 13(4): 600–612. doi: 10.1109/TIP.2003.819861. [113] HUANG G B, MATTAR M, BERG T, et al. Labeled faces in the wild: A database for studying face recognition in unconstrained environments[C]. Proceedings of the Workshop on Faces in ‘Real-Life’ Images: Detection, Alignment, and Recognition, Marseille, France, 2008. [114] LIU Ziwei, LUO Ping, WANG Xiaogang, et al. Deep learning face attributes in the wild[C]. Proceedings of the IEEE International Conference on Computer Vision, Santiago, Chile, 2015: 3730–3738. doi: 10.1109/ICCV.2015.425. [115] CAO Qiong, SHEN Li, XIE Weidi, et al. VGGFace2: A dataset for recognising faces across pose and age[C]. Proceedings of the 2018 13th IEEE International Conference on Automatic Face & Gesture Recognition, Xi'an, China, 2018: 67–74. doi: 10.1109/FG.2018.00020. [116] YI Dong, LEI Zhen, LIAO Shengcai, et al. Learning face representation from scratch[EB/OL]. https://arxiv.org/abs/1411.7923, 2014. [117] SENGUPTA S, CHEN Juncheng, CASTILLO C, et al. Frontal to profile face verification in the wild[C]. 2016 IEEE Winter Conference on Applications of Computer Vision, Lake Placid, USA, 2016: 1–9. doi: 10.1109/WACV.2016.7477558. [118] MOSCHOGLOU S, PAPAIOANNOU A, SAGONAS C, et al. AgeDB: The first manually collected, in-the-wild age database[C]. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, Honolulu, USA, 2017: 1997–2005. doi: 10.1109/CVPRW.2017.250. [119] ZHENG Tianyue and DENG Weihong. Cross-pose LFW: A database for studying cross-pose face recognition in unconstrained environments[J]. Beijing University of Posts and Telecommunications, Tech. Rep, 2018, 5(7): 1-6. (查阅网上资料, 未找到本条文献卷期, 刊名和页码信息, 请确认). [120] ZHENG Tianyue, DENG Weihong, and HU Jiani. Cross-age LFW: A database for studying cross-age face recognition in unconstrained environments[EB/OL]. https://arxiv.org/abs/1708.08197, 2017. [121] THOMAZ C E and GIRALDI G A. A new ranking method for principal components analysis and its application to face image analysis[J]. Image and Vision Computing, 2010, 28(6): 902–913. doi: 10.1016/j.imavis.2009.11.005. [122] WHITELAM C, TABORSKY E, BLANTON A, et al. IARPA JANUS benchmark-B face dataset[C]. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, Honolulu, USA, 2017: 592–600. doi: 10.1109/CVPRW.2017.87. [123] MAZE B, ADAMS J, DUNCAN J A, et al. IARPA Janus Benchmark-C: Face dataset and protocol[C]. 2018 International Conference on Biometrics (ICB), Gold Coast, Australia, 2018: 158–165. doi: 10.1109/ICB2018.2018.00033. [124] LEE K C, HO J, and KRIEGMAN D J. Acquiring linear subspaces for face recognition under variable lighting[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2005, 27(5): 684–698. doi: 10.1109/TPAMI.2005.92. [125] SAKTHIVEL S, LAKSHMIPATHI R, and ARUMUGAM M A M. Evaluation of feature extraction and dimensionality reduction algorithms for face recognition using ORL database[C]. Proceedings of the 2009 International Conference on Image Processing, Computer Vision, & Pattern Recognition, Las Vegas, USA, 2009: 367–373. doi: 10.1109/IPCV.2009.50. (查阅网上资料,未找到本条文献页码和doi信息,请确认). [126] MCCOOL C, WALLACE R, MCLAREN M, et al. Session variability modelling for face authentication[J]. IET Biometrics, 2013, 2(3): 117–129. doi: 10.1049/iet-bmt.2012.0059. [127] ZHANG R, ISOLA P, EFROS A A, et al. The unreasonable effectiveness of deep features as a perceptual metric[C]. 2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Salt Lake City, USA, 2018: 586–595. doi: 10.1109/CVPR.2018.00068. [128] GOMEZ-BARRERO M, GALBALLY J, RATHGEB C, et al. General framework to evaluate unlinkability in biometric template protection systems[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(6): 1406–1420. doi: 10.1109/TIFS.2017.2788000. [129] HEUSEL M, RAMSAUER H, UNTERTHINER T, et al. GANs trained by a two time-scale update rule converge to a local nash equilibrium[C]. Proceedings of the 31st International Conference on Neural Information Processing Systems, Long Beach, USA, 2017: 6629–6640. [130] ISO. ISO/IEC 24745: 2022 Information security, cybersecurity and privacy protection — biometric information protection[S]. Geneva: ISO, 2022. (查阅网上资料, 未找到本条文献出版地信息, 请确认). -





 下载:
下载:


 下载:
下载:
