Physical Layer Key Generation Method for Integrated Sensing and Communication Systems
-
摘要: 针对通信与感知一体化(ISAC)系统中存在的信息泄露问题,该文提出一种面向ISAC的物理层密钥生成(PLKG)方法。首先,提出一种面向ISAC系统的PLKG协议,并推导了总密钥生成速率(SKGR) 和感知精度克拉美罗界(CRB)的闭式表达式。其次,在感知精度的约束下,建立了一个总密钥生成速率SKGR最大化问题。最后,提出一种基于双延迟深度确定性策略梯度(TD3)的联合通信与感知波束赋形算法,进一步提升系统安全性。仿真结果表明,所提方法相较于基准方法具有更好的有效性和优越性。
-
关键词:
- 通信与感知一体化 /
- 物理层密钥生成 /
- 总密钥生成速率 /
- 克拉美罗界 /
- 双延迟深度确定性策略梯度算法
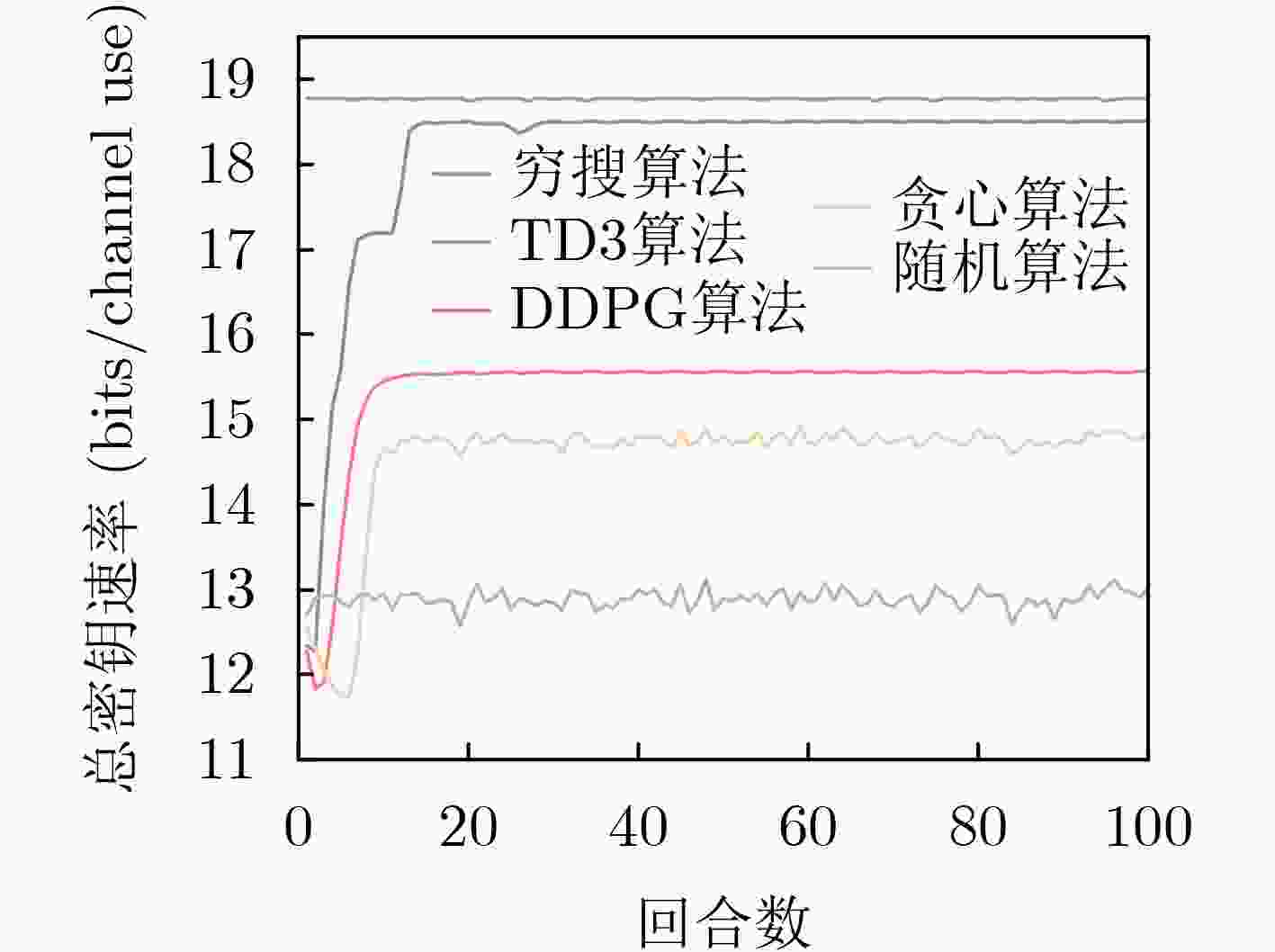
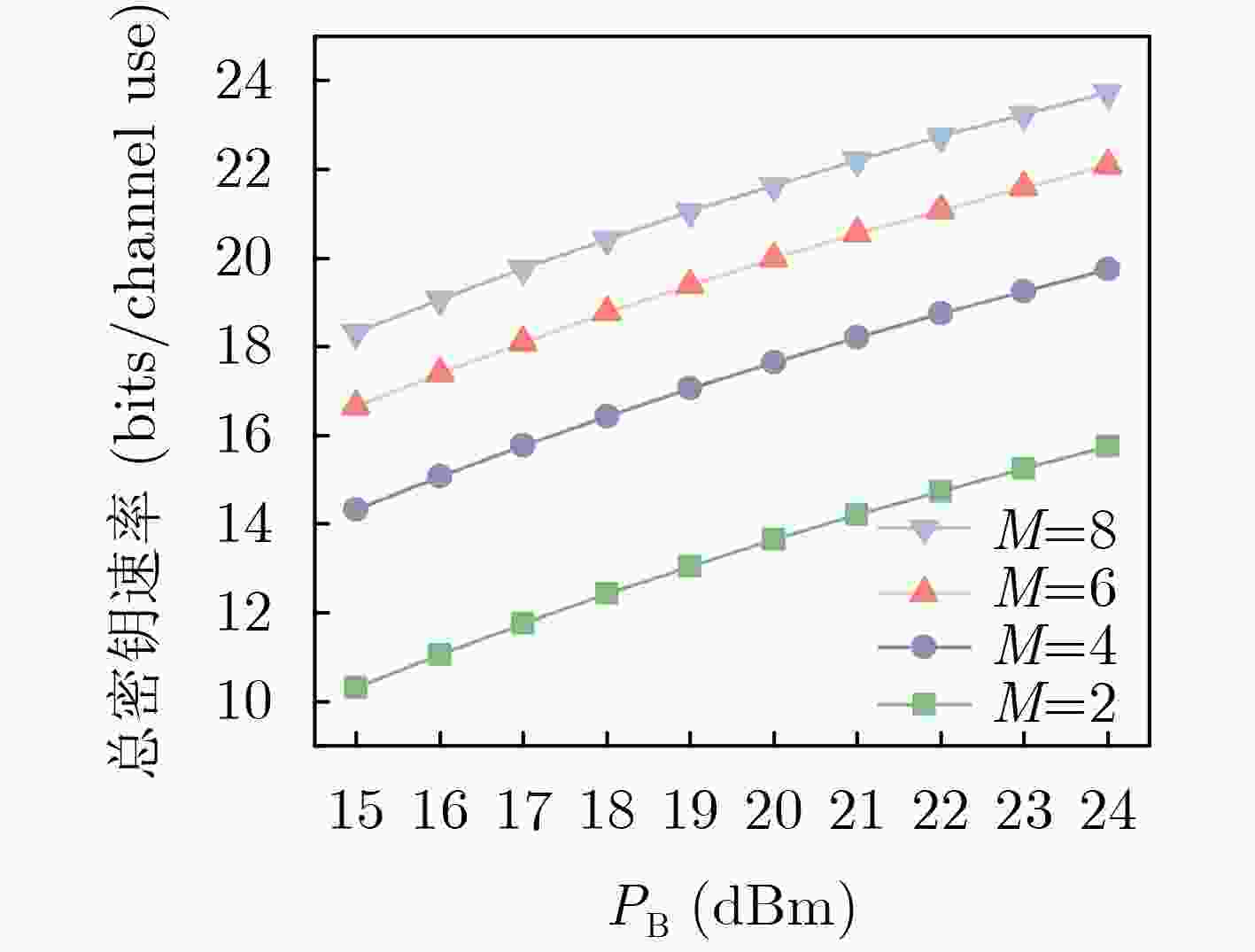
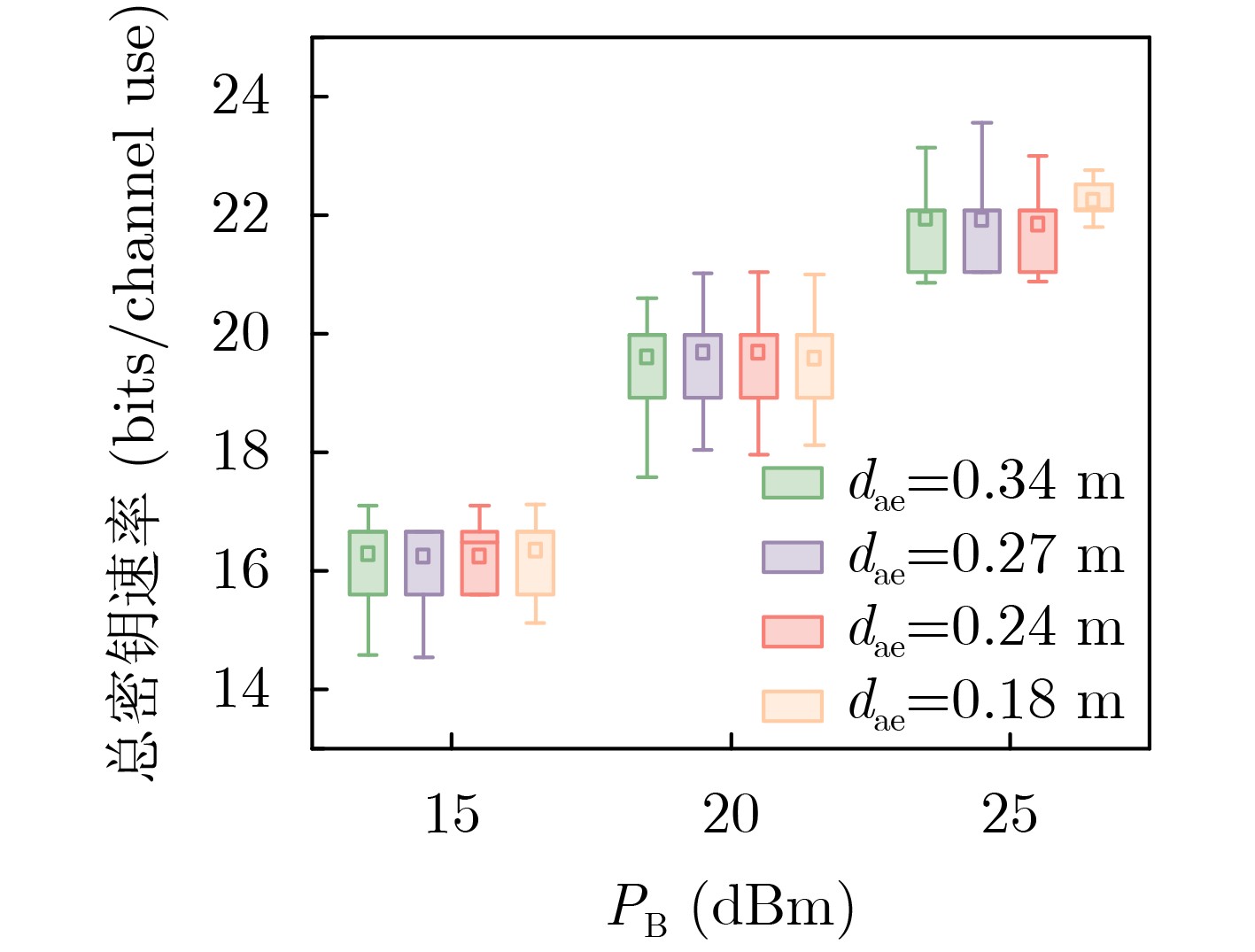
Abstract:Objective Integrated Sensing And Communication (ISAC) has become a central technology in Sixth-Generation (6G) wireless networks, enabling simultaneous data transmission and environmental sensing. However, the characteristics of ISAC systems, including highly directional sensing signals and the risk of sensitive information leakage to malicious sensing targets, create specific security challenges. Physical layer security provides lightweight methods to enhance confidentiality. In secure transmission, approaches such as artificial noise injection and beamforming can partially improve secrecy, although they may reduce sensing accuracy or communication efficiency. Their effect also depends on the quality advantage of legitimate channels over eavesdropping channels. For Physical Layer Key Generation (PLKG), existing work has only demonstrated basic feasibility. Most current schemes adopt a radar-centric design, which limits compatibility with communication protocols and restricts key generation rates. This paper proposes a PLKG method tailored for ISAC systems. It aims to maximize the Sum Key Generation Rate (SKGR) under sensing accuracy constraints through a Twin Delayed Deep Deterministic policy gradient (TD3)-based joint communication and sensing beamforming algorithm, thereby improving the security performance of ISAC systems. Methods A MIMO ISAC system is considered, where a base station (Alice) equipped with multiple antennas communicates with single-antenna users (Bobs) and senses a malicious target (Eve). The system operates under a TDD protocol to leverage channel reciprocity. A PLKG protocol designed for ISAC systems is developed, including channel estimation, joint communication and sensing beamforming, and key generation. The SKGR is derived in closed form, and sensing accuracy is evaluated using the Cramér-Rao Bound (CRB). To maximize the SKGR under CRB constraints, a non-convex optimization problem for the joint design of communication and sensing beamforming matrices is formulated. Given its NP-hardness, an algorithm based on TD3 is proposed. TD3 employs dual critic networks to reduce overestimation, delayed policy updates to enhance stability, and target policy smoothing to improve robustness. The state includes channel state information, the actions correspond to beamforming matrices, and the reward function combines SKGR, CRB, and power constraints. Results and Discussions Simulation results confirm the effectiveness of the proposed design. The TD3-based algorithm achieves a stable SKGR of 18.5 bits/channel use after training ( Fig. 4 ), outperforming benchmark schemes such as Deep Deterministic Policy Gradient (DDPG), greedy search, and random algorithms. The SKGR increases monotonically with transmit power because of reduced noise interference (Fig. 5 ). Increasing the number of antennas also improves SKGR, although the gain diminishes as power per antenna decreases. The scheme maintains stable SKGR across different distances to the eavesdropper (Fig. 6 ), demonstrating the robustness of PLKG against eavesdropping attacks. The proposed algorithm manages the complex optimization problem effectively and adapts to dynamic system conditions, offering a practical approach for secure ISAC systems.Conclusions This paper presents a PLKG method for ISAC systems. The proposed protocol generates consistent keys between the base station and communication users. The SKGR maximization problem with sensing constraints is solved using a TD3-based algorithm that jointly optimizes communication and sensing beamforming matrices. Simulation results show that the method outperforms benchmark schemes, with significant gains in SKGR and adaptability to system conditions. The study establishes a basis for integrating PLKG into ISAC to strengthen security without reducing sensing performance. Future work will examine real-time implementation and scalability in large networks. -
1 基于TD3的RL算法[27]
随机初始化两个评论家网络$ {Q}_{\theta 1} $,$ {Q}_{\theta 2} $和一个演员网络$ {\pi }_{\phi } $的参数 初始化目标网络参数$ \theta _{1}^{\prime}\leftarrow {\theta }_{1}, \theta _{2}^{\prime}\leftarrow {\theta }_{2}, {\phi }^{\prime}\leftarrow \phi $ 初始化经验回放缓冲区$ \mathcal{D} $ for每个时间步$ t=1 $to$ T $: 根据当前策略添加探索噪声选择动作:
$ a\sim {\pi }_{\phi }(s)+\epsilon , \epsilon \sim \mathcal{N}(0,\sigma ) $,并观测奖励$ r $和新状态$ s' $将转移元组$ \left(s,a,r,s'\right) $存入回放缓冲区$ \mathcal{D} $ 从$ \mathcal{D} $中采样$ N $个转移元组的小批量数据 为目标策略的输出添加平滑噪声:
$ \tilde{a}\leftarrow {\pi }_{{{\phi }^{\prime}}}({s}^{\prime})+\epsilon , \epsilon \sim \mathrm{clip}(\mathcal{N}(0,\tilde{\sigma }),-c,c) $计算目标$ Q $值$ y\leftarrow r+\gamma {\min }_{i=1,2}{Q}_{{\theta _{i}^{\prime}}}({s}^{\prime},\tilde{a}) $ 通过最小化均方误差来更新两个评论家网络:
$ {\theta }_{i}\leftarrow {\mathrm{argmin}}_{{{\theta }_{i}}}{N}^{-1}\sum{\left(y-{Q}_{{{\theta }_{i}}}(s,a)\right)}^{2} $if $ t\text{mod}d $(即每$ d $步),则执行以下操作: 通过确定性策略梯度更新演员网络参数: $ {{\text{∇}}}_{\phi }J(\phi )={N}^{-1}\sum{{\text{∇}}}_{a}{Q}_{{{\theta }_{1}}}(s,a){|}_{a={{\pi }_{\phi }}(s)}{{\text{∇}}}_{\phi }{\pi }_{\phi }(s) $ 软更新目标网络参数: $ \theta _{i}^{\prime}\leftarrow \tau {\theta }_{i}+(1-\tau )\theta _{i}^{\prime} $ $ {\phi }^{\prime}\leftarrow \tau \phi +(1-\tau ){\phi }^{\prime} $ End if End for 表 1 开发网络的主要参数设置[27]
参数 数值 学习率 3×10-4 折扣因子 0.99 梯度步数 20 目标策略噪声 0.60 回合数 100 每回合步数 512 -
[1] LIU Fan, CUI Yuanhao, MASOUROS C, et al. Integrated sensing and communications: Toward dual-functional wireless networks for 6G and beyond[J]. IEEE Journal on Selected Areas in Communications, 2022, 40(6): 1728–1767. doi: 10.1109/JSAC.2022.3156632. [2] GHOSH A, WILD T, DU Jinfeng, et al. A unified future: Integrated sensing and communication (ISAC) in 6G[J]. IEEE Journal of Selected Topics in Electromagnetics, Antennas and Propagation, 2025, 1(1): 365–374. doi: 10.1109/JSTEAP.2025.3603540. [3] WEI Zhiqing, QU Hanyang, WANG Yuan, et al. Integrated sensing and communication signals toward 5G-A and 6G: A survey[J]. IEEE Internet of Things Journal, 2023, 10(13): 11068–11092. doi: 10.1109/JIOT.2023.3235618. [4] LU Shihang, LIU Fan, LI Yunxin, et al. Integrated sensing and communications: Recent advances and ten open challenges[J]. IEEE Internet of Things Journal, 2024, 11(11): 19094–19120. doi: 10.1109/JIOT.2024.3361173. [5] 林粤伟, 张奇勋, 尉志青, 等. 通信感知一体化硬件设计——现状与展望[J]. 电子与信息学报, 2025, 47(1): 1–21. doi: 10.11999/JEIT240012.LIN Yuewei, ZHANG Qixun, WEI Zhiqing, et al. Status and prospect of hardware design on integrated sensing and communication[J]. Journal of Electronics & Information Technology, 2025, 47(1): 1–21. doi: 10.11999/JEIT240012. [6] OSORIO D P M, BARUA B, BESSER K L, et al. The rise of networked ISAC: Emerging aspects and challenges[J]. IEEE Open Journal of the Communications Society, 2025, 6: 5072–5091. doi: 10.1109/OJCOMS.2025.3575729. [7] QU Kaiqian, YE Jia, LI Xuran, et al. Privacy and security in ubiquitous integrated sensing and communication: Threats, challenges and future directions[J]. IEEE Internet of Things Magazine, 2024, 7(4): 52–58. doi: 10.1109/IOTM.001.2300180. [8] MELKI R, NOURA H N, MANSOUR M M, et al. A survey on OFDM physical layer security[J]. Physical Communication, 2019, 32: 1–30. doi: 10.1016/j.phycom.2018.10.008. [9] MATSUMINE T, OCHIAI H, and SHIKATA J. Physical layer security for integrated sensing and communication: A survey[J]. IEEE Open Journal of the Communications Society, 2025, 6: 6690–6743. doi: 10.1109/OJCOMS.2025.3598312. [10] KIHERO A B, FURQAN H M, SAHIN M M, et al. 6G and beyond wireless channel characteristics for physical layer security: Opportunities and challenges[J]. IEEE Wireless Communications, 2024, 31(3): 295–301. doi: 10.1109/MWC.002.2300002. [11] ILLI E, QARAQE M, ALTHUNIBAT S, et al. Physical layer security for authentication, confidentiality, and malicious node detection: A paradigm shift in securing IoT networks[J]. IEEE Communications Surveys & Tutorials, 2024, 26(1): 347–388. doi: 10.1109/COMST.2023.3327327. [12] ZHANG Wei, CHEN Jian, KUO Yonghong, et al. Artificial-noise-aided optimal beamforming in layered physical layer security[J]. IEEE Communications Letters, 2019, 23(1): 72–75. doi: 10.1109/LCOMM.2018.2881182. [13] LIU Peng, FEI Zesong, WANG Xinyi, et al. Outage constrained robust secure beamforming in integrated sensing and communication systems[J]. IEEE Wireless Communications Letters, 2022, 11(11): 2260–2264. doi: 10.1109/LWC.2022.3198683. [14] SU Nanchi, LIU Fan, and MASOUROS C. Sensing-assisted eavesdropper estimation: An ISAC breakthrough in physical layer security[J]. IEEE Transactions on Wireless Communications, 2024, 23(4): 3162–3174. doi: 10.1109/TWC.2023.3306029. [15] LIU Yuemin, LIU Xin, LIU Zechen, et al. Secure rate maximization for ISAC-UAV assisted communication amidst multiple eavesdroppers[J]. IEEE Transactions on Vehicular Technology, 2024, 73(10): 15843–15847. doi: 10.1109/TVT.2024.3412805. [16] YE Chunxuan, MATHUR S, REZNIK A, et al. Information-theoretically secret key generation for fading wireless channels[J]. IEEE Transactions on Information Forensics and Security, 2010, 5(2): 240–254. doi: 10.1109/TIFS.2010.2043187. [17] CHEN Chan and JENSEN M A. Secret key establishment using temporally and spatially correlated wireless channel coefficients[J]. IEEE Transactions on Mobile Computing, 2011, 10(2): 205–215. doi: 10.1109/TMC.2010.114. [18] JORSWIECK E A, WOLF A, and ENGELMANN S. Secret key generation from reciprocal spatially correlated MIMO channels[C]. 2013 IEEE Globecom Workshops (GC Wkshps), Atlanta, USA, 2013: 1245–1250. doi: 10.1109/GLOCOMW.2013.6825164. [19] ZHANG Junqing, MARSHALL A, WOODS R, et al. Efficient key generation by exploiting randomness from channel responses of individual OFDM subcarriers[J]. IEEE Transactions on Communications, 2016, 64(6): 2578–2588. doi: 10.1109/TCOMM.2016.2552165. [20] DWIVEDI S, ZOLI M, BARRETO A N, et al. Secure joint communications and sensing using chirp modulation[C]. 2020 2nd 6G Wireless Summit (6G SUMMIT). Levi, Finland, 2020: 1–5. doi: 10.1109/6GSUMMIT49458.2020.9083884. [21] MITEV M, MAYYA A, and CHORTI A. Joint secure communication and sensing in 6G networks[M]. MOHAPATRA P, PAPPAS N, CHORTI A, et al. Physical-layer Security for 6G. Electrical and Electronics Engineers, Inc. , 2024: 203–220. doi: 10.1002/9781394170944.ch10. [22] REN Zixiang, ZHANG Siyao, LI Xinmin, et al. Secure communications in near-field ISCAP systems with extremely large-scale antenna arrays[C]. 2024 19th International Symposium on Wireless Communication Systems (ISWCS), Rio de Janeiro, Brazil, 2024: 1–6. doi: 10.1109/ISWCS61526.2024.10639091. [23] PHAN A H, TUAN H D, KHA H H, et al. Nonsmooth optimization for efficient beamforming in cognitive radio multicast transmission[J]. IEEE Transactions on Signal Processing, 2012, 60(6): 2941–2951. doi: 10.1109/TSP.2012.2189857. [24] WU Huici, FANG Yi, LI Na, et al. Secret key generation with untrusted internal eavesdropper: Token-based anti-eavesdropping[J]. IEEE Transactions on Information Forensics and Security, 2025, 20: 2523–2537. doi: 10.1109/TIFS.2025.3542959. [25] QIN Dongrun and DING Zhi. Exploiting multi-antenna non-reciprocal channels for shared secret key generation[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(12): 2693–2705. doi: 10.1109/TIFS.2016.2594143. [26] QU Guanjin, WU Huaming, LI Ruidong, et al. DMRO: A deep meta reinforcement learning-based task offloading framework for edge-cloud computing[J]. IEEE Transactions on Network and Service Management, 2021, 18(3): 3448–3459. doi: 10.1109/TNSM.2021.3087258. [27] FUJIMOTO S, HOOF H, and MEGER D. Addressing function approximation error in actor-critic methods[C]. The 35th International Conference on Machine Learning, Stockholm, Sweden, 2018: 1587–1596. -





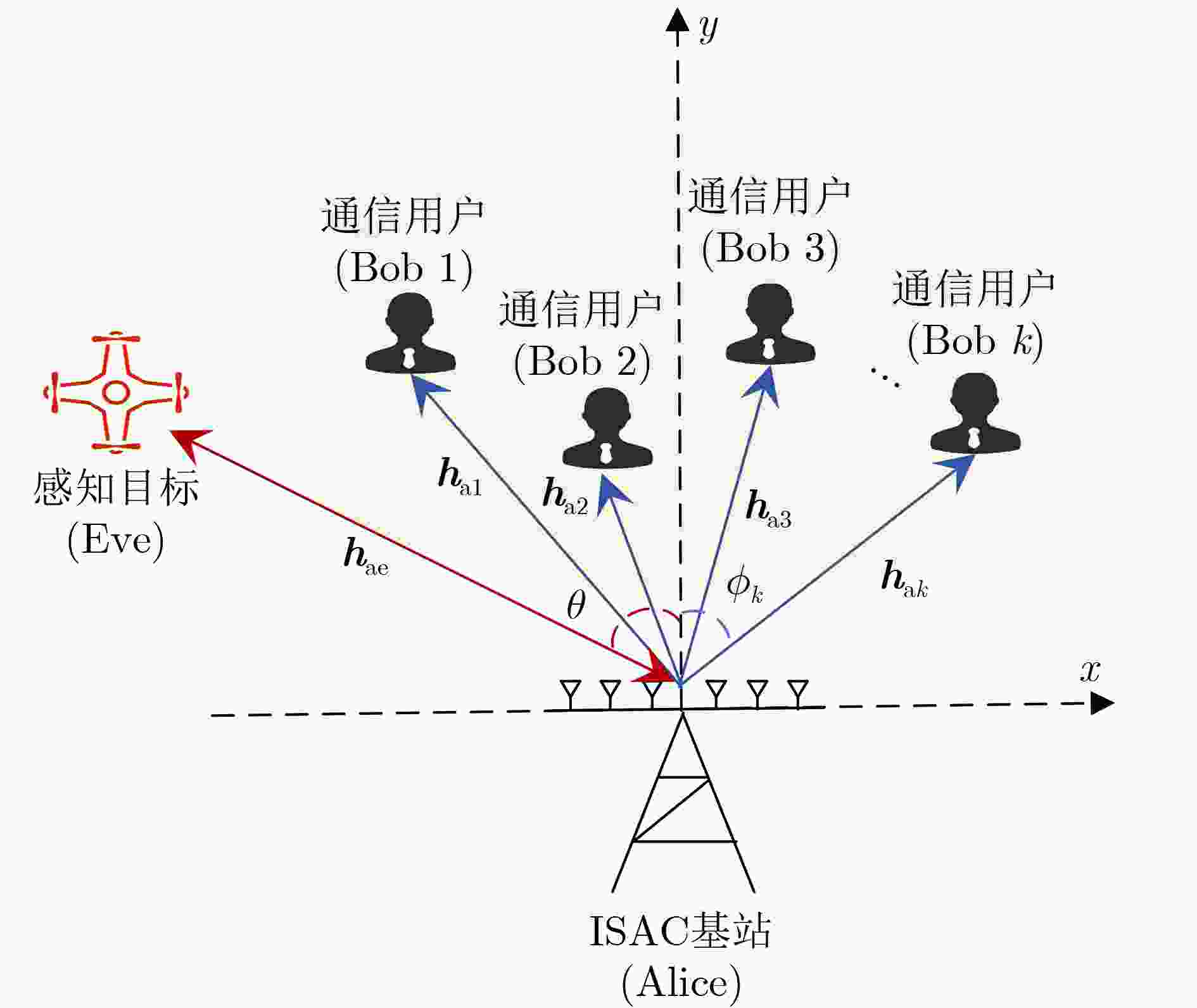
 下载:
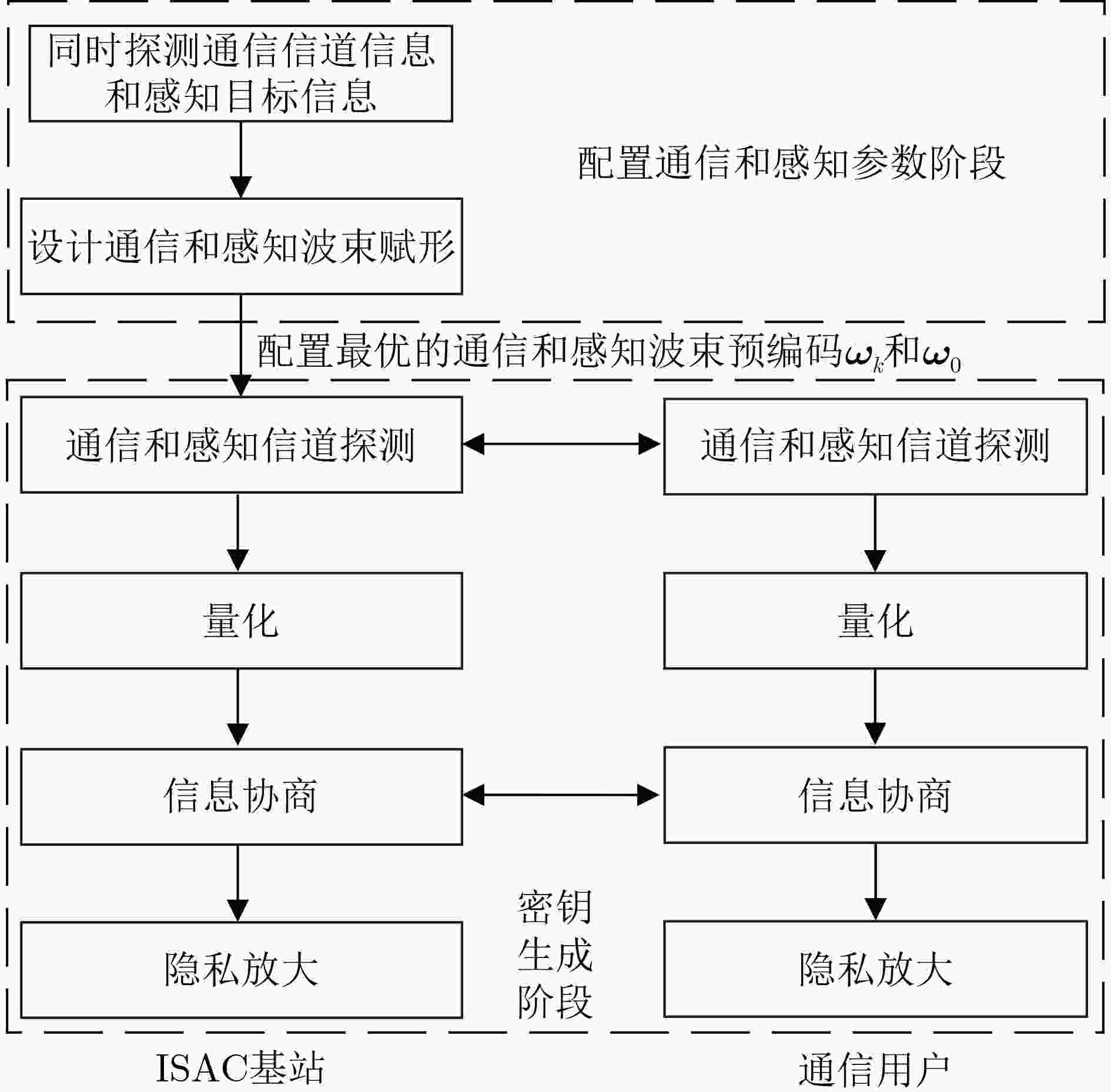
下载:
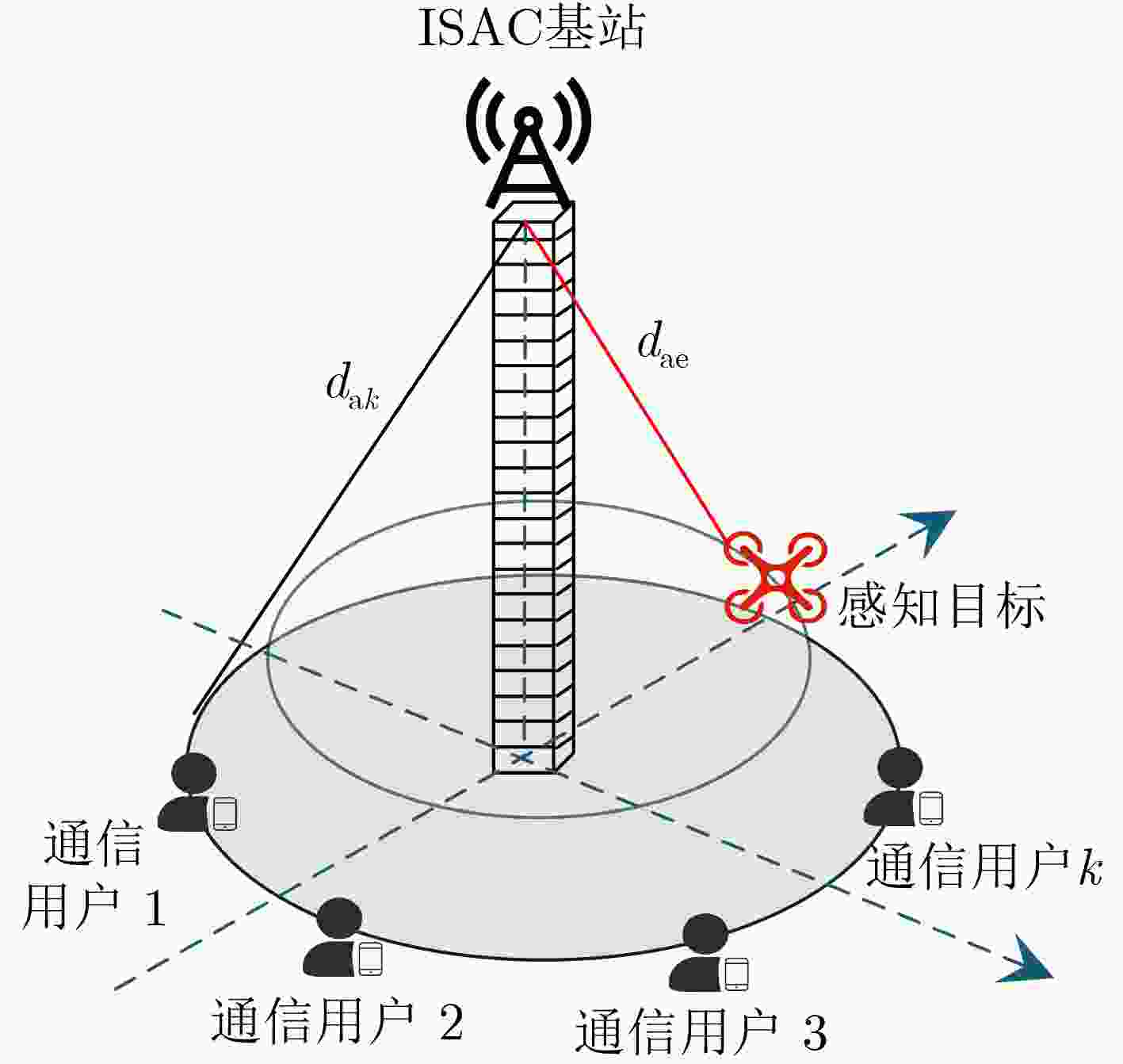


 下载:
下载:
