Key Technologies for Low-Altitude Internet Networks: Architecture, Security, and Optimization
-
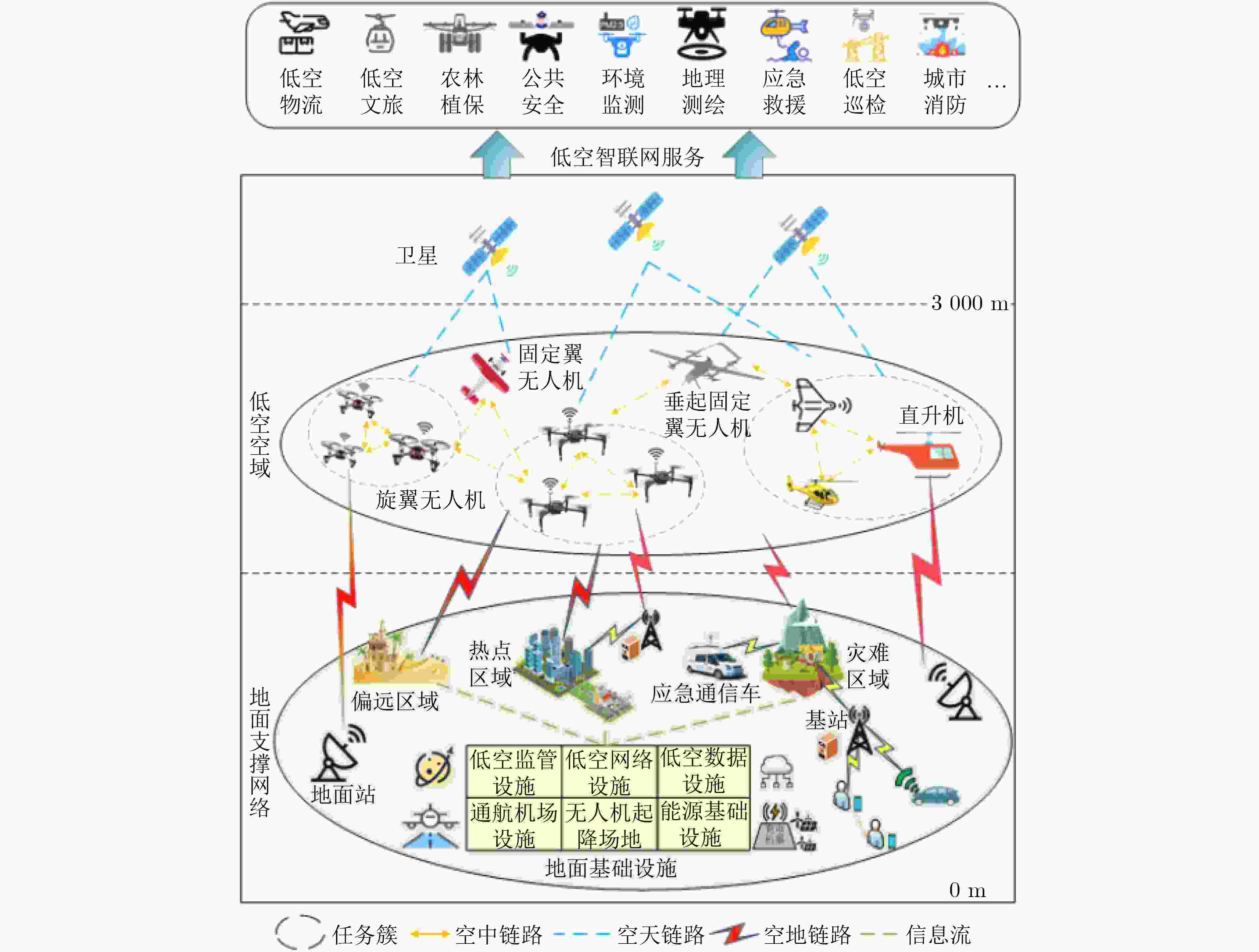
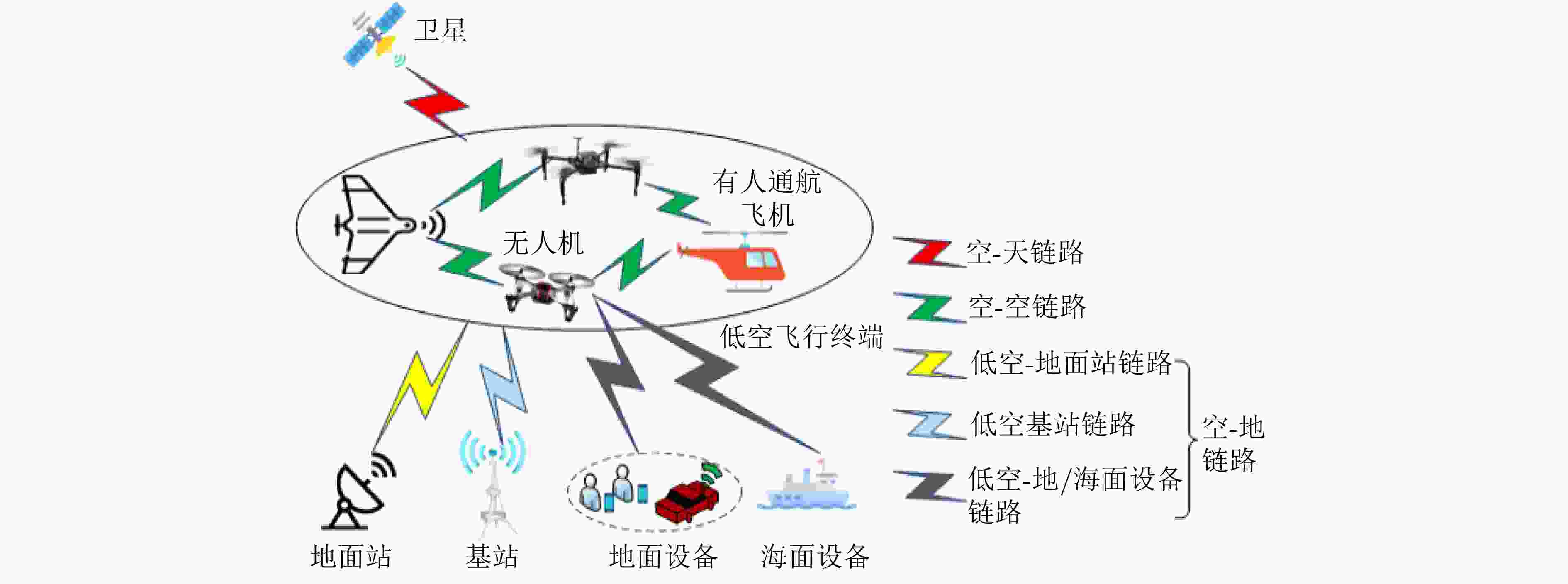
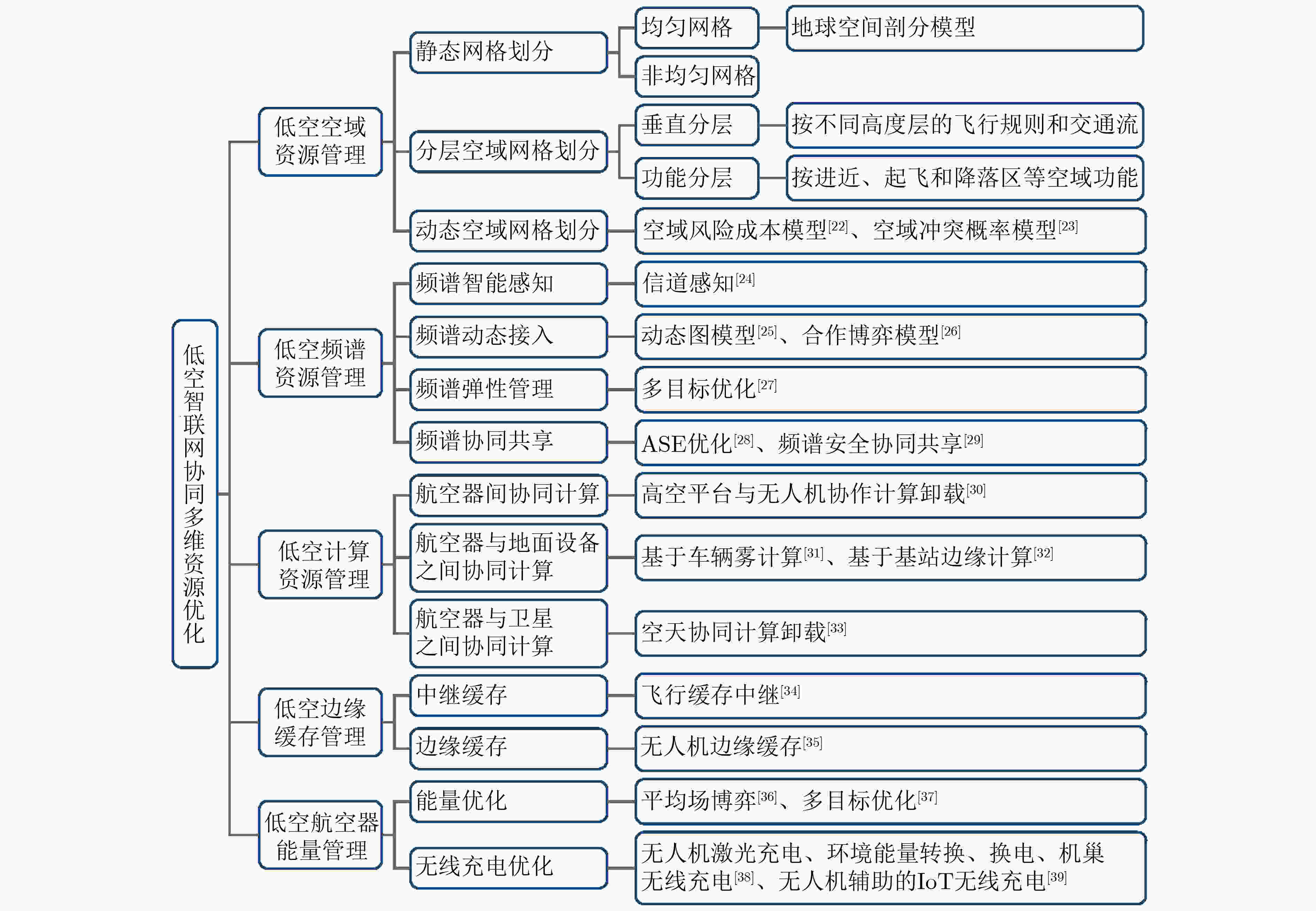
摘要: 低空智联网作为低空数字经济的关键基础设施,通过深度融合各类有人/无人航空器及其地面支撑网络,构建了低空空域人-机-物三元融合的智能互联体系。该文系统梳理了低空智联网的最新研究进展,从网络架构、资源优化、安全威胁与防护以及大模型赋能四个维度展开深入分析。首先,探讨了低空智联网的现有标准、组成架构、关键特性及组网模式;其次,研究了空域资源管理、频谱资源分配、计算资源调度和能量资源优化等关键问题;再次,从感知层、网络层、应用层和系统层剖析了核心安全威胁并综述了多层次防护策略;接着,探讨了大模型技术在低空智联网的应用前景,并分析了其在任务优化与安全防护中的潜力;最后,讨论了低空智联网的未来研究方向,为构建高效、安全、智能的低空智联网体系提供了理论参考和技术指导。Abstract:
Low-Altitude Intelligent Networks (LAINs) function as a core infrastructure for the emerging low-altitude digital economy by connecting humans, machines, and physical objects through the integration of manned and unmanned aircraft with ground networks and facilities. This paper provides a comprehensive review of recent research on LAINs from four perspectives: network architecture, resource optimization, security threats and protection, and large model-enabled applications. First, existing standards, general architecture, key characteristics, and networking modes of LAINs are investigated. Second, critical issues related to airspace resource management, spectrum allocation, computing resource scheduling, and energy optimization are discussed. Third, existing/emerging security threats across sensing, network, application, and system layers are assessed, and multi-layer defense strategies in LAINs are reviewed. Furthermore, the integration of large model technologies with LAINs is also analyzed, highlighting their potential in task optimization and security enhancement. Future research directions are discussed to provide theoretical foundations and technical guidance for the development of efficient, secure, and intelligent LAINs. Significance LAINs support the low-altitude economy by enabling the integration of manned and unmanned aircraft with ground communication, computing, and control networks. By providing real-time connectivity and collaborative intelligence across heterogeneous platforms, LAINs support applications such as precision agriculture, public safety, low-altitude logistics, and emergency response. However, LAINs continue to face challenges created by dynamic airspace conditions, heterogeneous platforms, and strict real-time operational requirements. The development of large models also presents opportunities for intelligent resource coordination, proactive defense, and adaptive network management, which signals a shift in the design and operation of low-altitude networks. Progress Recent studies on LAINs have reported progress in network architecture, resource optimization, security protection, and large model integration. Architecturally, hierarchical and modular designs are proposed to integrate sensing, communication, and computing resources across air, ground, and satellite networks, which enables scalable and interoperable operations. In system optimization research, attention is given to airspace resource management, spectrum allocation, computing offloading, and energy-efficient scheduling through distributed optimization and AI-driven orchestration methods. In security research, multi-layer defense frameworks are developed to address sensing-layer spoofing, network-layer intrusions, and application-layer attacks through cross-layer threat intelligence and proactive defense mechanisms. Large Language Models (LLMs), Vision-Language Models (VLMs), and Multimodal LLMs (MLLMs) also support intelligent task planning, anomaly detection, and autonomous decision-making in complex low-altitude environments, which enhances the resilience and operational efficiency of LAINs. Conclusions This survey provides a comprehensive review of the architecture, security mechanisms, optimization techniques, and large model applications in LAINs. The challenges in multi-dimensional resource coordination, cross-layer security protection, and real-time system adaptation are identified, and existing or potential approaches to address these challenges are analyzed. By synthesizing recent research on architectural design, system optimization, and security defense, this work offers a unified perspective for researchers and practitioners aiming to build secure, efficient, and scalable LAIN systems. The findings emphasize the need for integrated solutions that combine algorithmic intelligence, system engineering, and architectural innovation to meet future low-altitude network demands. Prospects Future research on LAINs is expected to advance the integration of architecture design, intelligent optimization, security defense, and privacy preservation technologies to meet the demands of rapidly evolving low-altitude ecosystems. Key directions include developing knowledge-driven architectures for cross-domain semantic fusion, service-oriented network slicing, and distributed autonomous decision-making. Furthermore, research should also focus on proactive cross-layer security mechanisms supported by large models and intelligent agents, efficient model deployment through AI-hardware co-design and hierarchical computing architectures, and improved multimodal perception and adaptive decision-making to strengthen system resilience and scalability. In addition, establishing standardized benchmarks, open-source frameworks, and realistic testbeds is essential to accelerate innovation and ensure secure, reliable, and intelligent deployment of LAIN systems in real-world environments. -
表 1 低空飞行终端类别与功能
分类 占比 常见细分类飞行器 典型机型 主要用途 有人 绝对少数
(千级)固定翼通航飞机 赛斯纳172、钻石DA40、运-12 航测测绘、飞行培训、短途客运 直升机 罗宾逊 R44、贝尔206、直-20 应急救援、医疗转运、城市巡逻 运动/娱乐类航空器 滑翔机、动力伞、热气球 航空运动、旅游观光、科普教育 无人 绝对多数(百万级) 多旋翼无人机 大疆 M300、Matrice 300 RTK 植保、低空物流、电力巡检、航拍 固定翼无人机 翼龙-2、TB-001 测绘、环境监测、边境巡逻 无人直升机 AV500W、铂影T1400 应急通信、森林防火、物资投送 电动垂直起降机(eVTOL)
模型航空器Volocopter、亿航EH216遥控滑翔机、
四旋翼模型城市空中出行、低空载人运输科研测试、
青少年培训表 2 低空智联网标准进展情况
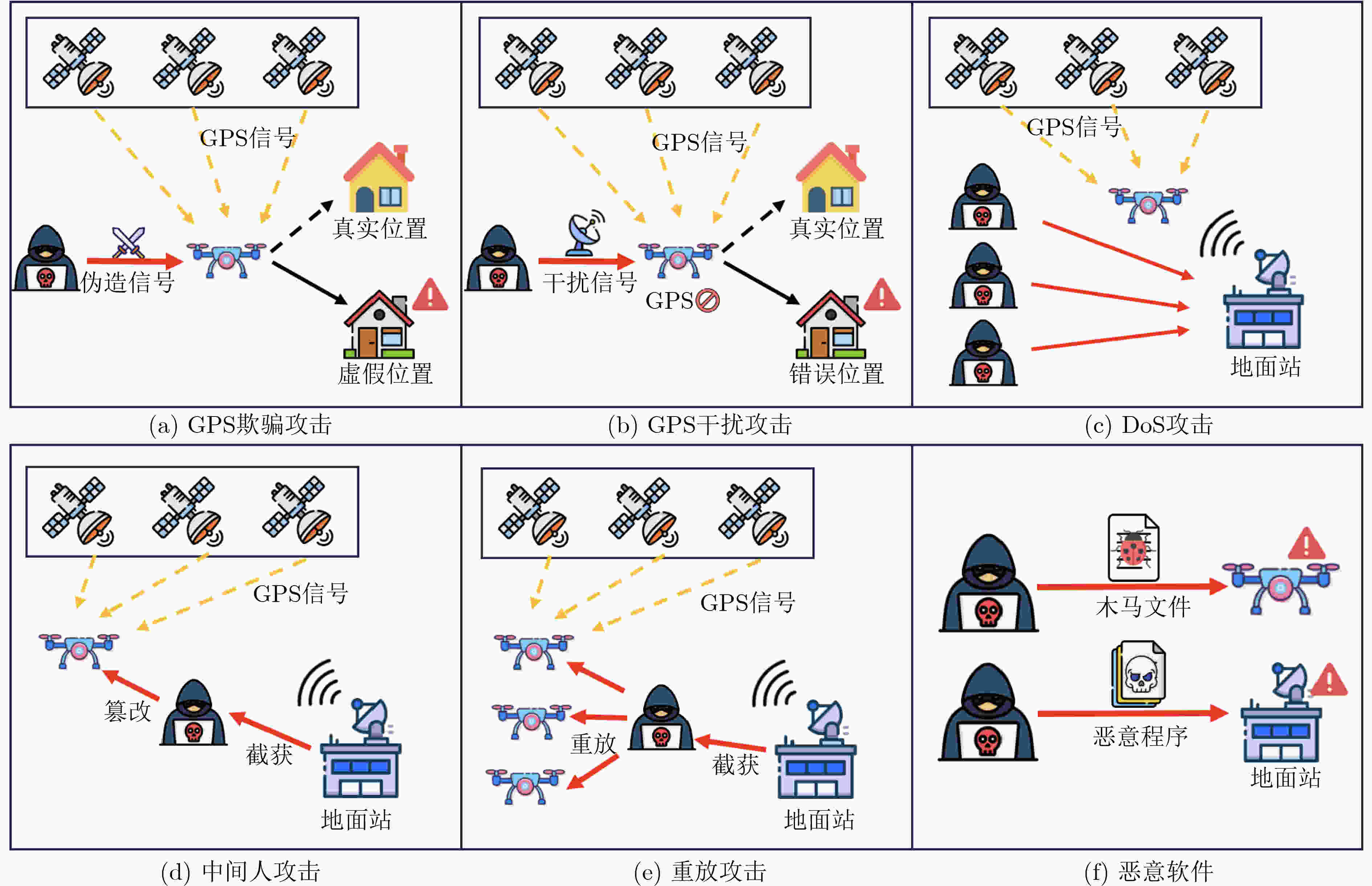
标准组织 标准编号 主要研究内容 ISO ISO/TR 23629 -1:2020联合国际民航组织等机构调查并分析了UTM标准化主题及未来趋势 ISO 23629 -7:2021制定了UAS服务提供商和运行控制系统之间空间信息的通用数据模型 ISO 23629 -12:2022研究了UTM场景下供应商合规监控、安全、安保、隐私等方面的指标和功能要求 ISO 23629 -8:2023定义了UAS远程识别的通用框架,设定了电子方式直接远程识别无人机的最低性能 ISO 23629 -9:2023研究了UTM服务提供商和不同用户之间为支持UTM服务进行的信息交换要素 ISO 23629 -5:2023确立了UTM核心功能和功能结构定义,并详细描述了UTM框架中的系统层面 IEEE IEEE 1939.1 -2021定义了用于有效管理无人机运行交通的低空空域结构 表 3 低空智联网安全威胁及其机理、攻击对象和影响
层级 威胁类型 攻击机理/要点 文献编号 目标对象 主要影响 感知层 GPS欺骗 伪造同步信号,渐进接管/覆盖式接管等 [41–46] UAV导航接收机 定位偏移、航迹劫持 干扰(Jamming/ IEMI/频扫) 恒定/随机/反应式干扰;IEMI篡改PWM/总线 [44,49–53] GNSS/通信链路、执行器 失锁、链路中断、姿态失稳/坠毁 声学/IMU注入 共振/声学注入破坏MEMS输出 [50,51] IMU/飞控 姿态漂移、控制环不稳 侧信道(EM/RF/Acoustic) 被动测量功耗/EM/RF特征
做识别情报[40,54–57] UAV/基站/
边缘节点型号识别、载荷推断、轨迹外泄 硬件木马 触发逻辑+负载,
条件触发篡改/泄露[58–61] 飞控/SoC/外设 永久后门、功能退化 网络层 DoS/洪泛/L7放大 去认证, ICMP/UDP/TCP flood; HTTP/2 Rapid Reset, CONTINUATION; DNSSEC/KeyTrap, DNSBomb CVE-2023- 44487 , CVE-2024-30255 , CVE-2023-50387 , [40,62–67]Wi-Fi/网关/DNS/应用网关/基站 拥塞、帧率下降、控制失效 认证绕过 Blast-RADIUS: MD5选择前缀碰撞, Reject→Accept [68] 接入网/地面站 未授权接入、接管 虫洞攻击 截获-高速隧穿-伪近路诱导路由 [69,70] 多跳UAV网 路由失真、时延异常 中间人攻击 监听/篡改/指令注入;
明文/弱加密[71–73] UAV$\leftrightarrow $地面
控制站链路接管、数据篡改 黑洞攻击 伪最优路由吸流并丢弃 [74,75] 路由层 投递率下降、鲁棒性劣化 重放攻击 复用合法消息破坏新鲜性 / 指令/遥测/同步 误动作、时序混乱 应用层 恶意软件/漏洞利用 广播/协议缺陷、模糊测试触发崩溃/绕过 [48,76,77] 飞控应用/地面站 RCE、崩溃、数据泄露 后门/供应链 更新链植入、持久化控制 [78,79] UAV 固件/模块 长期隐蔽控制 系统层 系统入侵/提权 缓冲区溢出、代码注入、提权 [80] OS/服务 远程接管、破坏任务 固件与更新链缺陷 PX4解析漏洞;签名绕过/
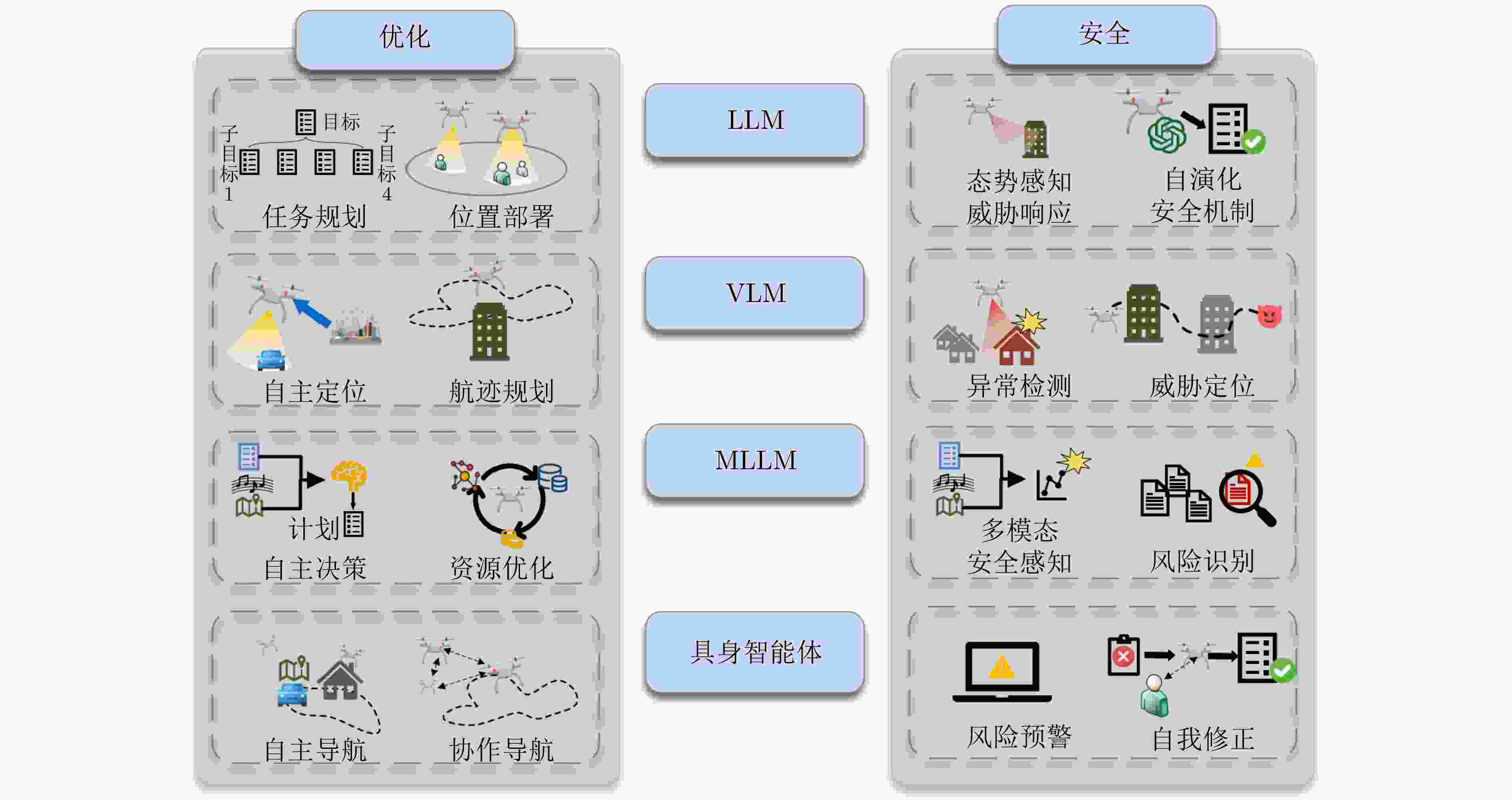
未授权补丁CVE-2023- 46256 , CVE-2023-47625 , CVE-2025-5640 , [76]PX4/固件链 崩溃、任意代码执行、持久化 表 4 大模型赋能低空智联网优化研究现状
大模型
类型研究方法 主要贡献 优势 不足 文献
编号LLM 自然语言指令,
代码生成提出TPML系统,实现基于LLM的任务规划 规划效率高,适应性强 指令理解要求高 [89] 结构化提示,
迭代优化提出LLM驱动的多无人机部署优化方法 快速收敛,计算时间减少 适应性不足 [90] VLM 视图文本描述生成 提出基于VLM的无人机跨视图地理定位方法 语义理解能力强 训练推理复杂,
资源消耗大[91] 文本描述生成,
特征融合提出UAV-VLA系统,实现基于文本请求的飞行路径
和行动计划生成飞行计划效率高,
准确性好卫星图像依赖度高 [92] MLLM 指令微调,提示微调 提出AirVista框架,提升UAV的3D空间感知和任务分解能力 自主性强,
任务执行效率高3D空间知识有限,
适应性待提升[93] LoRA微调,
少样本学习提出云边协同的ADAS架构,优化服务延迟、
能耗和QoS任务成功率高 系统复杂,依赖大
规模数据[94] 具身
智能体细粒度空间描述,
记忆检索提出城市级视觉语言导航的空中智能体,
增强空间感知和自主导航能力能够处理模糊指令 通信带宽限制,
策略学习复杂[95] 语义映射,通信机制 提出分层决策的多智能体协同导航框架 复杂任务成功率高,
适应性强依赖高质量数据,
模型训练成本高[96] 表 5 大模型赋能低空智联网安全研究现状
大模型
类型研究方法 主要贡献 优势 不足 文献
编号LLM 特征提取,态势感知 提出SAG-Attack和LLM-SA,增强零信任SAGIN安全 适应性强,可学习性高,协同性好 计算资源高,
推理时间长[97] 链式推理,策略生成 提出空天地一体化网络自进化安全框架,处理多维威胁信息并自适应更新 适应性强,策略准确 实时性不足,计算资源需求高 [98] VLM 数据分析,分类数据集成 提出集成分类数据提升VLM性能,有望结合空间信息用于异常检测 数据驱动性能提升 验证范围有限,数据类型依赖性强 [99] 指令微调,提示微调 提出无人机自主飞行的AirVista框架,有望对潜在威胁目标定位 空间感知能力强 数据与计算需求大 [100] MLLM 指令微调,数据集构建 提出EarthGPT,对多种遥感任务和多传感器图像的统一处理,有望实现多模态安全感知 泛化能力强 资源消耗大 [101] 数据集构建,多轮处理 提出VisCoT,实现输入的动态聚焦和可解释推理,有望实现风险识别 具有可解释性 依赖于数据集质量 [102] 具身
智能体特征融合,条件嵌入 提出FGPrompt方法,实现对目标相关区域的精准定位和注意力引导,有望实现风险预警 模型轻量化,
识别精确率高泛化能力不足 [103] 多模态分层强化学习 提出AVLEN框架,实现音频-视觉导航与自然语言指令的结合,可实现自我修正 成功率高,交互性强 模型依赖性强 [104] -
[1] 董超, 经宇骞, 屈毓锛, 等. 面向低空智联网频谱认知与决策的云边端融合体系架构[J]. 通信学报, 2023, 44(11): 1–12. doi: 10.11959/j.issn.1000-436x.2023228.DONG Chao, JING Yuqian, QU Yuben, et al. Cloud-edge-device fusion architecture oriented to spectrum cognition and decision in low altitude intelligence network[J]. Journal on Communications, 2023, 44(11): 1–12. doi: 10.11959/j.issn.1000-436x.2023228. [2] 新华社. 中央经济工作会议在北京举行 习近平发表重要讲话[EB/OL]. https://www.gov.cn/yaowen/liebiao/202312/content_6919834.htm, 2023. [3] SHAKERI R, AL-GARADI M A, BADAWY A, et al. Design challenges of multi-UAV systems in cyber-physical applications: A comprehensive survey and future directions[J]. IEEE Communications Surveys & Tutorials, 2019, 21(4): 3340–3385. doi: 10.1109/COMST.2019.2924143. [4] 董超, 崔灿, 贾子晔, 等. 面向低空智联网的多维信息统一表征技术综述[J]. 电子与信息学报, 2025, 47(5): 1215–1229. doi: 10.11999/JEIT240835.DONG Chao, CUI Can, JIA Ziye, et al. Survey of unified representation technology of multi-dimensional information for low altitude intelligent network[J]. Journal of Electronics & Information Technology, 2025, 47(5): 1215–1229. doi: 10.11999/JEIT240835. [5] CAI Lingyi, WANG Jiacheng, ZHANG Ruichen, et al. Secure physical layer communications for low-altitude economy networking: A survey[J]. arXiv preprint arXiv: 2504.09153, 2025. doi: 10.48550/arXiv.2504.09153. [6] WANG Zhaoxuan, LI Yang, WU Shihao, et al. A survey on cybersecurity attacks and defenses for unmanned aerial systems[J]. Journal of Systems Architecture, 2023, 138: 102870. doi: 10.1016/j.sysarc.2023.102870. [7] KHAWAJA W, EZUMA M, SEMKIN V, et al. A survey on detection, classification, and tracking of UAVs using radar and communications systems[J]. IEEE Communications Surveys & Tutorials, 2025: 1–44. doi: 10.1109/COMST.2025.3554613. [8] LI Xiao, DING Xue, XIE Weiliang, et al. Low-altitude sensing model: Analysis leveraging ISAC in real-world environments[J]. Drones, 2025, 9(4): 283. doi: 10.3390/drones9040283. [9] SABUJ S R, ALAM M S, HAIDER M, et al. Low altitude satellite constellation for futuristic aerial-ground communications[J]. Computer Modeling in Engineering & Sciences, 2023, 136(2): 1053–1089. doi: 10.32604/cmes.2023.024078. [10] BUTT M Z, NASIR N, and RASHID R B A. A review of perception sensors, techniques, and hardware architectures for autonomous low-altitude UAVs in non-cooperative local obstacle avoidance[J]. Robotics and Autonomous Systems, 2024, 173: 104629. doi: 10.1016/j.robot.2024.104629. [11] 樊邦奎, 李云, 张瑞雨. 浅析低空智联网与无人机产业应用[J]. 地理科学进展, 2021, 40(9): 1441–1450. doi: 10.18306/dlkxjz.2021.09.001.FAN Bangkui, LI Yun, and ZHANG Ruiyu. Initial analysis of low-altitude internet of intelligences (IOI) and the applications of unmanned aerial vehicle industry[J]. Progress in Geography, 2021, 40(9): 1441–1450. doi: 10.18306/dlkxjz.2021.09.001. [12] 中国民航网. 2023年中国通用航空盘点[EB/OL]. http://www.caacnews.com.cn/1/tbtj_/202401/t20240124_1374164.html, 2024. [13] ISO. ISO/TR 23629-1: 2020 UAS Traffic Management (UTM) Part 1: Survey results on UTM[S]. Geneva: ISO, 2020. [14] ISO. ISO 23629-7: 2021 UAS traffic management (UTM) Part 7: Data model for spatial data[S]. Geneva: ISO, 2021. [15] ISO. ISO 23629-12: 2022 UAS Traffic Management (UTM) Part 12: Requirements for UTM service providers[S]. Geneva: ISO, 2022. [16] ISO. ISO 23629-8: 2023 UAS Traffic Management (UTM) Part 8: Remote identification[S]. Geneva: ISO, 2023. [17] ISO. ISO 23629-9: 2023 UAS Traffic Management (UTM) Part 9: Interface between UTM service providers and users[S]. Geneva: ISO, 2023. [18] ISO. ISO 23629-5: 2023 UAS Traffic Management (UTM) Part 5: UTM functional structure[S]. Geneva: ISO, 2023. [19] IEEE. IEEE Std 1939.1-2021 IEEE Standard for a framework for structuring low-altitude airspace for Unmanned Aerial Vehicle (UAV) operations[S]. New York: IEEE, 2021. doi: 10.1109/IEEESTD.2021.9631203. [20] 中国民航局. 低空联网无人机安全飞行测试报告[EB/OL]. http://www.caac.gov.cn/XXGK/XXGK/GFXWJ/201811/t20181127_193186.html, 2018. [21] 尹浩, 魏急波, 赵海涛, 等. 面向有人/无人协同的智能通信与组网关键技术: 现状与趋势[J]. 通信学报, 2024, 45(1): 1–17. doi: 10.11959/j.issn.1000-436x.2024037.YIN Hao, WEI Jibo, ZHAO Haitao, et al. Intelligent communication and networking key technologies for manned/unmanned cooperation: States-of-the-art and trends[J]. Journal on Communications, 2024, 45(1): 1–17. doi: 10.11959/j.issn.1000-436x.2024037. [22] PANG Bizhao, DAI Wei, RA T, et al. A concept of airspace configuration and operational rules for UAS in current airspace[C]. 2020 AIAA/IEEE 39th Digital Avionics Systems Conference (DASC), San Antonio, USA, 2020: 1–9. doi: 10.1109/DASC50938.2020.9256627. [23] XIANG Jinwu, LIU Yang, and LUO Zhangping. Flight safety measurements of UAVs in congested airspace[J]. Chinese Journal of Aeronautics, 2016, 29(5): 1355–1366. doi: 10.1016/j.cja.2016.08.017. [24] REUS-MUNS G, DIDDI M, SINGHAL C, et al. Flying among stars: Jamming-resilient channel selection for UAVs through aerial constellations[J]. IEEE Transactions on Mobile Computing, 2023, 22(3): 1246–1262. doi: 10.1109/TMC.2021.3102883. [25] WANG Bowen, SUN Yanjing, ZHAO Nan, et al. Learn to coloring: Fast response to perturbation in UAV-assisted disaster relief networks[J]. IEEE Transactions on Vehicular Technology, 2020, 69(3): 3505–3509. doi: 10.1109/TVT.2020.2967124. [26] CHEN Jiaxin, WU Qihui, XU Yuhua, et al. Spectrum allocation for task-driven UAV communication networks exploiting game theory[J]. IEEE Wireless Communications, 2021, 28(4): 174–181. doi: 10.1109/MWC.001.2000444. [27] WU Jiehong, ZHOU Jianzhou, YU Lei, et al. MAC optimization protocol for cooperative UAV based on dual perception of energy consumption and channel gain[J]. IEEE Transactions on Mobile Computing, 2024, 23(10): 9851–9862. doi: 10.1109/TMC.2024.3372253. [28] SHANG Bodong, LIU Lingjia, RAO R M, et al. 3D spectrum sharing for hybrid D2D and UAV networks[J]. IEEE Transactions on Communications, 2020, 68(9): 5375–5389. doi: 10.1109/TCOMM.2020.2997957. [29] 王云涛, 苏洲, 许其超, 等. 基于审计博弈的安全协作频谱感知方案[J]. 通信学报, 2023, 44(12): 1–14. doi: 10.11959/j.issn.1000-436x.2023238.WANG Yuntao, SU Zhou, XU Qichao, et al. Secure and collaborative spectrum sensing scheme based on audit game[J]. Journal on Communications, 2023, 44(12): 1–14. doi: 10.11959/j.issn.1000-436x.2023238. [30] CHEN Ying, LI Kaixin, WU Yuan, et al. Energy efficient task offloading and resource allocation in air-ground integrated MEC systems: A distributed online approach[J]. IEEE Transactions on Mobile Computing, 2024, 23(8): 8129–8142. doi: 10.1109/TMC.2023.3346431. [31] WANG Yuntao, SU Zhou, LUAN T H, et al. SEAL: A strategy-proof and privacy-preserving UAV computation offloading framework[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 5213–5228. doi: 10.1109/TIFS.2023.3280740. [32] APOSTOLOPOULOS P A, FRAGKOS G, TSIROPOULOU E E, et al. Data offloading in UAV-assisted multi-access edge computing systems under resource uncertainty[J]. IEEE Transactions on Mobile Computing, 2023, 22(1): 175–190. doi: 10.1109/TMC.2021.3069911. [33] CHENG Nan, LYU Feng, QUAN Wei, et al. Space/aerial-assisted computing offloading for IoT applications: A learning-based approach[J]. IEEE Journal on Selected Areas in Communications, 2019, 37(5): 1117–1129. doi: 10.1109/JSAC.2019.2906789. [34] LIN Xiaochen, MEI Weidong, and ZHANG Rui. A new store-then-amplify-and-forward protocol for UAV mobile relaying[J]. IEEE Wireless Communications Letters, 2020, 9(5): 591–595. doi: 10.1109/LWC.2019.2961668. [35] ZHOU Fasheng, WANG Ning, LUO Gaoyong, et al. Edge caching in multi-UAV-enabled radio access networks: 3D modeling and spectral efficiency optimization[J]. IEEE Transactions on Signal and Information Processing over Networks, 2020, 6: 329–341. doi: 10.1109/TSIPN.2020.2986360. [36] LI Lixin, CHENG Qianqian, XUE Kaiyuan, et al. Downlink transmit power control in ultra-dense UAV network based on mean field game and deep reinforcement learning[J]. IEEE Transactions on Vehicular Technology, 2020, 69(12): 15594–15605. doi: 10.1109/TVT.2020.3043851. [37] LIU Yuan, XIONG Ke, NI Qiang, et al. UAV-assisted wireless powered cooperative mobile edge computing: Joint offloading, CPU control, and trajectory optimization[J]. IEEE Internet of Things Journal, 2020, 7(4): 2777–2790. doi: 10.1109/JIOT.2019.2958975. [38] WANG Yuntao, SU Zhou, ZHANG Ning, et al. Mobile wireless rechargeable UAV networks: Challenges and solutions[J]. IEEE Communications Magazine, 2022, 60(3): 33–39. doi: 10.1109/MCOM.001.2100731. [39] YE Hanting, KANG Xin, JOUNG J, et al. Optimization for wireless-powered IoT networks enabled by an energy-limited UAV under practical energy consumption model[J]. IEEE Wireless Communications Letters, 2021, 10(3): 567–571. doi: 10.1109/LWC.2020.3038079. [40] WEI Xiaomin, MA Jianfeng, and SUN Cong. A survey on security of unmanned aerial vehicle systems: Attacks and countermeasures[J]. IEEE Internet of Things Journal, 2024, 11(21): 34826–34847. doi: 10.1109/JIOT.2024.3429111. [41] WESTBROOK T. The global positioning system and military jamming: The geographies of electronic warfare[J]. Journal of Strategic Security, 2019, 12(2): 1–16. doi: 10.5038/1944-0472.12.2.1720. [42] TIPPENHAUER N O, PÖPPER C, RASMUSSEN K B, et al. On the requirements for successful GPS spoofing attacks[C]. The 18th ACM Conference on Computer and Communications Security, Chicago, USA, 2011: 75–86. doi: 10.1145/2046707.2046719. [43] KERNS A J, SHEPARD D P, BHATTI J A, et al. Unmanned aircraft capture and control via GPS spoofing[J]. Journal of Field Robotics, 2014, 31(4): 617–636. doi: 10.1002/rob.21513. [44] SATHAYE H, STROHMEIER M, LENDERS V, et al. An experimental study of GPS spoofing and takeover attacks on UAVs[C]. The 31st USENIX Security Symposium (USENIX Security 22), Boston, USA, 2022: 3503–3520. [45] ZENG K C, LIU Shinan, SHU Yuanchao, et al. All your GPS are belong to us: Towards stealthy manipulation of road navigation systems[C]. The 27th USENIX Security Symposium (USENIX Security 18), Baltimore, USA, 2018: 1527–1544. [46] 新华网. 乌克兰部署电子战系统“欺骗”俄无人机[EB/OL]. https://www.news.cn/mil/2024-02/07/c_1212333955.htm, 2024. [47] NIGHSWANDER T, LEDVINA B, DIAMOND J, et al. GPS software attacks[C]. 2012 ACM Conference on Computer and Communications Security, Raleigh, USA, 2012: 450–461. doi: 10.1145/2382196.2382245. [48] CEVIZ O, SEN S, and SADIOGLU P. A survey of security in UAVs and FANETs: Issues, threats, analysis of attacks, and solutions[J]. IEEE Communications Surveys & Tutorials, 2025, 27(5): 3227–3265. doi: 10.1109/COMST.2024.3515051. [49] PIRAYESH H and ZENG Huacheng. Jamming attacks and anti-jamming strategies in wireless networks: A comprehensive survey[J]. IEEE Communications Surveys & Tutorials, 2022, 24(2): 767–809. doi: 10.1109/COMST.2022.3159185. [50] SON Y, SHIN H, KIM D, et al. Rocking drones with intentional sound noise on gyroscopic sensors[C]. The 24th USENIX Security Symposium (USENIX Security 15), Washington, USA, 2015: 881–896. [51] TRIPPEL T, WEISSE O, XU Wenyuan, et al. WALNUT: Waging doubt on the integrity of MEMS accelerometers with acoustic injection attacks[C]. 2017 IEEE European Symposium on Security and Privacy (EuroS&P), Paris, France, 2017: 3–18. doi: 10.1109/EuroSP.2017.42. [52] DAYANIKLI G Y, SINHA S, MUNIRAJ D, et al. Physical-layer attacks against pulse width modulation-controlled actuators[C]. The 31st USENIX Security Symposium (USENIX Security 22), Boston, USA, 2022: 953–970. [53] JANG J H, CHO M, KIM J, et al. Paralyzing drones via EMI signal injection on sensory communication channels[C]. The 30th Annual Network and Distributed System Security (NDSS) Symposium, San Diego, USA, 2023: 1–18. [54] SPREITZER R, MOONSAMY V, KORAK T, et al. Systematic classification of side-channel attacks: A case study for mobile devices[J]. IEEE Communications Surveys & Tutorials, 2018, 20(1): 465–488. doi: 10.1109/COMST.2017.2779824. [55] JAHAN F, SUN Weiqing, NIYAZ Q, et al. Security modeling of autonomous systems: A survey[J]. ACM Computing Surveys, 2020, 52(5): 91. doi: 10.1145/3337791. [56] ZHANG Qibo, ZENG Fanzi, HU Jingyang, et al. E-Argus: Drones detection by side-channel signatures via electromagnetic radiation[J]. IEEE Transactions on Intelligent Transportation Systems, 2024, 25(11): 18978–18991. doi: 10.1109/TITS.2024.3432977. [57] NGUYEN P, KAKARAPARTHI V, BUI N, et al. DroneScale: Drone load estimation via remote passive RF sensing[C]. The 18th Conference on Embedded Networked Sensor Systems, Yokohama, Japan, 2020: 326–339. doi: 10.1145/3384419.3430778. [58] 黄钊, 王泉, 杨鹏飞. 硬件木马: 关键问题研究进展及新动向[J]. 计算机学报, 2019, 42(5): 993–1017. doi: 10.11897/SP.J.1016.2019.00993.HUANG Zhao, WANG Quan, and YANG Pengfei. Hardware trojan: Research progress and new trends on key problems[J]. Chinese Journal of Computers, 2019, 42(5): 993–1017. doi: 10.11897/SP.J.1016.2019.00993. [59] ASIF M, RAHMAN M A, AKKAYA K, et al. ConFIDe: A PWM-driven control-fused intrusion detection system for hardware security in unmanned aerial vehicles[C]. The 19th ACM Asia Conference on Computer and Communications Security, Singapore, Singapore, 2024: 886–901. doi: 10.1145/3634737.3657014. [60] WU T F, GANESAN K, HU Y A, et al. TPAD: Hardware trojan prevention and detection for trusted integrated circuits[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2016, 35(4): 521–534. doi: 10.1109/TCAD.2015.2474373. [61] REECE T and ROBINSON W H. Detection of hardware trojans in third-party intellectual property using untrusted modules[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2016, 35(3): 357–366. doi: 10.1109/TCAD.2015.2459038. [62] HASSIJA V, CHAMOLA V, AGRAWAL A, et al. Fast, reliable, and secure drone communication: A comprehensive survey[J]. IEEE Communications Surveys & Tutorials, 2021, 23(4): 2802–2832. doi: 10.1109/COMST.2021.3097916. [63] WANG Xiaojie, ZHAO Zhonghui, YI Ling, et al. A survey on security of UAV swarm networks: Attacks and countermeasures[J]. ACM Computing Surveys, 2025, 57(3): 74. doi: 10.1145/3703625. [64] TANG A C. A review on cybersecurity vulnerabilities for urban air mobility[C/OL]. AIAA Scitech 2021 Forum, 2021: 0773. doi: 10.2514/6.2021-0773. [65] VASCONCELOS G, CARRIJO G, MIANI R, et al. The impact of DoS attacks on the AR. Drone 2.0[C]. 2016 XIII Latin American Robotics Symposium and IV Brazilian Robotics Symposium (LARS/SBR), Recife, Brazil, 2016: 127–132. doi: 10.1109/LARS-SBR.2016.28. [66] GRUZA O, HEFTRIG E, JACOBSEN O, et al. Attacking with something that does not exist: 'Proof of non-existence' can exhaust DNS resolver CPU[C]. The 18th USENIX WOOT Conference on Offensive Technologies (WOOT 24), Philadelphia, USA, 2024: 45–57. [67] LI Xiang, WU Dashuai, DUAN Haixin, et al. DNSBomb: A new practical-and-powerful pulsing DoS attack exploiting DNS queries-and-responses[C]. 2024 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2024: 4478–4496. doi: 10.1109/SP54263.2024.00264. [68] GOLDBERG S, HALLER M, HENINGER N, et al. RADIUS/UDP considered harmful[C]. The 33rd USENIX Security Symposium (USENIX Security 24), Philadelphia, USA, 2024: 7429–7446. [69] HU Y C, PERRIG A, and JOHNSON D B. Packet leashes: A defense against wormhole attacks in wireless networks[C]. IEEE INFOCOM 2003. 22nd Annual Joint Conference of the IEEE Computer and Communications Societies (IEEE Cat. No. 03CH37428), San Francisco, USA, 2003: 1976–1986. doi: 10.1109/INFCOM.2003.1209219. [70] SCHWEITZER N, DVIR A, and STULMAN A. Network wormhole attacks without a traditional wormhole[J]. Ad Hoc Networks, 2023, 151: 103286. doi: 10.1016/j.adhoc.2023.103286. [71] CONTI M, DRAGONI N, and LESYK V. A survey of man in the middle attacks[J]. IEEE Communications Surveys & Tutorials, 2016, 18(3): 2027–2051. doi: 10.1109/COMST.2016.2548426. [72] PAULI D. Hacker reveals $40 attack that steals police drones from 2km away[EB/OL]. https://www.theregister.com/2016/04/01/hacker_reveals_40_attack_to_steal_28000_drones_from_2km_away, 2016. [73] RODDAY N M, SCHMIDT R D O, and PRAS A. Exploring security vulnerabilities of unmanned aerial vehicles[C]. 2016 IEEE/IFIP Network Operations and Management Symposium (NOMS), Istanbul, Turkey, 2016: 993–994. doi: 10.1109/NOMS.2016.7502939. [74] TSENG F H, CHOU L D, and CHAO H C. A survey of black hole attacks in wireless mobile ad hoc networks[J]. Human-centric Computing and Information Sciences, 2011, 1(1): 4. doi: 10.1186/2192-1962-1-4. [75] SCHWEITZER N, STULMAN A, MARGALIT R D, et al. Contradiction based gray-hole attack minimization for ad-hoc networks[J]. IEEE Transactions on Mobile Computing, 2017, 16(8): 2174–2183. doi: 10.1109/TMC.2016.2622707. [76] SCHILLER N, CHLOSTA M, SCHLOEGEL M, et al. Drone security and the mysterious case of DJI's DroneID[C]. The 30th Annual Network and Distributed System Security (NDSS) Symposium, San Diego, USA, 2023: 1–17. [77] 央视网. 美国无人机“捕食者”和“死神”的控制系统遭病毒入侵[EB/OL]. https://news.cntv.cn/world/20111009/101151.shtml, 2011. [78] LADISA P, PLATE H, MARTINEZ M, et al. SoK: Taxonomy of attacks on open-source software supply chains[C]. 2023 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2023: 1509–1526. doi: 10.1109/SP46215.2023.10179304. [79] KHANDELWAL S. MalDrone: First ever backdoor malware for drones[EB/OL]. https://thehackernews.com/2015/01/MalDrone-backdoor-drone-malware.html?utm_source=chatgpt.com, 2015. [80] JACOBSEN R H and MARANDI A. Security threats analysis of the unmanned aerial vehicle system[C]. 2021 IEEE Military Communications Conference (MILCOM), San Diego, USA, 2021: 316–322. doi: 10.1109/MILCOM52596.2021.9652900. [81] HU Jueming, AMMAR M, HUSSAIN B Z, et al. Reinforcement-learning-driven integrated detection and mitigation of UAV GPS spoofing attacks[J]. IEEE Internet of Things Journal, 2025, 12(18): 36926–36941. doi: 10.1109/JIOT.2025.3579307. [82] JEONG J, KIM D, JANG J H, et al. Un-rocking drones: Foundations of acoustic injection attacks and recovery thereof[C]. 30th Annual Network and Distributed System Security (NDSS) Symposium, San Diego, USA, 2023: 1–18. [83] WANG Han, SAYADI H, SASAN A, et al. Hybrid-Shield: Accurate and efficient cross-layer countermeasure for run-time detection and mitigation of cache-based side-channel attacks[C]. IEEE/ACM International Conference on Computer Aided Design, San Diego, USA, 2020: 1–9. [84] ALLADI T, NAREN, BANSAL G, et al. SecAuthUAV: A novel authentication scheme for UAV-ground station and UAV-UAV communication[J]. IEEE Transactions on Vehicular Technology, 2020, 69(12): 15068–15077. doi: 10.1109/TVT.2020.3033060. [85] HOSSEINZADEH M, ALI S, AHMAD H J, et al. A Novel Q-learning-based secure routing scheme with a robust defensive system against wormhole attacks in flying ad hoc networks[J]. Vehicular Communications, 2024, 49: 100826. doi: 10.1016/j.vehcom.2024.100826. [86] WAN Zelin, CHO J H, ZHU Mu, et al. Optimizing effectiveness and defense of drone surveillance missions via honey drones[J]. ACM Transactions on Internet Technology, 2024, 24(4): 22. doi: 10.1145/3701233. [87] LEKSSAYS A, MOUHCINE H, TRAN K, et al. LLMxCPG: Context-aware vulnerability detection through code property graph-guided large language models[C]. The 34th USENIX Security Symposium (USENIX Security 25), Seattle, USA, 2025: 489–507. [88] KOKKONIS D, MARCOZZI M, DECOUX E, et al. ROSA: Finding backdoors with fuzzing[C]. 2025 IEEE/ACM 47th International Conference on Software Engineering (ICSE), Ottawa, Canada, 2025: 2816–2828. doi: 10.1109/ICSE55347.2025.00183. [89] CUI Jinqiang, LIU Guocai, WANG Hui, et al. TPML: Task planning for multi-UAV system with large language models[C]. 2024 IEEE 18th International Conference on Control & Automation (ICCA), Reykjavík, Iceland, 2024: 886–891. doi: 10.1109/ICCA62789.2024.10591846. [90] WANG Yuhui, FAROOQ J, GHAZZAI H, et al. Multi-UAV placement for integrated access and backhauling using LLM-driven optimization[C]. 2025 IEEE Wireless Communications and Networking Conference (WCNC), Milan, Italy, 2025: 1–6. doi: 10.1109/WCNC61545.2025.10978733. [91] 陈鹏, 陈旭, 罗文, 等. 基于视觉语言模型的多模态无人机跨视图地理定位[J]. 机器人, 2025, 47(3): 416–426. doi: 10.13973/j.cnki.robot.240283.CHEN Peng, CHEN Xu, LUO Wen, et al. Multimodal drone cross-view geo-localization based on vision-language model[J]. Robot, 2025, 47(3): 416–426. doi: 10.13973/j.cnki.robot.240283. [92] SAUTENKOV O, YAQOOT Y, LYKOV A, et al. UAV-VLA: Vision-language-action system for large scale aerial mission generation[C]. 2025 20th ACM/IEEE International Conference on Human-Robot Interaction (HRI), Melbourne, Australia, 2025: 1588–1592. doi: 10.1109/HRI61500.2025.10974117. [93] LIN Fei, TIAN Yonglin, WANG Yunzhe, et al. AirVista: Empowering UAVs with 3D spatial reasoning abilities through a multimodal large language model agent[C]. 2024 IEEE 27th International Conference on Intelligent Transportation Systems (ITSC), Edmonton, Canada, 2024: 476–481. doi: 10.1109/ITSC58415.2024.10919532. [94] HU Yaqi, YE Dongdong, KANG Jiawen, et al. A cloud–edge collaborative architecture for multimodal LLM-based advanced driver assistance systems in IoT networks[J]. IEEE Internet of Things Journal, 2025, 12(10): 13208–13221. doi: 10.1109/JIOT.2024.3509628. [95] ZHANG Weichen, LIU Yuxuan, WANG Xuzhe, et al. Demo abstract: Embodied aerial agent for city-level visual language navigation using large language model[C]. The 23rd ACM/IEEE International Conference on Information Processing in Sensor Networks (IPSN), Hong Kong, China, 2024: 265–266. doi: 10.1109/IPSN61024.2024.00033. [96] LIU Xinzhu, GUO Di, LIU Huaping, et al. Multi-agent embodied visual semantic navigation with scene prior knowledge[J]. IEEE Robotics and Automation Letters, 2022, 7(2): 3154–3161. doi: 10.1109/LRA.2022.3145964. [97] CAO Xinye, NAN Guoshun, GUO Hongcan, et al. Exploring LLM-based multi-agent situation awareness for zero-trust space-air-ground integrated network[J]. IEEE Journal on Selected Areas in Communications, 2025, 43(6): 2230–2247. doi: 10.1109/JSAC.2025.3560042. [98] QIN Qi, CAO Xinye, NAN Guoshun, et al. An LLM-based self-evolving security framework for 6G space-air-ground integrated networks[J]. IEEE Communications Magazine, 2025, 63(10): 110–116. doi: 10.1109/MCOM.003.2400695. [99] ZHANG Yuhui, UNELL A, WANG Xiaohan, et al. Why are visually-grounded language models bad at image classification?[C]. The 38th International Conference on Neural Information Processing Systems, Vancouver, Canada, 2024: 1639. [100] ZHOU Yue, DING Ran, YANG Xue, et al. AirSpatialBot: A spatially aware aerial agent for fine-grained vehicle attribute recognition and retrieval[J]. IEEE Transactions on Geoscience and Remote Sensing, 2025, 63: 5624812. doi: 10.1109/TGRS.2025.3570895. [101] ZHANG Wei, CAI Miaoxin, ZHANG Tong, et al. EarthGPT: A universal multimodal large language model for multisensor image comprehension in remote sensing domain[J]. IEEE Transactions on Geoscience and Remote Sensing, 2024, 62: 5917820. doi: 10.1109/TGRS.2024.3409624. [102] SHAO Hao, QIAN Shengju, XIAO Han, et al. Visual CoT: Advancing multi-modal language models with a comprehensive dataset and benchmark for chain-of-thought reasoning[C]. The 38th International Conference on Neural Information Processing Systems, Vancouver, Canada, 2024: 275. [103] SUN Xinyu, CHEN Peihao, FAN Jugang, et al. FGPrompt: Fine-grained goal prompting for image-goal navigation[C]. The 37th International Conference on Neural Information Processing Systems, New Orleans, USA, 2023: 527. [104] PAUL S, ROY-CHOWDHURY A K, and CHERIAN A. AVLEN: Audio-visual-language embodied navigation in 3D environments[C]. The 36th International Conference on Neural Information Processing Systems, New Orleans, USA, 2022: 451. [105] LIU C Y, WANG Yaxuan, FLANIGAN J, et al. Large language model unlearning via embedding-corrupted prompts[C]. The 38th International Conference on Neural Information Processing Systems, Vancouver, Canada, 2024: 3754. [106] CHOQUETTE-CHOO C A, DVIJOTHAM K D, PILLUTLA K, et al. Correlated noise provably beats independent noise for differentially private learning[C]. The Twelfth International Conference on Learning Representations, Vienna, Austria, 2024: 1–61. [107] XI Zhaohan, DU Tianyu, LI Changjiang, et al. Defending pre-trained language models as few-shot learners against backdoor attacks[C]. The 37th International Conference on Neural Information Processing Systems, New Orleans, USA, 2023: 1420. -





 下载:
下载:


 下载:
下载:
