Physical Layer Authentication for Large Language Models in Maritime Communications
-
摘要: 物理层认证快速识别电子欺骗等攻击,但海域短包通信的信道估计误差大,且海域信道变化剧烈,造成认证精度低,速度慢,难以支撑基于大语言模型的智慧海洋业务。为此,该文研究面向大语言模型的海域通信物理层认证,根据终端无线信道和数据包的多种物理层特征,基于假设检验设计多模式认证机制,适配摄像头和温湿度传感器等多类型终端的长短包通信方式,并结合大语言模型推断结果的环境指示等,利用强化学习持续优化认证模式和检测阈值,提高认证精度和速度。设计漏报风险评估机制,修正认证策略分布,结合持续学习机制挖掘甲板和船舱等多场景下的多尺度认证经验,并在相似场景中快速回放,加速认证策略优化。基于LLaVA-1.5-7B大语言模型和海域实测信道数据的仿真结果表明,所提方案可显著提升认证精度和速度,防御多场景船载终端在大语言模型边缘推断过程中的电子欺骗等攻击,支撑智慧海洋业务。Abstract:
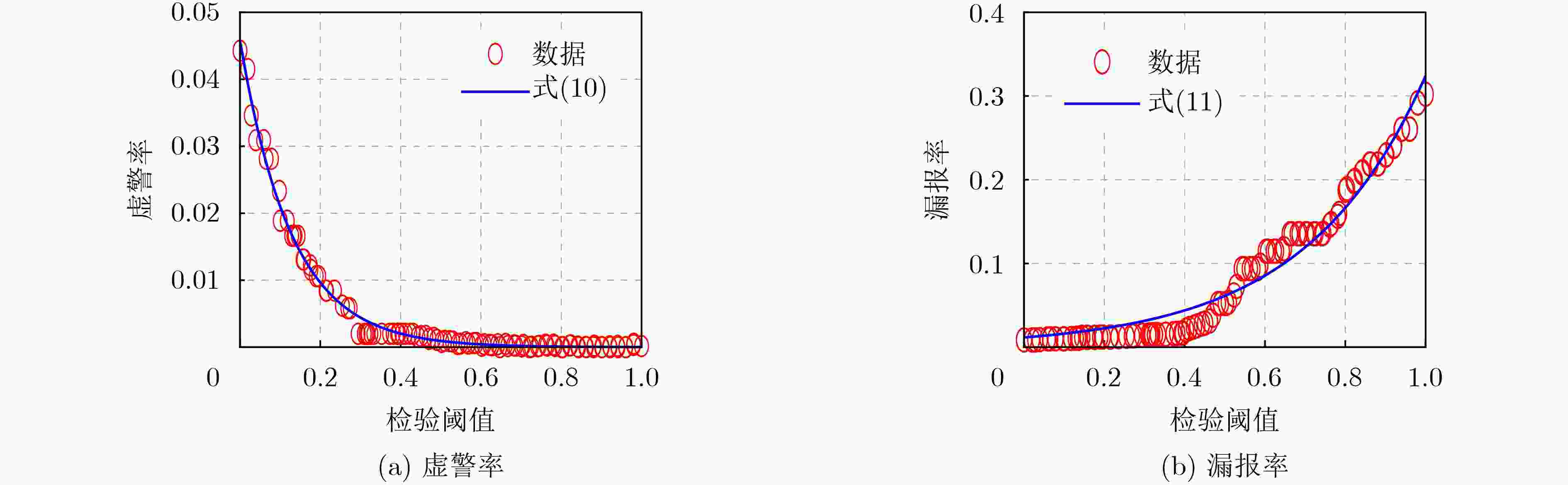
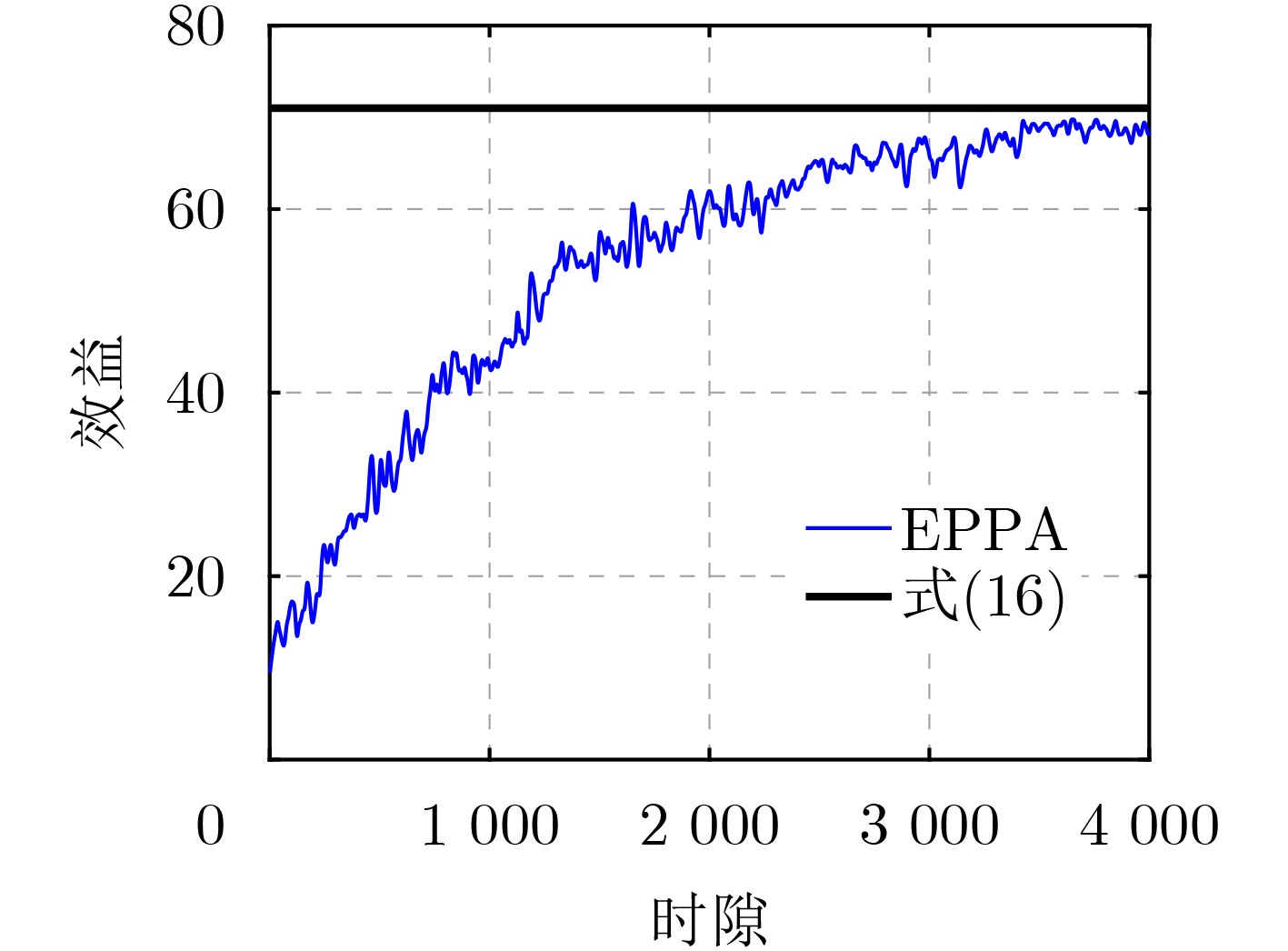
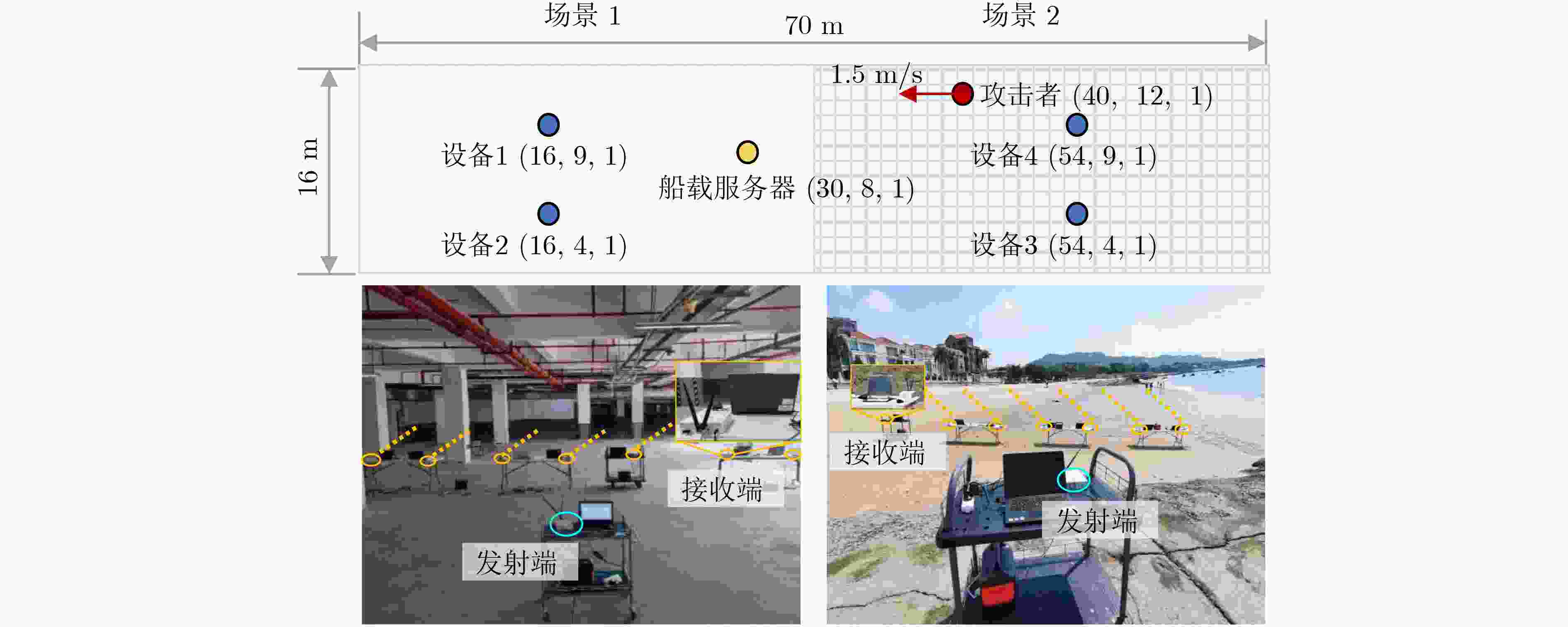
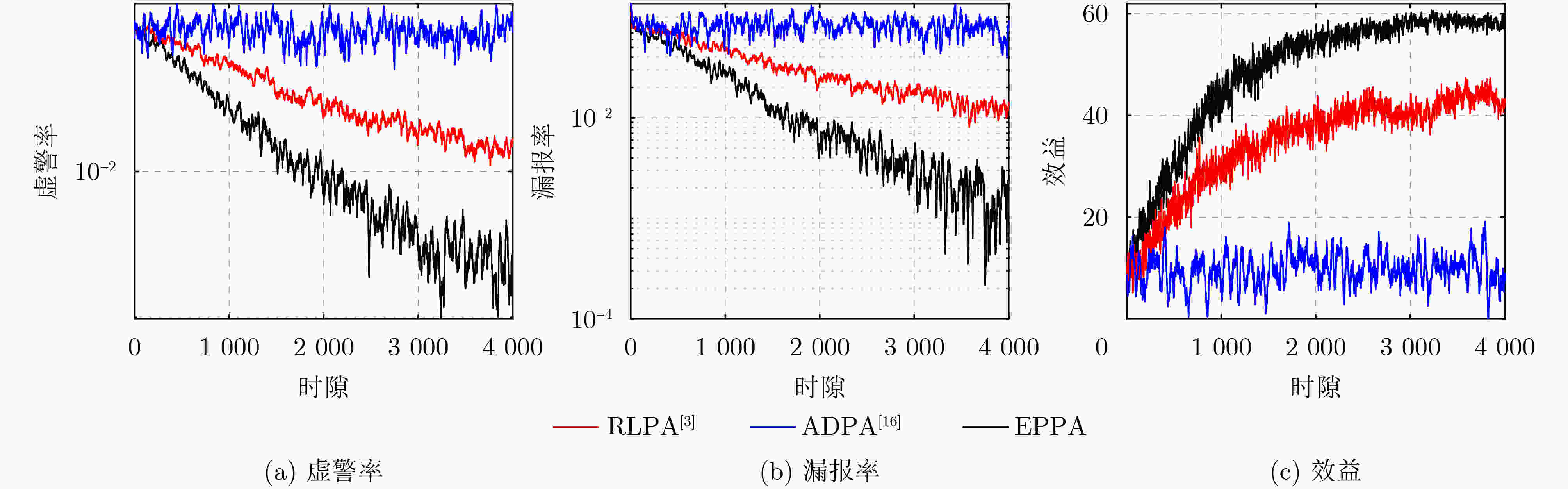
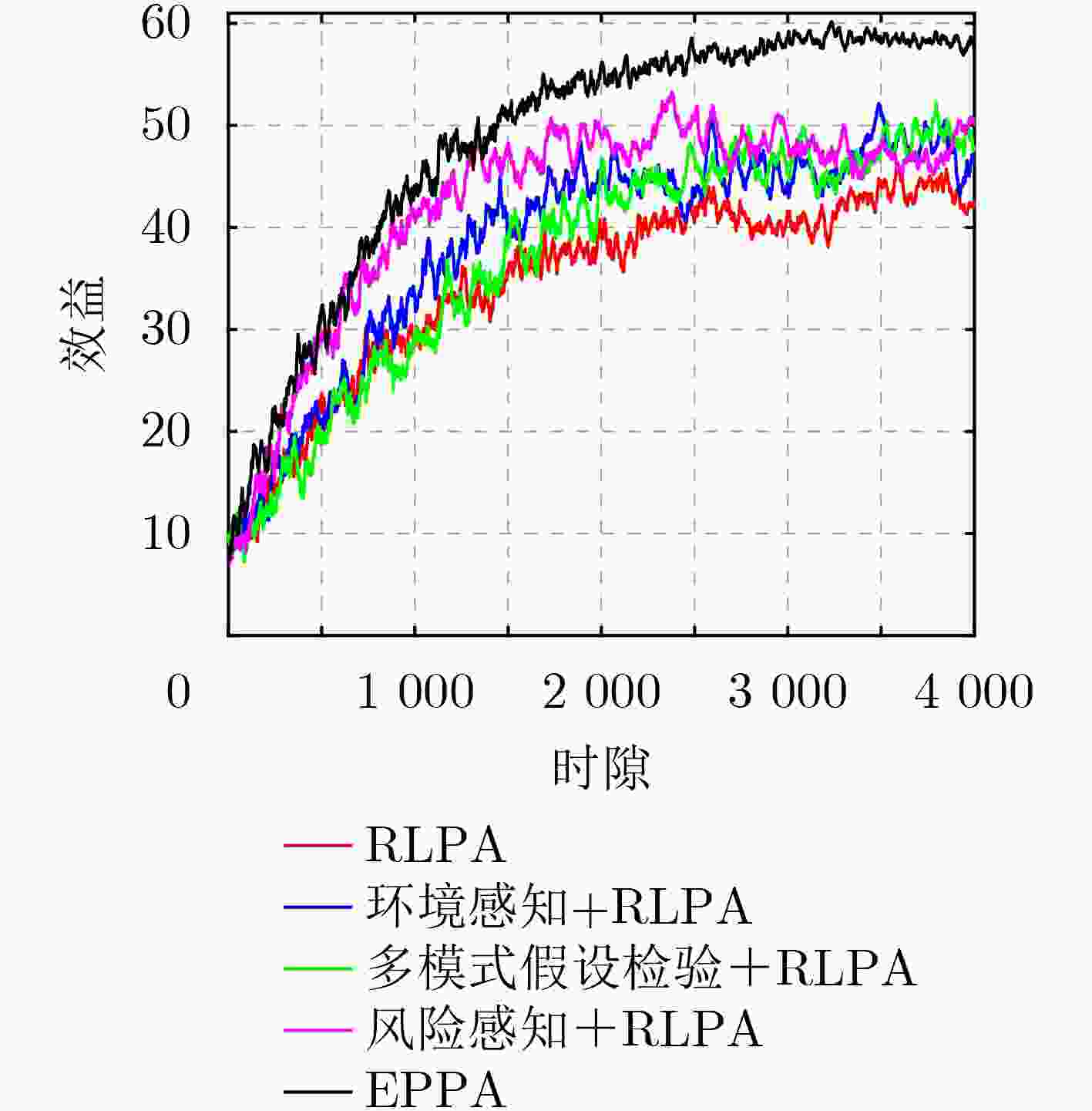
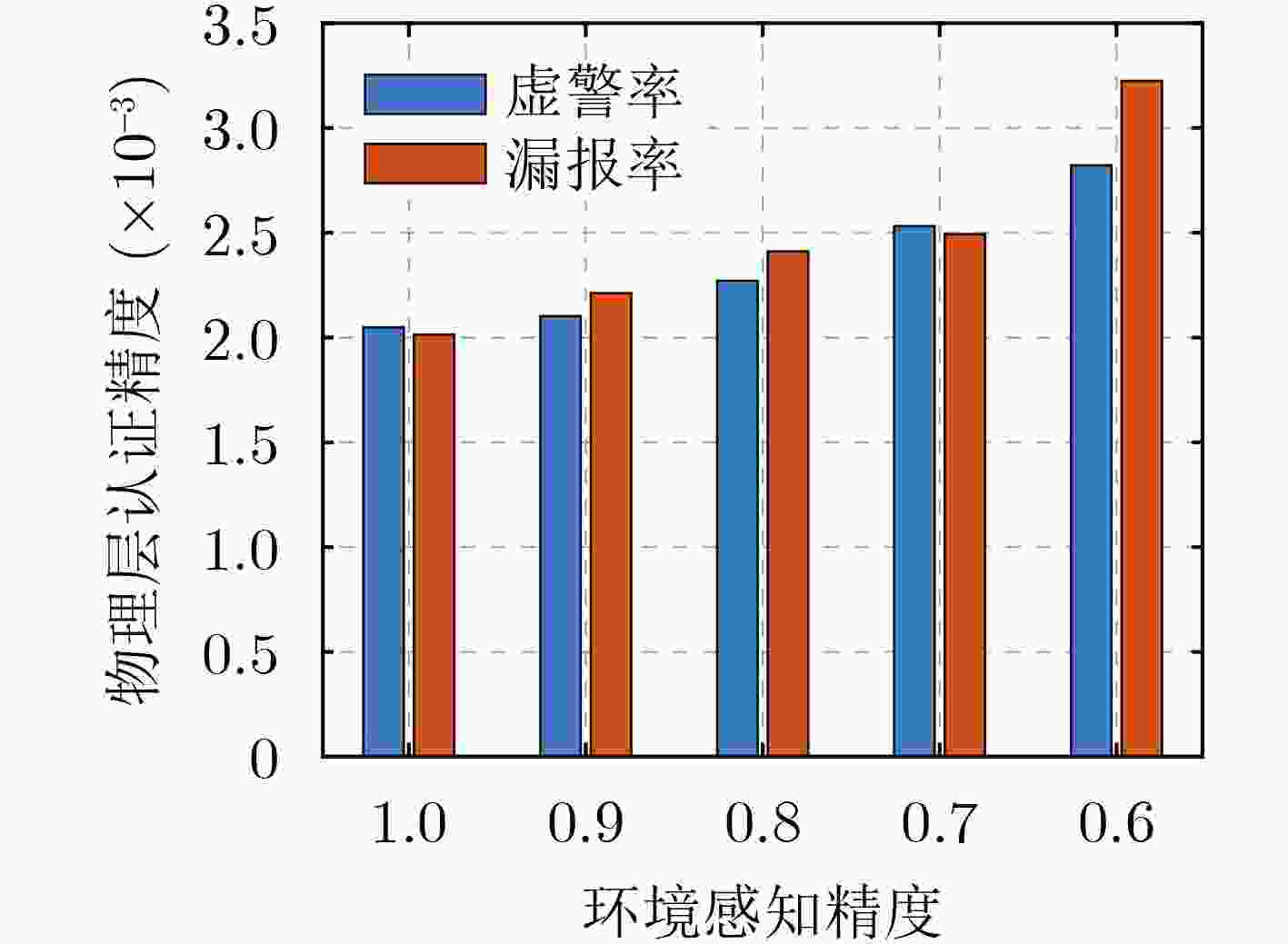
Objective PHYsical (PHY)-layer authentication exploits channel state information to detect spoofing attacks. However, for smart ocean applications supported by Large Language Models (LLMs), authentication accuracy and speed remain limited because of insufficient channel estimation and rapidly time-varying channels in short-packet communications with constrained preamble length. An environment perception-aware PHY-layer authentication scheme is therefore proposed for LLM edge inference in maritime applications. A hypothesis-testing-based multi-mode authentication framework is designed to evaluate channel state information and packet arrival interval. Application types and environmental indicators inferred by the LLM are used in reinforcement learning to optimize the authentication mode and test threshold, thereby improving authentication accuracy and speed. Methods An environment perception-aware PHY-layer authentication scheme is developed for LLM edge inference in maritime wireless networks. Hypothesis-testing-based multi-mode authentication is used to jointly evaluate channel state information and packet arrival interval for spoofing detection. Reinforcement learning is adopted to optimize the authentication mode and test threshold according to application types and environmental indicators inferred by a multimodal LLM fed with images and prompts. A multi-level policy risk function is formulated to quantify miss-detection risk and to reduce exploration probability for unsafe policies. A Benna-Fusi synapse-based continual learning mechanism is proposed to obtain multi-scale optimization experience across multiple maritime scenarios, such as deck and cabin environments, and to replay identical cases to accelerate policy optimization. Results and Discussions Simulations are conducted using four legal devices and a shipborne server with maritime channel data collected in the Xiamen Pearl Harbor area. A spoofing attacker moving at 1.5 m/s transmits false data packets to the server with a maximum power of 100 mW. The results demonstrate clear performance gains over benchmark methods. Compared with RLPA, the proposed scheme achieves an 84.2% reduction in false alarm rate and an 82.3% reduction in miss-detection rate. These gains are attributed to the use of LLM-derived environmental indicators and a safe exploration mechanism that avoids high-risk authentication policies leading to increased miss detection. Conclusions A PHY-layer authentication scheme is proposed for LLM-enabled intelligent maritime wireless networks, in which both the authentication mode and test threshold are optimized to counter spoofing attacks. By jointly using LLM-derived environmental indicators, channel state information, and packet arrival interval, a safe exploration mechanism is applied to improve authentication accuracy and efficiency. Simulation results confirm that the proposed scheme reduces the false alarm rate by 84.2% and the miss-detection rate by 82.3% compared with the benchmark RLPA. -
表 1 重要符号和含义
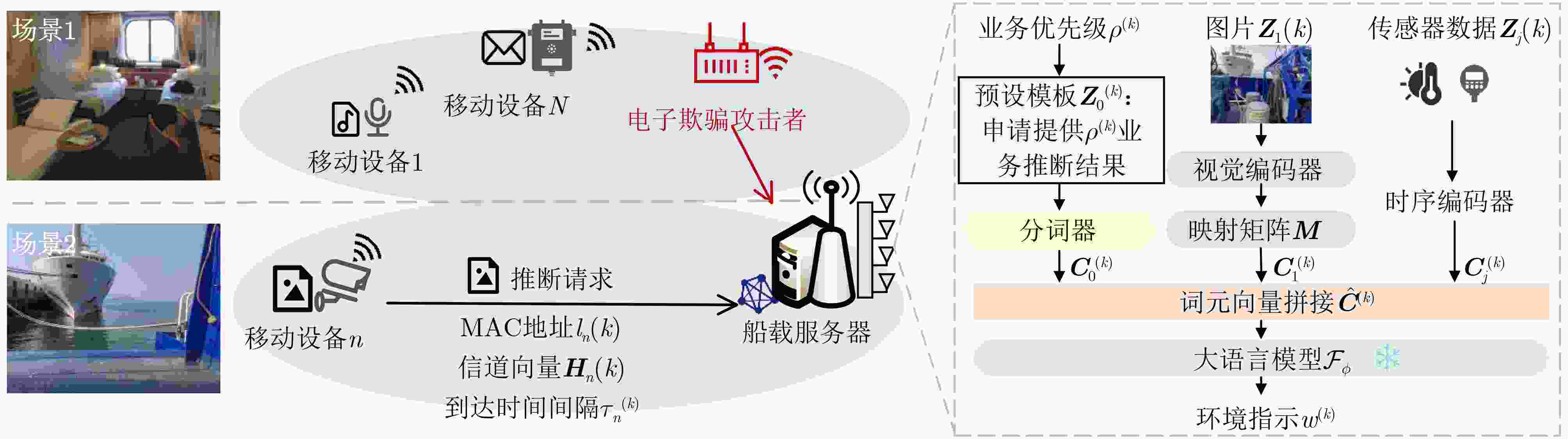
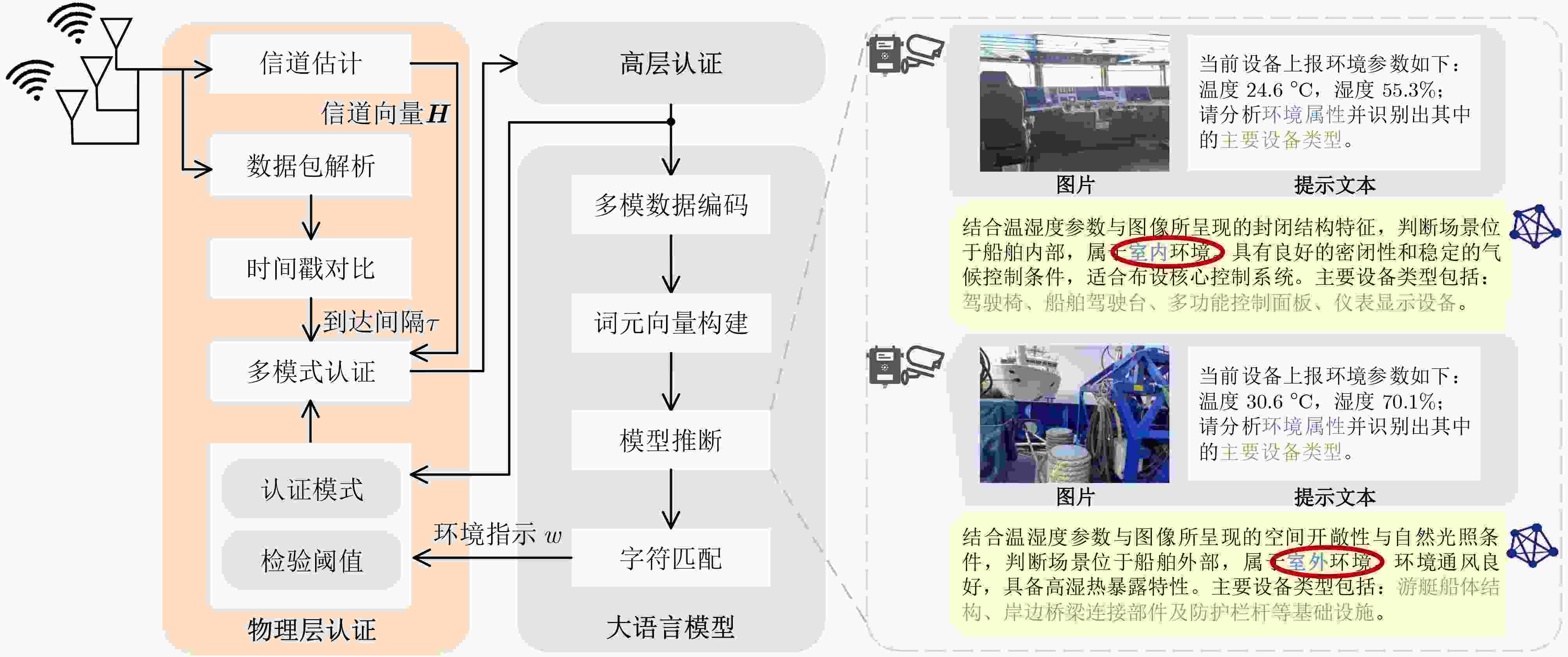
符号 含义 N 智能设备个数 J 大语言模型可推断数据模态数 $ \boldsymbol{Z}_{0}^{(k)} $/$ \boldsymbol{Z}_{1}^{(k)} $/$ \boldsymbol{Z}_{2\leq i\leq J}^{(k)} $ 预设文本提示模板/图像/传感器数据 $ \boldsymbol{C}_{1\leq i\leq J}^{(k)} $ 多模态数据生成的词元向量 $ {f}_{n} $ 智能设备$ n $的传输中心频点 $ {W}_{n} $ 传输带宽 $ l_{n}^{(k)} $ 媒体访问控制地址 $ {\rho }^{(k)} $ 数据包优先级 $ {\boldsymbol{H}}^{(k)} $ 信道状态向量 $ {\tau }^{(k)} $ 数据包到达时间间隔 $ N_{\text{T}}^{(k)} $ 待认证数据包总数 $ N_{\text{P}}^{(k)} $ 通过物理层认证的数据包个数 $ N_{\text{M}}^{(k)} $ 漏报的虚假数据包个数 1 环境感知辅助的海域物理层认证EPPA
1: 初始化:$ \alpha ,\beta ,\delta ,T,\boldsymbol{g},\boldsymbol{\gamma },\boldsymbol{\mu },{N}_{\text{T}} $ 2: For k = 1, 2, ···, do 3: 接收到来自MAC地址为$ {l}^{(k)} $的设备的数据包 4. 构建待测数据包信道向量$ {\boldsymbol{H}}^{(k)} $ 5: 评估数据包优先级$ {\rho }^{(k)} $和到达时间间隔$ {\tau }^{(k)} $ 6: 获取大语言模型历史推断中的设备环境指示$ {w}^{(k)} $ 7: 根据式(1)构建$ {\boldsymbol{s}}^{(k)} $ 8: 根据式(5)选择认证策略$ {\boldsymbol{a}}^{(k)} $ 9: 根据$ {a}_{1}{}^{(k)} $和式(2)计算$ \mathcal{L} $ 10: If $ \mathcal{L}\leq {a}_{2}{}^{(k)} $ then 11: 通过认证,$ \hat{\boldsymbol{H}}\leftarrow {\boldsymbol{H}}^{(k)} $, $ \hat{\tau }\leftarrow {\tau }^{(k)} $ 12: End if 13: 统计前$ {N}_{\text{T}} $个数据包中的认证通过数$ {N}_{\text{P}} $和漏报数$ {N}_{\text{M}} $ 14: 根据式(3)和式(4)计算效益$ {u}^{(k)} $和策略风险$ {e}^{(k)} $ 15: 根据式(7)和式(8)更新长期效益值$ Q $和长期风险值$ E $ 16: For i = 2, ···, $ T $ do 17: 根据式(6)更新深层经验$ {\hat{Q}}_{i} $ 18: End for 19: End for -
[1] 鲁信金, 施育鑫, 雷菁, 等. 无线通信物理层内生安全: 关键技术、优势与未来挑战[J]. 通信学报, 2024, 45(S1): 87–96. doi: 10.11959/j.issn.1000-436x.2024210.LU Xinjin, SHI Yuxin, LEI Jing, et al. Endogenous security in the physical layer of wireless communications: Key technologies, advantages and future challenges[J]. Journal on Communications, 2024, 45(S1): 87–96. doi: 10.11959/j.issn.1000-436x.2024210. [2] ZHANG Xinyuan, NIE Jiangtian, HUANG Yudong, et al. Beyond the cloud: Edge inference for generative large language models in wireless networks[J]. IEEE Transactions on Wireless Communications, 2025, 24(1): 643–658. doi: 10.1109/TWC.2024.3497923. [3] LU Xiaozhen, XIAO Liang, XU Tangwei, et al. Reinforcement learning based PHY authentication for VANETs[J]. IEEE Transactions on Vehicular Technology, 2020, 69(3): 3068–3079. doi: 10.1109/TVT.2020.2967026. [4] WANG Qi, PANG Zhibo, LIANG Wei, et al. Spatiotemporal gradient-based physical-layer authentication enhanced by CSI-to-image transformation for industrial mobile devices[J]. IEEE Transactions on Industrial Informatics, 2024, 20(3): 4236–4245. doi: 10.1109/TII.2023.3316178. [5] DURISI G, KOCH T, and POPOVSKI P. Toward massive, ultrareliable, and low-latency wireless communication with short packets[J]. Proceedings of the IEEE, 2016, 104(9): 1711–1726. doi: 10.1109/JPROC.2016.2537298. [6] LIN Jiaying, DIEKMANN P, FRAMING C E, et al. Maritime environment perception based on deep learning[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(9): 15487–15497. doi: 10.1109/TITS.2022.3140933. [7] ZHAO Changyuan, DU Hongyang, NIYATO D, et al. Generative AI for secure physical layer communications: A survey[J]. IEEE Transactions on Cognitive Communications and Networking, 2025, 11(1): 3–26. doi: 10.1109/TCCN.2024.3438379. [8] 杨立君, 李明航, 陆海涛, 等. 基于信道指纹的毫米波MIMO系统身份欺骗攻击检测方案[J]. 电子与信息学报, 2023, 45(12): 4228–4234. doi: 10.11999/JEIT220934.YANG Lijun, LI Minghang, LU Haitao, et al. Spoofing attack detection scheme based on channel fingerprint for millimeter wave MIMO system[J]. Journal of Electronics & Information Technology, 2023, 45(12): 4228–4234. doi: 10.11999/JEIT220934. [9] NOSOUHI M R, SOOD K, GROBLER M, et al. Towards spoofing resistant next generation IoT networks[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 1669–1683. doi: 10.1109/TIFS.2022.3170276. [10] WU Yuemei, WEI Dong, GUO Caili, et al. Physical layer authentication based on channel polarization response in dual-polarized antenna communication systems[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 2144–2159. doi: 10.1109/TIFS.2023.3263624. [11] MENG Rui, XU Xiaodong, WANG Bizhu, et al. Physical-layer authentication based on hierarchical variational autoencoder for Industrial Internet of Things[J]. IEEE Internet of Things Journal, 2023, 10(3): 2528–2544. doi: 10.1109/JIOT.2022.3213593. [12] HOANG T M, VAN CHIEN T, VAN LUONG T, et al. Detection of spoofing attacks in aeronautical ad-hoc networks using deep autoencoders[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 1010–1023. doi: 10.1109/TIFS.2022.3155970. [13] 毛丹丹, 王宁, 甄姬娜, 等. 基于毫米波MIMO信道多维优势提取的密钥协商方法[J]. 通信学报, 2025, 46(1): 124–143. doi: 10.11959/j.issn.1000-436x.2025005.MAO Dandan, WANG Ning, ZHEN Ji’na, et al. Key agreement method based on multi-dimensional advantage distillation over mmWave MIMO channels[J]. Journal on Communications, 2025, 46(1): 124–143. doi: 10.11959/j.issn.1000-436x.2025005. [14] 宋华伟, 金梁, 张胜军. 基于标签信号的物理层安全认证[J]. 电子与信息学报, 2018, 40(5): 1066–1071. doi: 10.11999/JEIT170672.SONG Huawei, JIN Liang, ZHANG Shengjun. Physical layer authentication based on tag signal[J]. Journal of Electronics & Information Technology, 2018, 40(5): 1066–1071. doi: 10.11999/JEIT170672. [15] FANG He, WANG Xianbin, and HANZO L. Learning-aided physical layer authentication as an intelligent process[J]. IEEE Transactions on Communications, 2019, 67(3): 2260–2273. doi: 10.1109/TCOMM.2018.2881117. [16] ABDRABOU M and GULLIVER T A. Adaptive physical layer authentication using machine learning with antenna diversity[J]. IEEE Transactions on Communications, 2022, 70(10): 6604–6614. doi: 10.1109/TCOMM.2022.3196648. [17] XIAO Liang, WAN Xiaoyue, and HAN Zhu. PHY-layer authentication with multiple landmarks with reduced overhead[J]. IEEE Transactions on Wireless Communications, 2018, 17(3): 1676–1687. doi: 10.1109/TWC.2017.2784431. [18] FANG He, XIAO Zhenlong, WANG Xianbin, et al. Collaborative authentication for 6G networks: An edge intelligence based autonomous approach[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 2091–2103. doi: 10.1109/TIFS.2023.3263636. [19] SCIANCALEPORE S, TEDESCHI P, AZIZ A, et al. Auth-AIS: Secure, flexible, and backward-compatible authentication of vessels AIS broadcasts[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(4): 2709–2726. doi: 10.1109/TDSC.2021.3069428. [20] ZHANG Peiying, WANG Yaqi, AUJLA G S, et al. A blockchain-based authentication scheme and secure architecture for IoT-enabled maritime transportation systems[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(2): 2322–2331. doi: 10.1109/TITS.2022.3159485. [21] VANGALA A, AGRAWAL S, DAS A K, et al. Big data-enabled authentication framework for offshore maritime communication using drones[J]. IEEE Transactions on Vehicular Technology, 2024, 73(7): 10196–10210. doi: 10.1109/TVT.2024.3367945. [22] BENNA M K and FUSI S. Computational principles of synaptic memory consolidation[J]. Nature Neuroscience, 2016, 19(12): 1697–1706. doi: 10.1038/nn.4401. [23] XIAO Liang, LU Xiaozhen, XU Tangwei, et al. Reinforcement learning-based physical-layer authentication for controller area networks[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 2535–2547. doi: 10.1109/TIFS.2021.3056206. [24] POPOVSKI P, STEFANOVIĆ Č, NIELSEN J J, et al. Wireless access in ultra-reliable low-latency communication (URLLC)[J]. IEEE Transactions on Communications, 2019, 67(8): 5783–5801. doi: 10.1109/TCOMM.2019.2914652. -





 下载:
下载:


 下载:
下载:
