Energy Consumption Optimization of Cooperative NOMA Secure Offload for Mobile Edge Computing
-
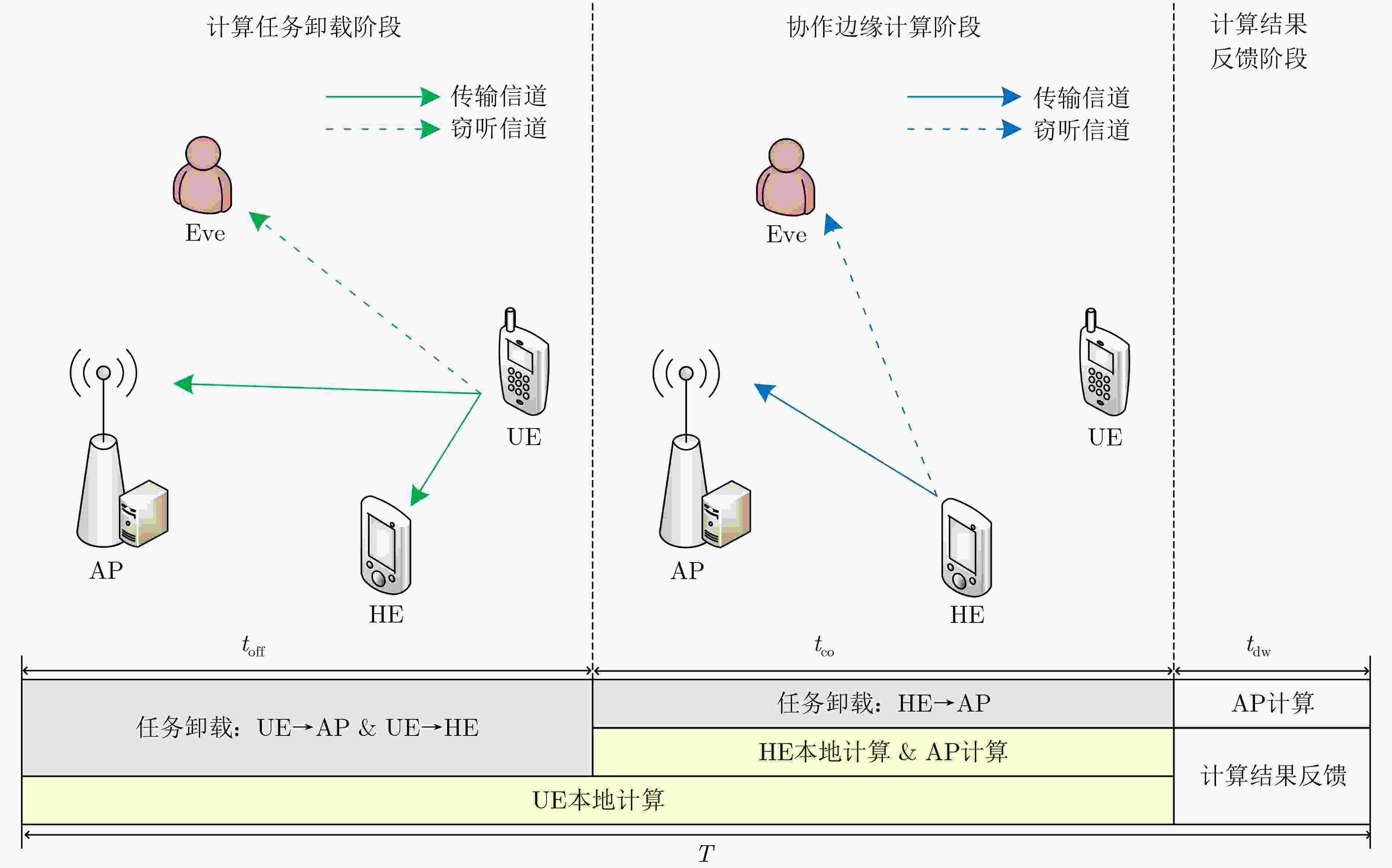
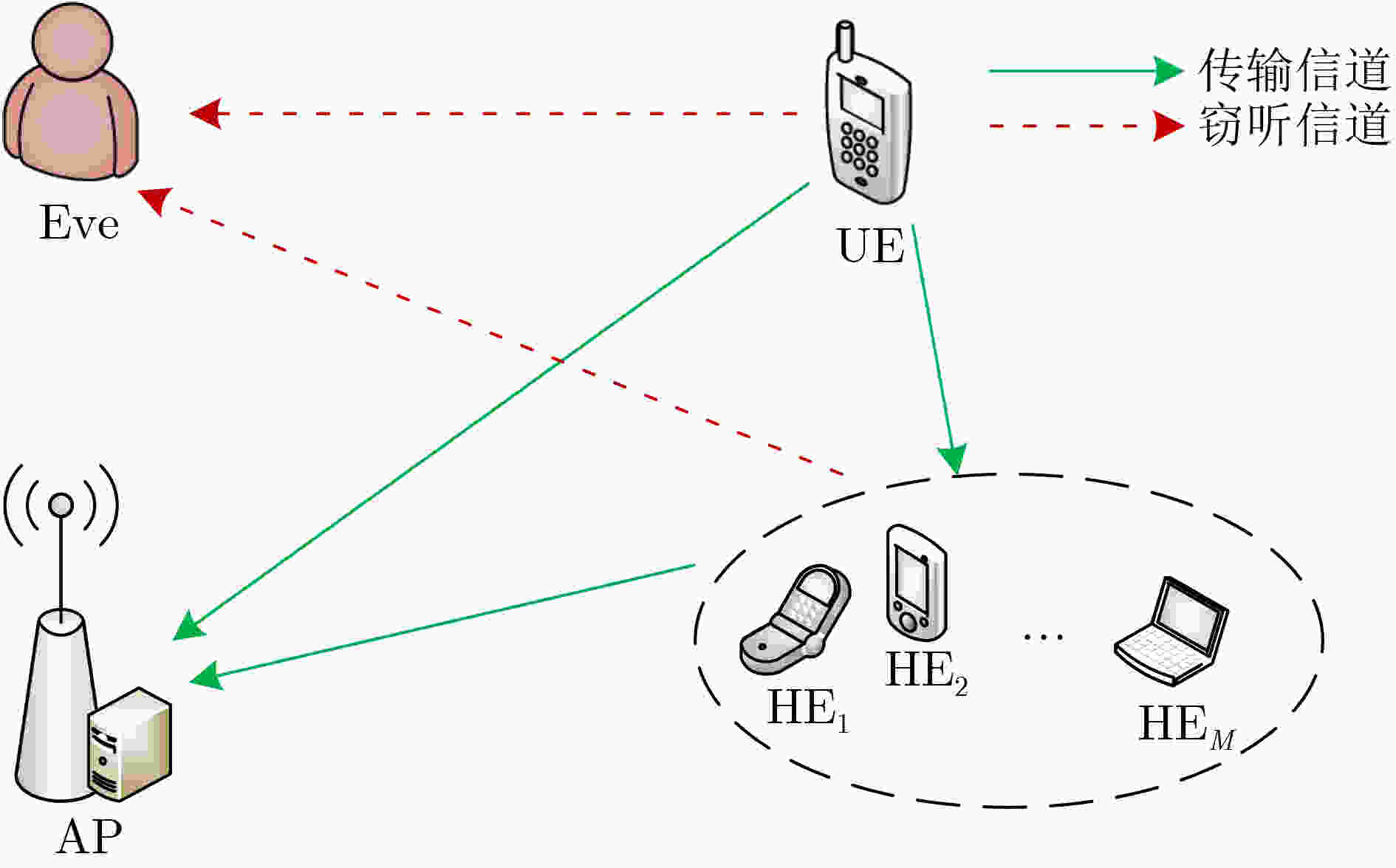
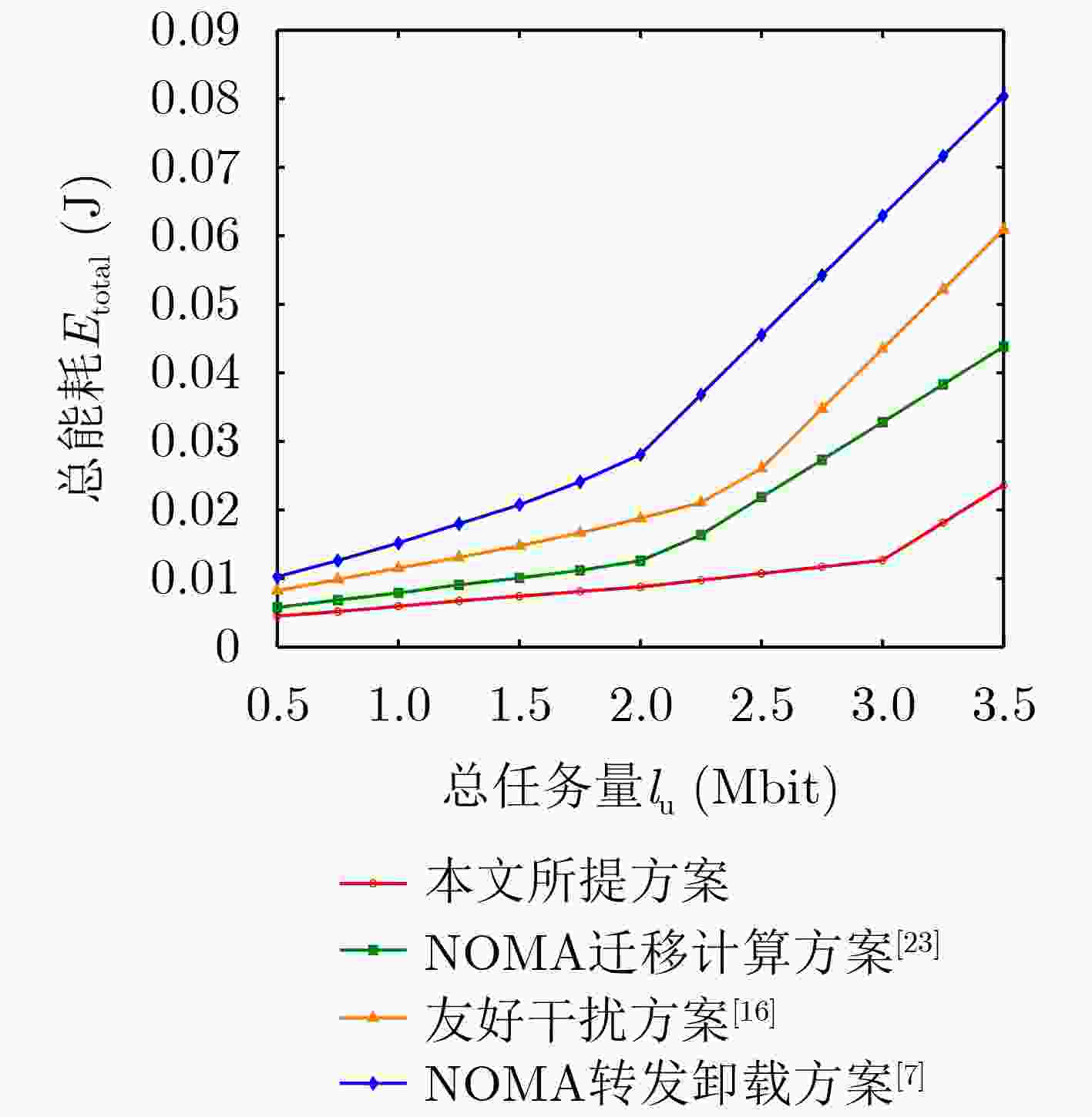
摘要: 为降低移动边缘计算(MEC)网络安全卸载过程的能耗,该文设计一种基于协作非正交多址(NOMA)的安全卸载模式,利用协作节点的通信和计算能力置换系统的安全性能。考虑设备计算和通信等资源分配的联合设计,该文提出保密中断概率(SOP)约束下的系统加权总能耗最小化问题。针对该非凸优化问题,将其分解为时隙与任务分配和功率分配两个子问题,并提出一种基于交替和逐次凸逼近(SCA)的迭代算法求解,依据信道状态和计算资源调整用户节点与协作节点之间的负载、功率和时隙分配。理论分析与仿真结果表明,所提算法收敛且具有低复杂度,相比于现有的NOMA转发卸载方案、友好干扰方案和NOMA迁移计算方案,可显著降低系统能耗,同时具备更高负载能力和更强的抗窃听能力,实现了节点在通信、计算和安全之间的权衡折衷。Abstract:
Objective Mobile Edge Computing (MEC) is used to strengthen the computational capability and response speed of mobile devices by shifting computing and caching functions to the network edge. Non-Orthogonal Multiple Access (NOMA) further supports high spectral efficiency and large-scale connectivity. Because wireless channels are broadcast, the MEC offload transmission process is exposed to potential eavesdropping. To address this risk, physical-layer security is integrated into a NOMA-MEC system to safeguard secure offloading. Existing studies mainly optimize performance metrics such as energy use, latency, and throughput, or improve security through NOMA-based co-channel interference and cooperative interference. However, the combined effect of performance and security has not been fully examined. To reduce the energy required for secure offloading, a cooperative NOMA secure offload scheme is designed. The distinctive feature of the proposed scheme is that cooperative nodes provide forwarding and computational assistance at the same time. Through joint local computation between users and cooperative nodes, the scheme strengthens security in the offload process while reducing system energy consumption. Methods The joint design of computational and communication resource allocation for the nodes is examined by dividing the offloading procedure into two stages: NOMA offloading and cooperative offloading. Offloading strategies for different nodes in each stage are considered, and an optimization problem is formulated to minimize the weighted total system energy consumption under secrecy outage constraints. To handle the coupled multi-variable and non-convex structure, secrecy transmission rate constraints and secrecy outage probability constraints, originally expressed in probabilistic form, are first transformed. The main optimization problem is then separated into two subproblems: slot and task allocation, and power allocation. For the non-convex power allocation subproblem, the non-convex constraints are replaced with bilinear substitutions, and sequential convex approximations are applied. An alternating iterative resource allocation algorithm is ultimately proposed, allowing the load, power, and slot assignment between users and cooperative nodes to be adjusted according to channel conditions so that energy consumption is minimized while security requirements are satisfied. Results and Discussions Theoretical analysis and simulation results show that the proposed scheme converges quickly and maintains low computational complexity. Relative to existing NOMA full-offloading schemes, assisted computing schemes, and NOMA cooperative interference schemes, the proposed offloading design reduces system energy consumption and supports a higher load under identical secrecy constraints. The scheme also demonstrates strong robustness, as its performance is less affected by weak channel conditions or increased eavesdropping capability. Conclusions The study shows that system energy consumption and security constraints are closely coupled. In the MECg offloading process, communication, computation, and security are not independent. Performance and security can be improved at the same time through the effective use of cooperative nodes. When cooperative nodes are present, NOMA and forwarding cooperation can reduce the effects of weak channel conditions or high eavesdropping risks on secure and reliable transmission. Cooperative nodes can also share users’ local computational load to strengthen overall system performance. Joint local computation between users and cooperative nodes further reduces the security risks associated with long-distance wireless transmission. Thus, secure offloading in MEC is not only a Physical Layer Security issue in wireless transmission but also reflects the coupled relationship between communication and computation that is specific to MEC. By making full use of idle resources in the network, cooperative communication and computation among idle nodes can enhance system security while maintaining performance. -
1 基于交替迭代的通算资源分配算法
1. 选取初始向量$ {{\boldsymbol{t}}_0} $, $ {{\boldsymbol{l}}_0} $,设置交替优化的迭代次数$ i = 0 $,最大
迭代次数$ {D_0} \gt 0 $和精度$ \delta _0^{{\text{tar}}} \gt 0 $, $ \delta_0^{\mathrm{var}} \gt 0 $;2. FOR $ i = 0:{D_0} $ 3. 内点法求解问题$ \text{P1-1} $,得到解$ {{\boldsymbol{t}}_{i + 1}} $和$ {{\boldsymbol{l}}_{i + 1}} $; 4. 选取初始向量$ {{\boldsymbol{p}}_0} $,设置SCA的迭代次数$ j = 0 $,最大迭代次
数$ {D_1} \gt 0 $和精度$ \delta _1^{{\text{tar}}} \gt 0 $, $ \delta_1^{\mathrm{var}} \gt 0 $;5. FOR $ j = 0:{D_1} $ 6. 内点法求解问题$ \text{P1-}\text{2}^{\boldsymbol{'}} $,得到解$ {{\boldsymbol{p}}_{j + 1}} $,并更新
$ {{\boldsymbol{p}}_{i + 1}} = {{\boldsymbol{p}}_{j + 1}} $;7. IF $ \left| {{E_{{\text{total}}}}({{\boldsymbol{p}}_j}) - {E_{{\text{total}}}}({{\boldsymbol{p}}_{j + 1}})} \right| \le \delta _1^{{\text{tar}}} $或
$ \left\| \boldsymbol{p}_j-\boldsymbol{p}_{j+1} \right\| \le\delta_1^{\mathrm{var}} $8. 获得问题$ {\text{P1-2}} $的解$ {{\boldsymbol{p}}_{i + 1}} $,BREAK; 9. ELSE $ j = j + 1 $; 10. END IF 11. END FOR 12. IF $ \left| {{E_{{\text{total}}}}({{\boldsymbol{t}}_i},{{\boldsymbol{l}}_i}) - {E_{{\text{total}}}}({{\boldsymbol{t}}_{i + 1}},{{\boldsymbol{l}}_{i + 1}})} \right| \le \delta _0^{{\text{tar}}} $或
$ \left\| [\boldsymbol{t}_i,\boldsymbol{l}_i]-[\boldsymbol{t}_{i+1},\boldsymbol{l}_{i+1}] \right\| \le\delta_0^{\mathrm{var}} $13. 获得问题$ {\text{P1}} $的解$ {{\boldsymbol{t}}_{i + 1}} $,$ {{\boldsymbol{p}}_{i + 1}} $,$ {{\boldsymbol{l}}_{i + 1}} $,BREAK; 14. ELSE $ i = i + 1 $; 15. END IF 16. END FOR 2 基于VIKOR的协作节点调度算法
1. 依据节点数目$ M $和属性维度$ N $构建VIKOR决策矩阵
$ {{\boldsymbol{W}}_{M \times N}} $;2. 归一化属性评估值$ {\sigma _{ij}} $; 3. FOR $ j = 0:N $ 4. FOR $ i = 0:M $ 5. 得到正理想解$ \sigma _j^ + = \{ {\max _i}{\sigma _{ij}}\} $和负理想解
$ \sigma _j^ - = \{ {\min _i}{\sigma _{ij}}\} $;6. END FOR 7. END FOR 8. FOR $ i = 0:M $ 9. 计算的群体效用值$ {S_i} $和个体遗憾值$ \mathit{\text{R}_i} $以及HEi的权重值$ {{Q}_i} $; 10. END FOR 11. 选取最优的协作节点$ \text{argmin}{{Q}_i},i\in M $; -
[1] CHEN Jingxuan, CAO Xianbin, YANG Peng, et al. Deep reinforcement learning based resource allocation in multi-UAV-aided MEC networks[J]. IEEE Transactions on Communications, 2023, 71(1): 296–309. doi: 10.1109/TCOMM.2022.3226193. [2] DJIGAL H, XU Jia, LIU Linfeng, et al. Machine and deep learning for resource allocation in multi-access edge computing: A survey[J]. IEEE Communications Surveys & Tutorials, 2022, 24(4): 2449–2494. doi: 10.1109/COMST.2022.3199544. [3] 周天清, 胡海琴, 曾新亮. NOMA-MEC系统中基于改进遗传算法的协作式计算卸载与资源管理[J]. 电子与信息学报, 2022, 44(9): 3014–3023. doi: 10.11999/JEIT220306.ZHOU Tianqing, HU Haiqin, and ZENG Xinliang. Cooperative computation offloading and resource management based on improved genetic algorithm in NOMA-MEC systems[J]. Journal of Electronics & Information Technology, 2022, 44(9): 3014–3023. doi: 10.11999/JEIT220306. [4] JIANG Hongbo, DAI Xingxia, XIAO Zhu, et al. Joint task offloading and resource allocation for energy-constrained mobile edge computing[J]. IEEE Transactions on Mobile Computing, 2023, 22(7): 4000–4015. doi: 10.1109/TMC.2022.3150432. [5] TAN Lin, KUANG Zhufang, ZHAO Lian, et al. Energy-efficient joint task offloading and resource allocation in OFDMA-based collaborative edge computing[J]. IEEE Transactions on Wireless Communications, 2022, 21(3): 1960–1972. doi: 10.1109/TWC.2021.3108641. [6] HAN Xiyu, LIAO Zhuofan, and TANG Xiaoyong. Pricing-based task offloading considering user energy consumption in MEC system[C]. 2024 IEEE International Symposium on Parallel and Distributed Processing with Applications, Kaifeng, China, 2024: 1911–1916. doi: 10.1109/ISPA63168.2024.00260. [7] 胡晗, 鲍楠, 凌章, 等. 基于NOMA的移动边缘计算系统公平能效调度算法[J]. 电子与信息学报, 2021, 43(12): 3563–3570. doi: 10.11999/JEIT200898.HU Han, BAO Nan, LING Zhang, et al. Fair energy efficiency scheduling in NOMA-based mobile edge computing[J]. Journal of Electronics & Information Technology, 2021, 43(12): 3563–3570. doi: 10.11999/JEIT200898. [8] DING Zhiguo, FAN Pingzhi, and POOR H V. Impact of non-orthogonal multiple access on the offloading of mobile edge computing[J]. IEEE Transactions on Communications, 2019, 67(1): 375–390. doi: 10.1109/TCOMM.2018.2870894. [9] WANG Lei, LIU Xin, JIANG Xue, et al. Effective computational efficiency maximization in cooperative NOMA based MEC system[C]. 2022 14th International Conference on Wireless Communications and Signal Processing, Nanjing, China, 2022: 788–793. doi: 10.1109/WCSP55476.2022.10039385. [10] ZENG Sheng, HUANG Xiaohong, and LI Dandan. Joint communication and computation cooperation in wireless-powered mobile-edge computing networks with NOMA[J]. IEEE Internet of Things Journal, 2023, 10(11): 9849–9862. doi: 10.1109/JIOT.2023.3236089. [11] RANAWEERA P, JURCUT A D, and LIYANAGE M. Survey on multi-access edge computing security and privacy[J]. IEEE Communications Surveys & Tutorials, 2021, 23(2): 1078–1124. doi: 10.1109/COMST.2021.3062546. [12] CHEN Yichao, ZHAO Kai, ZHANG Heng, et al. A comprehensive physical layer security mechanism for mobile edge computing[J]. IEEE Internet of Things Journal, 2023, 10(19): 16816–16829. doi: 10.1109/JIOT.2023.3272113. [13] WANG Qun, HU Han, SUN Haijian, et al. Secure and energy-efficient offloading and resource allocation in a NOMA-based MEC network[C]. 2020 IEEE/ACM Symposium on Edge Computing, San Jose, USA, 2020: 420–424. doi: 10.1109/SEC50012.2020.00063. [14] ZHENG Tongxing, CHEN Xin, WEN Yating, et al. Secure offloading in NOMA-enabled multi-access edge computing networks[J]. IEEE Transactions on Communications, 2024, 72(4): 2152–2165. doi: 10.1109/TCOMM.2023.3342242. [15] FU Xincheng, YU Xueyong, and WANG Shuyang. Optimization of energy consumption with hybrid cooperative NOMA for secure MEC[C]. 2022 4th International Academic Exchange Conference on Science and Technology Innovation, Guangzhou, China, 2022: 1279–1285. doi: 10.1109/IAECST57965.2022.10062073. [16] QIAN Liping, WU Weicong, LU Weidang, et al. Secrecy-based energy-efficient mobile edge computing via cooperative non-orthogonal multiple access transmission[J]. IEEE Transactions on Communications, 2021, 69(7): 4659–4677. doi: 10.1109/TCOMM.2021.3070620. [17] FANG Tao, YUAN Feng, AO Liang, et al. Joint task offloading, D2D pairing, and resource allocation in device-enhanced MEC: A potential game approach[J]. IEEE Internet of Things Journal, 2022, 9(5): 3226–3237. doi: 10.1109/JIOT.2021.3097754. [18] LONG Hao, XU Chen, ZHENG Guangyuan, et al. Socially-aware energy-efficient task partial offloading in MEC networks with D2D collaboration[J]. IEEE Transactions on Green Communications and Networking, 2022, 6(3): 1889–1902. doi: 10.1109/TGCN.2022.3153956. [19] YANG Long, CHEN Jian, JIANG Hai, et al. Optimal relay selection for secure cooperative communications with an adaptive eavesdropper[J]. IEEE Transactions on Wireless Communications, 2017, 16(1): 26–42. doi: 10.1109/TWC.2016.2617328. [20] WU Mengru, SONG Qingyang, GUO Lei, et al. Energy-efficient secure computation offloading in wireless powered mobile edge computing systems[J]. IEEE Transactions on Vehicular Technology, 2023, 72(5): 6907–6912. doi: 10.1109/TVT.2023.3236327. [21] MEHBODNIYA A, KALEEM F, YEN K K, et al. A fuzzy extension of VIKOR for target network selection in heterogeneous wireless environments[J]. Physical Communication, 2013, 7: 145–155. doi: 10.1016/j.phycom.2013.02.002. [22] BADEEL R, SUBRAMANIAM S K, MUHAMMED A, et al. A multicriteria decision-making framework for access point selection in hybrid LiFi/WiFi networks using integrated AHP–VIKOR technique[J]. Sensors, 2023, 23(3): 1312. doi: 10.3390/s23031312. [23] ZHANG Luyao and HAO Li. Delay minimization in NOMA-based cooperative Mobile Edge Computing(MEC) offloading[C]. 2024 IEEE International Workshop on Radio Frequency and Antenna Technologies, Shenzhen, China, 2024: 271–275. doi: 10.1109/iWRFAT61200.2024.10594572. [24] JAIN P and KAR P. Non-convex optimization for machine learning[J]. Foundations and Trends® in Machine Learning, 2017, 10(3/4): 142–363. doi: 10.1561/2200000058. -





 下载:
下载:







 下载:
下载:
