A Survey of Data Prefetcher Security on Modern Processors
-
摘要: 数据预取器是现代处理器用于提高性能的重要微架构组件。然而,由于在设计之初缺乏系统性的安全评估与考量,主流商用处理器中的预取器近年来被揭示出存在严重安全隐患,已被用于针对浏览器、操作系统和可信执行环境的侧信道攻击。面对这类新型微架构攻击,处理器安全研究亟需解决以下关键问题:如何系统性地分析攻击方法,全面认识预取器潜在风险,量化评估预取器安全程度,从而设计更加安全的数据预取器。为解决这些问题,该文系统调研了商用处理器中已知预取器设计及相关侧信道攻击,通过提取内存访问模式,为7种预取器建立行为模型,并基于此为20种侧信道攻击建立攻击模型,系统整理了各类攻击的触发条件和泄露信息,并分析可能存在的其他攻击方法。在此基础上,该文提出1套包含3个维度和24个指标的安全性评估体系,为数据预取器的安全性提供全面量化评估。最后,该文深入探讨了防御策略、安全预取器设计思路及未来研究方向。作为首篇聚焦于商用处理器数据预取器安全问题的综述性文章,该文有助于深入了解数据预取器面临的安全挑战,推动预取器的安全性量化评估体系构建,从而为设计更加安全的数据预取器提供指导。Abstract:
Significance The data prefetcher is a key microarchitectural component in modern processors, designed to enhance memory access performance by speculatively preloading data into the cache based on predictions of future access patterns. While effective at reducing cache misses, prefetcher design has historically neglected security considerations, resulting in various forms of information leakage. Recent studies have shown that data prefetchers can be exploited in side-channel attacks targeting cryptographic libraries, operating systems, hypervisors, and trusted execution environments. However, most existing attacks focus on specific implementations (eg., "one-spot" attacks) fail to comprehensively capture the broader attack surface exposed by diverse prefetcher designs. Two fundamental research questions remain open: (1) Do current attacks fully characterize all exploitable vectors in modern prefetchers, or are additional vectors yet to be explored? (2) How can the security of different prefetcher designs be systematically and quantitatively assessed to support comparative analysis and guide secure design? This paper addresses both questions through a systematic survey of data prefetcher attacks and a model-driven analysis. By generalizing known attack mechanisms, this work proposes a formalized framework for understanding and evaluating the security of data prefetchers. Methods To capture the behavior of data prefetchers, this study first presents a memory access model that specifies the instruction address, data address, and access attributes for each memory operation, which can be extended to represent access sequences. Building on this, a prefetcher model is proposed in which a prefetcher is trained by a sequence of memory accesses and triggered by a single access to generate a set of prefetches. Each prefetcher is characterized by design parameters. Attacker and victim profiles are then incorporated to construct attack models based on reduced memory access representations, enabling formalization of 20 known prefetcher-based attacks. Finally, a security evaluation framework is proposed, comprising 24 metrics across three dimensions—design parameters, isolation, and attack feasibility. This framework supports quantitative scoring and comparison of prefetcher designs. Results and Prospects In terms of attack modeling, the analysis shows that the 20 known attacks cover only a limited portion of the overall attack space. This study proposes several previously unexplored attack vectors, including those that exploit cache hit effects and speculative execution, attacks that leverage indexing collisions using instruction and data addresses, and additional side channels resulting from prefetcher-induced effects on other microarchitectural components, such as Translation Lookaside Buffer (TLB) state and cache coherence state. In terms of evaluation, this paper examines five commercial processors featuring different prefetchers: Intel’s Stride prefetcher and eXtended Page Table (XPT), AMD’s Stride prefetcher, Arm’s Spatial Memory Streaming (SMS) prefetcher, and Apple’s Data Memory Prefetcher (DMP). The findings reveal that all five prefetchers exhibit varying degrees of vulnerability to side-channel leakage, depending on their design parameters, isolation strategies, and the feasibility of exploitation. The paper further assesses three mitigation strategies and shows that while some measures substantially enhance security, residual risks remain, highlighting the need for improved countermeasures. Discussion Beyond characterizing existing attack vectors and evaluating the security of current prefetcher implementations, this study also outlines emerging directions for secure prefetcher design. Existing work primarily focuses on the Stride prefetcher, with preliminary defenses based on control registers that allow software to constrain the address range eligible for prefetching. This reduces the likelihood that secret-dependent memory accesses affect prefetcher state or trigger the prefetching of sensitive cache lines. Nevertheless, these approaches remain at an early stage, and a comprehensive framework for the systematic design of secure prefetchers has yet to be developed. Conclusions This paper presents a systematic study of data prefetcher security. It proposes a model-driven framework for analyzing potential attack vectors and introduces a quantitative method for evaluating prefetcher security. These contributions lay a theoretical foundation for identifying new attack mechanisms, guiding the development of effective countermeasures, and informing the secure design of data prefetchers in future processor architectures. -
Key words:
- Computer architecture /
- Processor /
- Data prefetcher /
- Microarchitectural security /
- Side channel attack
-
表 1 商用处理器中已发现数据预取器的关键设计参数以及求解这些参数的相关工作
预取器 参数声明 参数定义 Next-line $ {k}_{1} $: 跨页预取[49] $ {k}_{1}\in \left(\mathrm{0,1}\right) $, {$ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{p}\mathrm{p}\mathrm{g}\left(\left\langle a \right\rangle ,\left\langle a \right\rangle +1\right) $}: $ 0 $, $ a\to {k}_{1}(\left\langle a \right\rangle +1) $ Adjacent $ {k}_{1} $: 预取策略[36] $ {k}_{1}\in \left(-\mathrm{1,1}\right) $, {$ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{c}\mathrm{h}\mathrm{u}\mathrm{n}\mathrm{k}(\left\langle a \right\rangle ,\left\langle a \right\rangle +1) $}: $ 0 $, $ a\to \left\langle a \right\rangle +{k}_{1} $ Stride $ {k}_{1} $: 激活信心值[32,36] $ \left\lfloor{k}_{1}\right\rfloor $, {$ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}(a,s) $}: $ {\left[a\right]}_{{k}_{1},s},a+{k}_{1}s\to \left\langle a+({k}_{1}+1)s \right\rangle $ $ {k}_{2} $: 步长范围[30,32] $ \left\|{k}_{2}\right\| $, {$ n\ge {k}_{1} $}: $ {\left[a\right]}_{n,s} $, $ a+n{k}_{2}\to \left\langle a+(n+1){k}_{2} \right\rangle $ $ {k}_{3} $: 预取深度[36] $ \left\lceil{k}_{3}\right\rceil $, {$ n\ge {k}_{1} $, $ s\in \left\|{k}_{2}\right\| $}: $ {\left[a\right]}_{n,s} $, $ a+ns\to \left\langle a+(n+1){k}_{3} \right\rangle $ $ {k}_{4} $: 非等步长预取行为[30] $ {k}_{4}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ s\in \left\|{k}_{2}\right\| $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{c}\mathrm{l}(a+ns $, $ b) $}: $ {\left[a\right]}_{n,s} $, $ b\to {k}_{4}\left\langle b+s \right\rangle $ $ {k}_{5} $: 单次预取
数量[36]$ \left\|{k}_{5}\right\| $, {$ n\ge {k}_{1} $, $ s\in \left\|{k}_{2}\right\| $}: $ {\left[a\right]}_{n,s} $, $ a+ns\to \left\langle {[a+\left(n+1\right)s]}_{{k}_{5},s} \right\rangle $ $ {k}_{6} $: 小步长预取数量[38] $ \left\|{k}_{6}\right\| $, {$ \mathrm{s}\mathrm{a}\mathrm{m}\mathrm{e}\_\mathrm{c}\mathrm{l}\left({\left[a\right]}_{n,s}\right) $, $ c > 0 $}: $ {\left[{a}^{1,c}\right]}_{n,s} $, $ {a}^{1,c}+ns\to {\left\langle{\left\langle a \right\rangle +1}\right\rangle}_{{k}_{6},1} $ $ {k}_{7} $: PC 碰撞[30,32,36] $ {k}_{7}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ s\in \left\|{k}_{2}\right\| $, $ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}({i}_{1},{i}_{2}) $}: $ {\left[{a}^{{i}_{2}}\right]}_{n,s} $, $ {(a+ns)}^{{i}_{1}}\to {k}_{7}\left\langle a+\left(n+1\right)s \right\rangle $ $ {k}_{8} $: 数据地址碰撞[30] $ {k}_{8}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ s\in \left\|{k}_{2}\right\| $,$ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}(a,b) $}: $ {\left[\left(a,b\right)?\right]}_{n,s} $, $ a+ns\to {k}_{8}\left\langle a+\left(n+1\right)s \right\rangle $ $ {k}_{9} $: 随机块内偏移[36] $ {k}_{9}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ s\in \left\|{k}_{2}\right\| $, $ \mathrm{s}\mathrm{a}\mathrm{m}\mathrm{e}\_\mathrm{c}\mathrm{l}(a,b) $}: $ {[\left(a,b\right)?]}_{n,s} $, $ a+ns\to {k}_{9}\left\langle a+\left(n+1\right)s \right\rangle $ $ {k}_{10} $: 表项大小[32] $ \left\lceil{k}_{10}\right\rceil $, {$ n\ge {k}_{1} $, $ s\in \left\|{k}_{2}\right\| $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{p}\mathrm{p}\mathrm{g}(\left\langle {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{10}\right)} \right\rangle $ }: $ {[{\left[{a}^{i}\right]}_{n,s}{\text{~}}]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{10}\right),i:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{10}\right)} $, $ ({{a}_{1}+ns)}^{1}\to \left\langle {a}_{1}+\left(n+1\right)s \right\rangle $ $ {k}_{11} $: 跨页预取[30,32,36,37] $ {k}_{11}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ s\in \left\|{k}_{2}\right\| $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{p}\mathrm{p}\mathrm{g}(\left\langle a+ns \right\rangle ,\left\langle a+\left(n+1\right)s \right\rangle ) $}: $ {\left[a\right]}_{n,s} $, $ a+ns\to {k}_{11}\left\langle a+\left(n+1\right)s \right\rangle $ $ {k}_{12} $: 跨页训练[30,32] $ {k}_{12}\in \left(\mathrm{0,1}\right) $, {$ n={k}_{1} $, $ s\in \left\|{k}_{2}\right\|, $ $ \mathrm{s}\mathrm{a}\mathrm{m}\mathrm{e}\_\mathrm{p}\mathrm{p}\mathrm{g}\left(\left\langle {\left[a\right]}_{n-1,s} \right\rangle \right) $, $ \mathrm{s}\mathrm{a}\mathrm{m}\mathrm{e}\_\mathrm{p}\mathrm{p}\mathrm{g}\left(\left\langle {\left[a+(n-1)s\right]}_{3,s} \right\rangle \right) $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{p}\mathrm{p}\mathrm{g}(\left\langle a+(n-2)s \right\rangle ,\left\langle a+(n-1)s \right\rangle ) $}: $ {\left[a\right]}_{n,s} $, $ (a+ns)\to {k}_{12}\left\langle a+\left(n+1\right)s \right\rangle $ $ {k}_{13} $: 瞬态训练[30] $ {k}_{13}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ s\in \left\|{k}_{2}\right\| $}: $ {\left[\bar{a}\right]}_{n,s} $, $ a+ns\to {k}_{13}\left\langle a+\left(n+1\right)s \right\rangle $ $ {k}_{14} $: 瞬态预取[30] $ {k}_{14}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ s\in \left\|{k}_{2}\right\| $}: $ {\left[a\right]}_{n,s} $, $ \bar{a}+ns\to {k}_{14}\left\langle a+\left(n+1\right)s \right\rangle $ $ {k}_{15} $: 交叉训练[37] $ {k}_{15}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ s\in\left\|{k}_{2}\right\| $, $ 2\le y\le {k}_{10} $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{p}\mathrm{p}\mathrm{g}\left(\left\langle {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(y\right)} \right\rangle \right) $}: $ \left({{[\left[a\right]}_{n,s}~]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(y\right)}\right)! $, $ {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(y\right)}+ns\to {k}_{15}\left\langle {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(y\right)}+(n+1)s \right\rangle $ $ {k}_{16} $: Cache 命中影响[37] $ {k}_{16}\in \left(\mathrm{0,1}\right) $, {$ n={k}_{1}+2 $, $ s\in \left\|{k}_{2}\right\| $, $ c > \text{0} $}: $ {\left[{a}^{1}\right]}_{n-2,s}{\left(a+\left(n-2\right)s\right)}^{1,c}{\left(a+\left(n-1\right)s\right)}^{1} $,$ {\left(a+ns\right)}^{1}\to {k}_{16}\left\langle a+\left(n+1\right)s \right\rangle $ Stream $ {k}_{1} $: 流表初始化[49] $ \left\|{k}_{1}\right\|$, {$ d\in (-\mathrm{1,1}) $}: $ 0 $, $ a\to {\left\langle \left\langle a \right\rangle +d \right\rangle }_{{k}_{1},d} $ $ {k}_{2} $: 流向
初始化[49,50]$ {k}_{2}\in (-\mathrm{1,1}) $, {}: $ {a}_{1} $, $ {a}_{2}\to {\left\langle \left\langle {a}_{2} \right\rangle +{k}_{2} \right\rangle }_{2,{k}_{2}} $ $ {k}_{3} $: 流向更新[49,50] $ {k}_{3}\in (-\mathrm{1,1}) $, $\left\|{k}_{4}\right\| $, {}: $ {a}_{1}{a}_{2} $, $ {a}_{3}\to {\left\langle \left\langle {a}_{3} \right\rangle +{k}_{3} \right\rangle }_{{k}_{4},{k}_{3}} $ $ {k}_{4} $: 预取数量[49,50] $ {k}_{5} $: 表项大小[50] $\left\lceil{k}_{5}\right\rceil $, {$ y={k}_{2} $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{p}\mathrm{p}\mathrm{g}\left(\left\langle {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{5}\right)} \right\rangle \right) $}: $ {[{\left[{a}^{i}\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(2\right)}{\text{~}}]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{5}\right),i:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{5}\right)} $, $ {a}_{\mathrm{1,3}}\to {\left\langle \left\langle {a}_{\mathrm{1,3}} \right\rangle +y \right\rangle }_{2,y} $ $ {k}_{6} $: 跨页预取[50] $ {k}_{6}\in \left(\mathrm{0,1}\right) $, {$ y={k}_{2} $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{p}\mathrm{p}\mathrm{g}(\left\langle {a}_{1} \right\rangle ,\left\langle {a}_{2} \right\rangle ) $}: $ {a}_{1} $, $ {a}_{2}\to {k}_{6}{\left\langle \left\langle {a}_{2} \right\rangle +y \right\rangle }_{2,y} $ $ {k}_{7} $: Cache命中影响[49] $ {k}_{7}\in \left(\mathrm{0,1}\right) $, {$ y={k}_{3} $, $ x={k}_{4} $, $ c > 0 $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{c}\mathrm{l}\left({a}_{1},{a}_{2},{a}_{3}\right) $}: $ {a}_{1}^{1}{a}_{2}^{1,c} $, $ {a}_{3}^{1}\to {k}_{7}{\left\langle \left\langle {a}_{3} \right\rangle +y \right\rangle }_{x,y} $ XPT $ {k}_{1} $: 激活信心值[33] $ \left\lfloor{k}_{1}\right\rfloor $: $ {\left[a\right]}_{{k}_{1}} $, $ a\to \left\langle a \right\rangle $ $ {k}_{2} $: 数据地址
碰撞[33]$ {k}_{2}\in \left(\mathrm{0,1}\right) $, {$ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}(a,b) $, $ n\ge {k}_{1} $}: $ {[\left(a,b\right)?]}_{n} $, $ a\to {k}_{2}\left\langle a \right\rangle $ $ {k}_{3} $: PC碰撞[33] $ {k}_{3}\in \left(\mathrm{0,1}\right) $, {$ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}({i}_{1},{i}_{2}) $, $ \mathrm{s}\mathrm{a}\mathrm{m}\mathrm{e}\_\mathrm{c}\mathrm{l}({a}_{1},{a}_{2}) $, $ n\ge {k}_{1} $}: $ {\left[{a}_{1}^{{i}_{1}}\right]}_{n} $, $ {a}_{2}^{{i}_{2}}\to {k}_{3}\left\langle {a}_{1} \right\rangle $ $ {k}_{4} $: 是否跨页[33] $ {k}_{4}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}(a,b) $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{p}\mathrm{p}\mathrm{g}(\left\langle a \right\rangle ,\left\langle b \right\rangle ) $}: $ {\left[a\right]}_{n} $, $ b\to {k}_{4}\left\langle b \right\rangle $ $ {k}_{5} $: 表项大小[33] $ \left\lceil {k}_{5}\right\rceil $, {$ n\ge {k}_{1} $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{p}\mathrm{p}\mathrm{g}\left(\left\langle {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{5}\right)} \right\rangle \right) $}: $ {[{\left[{a}^{i}\right]}_{n}{\text{~}}]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{5}\right),i:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{5}\right)} $, $ {a}_{1}^{1}\to \left\langle a \right\rangle $ $ {k}_{6} $: 相联度[33] $ \left\lfloor{k}_{6}\right\rfloor $, {$ \text{n}\ge {k}_{1} $, $ \text{same\_lsb}({\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{6}+1\right)},{\mathrm{log}}_{2}\frac{4096{k}_{5}}{{k}_{6}}) $, $ \text{diff\_ppg}(\left\langle {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{6}+1\right)} \right\rangle $}: $ {[{\left[{a}^{i}\right]}_{n}{\text{~}}]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{6}+1\right),i:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}({k}_{6}+1)} $, $ {a}_{1}^{1}\to 0 $ $ {k}_{7} $: 替换策略 (LRU)[33] $ {k}_{7}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ y={k}_{6} $, $ \mathrm{s}\mathrm{a}\mathrm{m}\mathrm{e}\_\mathrm{l}\mathrm{s}\mathrm{b}({\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{6}+1\right)},{\mathrm{log}}_{2}\frac{4096{k}_{5}}{{k}_{6}}) $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{p}\mathrm{p}\mathrm{g}(\left\langle {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(y+1\right)} \right\rangle $}: $ {[{\left[{a}^{i}\right]}_{n}~]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(y\right),i:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(y\right)}{a}_{1}^{1}{a}_{y+1}^{y+1} $, $ {a}_{1}^{1}\to {k}_{7}\left\langle {a}_{1}^{1} \right\rangle $ SMS $ {k}_{1} $: 激活次数[36] $ \left\lfloor {k}_{1}\right\rfloor $, {$ {k}_{1}\ge 2 $, $ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}\left(b\right) $}: $ {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{1}\right)} $, $ b\to \left\langle b+{\left[\right(a-{a}_{1}\left)\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}(2,{k}_{1})} \right\rangle $ $ {k}_{2} $: 低地址预取
数量[36]$ \left\lceil{k}_{2}\right\rceil $, {$ {k}_{2}\ge {k}_{1} $, $ \mathrm{i}\mathrm{s}\_\mathrm{m}\mathrm{a}\mathrm{x}\mathrm{i}\mathrm{m}\mathrm{u}\mathrm{m}({\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{2}\right)},{a}_{1}) $, $ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}\left(b\right) $}: $ {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{2}\right)} $, $ b\to \left\langle b+{\left[\right(a-{a}_{1}\left)\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}(2,{k}_{2})} \right\rangle $ $ {k}_{3} $: 高地址预取
数量[36]$ \left\lceil{k}_{3}\right\rceil $, {$ \mathrm{i}\mathrm{s}\_\mathrm{m}\mathrm{i}\mathrm{n}\mathrm{i}\mathrm{n}\mathrm{u}\mathrm{m}({\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{3}\right)},{a}_{1}) $, $ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}\left(b\right) $}: $ {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{3}\right)} $, $ b\to \left\langle b+{\left[\right(a-{a}_{1}\left)\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}(2,{k}_{3})} \right\rangle $ $ {k}_{4} $: 预取边界[36] $ \left\|{k}_{4}\right\| $, {$ n={k}_{1} $, $ {a}_{n}=a+{k}_{4} $, $ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}\left(b\right) $}: $ {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(n\right)} $, $ b\to \left\langle b+{\left[\right(a-{a}_{1}\left)\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}(2,n)} \right\rangle $ $ {k}_{5} $: 数据地址碰撞[36] $ {k}_{5}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}\left(b\right) $, $ \mathrm{d}\mathrm{i}\mathrm{f}\mathrm{f}\_\mathrm{p}\mathrm{p}\mathrm{g}(\left\langle {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(n\right)} \right\rangle ,\left\langle b \right\rangle ) $}: $ {\left[\left(a,b\right)!\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(n\right)} $, $ b\to {k}_{5}\left\langle b+{\left[\right(a-{a}_{1}\left)\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}(2,n)} \right\rangle $ $ {k}_{6} $: PC碰撞[36] $ {k}_{6}\in \left(\mathrm{0,1}\right) $, {$ n\ge {k}_{1} $, $ \mathrm{e}\mathrm{x}\mathrm{i}\mathrm{s}\mathrm{t}({i}_{1},{i}_{2},b) $}: $ {\left[{a}^{{i}_{1}}\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left(n\right)} $, $ {b}^{{i}_{2}}\to {k}_{6}\left\langle b+{\left[\right(a-{a}_{1}\left)\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}(2,n)} \right\rangle $ DMP $ {k}_{1} $: 预取数量和
位置[31]$ \left\|{k}_{1}\right\| $: $ 0 $, $ a\to \left\langle {\left[{}_{8}{}^{\mathrm{*}}a\right]}_{8,{k}_{1}} \right\rangle $ $ {k}_{2} $: 历史过滤[31] $ {k}_{2}\in \left(\mathrm{0,1}\right) $, {$ \text{n}\in \left\|{k}_{1}\right\| $}: $ \text{a} $, $ a\to {k}_{2}\left\langle {\left[{}_{8}{}^{*}a\right]}_{8,n} \right\rangle $ $ {k}_{3} $: 历史过滤器
大小[31]$ \left\lfloor{k}_{3}\right\rfloor $, {$ \text{n}\in \left\|{k}_{1}\right\| $}: $ {\left[a\right]}_{a:\mathrm{r}\mathrm{a}\mathrm{n}\mathrm{g}\mathrm{e}\left({k}_{3}\right)} $, $ {a}_{1}\to \left\langle {\left[{}_{8}{}^{*}a\right]}_{8,n} \right\rangle $ $ {k}_{4} $: 预取范围[31] $ \left\|{k}_{4}\right\| $, {$ {}_{8}{}^{*}a\in {k}_{4} $, $ n\in \left\|{k}_{1}\right\| $}: $ \text{0} $, $ a\to \left\langle {\left[{}_{8}{}^{*}a\right]}_{8,n} \right\rangle $ $ {k}_{5} $: 瞬态预取[35] $ {k}_{5}\in \left(\mathrm{0,1}\right) $, {$ n\in \left\|{k}_{1}\right\| $}: $ 0 $, $ \stackrel{-}{a}\to {k}_{5}\left\langle {\left[{}_{8}{}^{*}a\right]}_{8,n} \right\rangle $ $ {k}_{6} $: L2 Cache命中
影响[31]$ {k}_{6}\in \left(\mathrm{0,1}\right) $, {$ c=2 $, $ n\in \left\|{k}_{1}\right\| $}: 0, $ {a}^{1,c}\to {k}_{6}\left\langle {\left[{}_{8}{}^{*}a\right]}_{8,n} \right\rangle $ $ {k}_{7} $: L1 Cache命中
影响[31]$ {k}_{7}\in \left(\mathrm{0,1}\right) $, {$ c=3 $, $ n\in \left\|{k}_{1}\right\| $}: 0, $ {a}^{1,c}\to {k}_{7}\left\langle {\left[{}_{8}{}^{*}a\right]}_{8,n} \right\rangle $ $ {k}_{8} $: TLB miss[35] $ {k}_{8}\in \left(\mathrm{0,1}\right) $, {$ c=0 $, $ t=0 $, $ n\in \left\|{k}_{1}\right\| $}: 0, $ {a}^{1,c,t}\to {k}_{8}\left\langle {\left[{}_{8}{}^{*}a\right]}_{8,n} \right\rangle $ 表 2 预取器设计参数简化
预取器 参数简化 Next-line $ {k}_{1}=0 $ Adjacent $ {k}_{1}=1 $ Stream $ {k}_{1}=0 $, $ {k}_{2}=1 $, $ {k}_{3}={a}_{1} > {a}_{2}?1:-1 $, $ {k}_{4}=\left[\mathrm{1,1}\right] $, $ {k}_{5}=1 $, $ {k}_{6}=0 $, $ {k}_{7}=1 $ Stride $ {k}_{1}=3 $, $ {k}_{2}=\left[\mathrm{1,1024}\right] $, $ {k}_{3}=1 $, $ {k}_{4}=1 $, $ {k}_{5}=\left[\mathrm{1,1}\right] $, $ {k}_{6}=\left[\mathrm{1,2}\right] $, $ {k}_{7}=1 $, $ {k}_{8}=1 $, $ {k}_{9}=1 $, $ {k}_{10}=1 $,
$ {k}_{11}=1 $, $ {k}_{12}=1 $, $ {k}_{13}=1 $, $ {k}_{14}=1 $, $ {k}_{15}=0 $, $ {k}_{16}=0 $XPT $ {k}_{1}=1 $, $ {k}_{2}=0 $, $ {k}_{3}=0 $, $ {k}_{4}=0 $, $ {k}_{5}=1 $, $ {k}_{6}=1 $, $ {k}_{7}=1 $ SMS $ {k}_{1}=1 $, $ {k}_{2}=1 $, $ {k}_{3}=1 $, $ {k}_{4}=1024 $, $ {k}_{5}=0 $, $ {k}_{6}=1 $ DMP $ {k}_{1}=1 $, $ {k}_{2}=1 $, $ {k}_{3}=1 $, $ {k}_{4}=[64,{2}^{32}] $, $ {k}_{5}=1 $, $ {k}_{6}=0 $, $ {k}_{7}=0 $, $ {k}_{8}=1 $ 注:表2所列参数的取值不表示实际情况,而仅用于描述一个简化后的模型。 表 3 预取器侧信道攻击模型
攻击原语 预取器 攻击模型 类型 秘密值 利用场景 Next-line-SCA[48] Next-line $ V\left(a\right)\to \left\langle a \right\rangle +1 $ Content 数据流 CLEFIA Stream-CC[50] Stream $ V{(a}_{1}) $, $ V\left({a}_{2}\right),V\left({a}_{3}\right)\to \left\langle {a}_{3} \right\rangle +1 $ Content 数据流 隐蔽信道 Stride-CC[52] Stride $ A\left(b\right) $, $ A(b+s) $, $ A\left(b+2s\right) $,$ V\left(a\right) $, $ V(a+s) $, $ V(a+2s)\to \left\langle b+3s \right\rangle $ Eviction 数据流 隐蔽信道 Stride-SCA[38,39] Stride $ V\left(a\right) $, $ V(a+s) $, $ V(a+2s)\to \left\langle a+3s \right\rangle $ Content 数据流 AES, ECDH PRFCF[37] Stride $ V\left(c\right) $, $ V(c+s) $, $ V\left(\mathrm{A}\mathrm{L}\mathrm{U}\left(a\right)\right) $, $ V(c+2s)\to \left\langle c+3s \right\rangle $ Content 控制流 隐蔽信道 PRFIS[37] Stride $ V\left({c}^{1}\right) $, $ V\left({(c+s)}^{1}\right) $, $ V\left({a}^{\mathrm{1,3}}\right) $, $ V\left({(c+2s)}^{1}\right)\to \left\langle c+6s \right\rangle $ Content 数据流 隐蔽信道 PRFOS[37] Stride $ V\left(c\right) $, $ V(c+s) $, $ V\left(a\right) $, $ V(c+2s)\to \left\langle c+3s \right\rangle $ Content 数据流 隐蔽信道 AfterImage-V1[32] Stride $ A\left({b}^{{i}_{1}}\right) $, $ A\left({(b+s)}^{{i}_{1}}\right) $, $ A\left({(b+2s)}^{{i}_{1}}\right) $, $ V\left({a}^{{i}_{2}}\right)\to \left\langle a+s \right\rangle $ Content 控制流 隐蔽信道 AfterImage-V2[32] Stride $ A\left({b}^{{i}_{1}}\right) $, $ A\left({(b+s)}^{{i}_{1}}\right) $, $ A\left({(b+2s)}^{{i}_{1}}\right) $, $ V\left({a}^{{i}_{2}}\right)\to \left\langle b+3s \right\rangle $ Content 控制流 RSA,中断检测 ShadowLoad-V1[30] Stride $ A\left({d}^{{i}_{1}}\right) $, $ A\left({(d+s)}^{{i}_{1}}\right) $, $ A\left({(d+2s)}^{{i}_{1}}\right) $, $ V\left({a}^{{i}_{2}}\right)\to \left\langle a+s \right\rangle $ Content 数据流 KASLR ShadowLoad-V2[30] Stride $ A\left({d}^{{i}_{1}}\right) $, $ A\left({(d+s)}^{{i}_{1}}\right) $, $ A\left({(d+2s)}^{{i}_{1}}\right) $, $ V\left({\stackrel{-}{a}}^{{i}_{2}}\right)\to \left\langle a+s \right\rangle $ Content 数据流 瞬态执行 FetchProbe-V1[30] Stride $ V\left({a}^{{i}_{1}}\right) $, $ A\left({d}^{{i}_{2}}\right) $, $ A\left({(d+s)}^{{i}_{2}}\right) $, $ A\left({(d+2s)}^{{i}_{2}}\right)\to \left\langle d+3s \right\rangle $ Content 数据流 Base64 FetchProbe-V2[30] Stride $ V\left({\stackrel{-}{a}}^{{i}_{1}}\right) $, $ A\left({d}^{{i}_{2}}\right) $, $ A\left({(d+s)}^{{i}_{2}}\right) $, $ A\left({(d+2s)}^{{i}_{2}}\right)\to \left\langle d+3s \right\rangle $ Content 数据流 瞬态执行 Prime-Reset[34] Stride $ A\left(b\right) $, $ A(b+s) $, $ A\left(b+2s\right),V\left(\mathrm{I}\mathrm{N}\mathrm{V}\right(a\left)\right)\to \left\langle b+3s \right\rangle $ Eviction 控制流 隐蔽信道 PrefetchX-V1[33] XPT $ A\left(b\right) $, $ V\left(a\right)\to \left\langle b \right\rangle $ Eviction 控制流 隐蔽信道,中断
检测,RSAPrefetchX-V2[33] XPT $ V\left(c\right)\text{,}V\left(a\right)\to \left\langle a \right\rangle $ Content 数据流 隐蔽信道 SMS-SCA[36] SMS $ V\left({a}^{{i}_{1}}\right) $, $ V\left({(a+s)}^{{i}_{1}}\right) $, $ A\left({b}^{{i}_{2}}\right)\to \left\langle b+s \right\rangle $ Content 数据流 AES,隐蔽信道 Augury-V1[35] DMP $ V\left({}_{8}{}^{\mathrm{*}}(a-24)\right) $,$ V\left({}_{8}{}^{\mathrm{*}}(a-16)\right)\text{,} $ $ V({}_{8}{}^{\mathrm{*}}a-8)\to \left\langle {}_{8}{}^{\mathrm{*}}a \right\rangle $ Content 数据流 绕过“幽灵”防御 Augury-V2[35] DMP $ V\left(\stackrel{-}{{}_{8}{}^{\mathrm{*}}(a-24)}\right) $, $ V\left(\stackrel{-}{{}_{8}{}^{\mathrm{*}}(a-16)}\right) $, $ V\left(\stackrel{-}{{}_{8}{}^{\mathrm{*}}a-8}\right)\to \left\langle {}_{8}{}^{\mathrm{*}}a \right\rangle $ Content 数据流 ASLR GoFetch[31] DMP $ V\left(a\right)\to \left\langle {}_{8}{}^{\mathrm{*}}a \right\rangle $ Content 数据流 DH, RSA, Kyber,
Dilithium表 4 预取器安全性评估指标
评估项 子项 评估指标 评估项 子项 评估指标 设计
参数$ {p}_{1}~{p}_{12} $激活长度 0或1 (4); 2(3); 3(2); 4+(1) 隔离性
$ {i}_{1}~{i}_{6} $同进程沙盒逃逸 可碰撞(0.2); 争用 (0.1); 隔离 (0) 预取数量 1 (1); 2+ (2) 跨核 可碰撞(0.2); 争用 (0.1); 隔离 (0) 预取深度(Byte) 63- (1); 64+, 4095 - (2);4096 + (4)跨进程 可碰撞(0.2); 争用 (0.1); 隔离 (0) 表项大小 7- (2); 8+ (1) 跨域-内核 可碰撞(0.2); 争用 (0.1); 隔离 (0) 是否可跨页训练 是 (4); 否 (0) 跨域-虚拟机 可碰撞(0.2); 争用 (0.1); 隔离 (0) 是否可跨页预取 是 (5); 否 (0) 跨域-可信执行环境 可碰撞(1); 争用 (0.5); 隔离 (0) 是否可推测训练 是 (4); 否 (0) 泄露粒度(Byte) 63-(1); 64+, 4095 - (0.9);4096 + (0.8)是否可推测预取 是 (5); 否 (0) 可利用性
$ {e}_{1}~{e}_{6} $是否跨页泄露 是 (1); 否 (0.9) cache命中是否影响 是 (4); 否 (0) 是否需预训练 是 (0.9); 否 (1) cache line内是否训练 是 (4); 否 (0) 是否需特权 是 (0.5); 否 (1) 是否PC碰撞 是 (6); 否 (0) 是否受指令流影响 是 (0.95); 否 (1) 是否数据地址碰撞 是 (6); 否 (0) 是否受数据流影响 是 (0.95); 否 (1) 表 5 数据预取器安全性评估案例分析
预取器 参数简化 评估结果 设计参数 隔离性 利用难度 UH H1 H2 H3 Intel Coffee Lake Stride 预取器[30,32,36] (2,2,2,0,0,4,5,4,4,6,6,1) (0.2,0,0.2,0.2,0.2,1) (1,0.9,0.9,1,1,0.95) 49.9 5.5 18.5 33.2 AMD Zen2 Stride 预取器[30,36] (2,2,4,4,5,4,5,4*,0,6,6,1) (0.2,0,0.2,0.2,0.2,1*) (0.9,0.9,0.9,1,1,0.95) 53.6 6.0 21.5 37.7 Intel Ice Lake XPT[33] (1,1,1,0,0,4*,5*,0*,0*,0,0,1) (0.2,0.1,0.1,0.1,0.1*,0.5*) (0.8,1,0.9,1,1,0.95) 9.8 1.8 9.8 2.5 Arm Cortex-A72 SMS预取器[36] (3,2,2,4,0,4*,5*,0*,0,6,0*,2) (0.2,0,0.2,0.2,0.2*,1) (0.9,1,0.9,1,1,0.95) 38.8 4.3 17.0 23.4 Apple M3 DMP[31,35,36] (4,2,4,4,5,4,5,0,4,0,0,2) (0.2,0.2*,0.2,0.2*,0.2*,1*) (1,1,1,1,1,1) 68.0 68.0 68.0 45.0 注:*表示目前仍未知的评估参数,并根据参考文献和处理器厂商开源文档的信息给出估计值。对于文献已经给出的评估参数,在满足表1定义的前提下,以最新论文的数据为准。 表 6 预取器组合侧信道的潜在攻击模型示例
可能的攻击原语 预取器 可能的攻击模型 可能的利用场景 Combination-V1 Stride, Stream $ V\left(a\right),V\left(a+s\right),V\left(a+2s\right),A\left(a+3s+1\right)\to \left\langle{a+3s}\right\rangle+2 $ 攻击者地址受限时的跨页数据泄露 Combination-V2 Stride, DMP $ A\left(b\right),A\left(b+s\right),A\left(b+2s\right),V\left(a\right)\to \left\langle{{}_{8}{}^{*}(a+s)}\right\rangle $ 受害者访问地址有限时的数据泄露 Combination-V3 Stride, DMP $ V\left(a\right),V\left(a+s\right),V\left(a+2s\right)\to \left\langle {\left[{}_{8}{}^{*}a\right]}_{\mathrm{8,24}s} \right\rangle $ 降低Stride预取器侧信道的噪声 Combination-V4 Stream, XPT $ A{(a}_{1}) $, $ A\left({a}_{2}\right),A\left({a}_{3}\right)\to \left\langle {a}_{3} \right\rangle $ 优化XPT驱逐集构建过程 Combination-V5 Stride, SMS $ V\left(a\right),V\left(a+s\right),V\left(a+2s\right),V\left(c\right),V\left(c+s\right),V\left(c+2s\right), $
$ A\left(b\right)\to \left\langle{b+a-c}\right\rangle $优化Stride预取器探测并行度 -
[1] LIPP M, SCHWARZ M, GRUSS D, et al. Meltdown: Reading kernel memory from user space[C]. The 27th USENIX Conference on Security Symposium, Baltimore, USA, 2018: 973–990. [2] KOCHER P, HORN J, FOGH A, et al. Spectre attacks: Exploiting speculative execution[C]. 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2019: 1–19. doi: 10.1109/SP.2019.00002. [3] VON BULCK J, MINKIN M, WEISSE O, et al. Foreshadow: Extracting the keys to the Intel SGX kingdom with transient out-of-order execution[C]. The 27th USENIX Conference on Security Symposium, Baltimore, USA, 2018: 991–1008. [4] CANELLA C, GENKIN D, GINER L, et al. Fallout: Leaking data on meltdown-resistant CPUs[C]. The 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 2019: 769–784. doi: 10.1145/3319535.3363219. [5] SCHWARZ M, LIPP M, MOGHIMI D, et al. ZombieLoad: Cross-privilege-boundary data sampling[C]. The 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 2019: 753–768. doi: 10.1145/3319535.3354252. [6] VAN SCHAIK S, MILBURN A, ÖSTERLUND S, et al. RIDL: Rogue in-flight data load[C]. 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2019: 88–105. doi: 10.1109/SP.2019.00087. [7] RAGAB H, BARBERIS E, BOS H, et al. Rage against the machine clear: A systematic analysis of machine clears and their implications for transient execution attacks[C]. The 30th USENIX Security Symposium, 2021: 1451–1468. [8] MOGHIMI D. Downfall: Exploiting speculative data gathering[C]. The 32nd USENIX Conference on Security Symposium, Anaheim, USA, 2023: 7179–7193. [9] BARBERIS E, FRIGO P, MUENCH M, et al. Branch history injection: On the effectiveness of hardware mitigations against cross-privilege spectre-v2 attacks[C]. The 31st USENIX Security Symposium, Boston, USA, 2022: 971–988. [10] BEHNIA M, SAHU P, PACCAGNELLA R, et al. Speculative interference attacks: Breaking invisible speculation schemes[C]. The 26th ACM International Conference on Architectural Support for Programming Languages and Operating Systems, 2021: 1046–1060. doi: 10.1145/3445814.3446708. [11] BHATTACHARYYA A, SANDULESCU A, NEUGSCHWANDTNER M, et al. SMoTherSpectre: Exploiting speculative execution through port contention[C]. The 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 2019: 785–800. doi: 10.1145/3319535.3363194. [12] REN Xida, MOODY L, TARAM M, et al. I see dead μops: Leaking secrets via Intel/AMD micro-op caches[C]. 2021 ACM/IEEE 48th Annual International Symposium on Computer Architecture (ISCA), Valencia, Spain, 2021: 361–374. doi: 10.1109/ISCA52012.2021.00036. [13] YAROM Y and FALKNER K. FLUSH+RELOAD: A high resolution, low noise, L3 cache side-channel attack[C]. The 23rd USENIX Conference on Security Symposium, San Diego, USA, 2014: 719–732. [14] LIU Fangfei, YAROM Y, GE Qian, et al. Last-level cache side-channel attacks are practical[C]. 2015 IEEE Symposium on Security and Privacy, San Jose, USA, 2015: 605–622. doi: 10.1109/SP.2015.43. [15] GRUSS D, MAURICE C, WAGNER K, et al. Flush+Flush: A fast and stealthy cache attack[C]. The 13th International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, San Sebastián, Spain, 2016: 279–299. doi: 10.1007/978-3-319-40667-1_14. [16] GUO Yanan, XIN Xin, ZHANG Youtao, et al. Leaky Way: A conflict-based cache covert channel bypassing set associativity[C]. 2022 55th IEEE/ACM International Symposium on Microarchitecture (MICRO), Chicago, USA, 2022: 646–661. doi: 10.1109/MICRO56248.2022.00053. [17] ZHANG Ruiyi, GERLACH L, WEBER D, et al. CacheWarp: Software-based fault injection using selective state reset[C]. The 33rd USENIX Conference on Security Symposium, Philadelphia, USA, 2024: 64. [18] DENG Shuwen, XIONG Wenjie, and SZEFER J. A benchmark suite for evaluating caches’ vulnerability to timing attacks[C]. The 25th ACM International Conference on Architectural Support for Programming Languages and Operating Systems, Lausanne, Switzerland, 2020: 683–697. doi: 10.1145/3373376.3378510. [19] GRAS B, RAZAVI K, BOS H, et al. Translation leak-aside buffer: Defeating cache side-channel protections with TLB attacks[C]. The 27th USENIX Conference on Security Symposium, Baltimore, USA, 2018: 955–972. [20] TATAR A, TRUJILLO D, GIUFFRIDA C, et al. TLB; DR: Enhancing TLB-based attacks with TLB desynchronized reverse engineering[C]. The 31st USENIX Security Symposium, Boston, USA, 2022: 989–1007. [21] DENG Shuwen, XIONG Wenjie, and SZEFER J. Secure TLBs[C]. The 46th International Symposium on Computer Architecture, Phoenix, USA, 2019: 346–359. doi: 10.1145/3307650.3322238. [22] LIPP M, GRUSS D, and SCHWARZ M. AMD prefetch attacks through power and time[C]. The 31st USENIX Security Symposium, Boston, USA, 2022: 643–660. [23] YAVARZADEH H, AGARWAL A, CHRISTMAN M, et al. Pathfinder: High-resolution control-flow attacks exploiting the conditional branch predictor[C]. The 29th ACM International Conference on Architectural Support for Programming Languages and Operating Systems, La Jolla, USA, 2024: 770–784. doi: 10.1145/3620666.3651382. [24] YU Jiyong, JAEGER T, and FLETCHER C W. All your PC are belong to Us: Exploiting non-control-transfer instruction BTB updates for dynamic PC extraction[C]. The 50th Annual International Symposium on Computer Architecture, Orlando, USA, 2023: 1–14. doi: 10.1145/3579371.3589100. [25] LI Luyi, YAVARZADEH H, and TULLSEN D M. Indirector: High-precision branch target injection attacks exploiting the indirect branch predictor[C]. The 33rd USENIX Conference on Security Symposium, Philadelphia, USA, 2024: 120. [26] CHOWDHURYY M H I and YAO Fan. Leaking secrets through modern branch predictors in the speculative world[J]. IEEE Transactions on Computers, 2022, 71(9): 2059–2072. doi: 10.1109/TC.2021.3122830. [27] LIU Chang, FENG Shuaihu, LI Yuan, et al. MDPeek: Breaking balanced branches in SGX with memory disambiguation unit side channels[C]. The 30th ACM International Conference on Architectural Support for Programming Languages and Operating Systems, Rotterdam, Netherlands, 2025: 622–638. doi: 10.1145/3676641.3716004. [28] LIU Chang, WANG Dongsheng, LYU Yongqiang, et al. Uncovering and exploiting AMD speculative memory access predictors for fun and profit[C]. 2024 IEEE International Symposium on High-Performance Computer Architecture (HPCA), Edinburgh, UK, 2024: 31–45. doi: 10.1109/HPCA57654.2024.00014. [29] ISLAM S, MOGHIMI A, BRUHNS I, et al. SPOILER: Speculative load hazards boost rowhammer and cache attacks[C]. The 28th USENIX Conference on Security Symposium, Santa Clara, USA, 2019: 621–637. [30] HETTERICH L, THOMAS F, GERLACH L, et al. ShadowLoad: Injecting state into hardware prefetchers[C]. The 30th ACM International Conference on Architectural Support for Programming Languages and Operating Systems, Rotterdam, Netherlands, 2025: 1060–1075. doi: 10.1145/3676641.3716020. [31] CHEN Boru, WANG Yingchen, SHOME P, et al. GoFetch: Breaking constant-time cryptographic implementations using data memory-dependent prefetchers[C]. The 33rd USENIX Conference on Security Symposium, Philadelphia, USA, 2024: 1117–1134. [32] CHEN Yun, PEI Lingfeng, and CARLSON T E. AfterImage: Leaking control flow data and tracking load operations via the hardware prefetcher[C]. The 28th ACM International Conference on Architectural Support for Programming Languages and Operating Systems, Vancouver, Canada, 2023: 16–32. doi: 10.1145/3575693.3575719. [33] CHEN Yun, HAJIABADI A, PEI Lingfeng, et al. PREFETCHX: Cross-core cache-agnostic prefetcher-based side-channel attacks[C]. 2024 IEEE International Symposium on High-Performance Computer Architecture (HPCA), Edinburgh, UK, 2024: 395–408. doi: 10.1109/HPCA57654.2024.00037. [34] CHEN Yun, PASHRASHID A, WU Yongzheng, et al. Prime+Reset: Introducing a novel cross-world covert-channel through comprehensive security analysis on ARM TrustZone[C]. 2024 Design, Automation & Test in Europe Conference & Exhibition (DATE), Valencia, Spain, 2024: 1–6. doi: 10.23919/DATE58400.2024.10546531. [35] VICARTE J R S, FLANDERS M, PACCAGNELLA R, et al. Augury: Using data memory-dependent prefetchers to leak data at rest[C]. 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2022: 1491–1505. doi: 10.1109/SP46214.2022.9833570. [36] SCHLÜTER T, CHOUDHARI A, HETTERICH L, et al. FetchBench: Systematic identification and characterization of proprietary prefetchers[C]. The 2023 ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 2023: 975–989. doi: 10.1145/3576915.3623124. [37] IBRAHIM A, NEMATI H, SCHLÜTER T, et al. Microarchitectural leakage templates and their application to cache-based side channels[C]. The 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, USA, 2022: 1489–1503. doi: 10.1145/3548606.3560613. [38] XIAO Chong, TANG Ming, and GUILLEY S. Exploiting the microarchitectural leakage of prefetching activities for side-channel attacks[J]. Journal of Systems Architecture, 2023, 139: 102877. doi: 10.1016/J.SYSARC.2023.102877. [39] SHIN Y, KIM H C, KWON D, et al. Unveiling hardware-based data prefetcher, a hidden source of information leakage[C]. The 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, Canada, 2018: 131–145. doi: 10.1145/3243734.3243736. [40] WANG Daimeng, QIAN Zhiyun, ABU-GHAZALEH N, et al. PAPP: Prefetcher-aware prime and probe side-channel attack[C]. The 56th Annual Design Automation Conference 2019, Las Vegas, USA, 2019: 1–6. doi: 10.1145/3316781.3317877. [41] WANG Quancheng, TANG Ming, XU Ke, et al. Unveiling and evaluating vulnerabilities in branch predictors via a three-step modeling methodology[J]. ACM Transactions on Architecture and Code Optimization, 2025, 22(1): 1–26. doi: 10.1145/3711923. [42] 刘畅, 杨毅, 李昊儒, 等. 处理器分支预测攻击研究综述[J]. 计算机学报, 2022, 45(12): 2475–2509. doi: 10.11897/SP.J.1016.2022.02475.LIU Chang, YANG Yi, LI Haoru, et al. A survey of branch prediction attacks on modern processors[J]. Chinese Journal of Computers, 2022, 45(12): 2475–2509. doi: 10.11897/SP.J.1016.2022.02475. [43] 吝常青. 基于RISC-V处理器的硬件数据预取安全机制研究[D]. [硕士论文], 中国科学院大学, 2020.LIN Changqing. Research on hardware data prefetch security mechanism based on RISC-V processor[D]. [Master dissertation], University of Chinese Academy of Sciences, 2020. [44] 吝常青, 田鑫, 侯锐, 等. 基于边界检测的安全数据预取方案[J]. 信息安全学报, 2022, 7(1): 114–125. doi: 10.19363/J.cnki.cn10-1380/tn.2022.01.08.LIN Changqing, TIAN Xin, HOU Rui, et al. Security data prefetching scheme based on boundary detection[J]. Journal of Cyber Security, 2022, 7(1): 114–125. doi: 10.19363/J.cnki.cn10-1380/tn.2022.01.08. [45] NATH S, NAVARRO-TORRES A, ROS A, et al. Secure prefetching for secure cache systems[C]. 2024 57th IEEE/ACM International Symposium on Microarchitecture (MICRO), Austin, USA, 2024: 92–104. doi: 10.1109/MICRO61859.2024.00017. [46] NEMATI H, BUIRAS P, LINDNER A, et al. Validation of abstract side-channel models for computer architectures[C]. The 32nd International Conference on Computer Aided Verification, Los Angeles, USA, 2020: 225–248. doi: 10.1007/978-3-030-53288-8_12. [47] ZHANG Zhiyuan, TAO Mingtian, O’CONNELL S, et al. BunnyHop: Exploiting the instruction prefetcher[C]. The 32nd USENIX Conference on Security Symposium, Anaheim, USA, 2023: 7321–7337. [48] BHATTACHARYA S, REBEIRO C, and MUKHOPADHYAY D. Hardware prefetchers leak: A revisit of SVF for cache-timing attacks[C]. 2012 45th Annual IEEE/ACM International Symposium on Microarchitecture Workshops, Vancouver, Canada, 2012: 17–23. doi: 10.1109/MICROW.2012.13. [49] DIDIER G, MAURICE C, GEIMER A, et al. Characterizing prefetchers using cacheobserver[C]. 2022 IEEE 34th International Symposium on Computer Architecture and High Performance Computing (SBAC-PAD), Bordeaux, France, 2022: 170–179. doi: 10.1109/SBAC-PAD55451.2022.00028. [50] ROHAN A, PANDA B, and AGARWAL P. Reverse engineering the stream prefetcher for profit[C]. 2020 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Genoa, Italy, 2020: 682–687. doi: 10.1109/EUROSPW51379.2020.00098. [51] WANG Quancheng, TANG Ming, XU Ke, et al. Modeling, derivation, and automated analysis of branch predictor security vulnerabilities[C]. 2024 IEEE International Symposium on High-Performance Computer Architecture (HPCA), Edinburgh, UK, 2024: 409–423. doi: 10.1109/HPCA57654.2024.00038. [52] CRONIN P and YANG Chengmo. A fetching tale: Covert communication with the hardware prefetcher[C]. 2019 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, USA, 2019: 101–110. doi: 10.1109/HST.2019.8741033. [53] FUCHS A and LEE R B. Disruptive prefetching: Impact on side-channel attacks and cache designs[C]. The 8th ACM International Systems and Storage Conference, Haifa, Israel, 2015: 14. doi: 10.1145/2757667.2757672. [54] KIM J, CHUANG J, GENKIN D, et al. FLOP: Breaking the apple M3 CPU via false load output predictions[C]. The 34th USENIX Security Symposium, Seattle, USA, 2025. [55] WICHELMANN J, RABICH A, PÄTSCHKE A, et al. Obelix: Mitigating side-channels through dynamic obfuscation[C]. 2024 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2024: 4182–4199. doi: 10.1109/SP54263.2024.00261. [56] GUO Yanan, ZIGERELLI A, ZHANG Youtao, et al. Adversarial prefetch: New cross-core cache side channel attacks[C]. 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2022: 1458–1473. doi: 10.1109/SP46214.2022.9833692. [57] GRUSS D, MAURICE C, FOGH A, et al. Prefetch side-channel attacks: Bypassing SMAP and kernel ASLR[C]. The 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 2016: 368–379. doi: 10.1145/2976749.2978356. [58] NESBIT K J and SMITH J E. Data cache prefetching using a global history buffer[C]. 10th International Symposium on High Performance Computer Architecture (HPCA'04), Madrid, Spain, 2004: 96–105. doi: 10.1109/HPCA.2004.10030. [59] JOSEPH D and GRUNWALD D. Prefetching using Markov predictors[C]. The 24th Annual International Symposium on Computer Architecture, Denver, USA, 1997: 252–263. doi: 10.1145/264107.264207. [60] WENISCH T F, SOMOGYI S, HARDAVELLAS N, et al. Temporal streaming of shared memory[C]. 32nd International Symposium on Computer Architecture (ISCA'05), Madison, USA, 2005: 222–233. doi: 10.1109/ISCA.2005.50. [61] SOMOGYI S, WENISCH T F, AILAMAKI A, et al. Spatio-temporal memory streaming[C]. The 36th Annual International Symposium on Computer Architecture, Austin, USA, 2009: 69–80. doi: 10.1145/1555754.1555766. [62] GRANNÆS M, JAHRE M, and NATVIG L. Multi-level hardware prefetching using low complexity delta correlating prediction tables with partial matching[C]. The 5th International Conference on High Performance Embedded Architectures and Compilers, Pisa, Italy, 2010: 247–261. doi: 10.1007/978-3-642-11515-8_19. [63] FALSAFI B and WENISCH T F. A Primer on Hardware Prefetching[M]. San Rafael: Morgan & Claypool Publishers, 2014: 1–53. doi: 10.2200/S00581ED1V01Y201405CAC028. -





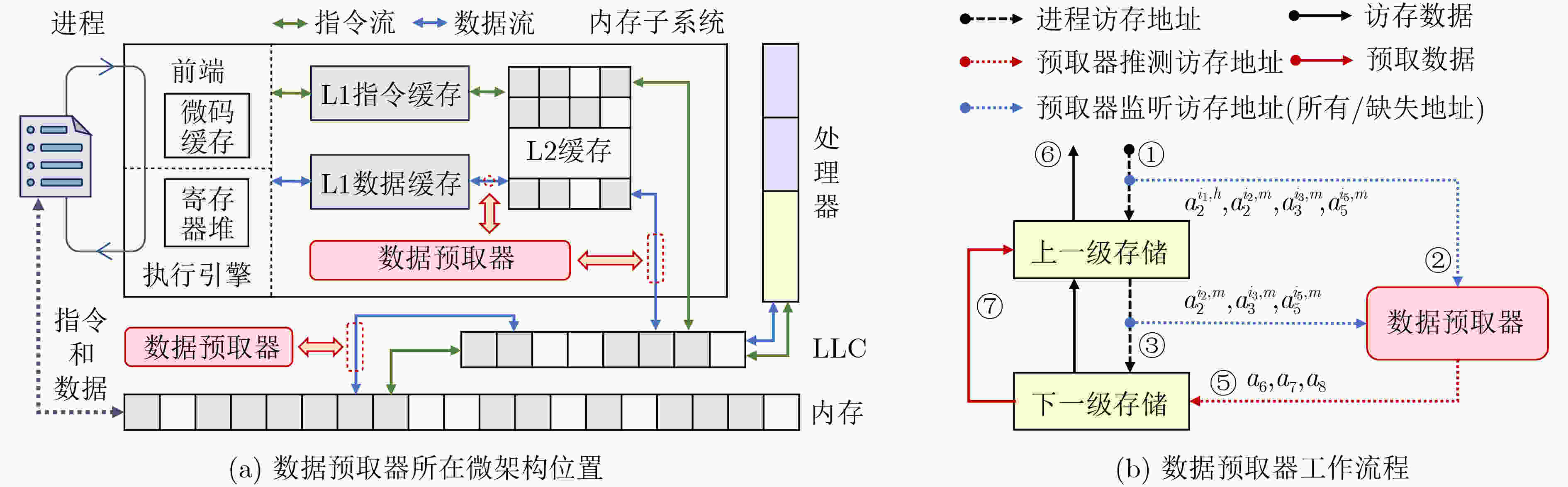
 下载:
下载:
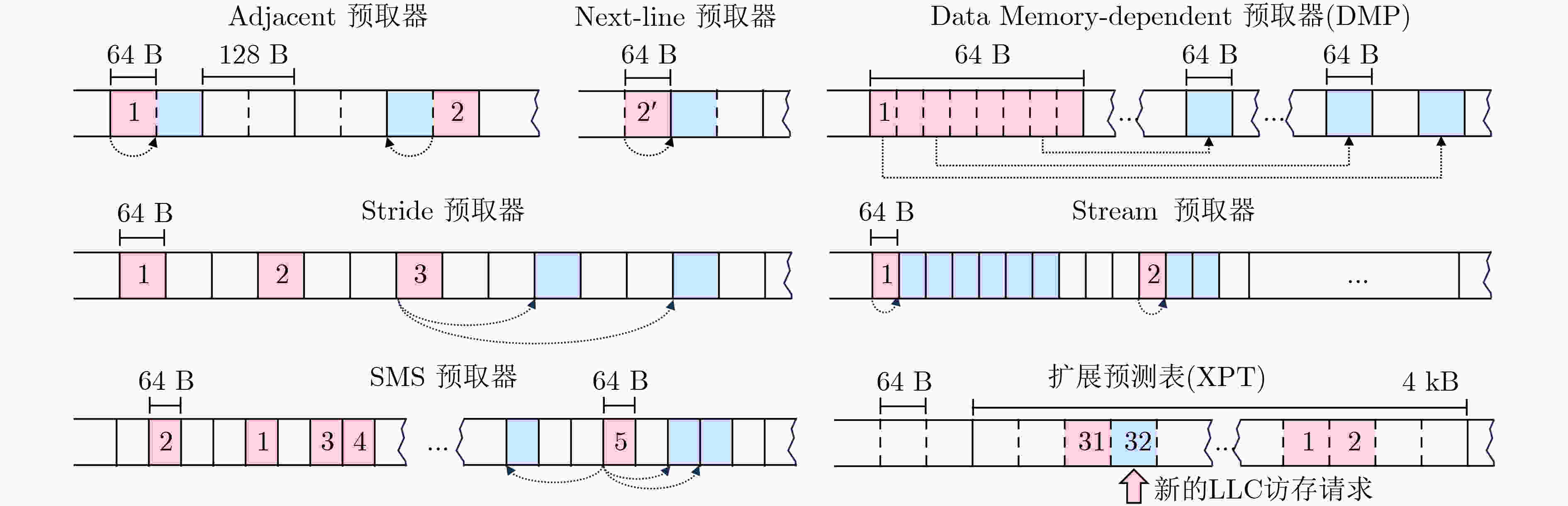
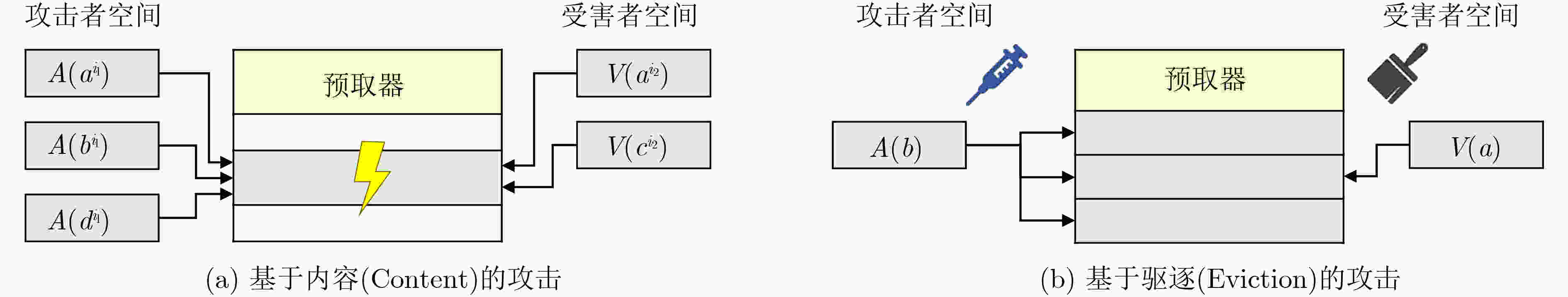
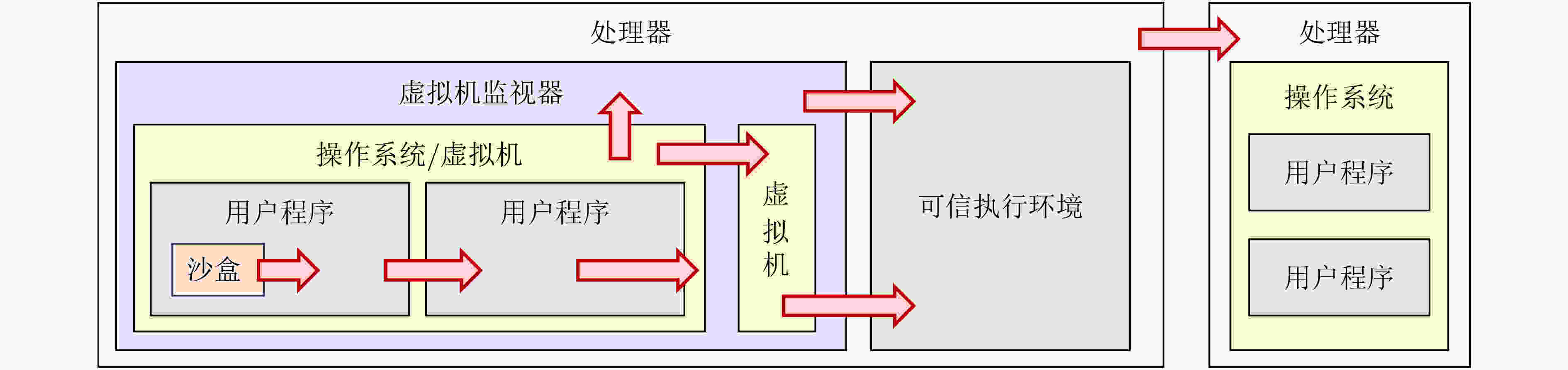


 下载:
下载:
