Covert Communication Transmission Scheme in Low Earth Orbit Satellite Integrated Sensing and Communication Systems
-
摘要: 该文考虑一种低轨(LEO)卫星通感一体化系统中的隐蔽通信传输方案,在确保系统的感知性能不低于预设阈值的同时,利用雷达波束干扰监听者,提高卫星通信的隐蔽性。首先,提出了LEO卫星通感一体化系统的系统模型,分析了系统中的隐蔽性约束。其次,在此基础之上,构建了以最大化多用户隐蔽通信速率总和为目标函数,以卫星功率上限、雷达功率上限、感知性能下限和隐蔽性要求为约束的优化问题。该优化问题非凸且变量耦合严重,无法直接求解,可以采用交替优化算法和连续凸近似(SCA)算法等方式对原问题进行转换和迭代求解。最后仿真结果表明,与无雷达波束干扰的卫星隐蔽通信系统相比,所提出的有雷达波束干扰的系统能够有效降低监听者的检测性能,从而提高通信的隐蔽性和速率。
-
关键词:
- 卫星通信 /
- 通感一体化 /
- 隐蔽通信 /
- 连续凸近似(SCA)
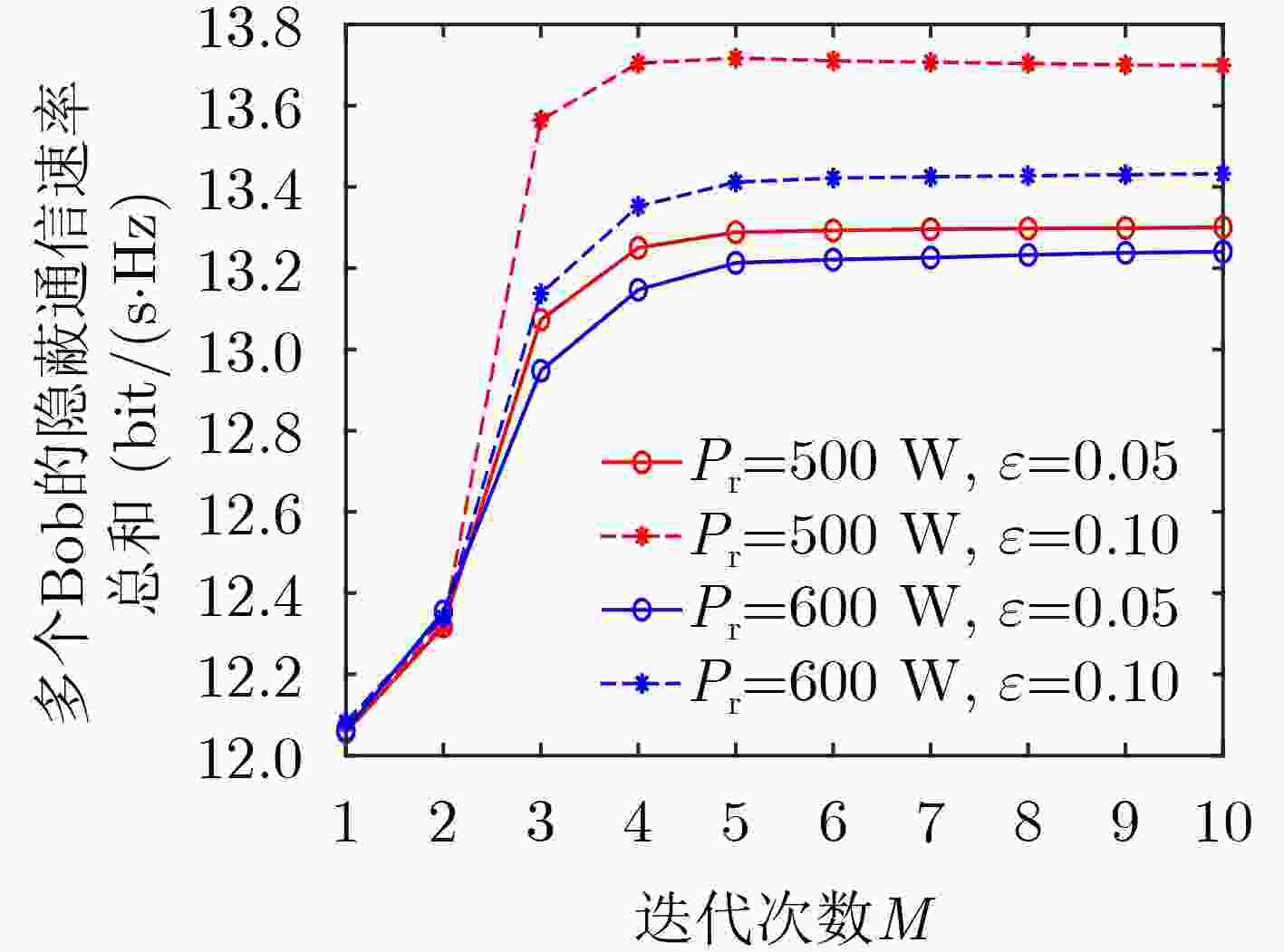
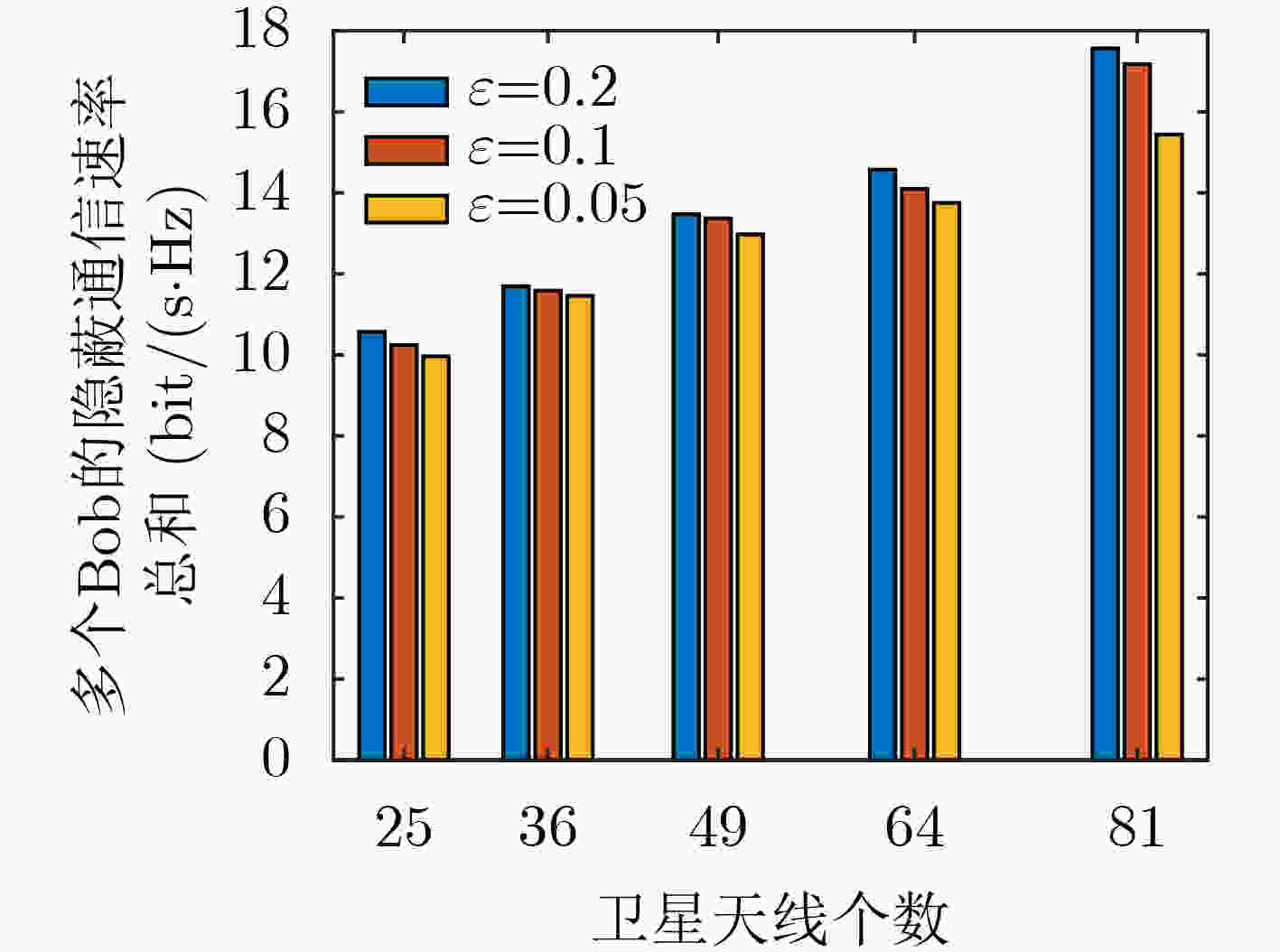
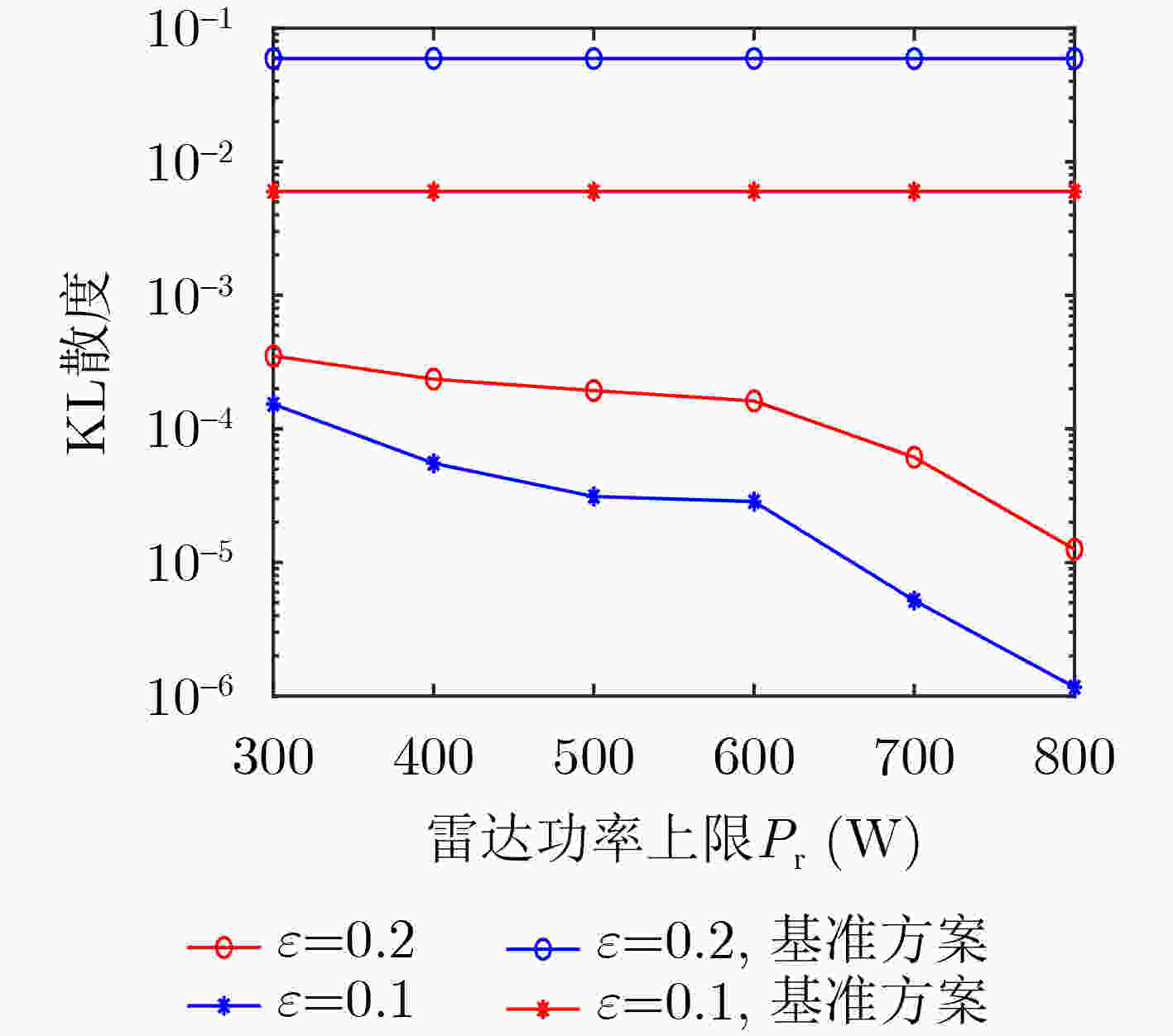
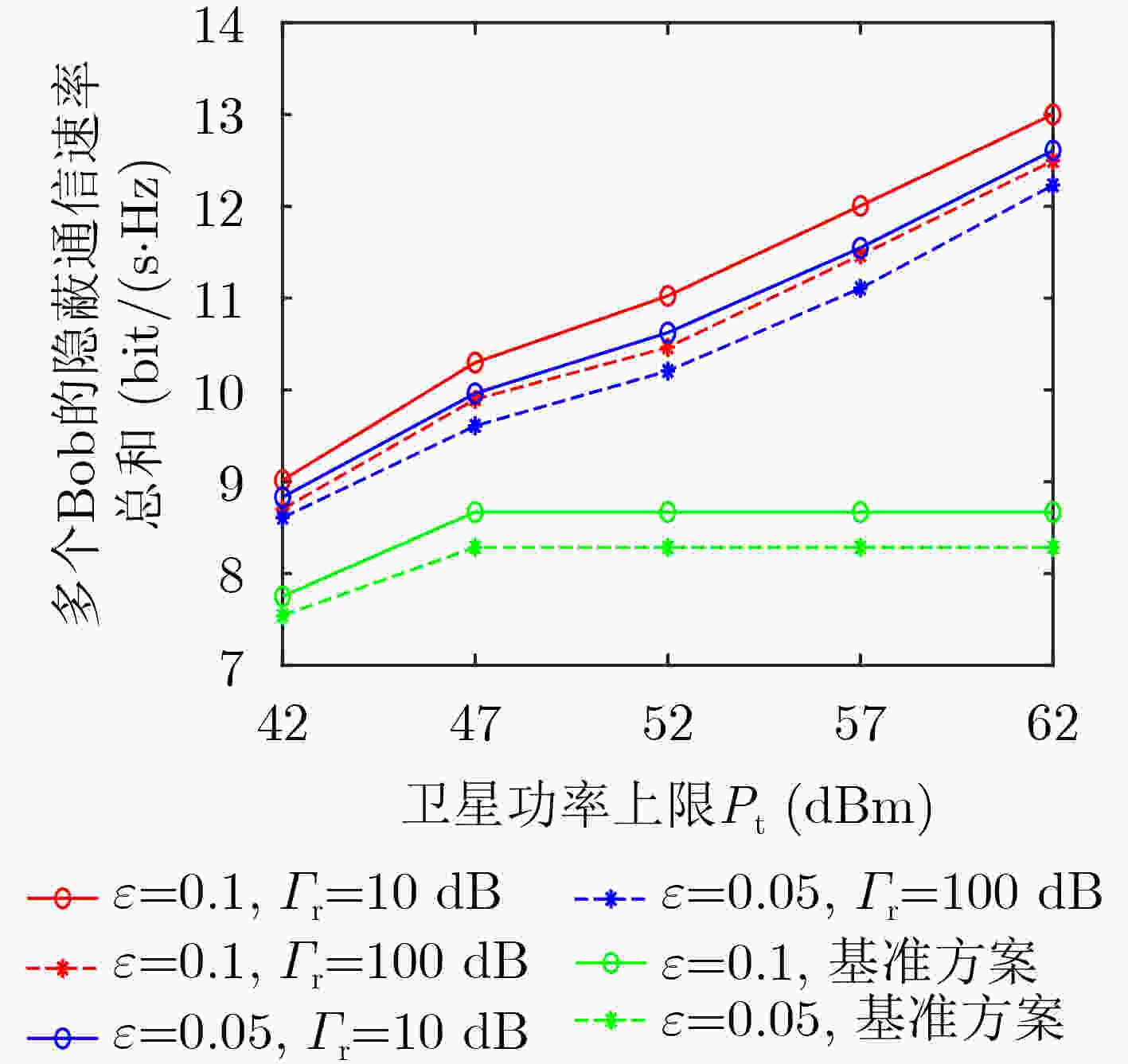
Abstract:Objective Globalization has driven growing demand for ubiquitous communication. However, traditional terrestrial networks face limitations in areas with poor infrastructure, such as deserts, oceans, and airspace. Satellite communication, with its flexibility, wide frequency coverage, and high capacity, offers a viable alternative for these environments. Yet, due to the open nature of satellite channels and long-distance transmission, signals remain vulnerable to interception, posing serious security challenges. Conventional wireless security measures, including physical-layer techniques and encryption, are limited by assumptions about computational hardness and the statistical structure of intercepted ciphertexts. Covert communication aims to reduce the probability of signal detection by eavesdroppers, providing an alternative layer of security. In Low Earth Orbit (LEO) satellite systems, high mobility leads to dynamic channel variations and misalignment of transmission beams, further complicating covert communication. To mitigate these challenges, Integrated Sensing And Communication (ISAC) technology can be embedded in satellite systems. By detecting the approximate location of potential eavesdroppers and directing radar beams to degrade their detection capability, ISAC improves communication covertness. This study proposes a covert communication strategy tailored for LEO satellite ISAC systems, offering enhanced security in satellite-based infrastructure. Methods This paper investigates a covert communication scheme in LEO satellite ISAC systems. First, the system model of the LEO satellite ISAC system is proposed, and the covertness constraints within the system are analyzed. Based on this, an optimization problem is formulated with the objective of maximizing the total covert communication rate for multiple users, subject to constraints including satellite power limits, radar power limits, sensing performance thresholds, and covertness requirements. This optimization problem is non-convex and highly coupled in variables, making it intractable to solve directly. To address this, relaxation variables are introduced to simplify the objective function into a solvable form. Subsequently, an alternating optimization algorithm is employed to decompose the original problem into two subproblems. One subproblem is transformed into an equivalent convex problem using methods like SemiDefinite Relaxation (SDR) and Successive Convex Approximation (SCA), which is then solved iteratively. The obtained solution from this subproblem is then used to solve the other subproblem. Once the solutions to both subproblems are determined, the original problem is effectively solved. Results and Discussions This paper validates the performance of the proposed covert communication transmission scheme through numerical simulations. To demonstrate the effectiveness of the proposed scheme, a comparison with a system lacking ISAC technology is introduced. First, the convergence of the proposed algorithm is verified ( Fig. 2 ). The algorithm achieves rapid convergence under different resource allocation configurations in the system (converging at the 7th iteration). Additionally, higher covertness requirements lead to lower covert communication rates, as stricter covertness constraints reduce the allowable upper limit oft the satellite transmit power. Increasing the upper limit of the radar power causes a slight decline in the covert rate because Bob is subjected to minor interference from the radar beam. However, since the primary radar beam is focused on Eve, the interference level remains limited. Second, a higher number of satellite antennas improves the system’s covert communication rate (Fig. 3 ). This is attributed to the increased spatial dimensions available for optimizing signal transmission and reception. More antennas enable additional independent signal paths, enhancing transmission performance and flexibility. When the satellite is equipped with 81 antennas and the covertness requirement is 0.1, the total covert rate reaches 17.18 bit/(s·Hz). Compared to the system without ISAC technology, the proposed system demonstrates superior resistance to detection (Fig. 4 ). The radar beam introduces interference to eavesdroppers, and higher upper limit of the radar power degrades the eavesdropper’s detection performance. Finally, increasing the upper limit of the satellite transmit power improves the covert communication rate (Fig. 5 ). In the system without ISAC, the upper limit of the satellite power cannot be arbitrarily increased due to covertness constraints. However, the ISAC-enabled system leverages radar integration to grant the satellite greater flexibility in power allocation, thereby enhancing the covert rate. Notably, raising the lower bound of sensing performance slightly reduces the covert rate, as higher sensing demands require increased upper limit of the radar power, which introduces additional interference to Bob’s signal reception.Conclusions This paper investigates a covert communication transmission scheme in an LEO satellite-enabled ISAC system. An optimization problem is formulated to maximize the sum of multi-user covert communication rates, subject to constraints including covertness requirements, minimum sensing performance, the upper limit of the radar power budget, and the upper limit of the satellite power budget. The alternating optimization algorithm and SCA algorithm are jointly employed to design the radar and satellite beamforming, as well as the radar receiver filter. Simulation results demonstrate that, compared to a system without radar beam interference, the proposed system with radar beam interference significantly reduces the detectability of communication between Alice and Bob. Furthermore, the integration of radar enhances the satellite’s flexibility to increase transmit power, thereby improving the overall covert communication rate of the system. -
1 求解问题式(28)的交替优化算法
输入:$ {\boldsymbol{h}}_{k},{\boldsymbol{h}}_{\mathrm{e}},{\boldsymbol{g}}_{k},{\sigma }_{k},{\sigma }_{0},\boldsymbol{A},\boldsymbol{Q},{\sigma }_{\mathrm{r}},\boldsymbol{I},{\boldsymbol{g}}_{\mathrm{e}},{\sigma }_{\mathrm{e}},{\gamma }_{\mathrm{e}}^{*},{P}_{\mathrm{c}},{P}_{\mathrm{r}} $ 输出:$ {\boldsymbol{w}}_{k}^{*},\forall k,{\boldsymbol{F}}^{*},{\boldsymbol{u}}^{*} $ (1) 初始化$ {\boldsymbol{W}}_{j}^{\left(0\right)},{\boldsymbol{R}}_{\boldsymbol F}^{\left(0\right)},\boldsymbol{u} $;设置收敛精度$ \varepsilon \ge 0 $;优化变量
$ {\boldsymbol{W}}_{k},{x}_{k},\forall k,{\boldsymbol{R}}_{\boldsymbol F} $;(2) 重复 (3) 求解问题式(37),得到$ {\boldsymbol{W}}_{k},{x}_{k},\forall k,{\boldsymbol{R}}_{\boldsymbol F} $; (4) 对$ {\boldsymbol{W}}_{k} $进行EVD分解得到相应的$ {\boldsymbol{w}}_{k} $,对$ {\boldsymbol{R}}_{\boldsymbol F} $进行
Cholesky分解得到相应的$ \boldsymbol{F} $;(5) 计算式(39)更新$ \boldsymbol{u} $; (6) 将$ {\boldsymbol{W}}_{k}={\boldsymbol{w}}_{k}{\boldsymbol{w}}_{k}^{\mathrm{H}} $用于迭代更新$ {\boldsymbol{W}}_{j}^{\left(i\right)} $,将$ {\boldsymbol{R}}_{\boldsymbol F}=\boldsymbol{F}{\boldsymbol{F}}^{{\mathrm{H}}} $
用于迭代更新$ {\boldsymbol{R}}_{\boldsymbol F}^{\left(i\right)} $;(7) 计算本次迭代目标函数值式(28a)$ {\displaystyle\sum\nolimits_{k=1}^{K}{x}_{k}}/{\mathrm{ln}2} $; (8) 直到本次迭代的目标函数值式(28a)和上次迭代的目标函数值
式(28a)的相差绝对值小于等于$ \varepsilon $;(9) 对$ {\boldsymbol{W}}_{k} $进行EVD得到相应的$ {\boldsymbol{w}}_{k}^{*} $,对$ {\boldsymbol{R}}_{\boldsymbol F} $进行Cholesky分解得
到相应的$ {\boldsymbol{F}}^{*} $;(10) 计算式(39)得到$ {\boldsymbol{u}}^{*} $; 表 1 仿真参数
参数 参数值 地球半径$ {\mathrm{R}}_{\mathrm{e}} $ 6371 kmLEO卫星高度$ {h}_{\mathrm{s}} $ 1000 km载波频率$ f $ 20 GHz 信道带宽$ B $ 50 MHz 噪声温度$ T $ 290 K 玻尔兹曼常数$ {\mathrm{k}}_{\mathrm{B}} $ 1.38$ \text{×}{10}^{-23} $ J$ \cdot{\mathrm{K}}^{-1} $ Bob个数 4 天线增益$ {G}_{\mathrm{s}},{G}_{\mathrm{u}} $ 3 dB 雷达感知性能下限$ {\varGamma }_{\mathrm{r}} $ 10 dB 第k个用户的俯仰角估计$ {\hat{\theta }}_{k} $[14] [0°,180°] 卫星天线个数 25 雷达天线个数 25 卫星功率上限$ {P}_{\mathrm{t}} $[14] 47 dbm 雷达功率上限$ {P}_{\mathrm{r}} $[15] 500 W 隐蔽性要求$ \varepsilon $ 0.1 第k个用户的方位角估计$ {\hat{\varphi }}_{k} $[14] [0°,180°] 路径损失指数$ \alpha $ 2.2 第k个用户的单位距离信道增益$ {\mathrm{\beta }}_{k} $[9] –30 dB 卫星天线阵列X轴和Y轴天线数量 5,5 -
[1] 易克初, 李怡, 孙晨华, 等. 卫星通信的近期发展与前景展望[J]. 通信学报, 2015, 36(6): 2015223. doi: 10.11959/j.issn.1000-436x.2015223.YI Kechu, LI Yi, SUN Chenhua, et al. Recent development and its prospect of satellite communications[J]. Journal on Communications, 2015, 36(6): 2015223. doi: 10.11959/j.issn.1000-436x.2015223. [2] CHEN Xinying, AN Jianping, XIONG Zehui, et al. Covert communications: A comprehensive survey[J]. IEEE Communications Surveys & Tutorials, 2023, 25(2): 1173–1198. doi: 10.1109/COMST.2023.3263921. [3] BASH B A, GOECKEL D, and TOWSLEY D. Limits of reliable communication with low probability of detection on AWGN channels[J]. IEEE Journal on Selected Areas in Communications, 2013, 31(9): 1921–1930. doi: 10.1109/JSAC.2013.130923. [4] YAN Shihao, HE Biao, ZHOU Xiangyun, et al. Delay-intolerant covert communications with either fixed or random transmit power[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(1): 129–140. doi: 10.1109/TIFS.2018.2846257. [5] 周小波, 于辉, 彭旭, 等. 智能反射面辅助及人工噪声增强的无线隐蔽通信[J]. 电子与信息学报, 2022, 44(7): 2392–2399. doi: 10.11999/JEIT211618.ZHOU Xiaobo, YU Hui, PENG Xu, et al. Wireless covert communications based on intelligent reflecting surface aided and artificial noise enhanced[J]. Journal of Electronics & Information Technology, 2022, 44(7): 2392–2399. doi: 10.11999/JEIT211618. [6] HE Biao, YAN Shihao, ZHOU Xiangyun, et al. Covert wireless communication with a Poisson field of interferers[J]. IEEE Transactions on Wireless Communications, 2018, 17(9): 6005–6017. doi: 10.1109/TWC.2018.2854540. [7] ZHANG Lei, CHEN Zhao, JIANG Chunxiao, et al. Covert communication in ultra-dense LEO satellite systems with interference uncertainty[C]. The ICC 2024 - IEEE International Conference on Communications, Denver, USA, 2024: 1255–1260. doi: 10.1109/ICC51166.2024.10622920. [8] XIONG Wenhui, YAO Yinfeng, FU Xiaoyu, et al. Covert communication with cognitive jammer[J]. IEEE Wireless Communications Letters, 2020, 9(10): 1753–1757. doi: 10.1109/LWC.2020.3003472. [9] LIU Pengpeng, SI Jiangbo, LI Zan, et al. Covert communications for cognitive satellite terrestrial networks[C]. 2024 IEEE Wireless Communications and Networking Conference, Dubai, United Arab Emirates, 2024: 1–6. doi: 10.1109/WCNC57260.2024.10570773. [10] LIU An, HUANG Zhe, LI Min, et al. A survey on fundamental limits of integrated sensing and communication[J]. IEEE Communications Surveys & Tutorials, 2022, 24(2): 994–1034. doi: 10.1109/COMST.2022.3149272. [11] LU Shihang, LIU Fan, LI Yunxin, et al. Integrated sensing and communications: Recent advances and ten open challenges[J]. IEEE Internet of Things Journal, 2024, 11(11): 19094–19120. doi: 10.1109/JIOT.2024.3361173. [12] LIU Rang, LI Ming, LIU Yang, et al. Joint transmit waveform and passive beamforming design for RIS-aided DFRC systems[J]. IEEE Journal of Selected Topics in Signal Processing, 2022, 16(5): 995–1010. doi: 10.1109/JSTSP.2022.3172788. [13] 朱政宇, 杨晨一, 李铮, 等. 智能反射面辅助通感一体化系统安全资源分配算法[J]. 电子与信息学报, 2025, 47(1): 66–74. doi: 10.11999/JEIT240083.ZHU Zhengyu, YANG Chenyi, LI Zheng, et al. Resource allocation algorithm for intelligent reflecting surface-assisted secure integrated sensing and communications system[J]. Journal of Electronics & Information Technology, 2025, 47(1): 66–74. doi: 10.11999/JEIT240083. [14] ZHANG Xue, WANG Ruibo, SHANG Bodong, et al. Joint robust secure beamforming designs for ISAC-enabled LEO satellite systems[C]. 2024 IEEE International Conference on Communications, Denver, USA, 2024: 1182–1188. doi: 10.1109/ICC51166.2024.10622473. [15] CHU Jinjin, LIU Rang, LI Ming, et al. Joint secure transmit beamforming designs for integrated sensing and communication systems[J]. IEEE Transactions on Vehicular Technology, 2023, 72(4): 4778–4791. doi: 10.1109/TVT.2022.3225952. [16] HU Jinsong, LIN Qingzhuan, YAN Shihao, et al. Covert transmission via integrated sensing and communication systems[J]. IEEE Transactions on Vehicular Technology, 2024, 73(3): 4441–4446. doi: 10.1109/TVT.2023.3326455. [17] HU Jinsong, LI Hongwei, CHEN Youjia, et al. Covert communication in cognitive radio networks with Poisson distributed jammers[J]. IEEE Transactions on Wireless Communications, 2024, 23(10): 13095–13109. doi: 10.1109/TWC.2024.3398651. [18] ZHOU Xiaobo, YAN Shihao, HU Jinsong, et al. Joint optimization of a UAV's trajectory and transmit power for covert communications[J]. IEEE Transactions on Signal Processing, 2019, 67(16): 4276–4290. doi: 10.1109/TSP.2019.2928949. [19] SHU Feng, XU Tingzhen, HU Jinsong, et al. Delay-constrained covert communications with a full-duplex receiver[J]. IEEE Wireless Communications Letters, 2019, 8(3): 813–816. doi: 10.1109/LWC.2019.2894617. [20] YAN Shihao, ZHOU Xiangyun, HU Jinsong, et al. Low probability of detection communication: Opportunities and challenges[J]. IEEE Wireless Communications, 2019, 26(5): 19–25. doi: 10.1109/MWC.001.1900057. [21] LIU Pengpeng, LI Zan, SI Jiangbo, et al. Joint information-theoretic secrecy and covertness for UAV-assisted wireless transmission with finite blocklength[J]. IEEE Transactions on Vehicular Technology, 2023, 72(8): 10187–10199. doi: 10.1109/TVT.2023.3254882. [22] LUO Zhiquan, MA W K, SO A M C, et al. Semidefinite relaxation of quadratic optimization problems[J]. IEEE Signal Processing Magazine, 2010, 27(3): 20–34. doi: 10.1109/MSP.2010.936019. [23] WANG Kunyu, SO A M C, CHANG T H, et al. Outage constrained robust transmit optimization for multiuser MISO downlinks: TRACTABLE approximations by conic optimization[J]. IEEE Transactions on Signal Processing, 2014, 62(21): 5690–5705. doi: 10.1109/TSP.2014.2354312. -





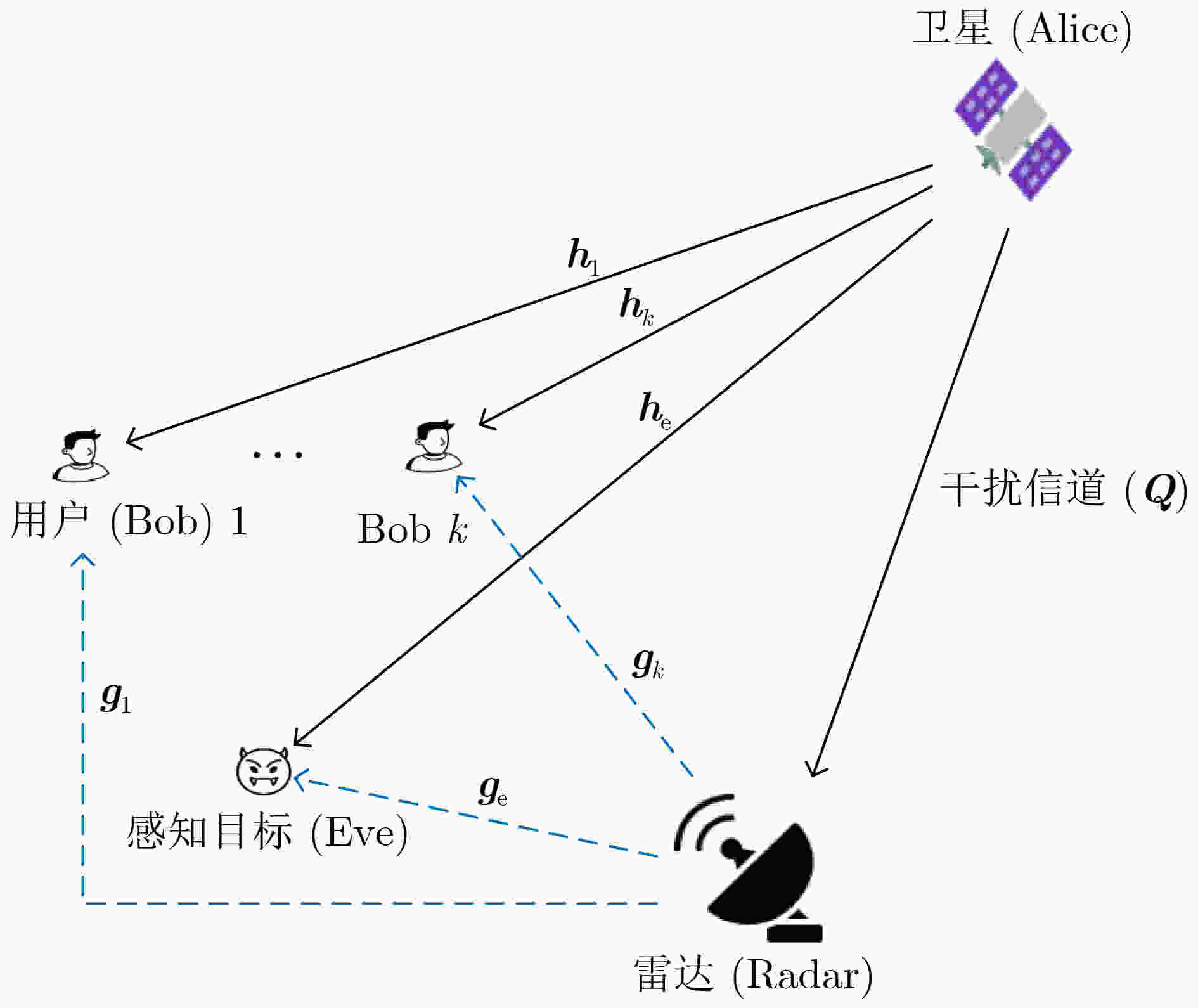
 下载:
下载:


 下载:
下载:
