HNN4RP: Heterogeneous Graph Neural Network for Rug Pull Detection on Ethereum
-
摘要: 去中心化金融(DeFi)依托区块链技术,实现了金融交易和服务的去中心化,重塑了传统金融体系中的信任机制,成为近年来学术界和工业界的研究热点。然而,DeFi的开放性、匿名性和无需许可的特征,虽然赋予用户更大的灵活性和自主权,但也带来了严峻的监管挑战,导致金融欺诈行为频发,尤其是地毯拉动骗局(Rug Pull)屡见不鲜。针对这一问题,该文提出一种基于异构图神经网络的地毯拉动骗局早期检测算法(HNN4RP),用于识别和预警DeFi生态中的地毯拉动骗局。具体而言,将以太坊交易数据建模为异构图,并结合重启随机游走采样策略、异构节点特征提取技术和基于双向长短期记忆网络的时序特征融合方法,以有效应对数据分布不均、异构节点特征提取困难以及时序信息缺失等3大关键挑战。实验结果表明,通过在真实的以太坊数据集上,HNN4RP取得了96%的精确率和94%的召回率,相较于基线方法精确率提升了17.8%,显著优于传统检测方法,并能够提供及时的欺诈预警。此外,消融实验和敏感性分析验证了模型的鲁棒性。Abstract:
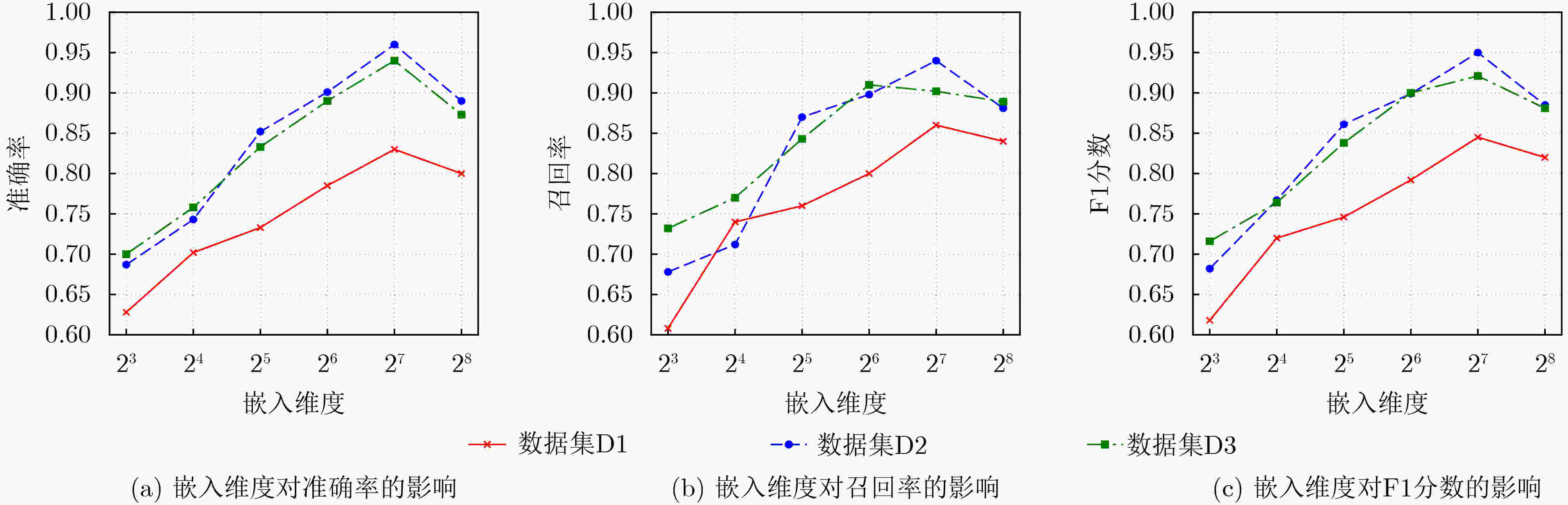
Objective The rapid expansion of Decentralized Finance (DeFi) has been accompanied by a rise in fraudulent activities, with Rug Pull scams posing a significant threat to the security, stability, and credibility of blockchain ecosystems. Due to the permissionless and decentralized nature of DeFi platforms, malicious actors can exploit smart contracts to deceive investors, artificially inflate token prices, and withdraw liquidity abruptly, leaving investors with worthless assets. The anonymous and pseudonymous characteristics of blockchain transactions further hinder fraud detection and regulatory oversight, making Rug Pull scams one of the most challenging forms of financial fraud in the DeFi sector. Although traditional fraud detection approaches, such as rule-based heuristics and statistical analysis, provide basic risk assessment, they often fail to capture the complex transaction patterns, dynamic interactions, and heterogeneous relationships within blockchain networks. To address these limitations, this study proposes Heterogeneous graph Neural Network for Rug Pull detection (HNN4RP), a fraud detection framework based on Heterogeneous Graph Neural Networks (GNNs), specifically designed for the early identification of Rug Pull scams. By leveraging the graph structure of blockchain transactions, HNN4RP models Ethereum transaction data as a heterogeneous graph to capture the relationships among smart contracts, liquidity pools, and trader addresses. The framework integrates advanced representation learning techniques to reveal hidden dependencies, detect anomalous patterns, and differentiate between legitimate and fraudulent behaviors in a scalable, data-driven manner. Furthermore, HNN4RP incorporates temporal dynamics and contextual information to adapt to evolving fraud tactics. Methods HNN4RP models Ethereum transactions as a heterogeneous graph, distinguishing between regular nodes and smart contract nodes while preserving both structured and unstructured transactional data. By leveraging a graph-based representation, the model captures complex interactions within the Ethereum network, supporting comprehensive analysis of transactional behavior. This approach explicitly represents key relationships between entities, including token transfers, contract interactions, and liquidity movements, thereby facilitating more accurate fraud detection.The core components of HNN4RP include a Random Walk with Restart (RWR) sampling mechanism, which mitigates biases caused by skewed transaction distributions and enables balanced exploration of node neighborhoods. This technique captures long-range dependencies in the transaction network while preserving the local structural context, which is essential for detecting anomalous behaviors associated with fraud. By dynamically adjusting the probability of revisiting specific nodes, RWR improves the model’s focus on relevant transactional pathways, reducing the effects of data sparsity and imbalance.In addition to RWR-based sampling, HNN4RP incorporates multi-modal feature encoding to capture both structured transactional relationships and unstructured node attributes, such as smart contract code and token metadata. This integration enables the model to leverage a diverse set of informative features, improving its ability to differentiate between legitimate and fraudulent activities. By encoding both numerical and textual representations of transaction data, the framework enhances the robustness of fraud detection against evasive tactics employed by malicious actors.Furthermore, HNN4RP employs a BiLSTM-based temporal fusion mechanism to retain the sequential dependencies within transaction histories, effectively modeling temporal behavioral patterns. This component is essential for capturing the evolution of fraudulent activities over time, as Rug Pull scams often exhibit time-dependent characteristics. By learning the progression of transactional patterns, the model enhances fraud classification accuracy and enables early detection of fraudulent schemes before they escalate. Through this comprehensive approach, HNN4RP provides a scalable, adaptive, and high-precision solution for fraud detection in decentralized financial ecosystems. Results and Discussions The performance of the proposed HNN4RP model is evaluated against three categories of baseline methods: attribute-based approaches, random walk-based algorithms, and deep learning models. Across all dataset scales, HNN4RP consistently outperforms these baselines across three predefined evaluation metrics, demonstrating superior fraud detection capability. Notably, on the D2 and D3 datasets, HNN4RP achieves an accuracy of 96% and an F1 score of 0.95 ( Table 2 ). Ablation experiments indicate that both attribute-based features and textual representations contribute significantly to Rug Pull detection performance (Fig. 3 ). Parameter sensitivity analysis shows that the optimal neighborhood size is 16, and the best embedding dimension is 27 (Figs. 4 and5 ). Further experiments incorporating different types of noise interference confirm that HNN4RP exhibits strong robustness to data perturbations, with the F1 score declining by no more than 7% under moderate noise levels (Table 3 ). Early fraud detection tests demonstrate that HNN4RP effectively identifies fraudulent activities at an early stage, providing reliable warning signals before scams fully develop (Table 4 ).Conclusions This study addresses the emerging challenge of Rug Pull scams in the DeFi and Web3 domains and proposes a deep learning-based detection model, HNN4RP, with significant implications for the stability and security of decentralized financial ecosystems. By formalizing the Rug Pull detection task using heterogeneous graph modeling, this work tackles three major challenges in Ethereum-based fraud detection: biased transaction exploration, incomplete feature representation, and insufficient temporal pattern recognition. These challenges are addressed through the integration of RWR-based random walks, heterogeneous node feature extraction, and BiLSTM-based temporal feature fusion. Experimental results on real Ethereum transaction datasets demonstrate that HNN4RP achieves 96% accuracy and provides reliable early warnings within four hours before fraudulent activities occur, confirming its practical applicability for early fraud detection in decentralized environments. -
Key words:
- Blockchain /
- Ethereum /
- Decentralized Finance (DeFi) /
- Graph Neural Network(GNN) /
- Rug pull
-
表 1 不同类型账户数据对比
评估指标 普通账户 合约账户 平均交易额 0.23 16.34 交易金额中位数 0.05 0.52 交易金额标准差 0.31 5.43 平均余额 0.12 3.48 余额中位数 0.01 0.50 平均入度 5.00 348.20 平均出度 6.10 503.10 表 2 不同算法针对地毯拉动骗局的检测效果对比
算法 数据集D1 数据集D2 数据集D3 精确率 召回率 F1 精确率 召回率 F1 精确率 召回率 F1 SVM 0.684 0.672 0.678 0.653 0.600 0.449 0.596 0.623 0.609 LightGBM 0.702 0.743 0.722 0.738 0.700 0.718 0.679 0.655 0.667 DeepWalk 0.581 0.550 0.565 0.612 0.594 0.603 0.630 0.624 0.627 Node2Vec 0.601 0.570 0.585 0.683 0.713 0.698 0.726 0.700 0.747 GIN 0.612 0.840 0.708 0.705 0.890 0.787 0.712 0.912 0.800 GAT 0.600 0.812 0.690 0.715 0.878 0.788 0.743 0.838 0.788 GraphSAGE 0.796 0.850 0.822 0.824 0.873 0.848 0.830 0.898 0.863 SOTA 0.763 0.742 0.752 0.782 0.766 0.773 0.795 0.792 0.793 GTN 0.835 0.872 0.853 0.933 0.914 0.923 0.938 0.910 0.923 HNN4RP 0.830 0.860 0.845 0.960 0.940 0.950 0.940 0.902 0.910 表 3 不同噪声水平下HNN4RP的检测结果
噪声类型 强度 精确率 F1 无噪声 - 0.960 0.950 特征噪声 $ \sigma $=0.05 0.926 0.907 特征噪声 $ \sigma $=0.10 0.912 0.896 特征噪声 $ \sigma $=0.20 0.887 0.862 标签噪声 $ \eta $=5% 0.905 0.898 标签噪声 $ \eta $=10% 0.874 0.886 标签噪声 $ \eta $=15% 0.853 0.861 表 4 不同时间窗口HNN4RP的检测结果
时间窗口(h) 精确率 召回率 F1 4 0.829 0.893 0.860 12 0.872 0.910 0.890 24 0.923 0.912 0.917 -
[1] Ethereum browser[EB/OL]. https://etherscan.io/chart/address, 2023. [2] JIN Hai and XIAO Jiang. Towards trustworthy blockchain systems in the era of "Internet of value": Development, challenges, and future trends[J]. Science China Information Sciences, 2022, 65(5): 153101. doi: 10.1007/s11432-020-3183-0. [3] BARTOLETTI M, CARTA S, CIMOLI T, et al. Dissecting Ponzi schemes on Ethereum: Identification, analysis, and impact[J]. Future Generation Computer Systems, 2020, 102: 259–277. doi: 10.1016/j.future.2019.08.014. [4] BOSHMAF Y, ELVITIGALA C, AL JAWAHERI H, et al. Investigating MMM Ponzi scheme on bitcoin[C]. The 15th ACM Asia Conference on Computer and Communications Security (ASIA CCS’20), Taipei, China, 2020: 519–530. doi: 10.1145/3320269.3384719. [5] CHEN Weili, GUO Xiongfeng, CHEN Zhiguang, et al. Phishing scam detection on ethereum: Towards financial security for blockchain ecosystem[C]. The 29th International Joint Conference on Artificial Intelligence (IJCAI’20), Yokohama, Japan, 2021: 621. [6] ZHANG Shijie, CHENG Ru, LIU Xinpeng, et al. Seer: Accelerating blockchain transaction execution by fine-grained branch prediction[J]. Proceedings of the VLDB Endowment, 2024, 18(3): 822–835. doi: 10.14778/3712221.3712245. [7] ZHANG Shijie, XIAO Jiang, WU Enping, et al. MorphDAG: A workload-aware elastic DAG-based blockchain[J]. IEEE Transactions on Knowledge and Data Engineering, 2024, 36(10): 5249–5264. doi: 10.1109/TKDE.2024.3382743. [8] CERNERA F, LA MORGIA M, MEI A, et al. Token spammers, rug pulls, and sniper bots: An analysis of the ecosystem of tokens in Ethereum and in the Binance smart chain (BNB)[C]. The 32nd USENIX Conference on Security Symposium (USENIX Security 2023), Anaheim, USA, 2023: 188. [9] 陈锦富, 冯乔伟, 蔡赛华, 等. 基于形式化方法的区块链系统漏洞检测模型[J]. 软件学报, 2024, 35(9): 4193–4217. doi: 10.13328/j.cnki.jos.007133.CHEN Jinfu, FENG Qiaowei, CAI Saihua, et al. Vulnerability detection model for blockchain systems based on formal method[J]. Journal of Software, 2024, 35(9): 4193–4217. doi: 10.13328/j.cnki.jos.007133. [10] 王利朋, 关志, 李青山, 等. 区块链数据安全服务综述[J]. 软件学报, 2023, 34(1): 1–32. doi: 10.13328/j.cnki.jos.006402.WANG Lipeng, GUAN Zhi, LI Qingshan, et al. Survey on blockchain-based security services[J]. Journal of Software, 2023, 34(1): 1–32. doi: 10.13328/j.cnki.jos.006402. [11] 郭加树, 王琪, 李择亚, 等. 基于双层孪生神经网络的区块链智能合约分类方法[J]. 电子与信息学报, 2024, 46(3): 1060–1068. doi: 10.11999/JEIT230185.GUO Jiashu, WANG Qi, LI Zeya, et al. Blockchain smart contract classification method based on double siamese neural network[J]. Journal of Electronics & Information Technology, 2024, 46(3): 1060–1068. doi: 10.11999/JEIT230185. [12] 徐恪, 凌思通, 李琦, 等. 基于区块链的网络安全体系结构与关键技术研究进展[J]. 计算机学报, 2021, 44(1): 55–83. doi: 10.11897/SP.J.1016.2021.00055.XU Ke, LING Sitong, LI Qi, et al. Research progress of network security architecture and key technologies based on blockchain[J]. Chinese Journal of Computers, 2021, 44(1): 55–83. doi: 10.11897/SP.J.1016.2021.00055. [13] CHEN Huashan, PENDLETON M, NJILLA L, et al. A survey on ethereum systems security: Vulnerabilities, attacks, and defenses[J]. ACM Computing Surveys, 2020, 53(3): 67. doi: 10.1145/3391195. [14] WU Jiajing, LIU Jieli, ZHAO Yijing, et al. Analysis of cryptocurrency transactions from a network perspective: An overview[J]. Journal of Network and Computer Applications, 2021, 190: 103139. doi: 10.1016/j.jnca.2021.103139. [15] ZHANG Peiyun, LI Chenxi, ZHOU Mengchu, et al. Transaction transmission model for blockchain channels based on non-cooperative games[J]. Science China Information Sciences, 2023, 66(1): 112105. doi: 10.1007/s11432-021-3362-9. [16] TOYODA K, OHTSUKI T, and MATHIOPOULOS P T. Identification of high yielding investment programs in bitcoin via transactions pattern analysis[C]. 2017 IEEE Global Communications Conference (GLOBECOM 2017), Singapore, Singapore, 2017: 1–6. doi: 10.1109/GLOCOM.2017.8254420. [17] CHEN Weili, ZHENG Zibin, CUI Jiahui, et al. Detecting ponzi schemes on ethereum: Towards healthier blockchain technology[C]. The 2018 World Wide Web Conference, Lyon, France, 2018: 1409–1418. doi: 10.1145/3178876.3186046. [18] WU Jiajing, YUAN Qi, LIN Dan, et al. Who are the phishers? Phishing scam detection on Ethereum via network embedding[J]. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 2022, 52(2): 1156–1166. doi: 10.1109/TSMC.2020.3016821. [19] NEUDECKER T and HARTENSTEIN H. Could network information facilitate address clustering in bitcoin?[C]. FC 2017 International Workshops, WAHC, BITCOIN, VOTING, WTSC, and TA on Financial Cryptography and Data Security, Sliema, Malta, 2017: 155–169. doi: 10.1007/978-3-319-70278-0_9. [20] SPAGNUOLO M, MAGGI F, and ZANERO S. BitIodine: Extracting intelligence from the bitcoin network[C]. The 18th International Conference on Financial Cryptography and Data Security, Christ Church, Barbados, 2014: 457–468. doi: 10.1007/978-3-662-45472-5_29. [21] OBER M, KATZENBEISSER S, and HAMACHER K. Structure and anonymity of the bitcoin transaction graph[J]. Future Internet, 2013, 5(2): 237–250. doi: 10.3390/fi5020237. [22] RON D and SHAMIR A. How did dread pirate roberts acquire and protect his bitcoin wealth?[C]. The 18th International Conference on Financial Cryptography and Data Security Workshops (FC’14), Christ Church, Barbados, 2014: 3–15. doi: 10.1007/978-3-662-44774-1_1. [23] CHEN Weili, WU Jun, ZHENG Zibin, et al. Market manipulation of bitcoin: Evidence from mining the Mt. Gox transaction network[C]. The 38th IEEE Conference on Computer Communications (INFOCOM’2019), Paris, France, 2019: 964–972. doi: 10.1109/INFOCOM.2019.8737364. [24] LIN Dan, WU Jiajing, YUAN Qi, et al. Modeling and understanding ethereum transaction records via a complex network approach[J]. IEEE Transactions on Circuits and Systems II: Express Briefs, 2020, 67(11): 2737–2741. doi: 10.1109/TCSII.2020.2968376. [25] LIN Dan, WU Jiajing, YUAN Qi, et al. T-EDGE: Temporal WEighted MultiDiGraph embedding for ethereum transaction network analysis[J]. Frontiers in Physics, 2020, 8: 204. doi: 10.3389/fphy.2020.00204. [26] SHEN Jie, ZHOU Jiajun, XIE Yunyi, et al. Identity inference on blockchain using graph neural network[C]. Tthe 3rd International Conference on Blockchain and Trustworthy Systems, Guangzhou, China, 2021: 3–17. doi: 10.1007/978-981-16-7993-3_1. [27] LI Sijia, GOU Gaopeng, LIU Chang, et al. TTAGN: Temporal transaction aggregation graph network for ethereum phishing scams detection[C]. The ACM Web Conference 2022 (WWW’22), Lyon, France, 2022: 661–669. doi: 10.1145/3485447.3512226. [28] ZHOU Jiajun, HU Chenkai, CHI Jianlei, et al. Behavior-aware account de-anonymization on ethereum interaction graph[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 3433–3448. doi: 10.1109/TIFS.2022.3208471. [29] MAKRIDIS C A, FRÖWIS M, SRIDHAR K, et al. The rise of decentralized cryptocurrency exchanges: Evaluating the role of airdrops and governance tokens[J]. Journal of Corporate Finance, 2023, 79: 102358. doi: 10.1016/j.jcorpfin.2023.102358. [30] WANG Chaofan, DAI Xiaohai, XIAO Jiang, et al. Demystifying ethereum account diversity: Observations, models and analysis[J]. Frontiers of Computer Science, 2022, 16(4): 164505. doi: 10.1007/s11704-021-0221-3. [31] JIN Hai, LI Chenchen, XIAO Jiang, et al. Detecting arbitrage on ethereum through feature fusion and positive-unlabeled learning[J]. IEEE Journal on Selected Areas in Communications, 2022, 40(12): 3660–3671. doi: 10.1109/JSAC.2022.3213335. [32] HU Jiahao, CAO Mingpei, ZHANG Xizhe, et al. Temporal weighted heterogeneous multigraph embedding for ethereum phishing scams detection[C]. The 26th International Conference on Computer Supported Cooperative Work in Design (CSCWD’23), Rio de Janeiro, Brazil, 2023: 1208–1213. doi: 10.1109/CSCWD57460.2023.10152679. [33] TAN Runnan, TAN Qingfeng, ZHANG Peng, et al. Graph neural network for ethereum fraud detection[C]. 2021 IEEE International Conference on Big Knowledge (ICBK'21), Auckland, New Zealand, 2021: 78–85. doi: 10.1109/ICKG52313.2021.00020. [34] ZHOU Chenyu, CHEN Hongzhou, WU Hao, et al. ARTEMIS: Detecting airdrop hunters in NFT markets with a graph learning system[C]. The ACM Web Conference 2024 (WWW’24), Singapore, Singapore, 2024: 1824–1834. doi: 10.1145/3589334.3645597. [35] XIA Pengcheng, WANG Haoyu, GAO Bingyu, et al. Trade or Trick?: Detecting and characterizing scam tokens on uniswap decentralized exchange[J]. Proceedings of the ACM on Measurement and Analysis of Computing Systems, 2021, 5(3): 39. doi: 10.1145/3491051. [36] MAZORRA B, ADAN V, and DAZA V. Do not rug on me: Leveraging machine learning techniques for automated scam detection[J]. Mathematics, 2022, 10(6): 949. doi: 10.3390/math10060949. [37] NGUYEN M H, HUYNH P D, DAU S H, et al. Rug-pull malicious token detection on blockchain using supervised learning with feature engineering[C]. 2023 Australasian Computer Science Week (ACSW’23), Melbourne, Australia, 2023: 72–81. doi: 10.1145/3579375.3579385. [38] VAPNIK V N. An overview of statistical learning theory[J]. IEEE Transactions on Neural Networks, 1999, 10(5): 988–999. doi: 10.1109/72.788640. [39] KE Guolin, MENG Qi, FINLEY T, et al. LightGBM: A highly efficient gradient boosting decision tree[C]. The 31st International Conference on Neural Information Processing Systems (NIPS’17), Long Beach, USA, 2017: 3149–3157. [40] PEROZZI B, AL-RFOU R, and SKIENA S. DeepWalk: Online learning of social representations[C]. The 20th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining (KDD’14), New York, USA, 2014: 701–710. doi: 10.1145/2623330.2623732. [41] GROVER A and LESKOVEC J. node2vec: Scalable feature learning for networks[C]. The 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining (KDD’16), San Francisco, USA, 2016: 855–864. doi: 10.1145/2939672.2939754. [42] XU Keyulu, HU Weihua, LESKOVEC J, et al. How powerful are graph neural networks?[C]. The 7th International Conference on Learning Representations (ICLR’19), New Orleans, USA, 2019. [43] VELIČKOVIĆ P, CUCURULL G, CASANOVA A, et al. Graph attention networks[C]. The 6th International Conference on Learning Representations (ICLR’18), Vancouver, Canada, 2018: 10–48550. [44] HAMILTON W L, YING R, and LESKOVEC J. Inductive representation learning on large graphs[C]. The 31st International Conference on Neural Information Processing Systems (NIPS’17), Long Beach, USA, 2017: 1025–1035. [45] YUN S, JEONG M, KIM R, et al. Graph transfomer networks[C]. The 33rd International Conference on Neural Information Processing Systems (NeurIPS’19), Vancouver, Canada, 2019: 1073. -





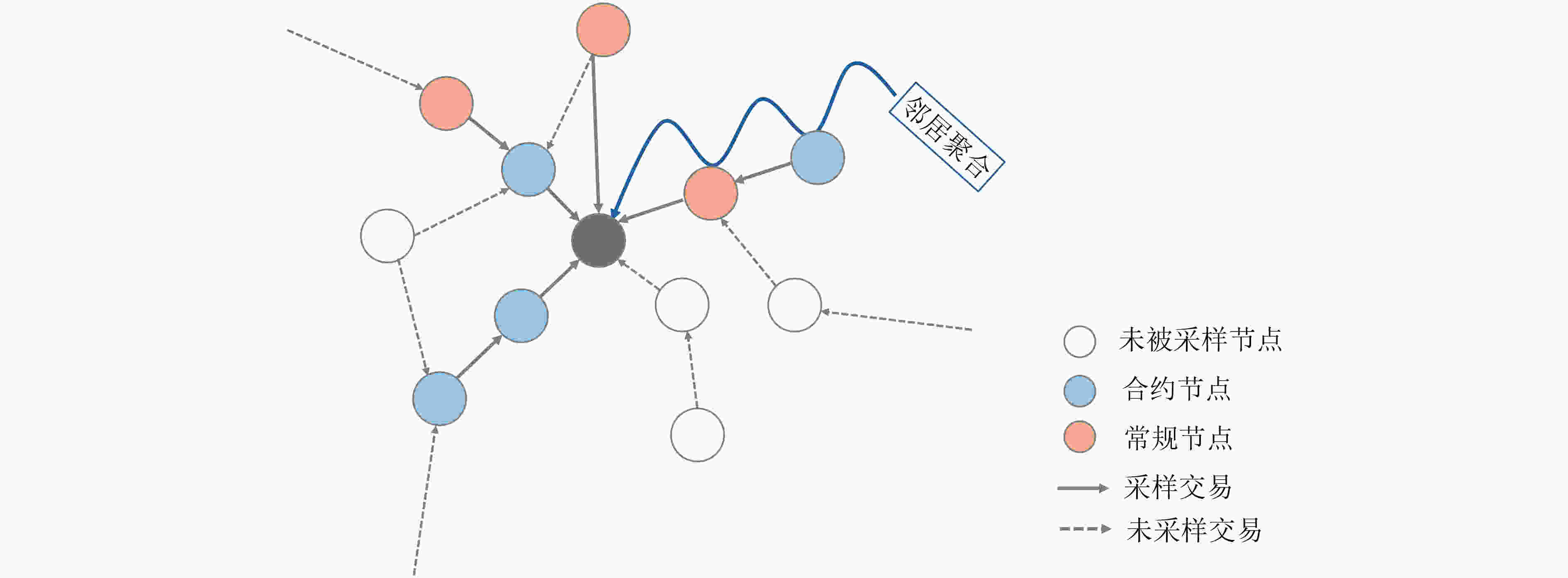
 下载:
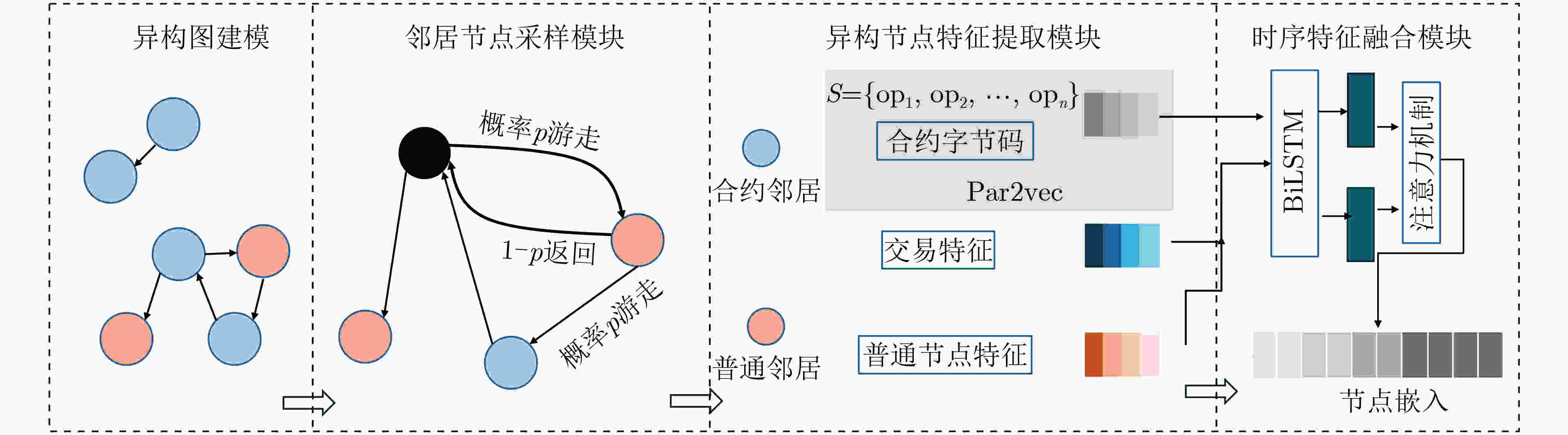
下载:
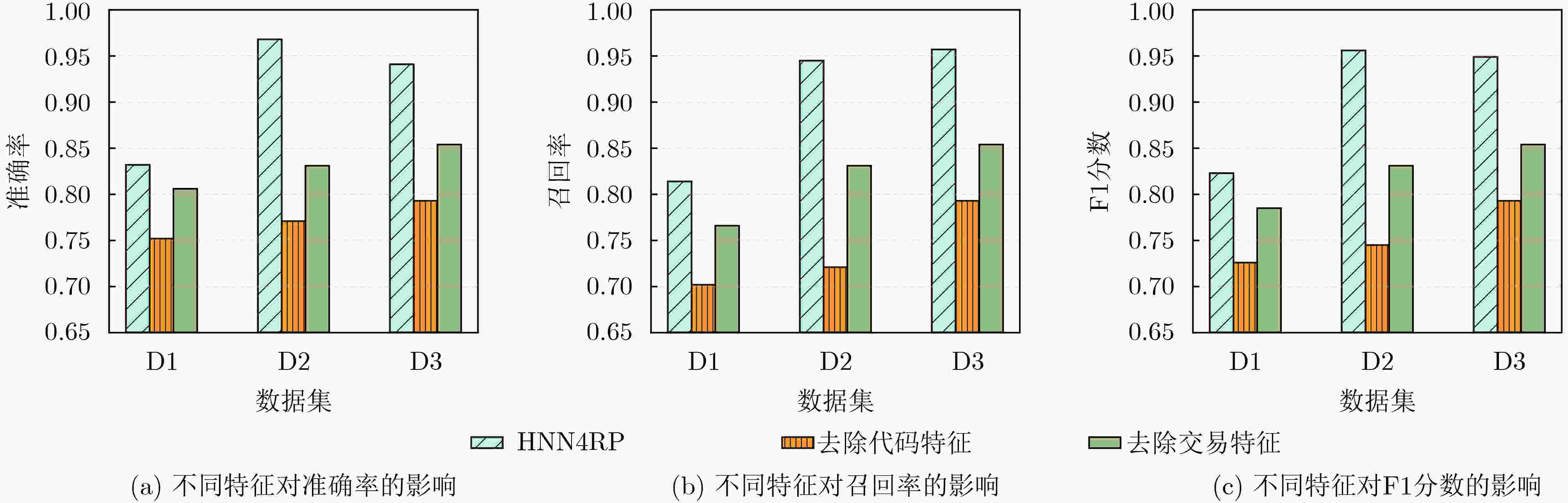
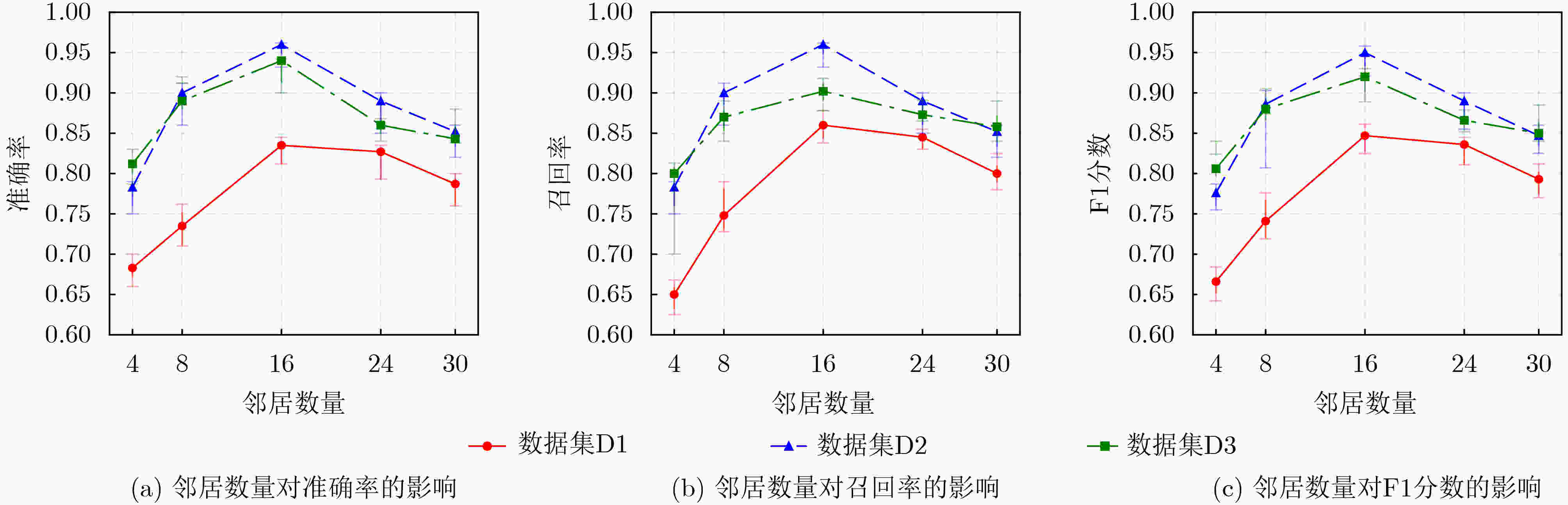


 下载:
下载:
