Decentralized Anti-quantum Internet of Vehicles Data Sharing Scheme
-
摘要: 基于传统密码技术的车联网数据共享正面临着量子计算威胁。NTRU格是当前保障抗量子数据共享的有效手段。该文提出基于NTRU格的去中心化车联网数据共享方案,环中带错误学习 (RLWE)问题和环中小整数解 (RSIS)问题的难解性下具有抗量子安全性,NTRU格密钥尺寸短且存储空间小的特性能够保证低计算复杂度。通过区块链技术实现车辆身份验证、权限管理、密钥分发及智能合约自动化执行。所提方案能够为智能安全交通未来发展奠定技术支撑。Abstract:
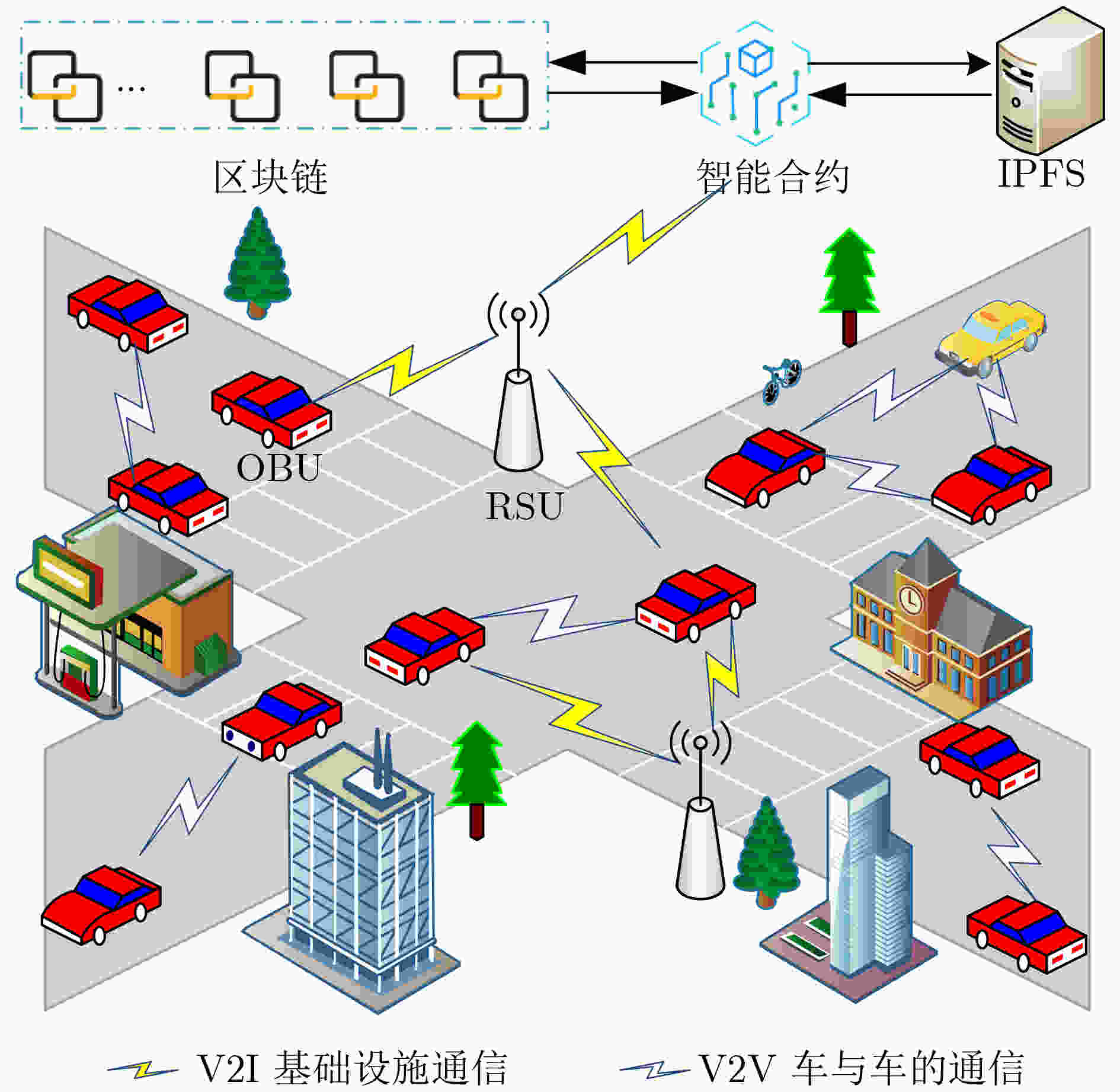
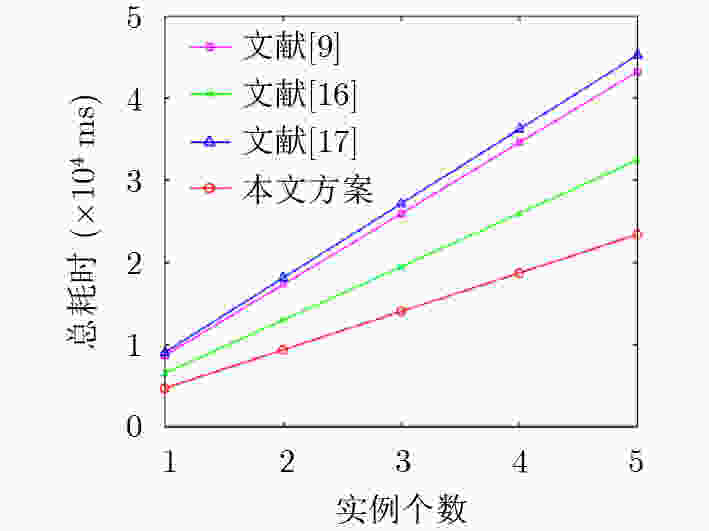
Objective Internet of Vehicles (IoV) faces emerging threats from quantum computing. NTRU lattice offers an effective approach to achieve anti-quantum security in data sharing. This study develops a decentralized anti-quantum IoV data sharing scheme. New scheme ensures the IND-CCA2 and UF-CMA security under the hardness of NTRU lattice computing problem; it uses short keys and small storage space to maintain low calculation complexity. Blockchain is employed to support the vehicle authentication, access control, key distribution and automated execution of smart contracts. New scheme provides a reliable anti-quantum solution for IoV data sharing and technical support for future development of intelligent transportation. Methods Based on unique identifiers and attribute set, the smart contract uses the Gaussian sampling algorithm to generate partial private keys and attribute private keys for users. Public-private key pairs are obtained during the key generation phase. IoV model integrates the blockchain, smart contracts, IPFS, RSUs, and OBUs. Smart contracts store and verify the data-sharing records, while IPFS stores encrypted IoV data to enhance the reliability and reduce the storage cost. RSUs collect the data uploaded by OBUs and forward it to the blockchain which broadcasts real-time traffic information to vehicles. Smart contracts dynamically evaluate the user permissions according to predefined access policies and trigger corresponding operations. Concurrent access experiments were conducted in large-scale and dynamic IoV scenario. Simulations under varying concurrent OBU access requests demonstrated that distributed blockchain architecture and smart contract permission verification enables the system to maintain stable performance under high concurrency. Results and Discussions The proposed scheme computes the data sharing signcryption strategy in accordance with current IoV security requirements. Table 2 reports four instances of private key, ciphertext and signature sizes.Table 3 compares its security characteristics and communication overhead , showing that the proposed scheme requires less overhead.Table 4 demonstrates that, as the number of concurrent users increases from 100 to1000 , the proposed scheme achieves lower total latency and more linear Throughput-Per-Second (TPS) growth compared with scheme [9].Figure 2 illustrates that although the time consumption of all schemes increases with higher parameter values, the proposed scheme consistently exhibits the lowest time cost.Conclusions In the proposed scheme, the user private keys are bound to attribute sets and the data access is controlled by predefined access policies. This design ensures that only users with specific attributes can perform unsigncryption, thereby enabling fine-grained access control. The trapdoor generation and Gaussian sampling algorithms within the NTRU lattice reduce key size while ensuring anti-quantum security for IoV data transmission and storage. The integration of IPFS, blockchain, and smart contracts enables efficient index management and permission control, which strengthens the reliability of IoV system. The scheme supports concurrent access by large numbers of IoV users and has the potential to mitigate traffic accidents. -
Key words:
- Internet of vehicles /
- NTRU lattice /
- Data sharing /
- Attribute-based signcryption /
- Smart contract
-
表 1 不同操作的平均时间(ms)
符号 执行操作 平均耗时 $ {T}_{\mathrm{M}} $ 矩阵或向量模乘 4.512 $ {T}_{\mathrm{h}} $ 哈希运算 11.135 $ {T}_{\mathrm{G}} $ 高斯采样算法运算 9.531 $ {T}_{\mathrm{M}\mathrm{u}\mathrm{l}} $ 多项式模乘 0.028 表 2 具体实例比较情况
实例1 实例2 实例3 实例4 $ n $ 128 136 192 256 $ k $ 16 16 16 16 $ m $ 25 25 25 25 $ q $ $ {2}^{18} $ $ {2}^{25} $ $ {2}^{26} $ $ {2}^{33} $ 文献[9]私钥大小 36 864 85 000 79 872 135 168 文献[16]私钥大小 44 064 64 400 86 800 112 400 文献[17]私钥大小 74 628 110 050 161 044 271 986 本文方案私钥大小 9 216 13 600 19 968 33 792 文献[9]的签名大小 4 680 6 880 9 984 16 896 本文方案签名大小 2 304 3 440 4 992 8 448 文献[9]密文大小 9 360 13 760 19 768 33 792 文献[16]密文大小 9 216 13 600 19 968 33 792 文献[17]密文大小 5 508 8 050 11 284 18 546 本文方案密文大小 4 680 6 880 9 984 16 896 表 3 安全属性和开销比较情况
文献[9] 文献[16] 文献[17] 本文方案 抗量子安全 √ √ √ √ 不可伪造性 √ × × √ 机密性 √ √ √ √ 困难问题 LWE/SIS RLWE LWE RLWE/RSIS 无证书管理 √ √ × √ 应用于区块链 √ × × √ 私钥大小 $ mn{\mathrm{l}\mathrm{o}\mathrm{g}}_{2}\left(q\right) $ $ (n+m)k{\mathrm{l}\mathrm{o}\mathrm{g}}_{2}\left(q\right) $ $ (nk+m){\mathrm{l}\mathrm{o}\mathrm{g}}_{2}\left(2q\right) $ $ 4n{\mathrm{l}\mathrm{o}\mathrm{g}}_{2}q $ 签名大小 $ 2n{\mathrm{l}\mathrm{o}\mathrm{g}}_{2}\left(q\right) $ / / $ n{\mathrm{l}\mathrm{o}\mathrm{g}}_{2}\left(q\right) $ 密文大小 $ {n}^{2}{\mathrm{l}\mathrm{o}\mathrm{g}}_{2}\left(q\right) $ $ 2n{\mathrm{l}\mathrm{o}\mathrm{g}}_{2}\left(2q\right) $ $ \left(n+m\right){\mathrm{l}\mathrm{o}\mathrm{g}}_{2}\left(2q\right) $ $ 2n{\mathrm{l}\mathrm{o}\mathrm{g}}_{2}\left(q\right) $ 总耗时(ms) $ 5{T}_{\mathrm{h}}+7{T}_{\mathrm{M}} $ $ 3{T}_{\mathrm{G}}+{8T}_{\mathrm{M}}+16{T}_{\mathrm{M}\mathrm{u}\mathrm{l}} $ $ 4{T}_{\mathrm{h}}+3{T}_{\mathrm{G}}+{4T}_{\mathrm{M}} $ $ 3{T}_{\mathrm{h}}+2{T}_{\mathrm{G}}+{T}_{\mathrm{M}}+12{T}_{\mathrm{M}\mathrm{u}\mathrm{l}} $ -
[1] TAN K, BREMNER D, LE KERNEC J, et al. Machine learning in vehicular networking: An overview[J]. Digital Communications and Networks, 2022, 8(1): 18–24. doi: 10.1016/j.dcan.2021.10.007. [2] YU Huifang, ZHANG Qi, and LI Lei. Certificateless anti-quantum blind signcryption for e-cash[J]. Journal of Industrial Information Integration, 2024, 40: 100632. doi: 10.1016/j.jii.2024.100632. [3] WU Dapeng, NIE Chengyu, YANG Zhigang, et al. Distributed secure data sharing method for internet of vehicles based on homomorphic hash tree[J]. IEEE Transactions on Vehicular Technology, 2024, 73(11): 17572–17585. doi: 10.1109/TVT.2024.3422974. [4] TAN Xudong, CHENG Wei, HUANG Haiping, et al. Edge-aided searchable data sharing scheme for IoV in the 5G environment[J]. Journal of Systems Architecture, 2023, 136: 102834. doi: 10.1016/j.sysarc.2023.102834. [5] ZU Guangao, LU Yang, and LI Jiguo. Comment on an attribute-based searchable encryption scheme with receiver anonymity[J]. IEEE Transactions on Services Computing, 2024, 17(4): 1875–1876. doi: 10.1109/TSC.2023.3332864. [6] GU Ke, QIU Juan, PENG Xin, et al. Traceable attribute-based keyword search scheme for distributed data storage under fog computing-based social internet of vehicles[J]. IEEE Transactions on Cognitive Communications and Networking. doi: 10.1109/TCCN.2025.3528887. [7] GUO Zhenzhen, WANG Gaodi, LI Yingxin, et al. Accountable attribute-based data-sharing scheme based on blockchain for vehicular ad hoc network[J]. IEEE Internet of Things Journal, 2023, 10(8): 7011–7026. doi: 10.1109/JIOT.2022.3228550. [8] LI Yuhong, CHEN Ruoyu, and RAHMANI R. Secure data sharing in internet of vehicles based on blockchain and attribute-based encryption[C]. IEEE International Conference on Smart Internet of Things (SmartIoT), Xining, China, 2023: 56–63. doi: 10.1109/SmartIoT58732.2023.00016. [9] CHEN Chen, WANG Lankai, and SHI Quan. A lattice-based certificateless secure data transmission scheme for Internet of Vehicles Based-Blockchain[J]. IEEE Transactions on Vehicular Technology, 2025, 74(2): 2308–2322. doi: 10.1109/TVT.2024.3469385. [10] LIU Gongren, WU Guangfu, XU Su, et al. A data sharing scheme based on consortium blockchain and lattice cryptography in internet of vehicles[C]. 2024 4th International Conference on Blockchain Technology and Information Security (ICBCTIS), Wuhan, China, 2024: 119–123. doi: 10.1109/ICBCTIS64495.2024.00026. [11] GAO Mengli, LI Jinqing, DI Xiaoqiang, et al. A blind signature scheme for IoV based on 2D-SCML image encryption and lattice cipher[J]. Expert Systems with Applications, 2024, 246: 123215. doi: 10.1016/j.eswa.2024.123215. [12] YU Huifang and MU Wenzhuo. ABE-based postquantum cross-blockchain data exchange approach for smart agriculture[J]. IEEE Transactions on Industrial Informatics, 2024, 20(10): 12083–12091. doi: 10.1109/TII.2024.3413684. [13] ANJUM N, LATIF Z, and CHEN Hongsong. Security and privacy of industrial big data: Motivation, opportunities, and challenges[J]. Journal of Network and Computer Applications, 2025, 237: 104130. doi: 10.1016/j.jnca.2025.104130. [14] YU Huifang, WANG Weike, and ZHANG Qi. Certificateless anti-quantum ring signcryption for network coding[J]. Knowledge-Based Systems, 2022, 235: 107655. doi: 10.1016/j.knosys.2021.107655. [15] LI Ruonan, WANG Fuqun, ZHANG Renjun, et al. NTRU-based fully homomorphic signature[J]. Security and Communication Networks, 2022, 2022(1): 9942717. doi: 10.1155/2022/9942717. [16] GUO Kaiyang, HAN Yiliang, WU Riming, et al. CD-ABSE: Attribute-based searchable encryption scheme supporting cross-domain sharing on blockchain[J]. Wireless Communications and Mobile Computing, 2022, 2022(1): 6719302. doi: 10.1155/2022/6719302. [17] WANG Fenghe, WANG Junquan, and SHI Shaoquan. Efficient data sharing with privacy preservation over lattices for secure cloud storage[J]. IEEE Systems Journal, 2022, 16(2): 2507–2517. doi: 10.1109/JSYST.2021.3077236. -





 下载:
下载:


 下载:
下载:
