Reconfigurable Intelligent Surface-empowered Covert Communication Strategies for D2D Systems
-
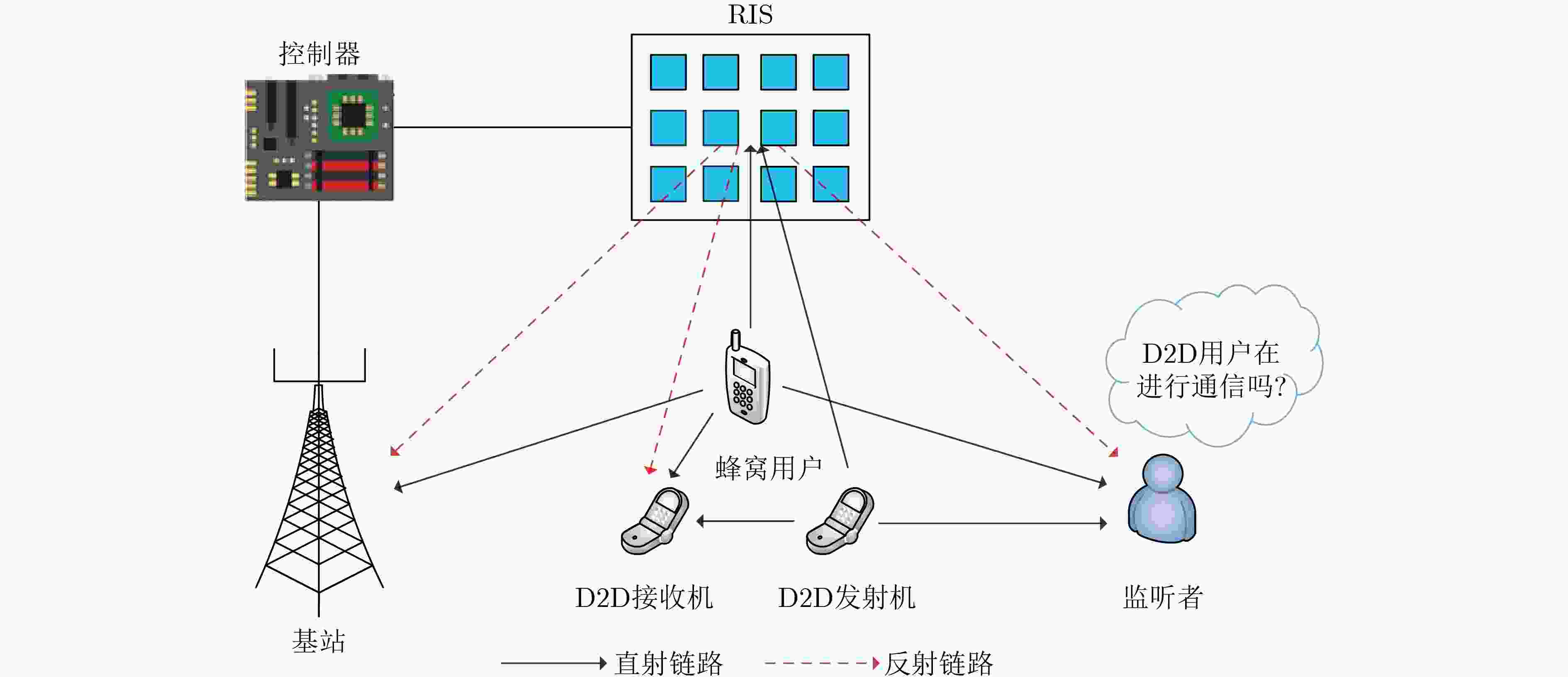
摘要: 为了应对目前设备到设备 (D2D) 隐蔽通信研究中引入额外不确定性源而带来高成本、高功耗的问题,该文提出一种智能超表面 (RIS) 赋能的D2D隐蔽传输方法。该方法借助RIS为合法用户创造更好的无线传播条件的同时,利用RIS的相移不确定性来混淆监听者的检测。为探究所提方法的隐蔽性能增益,在保证监听者低检测概率以及满足蜂窝用户服务质量的条件下,构建通过联合优化蜂窝用户、D2D发射机的发射功率以及RIS相移来最大化D2D用户的隐蔽速率的优化问题。为解决上述变量和约束高度耦合的非凸优化问题,提出一种高效的基于高斯随机化的交替优化算法,求解出最优的蜂窝用户和D2D发射机的发射功率以及RIS相移。仿真结果表明,RIS的辅助给D2D隐蔽传输系统带来了显著的性能提升,通过增加RIS反射元件数量,或提升蜂窝用户发射功率为D2D隐蔽传输提供更好的掩体,都可以进一步提升隐蔽通信性能。Abstract:
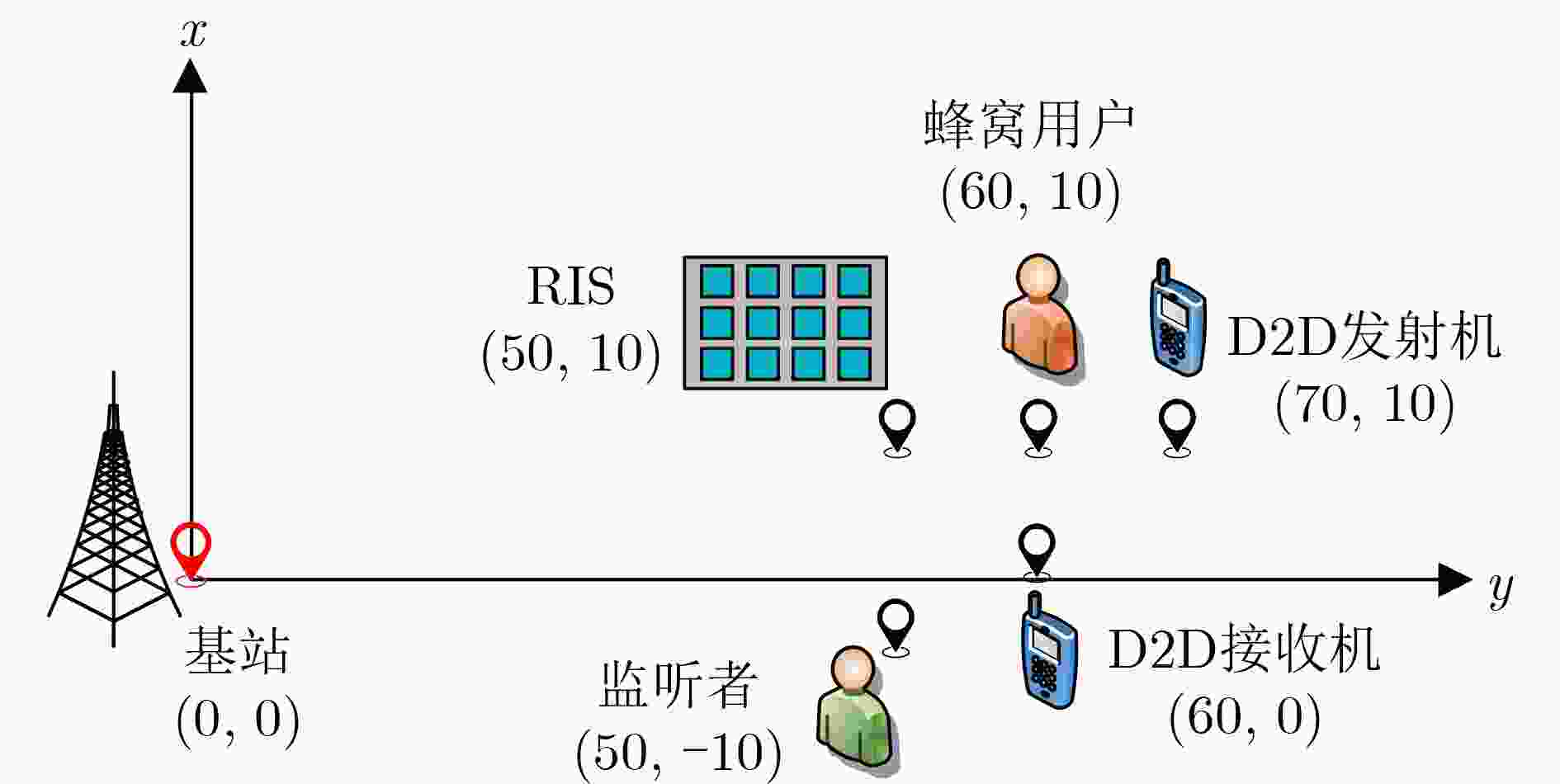
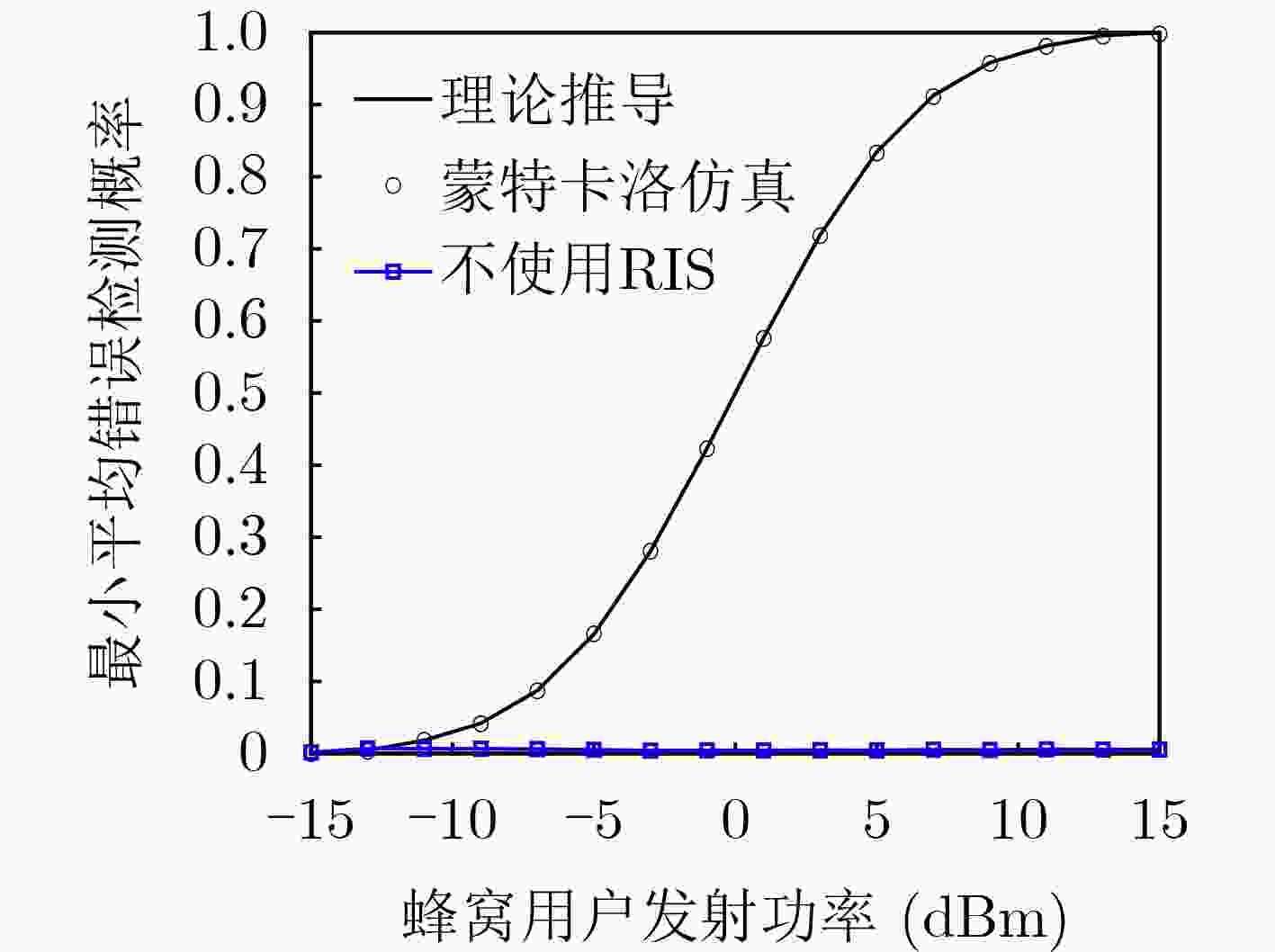
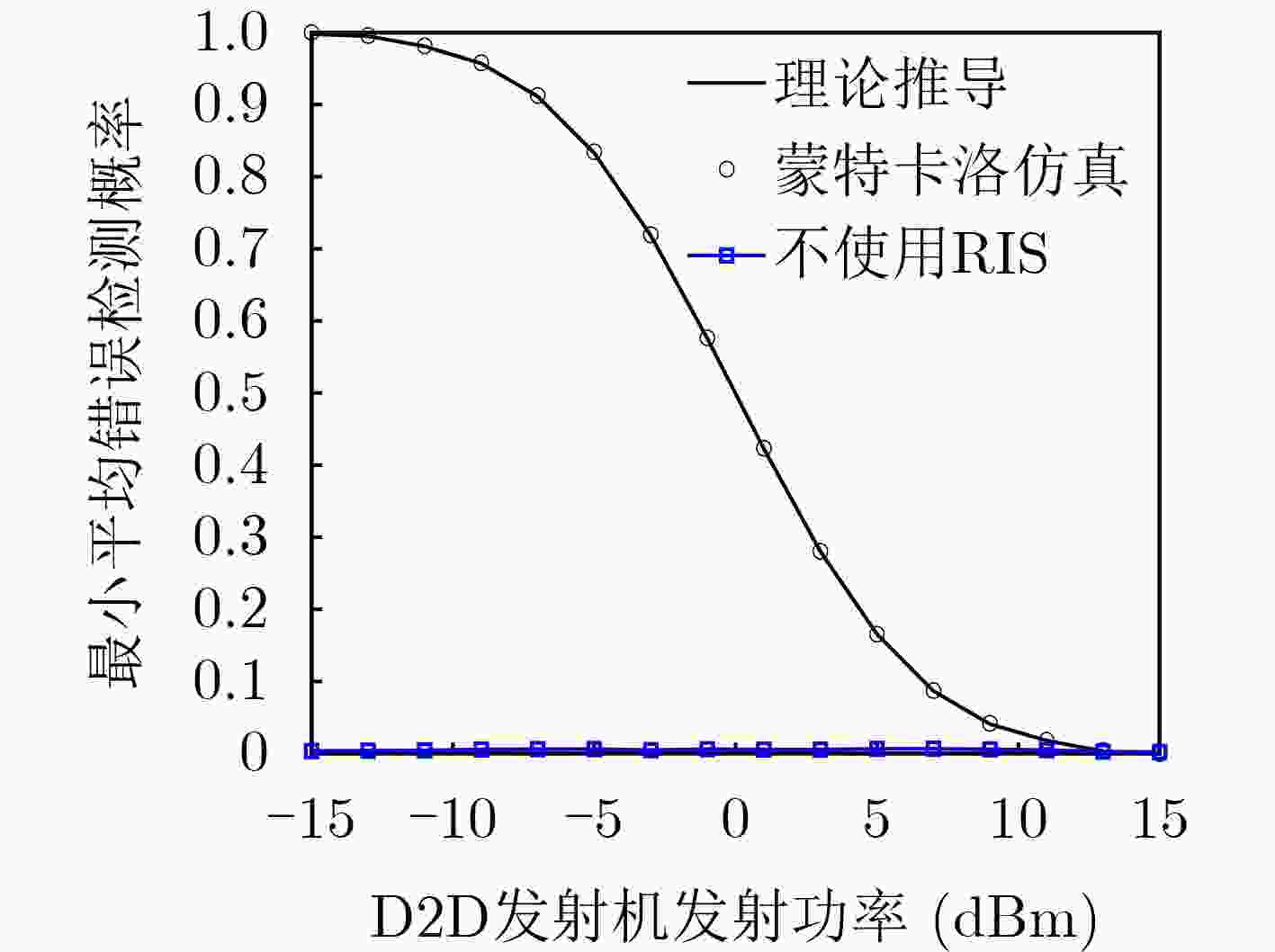
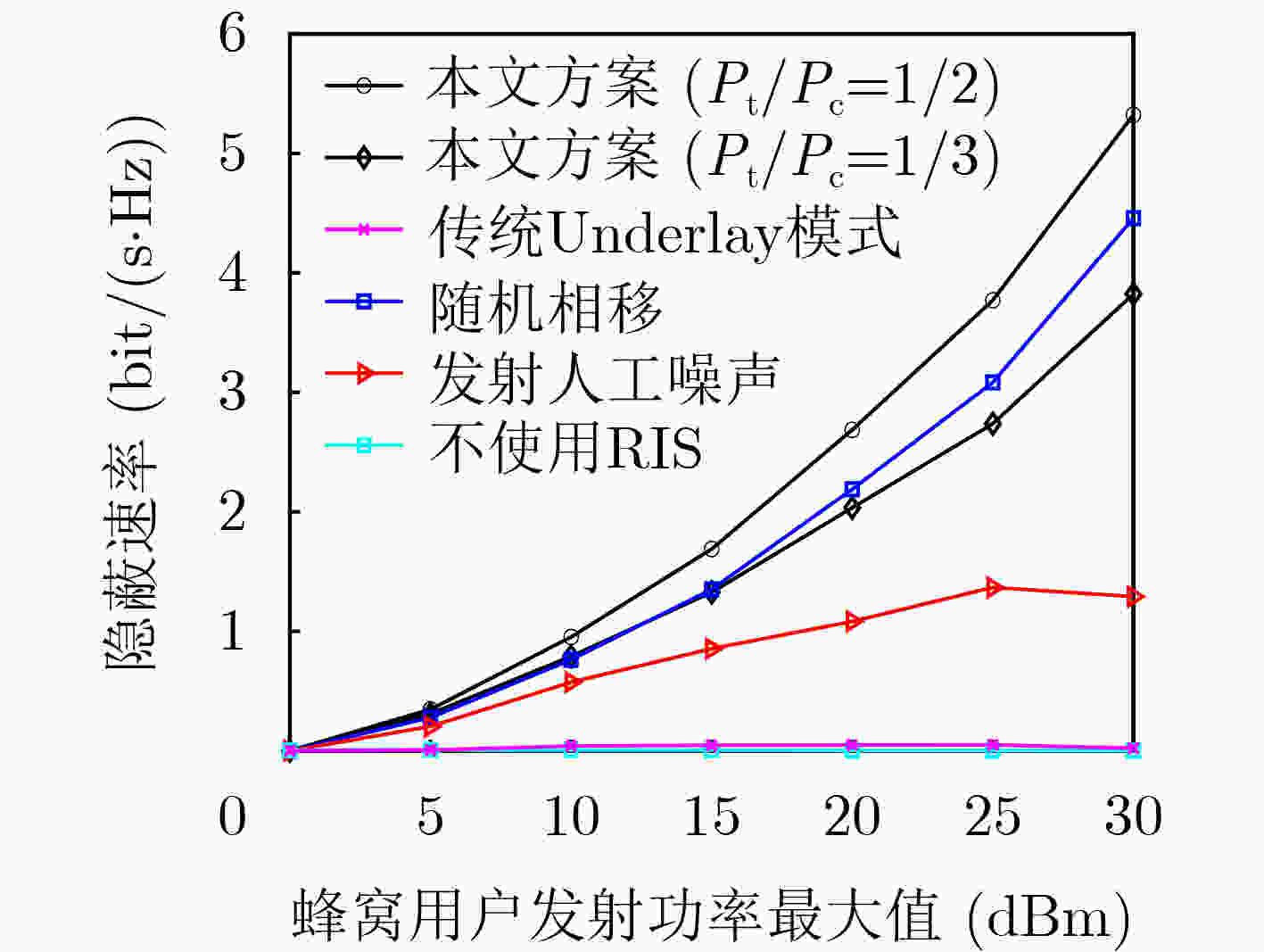
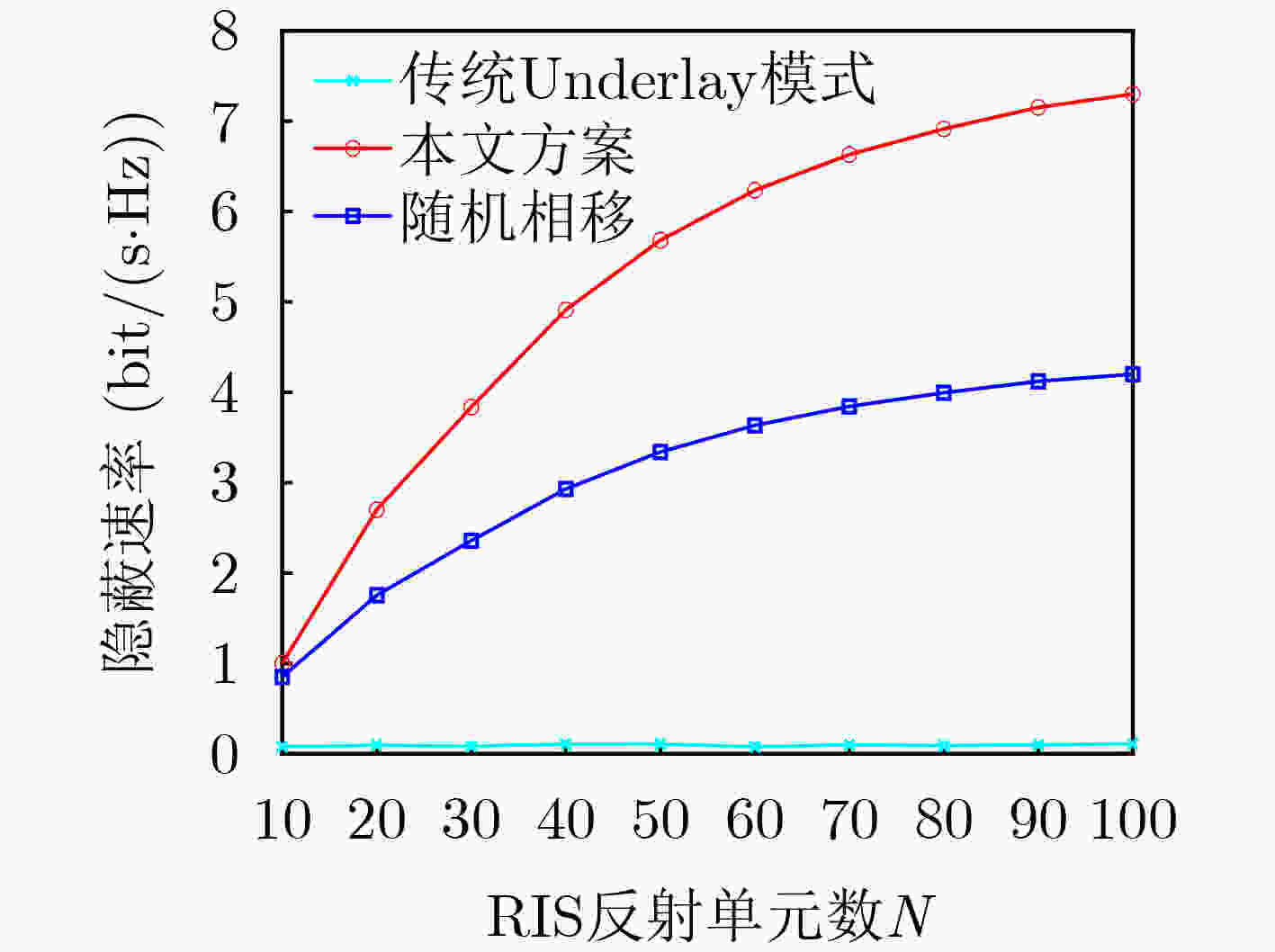
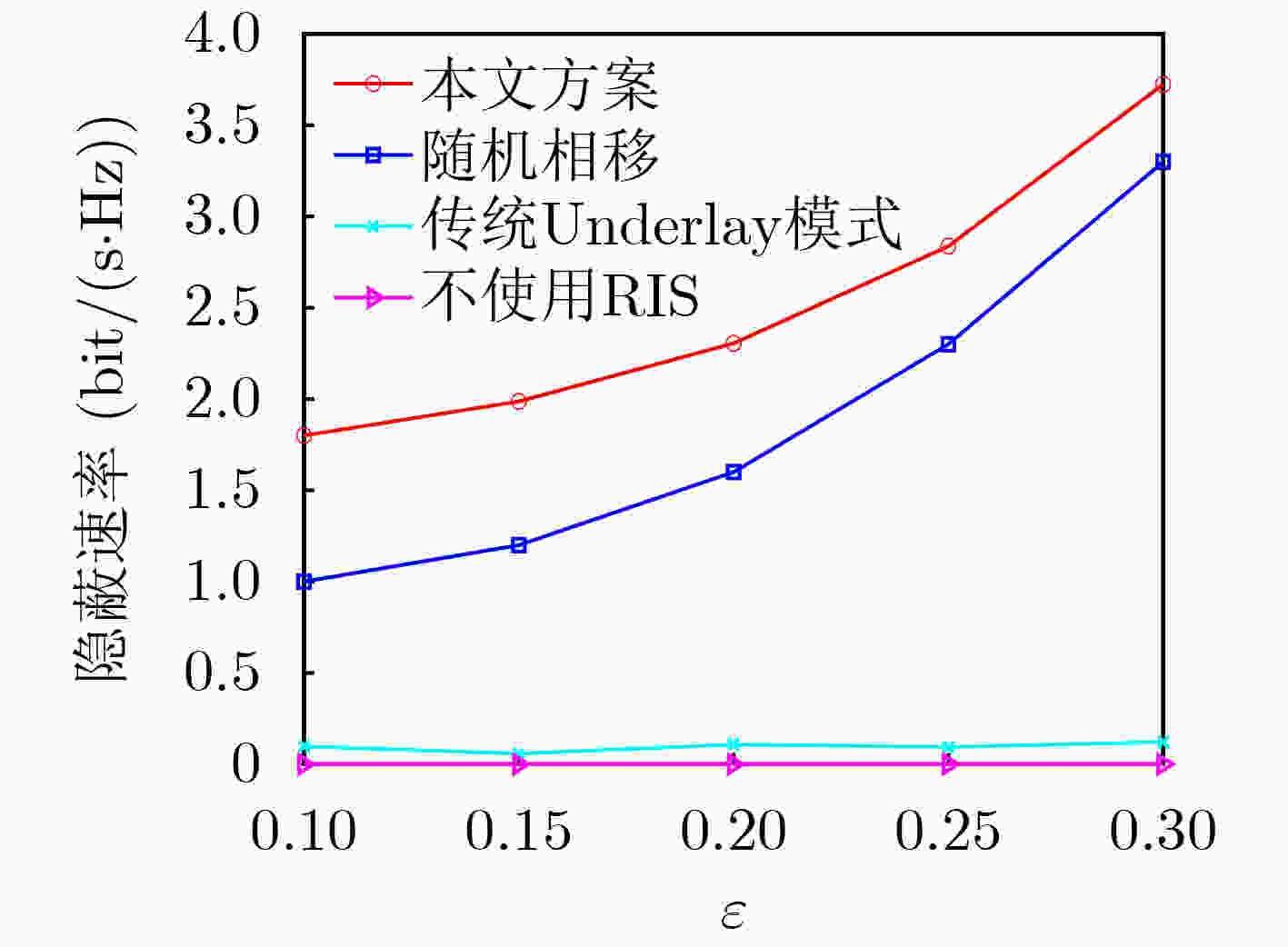
Objective The rising demand for secure communication in sensitive data transmission scenarios has increased interest in covert communication research. Existing Device-to-Device (D2D) covert communication solutions typically employ additional uncertainty mechanisms, such as artificial noise, leading to elevated energy consumption and implementation complexity. This study addresses these issues by investigating a novel covert communication strategy enabled by Reconfigurable Intelligent Surfaces (RIS). The strategy exploits RIS to enhance wireless propagation for legitimate users and simultaneously introduces controlled phase-shift uncertainty to impair eavesdropping effectiveness. The primary objective is to maximize the covert communication rate among D2D users while maintaining a low probability of detection and guaranteeing the Quality of Service (QoS) requirements for cellular users. Methods The proposed framework consists of an RIS-assisted D2D communication network comprising one cellular user, one pair of D2D users, and an eavesdropper aiming to detect ongoing communications. A comprehensive optimization problem is established to jointly optimize the transmit powers of both the cellular and D2D transmitters, as well as the phase shifts of the RIS, to maximize the covert communication rate for D2D users. Given the non-convex nature and highly interdependent variables within the optimization problem, an alternating optimization algorithm utilizing Gaussian randomization is developed. This algorithm iteratively determines the optimal transmission powers and RIS phase-shift configurations, adhering strictly to constraints on power consumption, RIS characteristics, and covert communication detection probabilities. Additionally, Successive Interference Cancellation (SIC) is integrated at the D2D receiver to effectively mitigate interference from cellular communications, facilitating accurate decoding of covert signals. Results and Discussions Simulation results confirm the efficacy of the proposed RIS-enabled covert communication strategy, showing significant performance enhancements over traditional methods. The inclusion of RIS notably improves the covert communication rate for D2D transmissions. For instance, increasing the number of RIS reflective elements enhances system performance further by introducing greater uncertainty in the received signals at the eavesdropper, thus complicating detection efforts ( Fig. 8 ). Furthermore, it is observed that the cellular user’s transmit power inherently acts as an effective shield, increasing confusion for eavesdropping attempts and thus reducing detection accuracy.Convergence of the proposed optimization algorithm is validated through iterative simulation experiments, demonstrating stable and reliable performance across varied conditions and constraints (Fig. 4 ). Additionally, Monte Carlo simulations verify the accuracy of the analytical expressions derived for the minimum average detection error probability achievable by the eavesdropper, highlighting the critical role of RIS in generating sufficient energy uncertainty to ensure covert communication effectiveness (Fig. 5 ,Fig. 6 ). Comparative analyses further illustrate the superior performance of the proposed RIS-based approach relative to conventional artificial noise techniques, particularly in scenarios demanding high covert communication rates. Moreover, the integration of RIS and SIC methods demonstrates notable benefits; SIC efficiently reduces interference from cellular signals, maintaining the cellular user’s QoS without compromising the integrity of covert signals decoded at the D2D receiver.Conclusions This study proposes an advanced RIS-empowered covert communication strategy tailored specifically for D2D networks. The approach successfully leverages RIS-induced phase-shift uncertainty and capitalizes on cellular transmissions as natural interference sources, significantly enhancing covert communication capabilities. Through joint optimization of transmission power allocation and RIS configurations, the proposed method effectively maximizes the covert communication rate while satisfying QoS constraints for cellular users. These promising results establish a solid foundation for future exploration into active RIS-assisted communication schemes and the development of sophisticated optimization strategies aimed at further improving covert communication effectiveness. -
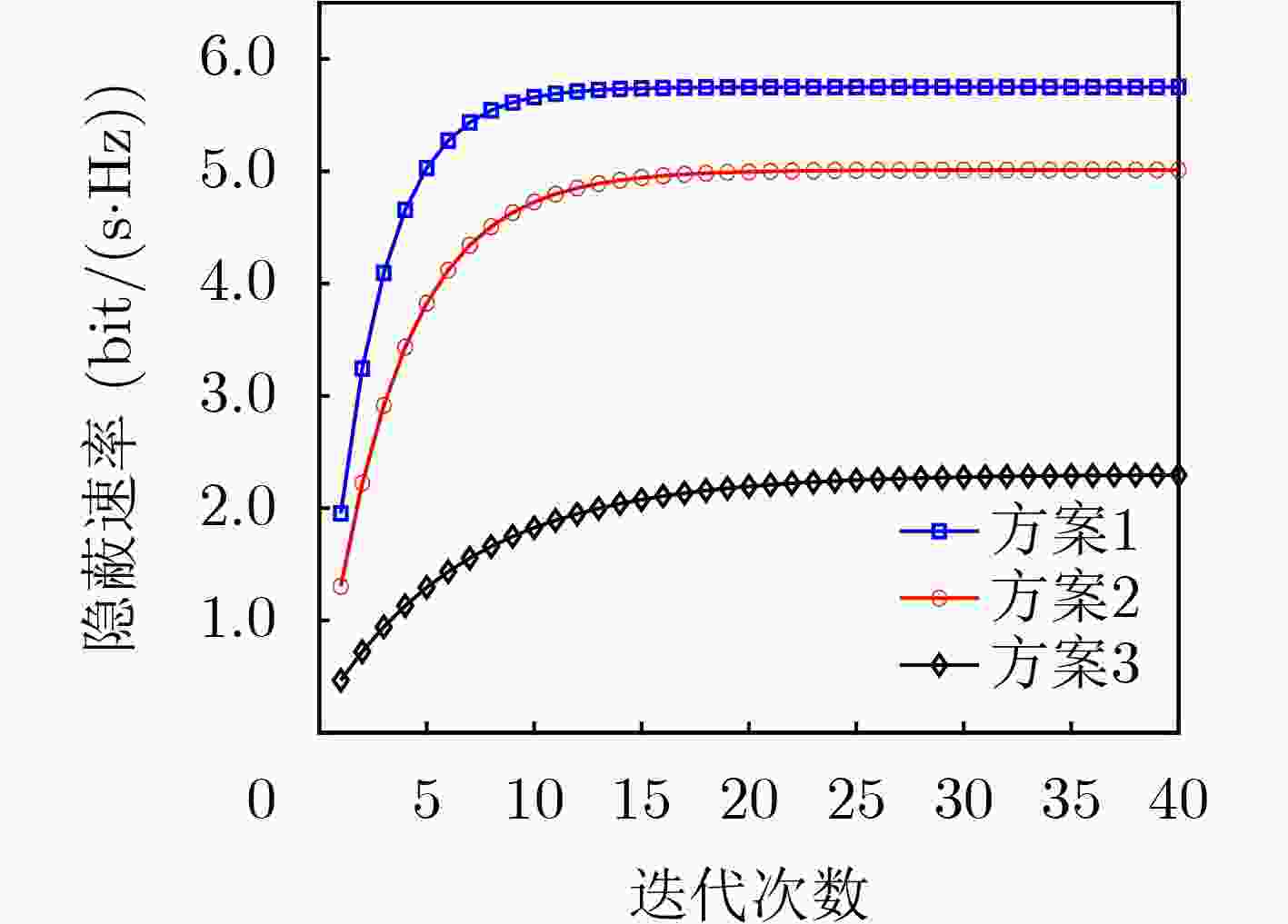
图 4 算法2收敛性曲线
1 高斯随机化算法
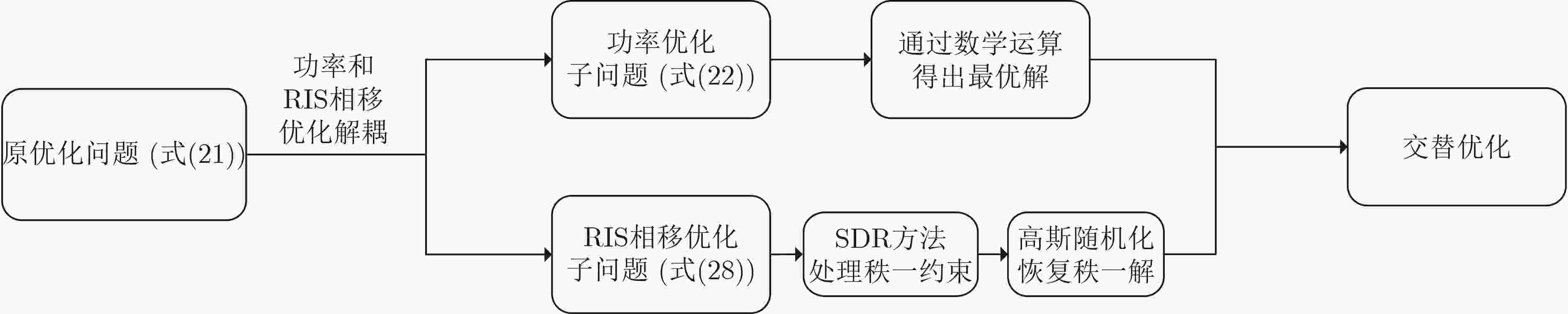
(1) 如果$ {\text{rank}}({\boldsymbol{U}}(t + 1)) = 1 $,则执行: (2) 计算$ {\boldsymbol{U}}(t + 1) $的非零特征值$ {\lambda _{{\mathrm{eigen}}}} $和特征向量$ {{\boldsymbol{\nu}} _{{\mathrm{eigen}}}} $; (3) 返回$ {\boldsymbol{\varTheta}} \left( {t + 1} \right) = {\text{diag}}(\sqrt {{\lambda _{{\mathrm{eigen}}}}} {{\boldsymbol{\nu}} _{{\mathrm{eigen}}}}) $; (4) 否则,执行: (5) 对于$ q = 1,2,\cdots,Q $: (6) 计算$ {\boldsymbol{U}}(t + 1) = {\boldsymbol{V}}{\boldsymbol{\varSigma}} {{\mathbf{V}}^{\rm H}} $并生成$ {e_q} = {\boldsymbol{V}}{\varSigma ^{\frac{1}{2}}}{\boldsymbol{r}}_q $,其中
$ {{\boldsymbol{r}}_q}\text{~}\mathcal{C}\mathcal{N}\left( {{{{\textit{0}}}_{N + 1}},{{\boldsymbol{I}}_{N + 1}}} \right) $;(7) 计算: $ {{\boldsymbol{\varTheta}} _q} = {{\mathrm{diag}}} \left( {{{\rm e}^{{\mathrm{j}}\arg \left( {\frac{{{{\bf{e}}_q}[1]}}{{{{\bf{e}}_q}[N + 1]}}} \right)}}, \cdots ,{{\rm e}^{{\mathrm{j}}\arg \left( {\frac{{{{\bf{e}}_q}[N]}}{{{{\bf{e}}_q}[N + 1]}}} \right)}}} \right) $; (8) 解决问题式(29),更新其目标值,记为$ {R_q} $; (9) 返回: $ {\mathrm{return}}{\text{ }}{\boldsymbol{\varTheta}} \left( {t + 1} \right){\text{ }} = {\text{ }}{\mathrm{arg}}{\text{ }}{\max_{q = 1,2,\cdots,Q}}{\text{ }}{R_q} $; (10) 结束 2 基于高斯随机化的交替优化算法
(1)初始化:${\boldsymbol{\varTheta}} \left( 1 \right)$, ${P_{\rm c}}\left( 1 \right)$, ${P_{\rm t}}\left( 1 \right)$, $ \varrho $;设置迭代索引$t = 1$; (2)重复: (3) 设定$ {\boldsymbol{\varTheta}} \left( t \right) $,解决问题式(22),更新$ {P_{\rm c}}\left( {t + 1} \right) $和$ {P_{\rm t}}\left( {t + 1} \right) $; (4) 设定$ {P_{\rm c}}\left( {t + 1} \right) $和$ {P_{\rm t}}\left( {t + 1} \right) $,解决问题式(28),更新
$ {\boldsymbol{U}}(t + 1) $;(5) 更新$ t = t + 1 $; (6) 结束:目标值的变化量低于阈值$ \varrho $; (7) 通过算法1从$ {\boldsymbol{U}}(t + 1) $中恢复$ {\boldsymbol{\varTheta}} \left( {t + 1} \right) $; -
[1] 卢汉成, 王亚正, 赵丹, 等. 智能反射表面辅助的无线通信系统的物理层安全综述[J]. 通信学报, 2022, 43(2): 171–184. doi: 10.11959/j.issn.1000−436x.2022025.LU Hancheng, WANG Yazheng, ZHAO Dan, et al. Survey of physical layer security of intelligent reflecting surface-assisted wireless communication systems[J]. Journal on Communications, 2022, 43(2): 171–184. doi: 10.11959/j.issn.1000−436x.2022025. [2] MUKHERJEE A, FAKOORIAN S A A, HUANG Jing, et al. Principles of physical layer security in multiuser wireless networks: A survey[J]. IEEE Communications Surveys & Tutorials, 2014, 16(3): 1550–1573. doi: 10.1109/SURV.2014.012314.00178. [3] LV Lu, XU Dongyang, HU R Q, et al. Safeguarding next-generation multiple access using physical layer security techniques: A tutorial[J]. Proceedings of the IEEE, 2024, 112(9): 1421–1466. doi: 10.1109/JPROC.2024.3420127. [4] ZHANG Zheng, CHEN Jian, WU Qingqing, et al. Securing NOMA networks by exploiting intelligent reflecting surface[J]. IEEE Transactions on Communications, 2022, 70(2): 1096–1111. doi: 10.1109/TCOMM.2021.3126636. [5] 罗志勇, 谢映海. 一种用于隐蔽通信的低检测概率波形设计[J]. 信息通信, 2018(8): 63–64. doi: 10.3969/j.issn.1673-1131.2018.08.026.LUO Zhiyong and XIE Yinghai. A low probability of detection waveform design for covert communication[J]. Information & Communications, 2018(8): 63–64. doi: 10.3969/j.issn.1673-1131.2018.08.026. [6] YAN Shihao, ZHOU Xiangyun, HU Jinsong, et al. Low probability of detection communication: Opportunities and challenges[J]. IEEE Wireless Communications, 2019, 26(5): 19–25. doi: 10.1109/MWC.001.1900057. [7] 周小波, 于辉, 彭旭, 等. 智能反射面辅助及人工噪声增强的无线隐蔽通信[J]. 电子与信息学报, 2022, 44(7): 2392–2399. doi: 10.11999/JEIT211618.ZHOU Xiaobo, YU Hui, PENG Xu, et al. Wireless covert communications based on intelligent reflecting surface aided and artificial noise enhanced[J]. Journal of Electronics & Information Technology, 2022, 44(7): 2392–2399. doi: 10.11999/JEIT211618. [8] 陈炜宇, 骆俊杉, 王方刚, 等. 无线隐蔽通信容量限与实现技术综述[J]. 通信学报, 2022, 43(8): 203–218. doi: 10.11959/j.issn.1000−436x.2022153.CHEN Weiyu, LUO Junshan, WANG Fanggang, et al. Survey of capacity limits and implementation techniques in wireless covert communication[J]. Journal on Communications, 2022, 43(8): 203–218. doi: 10.11959/j.issn.1000−436x.2022153. [9] MA Yue, MA Ruiqian, LIN Zhi, et al. Improving age of information for covert communication with time-modulated arrays[J]. IEEE Internet of Things Journal, 2025, 12(2): 1718–1731. doi: 10.1109/JIOT.2024.3466855. [10] WANG Chao, XIONG Zehui, ZHENG Meng, et al. Covert communications via two-way IRS with noise power uncertainty[J]. IEEE Transactions on Communications, 2024, 72(8): 4803–4815. doi: 10.1109/TCOMM.2024.3381672. [11] WANG Chao, LI Zan, SHI Jia, et al. Intelligent reflecting surface-assisted multi-antenna covert communications: Joint active and passive beamforming optimization[J]. IEEE Transactions on Communications, 2021, 69(6): 3984–4000. doi: 10.1109/TCOMM.2021.3062376. [12] FENG Shaohan, LU Xiao, SUN Sumei, et al. Securing large-scale D2D networks using covert communication and friendly jamming[J]. IEEE Transactions on Wireless Communications, 2024, 23(1): 592–606. doi: 10.1109/TWC.2023.3280464. [13] HE Biao, YAN Shihao, ZHOU Xiangyun, et al. On covert communication with noise uncertainty[J]. IEEE Communications Letters, 2017, 21(4): 941–944. doi: 10.1109/LCOMM.2016.2647716. [14] YANG Bin, TALEB T, FAN Yuanyuan, et al. Mode selection and cooperative jamming for covert communication in D2D underlaid UAV networks[J]. IEEE Network, 2021, 35(2): 104–111. doi: 10.1109/MNET.011.2000100. [15] HU Jinsong, YAN Shihao, ZHOU Xiangyun, et al. Covert communication achieved by a greedy relay in wireless networks[J]. IEEE Transactions on Wireless Communications, 2018, 17(7): 4766–4779. doi: 10.1109/TWC.2018.2831217. [16] LV Lu, LI Zan, DING Haiyang, et al. Achieving covert wireless communication with a multi-antenna relay[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 760–773. doi: 10.1109/TIFS.2022.3152353. [17] SHMUEL O, COHEN A, and GUREWITZ O. Multi-antenna jamming in covert communication[J]. IEEE Transactions on Communications, 2021, 69(7): 4644–4658. doi: 10.1109/TCOMM.2021.3067386. [18] JIANG Yu’e, WANG Liangmin, and CHEN H H. Covert communications in D2D underlaying cellular networks with antenna array assisted artificial noise transmission[J]. IEEE Transactions on Vehicular Technology, 2020, 69(3): 2980–2992. doi: 10.1109/TVT.2020.2966538. [19] TAO Liwei, YANG Weiwei, YAN Shihao, et al. Covert communication in downlink NOMA systems with random transmit power[J]. IEEE Wireless Communications Letters, 2020, 9(11): 2000–2004. doi: 10.1109/LWC.2020.3011191. [20] TAO Liwei, YANG Weiwei, LU Xingbo, et al. Achieving covert communication in uplink NOMA systems via energy harvesting jammer[J]. IEEE Communications Letters, 2021, 25(12): 3785–3789. doi: 10.1109/LCOMM.2021.3114231. [21] LIU Yuanwei, LIU Xiao, MU Xidong, et al. Reconfigurable intelligent surfaces: Principles and opportunities[J]. IEEE Communications Surveys & Tutorials, 2021, 23(3): 1546–1577. doi: 10.1109/COMST.2021.3077737. [22] LU Xiao, HOSSAIN E, SHAFIQUE T, et al. Intelligent reflecting surface enabled covert communications in wireless networks[J]. IEEE Network, 2020, 34(5): 148–155. doi: 10.1109/MNET.011.1900579. [23] ZHOU Xiaobo, YAN Shihao, WU Qingqing, et al. Intelligent reflecting surface (IRS)-aided covert wireless communications with delay constraint[J]. IEEE Transactions on Wireless Communications, 2022, 21(1): 532–547. doi: 10.1109/TWC.2021.3098099. [24] SI Jiangbo, LI Zan, ZHAO Yan, et al. Covert transmission assisted by intelligent reflecting surface[J]. IEEE Transactions on Communications, 2021, 69(8): 5394–5408. doi: 10.1109/TCOMM.2021.3082779. [25] LV Lu, WU Qingqing, LI Zan, et al. Covert communication in intelligent reflecting surface-assisted NOMA systems: Design, analysis, and optimization[J]. IEEE Transactions on Wireless Communications, 2022, 21(3): 1735–1750. doi: 10.1109/TWC.2021.3106346. [26] MARDIA K V and JUPP P E. Directional Statistics[M]. Chichester: John Wiley & Sons, 2009: 15–18. [27] DING Zhiguo, SCHOBER R, and POOR H V. On the impact of phase shifting designs on IRS-NOMA[J]. IEEE Wireless Communications Letters, 2020, 9(10): 1596–1600. doi: 10.1109/LWC.2020.2991116. -





 下载:
下载:


 下载:
下载:
