A Review and Prospect of Cybersecurity Research on Air Traffic Management Systems
-
摘要: 空中交通管理系统是关乎空天安全和人民生命财产安全的国家大型关键信息基础设施。随着信息化、网络化和智能化技术的广泛应用,现代空中交通管理系统已经演化成为由多利益相关方异构融合的空天地海一体化网络。尽管系统的开放性和连接性提升了空中交通管理效率,但也引入了新的网络安全威胁,扩大了系统攻击面,使得网络安全生态复杂且形势严峻。该文以资产梳理、威胁分析、攻击建模、防御机制为主线,从不同的利益相关方(Stakeholders)出发,如电子使能飞机、空中交通管理(CNS/ATM)、智慧机场、智能决策等方面对空中交通管理系统的网络安全研究现状进行了全面系统的综述,并提出了动态网络安全分析、攻击影响传播建模、人在回路网络安全分析、分布式入侵检测系统等方面的研究问题与挑战。Abstract:
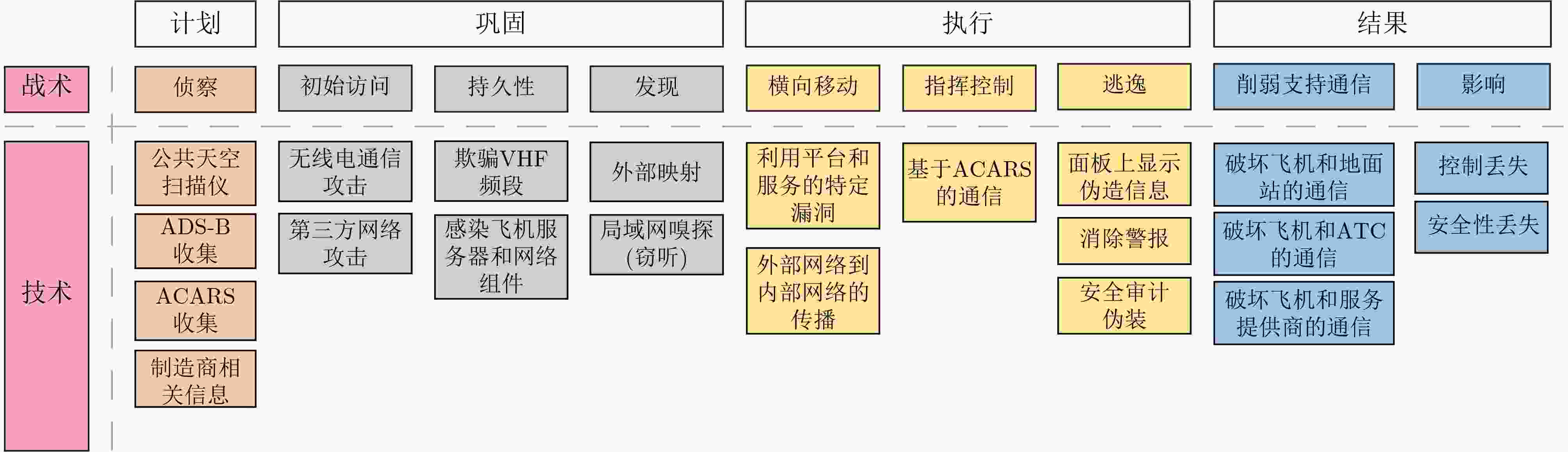
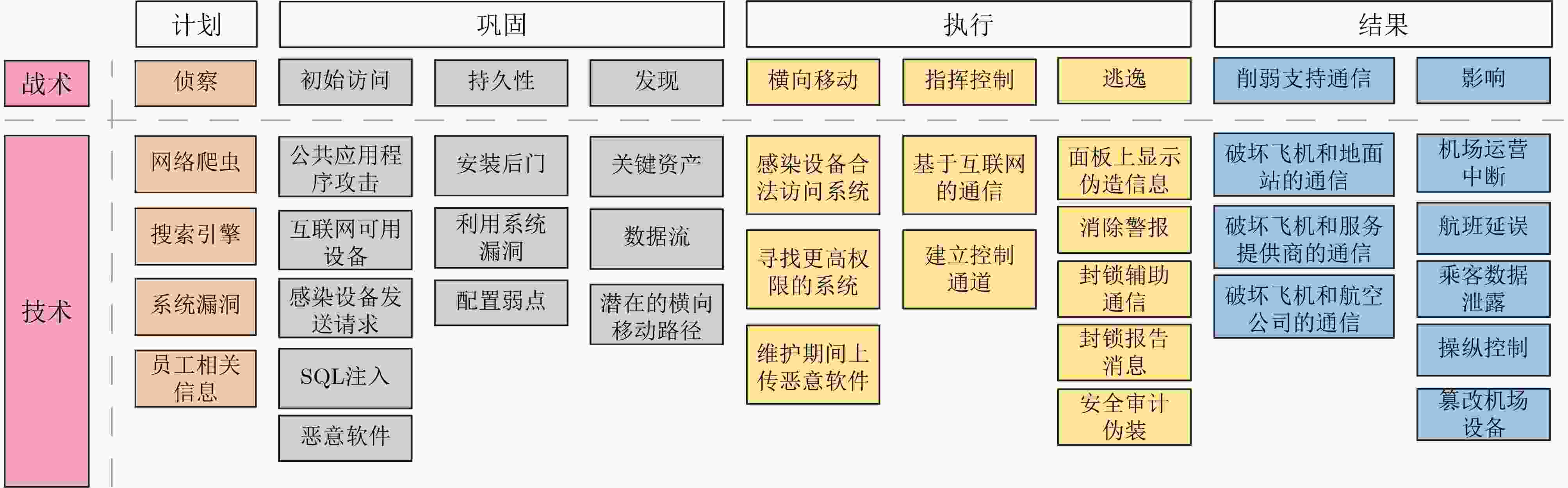
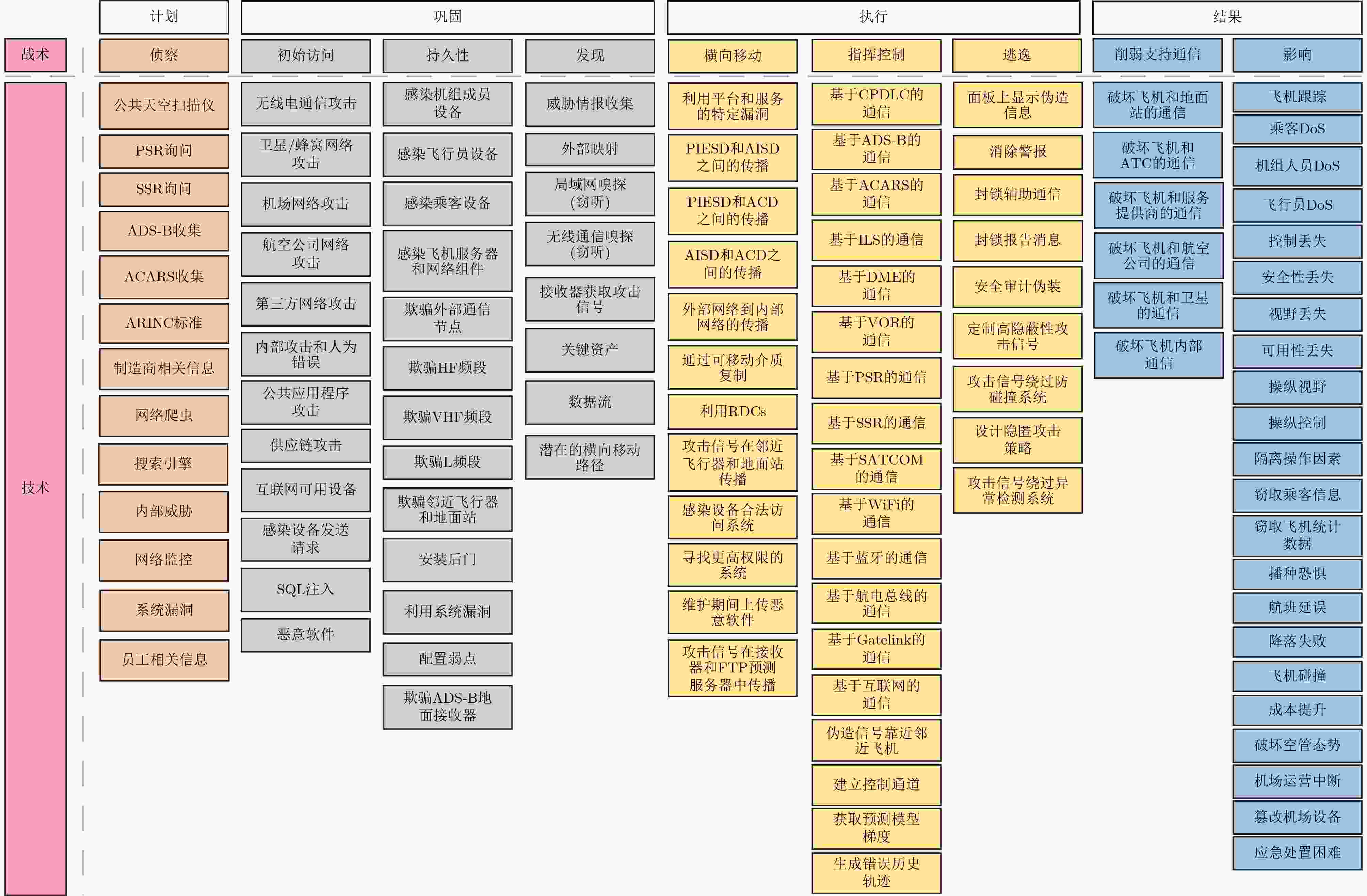
Significance The air traffic management system is a critical national infrastructure that impacts both aerospace security and the safety of lives and property. With the widespread adoption of information, networking, and intelligent technologies, the modern air traffic management system has evolved into a space-air-ground-sea integrated network, incorporating heterogeneous systems and multiple stakeholders. The network security of the system can no longer be effectively ensured by device redundancy, physical isolation, security by obscurity, or human-in-the-loop strategies. Due to the stringent requirements for aviation airworthiness certification, the implementation of new cybersecurity technologies is often delayed. New types of cyberattacks, such as advanced persistent threats and supply chain attacks, are increasingly prevalent. Vulnerabilities in both hardware and software, particularly in embedded systems and industrial control systems, are continually being exposed, widening the attack surface and increasing the number of potential attack vectors. Cyberattack incidents are frequent, and the network security situation remains critical. Progress The United States’ Next Generation Air Transportation System (NextGen), the European Commission’s Single European Sky Air Traffic Management Research (SESAR), and the Civil Aviation Administration of China have prioritized cybersecurity in their development plans for next-generation air transportation systems. Several countries and organizations, including the United States, Japan, China, the European Union, and Germany, have established frameworks for the information security of air traffic management systems. Although network and information security for air traffic management systems is gaining attention, many countries prioritize operational safety over cybersecurity concerns. Existing security specifications and industry standards are limited in addressing network and information security. Most of them focus on top-level design and strategic directions, with insufficient attention to fundamental theories, core technologies, and key methodologies. Current review literature lacks a comprehensive assessment of assets within air traffic management systems, often focusing only on specific components such as aircraft or airports. Furthermore, research on aviation information security mainly addresses traditional concerns, without fully considering the intelligent and dynamic security challenges facing next-generation air transportation systems. Conclusions This paper comprehensively examines the complexity of the cybersecurity ecosystem in air traffic management systems, considering various entities such as electronic-enabled aircraft, communication, navigation, Surveillance/Air Traffic Management (CNS/ATM), smart airports, and intelligent computing. It focuses on asset categorization, information flow, threat analysis, attack modeling, and defense mechanisms, integrating dynamic flight phases to systematically review the current state of cybersecurity in air traffic management systems. Several scientific issues are identified that must be addressed in constructing a secure ecological framework for air traffic management. Based on the Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) model, this paper analyzes typical attack examples related to the four ecological entities ( Figs. 7 ,9 ,12 , and14 ) and constructs an ATT&CK matrix for air traffic management systems (Fig. 15 ). Additionally, with the intelligent development goal of next-generation air transportation systems as a guide, ten typical applications of intelligent air traffic management are outlined (Fig. 13 ,Table 11 ), with a systematic analysis of the attack patterns and defense mechanisms of their intelligent algorithms (Tables 12 ,13 ). These findings provide theoretical references for the development of smart civil aviation and the assurance of cybersecurity in China.Prospects Currently, the cybersecurity ecosystem of air traffic management systems is highly complex, with unclear mechanisms, indistinct boundaries for cybersecurity assets, and incomplete security assurance requirements. Moreover, there is a lack of comprehensive, systematic, and holistic cybersecurity design and defense mechanisms, which limits the ability to counter various subjective, human-driven, and emerging types of malicious cyberattacks. This paper highlights key research challenges in areas such as dynamic cybersecurity analysis, attack impact propagation modeling, human-in-the-loop cybersecurity analysis, and distributed intrusion detection systems. Cybersecurity analysis of air traffic management systems should be conducted within the dynamic operational environment of a space-air-ground-sea integrated network, accounting for the cybersecurity ecosystem and analyzing it across different spatial and temporal dimensions. As aircraft are cyber-physical systems, cybersecurity threat analysis should focus on the interrelated propagation mechanisms between security and safety, as well as their cascading failure models. Furthermore, humans serve as the last line of defense in cybersecurity. When performing threat modeling and risk assessment for avionics systems, it is crucial to fully incorporate “human-in-the-loop” characteristics to derive comprehensive and objective conclusions. Finally, the design, testing, certification, and updating of civil aviation avionics systems are constrained by strict airworthiness requirements, preventing the rapid implementation of advanced cybersecurity technologies. Distributed anomaly detection systems, however, currently represent an effective technical approach for combating cyberattacks in air traffic management systems. -
Key words:
- Air traffic management system /
- Cyber security /
- Research review /
- Research challenges
-
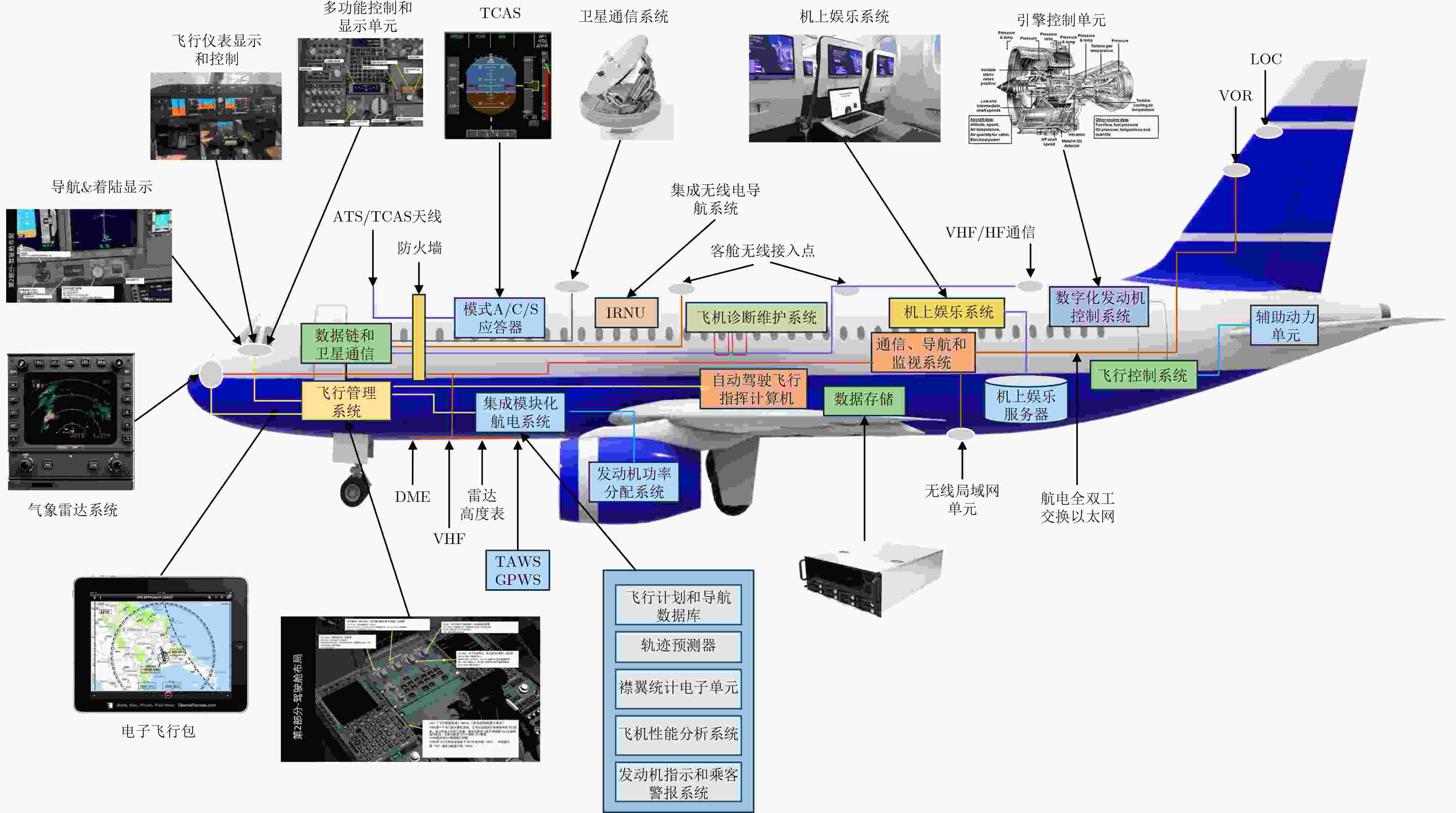
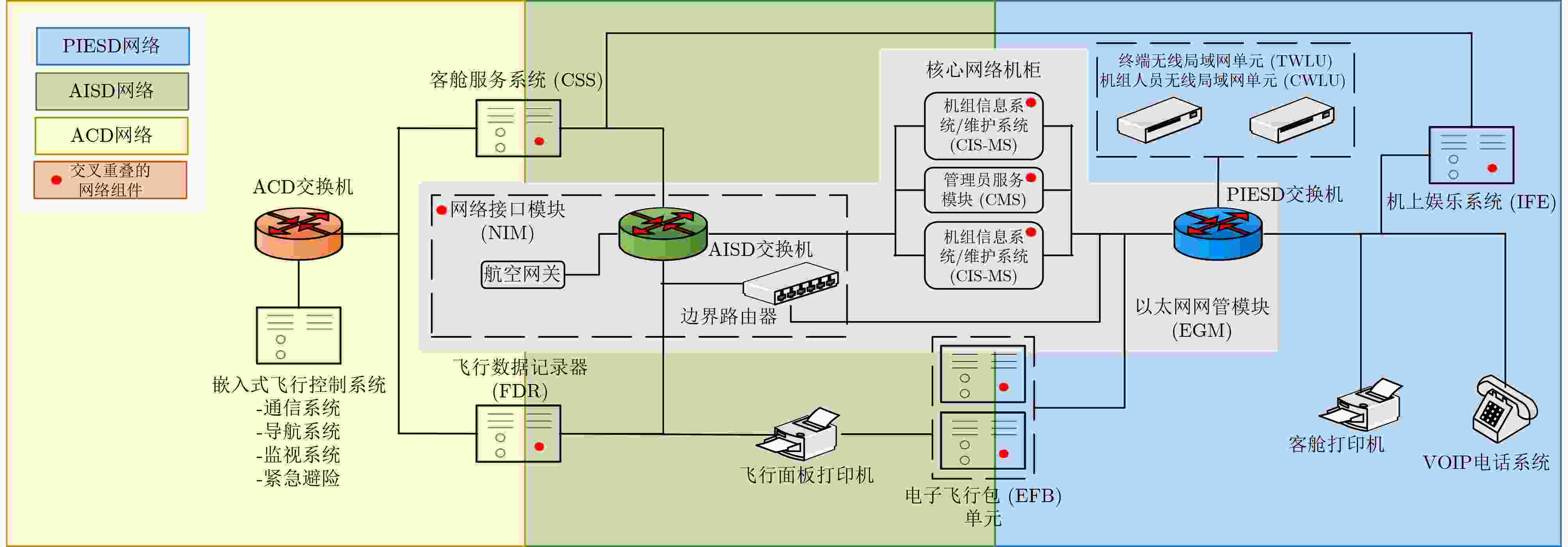
图 4 民机航电网络内部资产[31]
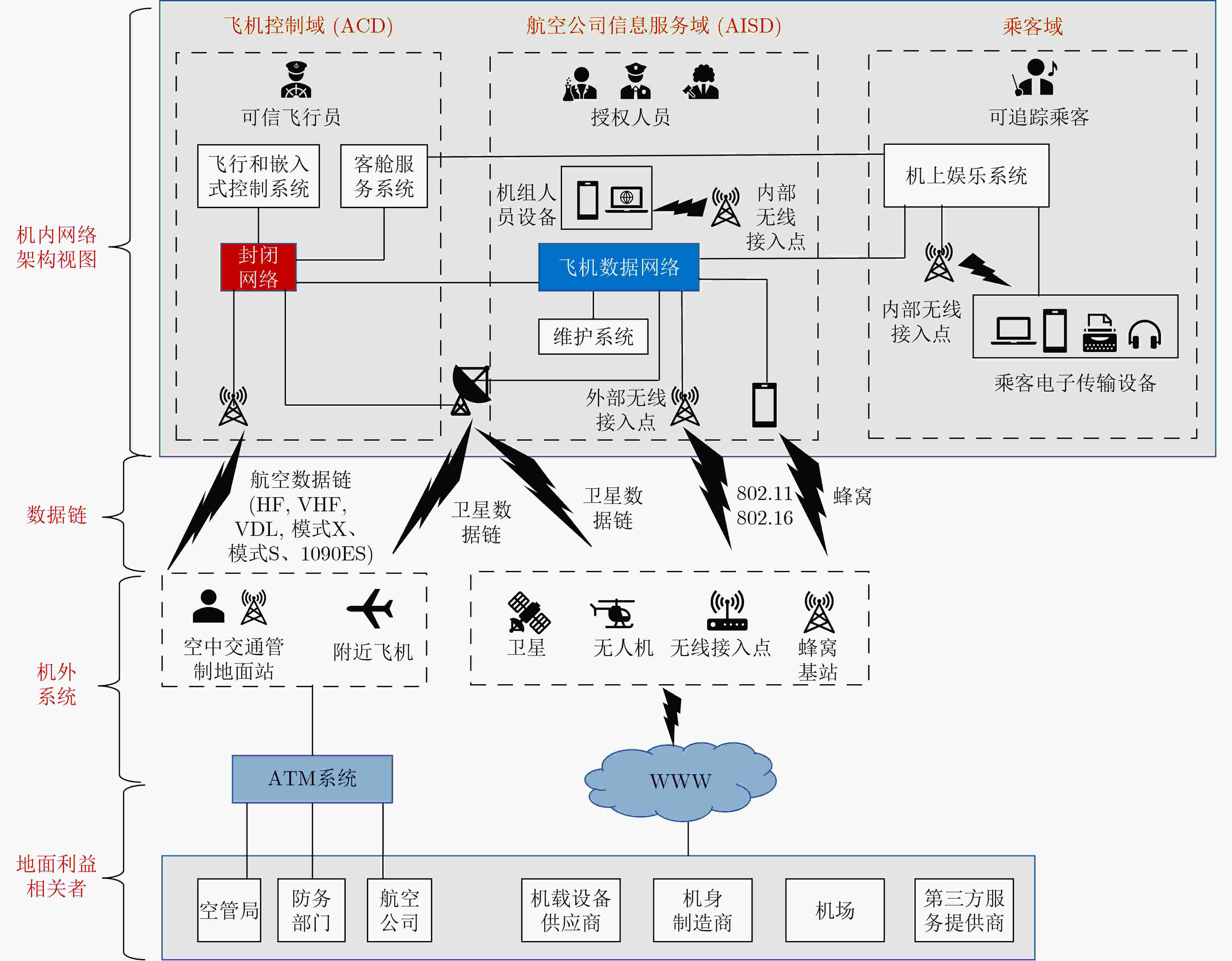
图 5 民机航电网络内部架构及外部连接关系[11]
图 6 民用飞机内部连接[27]
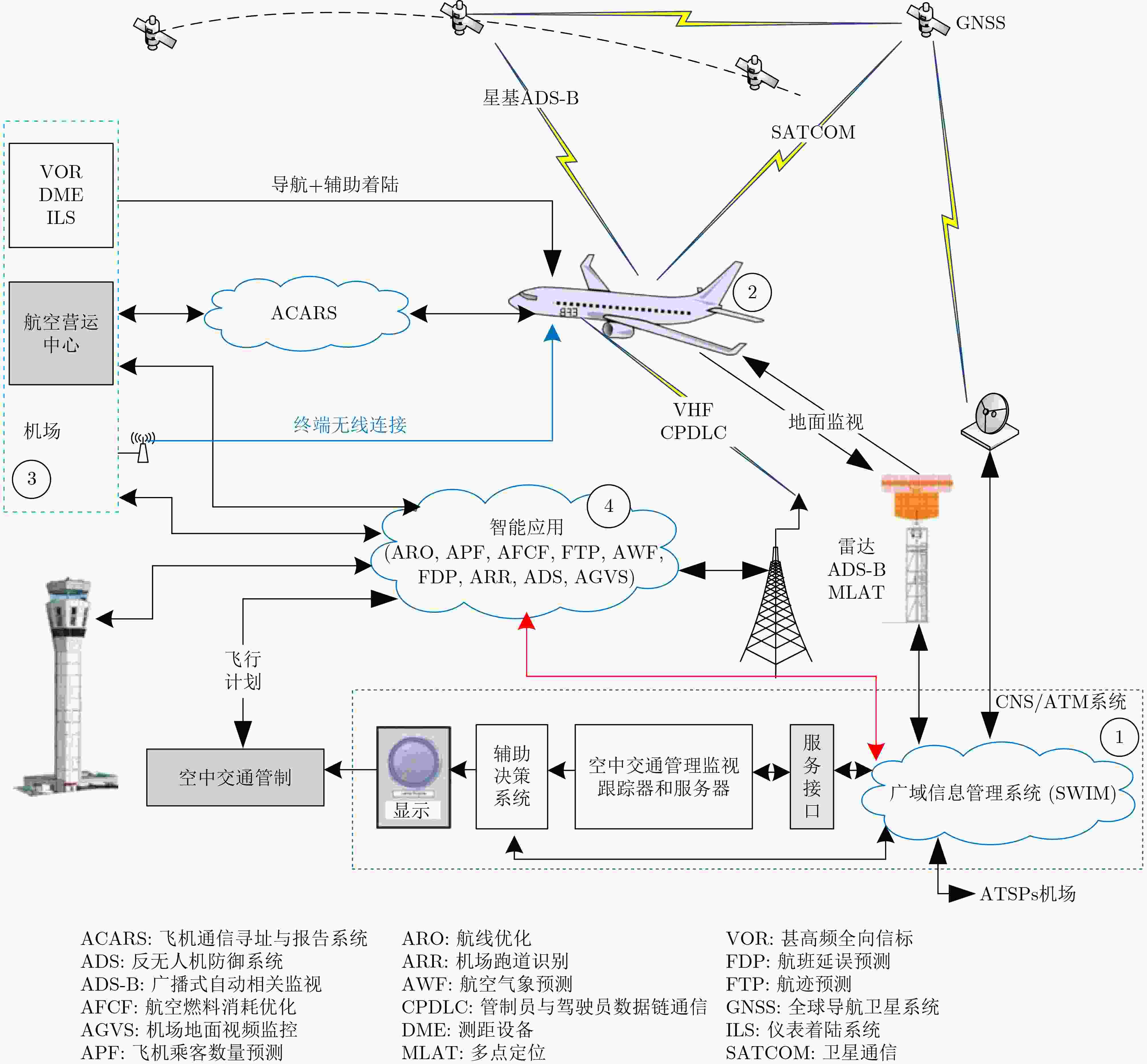
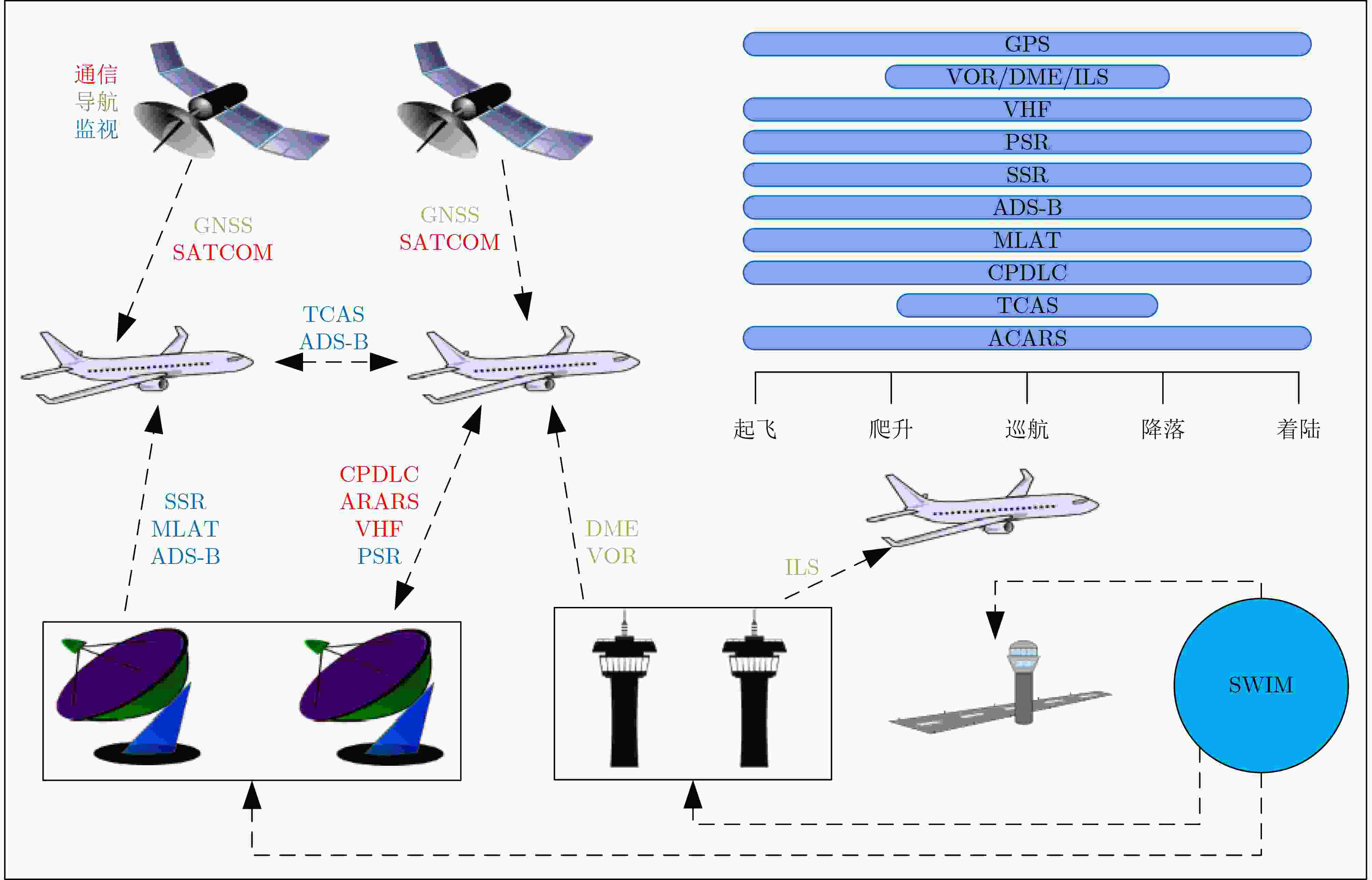
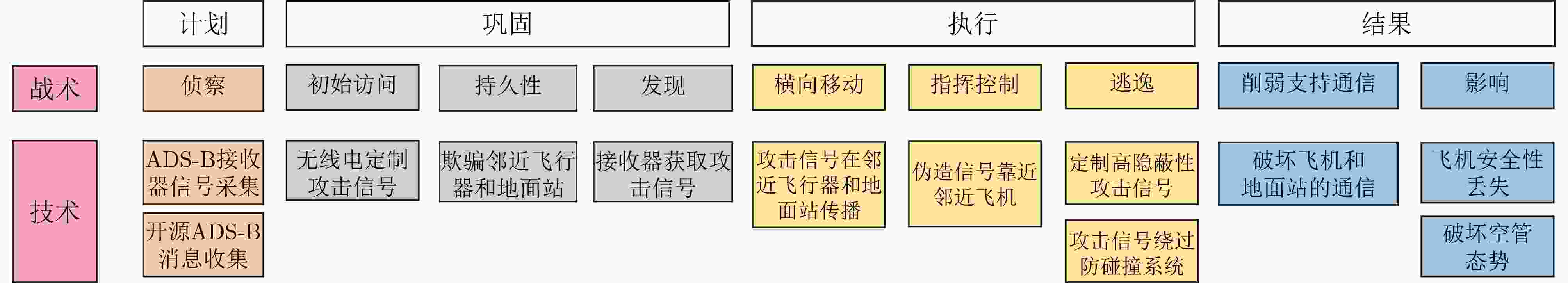
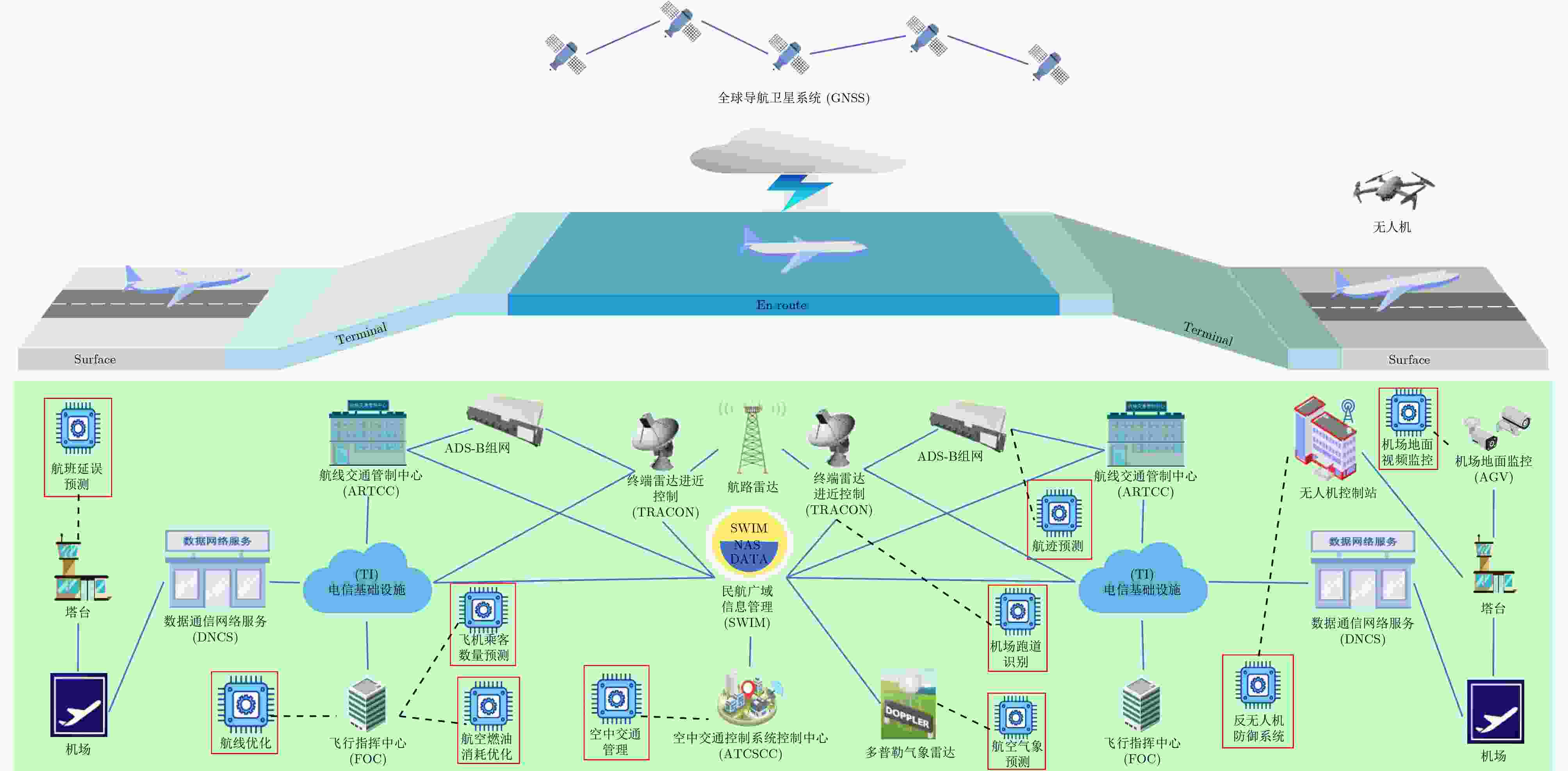
图 8 CNS/ATM空管系统信息流图[70]
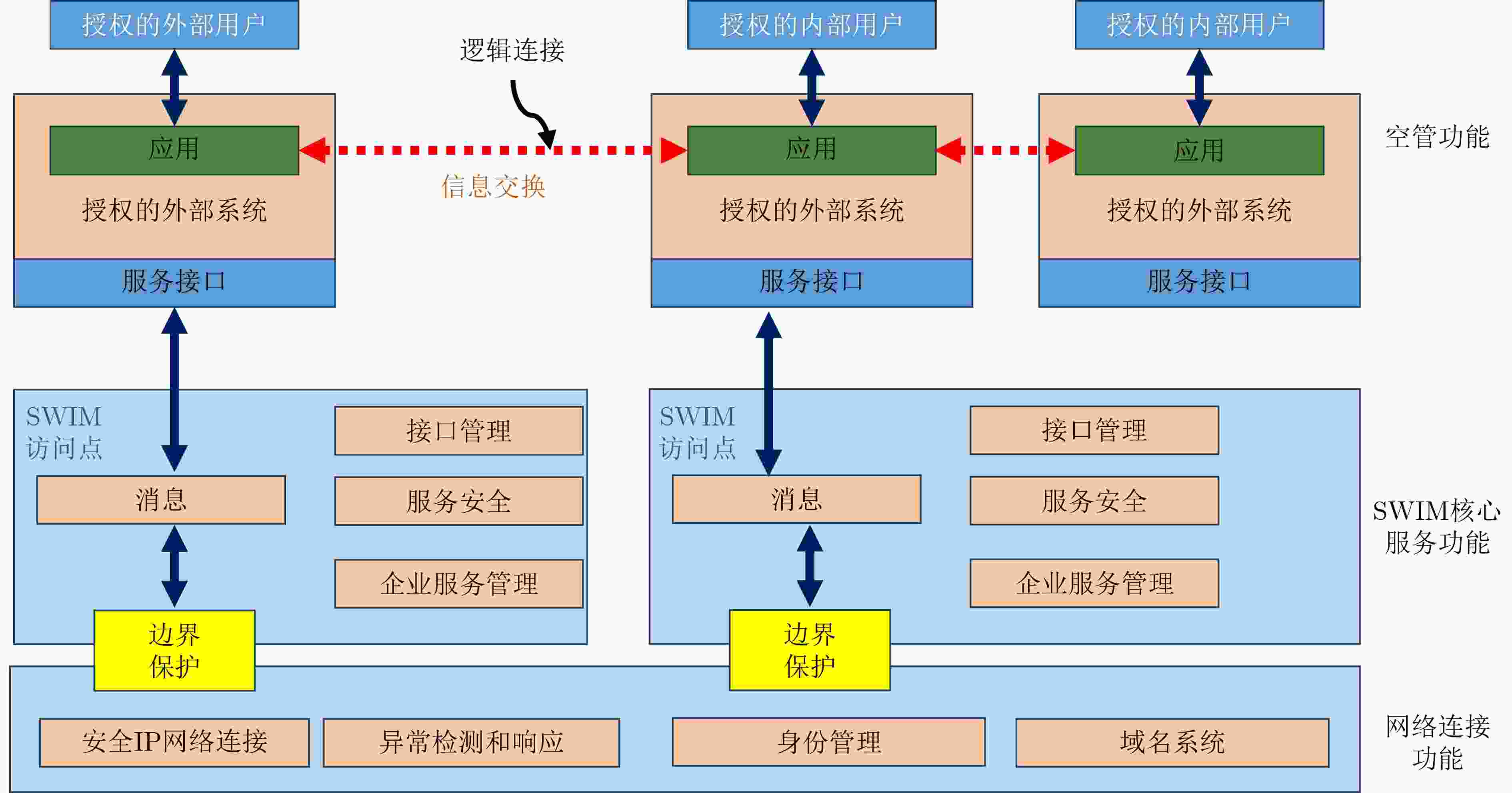
图 10 空管SWIM总体架构[12]
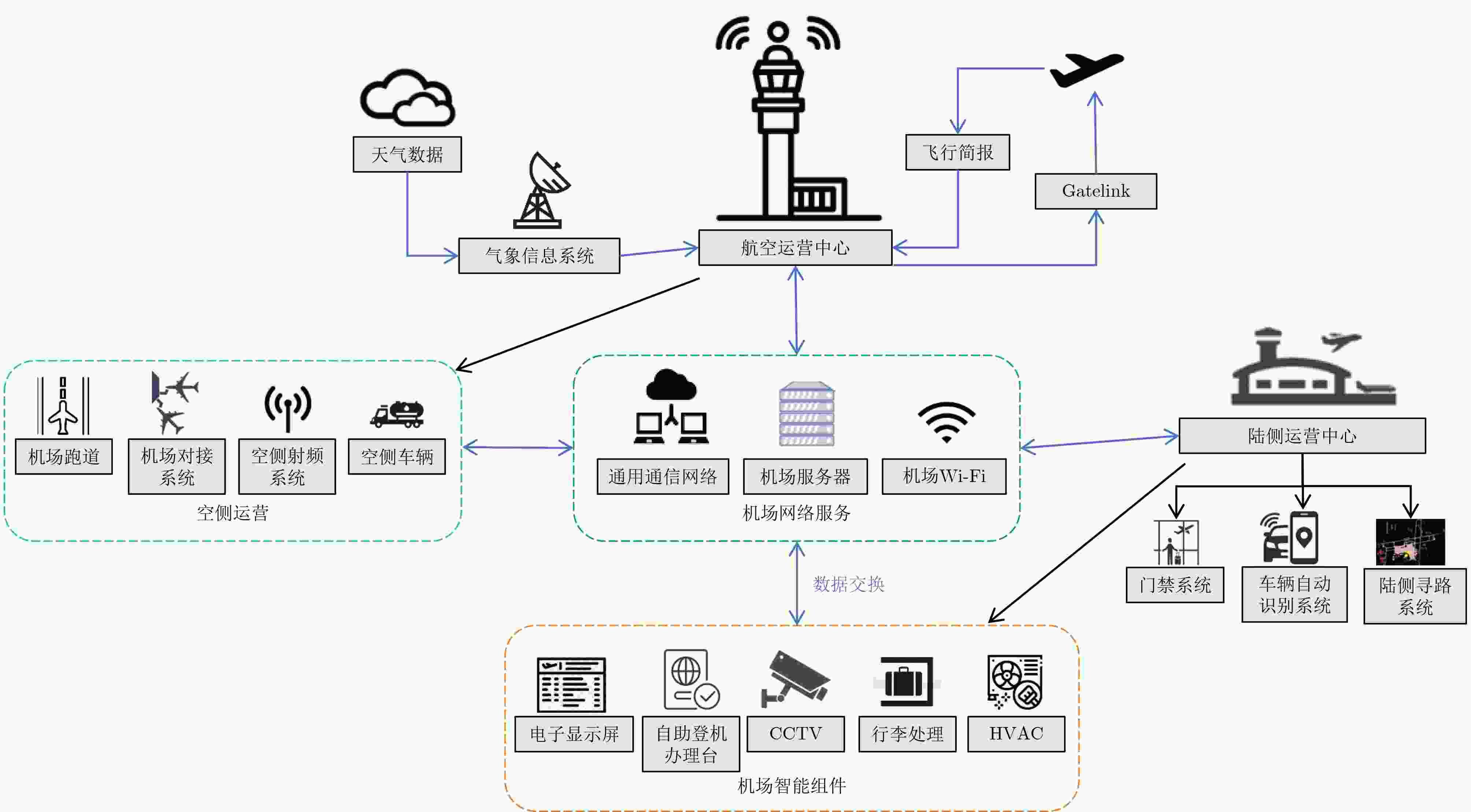
图 13 不同飞行阶段的智能化空管典型应用[149]
表 1 空中交通管理系统信息安全保障框架
国家/组织 制定时间 框架名称 美国 1999 Information Systems Security 日本 2010 Collaborative Actions for Renovation
of Air Traffic Systems中国 2012 民用航空网络与信息安全管理规范 欧盟 2013 Global ATM Security Management 德国 2015 Air Traffic Resilience 美国CSFI 2015 Air Traffic Control Cyber Security Project 表 2 现有综述文献总结
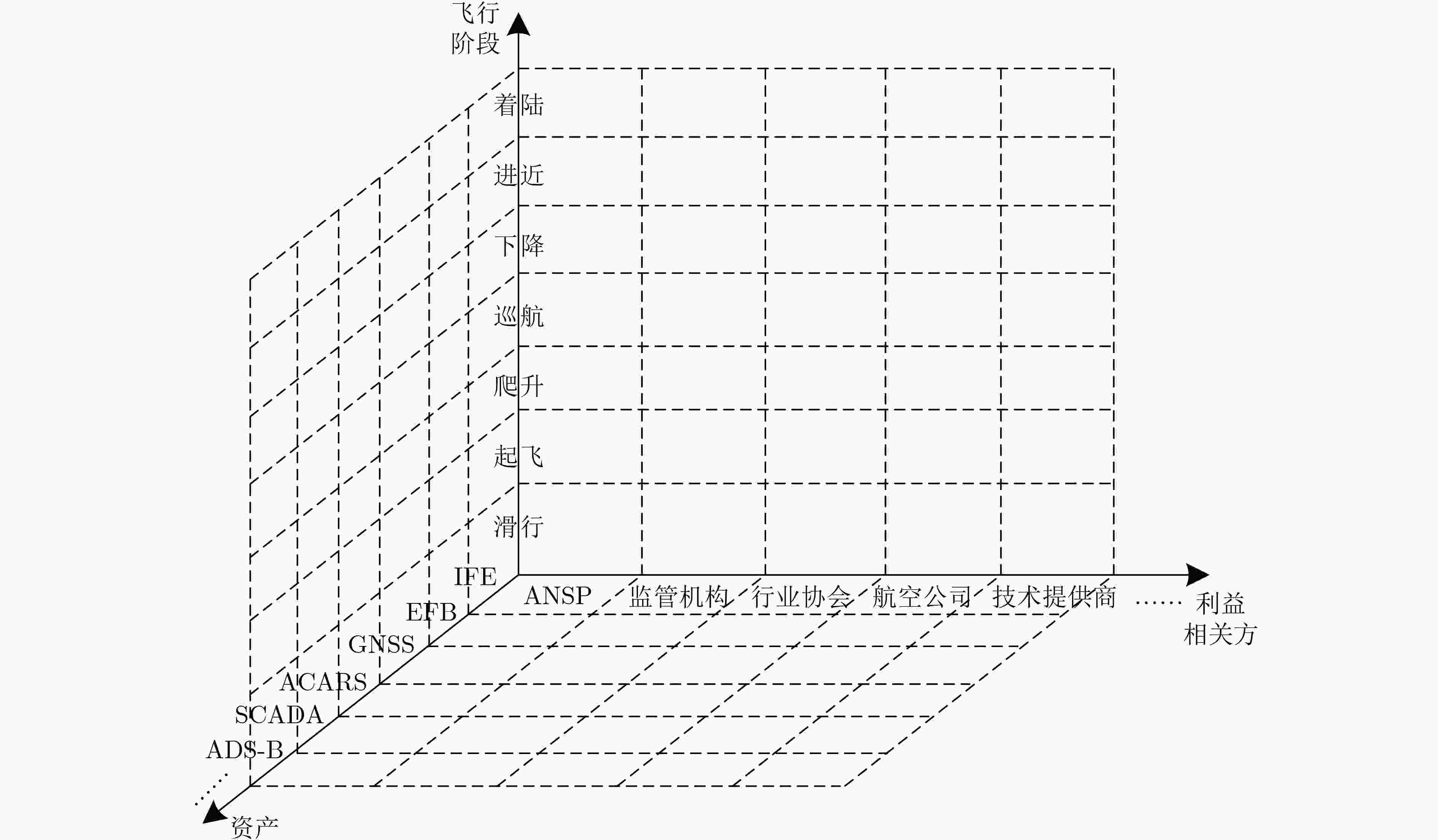
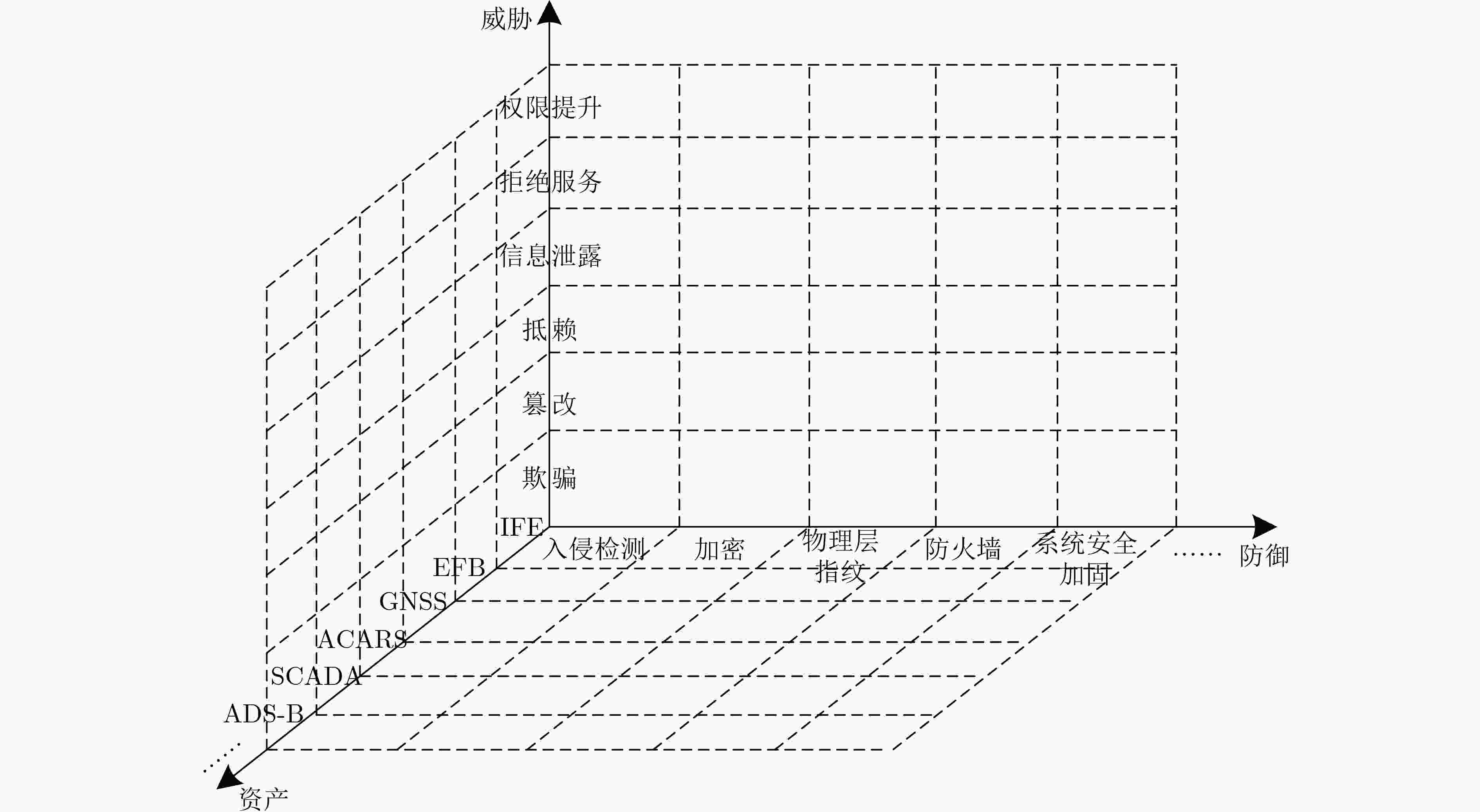
表 3 航电网络各管理域相关资产梳理
表 4 民用飞机面临的具体攻击样式及分类
资产 攻击技术 攻击影响 STRIDE 飞行管理系统[55–57] 向FMS注入虚假数据 操纵控制装置 篡改 用损坏的导航数据更新FMS 远程更新恶意的航空公司修改信息(AMI) 发动机警报系统[58] 注入恶意的发动机警报消息 安全性损失 欺骗 机上娱乐和通信系统[59] 获取乘客的显示系统的控制权 播种恐惧 篡改 获取客舱的控制权 权限提升 收集乘客的隐私信息 盗窃乘客信息 信息泄露 电子飞行包[60] 利用蓝牙、Wi-Fi或蜂窝网络获取EFB的控制权 失去控制 篡改 通过检索日志收集应用程序的存储信息 盗窃飞机统计数据 信息泄露 修改飞行计划和导航数据 操纵控制装置 篡改 安装恶意应用程序 篡改 滥用托管应用程序并修改操纵指令(例如控制客舱灯光) 播种恐惧 权限提升 资产名称 用途 发送方 接收方 通信系统 CPDLC 数字通信 飞机和地面站 飞机和地面站 SATCOM 卫星通信 卫星、飞机和地面站 飞机和地面站 ACARS 数字通信 飞机和地面站 飞机和地面站 导航系统 DME 测量距离 地面站 飞机 VOR 提供方位 地面站 飞机 ILS 着陆引导 地面站 飞机 GNSS 定位和导航 卫星和地面站 飞机 监视系统 PSR 提供位置、速度和航行等信息 地面站 飞机和地面站 SSR 提供识别码、高度、速度等信息 飞机 飞机和地面站 ADS-B 提供位置、速度和航行等信息,防碰撞 卫星和飞机 飞机和地面站 MLAT 提供位置信息 飞机 地面站 表 6 空管通信、导航、监视系统资产面临的安全威胁
资产 攻击技术 攻击影响 STRIDE CPDLC[86] 用无线电接收机接收、解析和收集信息;注入定制的
虚假消息;篡改飞机和空中交通服务机构
之间的通信;洪泛攻击窃取飞机相关信息;欺骗飞行员和管制员;飞行员无法获取
有效通信数据信息泄露;欺骗;篡改;拒绝服务 SATCOM[87] 破坏、拦截或修改机上Wi-Fi;破坏飞行和卫星的通信 乘客和机组人员无法获取服务 拒绝服务 ACARS[88] 飞机侦察;发布并传输虚假的信息 飞机航迹泄露;扰乱空管态势 信息泄露;欺骗 DME/VOR/ILS[89] 飞机侦察;使用定制信号压制合法信号 飞机航迹泄露;破坏飞行安全 信息泄露;欺骗 GNSS[90] 使用GPS信号欺骗GNSS系统;发送比卫星
GPS信号强的信号破坏飞行安全;扰乱空管态势 欺骗;篡改;拒绝服务 PSR/SSR[91] 攻击者使用软件无线电修改、阻碍、注入监视雷达消息 破坏空管态势 欺骗;篡改;拒绝服务 ADS-B[92] 飞机侦察;幽灵飞机注入;轨迹篡改;泛洪拒绝 飞机航迹泄露;扰乱空管态势;
扰乱空管态势信息泄露;欺骗;篡改;拒绝服务 MLAT[93] 阻碍GPS信号的信号同步;使用多个设备欺骗GPS信号 扰乱空管态势 欺骗 表 7 针对空管通信、导航、监视系统的安全防御手段
表 8 机场资产总结
名称 用途 机场管理 企业管理系统 用于机场的行政管理 资产盘点系统 跟踪和管理机场的物理资产 人力资源系统 管理机场员工的招聘、培训、调度和绩效评估 空侧运营 空中交通管理系统 指挥和监控飞机在空中的飞行路径 导航着陆设备 辅助飞机安全起降 飞行追踪系统 实时监控飞机位置 气象信息系统 提供实时气象数据 出发控制系统 管理飞机的起飞顺序和时间 航空运营中心 处理机场和航空公司的业务 货物处理系统 管理机场的货物装卸、存储和运输 通信导航监视系统 集成通信、导航和监视功能 机场运行数据库 存储和管理机场运营的关键数据 陆侧运营 机场陆侧运营系统控制中心 协调机场地面交通和运营活动 自动车辆识别系统 自动识别和监控机场内的车辆 燃料管理系统 管理机场的燃料供应和分配 交通运输系统 提供机场与城市之间的交通连接 寻路服务系统 帮助乘客在机场内导航 安全和安保 身份验证系统 验证乘客和员工的身份 行李处理系统 自动化处理乘客行李的检查、分拣和运输 智能监控系统 监控机场的关键区域 海关和移民 管理国际旅客的入境和出境检查 简易爆炸物探测系统 检测潜在的爆炸物威胁 门禁系统 控制对机场敏感区域的访问 周界入侵检测系统 监测机场周边 应急响应系统消防系统 在紧急情况下提供快速响应 IT和通信 内部 局域网和虚拟私人网络 为机场内部提供安全的网络连接 通信系统(如无线电频谱管理系统) 为机场提供通信服务 存储数据 保存机场运营中产生的数据 IT设备(软件和硬件) 支持机场的信息技术需求 飞行显示管理系统 向乘客提供航班信息 移动电话网络或APP 提供移动通信服务 外部 全球定位系统 提供精确的定位服务 网络安全管理 保护机场网络不受攻击 广域网 连接机场与外部网络 地理信息系统 用于机场的地理数据分析和地图服务 设施与维护 机场车辆维修 维护和修理机场车辆 能源管理(发电机) 管理机场的能源供应 数据采集与监视控制系统 监控和控制机场的关键基础设施 乘客系统 后勤系统 支持机场的后勤服务 电子显示屏 机场内显示信息 乘客办理登机和登机系统 自动化处理乘客的登机手续 乘客姓名登记系统 管理乘客信息 预约系统 管理航空公司的座位预订和航班安排 行李处理系统 自动化处理乘客行李的检查、分拣和运输 表 9 机场资产面临的安全威胁
资产 技术 攻击面 影响 STRIDE 机场管理 DDoS攻击 有线通信与IT资产的交互 机场服务器瘫痪 拒绝服务 滥用授权 物理与IT资产的交互 未授权人员访问敏感系统 权限提升 社交和网络钓鱼攻击 与员工或乘客的交互 诱导员工泄露敏感信息 信息泄露 空侧运营 通信攻击 无线通信与IT资产的交互 通信系统被监听或篡改 篡改 恶意软件 资产间的跳跃攻击 数据丢失或被远程控制 欺骗 滥用授权 物理与IT资产的交互 未授权人员访问敏感系统 权限提升 陆侧运营 网络攻击 有线通信与IT资产的交互 监控设施或注入受损数据 欺骗 篡改设备 有线通信与IT资产的交互 设备的功能和数据被修改 篡改 社交和网络钓鱼攻击 与员工或乘客的交互 诱导员工泄露敏感信息 信息泄露 安全和安保 恶意软件 资产间的跳跃攻击 数据丢失或被远程控制 欺骗 滥用授权 物理与IT资产的交互 未授权人员访问敏感系统 权限提升 IT和通信 DDoS攻击 有线通信与IT资产的交互 机场服务器瘫痪 拒绝服务 通信攻击 无线通信与IT资产的交互 通信系统被监听或篡改 篡改 恶意软件 资产间的跳跃攻击 数据丢失或被远程控制 篡改 网络攻击 有线通信与IT资产的交互 监控设施或注入受损数据 欺骗 社交和网络钓鱼攻击 与员工或乘客的交互 诱导员工泄露敏感信息 信息泄露 设施与维护 滥用授权 物理与IT资产的交互 未授权人员访问敏感系统 权限提升 网络攻击 有线通信与IT资产的交互 监控设施或注入受损数据 欺骗 社交和网络钓鱼攻击 与员工或乘客的交互 诱导员工泄露敏感信息 信息泄露 乘客系统 篡改设备 有线通信与IT资产的交互 设备的功能和数据被修改 篡改 恶意软件 资产间的跳跃攻击 数据丢失或被远程控制 欺骗 表 10 机场资产的安全防御手段
攻击 涉及资产 安全防御 DDoS攻击 企业管理系统 入侵检测/保护
系统安全强化[131,132]
防火墙、网络分段和纵深防御[133,134]
IT资产的灾难恢复计划[135]人力资源系统 IT设备(软件和硬件) 网络安全管理 广域网 移动电话网络或APP 网络安全管理 通信攻击 空中交通管理系统 入侵检测/保护
反欺骗控制[136,137]
强用户身份验证[138]
应用安全和安全设计[139,140]
数据加密[141,142]导航着陆设备 飞行追踪系统 气象信息系统 出发控制系统 通信导航监视系统 通信系统(如无线电频谱管理系统) 飞行显示管理系统 全球定位系统 地理信息系统 恶意软件 通信系统(如无线电频谱管理系统) 入侵检测/保护
反恶意软件
技术控制 BYOD
最小特权访问
管理[143]
软件和硬件更新[144]
防火墙、网络分段和纵深防御IT设备(软件和硬件) 飞行显示管理系统 全球定位系统 广域网 地理信息系统 乘客姓名登记系统 预约系统 篡改设备 自动车辆识别系统 限制外部设备的使用[145]
入侵检测/保护
数据加密
增强物理安全和监控系统[146]燃料管理系统 交通运输系统 寻路服务系统 后勤系统 电子显示屏 乘客办理登机和登机系统 乘客姓名登记系统 预约系统 行李处理系统 网络攻击 机场陆侧运营系统控制中心 防火墙、网络分段和纵深防御
入侵检测/保护
强用户身份验证
更改设备的默认管理员凭据
技术控制BYOD
数据加密自动车辆识别系统 交通运输系统 寻路服务系统 通信系统(如无线电频谱管理系统) IT设备(软件和硬件) 网络安全管理 广域网 社交和网
钓鱼攻击企业管理系统 入侵检测/保护
软件和硬件更新
防火墙、网络分段和纵深防御
反欺骗控制
强用户身份验证
应用程序安全和安全设计资产盘点系统 人力资源系统 IT设备(软件和硬件) 移动电话网络或APP 网络安全管理 广域网 数据采集与监视控制系统 滥用授权 企业管理系统 更改设备的默认凭据
技术控制BYOD
软件和硬件更新
最小特权和数据分类
数据加密
强用户身份验证
用户访问管理资产盘点系统 人力资源系统 空中交通管理系统 航空公司网关服务器系统 货物处理系统 机场运行数据库 身份验证系统 行李处理系统 智能监控系统 门禁系统 周界入侵检测系统 应急响应系统消防系统 机场车辆维修 能源管理(发电机) 数据采集与监视控制系统 表 11 空管典型应用
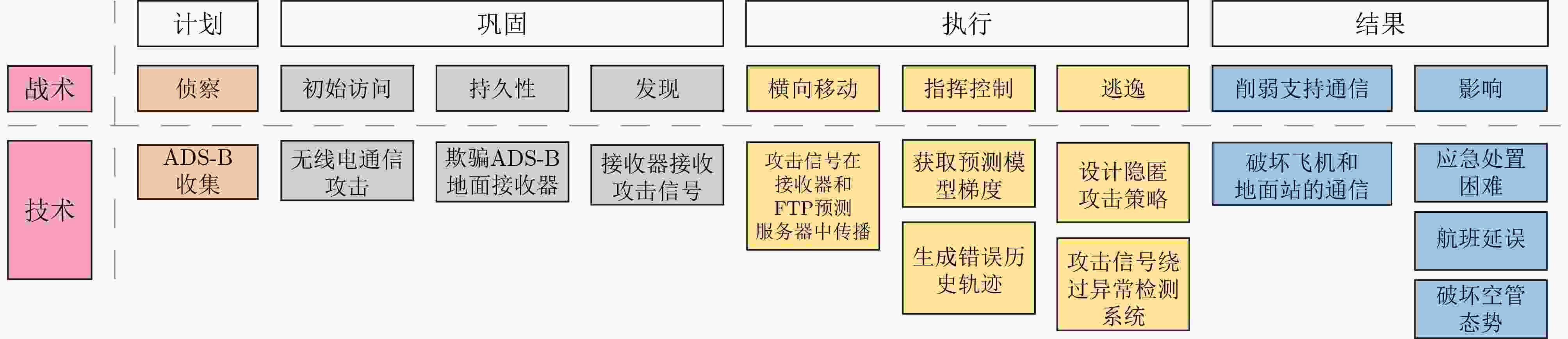
飞行阶段 典型应用 模型类别 模型优势 起飞前阶段 FDP[150–154] 图神经网络 基于图神经网络具有能够捕捉复杂关系、动态信息建模、上下文信息利用、提高泛化能力、
多模态融合、高效计算的优势。起飞前阶段 ARO[155] 强化学习 基于强化学习的动态决策、长远优化、自适应学习、资源优化、高维度和复杂的调度、
在线学习能力、低人工依赖优势。降落阶段 ARR[156–159] 目标检测算法 基于深度学习的跑道目标检测有检测实时性、适应复杂天气环境、人工干预降低、多源信息融合、
导航能力、运营效率优化、多机协同、数据收集与分析优势。降落阶段 ADS[160–162] 目标检测算法 基于目标检测算法的反无人机技术在机场安全中具有实时监控与响应、精准检测、多传感器融合、
自动化部署、提升事件响应效率、安全数据分析、协同作战、司法取证的优势。起飞前阶段 APF[163,164] 时序预测模型 时序预测模型在乘客数量预测中的应用,带来了历史数据利用、季节性波动感知、样本获取与自动更新、多变量出局处理、预测周期灵活性、决策效率、财务风险管理、成本效益、政策制定支持、
客户体验优化优势。飞行阶段 ATM[165–169] 强化学习 基于强化学习的空中交通管理具有自适应决策、优化调度、实时反馈、多目标优化、
解决高维问题、经验积累与迁移的优势。飞行阶段 AFCF[170–172] 时序预测模型 在航空燃油消耗预测中,时序预测模型具有动态数据处理、非线性关系获取、偶发事件处理、
油量节约、历史趋势分析、多模型集成能力优势。起飞前阶段 FTP[173–177] 时序预测模型 在航迹预测中,时序预测模型具有处理序列数据的能力、动态更新、非线性关系建模、自适应性、
多变量输入、并行处理与效率、强大的特征提取优势。飞行阶段 AWF[178–182] 时序预测模型 在航空气象预测中,时序预测模型具有动态特性捕捉、气象延续性与记忆能力、自动特征学习、实时天气预测、气象预警功能、交互式决策支持优势。 降落阶段 AGVS[183–186] 目标检测算法 在机场安全检测中,目标检测算法具有快速响应、高准确率、小目标检测能力、自动化监控、模型集成性强、复杂环境适应能力、可扩展性强、机场数据采集与分析、智能安全报警机制的优势。 表 12 攻击样式
攻击样式 模型类别 攻击优势 对抗样本攻击 图神经网络[187–189] (1)结构敏感性:GNN依赖于节点及其邻域之间的结构信息。对抗攻击可以通过小规模的边或节点操作来影响整个图的特征传播。(2)局部性与全局性的相互作用:GNN聚合邻居节点的信息,局部的扰动可能会引起全局的效果。(3)传播效应:图中某个节点的标签变化可以通过连接的边影响其他节点,导致连锁反应,从而提高攻击效果。 目标检测算法[190,191] (1)复杂性与高维特征:针对多维度特征,细微对抗扰动可以维持视觉效果的同时,降低模型的检测精度。(2)多阶梯输出:目标检测算法的决策过程涉及多步骤,每一阶段都可能受到对抗样本的影响。对抗攻击可针对特定阶段进行设计,从而提高攻击的成功率。(3)隐蔽性与实时性:对抗样本能够在视觉上保持自然状态,且易于实现针对现实世界中摄像头捕获的图像,这使得攻击具有较好的隐蔽性。 时序预测模型[192,193] (1)序列长度与复杂性:时序数据长且具有复杂的时序关系。扰动可能对后续多个时刻的预测造成影响,使得攻击在序列中传播。(2)环境噪声与变化的脆弱性:算法经常需要应对环境噪声和随机性,对抗攻击可以精确地伪造
这种噪声。强化学
习[194,195](1)环境动态性:强化学习通常在动态环境中进行决策。当攻击者在环境中施加对抗扰动时,这些扰动可以有效地影响智能体的观测状态和决策行为。(2)奖励信号:强化学习对抗样本可以通过改变环境状态,使得智能体接收到误导性的奖励信号。(3)多步决策链:强化学习攻击能在早期步骤干扰智能体的决策,将导致后续动作产生连锁反应,进一步降低整体任务表现。 模型窃取攻击 图神经网络[196–198] (1)信息聚合机制:这一机制意味着即便攻击者没有直接访问完整模型参数,也能通过观察输入-输出对推测出某些权重或结构特征,从而近似重建模型。(2)高维特征表达能力:GNN能够捕捉高维特征并能够灵活地处理不同大小和形状的图。(3)可互操作性与迁移:许多GNN模型是基于相似的原理和结构,攻击者可以从一个模型窃取知识,然后将其迁移到其他任务中。 后门攻击 图神经网络[199,200] (1)数据依赖性:GNN处理的输入数据通常包含节点及其连接关系,后门攻击可以通过注入特定的“干净”样本来劫持模型。(2)图拓扑结构利用:由于图拥有复杂的拓扑结构,攻击者可以设计特定的后门模式,使得在特定条件下影响某些节点或边的状态。 目标检测算法[201,202] (1)后门隐匿性:攻击者可以通过在训练集中注入带有隐藏标记的图像样本,而这些图像貌似正常,因此更容易掩盖后门的存在。(2)标签操控:攻击者可以通过操控图像及其对应的标签,设计特定的后门触发条件。(3)难以回溯性:由于目标检测涉及大量的特征计算和复杂的数据流,后门的源头可能难以追踪,增加了后门被识别的难度。 强化学习模型[203,204] (1)策略更新机制:攻击者可以设计一些特定的触发事件,引导代理在特定状态下意外地优化为不希望的策略,从而实现对模型的控制。(2)长期影响:由于RL侧重于长期奖励,攻击者可以精心选择后门样本,使得在触发后,代理会持续受到影响,从而实施潜在的危险行为。 表 13 智能化空管典型应用攻击样式的安全防御手段
攻击样式 安全防御 防御概述 对抗样本攻击 对抗训练 对抗训练在模型训练过程中,将对抗样本加入到训练集中。对于给定的训练样本,通过特定的攻击算法
生成对抗样本,然后将其作为训练数据来更新模型参数。使模型在训练时就会接触到对抗样本,
从而学习到对这些扰动更具鲁棒性的特征表示。输入预
处理(1)滤波技术去除对抗样本中的噪声扰动。它可以在一定程度上削弱添加的微小扰动,使对抗样本更接近原始样本,
减少扰动对模型决策的影响。(2)特征压缩减少输入数据的维度或复杂度,去除可能包含对抗扰动的冗余信息,
去除与对抗扰动相关的次要特征,提升模型鲁棒性。模型增强 (1)多模型融合是指将多个不同的模型进行融合,不同模型对对抗样本的脆弱性可能不同,通过融合可以综合
各个模型的优势,提高整体的鲁棒性。(2)防御蒸馏借鉴知识蒸馏的思想,在防御对抗样本时,教师模型在
对抗样本上的输出作为软标签,学生模型通过学习这些软标签来提高对对抗样本的鲁棒性。对抗样
本检测分析对抗样本和正常样本在统计特征上的差异,包括样本的激活值分布、梯度分布等统计量。
对抗样本的这些统计量往往与正常样本不同,设定阈值可以检测出对抗样本。模型窃取攻击 混淆技术 旨在通过对模型或模型输出进行各种变换,增加攻击者窃取模型知识的难度。 访问控制与加密 对模型的参数、结构以及可能传输的数据进行加密处理。 基于证明的防御 要求用户在获取模型的预测结果之前,完成一定的计算任务或提供某种形式的证明。 后门攻击 数据检测
与清洗(1)异常样本检测通过统计分析、聚类等方法识别训练数据中的异常样本。
(2)触发模式检测分析数据集中是否存在特定的触发模式。模型训练过程防御 在模型训练中使用 L1 和 L2 正则化等技术。减少后门攻击可利用的冗余参数,
约束参数大小防止模型过拟合后门样本。模型检测与加固 (1)对训练好的模型进行逆向分析,检查模型结构和参数中是否存在隐藏的后门。(2)在模型训练过程中
嵌入水印信息,通过检测水印的完整性来判断模型是否被篡改。运行时
监测(1)在模型运行时,实时监测输入数据,检查是否存在与已知后门触发条件匹配的输入。(2)输出监测观察模型结果,判断是否存在异常。(3)监控模型内部的行为,如神经元的激活状态、中间层输出等。 -
[1] ZHANG Jun. Aeronautical mobile communication: The evolution from narrowband to broadband[J]. Engineering, 2021, 7(4): 431–434. doi: 10.1016/j.eng.2021.02.002. [2] POST J. The next generation air transportation system of the united states: Vision, accomplishments, and future directions[J]. Engineering, 2021, 7(4): 427–430. doi: 10.1016/j.eng.2020.05.026. [3] BOLIĆ T and RAVENHILL P. SESAR: The past, present, and future of European air traffic management research[J]. Engineering, 2021, 7(4): 448–451. doi: 10.1016/j.eng.2020.08.023. [4] 中国民用航空局. 智慧民航建设路线图[R]. 2022.Civil Aviation Administration of China. Roadmap for building intelligent civil aviation[R]. 2022. [5] International Civil Aviation Organization. Global air traffic management operational concept[R]. Doc 9854, 2005. [6] 马兰, 孟诗君, 吴志军. 基于BERT与生成对抗的民航陆空通话意图挖掘[J]. 系统工程与电子技术, 2024, 46(2): 740–750. doi: 10.12305/j.issn.1001-506X.2024.02.38.MA Lan, MENG Shijun, and WU Zhijun. Intention mining for civil aviation radiotelephony communication based on BERT and generative adversarial[J]. Systems Engineering and Electronics, 2024, 46(2): 740–750. doi: 10.12305/j.issn.1001-506X.2024.02.38. [7] WU Zhijun, LIANG Cheng, and ZHANG Yuan. Blockchain-based authentication of GNSS civil navigation message[J]. IEEE Transactions on Aerospace and Electronic Systems, 2023, 59(4): 4380–4392. doi: 10.1109/TAES.2023.3241041. [8] KHAN H A, KHAN H, GHAFOOR S, et al. A survey on security of Automatic Dependent Surveillance -Broadcast (ADS-B) protocol: Challenges, potential solutions and future directions[J]. IEEE Communications Surveys & Tutorials, 2024. [9] NÖHREN L, SCHAPER M, and TYBURZY L. Towards full ATC automation for aircraft ground movement: A first step[C]. 2024 AIAA DATC/IEEE 43rd Digital Avionics Systems Conference (DASC), San Diego, USA, 2024: 1–9. doi: 10.1109/DASC62030.2024.10749019. [10] ENAYATOLLAHI F, ATASHGAH M A A, MALAEK S M B, et al. PBN-based time-optimal terminal air traffic control using cellular automata[J]. IEEE Transactions on Aerospace and Electronic Systems, 2021, 57(3): 1513–1523. doi: 10.1109/TAES.2020.3048787. [11] SAMPIGETHAYA K. Aircraft cyber security risk assessment: Bringing air traffic control and cyber-physical security to the forefront[C]. The AIAA Scitech 2019 Forum, San Diego, USA, 2019: 1–17. doi: 10.2514/6.2019-0061. [12] BOGODA L, MO J, and BIL C. A systems engineering approach to appraise cybersecurity risks of CNS/ATM and avionics systems[C]. 2019 Integrated Communications, Navigation and Surveillance Conference (ICNS), Herndon, USA, 2019: 1–15. doi: 10.1109/ICNSURV.2019.8735376. [13] MEHAN D J. Information systems security: The federal aviation administration’s layered approach[R]. 2000. [14] KIESLING T and KREUZER M. Recommendations to strengthen the cyber resilience of the air traffic system[EB/OL]. http://lb-campus.de/images/content/ARIEL_Recommendations_v2.0.pdf, 2017. [15] CSFI. CSFI ATC (Air Traffic Control) cyber security project[EB/OL]. https://csfi.us/pubdocs/?id=47, 2015. [16] European Commission. Global ATM security management project[EB/OL]. https://www.gamma-project.eu/, 2024. [17] Collaborative Actions for Renovation of Air Traffic Systems. Long-term vision for the future air traffic systems ~ changes to intelligent air traffic systems ~[EB/OL]. https://www.mlit.go.jp/koku/carats/rdk40188/wp-content/uploads/2020/06/LongTermVisionForTheFutureAirTrafficSystemsCARATS.pdf, 2010. [18] 中国民用航空局. MH/T 0035-2012 民用航空网络与信息安全管理规范[S]. 北京: 中国民用航空局, 2012.Civil Aviation Administration of China. MH/T 0035-2012 Specification for civil aviation network and information security management[S]. Beijing: Civil Aviation Administration of China, 2012. [19] 中国民用航空局. MH/T 0067-2018 民航Web应用系统安全检查指南[S]. 北京: 中国民用航空局, 2018.Civil Aviation Administration of China. MH/T 0067-2018 Security testing guide for Web application system of civil aviation[S]. Beijing: Civil Aviation Administration of China, 2018. [20] 中国民用航空局. MH/T 0068-2018 民用航空移动应用程序安全测评指南[S]. 北京: 中国民用航空局, 2018.Civil Aviation Administration of China. MH/T 0068-2018 Security testing guide for mobile application program of civil aviation[S]. Beijing: Civil Aviation Administration of China, 2018. [21] 中国民用航空局. MH/T 0069-2018 民用航空网络安全等级保护定级指南[S]. 北京: 中国民用航空局, 2018.Civil Aviation Administration of China. MH/T 0069-2018 Guidelines for grading of classified cyber security protection in civil aviation[S]. Beijing: Civil Aviation Administration of China, 2018. [22] 中国民用航空局. MH/T 0076-2020 民用航空网络安全等级保护基本要求[S]. 北京: 中国民用航空局, 2020.Civil Aviation Administration of China. MH/T 0076-2020 Baseline for classified protection of cybersecurity in civil aviation[S]. Beijing: Civil Aviation Administration of China, 2020. [23] PIK E. Airport security: The impact of AI on safety, efficiency, and the passenger experience[J]. Journal of Transportation Security, 2024, 17: 9. doi: 10.1007/S12198-024-00276-6. [24] LYKOU G, ANAGNOSTOPOULOU A, and GRITZALIS D. Smart airport cybersecurity: Threat mitigation and cyber resilience controls[J]. Sensors, 2019, 19(1): 19. doi: 10.3390/s19010019. [25] LYKOU G, ANAGNOSTOPOULOU A, and GRITZALIS D. Implementing cyber-security measures in airports to improve cyber-resilience[C]. 2018 Global Internet of Things Summit (GIoTS), Bilbao, Spain, 2018: 1–6. doi: 10.1109/GIOTS.2018.8534523. [26] KORONIOTIS N, MOUSTAFA N, SCHILIRO F, et al. A holistic review of cybersecurity and reliability perspectives in smart airports[J]. IEEE Access, 2020, 8: 209802–209834. doi: 10.1109/ACCESS.2020.3036728. [27] HABLER E, BITTON R, and SHABTAI A. Assessing aircraft security: A comprehensive survey and methodology for evaluation[J]. ACM Computing Surveys, 2024, 56(4): 96. doi: 10.1145/3610772. [28] FAKEEH K A. An analysis of airports cyber-security[J]. Communications on Applied Electronics, 2016, 4(7): 11–15. doi: 10.5120/cae2016652129. [29] European Union Agency for Network and Information Security. Securing smart airports[R]. 2016. [30] DAVE G, CHOUDHARY G, SIHAG V, et al. Cyber security challenges in aviation communication, navigation, and surveillance[J]. Computers & Security, 2022, 112: 102516. doi: 10.1016/j.cose.2021.102516. [31] VILLEGAS J, FORTES S, ESCAÑO V, et al. Verification and validation framework for AFDX avionics networks[J]. IEEE Access, 2022, 10: 66743–66756. doi: 10.1109/ACCESS.2022.3184329. [32] 张双, 孔德岐, 王元勋, 等. 基于虚拟化航电平台的网络域间安全通信技术[J]. 西北工业大学学报, 2022, 40(3): 530–537. doi: 10.1051/jnwpu/20224030530.ZHANG Shuang, KONG Deqi, WANG Yuanxun, et al. Secure communication technology between network domains based on virtualization avionics platform[J]. Journal of Northwestern Polytechnical University, 2022, 40(3): 530–537. doi: 10.1051/jnwpu/20224030530. [33] HINTZE H, GIERTZSCH F, and GOD R. Design approach for secure networks to introduce data analytics within the aircraft cabin[J]. SAE International Journal of Advances and Current Practices in Mobility, 2019, 2(2): 737–746. doi: 10.4271/2019-01-1853. [34] 郭鹏军, 张泾周, 杨远帆, 等. 飞机机内无线通信网络架构与接入控制算法研究[J]. 计算机科学, 2022, 49(9): 268–274. doi: 10.11896/jsjkx.210700220.GUO Pengjun, ZHANG Jingzhou, YANG Yuanfan, et al. Study on wireless communication network architecture and access control algorithm in aircraft[J]. Computer Science, 2022, 49(9): 268–274. doi: 10.11896/jsjkx.210700220. [35] WERTHWEIN M, BRUNNER M, and ANNIGHOEFER B. A concept enabling cybersecurity for a self-adaptive avionics platform with respect to RTCA DO-326 and RTCA DO-356[C]. 2023 IEEE/AIAA 42nd Digital Avionics Systems Conference (DASC), Barcelona, Spain, 2023: 1–10. doi: 10.1109/DASC58513.2023.10311289. [36] SHAIKH F, RAHOUTI M, GHANI N, et al. A review of recent advances and security challenges in emerging E-enabled aircraft systems[J]. IEEE Access, 2019, 7: 63164–63180. doi: 10.1109/ACCESS.2019.2916617. [37] WU Zhijun, YOU Zhenghang, and WANG Peng. Attribute encryption based access control methods under airborne networks[C]. 2022 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), Melbourne, Australia, 2022: 302–306. doi: 10.1109/ISPA-BDCloud-SocialCom-SustainCom57177.2022.00045. [38] PREDESCU A V and STELKENS-KOBSCH T H. Aviation Security Lab: A testbed for security testing of current and future aviation technologies[C]. 2022 IEEE/AIAA 41st Digital Avionics Systems Conference (DASC), Portsmouth, USA, 2022: 1–5. doi: 10.1109/DASC55683.2022.9925750. [39] ŠEGVIĆ M, NIKOLIĆ K K, and IVANJKO E. A proposal for a Fully Distributed Flight Control System design[C]. 2016 39th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 2016: 1099–1103. doi: 10.1109/MIPRO.2016.7522304. [40] WIELAND F and KILBOURNE T. A digital twin of a flight management system: Findings from the cloud FMS project[C]. The AIAA SCITECH 2024 Forum, Orlando, USA, 2024: 0278. doi: 10.2514/6.2024-0278. [41] HUANG Chenyu and CHENG Xiaoyue. Estimation of aircraft fuel consumption by modeling flight data from avionics systems[J]. Journal of Air Transport Management, 2022, 99: 102181. doi: 10.1016/j.jairtraman.2022.102181. [42] ZARIKOFF B, MARTIN D, and INSLEY M. Lightweight, low-cost and flexible flight data monitoring[C]. 2014 IEEE AUTOTEST, St. Louis, USA, 2014: 251–259. doi: 10.1109/AUTEST.2014.6935154. [43] TANGTHONG N and AKTIMAGOOL S. Management of laboratory-based learning activity on electronic flight instrument system[C]. 2021 6th International STEM Education Conference (iSTEM-Ed), Pattaya, Thailand, 2021: 1–4. doi: 10.1109/iSTEM-Ed52129.2021.9625098. [44] KHAN G A I and MAJID I. Modeling and simulation of interference between aircraft radar altimeter and 5G-C band transmissions along with implementation of proposed solution[C]. The International Conference on Aeronautical Sciences, Engineering and Technology, Muscat, Oman, 2024: 176–185. doi: 10.1007/978-981-99-7775-8_18. [45] CARROLL M, REBENSKY S, WILT D, et al. Integrating uncertified information from the electronic flight bag into the aircraft panel: Impacts on pilot response[J]. International Journal of Human-Computer Interaction, 2021, 37(7): 630–641. doi: 10.1080/10447318.2020.1854001. [46] TURTIAINEN H, COSTIN A, KHANDKER S, et al. GDL90fuzz: Fuzzing-GDL-90 data interface specification within aviation software and avionics devices–a cybersecurity pentesting perspective[J]. IEEE Access, 2022, 10: 21554–21562. doi: 10.1109/ACCESS.2022.3150840. [47] MANIKATH E, LI W C, and PIOTROWSKI P. Usability assessment on existing alerting designs for emergency communication between passengers and cabin crews[C]. The German Aerospace Conference (Deutscher Luft- und Raumfahrtkongress) 2023, Stuttgart, Germany, 2024: 610019. doi: 10.25967/610019. [48] METWALLY E A and MOHAMMED H T. Hacking an aircraft: Hacking the in-flight entertainment system[J]. Advances in Networks, 2022, 10(1): 7–14. doi: 10.11648/j.net.20221001.12. [49] AYUB S, PETRUNIN I, TSOURDOS A, et al. In-flight entertainment datalink analysis and simulation[C]. 2020 AIAA/IEEE 39th Digital Avionics Systems Conference (DASC), San Antonio, USA, 2020: 1–10. doi: 10.1109/DASC50938.2020.9256432. [50] 苟江, 梁卫星, 田伟, 等. 民机后舱一体化网络架构QoS算法设计[J]. 计算机与网络, 2024, 50(2): 156–162. doi: 10.20149/j.cnki.issn1008-1739.2024.02.011.GOU Jiang, LIANG Weixing, TIAN Wei, et al. Design of QoS algorithm for civil aircraft rear cabin integrated network architecture[J]. Computer & Network, 2024, 50(2): 156–162. doi: 10.20149/j.cnki.issn1008-1739.2024.02.011. [51] ZHOU Xuan, HE Feng, ZHAO Luxi, et al. Hybrid scheduling of tasks and messages for TSN-based avionics systems[J]. IEEE Transactions on Industrial Informatics, 2024, 20(2): 1081–1092. doi: 10.1109/TII.2023.3254608. [52] 赵长啸, 汪克念, 张伟, 等. 民机航电系统功能-信息安全一体化分析方法[J]. 中国安全科学学报, 2022, 32(9): 49–56. doi: 10.16265/j.cnki.issn1003-3033.2022.09.2126.ZHAO Changxiao, WANG Kenian, ZHANG Wei, et al. Integrated analysis method of functional safety and cyber security of avionics system for civil aircraft[J]. China Safety Science Journal, 2022, 32(9): 49–56. doi: 10.16265/j.cnki.issn1003-3033.2022.09.2126. [53] SIDDIQUI F, AHLBRECHT A, KHAN R, et al. Cybersecurity engineering: Bridging the security gaps in avionics architectures and DO-326A/ED-202A[C]. 2023 IEEE/AIAA 42nd Digital Avionics Systems Conference (DASC), Barcelona, Spain, 2023: 1–8. doi: 10.1109/DASC58513.2023.10311187. [54] RAMANATT P R, NATARAJAN K, and SHOBHA K R. Challenges in implementing a wireless avionics network[J]. Aircraft Engineering and Aerospace Technology, 2020, 92(3): 482–494. doi: 10.1108/AEAT-07-2019-0144. [55] KULESHOV Y A, NAGPAL K, UCPINAR K, et al. Cyber attacks on avionics networks in digital twin environment: Detection and defense[C]. The AIAA SCITECH 2024 Forum, Orlando, USA, 2024: 0277. doi: 10.2514/6.2024-0277. [56] WU Zhijun, ZHANG Yun, YANG Yiming, et al. Spoofing and anti-spoofing technologies of global navigation satellite system: A survey[J]. IEEE Access, 2020, 8: 165444–165496. doi: 10.1109/ACCESS.2020.3022294. [57] VILLAGE A. DEF CON 28 aerospace village: Attacking flight management systems[J]. Retrieved Feb, 2020, 12: 2022. [58] SHATILIN I. Hacking an aircraft: Is it already real?[R]. 2015. [59] ISHTIAQ S and ABD RAHMAN N A. Cybersecurity vulnerabilities and defence techniques in aviation industry[C/OL]. The 3rd International Conference on Integrated Intelligent Computing Communication & Security (ICIIC 2021), 2021: 559–567. [60] DORIGATTI D, STROHMEIER M, and NEUHAUS S. Air-bus hijacking: Silently taking over avionics systems[C]. The 10th ACM Cyber-Physical System Security Workshop, Singapore, 2024: 53–63. doi: 10.1145/3626205.3659144. [61] AL-SHAER R, SPRING J M, and CHRISTOU E. Learning the associations of MITRE ATT & CK adversarial techniques[C]. 2020 IEEE Conference on Communications and Network Security (CNS), Avignon, France, 2020: 1–9. doi: 10.1109/CNS48642.2020.9162207. [62] HILLEBRECHT A, MARKS T, and GOLLNICK V. An aeronautical data communication demand model for the North Atlantic oceanic airspace[J]. CEAS Aeronautical Journal, 2023, 14(2): 553–567. doi: 10.1007/s13272-023-00651-4. [63] BARON C and LOUIS V. Towards a continuous certification of safety-critical avionics software[J]. Computers in Industry, 2021, 125: 103382. doi: 10.1016/j.compind.2020.103382. [64] KAMBOJ P, KHARE S, and PAL S. User authentication using Blockchain based smart contract in role-based access control[J]. Peer-to-Peer Networking and Applications, 2021, 14(5): 2961–2976. doi: 10.1007/s12083-021-01150-1. [65] KO Y, KIM J, DUGUMA D G, et al. Drone secure communication protocol for future sensitive applications in military zone[J]. Sensors, 2021, 21(6): 2057. doi: 10.3390/s21062057. [66] JANGJOU M and SOHRABI M K. A comprehensive survey on security challenges in different network layers in cloud computing[J]. Archives of Computational Methods in Engineering, 2022, 29(6): 3587–3608. doi: 10.1007/s11831-022-09708-9. [67] ASANTE M, EPIPHANIOU G, MAPLE C, et al. Distributed ledger technologies in supply chain security management: A comprehensive survey[J]. IEEE Transactions on Engineering Management, 2023, 70(2): 713–739. doi: 10.1109/TEM.2021.3053655. [68] CASADO E, RODRIGUEZ R M, TABOSO P, et al. Information security in future air traffic management systems[J]. Journal of Aerospace Information Systems, 2016, 13(3): 101–112. doi: 10.2514/1.I010233. [69] PRANDINI M, PIRODDI L, PUECHMOREL S, et al. Toward air traffic complexity assessment in new generation air traffic management systems[J]. IEEE Transactions on Intelligent Transportation Systems, 2011, 12(3): 809–818. doi: 10.1109/TITS.2011.2113175. [70] STROHMEIER M, SCHAFER M, PINHEIRO R, et al. On perception and reality in wireless air traffic communication security[J]. IEEE Transactions on Intelligent Transportation Systems, 2017, 18(6): 1338–1357. doi: 10.1109/TITS.2016.2612584. [71] 杨乐. 民航空管信息系统网络安全态势感知与分析[J]. 管理科学与工程, 2022, 11(4): 665–671. doi: 10.12677/MSE.2022.114079.YANG Le. Network security situation awareness and analysis of civil aviation management information system[J]. Management Science and Engineering, 2022, 11(4): 665–671. doi: 10.12677/MSE.2022.114079. [72] CHEN Shichuan, ZHENG Shilian, YANG Lifeng, et al. Deep learning for large-scale real-world ACARS and ADS-B radio signal classification[J]. IEEE Access, 2019, 7: 89256–89264. doi: 10.1109/ACCESS.2019.2925569. [73] GULTEPE G, KANAR T, ZIHIR S, et al. A 1024-element Ku-band SATCOM dual-polarized receiver with >10-dB/K G/T and embedded transmit rejection filter[J]. IEEE Transactions on Microwave Theory and Techniques, 2021, 69(7): 3484–3495. doi: 10.1109/TMTT.2021.3073321. [74] JIANG Wei, LIU Dan, CAI Baigen, et al. A fault-tolerant tightly coupled GNSS/INS/OVS integration vehicle navigation system based on an FDP algorithm[J]. IEEE Transactions on Vehicular Technology, 2019, 68(7): 6365–6378. doi: 10.1109/TVT.2019.2916852. [75] 李腾耀, 王布宏, 尚福特, 等. ADS-B 攻击数据弹性恢复方法[J]. 电子与信息学报, 2020, 42(10): 2365–2373. doi: 10.11999/JEIT191020.LI Tengyao, WANG Buhong, SHANG Fute, et al. A resilient recovery method on ADS-B attack data[J]. Journal of Electronics & Information Technology, 2020, 42(10): 2365–2373. doi: 10.11999/JEIT191020. [76] 罗鹏, 王布宏, 李腾耀. 基于BiGRU-SVDD的ADS-B异常数据检测模型[J]. 航空学报, 2020, 41(10): 323878. doi: 10.7527/S1000-6893.2020.23878.LUO Peng, WANG Buhong, and LI Tengyao. ADS-B anomaly data detection model based on BiGRU-SVDD[J]. Acta Aeronautica et Astronautica Sinica, 2020, 41(10): 323878. doi: 10.7527/S1000-6893.2020.23878. [77] 董襄宁, 赵征, 张洪海. 空中交通管理基础[M]. 北京: 科学出版社, 2011: 1–3.DONG Xiangning, ZHAO Zheng, and ZHANG Honghai. Fundamentals of Air Traffic Management[M]. Beijing: Science Press, 2011: 1–3. [78] WILLIAMSON T and SPENCER N A. Development and operation of the Traffic Alert and Collision Avoidance System (TCAS)[J]. Proceedings of the IEEE, 1989, 77(11): 1735–1744. doi: 10.1109/5.47735. [79] 王布宏, 罗鹏, 李腾耀, 等. 基于粒子群优化多核支持向量数据描述的广播式自动相关监视异常数据检测模型[J]. 电子与信息学报, 2020, 42(11): 2727–2734. doi: 10.11999/JEIT190767.WANG Buhong, LUO Peng, LI Tengyao, et al. ADS-B anomalous data detection model based on PSO-MKSVDD[J]. Journal of Electronics & Information Technology, 2020, 42(11): 2727–2734. doi: 10.11999/JEIT190767. [80] SHANG Fute, WANG Buhong, YAN Fuhu, et al. Multidevice false data injection attack models of ADS-B multilateration systems[J]. Security and Communication Networks, 2019, 2019(1): 8936784. doi: 10.1155/2019/8936784. [81] LI Tengyao, WANG Buhong, SHANG Fute, et al. Threat model and construction strategy on ADS-B attack data[J]. IET Information Security, 2020, 14(5): 542–552. doi: 10.1049/iet-ifs.2018.5635. [82] SHANG Fute, WANG Buhong, LI Tengyao, et al. Adversarial examples on deep-learning based ADS-B spoofing detection[J]. IEEE Wireless Communications Letters, 2020, 9(10): 1734–1737. doi: 10.1109/LWC.2020.3002914. [83] LI Tengyao, WANG Buhong, SHANG Fute, et al. Dynamic temporal ADS-B data attack detection based on sHDP-HMM[J]. Computers & Security, 2020, 93: 101789. doi: 10.1016/j.cose.2020.101789. [84] LI Tengyao, WANG Buhong, SHANG Fute, et al. Online sequential attack detection for ADS-B data based on hierarchical temporal memory[J]. Computers & Security, 2019, 87: 101599. doi: 10.1016/j.cose.2019.101599. [85] LI Tengyao and WANG Buhong. Sequential collaborative detection strategy on ADS-B data attack[J]. International Journal of Critical Infrastructure Protection, 2019, 24: 78–99. doi: 10.1016/j.ijcip.2018.11.003. [86] ESKILSSON S, GUSTAFSSON H, KHAN S, et al. Demonstrating ADS-B AND CPDLC attacks with software-defined radio[C]. 2020 Integrated Communications Navigation and Surveillance Conference (ICNS), Herndon, USA, 2020: 1B2-1–1B2-9. doi: 10.1109/ICNS50378.2020.9222945. [87] NGUYEN L K, NGUYEN D H N, TRAN N H, et al. SATCOM jamming resiliency under non-uniform probability of attacks[C]. The MILCOM 2021 - 2021 IEEE Military Communications Conference (MILCOM), San Diego, USA, 2021: 85–90. doi: 10.1109/MILCOM52596.2021.9652944. [88] LI Xinwei, ZHANG Qianyun, XU Lexi, et al. A compatible and identity privacy-preserving security protocol for ACARS[C]. 2022 IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Wuhan, China, 2022: 1048–1053. doi: 10.1109/TrustCom56396.2022.00143. [89] CHOUDHARY G, SIHAG V, GUPTA S, et al. Aviation attacks based on ILS and VOR vulnerabilities[J]. Journal of Surveillance, Security and Safety, 2022, 3: 27–40. doi: 10.20517/jsss.2021.17. [90] YANG Zhen, YING Jun, SHEN Junjie, et al. Anomaly detection against GPS spoofing attacks on connected and autonomous vehicles using learning from demonstration[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(9): 9462–9475. doi: 10.1109/TITS.2023.3269029. [91] OBOD I, SVYD I, ZAVOLODKO G, et al. Assessing SSR relative data capacity[C]. 2021 IEEE 3rd Ukraine Conference on Electrical and Computer Engineering (UKRCON), Lviv, Ukraine, 2021: 142–146. doi: 10.1109/UKRCON53503.2021.9575971. [92] ZHANG Qianyun, WANG Zhendong, WU Biyi, et al. A Robust and Practical Solution to ADS-B security against denial-of-service attacks[J]. IEEE Internet of Things Journal, 2024, 11(8): 13647–13659. doi: 10.1109/JIOT.2023.3337543. [93] MONTEIRO M. Detecting malicious ADS-B broadcasts using wide area multilateration[C]. 2015 IEEE/AIAA 34th Digital Avionics Systems Conference (DASC), Prague, Czech Republic, 2015: 1–28. doi: 10.1109/DASC.2015.7311579. [94] LUO Peng, WANG Buhong, LI Tengyao, et al. ADS-B anomaly data detection model based on VAE-SVDD[J]. Computers & Security, 2021, 104: 102213. doi: 10.1016/j.cose.2021.102213. [95] LUO Peng, WANG Buhong, and TIAN Jiwei. TTSAD: TCN-Transformer-SVDD Model for Anomaly Detection in air traffic ADS-B data[J]. Computers & Security, 2024, 141: 103840. doi: 10.1016/j.cose.2024.103840. [96] LUO Peng, WANG Buhong, TIAN Jiwei, et al. ADS-Bpois: Poisoning attacks against deep-learning-based air traffic ADS-B unsupervised anomaly detection models[J]. IEEE Internet of Things Journal, 2024, 11(23): 38301–38311. doi: 10.1109/JIOT.2024.3446675. [97] LUO Peng, WANG Buhong, TIAN Jiwei, et al. Adversarial attacks against deep-learning-based automatic dependent surveillance-broadcast unsupervised anomaly detection models in the context of air traffic management[J]. Sensors, 2024, 24(11): 3584. doi: 10.3390/s24113584. [98] MCPARLAND T, PATEL V, and HUGHES W J. Securing air-ground communications[C]. The 20th Digital Avionics Systems Conference, Daytona Beach, USA, 2001: 7A7/1–7A7/9. doi: 10.1109/DASC.2001.964187. [99] SCHRAML M G and KNOPP A. Physical layer security with unknown eavesdroppers in beyond-5G MU-MIMO SATCOM[C]. Proceedings of 2020 IEEE 3rd 5G World Forum (5GWF), Bangalore, India, 2020: 180–185. doi: 10.1109/5GWF49715.2020.9221107. [100] YUE Meng and WU Xiaofeng. The approach of ACARS data encryption and authentication[C]. 2010 International Conference on Computational Intelligence and Security, Nanning, China, 2010: 556–560. doi: 10.1109/CIS.2010.127. [101] ADAMY D. EW 102: A Second Course in Electronic Warfare[M]. Norwood, USA: Artech House, 2003. [102] BLANCH J, WALTER T, and ENGE P. Satellite navigation for aviation in 2025[J]. Proceedings of the IEEE, 2012, 100(Special Centennial Issue): 1821–1830. doi: 10.1109/JPROC.2012.2190154. [103] STROHMEIER M, LENDERS V, and MARTINOVIC I. Intrusion detection for airborne communication using PHY-layer information[C]. The 12th International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Milan, Italy, 2015: 67–77. doi: 10.1007/978-3-319-20550-2_4. [104] CHIANG J T, HAAS J J, CHOI J, et al. Secure location verification using simultaneous multilateration[J]. IEEE Transactions on Wireless Communications, 2012, 11(2): 584–591. doi: 10.1109/TWC.2011.120911.101147. [105] MUNIR A, AVED A, and BLASCH E. Situational awareness: Techniques, challenges, and prospects[J]. AI, 2022, 3(1): 55–77. doi: 10.3390/ai3010005. [106] WU Zhijun, XU Pei, and FAN Haoyu. Network security situation assessment method based eigenvector centrality[C]. 2024 International Wireless Communications and Mobile Computing (IWCMC), Ayia Napa, Cyprus, 2024: 103–108. doi: 10.1109/IWCMC61514.2024.10592357. [107] WU Zhijun and FAN Haoyu. Aviation network security situation awareness based on game theory[C]. 2023 IEEE Aerospace Conference, Big Sky, USA, 2023: 1–8. doi: 10.1109/AERO55745.2023.10115582. [108] WU Zhijun, BAI Zhuoning, ZHANG Lizhe, et al. Feature extraction method based on sparse autoencoder for air traffic management system security situation awareness[J]. Security and Communication Networks, 2022, 2022(1): 3757662. doi: 10.1155/2022/3757662. [109] MA Lan, MA Shaopu, and WU Zhijun. WNN-based prediction of security situation awareness for the civil aviation network[J]. Journal of Intelligent Systems, 2014, 24(1): 55–67. doi: 10.1515/jisys-2014-0004. [110] SMITH M, MOSER D, STROHMEIER M, et al. Undermining privacy in the Aircraft Communications Addressing and Reporting System (ACARS)[J]. Proceedings on Privacy Enhancing Technologies, 2018, 2018(3): 105–122. doi: 10.1515/popets-2018-0023. [111] UKWANDU E, BEN-FARAH M, HINDY H, et al. Cyber-security challenges in aviation industry: A review of current and future trends[J]. Information, 2022, 13(3): 146. doi: 10.3390/info13030146. [112] 吴志军. 广域信息管理SWIM信息安全关键技术[M]. 北京: 人民邮电出版社, 2020: 13–19.WU Zhijun. Key Technologies of Information Assurance for System Wide Information Management (SWIM)[M]. Beijing: Posts & Telecommunications Press, 2020: 13–19. [113] 李晛. 基于物联网技术的智慧机场设计与应用探讨[J]. 工程管理, 2024, 5(7): 14–15. doi: 10.12238/jpm.v5i7.6950.LI Xian. Discussion on the smart airport design and application based on the Internet of Things technology[J]. Journal of Project Management, 2024, 5(7): 14–15. doi: 10.12238/jpm.v5i7.6950. [114] 顾兆军, 张一诺, 宋跃东, 等. 智慧机场物联网应用及网络安全挑战[J]. 指挥信息系统与技术, 2023, 14(5): 14–20. doi: 10.15908/j.cnki.cist.2023.05.003.GU Zhaojun, ZHANG Yinuo, SONG Yuedong, et al. IoT applications and cyber security challenges in smart airports[J]. Command Information System and Technology, 2023, 14(5): 14–20. doi: 10.15908/j.cnki.cist.2023.05.003. [115] MAJID S A, NUGRAHA A, SULISTIYONO B S, et al. The effect of safety risk management and airport personnel competency on aviation safety performance[J]. Uncertain Supply Chain Management, 2022, 10(4): 1509–1522. doi: 10.5267/j.uscm.2022.6.004. [116] XIONG Wenjun and LAGERSTRÖM R. Threat modeling–a systematic literature review[J]. Computers & Security, 2019, 84: 53–69. doi: 10.1016/j.cose.2019.03.010. [117] 邢馨心, 左青雅, 刘建伟. 基于5G的智慧机场网络安全方案设计与安全性分析[J]. 网络与信息安全学报, 2023, 9(5): 116–126. doi: 10.11959/j.issn.2096-109x.2023075.XING Xinxin, ZUO Qingya, and LIU Jianwei. 5G-based smart airport network security scheme design and security analysis[J]. Chinese Journal of Network and Information Security, 2023, 9(5): 116–126. doi: 10.11959/j.issn.2096-109x.2023075. [118] FLORIDO-BENÍTEZ L. Identifying and classifying cyberattacks on airports[J]. Cyber Security: A Peer-Reviewed Journal, 2024, 8(1): 63–79. doi: 10.69554/TWHW5595. [119] SUCIU G, SCHEIANU A, VULPE A, et al. Cyber-attacks-the impact over airports security and prevention modalities[C]. The WorldCIST: World Conference on Information Systems and Technologies, Naples, Italy, 2018: 154–162. doi: 10.1007/978-3-319-77700-9_16. [120] KALAIVANI N, RAMAN R, BASAVARADDI C C S, et al. Enhancing air travel with IoT: Smart airports and passenger experience[C]. 2023 7th International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 2023: 1300–1305. doi: 10.1109/ICECA58529.2023.10394746. [121] SAADA H, ORIZIO R, and SEBASTIO S. Modeling and conducting security risk assessment of smart airport infrastructures with SecRAM[C]. The 7th International Conference on Networking, Intelligent Systems and Security, Meknes, Morocco, 2024: 59. doi: 10.1145/3659677.3659992. [122] ALLABERGANOV B A and ABDULLAYEV D. Models for protecting airport information systems from cyber incidents[J]. Science and Innovation, 2022, 1(8): 919–923. doi: 10.5281/zenodo.7445057. [123] FERON E M, SANNI O, MOTE M, et al. Ariadne: A common-sense thread for enabling provable safety in air mobility systems with unreliable components[C]. The AIAA SciTech 2022 Forum, San Diego, USA, 2022: 0057. doi: 10.2514/6.2022-0057. [124] ABOAOJA F A, ZAINAL A, GHALEB F A, et al. Malware detection issues, challenges, and future directions: A survey[J]. Applied Sciences, 2022, 12(17): 8482. doi: 10.3390/app12178482. [125] ABELSON H, ANDERSON R, BELLOVIN S M, et al. Bugs in our pockets: The risks of client-side scanning[J]. Journal of Cybersecurity, 2024, 10(1): tyad020. doi: 10.1093/cybsec/tyad020. [126] LI Tong, WANG Xiaowei, and NI Yeming. Aligning social concerns with information system security: A fundamental ontology for social engineering[J]. Information Systems, 2022, 104: 101699. doi: 10.1016/j.is.2020.101699. [127] ELSALLAMY S and ABD RAHMAN N A. AI implementation in airport system: A study of vulnerabilities and countermeasures[J]. Journal of Applied Technology and Innovation, 2022, 6(2): 11–16. [128] SEN S, AYDOGAN E, and AYSAN A I. Coevolution of mobile malware and anti-malware[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(10): 2563–2574. doi: 10.1109/TIFS.2018.2824250. [129] 丁磊, 韩建云, 张西武, 等. 智慧机场物联网系统安全防护研究[J]. 民航学报, 2021, 5(5): 81–84. doi: 10.3969/j.issn.2096-4994.2021.05.021.DING Lei, HAN Jianyun, ZHANG Xiwu, et al. Research on cyber security protection of IOT system of smart airport[J]. Journal of Civil Aviation, 2021, 5(5): 81–84. doi: 10.3969/j.issn.2096-4994.2021.05.021. [130] SCOZZARO G, MUJICA MOTA M, DELAHAYE D, et al. Simulation-optimisation-based decision support system for managing airport security resources[C]. The 11th Congress on Simulation for a Sustainable Future, Amsterdam, The Netherlands, 2023: 140–155. doi: 10.1007/978-3-031-68438-8_11. [131] ALSULAMI A A and ZEIN-SABATTO S. Resilient cyber-security approach for aviation cyber-physical systems protection against sensor spoofing attacks[C]. Proceedings of 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), USA, 2021: 565–571. doi: 10.1109/CCWC51732.2021.9376158. [132] ABDELGHANI T. Implementation of defense in depth strategy to secure industrial control system in critical infrastructures[J]. American Journal of Artificial Intelligence, 2019, 3(2): 17–22. doi: 10.11648/j.ajai.20190302.11. [133] VYAS S, HANNAY J, BOLTON A, et al. Automated cyber defence: A review[EB/OL]. https://arxiv.org/abs/2303.04926, 2023. [134] ALABBAD M, MHASKAR N, and KHEDRI R. Hardening of network segmentation using automated referential penetration testing[J]. Journal of Network and Computer Applications, 2024, 224: 103851. doi: 10.1016/j.jnca.2024.103851. [135] ASHRAFI R and ALKINDI H. A framework for IS/IT disaster recovery planning[J]. International Journal of Business Continuity and Risk Management, 2022, 12(1): 1–21. doi: 10.1504/IJBCRM.2022.121645. [136] BEAN B. Mitigating insider threats in the domestic aviation system: Policy options for TSA[J]. Homeland Security Affairs, 2017. [137] CORNACCHIA M, PAPA F, and SAPIO B. User acceptance of voice biometrics in managing the physical access to a secure area of an international airport[J]. Technology Analysis & Strategic Management, 2020, 32(10): 1236–1250. doi: 10.1080/09537325.2020.1758655. [138] CURRAH P and MULQUEEN T. Securitizing gender: Identity, biometrics, and transgender bodies at the airport[J]. Social Research: An International Quarterly, 2011, 78(2): 557–582. doi: 10.1353/sor.2011.0030. [139] KARAMITSOS I, PAPADAKI M, AL-HUSSAENI K, et al. Transforming airport security: Enhancing efficiency through blockchain smart contracts[J]. Electronics, 2023, 12(21): 4492. doi: 10.3390/electronics12214492. [140] MALIK H, TAHIR S, TAHIR H, et al. A homomorphic approach for security and privacy preservation of Smart Airports[J]. Future Generation Computer Systems, 2023, 141: 500–513. doi: 10.1016/j.future.2022.12.005. [141] ALI A S and HASAN D S. An IoT-based smart airport check-in system via three-factor authentication (3FA)[J]. Zanco Journal of Pure and Applied Sciences, 2023, 35(4): 1–13. doi: 10.21271/ZJPAS.35.4.01. [142] NIRAULA M. Cybersecurity and interoperability of aviation safety service ecosystem[C]. 2022 Integrated Communication, Navigation and Surveillance Conference (ICNS), Dulles, USA, 2022: 1–12. doi: 10.1109/ICNS54818.2022.9771482. [143] SUCIU G, SCHEIANU A, PETRE I, et al. Cybersecurity threats analysis for airports[C]. Proceedings of the World Conference on Information Systems and Technologies, Galicia, Spain, 2019: 252–262. doi: 10.1007/978-3-030-16184-2_25. [144] ZORLU O, OZSOY A, SERT S A. A role-based access control management model on blockchain for restricted facilities: An airport example[C]. 2023 10th International Conference on Recent Advances in Air and Space Technologies (RAST), Istanbul, Turkiye, 2023: 1–6. doi: 10.1109/RAST57548.2023.10197974. [145] WILLEMSEN B and CADEE M. Extending the airport boundary: Connecting physical security and cybersecurity[J]. Journal of Airport Management, 2018, 12(3): 236–247. doi: 10.69554/UVLU6436. [146] MENZEL D and HESTERMAN J. Airport security threats and strategic options for mitigation[J]. Journal of Airport Management, 2018, 12(2): 118–131. doi: 10.69554/EFBM2046. [147] ZHOU Zhipeng, YU Xinhui, ZHU Zeyu, et al. Development and application of a Bayesian network-based model for systematically reducing safety risks in the commercial air transportation system[J]. Safety Science, 2023, 157: 105942. doi: 10.1016/j.ssci.2022.105942. [148] EILSTRUP-SANGIOVANNI M. Ordering global governance complexes: The evolution of the governance complex for international civil aviation[J]. The Review of International Organizations, 2022, 17(2): 293–322. doi: 10.1007/s11558-020-09411-z. [149] Federal Aviation Administration. NAS operational view[EB/OL]. https://www.faa.gov/about/office_org/headquarters_offices/ang/offices/tc/library/Storyboard/nextgen-overview.html, 2022. [150] SUN Mengyuan, TIAN Yong, WANG Xunuo, et al. Transport causality knowledge-guided GCN for propagated delay prediction in airport delay propagation networks[J]. Expert Systems with Applications, 2024, 240: 122426. doi: 10.1016/j.eswa.2023.122426. [151] CAI Kaiquan, LI Yue, ZHU Yongwen, et al. A geographical and operational deep graph convolutional approach for flight delay prediction[J]. Chinese Journal of Aeronautics, 2023, 36(3): 357–367. doi: 10.1016/j.cja.2022.10.004. [152] CAI Kaiquan, LI Yue, FANG Yiping, et al. A deep learning approach for flight delay prediction through time-evolving graphs[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(8): 11397–11407. doi: 10.1109/TITS.2021.3103502. [153] GUO Ziyu, MEI Guangxu, LIU Shijun, et al. SGDAN—A spatio-temporal graph dual-attention neural network for quantified flight delay prediction[J]. Sensors, 2020, 20(22): 6433. doi: 10.3390/s20226433. [154] LI Chi, QI Xixian, YANG Yuzhe, et al. FAST-CA: Fusion-based adaptive spatial-temporal learning with coupled attention for airport network delay propagation prediction[J]. Information Fusion, 2024, 107: 102326. doi: 10.1016/j.inffus.2024.102326. [155] RUAN J H, WANG Z X, CHAN F T S, et al. A reinforcement learning-based algorithm for the aircraft maintenance routing problem[J]. Expert Systems with Applications, 2021, 169: 114399. doi: 10.1016/j.eswa.2020.114399. [156] OSZUST M, KAPUSCINSKI T, WARCHOL D, et al. A vision-based method for supporting autonomous aircraft landing[J]. Aircraft Engineering and Aerospace Technology, 2018, 90(6): 973–982. doi: 10.1108/AEAT-11-2017-0250. [157] GAO Ruizhen, CHEN Meng, ZHAO Ziyue, et al. Real-time detection algorithm of aircraft landing gear based on improved YOLOv8[J]. 2024. doi: 10.21203/rs.3.rs-4493909/v1. [158] AMIT R A and MOHAN C K. A robust airport runway detection network based on R-CNN using remote sensing images[J]. IEEE Aerospace and Electronic Systems Magazine, 2021, 36(11): 4–20. doi: 10.1109/MAES.2021.3088477. [159] LIU Mingkun, FENG Guangkun, XU Tingbing, et al. Fusing dense features and pose consistency: A regression method for attitude measurement of aircraft landing[J]. IEEE Transactions on Instrumentation and Measurement, 2023, 72: 5007913. doi: 10.1109/TIM.2023.3244803. [160] SHI Qingbang and LI Jun. Objects detection of UAV for anti-UAV based on YOLOv4[C]. 2020 IEEE 2nd International Conference on Civil Aviation Safety and Information Technology, Weihai, China, 2020: 1048–1052. doi: 10.1109/ICCASIT50869.2020.9368788. [161] ZHAO Jie, ZHANG Jingshu, LI Dongdong, et al. Vision-based anti-UAV detection and tracking[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(12): 25323–25334. doi: 10.1109/TITS.2022.3177627. [162] WANG Chuanyu, WANG Tian, WANG Ershen, et al. Flying small target detection for anti-UAV based on a Gaussian mixture model in a compressive sensing domain[J]. Sensors, 2019, 19(9): 2168. doi: 10.3390/s19092168. [163] KANAVOS A, KOUNELIS F, ILIADIS L, et al. Deep learning models for forecasting aviation demand time series[J]. Neural Computing and Applications, 2021, 33(23): 16329–16343. doi: 10.1007/s00521-021-06232-y. [164] GU Weifan, GUO Baohua, ZHANG Zhezhe, et al. Civil aviation passenger traffic forecasting: Application and comparative study of the seasonal autoregressive integrated moving average model and backpropagation neural network[J]. Sustainability, 2024, 16(10): 4110. doi: 10.3390/su16104110. [165] BRITTAIN M and WEI Peng. Scalable autonomous separation assurance with heterogeneous multi-agent reinforcement learning[J]. IEEE Transactions on Automation Science and Engineering, 2022, 19(4): 2837–2848. doi: 10.1109/TASE.2022.315160. [166] KRAVARIS T, LENTZOS K, SANTIPANTAKIS G, et al. Explaining deep reinforcement learning decisions in complex multiagent settings: Towards enabling automation in air traffic flow management[J]. Applied Intelligence, 2023, 53(4): 4063–4098. doi: 10.1007/s10489-022-03605-1. [167] WANG Yuan, CAI Weilin, TU Yilei, et al. Reinforcement-learning-informed prescriptive analytics for air traffic flow management[J]. IEEE Transactions on Automation Science and Engineering, 2024, 21(3): 4188–4202. doi: 10.1109/TASE.2023.3292921. [168] SPATHARIS C, BASTAS A, KRAVARIS T, et al. Hierarchical multiagent reinforcement learning schemes for air traffic management[J]. Neural Computing and Applications, 2023, 35(1): 147–159. doi: 10.1007/S00521-021-05748-7. [169] PAPADOPOULOS G, BASTAS A, VOUROS G A, et al. Deep reinforcement learning in service of air traffic controllers to resolve tactical conflicts[J]. Expert Systems with Applications, 2024, 236: 121234. doi: 10.1016/j.eswa.2023.121234. [170] BAUMANN S and KLINGAUF U. Modeling of aircraft fuel consumption using machine learning algorithms[J]. CEAS Aeronautical Journal, 2020, 11(1): 277–287. doi: 10.1007/s13272-019-00422-0. [171] ZHU Xinting and LI Lishuai. Flight time prediction for fuel loading decisions with a deep learning approach[J]. Transportation Research Part C: Emerging Technologies, 2021, 128: 103179. doi: 10.1016/j.trc.2021.103179. [172] METLEK S. A new proposal for the prediction of an aircraft engine fuel consumption: A novel CNN-BiLSTM deep neural network model[J]. Aircraft Engineering and Aerospace Technology, 2023, 95(5): 838–848. doi: 10.1108/AEAT-05-2022-0132. [173] EUROCONTROL. AI/ML based augmented 4D trajectory[EB/OL]. https://www.eurocontrol.int/publication/aiml-based-augmented-4d-trajectory, 2021. [174] SHI Zhiyuan, XU Min, PAN Quan, et al. LSTM-based flight trajectory prediction[C]. 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 2018: 1–8. doi: 10.1109/IJCNN.2018.8489734. [175] ZHANG Xiaoge and MAHADEVAN S. Bayesian neural networks for flight trajectory prediction and safety assessment[J]. Decision Support Systems, 2020, 131: 113246. doi: 10.1016/j.dss.2020.113246. [176] ZHANG Zheng, GUO Dongyue, ZHOU Shizhong, et al. Flight trajectory prediction enabled by time-frequency wavelet transform[J]. Nature Communications, 2023, 14(1): 5258. doi: 10.1038/s41467-023-40903-9. [177] SHI Zhiyuan, XU Min, and PAN Quan. 4-D flight trajectory prediction with constrained LSTM network[J]. IEEE Transactions on Intelligent Transportation Systems, 2021, 22(11): 7242–7255. doi: 10.1109/TITS.2020.3004807. [178] CHEN C J, HUANG C N, and YANG S M. Application of deep learning to multivariate aviation weather forecasting by long short-term memory[J]. Journal of Intelligent & Fuzzy Systems, 2023, 44(3): 4987–4997. doi: 10.3233/JIFS-223183. [179] YUAN Ligang, ZENG Yang, CHEN Haiyan, et al. Terminal traffic situation prediction model under the influence of weather based on deep learning approaches[J]. Aerospace, 2022, 9(10): 580. doi: 10.3390/aerospace9100580. [180] CHEN C J, HUANG C N, and YANG S M. Aviation visibility forecasting by integrating Convolutional Neural Network and long short-term memory network[J]. Journal of Intelligent & Fuzzy Systems, 2023, 45(3): 5007–5020. doi: 10.3233/JIFS-230483. [181] ZHAO Tianyu, ESCRIBANO J, MAJUMDAR A, et al. Spatiotemporal thunderstorm forecasting for pre-tactical air traffic operation: A deep learning approach[C]. Proceedings of AIAA Aviation Forum and Ascend 2024, Las Vegas, Nevada, 2024: 4634. doi: 10.2514/6.2024-4634. [182] AYHAN B, VARGO E P, and TANG Huang. On the exploration temporal fusion transformers for anomaly detection with multivariate aviation time-series data[J]. Aerospace, 2024, 11(8): 646. doi: 10.3390/aerospace11080646. [183] ZHOU Wentao, CAI Chengtao, WU Kejun, et al. Las-yolo: A lightweight detection method based on YOLOv7 for small objects in airport surveillance[J]. The Journal of Supercomputing, 2024, 80(15): 21764–21789. doi: 10.1007/S11227-024-06289-1. [184] ZHANG Xiang, SHU Chang, LI Shuai, et al. AGVS: A new change detection dataset for airport ground video surveillance[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(11): 20588–20600. doi: 10.1109/TITS.2022.3184978. [185] LI Weidong, LIU Jia, and MEI Hang. Lightweight convolutional neural network for aircraft small target real-time detection in Airport videos in complex scenes[J]. Scientific Reports, 2022, 12(1): 14474. doi: 10.1038/s41598-022-18263-z. [186] ZHOU Wentao, CAI Chengtao, ZHENG Liying, et al. ASSD-YOLO: A small object detection method based on improved YOLOv7 for airport surface surveillance[J]. Multimedia Tools and Applications, 2024, 83(18): 55527–55548. doi: 10.1007/S11042-023-17628-4. [187] ZHANG Mengmei, WANG Xiao, ZHU Meiqi, et al. Robust heterogeneous graph neural networks against adversarial attacks[C]. The 36th AAAI Conference on Artificial Intelligence, 2022, 36(4): 4363–4370. doi: 10.1609/aaai.v36i4.20357. [188] LIN Xixun, ZHOU Chuan, WU Jia, et al. Exploratory adversarial attacks on graph neural networks for semi-supervised node classification[J]. Pattern Recognition, 2023, 133: 109042. doi: 10.1016/j.patcog.2022.109042. [189] FINKELSHTEIN B, BASKIN C, ZHELTONOZHSKII E, et al. Single-node attacks for fooling graph neural networks[J]. Neurocomputing, 2022, 513: 1–12. doi: 10.1016/j.neucom.2022.09.115. [190] ZHANG Haotian and MA Xu. Misleading attention and classification: An adversarial attack to fool object detection models in the real world[J]. Computers & Security, 2022, 122: 102876. doi: 10.1016/j.cose.2022.102876. [191] LI Guopeng, XU Yue, DING Jian, et al. Towards generic and controllable attacks against object detection[J]. IEEE Transactions on Geoscience and Remote Sensing, 2024, 62: 5635812. doi: 10.1109/TGRS.2024.3417958. [192] WU Tao, WANG Xuechun, QIAO Shaojie, et al. Small perturbations are enough: Adversarial attacks on time series prediction[J]. Information Sciences, 2022, 587: 794–812. doi: 10.1016/j.ins.2021.11.007. [193] KARIM F, MAJUMDAR S, and DARABI H. Adversarial attacks on time series[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2021, 43(10): 3309–3320. doi: 10.1109/TPAMI.2020.2986319. [194] LIU Guanlin and LAI Lifeng. Efficient adversarial attacks on online multi-agent reinforcement learning[C]. The 37th International Conference on Neural Information Processing Systems, New Orleans, USA, 2023: 1062. [195] YOU Qiaoben, YING Chengyang, ZHOU Xinning, et al. Understanding adversarial attacks on observations in deep reinforcement learning[J]. Science China Information Sciences, 2024, 67(5): 152104. doi: 10.1007/s11432-021-3688-y. [196] SHEN Yun, HE Xinlei, HAN Yufei, et al. Model stealing attacks against inductive graph neural networks[C]. 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2022: 1175–1192. doi: 10.1109/SP46214.2022.9833607. [197] HE X, JIA J, BACKES M, et al. Stealing links from graph neural networks[C/OL]. Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), 2021: 2669–2686. [198] PODHAJSKI M, DUBIŃSKI J, BOENISCH F, et al. Efficient model-stealing attacks against inductive graph neural networks[J]. Frontiers in Artificial Intelligence and Applications, 2024, 392: 1438–1445. doi: 10.3233/FAIA240646. [199] XU Jing, XUE Minhui, and PICEK S. Explainability-based backdoor attacks against graph neural networks[C]. The 3rd ACM Workshop on Wireless Security and Machine Learning, Abu Dhabi, United Arab Emirates, 2021: 31–36. doi: 10.1145/3468218.3469046. [200] ZHENG Haibin, XIONG Haiyang, CHEN Jinyin, et al. Motif-backdoor: Rethinking the backdoor attack on graph neural networks via motifs[J]. IEEE Transactions on Computational Social Systems, 2024, 11(2): 2479–2493. doi: 10.1109/TCSS.2023.3267094. [201] CHAN S H, DONG Yinpeng, ZHU Jun, et al. BadDet: Backdoor attacks on object detection[C]. The European Conference on Computer Vision, Tel Aviv, Israel, 2022: 396–412. doi: 10.1007/978-3-031-25056-9_26. [202] LUO Chengxiao, LI Yiming, JIANG Yong, et al. Untargeted backdoor attack against object detection[C]. Proceedings of 2023 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Rhodes Island, Greece, 2023: 1–5. doi: 10.1109/ICASSP49357.2023.10095980. [203] KIOURTI P, WARDEGA K, JHA S, et al. TrojDRL: Evaluation of backdoor attacks on deep reinforcement learning[C]. 2020 57th ACM/IEEE Design Automation Conference (DAC), San Francisco, USA, 2020: 1–6. doi: 10.1109/DAC18072.2020.9218663. [204] CHEN Yanjiao, ZHENG Zhicong, and GONG Xueluan. MARNet: Backdoor attacks against cooperative multi-agent reinforcement learning[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(5): 4188–4198. doi: 10.1109/TDSC.2022.3207429. [205] HASHEMI S M, BOTEZ R M, and GRIGORIE T L. New reliability studies of data-driven aircraft trajectory prediction[J]. Aerospace, 2020, 7(10): 145. doi: 10.3390/aerospace7100145. [206] DONG Guimin, TANG Mingyue, WANG Zhiyuan, et al. Graph neural networks in IoT: A survey[J]. ACM Transactions on Sensor Networks, 2023, 19(2): 47. doi: 10.1145/3565973. [207] KIM S and PARK K J. A survey on machine-learning based security design for cyber-physical systems[J]. Applied Sciences, 2021, 11(12): 5458. doi: 10.3390/app11125458. [208] VAN IERSEL Q G, MURRIETA MENDOZA A, FELIX PATRON R S, et al. Attack and defense on aircraft trajectory prediction algorithms[C]. The AIAA AVIATION 2022 Forum, Chicago, USA, 2022: 4027. doi: 10.2514/6.2022-4027. [209] KIANPOUR M and WEN Shaofang. Timing attacks on machine learning: State of the art[C]. 2019 Intelligent Systems Conference, London, UK, 2020: 111–125. doi: 10.1007/978-3-030-29516-5_10. [210] MADRY A, MAKELOV A, SCHMIDT L, et al. Towards deep learning models resistant to adversarial attacks[C]. Proceedings of the 6th International Conference on Learning Representations, Vancouver, Canada, 2017: 1–23. [211] MIYATO T, MAEDA S, KOYAMA M, et al. Virtual adversarial training: A regularization method for supervised and semi-supervised learning[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2019, 41(8): 1979–1993. doi: 10.1109/TPAMI.2018.2858821. [212] YE Hongwei, LIU Xiaozhang, and LI Chunlai. DSCAE: A denoising sparse convolutional autoencoder defense against adversarial examples[J]. Journal of Ambient Intelligence and Humanized Computing, 2022, 13(3): 1419–1429. doi: 10.1007/s12652-020-02642-3. [213] XU Weilin, EVANS D, and QI Yanjun. Feature squeezing: Detecting adversarial examples in deep neural networks[EB/OL]. https://arxiv.org/abs/1704.01155, 2017. [214] TRAMÈR F, KURAKIN A, PAPERNOT N, et al. Ensemble adversarial training: Attacks and defenses[EB/OL]. https://arxiv.org/abs/1705.07204, 2017. [215] KUZLU M, CATAK F O, CALI U, et al. Adversarial security mitigations of mmWave beamforming prediction models using defensive distillation and adversarial retraining[J]. International Journal of Information Security, 2023, 22(2): 319–332. doi: 10.1007/s10207-022-00644-0. [216] TSENG F H, ZENG Jiangyi, CHO H H, et al. Detecting adversarial examples of fake news via the neurons activation state[J]. IEEE Transactions on Computational Social Systems, 2024, 11(4): 5199–5209. doi: 10.1109/TCSS.2023.3293718. [217] ZHANG Lei, ZHOU Yuhang, YANG Yi, et al. Meta invariance defense towards generalizable robustness to unknown adversarial attacks[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2024, 46(10): 6669–6687. doi: 10.1109/TPAMI.2024.3385745. [218] KHALED K, DHAOUADI M, DE MAGALHAES F G, et al. Efficient defense against model stealing attacks on convolutional neural networks[C]. 2023 International Conference on Machine Learning and Applications (ICMLA), Jacksonville, USA, 2023: 45–52. DOI: 10.1109/ICMLA58977.2023.00015. [219] 郭鑫. 基于决策空间的模型窃取攻击检测与防御方法[D]. [硕士论文], 西安电子科技大学, 2023.GUO Xin. Decision space based approach to detect and defend against model stealing attacks[D]. [Master dissertation], Xidian University, 2023. [220] LI Yiming, ZHU Linghui, JIA Xiaojun, et al. Defending against model stealing via verifying embedded external features[C]. The 36th AAAI Conference on Artificial Intelligence, Palo Alto, USA, 2022: 1464–1472. doi: 10.1609/aaai.v36i2.20036. [221] THUDUMU S, BRANCH P, JIN Jiong, et al. A comprehensive survey of anomaly detection techniques for high dimensional big data[J]. Journal of Big Data, 2020, 7: 42. doi: 10.1186/s40537-020-00320-x. [222] GU Tianyu, DOLAN-GAVITT B, and GARG S. BadNets: Identifying vulnerabilities in the machine learning model supply chain[EB/OL]. https://arxiv.org/abs/1708.06733, 2017. [223] WAN Li, ZEILER M, ZHANG Sixin, et al. Regularization of neural networks using dropconnect[C]. The 30th International Conference on International Conference on Machine Learning, Atlanta, USA, 2013: III-1058–III-1066. [224] QIAN Zhuang, HUANG Kaizhu, WANG Qiufeng, et al. A survey of robust adversarial training in pattern recognition: Fundamental, theory, and methodologies[J]. Pattern Recognition, 2022, 131: 108889. doi: 10.1016/j.patcog.2022.108889. [225] FREDRIKSON M, JHA S, and RISTENPART T. Model inversion attacks that exploit confidence information and basic countermeasures[C]. The 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, USA, 2015: 1322–1333. doi: 10.1145/2810103.2813677. [226] CHEN Huajie, LIU Chi, ZHU Tianqing, et al. When deep learning meets watermarking: A survey of application, attacks and defenses[J]. Computer Standards & Interfaces, 2024, 89: 103830. doi: 10.1016/j.csi.2023.103830. [227] DENG Lei, LI Guoqi, HAN Song, et al. Model compression and hardware acceleration for neural networks: A comprehensive survey[J]. Proceedings of the IEEE, 2020, 108(4): 485–532. doi: 10.1109/JPROC.2020.2976475. [228] GUO Sensen, LI Xiaoyu, ZHU Peican, et al. ADS-detector: An attention-based dual stream adversarial example detection method[J]. Knowledge-Based Systems, 2023, 265: 110388. doi: 10.1016/j.knosys.2023.110388. [229] SCHIOPPA A, FILIPPOVA K, TITOV I, et al. Theoretical and practical perspectives on what influence functions do[C]. The Thirty-Seventh Annual Conference on Neural Information Processing Systems, New Orleans, USA, 2023. [230] EU Commission. EU Commission—Proposal for a Regulation of the European Parliament and of the Council laying down harmonised rules on artificial intelligence (Artificial Intelligence Act) and amending certain Union legislative acts, COM/2021/206 final[S]. 2021. [231] ZENG Leya, WANG Buhong, TIAN Jiwei, et al. Threat impact analysis to air traffic control systems through flight delay modeling[J]. Computers & Industrial Engineering, 2021, 162: 107731. doi: 10.1016/j.cie.2021.107731. [232] ZENG Leya, WANG Buhong, WANG Tianrui, et al. Research on delay propagation mechanism of air traffic control system based on causal inference[J]. Transportation Research Part C: Emerging Technologies, 2022, 138: 103622. doi: 10.1016/j.trc.2022.103622. [233] 白洁, 王布宏, 田继伟, 等. 基于动态离散模型的机场ADS-B攻击威胁影响研究[J]. 电光与控制, 2024, 31(7): 27–35, 52. doi: 10.3969/j.issn.1671-637X.2024.07.005.BAI Jie, WANG Buhong, TIAN Jiwei, et al. On threat impact of airport ADS-B attack based on dynamic discrete model[J]. Electronics Optics & Control, 2024, 31(7): 27–35, 52. doi: 10.3969/j.issn.1671-637X.2024.07.005. -





 下载:
下载:


 下载:
下载:
