Graph Features Analysis and Detection Method of IP Soft Core Hardware Trojan
-
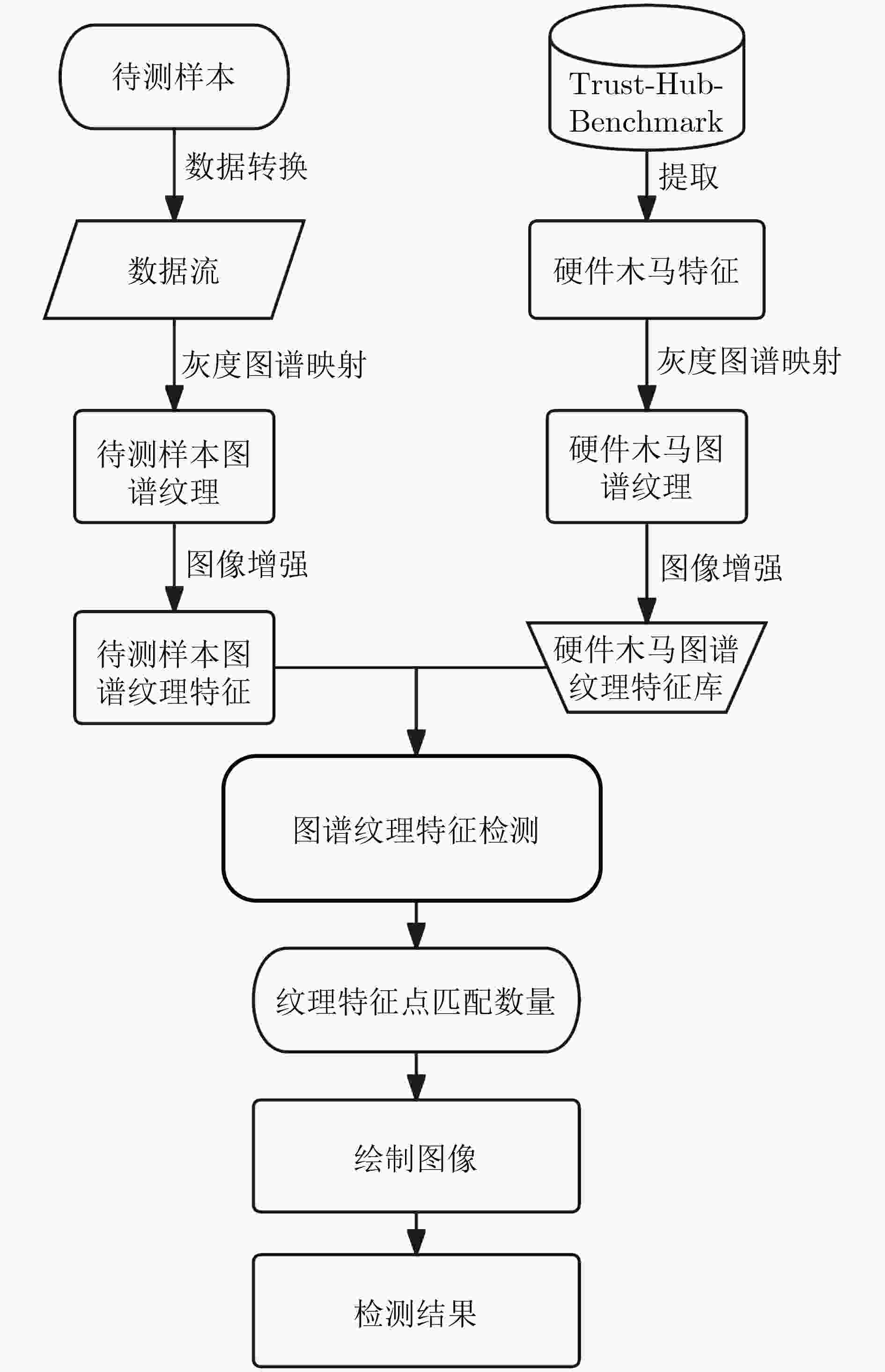
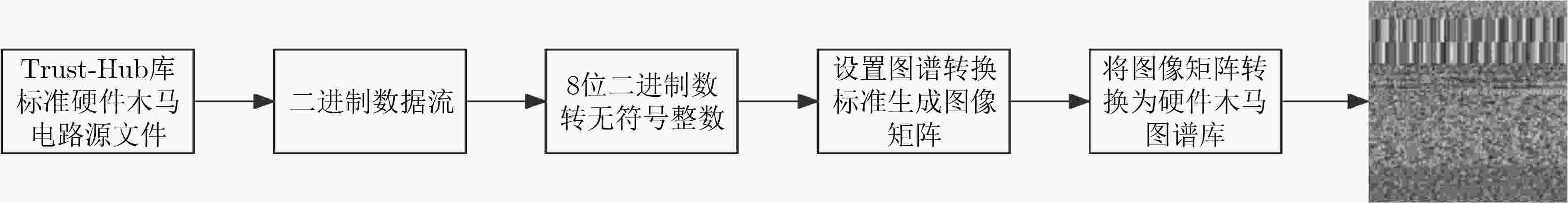
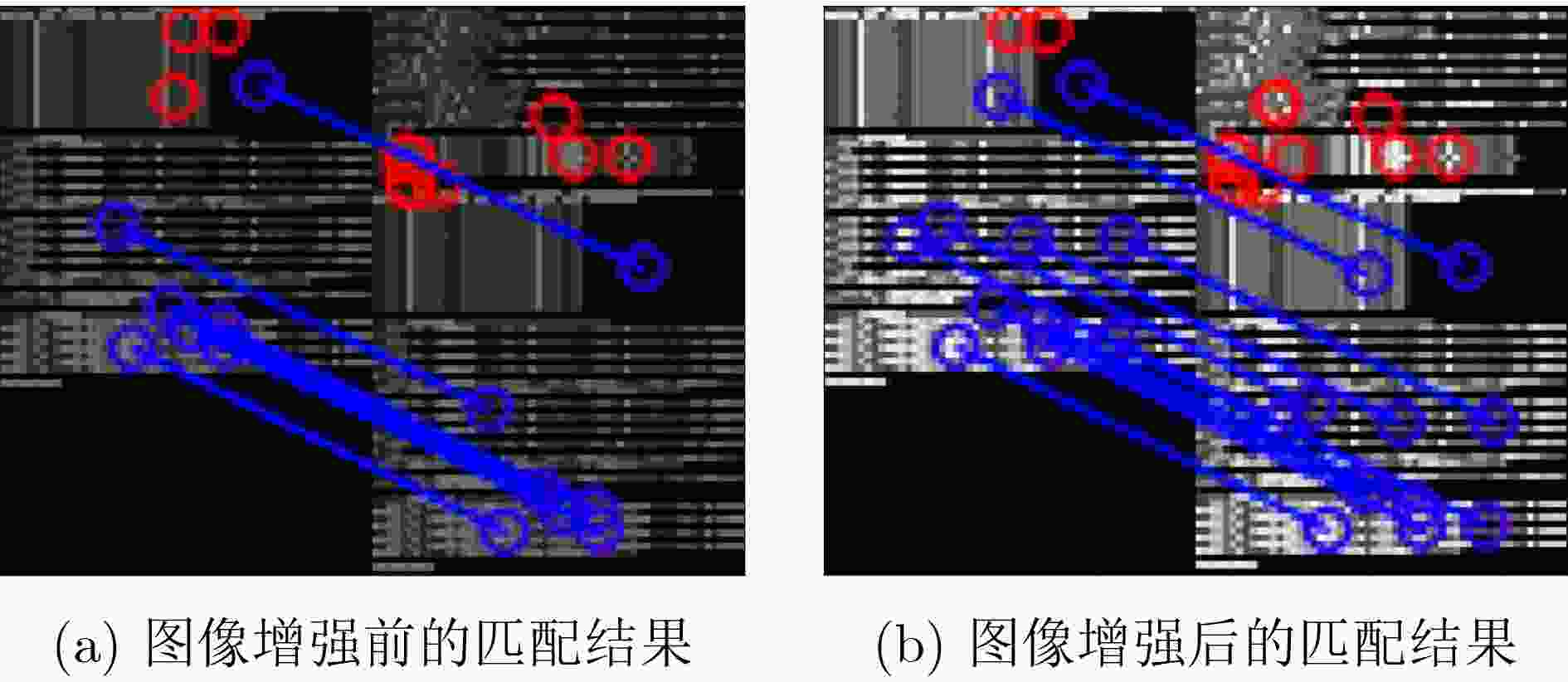
摘要: 随着集成电路技术的飞速发展,芯片在设计、生产和封装过程中,很容易被恶意植入硬件木马逻辑,当前IP软核的安全检测方法逻辑复杂、容易错漏且无法对加密IP软核进行检测。该文利用非可控IP软核与硬件木马寄存器传输级(RTL)代码灰度图谱的特征差异,提出一种基于图谱特征分析的IP软核硬件木马检测方法,通过图谱转换和图谱增强得到标准图谱,利用纹理特征提取匹配算法实现硬件木马检测。实验使用设计阶段被植入7类典型木马的功能逻辑单元为实验对象,检测结果显示7类典型硬件木马的检测正确率均达到了90%以上,图像增强后特征点匹配成功数量的平均增长率达到了13.24%,有效提高了硬件木马检测的效率。Abstract: With the rapid development of integrated circuit technology, chips are easily implanted with malicious hardware Trojan logic in the process of design, production and packaging. Current security detection methods for IP soft core are logically complex, prone to errors and omissions, and unable to detect encrypted IP soft core. The paper uses the feature differences of non-controllable IP soft core and hardware Trojan Register Transfer Level (RTL) code grayscale map, proposing a hardware Trojan detection method for IP soft cores based on graph feature analysis, through the map conversion and map enhancement to get the standard map, using the texture feature extraction matching algorithm to achieve hardware Trojan detection. The experimental subjects are functional logic units with seven types of typical Trojans implanted during the design phase, and the detection results show that the detection correct rate of seven types of typical hardware Trojans has reached more than 90%, and the average growth rate of the number of successful feature point matches after the image enhancement has reached 13.24%, effectively improving the effectiveness of hardware Trojan detection.
-
Key words:
- IP soft core /
- Hardware Trojan /
- Grayscale map /
- Texture feature /
- Detection algorithm
-
表 1 7种硬件木马分类原理特点对照表
插入阶段 抽象层次 激活机制 效果 物理特性 B19-T100 设计阶段 门级 基于内部时间的触发 改变功能 紧密、功能性、布局相同 PIC16F84-T100 设计阶段 寄存器传输级别 内部条件触发 服务拒绝 功能性 s35932-T100 设计阶段 门级 内部条件触发 改变功能,泄露信息 功能性 AES-T100 设计阶段 寄存器传输级别 始终激活 泄露信息 功能性 wb_conmax-T100 设计阶段 门级 内部条件触发 改变功能,拒绝服务 功能性 BasicRSA-T100 设计阶段 寄存器传输级别 外部用户输入触发 泄露信息 功能性 RS232-T100 设计阶段 寄存器传输级别 内部条件触发 拒绝服务 功能性 表 2 7种木马图谱图像增强前后的图谱特征提取匹配结果
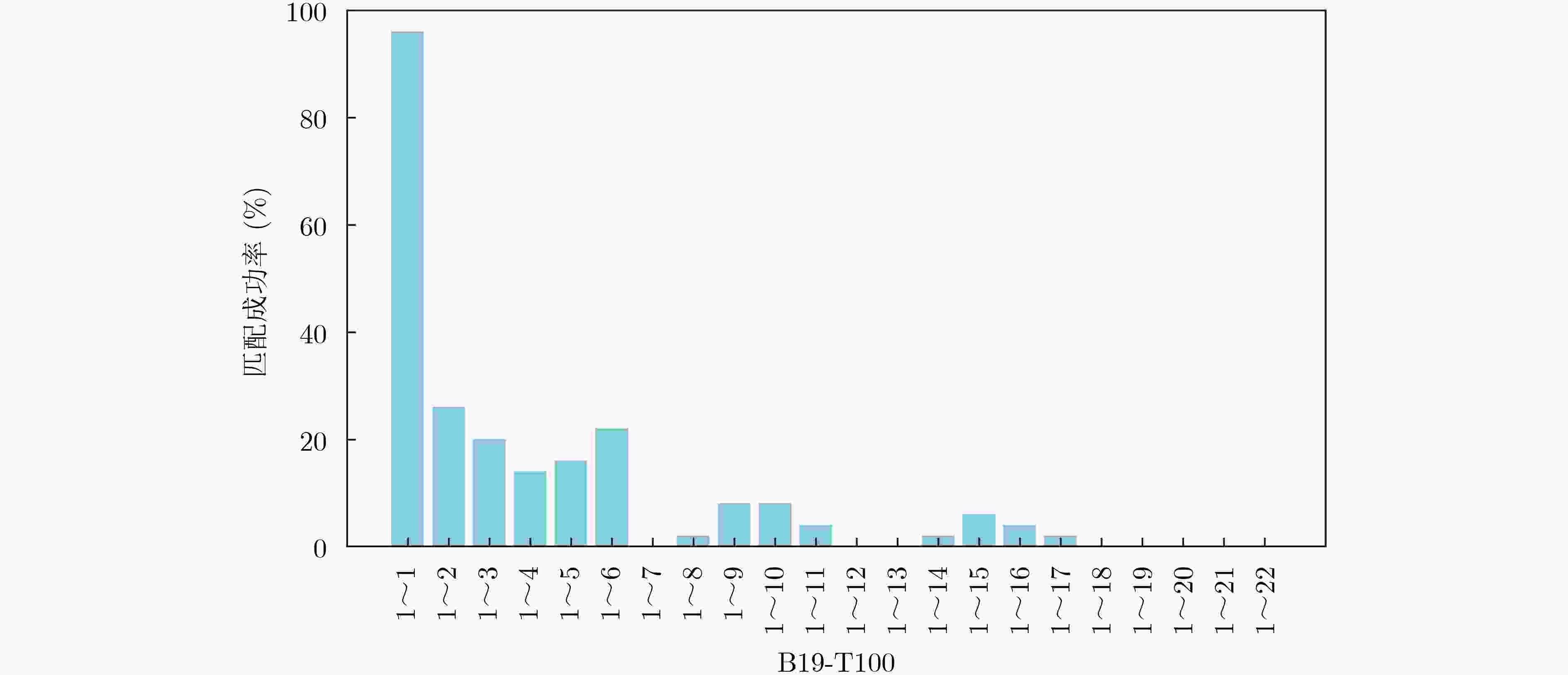
木马类型 图像增强前 图像增强后 特征点总数 匹配成功的数量 特征点总数 匹配成功的数量 B19-T100 46 44 50 48 PIC16F84-T100 6 6 6 6 s35932-T100 40 37 41 39 AES-T100 22 22 25 25 wb_conmax-T100 10 7 13 11 BasicRSA-T100 63 49 65 51 RS232-T100 51 30 52 31 表 3 BasicRSA-T100在宽度为25不同高度下的匹配结果
25 50 75 100 125 150 175 200 特征点总数 54 62 62 65 68 68 68 68 匹配成功的数量 27 37 47 51 61 52 52 52 匹配成功率(%) 50.00 59.68 75.81 78.46 89.71 76.47 76.47 76.47 表 4 BasicRSA-T100在高度为100不同宽度下的匹配结果
25 50 75 100 125 150 175 200 特征点总数 65 60 81 80 80 80 80 80 匹配成功的数量 51 44 65 67 67 67 67 67 匹配成功率(%) 78.46 73.33 80.25 83.75 83.75 83.75 83.75 83.75 -
[1] 杨达明, 黄姣英, 高成. 工艺偏差影响下硬件木马检测功率分析方法[J]. 计算机工程与应用, 2018, 54(24): 1–5,45. doi: 10.3778/j.issn.1002-8331.1810-0197.YANG Daming, HUANG Jiaoying, and GAO Cheng. Power analysis method of hardware Trojan detection considering process variation[J]. Computer Engineering and Applications, 2018, 54(24): 1–5,45. doi: 10.3778/j.issn.1002-8331.1810-0197. [2] 刘志强, 张铭津, 池源, 等. 一种深度学习的硬件木马检测算法[J]. 西安电子科技大学学报, 2019, 46(6): 37–45. doi: 10.19665/j.issn1001-2400.2019.06.006.LIU Zhiqiang, ZHANG Mingjin, CHI Yuan, et al. Hardware Trojan detection algorithm based on deep learning[J]. Journal of Xidian University, 2019, 46(6): 37–45. doi: 10.19665/j.issn1001-2400.2019.06.006. [3] 成祥, 李磊, 程伟. 基于RTL级硬件木马的检测方法[J]. 微电子学与计算机, 2017, 34(3): 56–60. doi: 10.19304/j.cnki.issn1000-7180.2017.03.012.CHENG Xiang, LI Lei, and CHENG Wei. A detection method of hardware Trojans based on RTL[J]. Microelectronics & Computer, 2017, 34(3): 56–60. doi: 10.19304/j.cnki.issn1000-7180.2017.03.012. [4] SANKAR V and NIRMALA DEVI M. Efficient hardware Trojan detection using generic feature extraction and weighted ensemble method[C]. The ICACIT 2021 on Advanced Computing and Intelligent Technologies, Singapore, Singapore, 2022: 165–181. doi: 10.1007/978-981-16-2164-2_14. [5] 谢俊, 周慧忠, 厉小燕, 等. 基于旁路分析的集成电路芯片硬件木马检测分析[J]. 电子技术与软件工程, 2022(18): 112–115.XIE Jun, ZHOU Huizhong, LI Xiaoyan, et al. Hardware Trojan detection and analysis of integrated circuit chips based on bypass analysis[J]. Electronic Technology and Software Engineering, 2022(18): 112–115. [6] 徐皓, 易茂祥, 金礼玉, 等. 电路分区自比较的硬件木马检测方法[J]. 合肥工业大学学报: 自然科学版, 2022, 45(12): 1630–1636. doi: 10.3969/j.issn.1003-5060.2022.12.007.XU Hao, YI Maoxiang, JIN Liyu, et al. Hardware Trojan detection method based on circuit partition self-comparison[J]. Journal of Hefei University of Technology: Natural Science, 2022, 45(12): 1630–1636. doi: 10.3969/j.issn.1003-5060.2022.12.007. [7] 赵毅强, 李博文, 马浩诚, 等. 基于混合特征分析的硬件木马检测方法[J]. 华中科技大学学报: 自然科学版, 2021, 49(5): 1–6. doi: 10.13245/j.hust.210501.ZHAO Yiqiang, LI Bowen, MA Haocheng, et al. Hardware Trojan detection method based on combined features analysis[J]. Journal of Huazhong University of Science and Technology: Natural Science Edition, 2021, 49(5): 1–6. doi: 10.13245/j.hust.210501. [8] JOSE F, PRIYATHARISHINI M, and NIRMALA DEVI M. Hardware Trojan detection using deep learning-generative adversarial network and stacked auto encoder neural networks[C]. The ICT Analysis and Applications, Singapore, Singapore, 2022: 203–210. doi: 10.1007/978-981-16-5655-2_19. [9] 李林源, 徐金甫, 严迎建, 等. 基于多维特征的门级硬件木马检测技术[J]. 计算机工程与应用, 2023, 59(18): 278–284. doi: 10.3778/j.issn.1002-8331.2206-0101.LI Linyuan, XU Jinfu, YAN Yingjian, et al. Hardware Trojan detection for gate-level netlists based on multidimensional features[J]. Computer Engineering and Applications, 2023, 59(18): 278–284. doi: 10.3778/j.issn.1002-8331.2206-0101. [10] 杨欢, 李海明. MLDet: 基于结构特征和XGBoost的硬件木马检测方法[J]. 计算机应用与软件, 2023, 40(11): 302–307. doi: 10.3969/j.issn.1000-386x.2023.11.045.YANG Huan and LI Haiming. MLDet: Hardware Trojan detection method based on structural features and XGBoost[J]. Computer Applications and Software, 2023, 40(11): 302–307. doi: 10.3969/j.issn.1000-386x.2023.11.045. [11] 史江义, 温聪, 刘鸿瑾, 等. 基于图神经网络的门级硬件木马检测方法[J]. 电子与信息学报, 2023, 45(9): 3253–3262. doi: 10.11999/JEIT221201.SHI Jiangyi, WEN Cong, LIU Hongjin, et al. Hardware Trojan detection for gate-level netlists based on graph neural network[J]. Journal of Electronics & Information Technology, 2023, 45(9): 3253–3262. doi: 10.11999/JEIT221201. [12] PAN Zhixin and MISHRA P. Hardware Trojan detection using side -channel analysis[M]. PAN Zhixin and MISHRA P. Explainable AI for Cybersecurity. Cham: Springer, 2023: 123–140. doi: 10.1007/978-3-031-46479-9_6. [13] JYOTHI V and RAJENDRAN J. Hardware Trojan attacks in FPGA and protection approaches[M]. BHUNIA S and TEHRANIPOOR M. The Hardware Trojan War: Attacks, Myths, and Defenses. Cham: Springer, 2018: 345–368. doi: 10.1007/978-3-319-68511-3_14. [14] ABDELLATIF K M, CORNESSE C, FOURNIER J, et al. New partitioning approach for hardware Trojan detection using side-channel measurements[C]. Proceedings of the 12th International Symposium on Applied Reconfigurable Computing, Mangaratiba, Brazil, 2016: 171–182. doi: 10.1007/978-3-319-30481-6_14. [15] VINOD G, RAMESH S R, and NIRMALA DEVI M. Simulation based hardware Trojan detection using path delay analysis[M]. RANGANATHAN G, FERNANDO X, and ROCHA Á. Inventive Communication and Computational Technologies. Singapore: Springer, 2022: 853–863. doi: 10.1007/978-981-19-4960-9_64. [16] NOZAWA K, HASEGAWA K, HIDANO S, et al. Adversarial examples for hardware-Trojan detection at gate-level netlists[C]. Proceedings of the ESORICS 2019 International Workshops, CyberICPS, SECPRE, SPOSE, and ADIoT on Computer Security, Luxembourg City, Luxembourg, 2020: 341–359. doi: 10.1007/978-3-030-42048-2_22. -





 下载:
下载:








 下载:
下载:
