SM4-XTS Side Channel Analysis Method Based on Multi-stage CPA
-
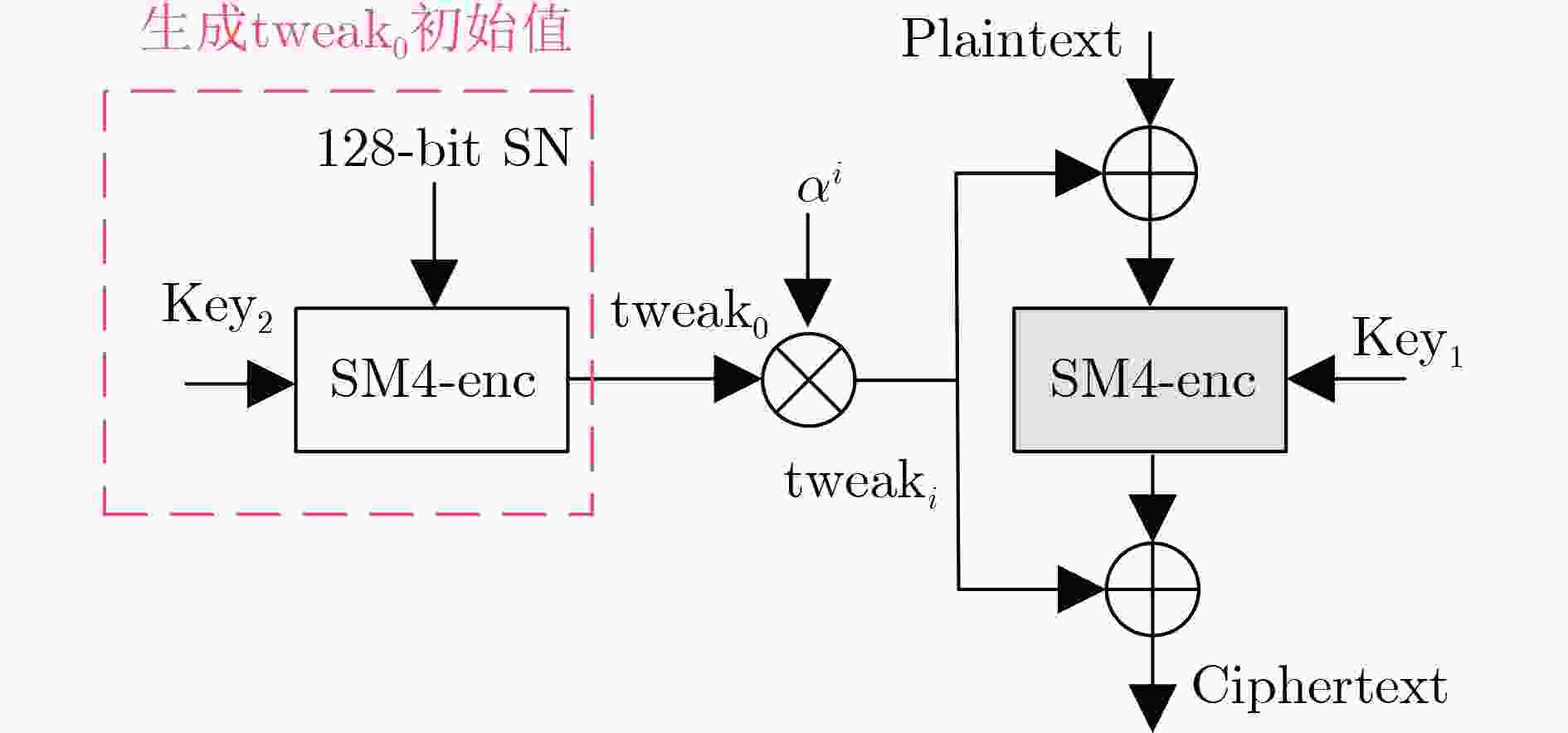
摘要: 带密文挪用的XEX可调分组密码(XTS)被广泛应用于存储加密中,随着大数据计算与新型侧信道分析方法的提出与应用,XTS加密模式的安全性成为一个值得关注的问题。近年来,已有部分研究针对XTS模式进行了侧信道的分析研究,通过确定部分密钥与调整值tweak,进而缩小密钥检索范围,但并没有实现对XTS模式系统的分析。该文提出一种针对SM4-XTS电路的侧信道分析技术,通过结合传统的相关功耗分析(CPA)与多阶段融合的CPA技术,解决了针对调整值模乘迭代导致的二进制数移位问题,从而实现调整值与密钥的精确提取。为了验证这种分析技术的有效性,在FPGA上实现了SM4-XTS加密模块来模拟实际情况中的加密存储器。实验结果表明,在
10000 条功耗曲线下,该技术可以成功提取目标加密电路的部分调整值与密钥。Abstract: The XEX-based Tweaked-codebook mode with ciphertext Stealing (XTS) is widely used in storage encryption. With the emergence and application of big data computing and novel side-channel analysis methods, the security of the XTS encryption mode has become a matter of concern. Recent studies have attempted side-channel analysis on the XTS mode, aiming to narrow down the key search space by identifying partial keys and tweak values, but a comprehensive analysis of the XTS mode system has not been achieved. In this paper, a side-channel analysis technique targeting the SM4-XTS circuit is proposed. By combining traditional Correlation Power Analysis (CPA) with a multi-stage fusion CPA technique, the technique addresses the binary number shifting issue caused by the iterative modulation multiplication of the tweak values, enabling precise extraction of both the tweak values and keys. To validate the effectiveness of this analytical technique, an SM4-XTS encryption module is implemented on an FPGA to simulate real-world encryption memory scenarios. Experimental results demonstrate that the technique can successfully extract partial tweak values and keys from the target encryption circuit using only 10 000 power traces.-
Key words:
- SM4-XTS /
- Side-channel Analysis /
- Block ciphers /
- Correlation Power Analysis (CPA)
-
1 tweak0后96比特分析
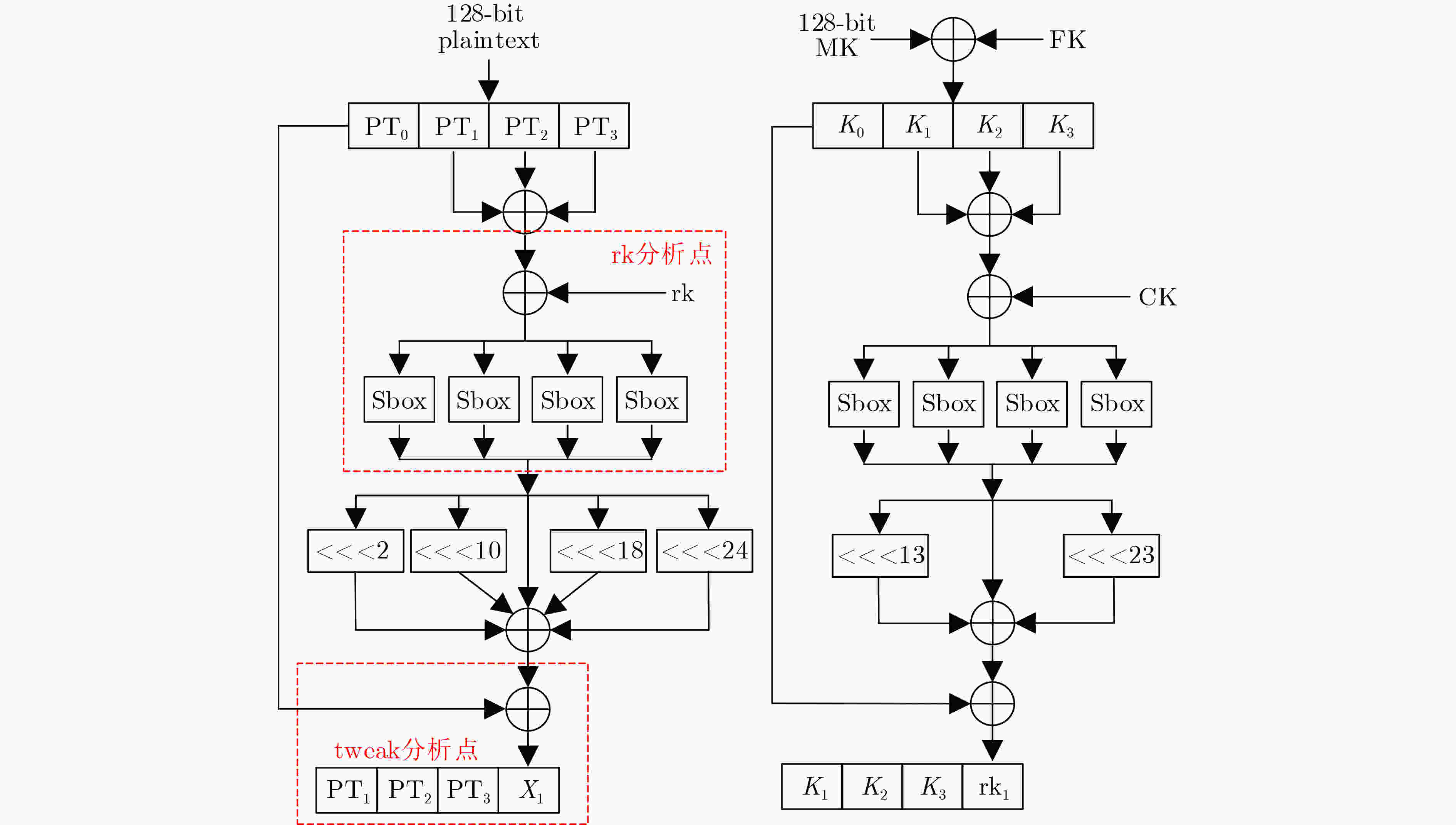
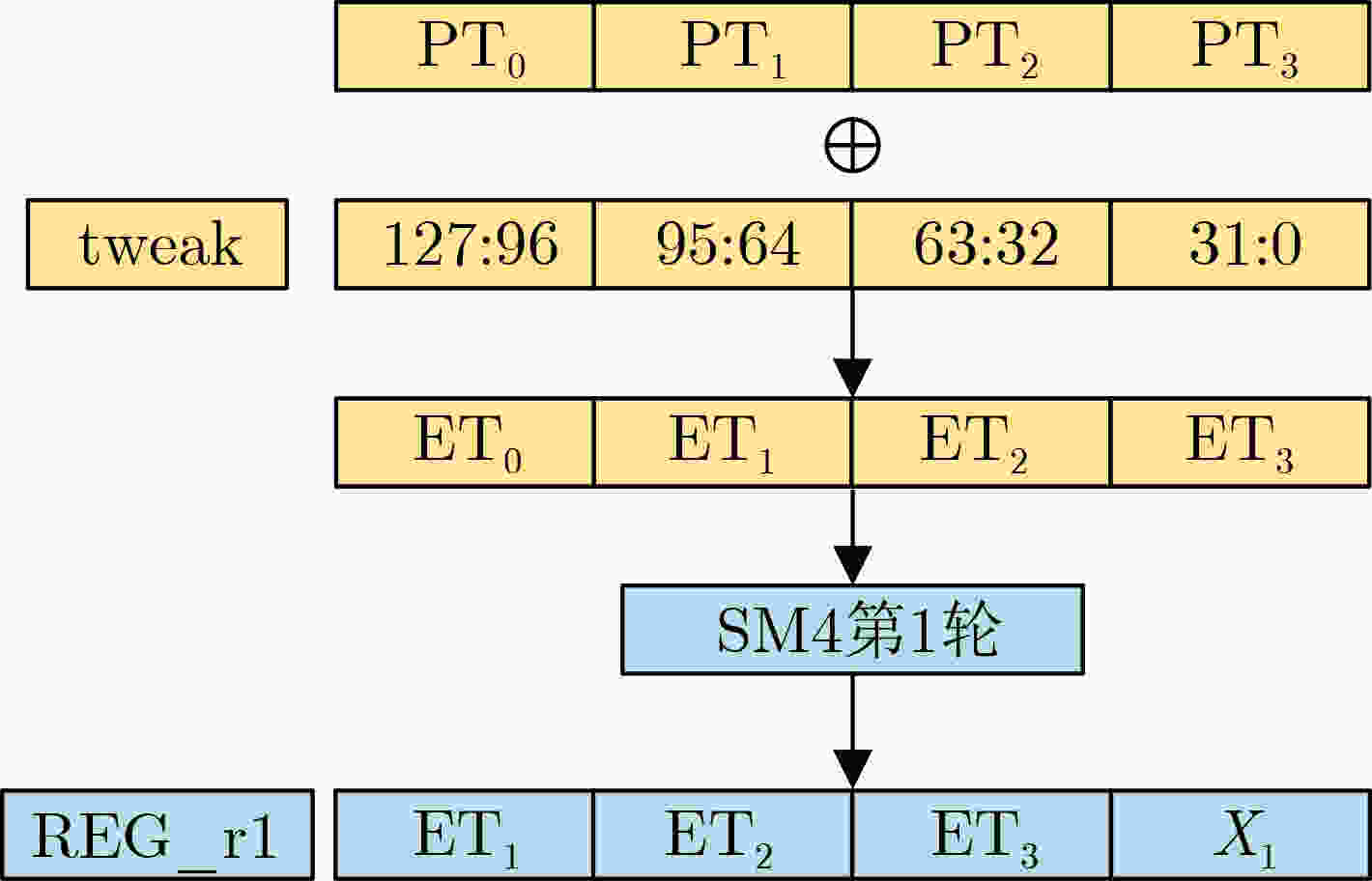
Input: 128-bit PT Output: $ {\text{twea}}{{\text{k}}_0}\left[ {95:0} \right] $ 1: $ {\text{ET}} = {\text{PT}} \oplus {\text{twea}}{{\text{k}}_0} $ 2: $ {X_1} = {\mathrm{{F}}} \_{\mathrm{function}}\left( {{\text{ET}},{\text{r}}{{\text{k}}_1}} \right) $ 3: $ {\bf{PowerTrace1}} = {{\mathrm{HW}}} \left( {{\text{reg\_round1}} \leftarrow \{ {\text{PT}}[95:0],{X_4}\} } \right) $ //采集功耗数据并生成reg_round1保存数据的汉明重量,作为
分析数据集PowerTrace14: $ {\text{twea}}{{\text{k}}_0}\left[ {95:0} \right] = \max ({{\mathrm{correlation}}} ({\bf{PowerTrace1}},{\text{PT}})) $ 2 tweak0前32比特分析
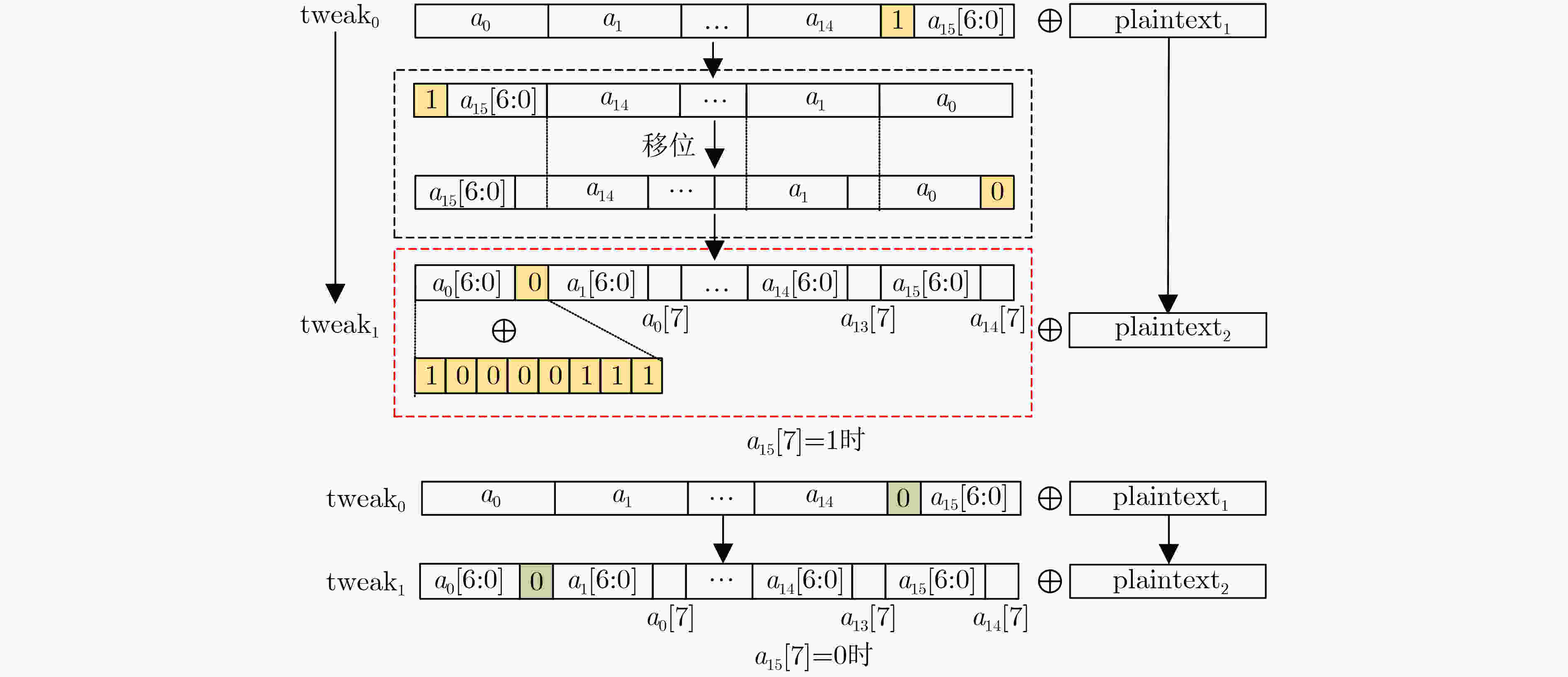
Input: 128-bit $ {\text{P}}{{\text{T}}_0} $ Output: $ {\text{twea}}{{\text{k}}_0}\left[ {127:96} \right] $ 1: $ {\text{E}}{{\text{T}}_0} = {\text{P}}{{\text{T}}_0} \oplus {\text{twea}}{{\text{k}}_0} $ 2: $ {X_{1,0}} = {{\mathrm{F}}} \_{\mathrm{function}}\left( {{\text{E}}{{\text{T}}_0},{\text{r}}{{\text{k}}_1}} \right) $ 3: for i in range(1,32): 4: if ($ {\text{twea}}{{\text{k}}_i}\left[ {127} \right] = = 0 $) then 5: $ {\text{twea}}{{\text{k}}_i} = {\text{twea}}{{\text{k}}_{i - 1}} \lt \lt \lt 1 $ 6: else then 7: $ {\text{twea}}{{\text{k}}_i} = ({\text{twea}}{{\text{k}}_{i - 1}} \lt \lt \lt 1) \oplus {\text{0x}}87 $ 8: if ($ {\text{P}}{{\text{T}}_i}\left[ {127} \right] = = 0 $) then 9: $ {\text{P}}{{\text{T}}_i} = {\text{P}}{{\text{T}}_{i - 1}} \lt \lt \lt 1 $ 10: else then 11: $ {\text{P}}{{\text{T}}_i} = ({\text{P}}{{\text{T}}_{i - 1}} \lt \lt \lt 1) \oplus {\text{0x}}87 $ 12: $ {\text{E}}{{\text{T}}_i} = {\text{P}}{{\text{T}}_i} \oplus {\text{twea}}{{\text{k}}_i} $ 13: $ {X_{1,i}} = {{\mathrm{F}}} \_{\mathrm{function}}\left( {{\text{E}}{{\text{T}}_i},{\text{r}}{{\text{k}}_1}} \right) $ 14: $ {\bf{PowerTrace}}2=\text{HD}(\{{\text{ET}}_{i-1}[95:0],{X}_{1,i\text{-1}}\}, $
$\{{\text{ET}}_{i}[95:0],{X}_{1,i}\}) $//采集功耗数据并生成寄存器内存储值变化的汉明距离,作为分
析数据集PowerTrace215: $ {\text{twea}}{{\text{k}}_0}\left[ {127:96} \right] = \max ({{\mathrm{correlation}}} $
$({\bf{PowerTrace}}2,{\text{PT}})) $3 Key1分析
Input: 128-bit PT Output: $ {\text{Ke}}{{\text{y}}_1} $ 1: $ {\text{ET}} = {\text{PT}} \oplus {\text{twea}}{{\text{k}}_0} $ 2: $ {\bf{PowerTrace}}3 = {{\mathrm{HW}}} ( {\text{Sbox}}\{ {\text{ET}}\left[ {95:64} \right] \oplus {\text{ET}}\left[ {63:32} \right] $
$ \oplus {\text{ET}}\left[ {31:0} \right] \oplus {\text{r}}{{\text{k}}_1}\} ) $//采集功耗数据并生成Sbox输出值的汉明重量,作为分析数据
集PowerTrace33: $ {\bf{grk}} = \max ({{\mathrm{correlation}}} ({\bf{PowerTrace3}},{\text{PT}})) $ //根据数据集计算相关性最大的rk值,作为grk(guess round
key)4: $ {\text{Ke}}{{\text{y}}_1} = Key\_{\exp ^{ - 1}}({\bf{grk}}) $ //由密钥扩展算法的逆映射计算密钥Key1值 -
[1] IEEE. IEEE Std 1619–2007 IEEE standard for cryptographic protection of data on block-oriented storage devices[S]. New York: IEEE, 2008. doi: 10.1109/IEEESTD.2008.4493450. [2] LISKOV M, RIVEST R L, and WAGNER D. Tweakable block ciphers[J]. Journal of Cryptology, 2011, 24(3): 588–613. doi: 10.1007/s00145-010-9073-y. [3] 王永娟, 樊昊鹏, 代政一, 等. 侧信道攻击与防御技术研究进展[J]. 计算机学报, 2023, 46(1): 202–228. doi: 10.11897/SP.J.1016.2023.00202.WANG Yongjuan, FAN Haopeng, DAI Zhengyi, et al. Advances in side channel attacks and countermeasures[J]. Chinese Journal of Computers, 2023, 46(1): 202–228. doi: 10.11897/SP.J.1016.2023.00202. [4] JIN Xin, FENG Junhao, and HUANG Boyang. Side channel attack on sm4 algorithm with deep learning-based analysis[C]. 2022 IEEE International Conference on Advances in Electrical Engineering and Computer Applications (AEECA), Dalian, China, 2022: 749–752. doi: 10.1109/AEECA55500.2022.9919093. [5] UNTERLUGGAUER T and MANGARD S. Exploiting the physical disparity: Side-channel attacks on memory encryption[C]. The 7th International Workshop on Constructive Side-Channel Analysis and Secure Design, Graz, Austria, 2016: 3–18. doi: 10.1007/978-3-319-43283-0_1. [6] LUO Chao, FEI Yunsi, and DING A A. Side-channel power analysis of XTS-AES[C]. Proceedings of Design, Automation & Test in Europe Conference & Exhibition (DATE), Lausanne, Switzerland, 2017: 1330–1335. doi: 10.23919/DATE.2017.7927199. [7] LUO Chao, FEI Yunsi, DING A A, et al. Comprehensive side-channel power analysis of XTS-AES[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2019, 38(12): 2191–2200. doi: 10.1109/TCAD.2018.2878171. [8] TRAUTMANN J, KRÜGER P, BECHER A, et al. Design, calibration, and evaluation of real-time waveform matching on an FPGA-based digitizer at 10 GS/s[J]. ACM Transactions on Reconfigurable Technology and Systems, 2024, 17(2): 24. doi: 10.1145/3635719. [9] 朱圆. 抗旁路攻击的高性能小面积XTS-SM4密码电路设计[D]. [硕士论文]. 南京航空航天大学, 2018.ZHU Yuan. Design of high-performance and small-area XTS-SM4 cipher circuit against side-channel attack[D]. [Master dissertation], Nanjing University of Aeronautics and Astronautics, 2018. [10] AN S and SEO S C. Designing a new XTS-AES parallel optimization implementation technique for fast file encryption[J]. IEEE Access, 2022, 10: 25349–25357. doi: 10.1109/ACCESS.2022.3155810. [11] DIFFIE W and LEDIN G. SMS4 encryption algorithm for wireless networks[J]. Cryptology Eprint Archive, 2008, 329. [12] 李子磊, 刘政林, 霍文捷, 等. 高吞吐率XTS-AES加密算法的硬件实现[J]. 微电子学与计算机, 2011, 28(4): 95–98,102. doi: 10.19304/j.cnki.issn1000-7180.2011.04.024.LI Zilei, LIU Zhenglin, and HUO Wenjie, et al. A high-throughput hardware implementation of XTS-AES encryption algorithm[J]. Microelectronics & Computer, 2011, 28(4): 95–98,102. doi: 10.19304/j.cnki.issn1000-7180.2011.04.024. [13] ZHENG Liang, LI Changting, LIU Zongbin, et al. Implementation of high throughput XTS-SM4 module for data storage devices[C]. The 14th International Conference, SecureComm 2018 on Security and Privacy in Communication Networks, Singapore, Singapore, 2018: 271–290. doi: 10.1007/978-3-030-01704-0_15. [14] KOCHER P, JAFFE J, and JUN B. Differential power analysis[C]. The 19th Annual International Cryptology Conference on Advances in Cryptology. Santa Barbara, USA, 1999: 388–397. doi: 10.1007/3-540-48405-1_25. [15] 安聪. 基于AES加密算法的侧信道攻击的研究[D]. [硕士论文], 南京邮电大学, 2023. doi: 10.27251/d.cnki.gnjdc.2022.001262.AN Cong. Research on side channel attack based on AES encryption algorithms[D]. [Master dissertation], Nanjing University of Posts and Telecommunications, 2023. doi: 10.27251/d.cnki.gnjdc.2022.001262. [16] SHAN Weijun, WANG Lihui, LI Qing, et al. A chosen-plaintext method of CPA on SM4 block cipher[C]. 2014 Tenth International Conference on Computational Intelligence and Security, Kunming, China, 2014: 363–366. doi: 10.1109/CIS.2014.57. [17] ZHAO Cheng, LI Xiuying, JIN Jifang, et al. Two-point joint CPA attacks against SM4 algorithm[C]. 2019 IEEE 11th International Conference on Communication Software and Networks (ICCSN), Chongqing, China, 2019: 826–829. doi: 10.1109/ICCSN.2019.8905348. -





 下载:
下载:




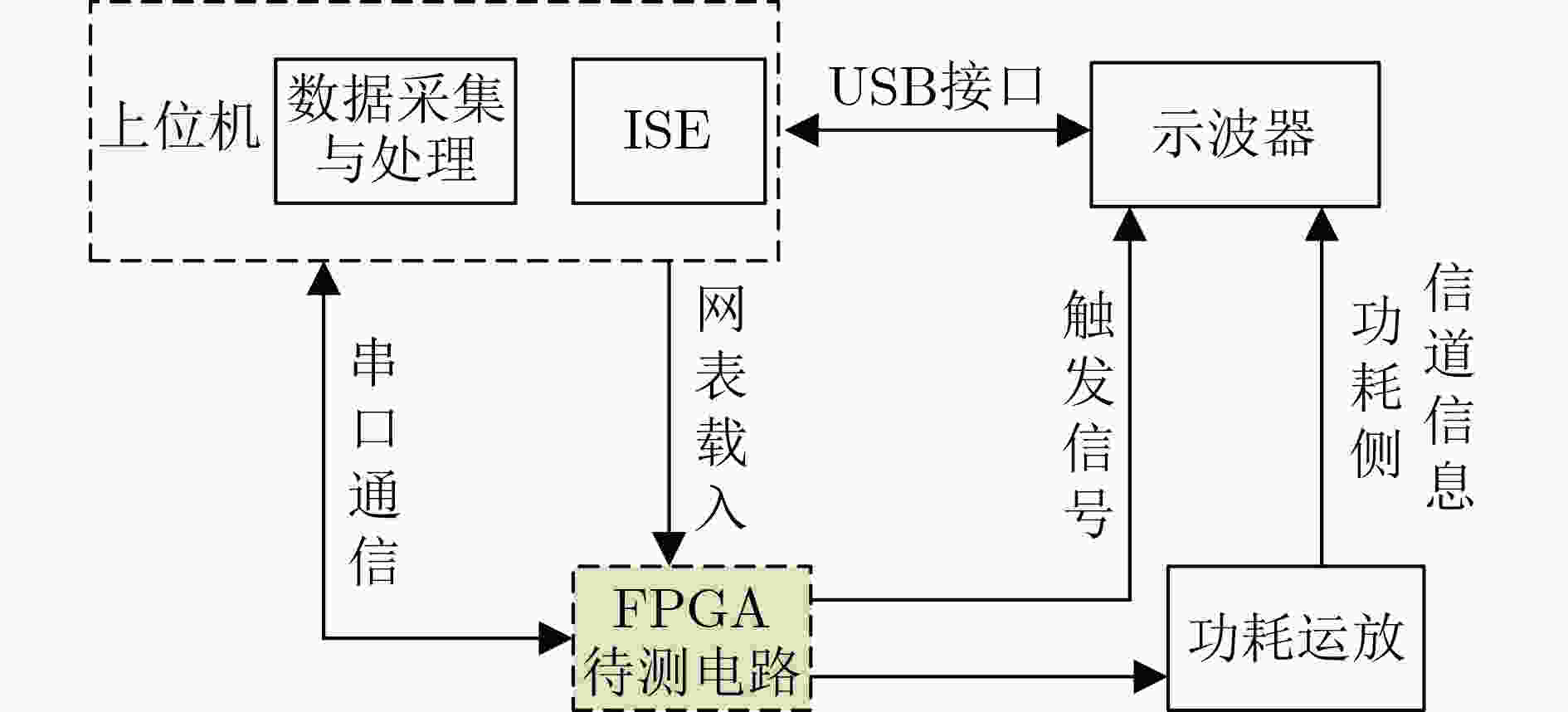
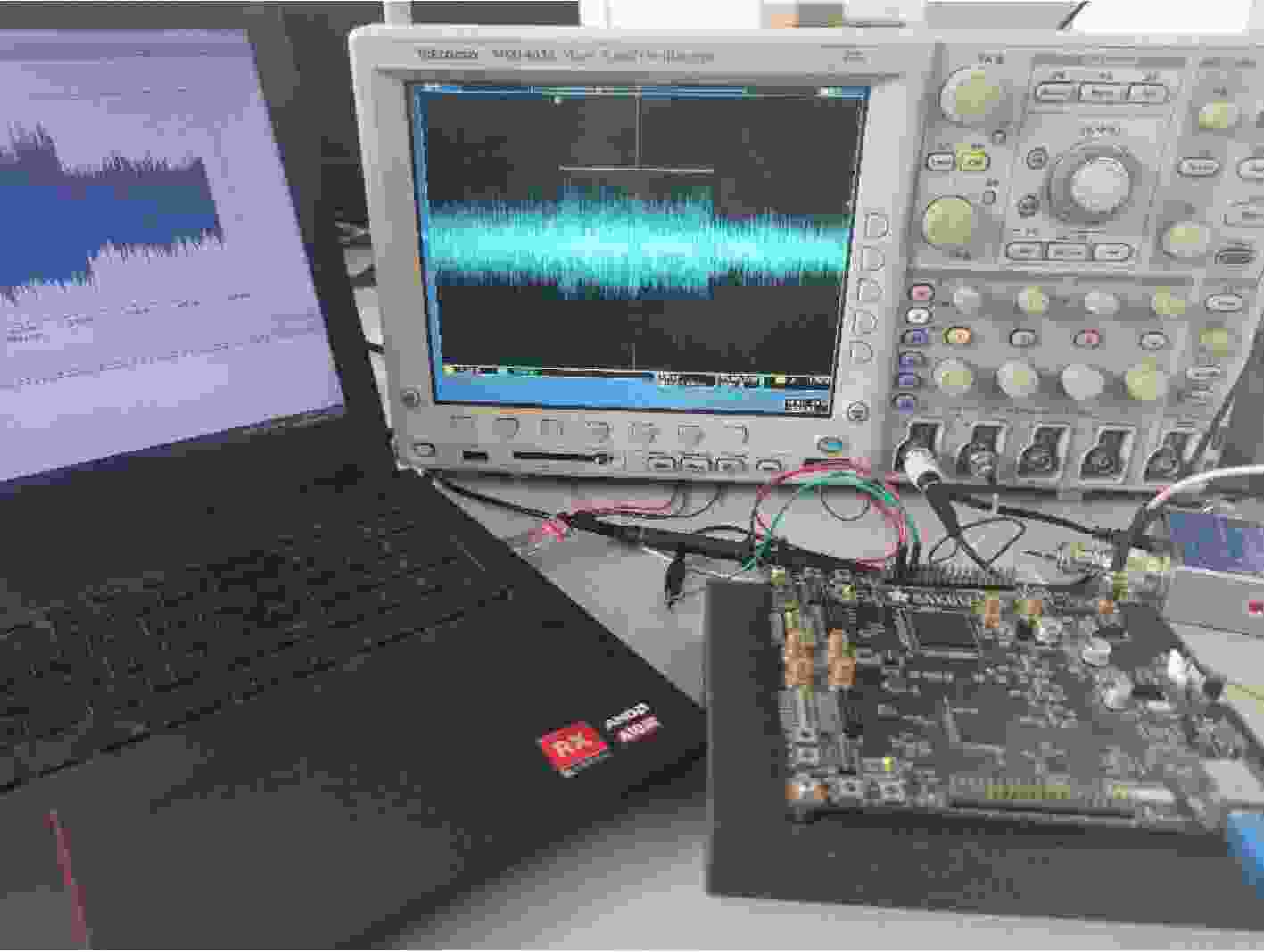
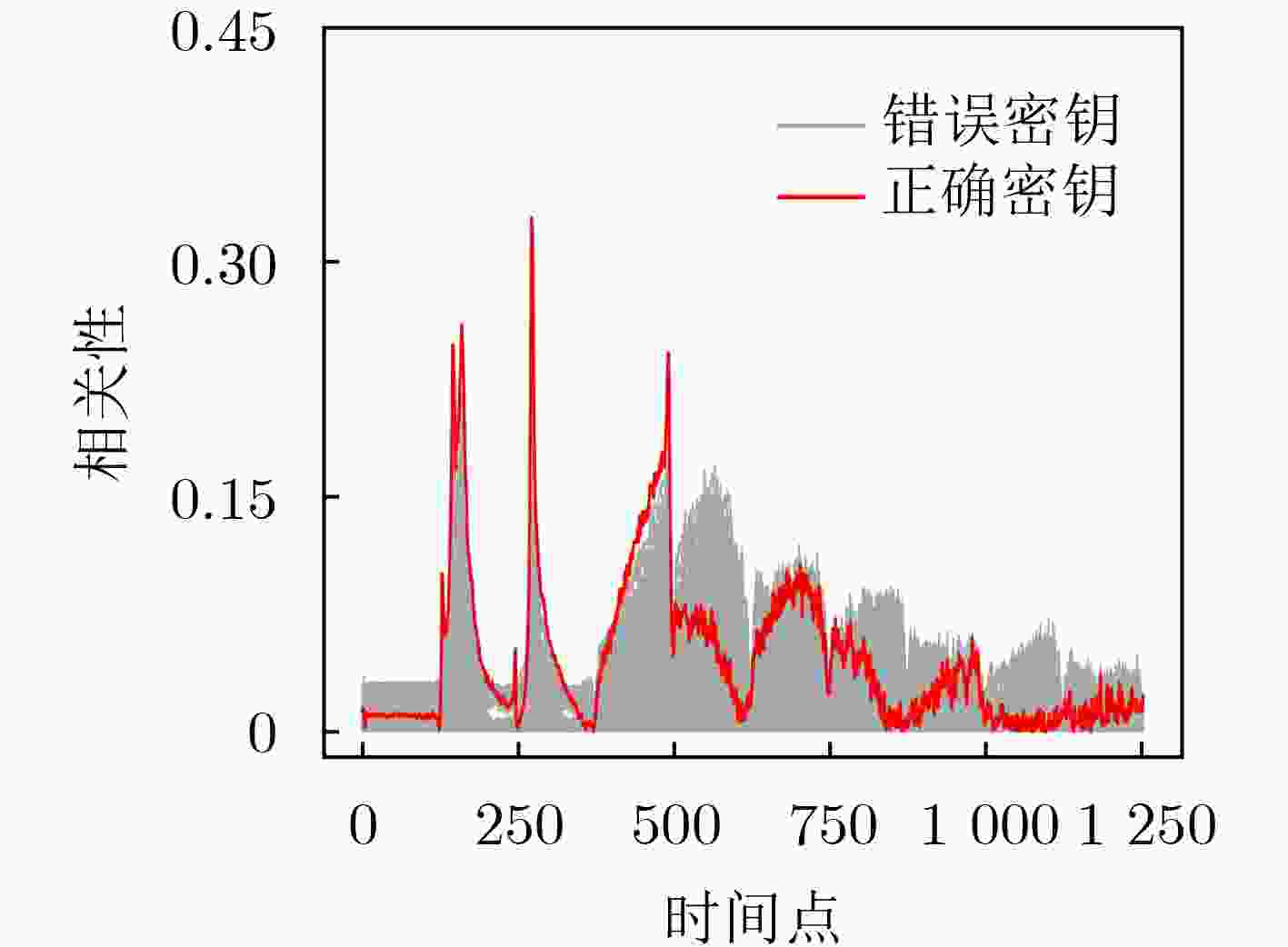


 下载:
下载:
