Website Fingerprinting Attacks and Defenses on Tor: A Survey
-
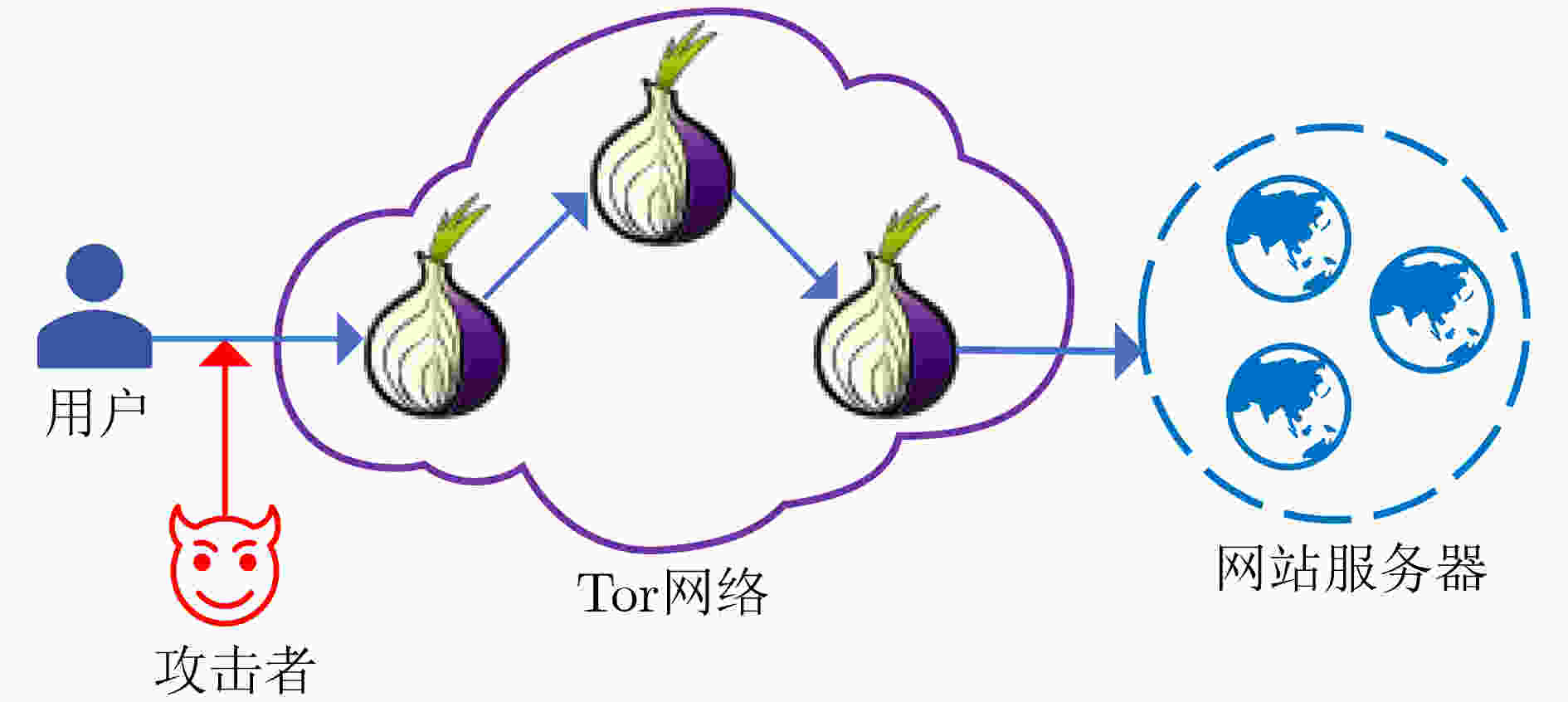
摘要: 以洋葱路由器(Tor)为代表的匿名网络是目前使用最广泛的加密通信网络之一,违法分子利用加密网络以掩盖其违法行为,给网络监管和网络安全带来极大的挑战。网站指纹攻击技术的出现使得对加密流量的分析成为可能,监管者利用数据包方向等信息对Tor流量进行解密,推断用户正在访问的网页。该文对Tor网站指纹攻击与防御方法进行了调研和分析。首先,对Tor网站指纹攻击的相关技术进行总结与比较,重点分析基于传统机器学习和深度学习的Tor网站指纹攻击;其次,对目前多种防御方法进行全面调研和分析;针对现有Tor网站指纹攻击方法存在的局限性进行分析和总结,展望未来发展方向和前景。Abstract: The anonymity network represented by The onion router(Tor) is one of the most widely used encrypted communication networks, criminals utilize encrypted networks to conceal their illegal activities, posing significant challenges to network regulation and cybersecurity. The emergence of website fingerprinting attack has made the analysis of encrypted traffic possible, enabling supervisors to identify Tor traffic and infer the web pages being visited by users by utilizing features such as packet direction and so on. In this paper, a wide survey and analysis of website fingerprinting attack and defense methods on Tor are conducted. Firstly, relevant techniques of website fingerprinting attacks on Tor are summarized and compared. The emphasis is placed on website fingerprinting attacks based on traditional machine learning and deep learning technologies. Secondly, a comprehensive survey and analysis of various existing defense methods are conducted. The limitations in the field of website fingerprinting attack methods on Tor are analyzed and summarized, and the future development directions and prospects are looked forward to.
-
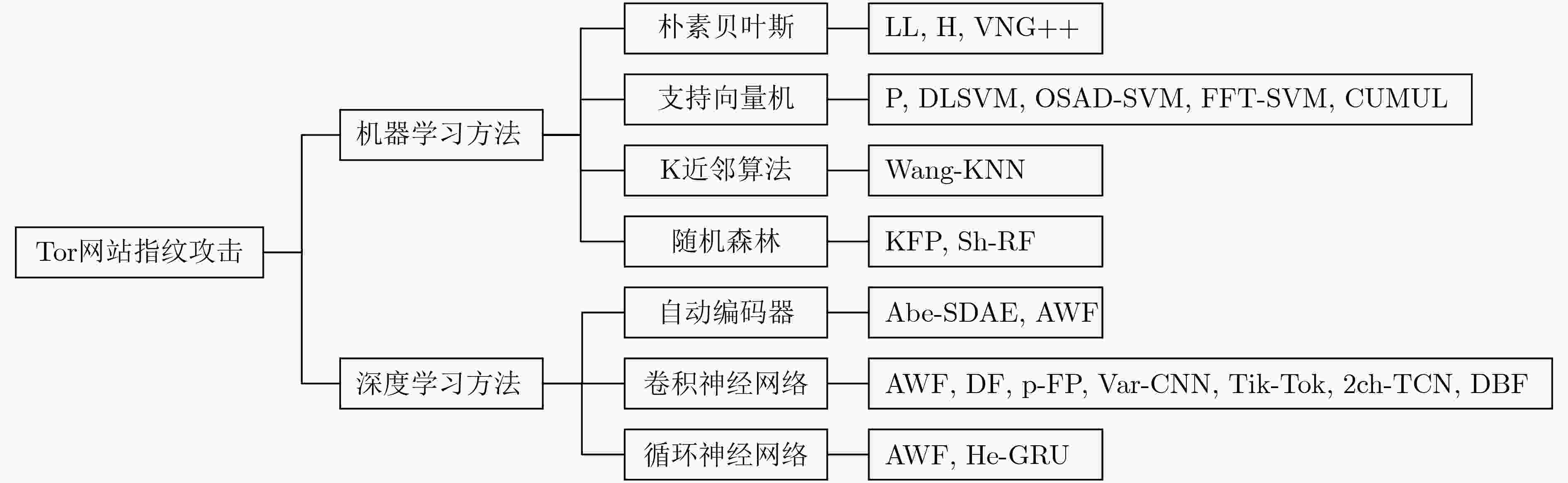
表 1 基于传统机器学习的Tor网站指纹攻击模型比较
分类器 模型 数据单元 特征 封闭世界 开放世界 数据集规模 准确率(%) 数据集规模 TPR(%) FPR(%) H[10] MNB TCP/IP 带方向包长及计数 775×4 2.96 P[11] SVM TCP/IP 带方向包长及计数等 775×20 54.61 4 000×1 73.00 0.05 DLSVM[15] SVM TCP/IP 数据包总数 100×40 83.70 OSAD-SVM[12] SVM Cell Cell方向 100×40 91.00 860×1 96.90 0.20 FFT-SVM[16] SVM TCP/IP 数据包大小、方向 100×40 >95.00 CUMUL[17] SVM Cell Cell大小、方向、顺序 100×90 91.38 9 000×1 96.64 9.61 Wang-KNN[18] KNN Cell 数据包长度等3 736个特征 100×90 91.00 5 000×1 85.00 0.60 KFP[19] RF, KNN TCP/IP 数据包统计特征 55×100+30×80 91.00 30×80+16 000×1 81.00 0.02 注:分类器命名规则采用已发表文献中使用的名称,若无统一名称,则根据作者名称的首部两个字符结合分类器类型自拟。 表 2 基于深度学习的Tor网站指纹攻击模型比较(%)
分类器 模型 数据单元 特征 数据集 封闭世界性能 开放世界性能 准确率 TPR FPR Abe-SDAE[23] SDAE Cell Cell方向 Wang16 88.00 86.00 2.00 AWF_SDAE[24] SDAE Cell Cell方向 Rimmer18 94.25 71.30 3.40 AWF_CNN[24] CNN Cell Cell方向 Rimmer18 91.79 70.94 3.82 AWF_LSTM[24] LSTM Cell Cell方向 Rimmer18 88.04 53.39 3.67 p-FP_MLP[25] MLP Cell Cell序列、Burst WTT 90.00 1.00 p-FP_CNN[25] CNN Cell Cell序列、Burst WTT 94.00 2.00 DF[13] CNN Cell Cell方向 Sirinam18 98.30 95.70 0.70 Var-CNN[26] CNN Cell Cell方向、时间戳 Rimmer18 98.80 98.01 0.36 Tik-Tok[27] CNN TCP/IP、TLS、Cell Burst、原始时间序列 Sirinam18 98.40 94.00 DBF[28] CNN Cell Cell方向、Burst Rimmer18 98.31 98.44 1.70 DBF[28] CNN Cell Cell方向、Burst Sirinam18 98.77 99.00 6.76 DBF[28] CNN Cell Cell方向、Burst Hayes16 70.60 68.42 0.57 2ch-TCN[29] CNN Cell Cell方向、时间戳 Wang14 93.73 WF-Transformer[30] Transformer Cell Cell方向、时序特征 Sirinam18 99.10 96.90 0.70 He-GRU[31] ResNet, GRU Cell Cell方向 Rimmer18 99.85 84.25 表 3 单标签Tor网站指纹攻击常用数据集
数据集名称 数据集规模 研究方法关联 封闭世界 开放世界 Cai12[15] 100×40 DLSVM, FFT-SVM Wang13[12] 100×40 860×1 OSAD-SVM, FFT-SVM Wang14[18] 100×90 9 000×1 Wang-KNN, TF, AdaWFPA, 2ch-TCN Wang16[36] 100×40 5 000×1 Abe-SDAE, p-FP ALEXA100[17] 100×40 860×1 CUMUL, Sh-RF Hayes16[19] 55×100+30×80 100 000×1 KFP, DBF Rimmer18[24] 900×2 500 400 000×1 AWF, Var-CNN, TF, 2ch-TCN, DBF, He-GRU, snWF Sirinam18[13] 95×1 000 40 716×1 DF, Tik-Tok, TF, DBF, WF-Transformer 表 4 随机化防御方法比较
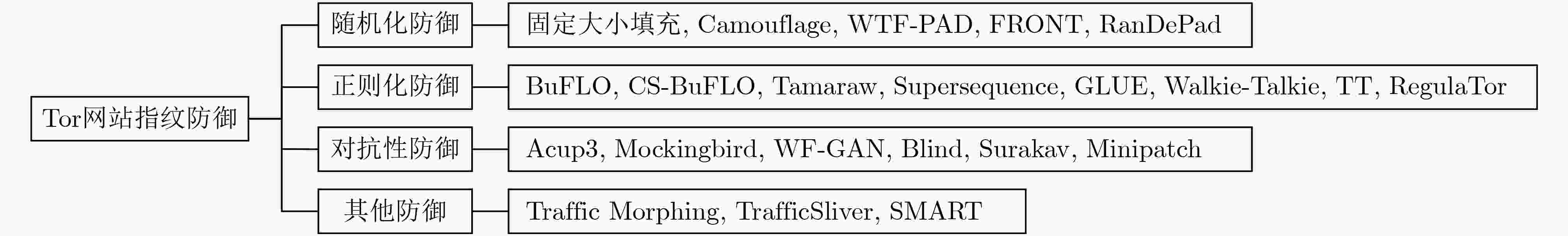
防御名称 防御效果 优点 缺点 分类器模型 准确率变化(%) WTF-PAD[37] P 55.00→15.33 轻量级防御,无通信延迟 混淆时间特征的能力有限 DLSVM 83.70→23.00 FRONT[14] Wang-KNN 83.18→41.22 轻量级防御,专注于混淆跟踪前端,随机化虚拟数据包的数量和分布,无通信延迟 混淆时间特征的能力有限 CUMUL 64.22→11.97 KFP 94.38→71.19 DF 91.12→34.88 Camouflage[11] P 55.00→3.00 无需对匿名网络进行任何修改,易于实施 对部分页面仍然无法提供有效保护 RanDePad[38] KFP
CUMUL
DF89.98→54.15 具备低且可控的带宽开销 未设计延迟控制方案 90.77→50.39 94.57→62.40 表 5 正则化防御方法比较
防御名称 防御效果 优点 缺点 分类器模型 准确率变化(%) BuFLO[20] H 2.96→0.80 严格限制攻击者可利用的特征空间 效率极低,粗粒度特征仍然会泄露网站有关信息 P 54.61→27.30 CS-BuFLO[40] P 54.61→23.40 具有拥塞敏感和自适应速率等功能,减少带宽对BuFLO进行改进以隐藏最重要的流量特征,
开销可调节延迟较高 DLSVM 83.70→<30.00 Tamaraw[41] 重量级防御,延迟较高 Supersequence[18] Wang-KNN 91.00→6.80 可得到最优防御的输出包序列 需要先验知识,选择最短公共超序列问题面临较大计算复杂度 GLUE[14] Wang-KNN 83.18→<5.00 攻击者需要对页面进行分割,难度较大。用户可根据选择定制开销 延迟较高 CUMUL 64.22→<5.00 KFP 94.38→<5.00 DF 91.12→<5.00 Walkie-Talkie[42] P 81.00→44.00 带宽可调节,灵活且开销极低 前提需要知道用户将要访问网页的一些信息。需要修改浏览器加载网页的
方式,部署困难DLSVM 94.00→19.00 OSAD-SVM 97.00→25.00 Wang-KNN 95.00→28.00 CUMUL 64.00→20.00 KFP 86.00→41.00 Tik-Tok 97.00→25.40 带宽开销最小,且不需要额外的基础设施或其他跟踪知识 需要延迟数据传输 RegulaTor[43] DF 98.40→19.60 CUMUL 97.20→16.30 表 6 对抗性防御方法比较
防御名称 防御效果 优点 缺点 分类器模型 准确率变化(%) Mockingbird[46] DF 97.00→38.00 限制对抗性训练的有效性 需要提前了解完整的流量突发
序列,实时性较差,部署性较差Var-CNN 98.00→30.00 CUMUL 93.00→20.00 KFP 85.00→26.00 Wang-KNN 86.00→12.00 WF-GAN[47] DF 90.00(扰动成功率) 同时具备无针对性和有针对性的防御能力 需要提前了解完整的流量突发序列,部署性较差 Surakav[48] KFP 73.62→0.01 采用多种发送模式,实时灵活调整,
开销较小产生一定程度的拥塞,
影响数据包调度CUMUL 74.23→2.74 DF 96.24→8.14 Tik-Tok 96.68→6.28 Blind[49] DF 92.00→1.00 能够有效防御盲目对抗性攻击 模型训练时间较长,无法扩展到
更大的模型Var-CNN 93.00→1.40 Minipatch[50] AWF 83.60(扰动成功率) 带宽消耗更低,防御性能更好 不能防御使用时间特征的网指纹
攻击模型DF 60.90(扰动成功率) Var-CNN 70.50(扰动成功率) -
[1] DINGLEDINE R, MATHEWSON N, and SYVERSON P F. Tor: The second-generation onion router[C]. The 13th USENIX Security Symposium, San Diego, USA, 2004: 303–320. [2] KARUNANAYAKE I, AHMED N, MALANEY R, et al. De-anonymisation attacks on Tor: A survey[J]. IEEE Communications Surveys & Tutorials, 2021, 23(4): 2324–2350. doi: 10.1109/COMST.2021.3093615. [3] 孙学良, 黄安欣, 罗夏朴, 等. 针对Tor的网页指纹识别研究综述[J]. 计算机研究与发展, 2021, 58(8): 1773–1788. doi: 10.7544/issn1000-1239.2021.20200498.SUN Xueliang, HUANG Anxin, LUO Xiapu, et al. Webpage fingerprinting identification on Tor: A survey[J]. Journal of Computer Research and Development, 2021, 58(8): 1773–1788. doi: 10.7544/issn1000-1239.2021.20200498. [4] 邹鸿程, 苏金树, 魏子令, 等. 网站指纹识别与防御研究综述[J]. 计算机学报, 2022, 45(10): 2243–2278. doi: 10.11897/SP.J.1016.2022.02243.ZOU Hongcheng, SU Jinshu, WEI Ziling, et al. A review of the research of website fingerprinting identification and defense[J]. Chinese Journal of Computers, 2022, 45(10): 2243–2278. doi: 10.11897/SP.J.1016.2022.02243. [5] SHEN Meng, YE Ke, LIU Xingtong, et al. Machine learning-powered encrypted network traffic analysis: A comprehensive survey[J]. IEEE Communications Surveys & Tutorials, 2023, 25(1): 791–824. doi: 10.1109/COMST.2022.3208196. [6] WAGNER D and SCHNEIER B. Analysis of the SSL 3.0 protocol[C]. The 2nd USENIX Workshop on Electronic Commerce, Oakland, USA, 1996: 4. doi: 10.5555/1267167.1267171. [7] HINTZ A. Fingerprinting websites using traffic analysis[C]. The 2nd International Workshop on Privacy Enhancing Technologies, San Francisco, USA, 2003: 171–178. doi: 10.1007/3-540-36467-6_13. [8] LIBERATORE M and LEVINE B N. Inferring the source of encrypted HTTP connections[C]. The 13th ACM Conference on Computer and Communications Security, Alexandria, USA, 2006: 255–263. doi: 10.1145/1180405.1180437. [9] BISSIAS G D, LIBERATORE M, JENSEN D, et al. Privacy vulnerabilities in encrypted HTTP streams[C]. The 5th International Workshop on Privacy Enhancing Technologies, Cavtat, Croatia, 2006: 1–11. doi: 10.1007/11767831_1. [10] HERRMANN D, WENDOLSKY R, and FEDERRATH H. Website fingerprinting: Attacking popular privacy enhancing technologies with the multinomial naïve-Bayes classifier[C]. The ACM Workshop on Cloud Computing Security, Chicago, USA, 2009: 31–42. doi: 10.1145/1655008.1655013. [11] PANCHENKO A, NIESSEN L, ZINNEN A, et al. Website fingerprinting in onion routing based anonymization networks[C]. The 10th Annual ACM Workshop on Privacy in the Electronic Society, Chicago, USA, 2011: 103–114. doi: 10.1145/2046556.2046570. [12] WANG Tao and GOLDBERG I. Improved website fingerprinting on tor[C]. The 12th ACM Workshop on Privacy in the Electronic Society, Berlin, Germany, 2013: 201–212. doi: 10.1145/2517840.2517851. [13] SIRINAM P, IMANI M, JUAREZ M, et al. Deep fingerprinting: Undermining website fingerprinting defenses with deep learning[C]. The 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, Canada, 2018: 1928–1943. doi: 10.1145/3243734.3243768. [14] GONG Jiajun and WANG Tao. Zero-delay lightweight defenses against website fingerprinting[C]. The 29th USENIX Conference on Security Symposium, Berkley, USA, 2020: 41. doi: 10.5555/3489212.3489253. [15] CAI Xiang, ZHANG Xincheng, JOSHI B, et al. Touching from a distance: Website fingerprinting attacks and defenses[C]. The ACM Conference on Computer and Communications Security, Raleigh, USA, 2012: 605–616. doi: 10.1145/2382196.2382260. [16] JAHANI H and JALILI S. A novel passive website fingerprinting attack on tor using fast Fourier transform[J]. Computer Communications, 2016, 96: 43–51. doi: 10.1016/j.comcom.2016.05.019. [17] PANCHENKO A, LANZE F, PENNEKAMP J, et al. Website fingerprinting at internet scale[C]. The 23rd Annual Network and Distributed System Security Symposium, San Diego, USA, 2016: 1–15. [18] WANG Tao, CAI Xiang, NITHYANAND R, et al. Effective attacks and provable defenses for website fingerprinting[C]. The 23rd USENIX Conference on Security Symposium, San Diego, USA, 2014: 143–157. doi: 10.5555/2671225.2671235. [19] HAYES J and DANEZIS G. K-fingerprinting: A robust scalable website fingerprinting technique[C]. The 25th USENIX Conference on Security Symposium, Austin, USA, 2016: 1187–1203. doi: 10.5555/3241094.3241186. [20] DYER K P, COULL S E, RISTENPART T, et al. Peek-a-boo, I still see you: Why efficient traffic analysis countermeasures fail[C]. The IEEE Symposium on Security and Privacy, San Francisco, USA, 2012: 332–346. doi: 10.1109/SP.2012.28. [21] CHANG C C and LIN C J. LIBSVM: A library for support vector machines[J]. ACM Transactions on Intelligent Systems and Technology, 2011, 2(3): 27. doi: 10.1145/1961189.1961199. [22] SHEN Meng, LIU Yiting, ZHU Liehuang, et al. Optimizing feature selection for efficient encrypted traffic classification: A systematic approach[J]. IEEE Network, 2020, 34(4): 20–27. doi: 10.1109/MNET.011.1900366. [23] ABE K and GOTO S. Fingerprinting attack on Tor anonymity using deep learning[J]. Proceedings of the Asia-Pacific Advanced Network, Hongkong, China, 2016, 42: 15–20. [24] RIMMER V, PREUVENEERS D, JUAREZ M, et al. Automated website fingerprinting through deep learning[C]. The 25th Network and Distributed System Security Symposium, San Diego, USA, 2018. [25] OH S E, SUNKAM S, and HOPPER N. p1-FP: Extraction, classification, and prediction of website fingerprints with deep learning[J]. Proceedings on Privacy Enhancing Technologies, 2019, 2019(3): 191–209. doi: 10.2478/popets-2019-0043. [26] BHAT S, LU D, KWON A, et al. Var-CNN: A data-efficient website fingerprinting attack based on deep learning[J]. Proceedings on Privacy Enhancing Technologies, 2019, 2019(4): 292–310. doi: 10.2478/popets-2019-0070. [27] RAHMAN M S, SIRINAM P, MATHEWS N, et al. Tik-Tok: The utility of packet timing in website fingerprinting attacks[J]. Proceedings on Privacy Enhancing Technologies, 2020, 2020(3): 5–24. doi: 10.2478/popets-2020-0043. [28] 马陈城, 杜学绘, 曹利峰, 等. 基于深度神经网络burst特征分析的网站指纹攻击方法[J]. 计算机研究与发展, 2020, 57(4): 746–766. doi: 10.7544/issn1000-1239.2020.20190860.MA Chencheng, DU Xuehui, CAO Lifeng, et al. Burst-analysis website fingerprinting attack based on deep neural network[J]. Journal of Computer Research and Development, 2020, 57(4): 746–766. doi: 10.7544/issn1000-1239.2020.20190860. [29] WANG Meiqi, LI Yanzeng, WANG Xuebin, et al. 2ch-TCN: A website fingerprinting attack over tor using 2-channel temporal convolutional networks[C]. The IEEE Symposium on Computers and Communications, Rennes, France, 2020: 1–7. doi: 10.1109/ISCC50000.2020.9219717. [30] ZHOU Qiang, WANG Liangmin, ZHU Huijuan, et al. WF-transformer: Learning temporal features for accurate anonymous traffic identification by using transformer networks[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 30–43. doi: 10.1109/TIFS.2023.3318966. [31] HE Xiaomin, WANG Jin, HE Yueying, et al. A deep learning approach for website fingerprinting attack[C]. The 4th International Conference on Computer and Communications, Chengdu, China, 2018: 1419–1423. doi: 10.1109/CompComm.2018.8780755. [32] XU Yixiao, WANG Tao, LI Qi, et al. A multi-tab website fingerprinting attack[C]. The 34th Annual Computer Security Applications Conference, San Juan, USA, 2018: 327–341. doi: 10.1145/3274694.3274697. [33] YIN Qilei, LIU Zhuotao, LI Qi, et al. An automated multi-tab website fingerprinting attack[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(6): 3656–3670. doi: 10.1109/TDSC.2021.3104869. [34] GU Xiaodan, YANG Ming, SONG Bingchen, et al. A practical multi-tab website fingerprinting attack[J]. Journal of Information Security and Applications, 2023, 79: 103627. doi: 10.1016/j.jisa.2023.103627. [35] DENG Xinhao, YIN Qilei, LIU Zhuotao, et al. Robust multi-tab website fingerprinting attacks in the wild[C]. 2023 IEEE Symposium on Security and Privacy, San Francisco, USA, 2023: 1005–1022. doi: 10.1109/SP46215.2023.10179464. [36] WANG Tao and GOLDBERG I. On realistically attacking tor with website fingerprinting[J]. Proceedings on Privacy Enhancing Technologies, 2016, 2016(4): 21–36. doi: 10.1515/popets-2016-0027. [37] JUAREZ M, IMANI M, PERRY M, et al. Toward an efficient website fingerprinting defense[C]. The 21st European Symposium on Research in Computer Security, Heraklion, Greece, 2016: 27–46. doi: 10.1007/978-3-319-45744-4_2. [38] HONG Xueshu, MA Xingkong, LI Shaoyong, et al. A website fingerprint defense technology with low delay and controllable bandwidth[J]. Computer Communications, 2022, 193: 332–345. doi: 10.1016/j.comcom.2022.06.028. [39] LIU Peidong, HE Longtao, and LI Zhoujun. A survey on deep learning for website fingerprinting attacks and defenses[J]. IEEE Access, 2023, 11: 26033–26047. doi: 10.1109/ACCESS.2023.3253559. [40] CAI Xiang, NITHYANAND R, and JOHNSON R. CS-BuFLO: A congestion sensitive website fingerprinting defense[C]. The 13th Workshop on Privacy in the Electronic Society, Scottsdale, USA, 2014: 121–130. doi: 10.1145/2665943.2665949. [41] CAI Xiang, NITHYANAND R, WANG Tao, et al. A systematic approach to developing and evaluating website fingerprinting defenses[C]. The 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, USA, 2014: 227–238. doi: 10.1145/2660267.2660362. [42] WANG Tao and GOLDBERG I. Walkie-talkie: An efficient defense against passive website fingerprinting attacks[C]. The 26th USENIX Conference on Security Symposium, Vancouver, Canada, 2017: 1375–1390. doi: 10.5555/3241189.3241296. [43] HOLLAND J K and HOPPER N. RegulaTor: A straightforward website fingerprinting defense[J]. Proceedings on Privacy Enhancing Technologies, 2022, 2022(2): 344–362. doi: 10.2478/popets-2022-0049. [44] LIANG Jingyuan, YU Chansu, SUH K, et al. Tail time defense against website fingerprinting attacks[J]. IEEE Access, 2022, 10: 18516–18525. doi: 10.1109/ACCESS.2022.3146236. [45] GOODFELLOW I J, SHLENS J, and SZEGEDY C. Explaining and harnessing adversarial examples[C]. The 3rd International Conference on Learning Representations, San Diego, USA, 2015. [46] RAHMAN M S, IMANI M, MATHEWS N, et al. Mockingbird: Defending against deep-learning-based website fingerprinting attacks with adversarial traces[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 1594–1609. doi: 10.1109/TIFS.2020.3039691. [47] HOU Chengshang, GOU Gaopeng, SHI Junzheng, et al. WF-GAN: Fighting back against website fingerprinting attack using adversarial learning[C]. The IEEE Symposium on Computers and Communications, Rennes, France, 2020: 1–7. doi: 10.1109/ISCC50000.2020.9219593. [48] GONG Jiajun, ZHANG Wuqi, ZHANG C, et al. Surakav: Generating realistic traces for a strong website fingerprinting defense[C]. The IEEE Symposium on Security and Privacy, San Francisco, USA, 2022: 1558–1573. doi: 10.1109/SP46214.2022.9833722. [49] NASR M, BAHRAMALI A, and HOUMANSADR A. Defeating DNN-based traffic analysis systems in real-time with blind adversarial perturbations[C]. The 30th USENIX Security Symposium, Vancouver, Canada, 2021: 2705–2722. [50] LI Ding, ZHU Yuefei, CHEN Minghao, et al. Minipatch: Undermining DNN-based website fingerprinting with adversarial patches[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 2437–2451. doi: 10.1109/TIFS.2022.3186743. [51] QIAO Litao, WU Bang, YIN Shuijun, et al. Resisting DNN-based website fingerprinting attacks enhanced by adversarial training[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 5375–5386. doi: 10.1109/TIFS.2023.3304528. [52] GU Xiaodan, SONG Bingchen, LAN Wei, et al. An online website fingerprinting defense based on the non-targeted adversarial patch[J]. Tsinghua Science and Technology, 2023, 28(6): 1148–1159. doi: 10.26599/TST.2023.9010062. [53] GONG Jiajun, ZHANG Wuqi, ZHANG C, et al. WFDefProxy: Real world implementation and evaluation of website fingerprinting defenses[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 1357–1371. doi: 10.1109/TIFS.2023.3327662. [54] XIAO Xi, ZHOU Xiang, YANG Zhenyu, et al. A comprehensive analysis of website fingerprinting defenses on Tor[J]. Computers & Security, 2024, 136: 103577. doi: 10.1016/J.COSE.2023.103577. [55] WRIGHT C V, COULL S E, and MONROSE F. Traffic morphing: An efficient defense against statistical traffic analysis[C]. The 16th Network and Distributed System Security Symposium, San Diego, USA, 2009. [56] DE LA CADENA W, MITSEVA A, HILLER J, et al. TrafficSliver: Fighting website fingerprinting attacks with traffic splitting[C]. The 2020 ACM SIGSAC Conference on Computer and Communications Security, Orlando, USA, 2020: 1971–1985. doi: 10.1145/3372297.3423351. [57] LIU Ling, HU Ning, SHAN Chun, et al. SMART: A lightweight and reliable multi-path transmission model against website fingerprinting attacks[J]. Electronics, 2023, 12(7): 1668. doi: 10.3390/electronics12071668. [58] JUAREZ M, AFROZ S, ACAR G, et al. A critical evaluation of website fingerprinting attacks[C]. The 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, USA, 2014: 263–274. doi: 10.1145/2660267.2660368. [59] AMINUDDIN M A I M, ZAABA Z F, SAMSUDIN A, et al. The rise of website fingerprinting on Tor: Analysis on techniques and assumptions[J]. Journal of Network and Computer Applications, 2023, 212: 103582. doi: 10.1016/j.jnca.2023.103582. [60] Al-NAAMI K, CHANDRA S, MUSTAFA A, et al. Adaptive encrypted traffic fingerprinting with bi-directional dependence[C]. The 32nd Annual Conference on Computer Security Applications, Los Angeles, USA, 2016: 177–188. doi: 10.1145/2991079.2991123. [61] ATTARIAN R and HASHEMI S. Investigating the streaming algorithms usage in website fingerprinting attack against Tor privacy enhancing technology[C]. The 16th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology, Mashhad, Iran, 2019: 33–38. doi: 10.1109/ISCISC48546.2019.8985162. [62] PFAHRINGER B, HOLMES G, and KIRKBY R. New options for hoeffding trees[C]. The 20th Australian Joint Conference on Artificial Intelligence, Gold Coast, Australia, 2007: 90–99. doi: 10.1007/978-3-540-76928-6_11. [63] HULTEN G, SPENCER L, and DOMINGOS P. Mining time-changing data streams[C]. The Seventh ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, San Francisco, USA, 2001: 97–106. doi: 10.1145/502512.502529. [64] OZA N C and RUSSELL S J. Online bagging and boosting[C]. The Eighth International Workshop on Artificial Intelligence and Statistics, Key West, USA, 2001: 229–236. [65] MANAPRAGADA C, WEBB G I, and SALEHI M. Extremely fast decision tree[C]. The 24th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, London, UK, 2018: 1953–1962. doi: 10.1145/3219819.3220005. [66] ATTARIAN R, ABDI L, and HASHEMI S. AdaWFPA: Adaptive online website fingerprinting attack for tor anonymous network: A stream-wise paradigm[J]. Computer Communications, 2019, 148: 74–85. doi: 10.1016/j.comcom.2019.09.008. [67] WANG Yanbin, XU Haitao, GUO Zhenhao, et al. SnWF: Website fingerprinting attack by ensembling the snapshot of deep learning[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 1214–1226. doi: 10.1109/TIFS.2022.3158086. [68] SIRINAM P, MATHEWS N, RAHMAN M S, et al. Triplet fingerprinting: More practical and portable website fingerprinting with N-shot learning[C]. The 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 2019: 1131–1148. doi: 10.1145/3319535.3354217. [69] CHEN Mantun, WANG Yongjun, and ZHU Xiatian. Few-shot website fingerprinting attack with meta-bias learning[J]. Pattern Recognition, 2022, 130: 108739. doi: 10.1016/j.patcog.2022.108739. [70] ZHOU Qiang, WANG Liangmin, ZHU Huijuan, et al. Few-shot website fingerprinting attack with cluster adaptation[J]. Computer Networks, 2023, 229: 109780. doi: 10.1016/j.comnet.2023.109780. [71] CHEN Yongxin, WANG Yongjun, and YANG Luming. SRP: A microscopic look at the composition mechanism of website fingerprinting[J]. Applied Sciences, 2022, 12(15): 7937. doi: 10.3390/app12157937. [72] KARUNANAYAKE I, JIANG Jiaojiao, AHMED N, et al. Exploring uncharted waters of website fingerprinting[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 1840–1854. doi: 10.1109/TIFS.2023.3342607. [73] SHEN Meng, JI Kexin, GAO Zhenbo, et al. Subverting website fingerprinting defenses with robust traffic representation[C]. The 32th USENIX Security Symposium, Anaheim, USA, 2023: 607–624. -





 下载:
下载:


 下载:
下载:
