Detecting and Mapping Framework for Physical Devices Based on Rowhammer Physical Unclonable Function
-
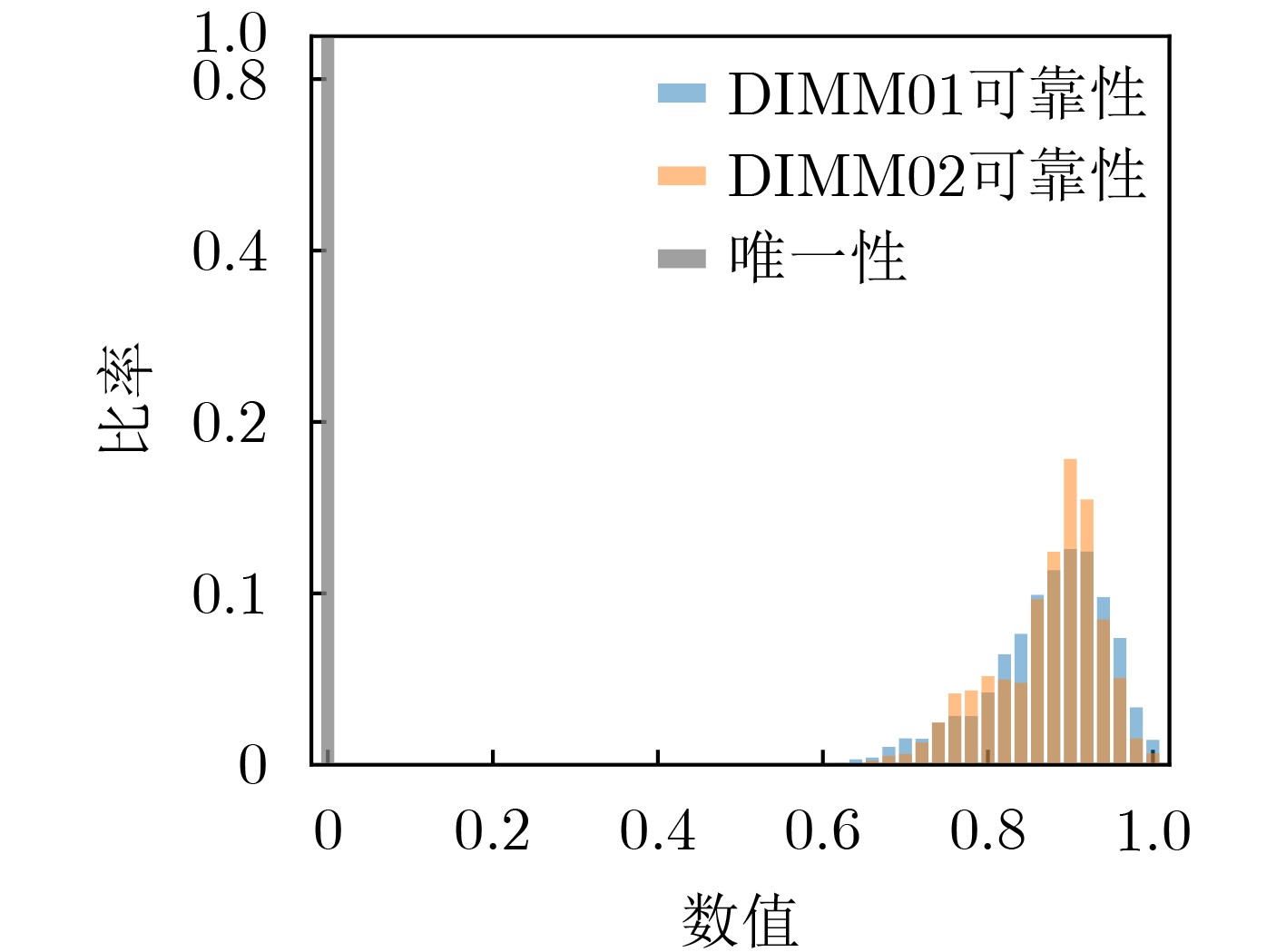
摘要: 网络空间测绘的核心问题是准确识别和动态跟踪设备。然而,随着匿名化技术的发展,设备可以拥有多个IP地址和MAC地址。这使得通过传统的测绘技术将多个虚拟属性映射到同一个物理设备上变得更加困难。该文提出一种基于物理不可克隆函数(PUF)的测绘框架。该框架可以主动检测网络空间中的物理资源,并根据物理指纹构建资源画像来动态跟踪设备。同时,该文提出一种在配备第四代双倍速率(DDR4)内存的个人电脑(PC)上实现基于Rowhammer的动态随机存取存储器物理不可克隆函数(DRAM PUF)的方法。性能评估表明,该方法在PC上提取的Rowhammer PUF的响应是唯一且可靠的,并可以作为设备的唯一物理指纹。实验结果表明,即使目标设备修改了MAC地址、IP地址或重装了操作系统,该文提出的框架仍然可以通过构建一个用于设备匹配的物理指纹数据库,对目标设备进行准确的标识。
-
关键词:
- 网络空间测绘 /
- 物理指纹 /
- 物理不可克隆函数 /
- Rowhammer物理不可克隆函数
Abstract: The core problem of cyberspace mapping is to identify accurately and track dynamically devices. However, with the development of anonymization technology, devices can have multiple IP addresses and MAC addresses. This makes it increasingly difficult to map multiple virtual attributes to the same physical device through traditional mapping techniques. In this paper, a mapping framework based on Physical Unclonable Function (PUF) is proposed which can actively detect physical resources in cyberspace and track dynamically devices based on physical fingerprints to construct resource portraits. Furthermore, a new method is proposed to implement the Rowhammer-based Dynamic Random-Access Memory Physical Unclonable Function (DRAM PUF) on a regular Personal Computer (PC) equipped with Double Data Rate Fourth (DDR4) memory. Performance evaluation shows that the response extracted from the Rowhammer PUF on the PC using the proposed method is unique and reliable, and can be used as a unique physical fingerprint of the device. Experimental results show that even if the target device modifies its MAC address, IP address, or reinstalls operating system, the framework proposed in this paper can still accurately identify the target device by constructing a physical fingerprint database for device matching. -
算法1 Rowhammer PUF查询过程 输入:PUF地址、内存访问模式、数据模式、测量次数 输出:PUF响应 分配所需的内存; while m < 测量次数 do: while b < bank数量 do: 初始化内存访问行和PUF行; end while b < bank数量 do: 快速、重复访问所有的内存访问行; 扫描所有的PUF行并输出比特翻转的位置; end end 表 1 PUF 参数设置
参数 值 PUF地址 行基址 = 0,地址偏移 = 0 内存访问模式 22 sided 数据模式 PUF行 = 0x55,内存访问行 = 0xAA 测量次数 5个bank, 10次测量 表 2 实验1目标设备画像
A1 A2 A3 A4 物理指纹 数据库1 数据库2 数据库3 数据库4 MAC地址 f4:4d:30:d0:f1:32 f4:4d:30:d0:f2:bf f4:4d:30:32:2a:fb f4:4d:30:82:73:91 IP地址 192.168.171.100 192.168.171.122 192.168.171.125 192.168.171.147 端口号 22:sshd 22:sshd 22:sshd; 80:http; 443:https 22:sshd; 3306:mysql 网关 192.168.171.1 192.168.171.1 192.168.171.1 192.168.171.1 内存序列号 M378A1K43
DB2-CVFM378A1K43
DB2-CVFM378A1K43
DB2-CVFM378A1K43
DB2-CVF操作系统版本 Ubuntu 20.04.3 LTS CPU型号 Intel(R) Core(TM) i7-10700 CPU @ 2.90 GHz 表 3 实验2目标设备画像
B1 B2 B3 B4 物理指纹 PUF查询1 PUF查询2 PUF查询3 PUF查询4 MAC地址 c0:c6:f7:cf:08:0e 01:e7:19:da:a2:5c f6:d9:68:a1:88:03 00:86:af:33:84:66 IP地址 192.168.171.100 192.168.171.8 192.168.171.215 192.168.171.216 端口号 22:sshd 22:sshd 22:sshd; 80:http; 443:https 22:sshd; 3306:mysql 网关 192.168.171.1 192.168.171.1 192.168.171.1 192.168.171.1 内存序列号 M378A1K43
DB2-CVFM378A1K43
DB2-CVFM378A1K43
DB2-CVFM378A1K43
DB2-CVF操作系统版本 Ubuntu 18.04.3 LTS CPU型号 Intel(R) Core(TM) i7-10700 CPU @ 2.90 GHz 表 4 实验2与实验1设备之间的$ {\bf{Jaccard}}'$值
${\mathrm{J}\mathrm{a}\mathrm{c}\mathrm{c}\mathrm{a}\mathrm{r}\mathrm{d} }{{' } }$ A1 A2 A3 A4 B1 0.96 0 0 0 B2 0 0 0.94 0 B3 0 0.95 0 0 B4 0 0 0 1 表 5 实验3与实验1设备之间的${\bf{Jaccard}}'$值
${\mathrm{J}\mathrm{a}\mathrm{c}\mathrm{c}\mathrm{a}\mathrm{r}\mathrm{d} }'$ A1 A2 A3 A4 C1 0 0 0 0 C2 0 0 0.96 0 C3 0 0 0 0 C4 0 0 0 1 -
[1] 郭莉, 曹亚男, 苏马婧, 等. 网络空间资源测绘: 概念与技术[J]. 信息安全学报, 2018, 3(4): 1–14. doi: 10.19363/J.cnki.cn10-1380/tn.2018.07.01GUO Li, CAO Ya’nan, SU Majing, et al. Cyberspace resources surveying and mapping: The concepts and technologies[J]. Journal of Cyber Security, 2018, 3(4): 1–14. doi: 10.19363/J.cnki.cn10-1380/tn.2018.07.01 [2] 陈庆, 李晗, 杜跃进, 等. 网络空间测绘技术的实践与思考[J]. 信息通信技术与政策, 2021, 47(8): 30–38. doi: 10.12267/j.issn.2096-5931.2021.08.005CHEN Qing, LI Han, DU Yuejin, et al. Practice and thinking of cyberspace surveying and mapping technology[J]. Information and Communications Technology and Policy, 2021, 47(8): 30–38. doi: 10.12267/j.issn.2096-5931.2021.08.005 [3] HOU Yuanwei, CHEN Xiaoxiao, HAO Yongle, et al. Survey of cyberspace resources scanning and analyzing[C]. The 14th International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS-2020), Lodz, Poland, 2021: 279–291. [4] NMAP. Nmap: The network mapper - free security scanner[EB/OL]. https://nmap.org/, 2023. [5] DURUMERIC Z, WUSTROW E, and HALDERMAN J A. ZMap: Fast internet-wide scanning and its security applications[C]. The 22th USENIX Security Symposium, Washington, USA, 2013: 605–620. [6] GRAHAM R D. MASSCAN: Mass IP port scanner[EB/OL]. https://github.com/robertdavidgraham/masscan, 2023. [7] Shodan. Search engine for the internet of everything[EB/OL]. https://www.shodan.io, 2023. [8] KIM Y, DALY R, KIM J, et al. Flipping bits in memory without accessing them: An experimental study of DRAM disturbance errors[J]. ACM SIGARCH Computer Architecture News, 2014, 42(3): 361–372. doi: 10.1145/2678373.2665726 [9] COJOCAR L, KIM J, PATEL M, et al. Are we susceptible to rowhammer? An end-to-end methodology for cloud providers[C]. 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2020: 712–728. [10] GRUSS D, MAURICE C, and MANGARD S. Rowhammer. js: A remote software-induced fault attack in javascript[C]. 13th International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, San Sebastián, Spain, 2016: 300–321. [11] DE RIDDER F, FRIGO P, VANNACCI E, et al. SMASH: Synchronized many-sided rowhammer attacks from JavaScript[C/OL]. 30th USENIX Security Symposium, 2021: 1001–1018. [12] QIAO Rui and SEABORN M. A new approach for rowhammer attacks[C]. 2016 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, USA, 2016: 161–166. [13] KWONG A, GENKIN D, GRUSS D, et al. RAMBleed: Reading bits in memory without accessing them[C]. 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2020: 695–711. [14] ZHANG Zhi, CHENG Yueqiang, WANG Minghua, et al. SoftTRR: Protect page tables against rowhammer attacks using software-only target row refresh[C]. 2022 USENIX Annual Technical Conference, Carlsbad, USA, 2022: 399–414. [15] PESSL P, GRUSS D, MAURICE C, et al. DRAMA: Exploiting DRAM addressing for cross-CPU attacks[C]. The 25th USENIX Conference on Security Symposium, Austin, USA, 2016: 565–581. [16] WANG Minghua, ZHANG Zhi, CHENG Yueqiang, et al. DRAMDig: A knowledge-assisted tool to uncover DRAM address mapping[C]. 2020 57th ACM/IEEE Design Automation Conference (DAC), San Francisco, USA, 2020: 1–6. [17] GRUSS D, LIPP M, SCHWARZ M, et al. Another flip in the wall of rowhammer defenses[C]. 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2018: 245–261. [18] SAROIU S, WOLMAN A, and COJOCAR L. The price of secrecy: How hiding internal DRAM topologies hurts rowhammer defenses[C]. 2022 IEEE International Reliability Physics Symposium (IRPS), Dallas, USA, 2022: 2C. 3–1–2C. 3–6. [19] FRIGO P, VANNACC E, HASSAN H, et al. TRRespass: Exploiting the many sides of target row refresh[C]. 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, USA, 2020: 747–762. [20] VAN DER VEEN V, FRATANTONIO Y, LINDORFER M, et al. Drammer: Deterministic rowhammer attacks on mobile platforms[C]. 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 2016: 1675–1689. [21] SHARIFFUDDIN S, SIVAMANGAI N M, NAPOLEAN A, et al. Review on arbiter physical unclonable function and its implementation in FPGA for IoT security applications[C]. 2022 6th International Conference on Devices, Circuits and Systems (ICDCS), Coimbatore, India, 2022: 369–374. [22] TEHRANIPOOR F, KARIMIAN N, YAN Wei, et al. DRAM-based intrinsic physically unclonable functions for system-level security and authentication[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2017, 25(3): 1085–1097. doi: 10.1109/tvlsi.2016.2606658 [23] NAJAFI F, KAVEH M, MARTÍN D, et al. Deep PUF: A highly reliable DRAM PUF-based authentication for IoT networks using deep convolutional neural networks[J]. Sensors, 2021, 21(6): 2009. doi: 10.3390/s21062009 [24] SCHALLER A, XIONG Wenjie, ANAGNOSTOPOULOS N A, et al. Intrinsic rowhammer PUFs: Leveraging the rowhammer effect for improved security[C]. 2017 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Mclean, USA, 2017: 1–7. [25] SCHALLER A, XIONG Wemjie, ANAGNOSTOPOULOS N A, et al. Decay-based DRAM PUFs in commodity devices[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 16(3): 462–475. doi: 10.1109/TDSC.2018.2822298 [26] SUTAR S, RAHA A, and RAGHUNATHAN V. D-PUF: An intrinsically reconfigurable DRAM PUF for device authentication in embedded systems[C]. The International Conference on Compliers, Architectures, and Sythesis of Embedded Systems, Pittsburgh, USA, 2016: 1–10. [27] TALUKDER B M S B, RAY B, FORTE D, et al. PreLatPUF: Exploiting DRAM latency variations for generating robust device signatures[J]. IEEE Access, 2019, 7: 81106–81120. doi: 10.1109/ACCESS.2019.2923174 -





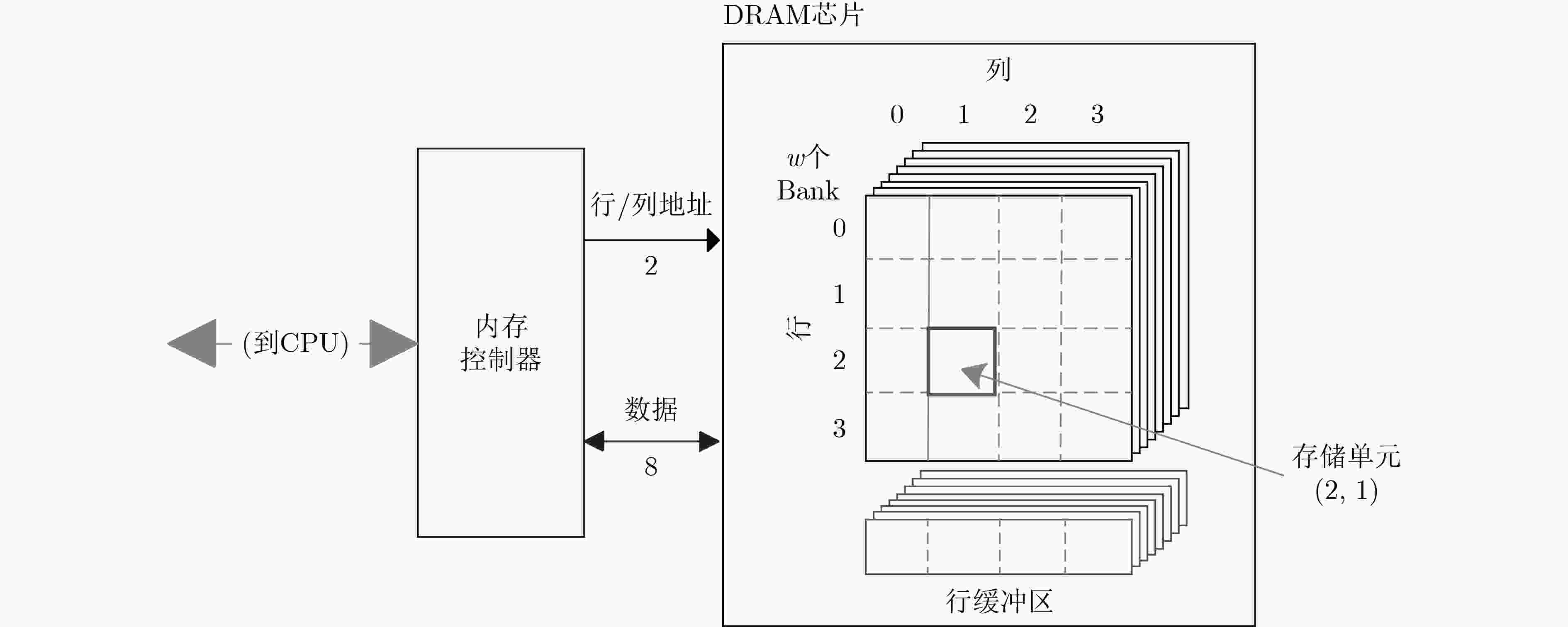
 下载:
下载:
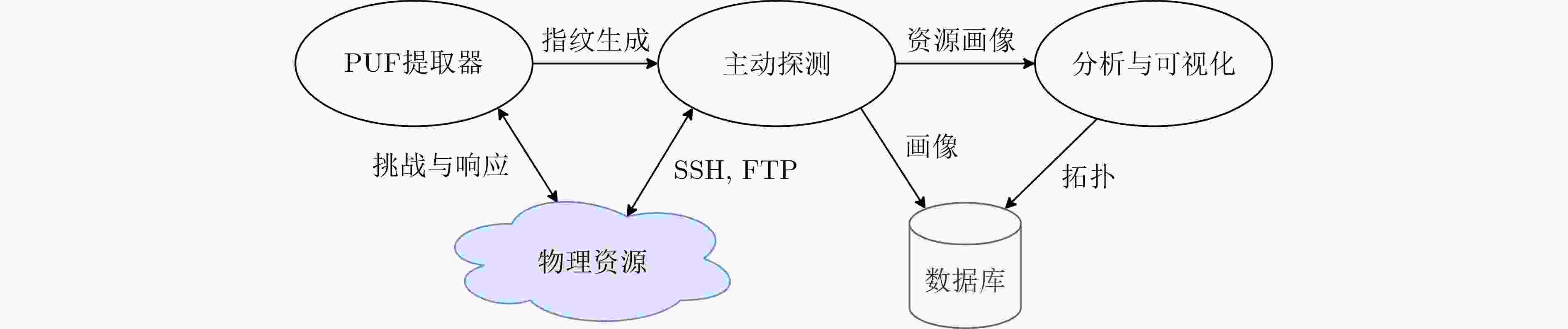
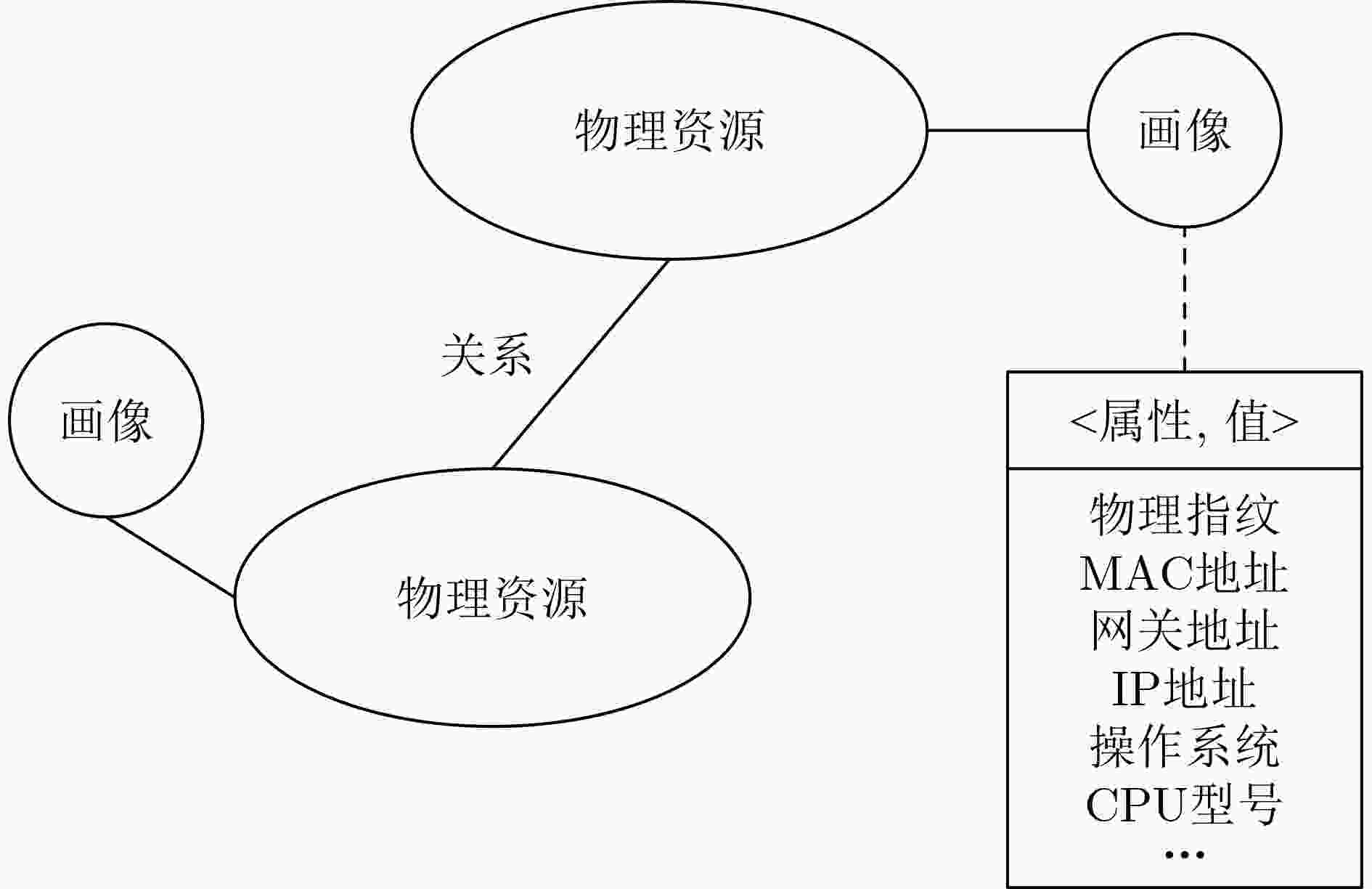
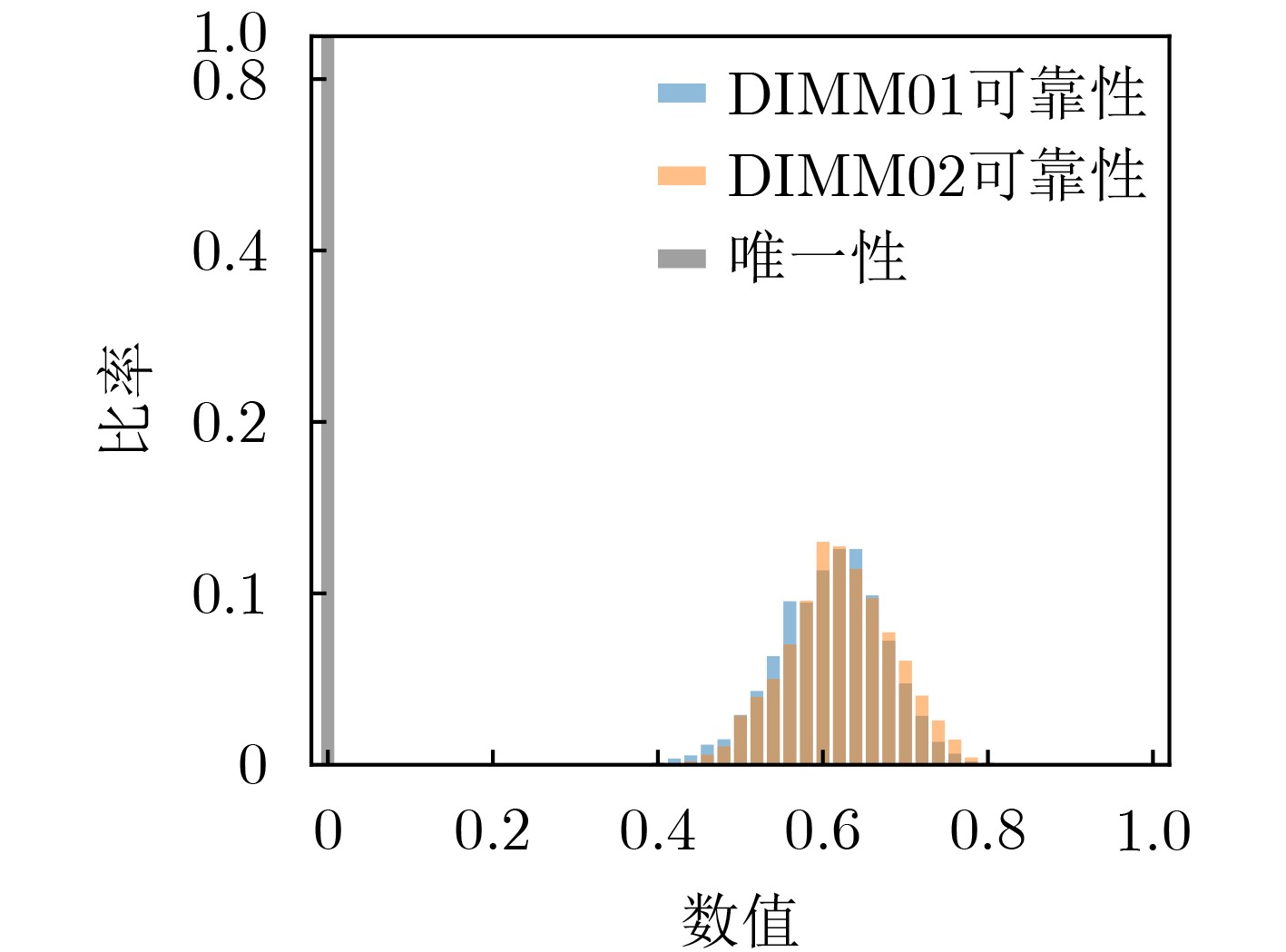
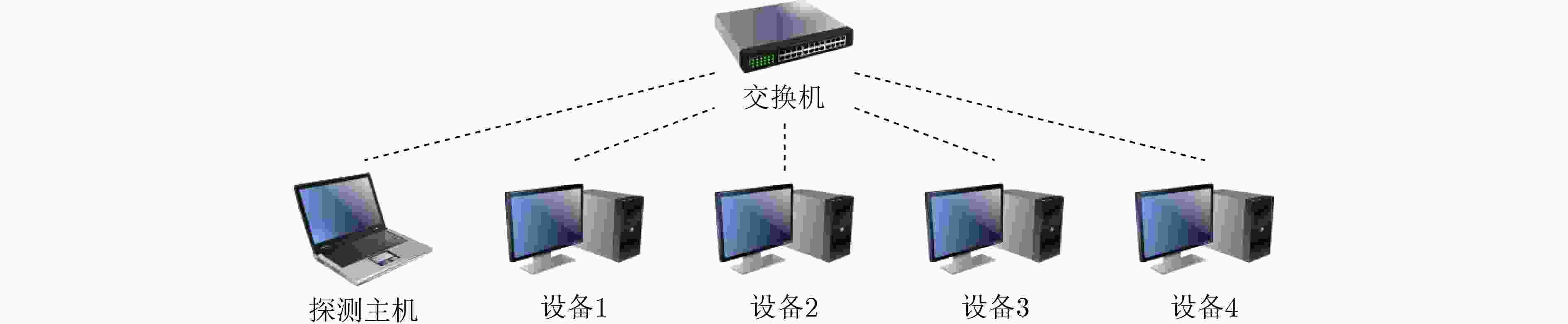



 下载:
下载:
