| [1] |
ZOU Yulong, ZHU Jia, WANG Xianbin, et al. A survey on wireless security: Technical challenges, recent advances, and future trends[J]. Proceedings of the IEEE, 2016, 104(9): 1727–1765. doi: 10.1109/JPROC.2016.2558521.
|
| [2] |
GOEL S and NEGI R. Guaranteeing secrecy using artificial noise[J]. IEEE Transactions on Wireless Communications, 2008, 7(6): 2180–2189. doi: 10.1109/TWC.2008.060848.
|
| [3] |
LI Guoquan, ZHANG Hui, WANG Yuhui, et al. QoS guaranteed power minimization and beamforming for IRS-assisted NOMA systems[J]. IEEE Wireless Communications Letters, 2023, 12(3): 391–395. doi: 10.1109/LWC.2022.3189272.
|
| [4] |
KAWAI Y and SUGIURA S. QoS-constrained optimization of intelligent reflecting surface aided secure energy-efficient transmission[J]. IEEE Transactions on Vehicular Technology, 2021, 70(5): 5137–5142. doi: 10.1109/TVT.2021.3075685.
|
| [5] |
LI Baogang, WU Wenjing, LI Yonghui, et al. Intelligent reflecting surface and artificial-noise-assisted secure transmission of MEC system[J]. IEEE Internet of Things Journal, 2022, 9(13): 11477–11488. doi: 10.1109/JIOT.2021.3127534.
|
| [6] |
ZHOU Gui, PAN Cunhua, REN Hong, et al. A framewo202rk of robust transmission design for IRS-aided MISO communications with imperfect cascaded channels[J]. IEEE Transactions on Signal Processing, 2020, 68: 5092–5106. doi: 10.1109/TSP.2020.3019666.
|
| [7] |
SHEN Meng, LEI Xianfu, MATHIOPOULOS P T, et al. Robust beamforming design for IRS-aided secure communication systems under complete imperfect CSI[J]. IEEE Transactions on Vehicular Technology, 2023, 72(6): 8204–8209. doi: 10.1109/TVT.2023.3243115.
|
| [8] |
YU Xianghao, XU Dongfang, SUN Ying, et al. Robust and secure wireless communications via intelligent reflecting surfaces[J]. IEEE Journal on Selected Areas in Communications, 2020, 38(11): 2637–2652. doi: 10.1109/JSAC.2020.3007043.
|
| [9] |
JI Zhi, YANG Wendong, GUAN Xinrong, et al. Trajectory and transmit power optimization for IRS-assisted UAV communication under malicious jamming[J]. IEEE Transactions on Vehicular Technology, 2022, 71(10): 11262–11266. doi: 10.1109/TVT.2022.3187092.
|
| [10] |
SUN Yifu, AN Kang, LUO Junshan, et al. Outage constrained robust beamforming optimization for multiuser IRS-assisted anti-jamming communications with incomplete information[J]. IEEE Internet of Things Journal, 2022, 9(15): 13298–13314. doi: 10.1109/JIOT.2022.3140752.
|
| [11] |
徐勇军, 符加劲, 黄琼, 等. 智能反射面辅助的多天线通信系统鲁棒安全资源分配算法[J]. 电子与信息学报, 2024, 46(1): 165–174.XU Yongjun, FU Jiajin, HUANG Qiong, et al. Robust Secure resource allocation algorithm for intelligent reflecting surface-assisted multi-antenna communication systems[J]. Journal of Electronics & Information Technology, 2024, 46(1): 165–174.
|
| [12] |
ZHOU Gui, PAN Cunhua, REN Hong, et al. Robust beamforming design for intelligent reflecting surface aided MISO communication systems[J]. IEEE Wireless Communications Letters, 2020, 9(10): 1658–1662. doi: 10.1109/LWC.2020.3000490.
|
| [13] |
NIU Hehao, CHU Zheng, ZHOU Fuhui, et al. Weighted sum secrecy rate maximization using intelligent reflecting surface[J]. IEEE Transactions on Communications, 2021, 69(9): 6170–6184. doi: 10.1109/TCOMM.2021.3085780.
|
| [14] |
XU Yongjun, ZHAO Xiaohui, and LIANG Yingchang. Robust power control and beamforming in cognitive radio networks: A survey[J]. IEEE Communications Surveys & Tutorials, 2015, 17(4): 1834–1857. doi: 10.1109/COMST.2015.2425040.
|
| [15] |
SHEN Zhexian, XU Kui, and XIA Xiaochen. Beam-domain anti-jamming transmission for downlink massive MIMO systems: A stackelberg game perspective[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 2727–2742. doi: 10.1109/TIFS.2021.3063632.
|
| [16] |
BOYD S P and VANDENBERGHE L. Convex Optimization[M]. Cambridge: Cambridge University Press, 2004.
|
| [17] |
GHARAVOL E A and LARSSON E G. The sign-definiteness lemma and its applications to robust transceiver optimization for multiuser MIMO systems[J]. IEEE Transactions on Signal Processing, 2013, 61(2): 238–252. doi: 10.1109/TSP.2012.2222379.
|
| [18] |
XU Yongjun, XIE Hao, LIANG Chengchao, et al. Robust secure energy-efficiency optimization in SWIPT-aided heterogeneous networks with a nonlinear energy-harvesting model[J]. IEEE Internet of Things Journal, 2021, 8(19): 14908–14919. doi: 10.1109/JIOT.2021.3072965.
|
| [19] |
BOYD S, EL GHAOUI L, FERON E, et al. Linear Matrix Inequalities in System and Control Theory[M]. Philadelphia: Society for Industrial and Applied Mathematics, 1994.
|
| [20] |
LUO Zhiquan, MA W K, SO A M C, et al. Semidefinite relaxation of quadratic optimization problems[J]. IEEE Signal Processing Magazine, 2010, 27(3): 20–34. doi: 10.1109/MSP.2010.936019.
|
| [21] |
BAHINGAYI E E and LEE K. Low-complexity beamforming algorithms for IRS-aided single-user massive MIMO mmWave systems[J]. IEEE Transactions on Wireless Communications, 2022, 21(11): 9200–9211. doi: 10.1109/TWC.2022.3174154.
|
| [22] |
WANG Kunyu, SO A M C, CHANG T H, et al. Outage constrained robust transmit optimization for multiuser MISO downlinks: Tractable approximations by conic optimization[J]. IEEE Transactions on Signal Processing, 2014, 62(21): 5690–5705. doi: 10.1109/TSP.2014.2354312.
|





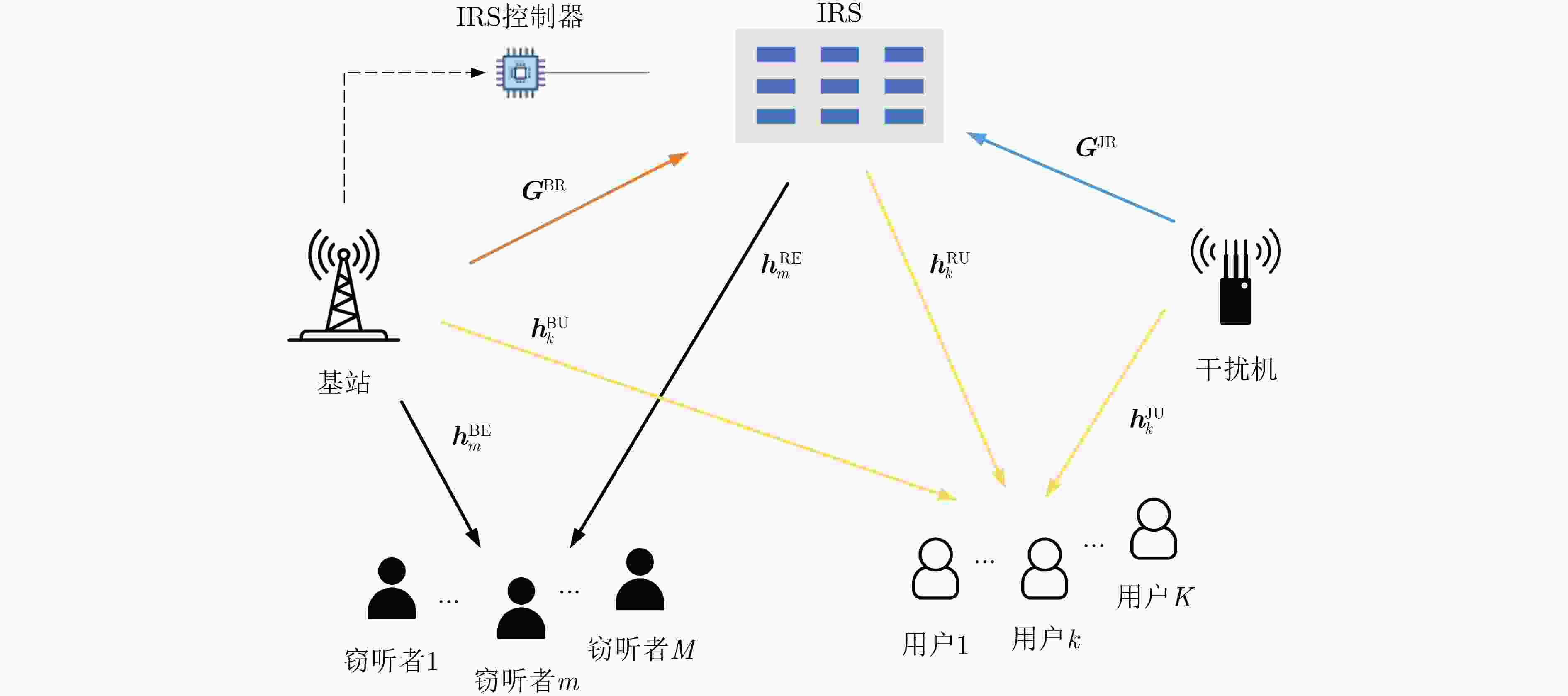
 下载:
下载:
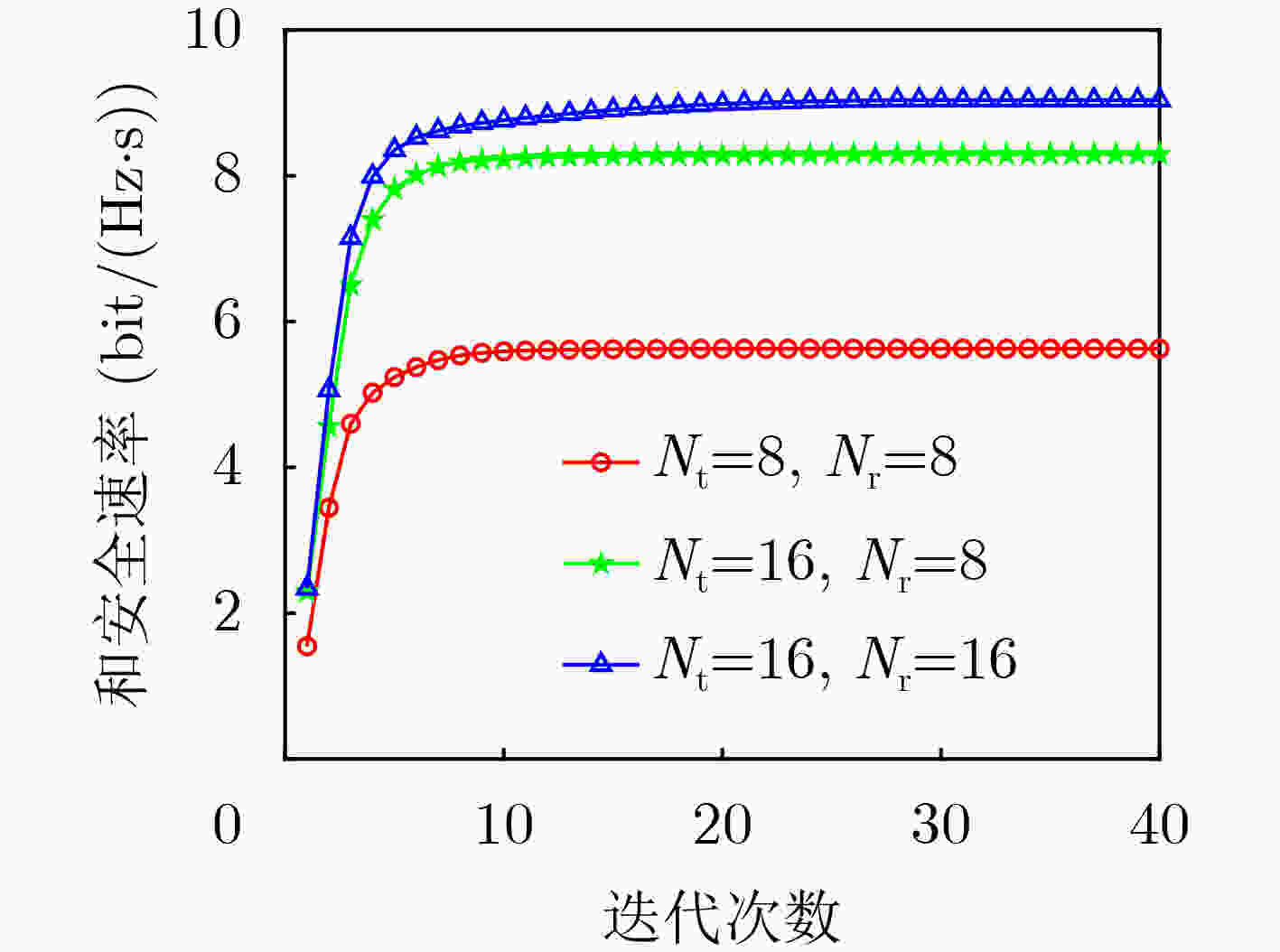
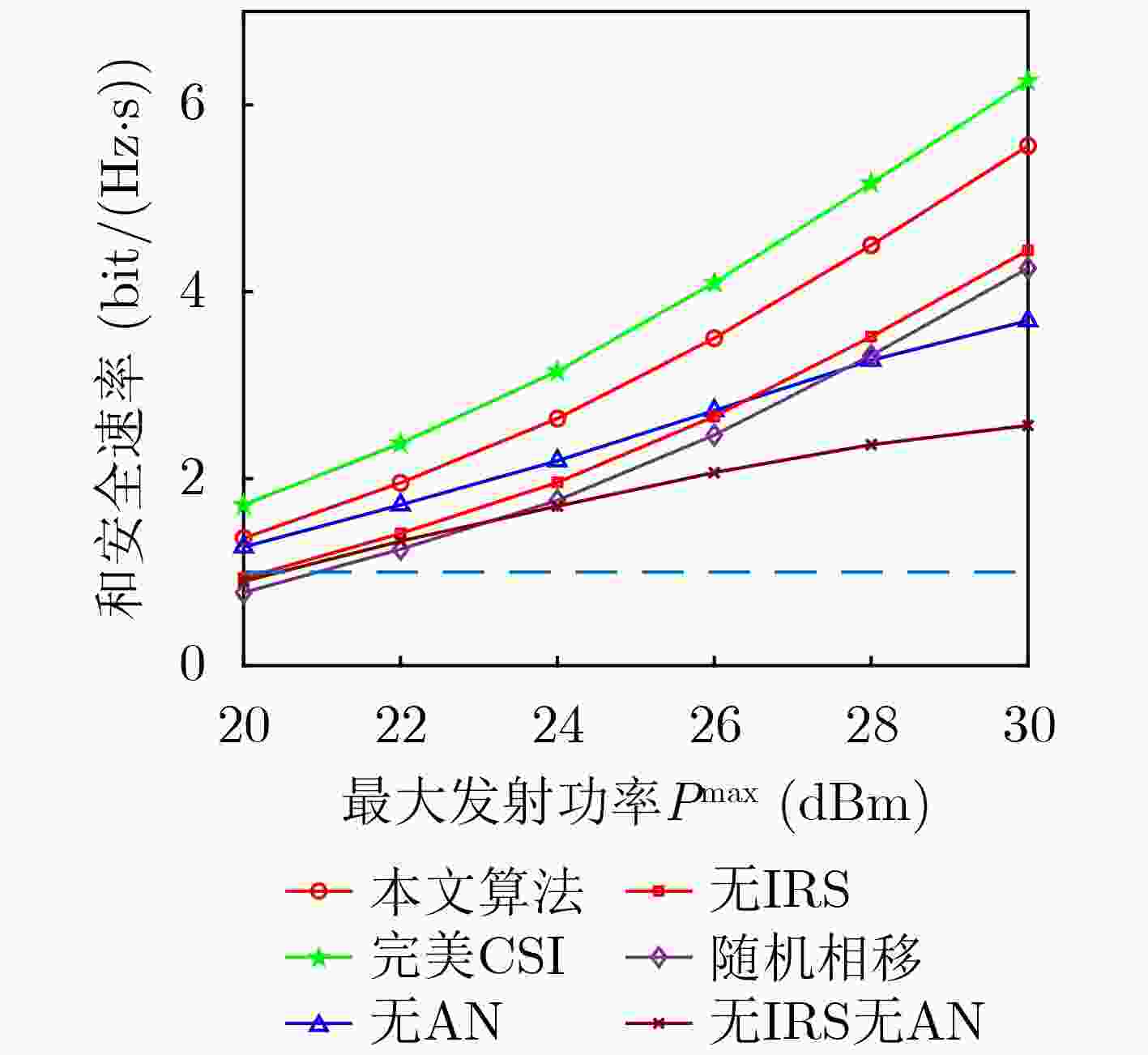
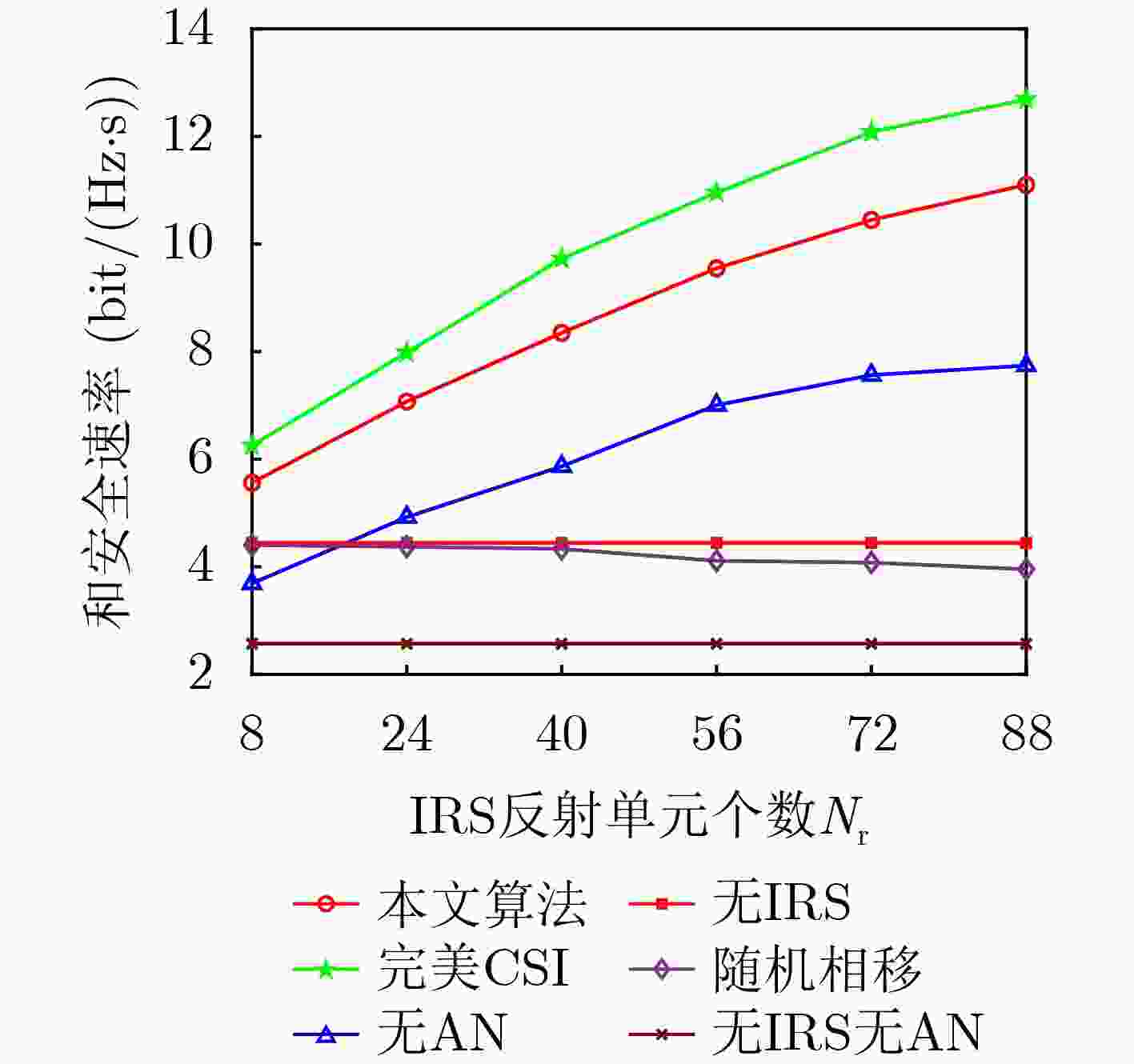


 下载:
下载:
