A Location Privacy and Query Privacy Joint Protection Scheme for POI Query in Vehicular Networks
-
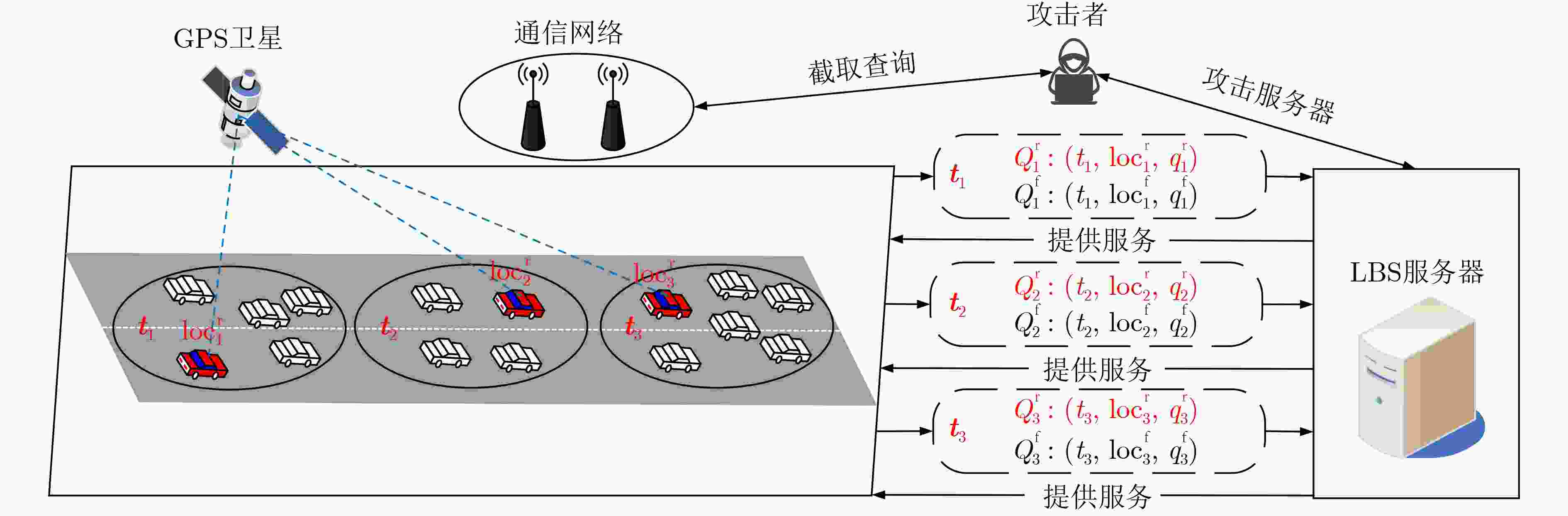
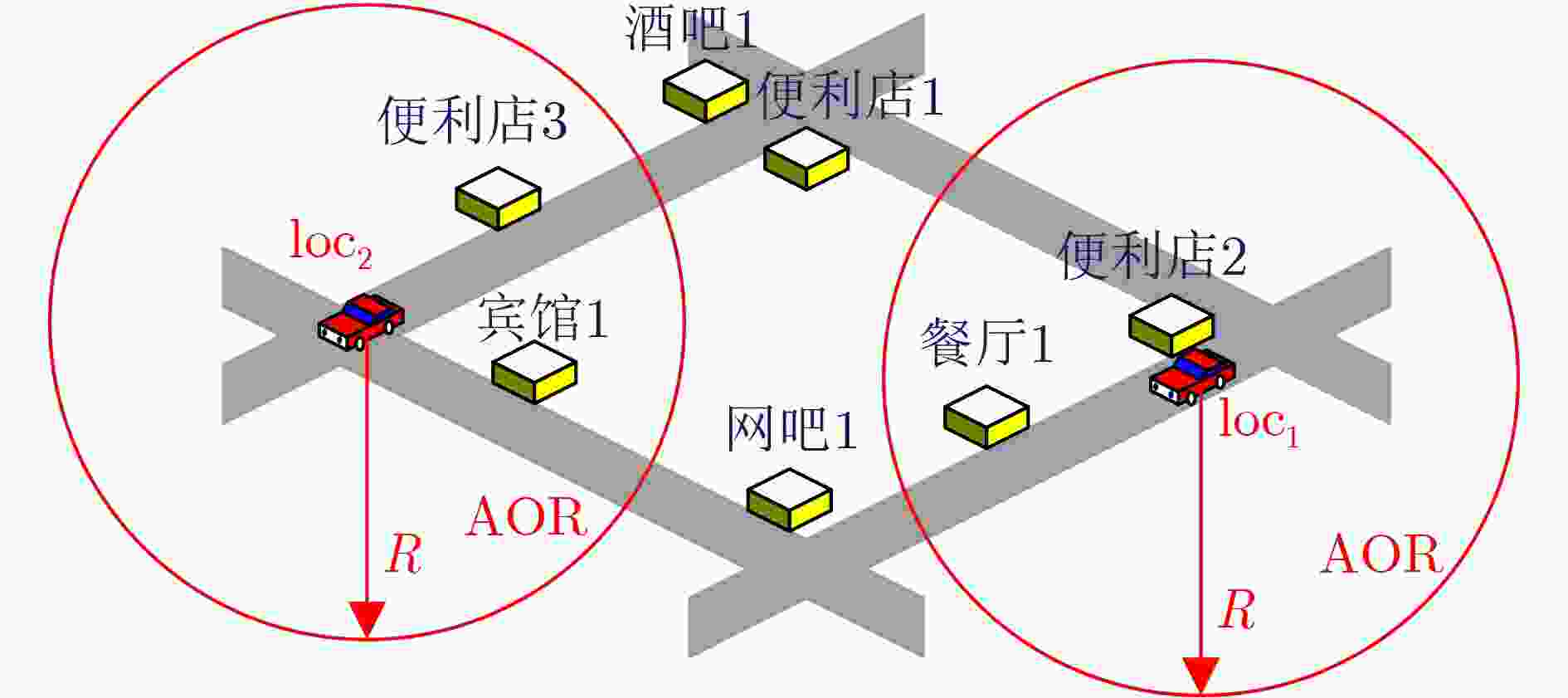
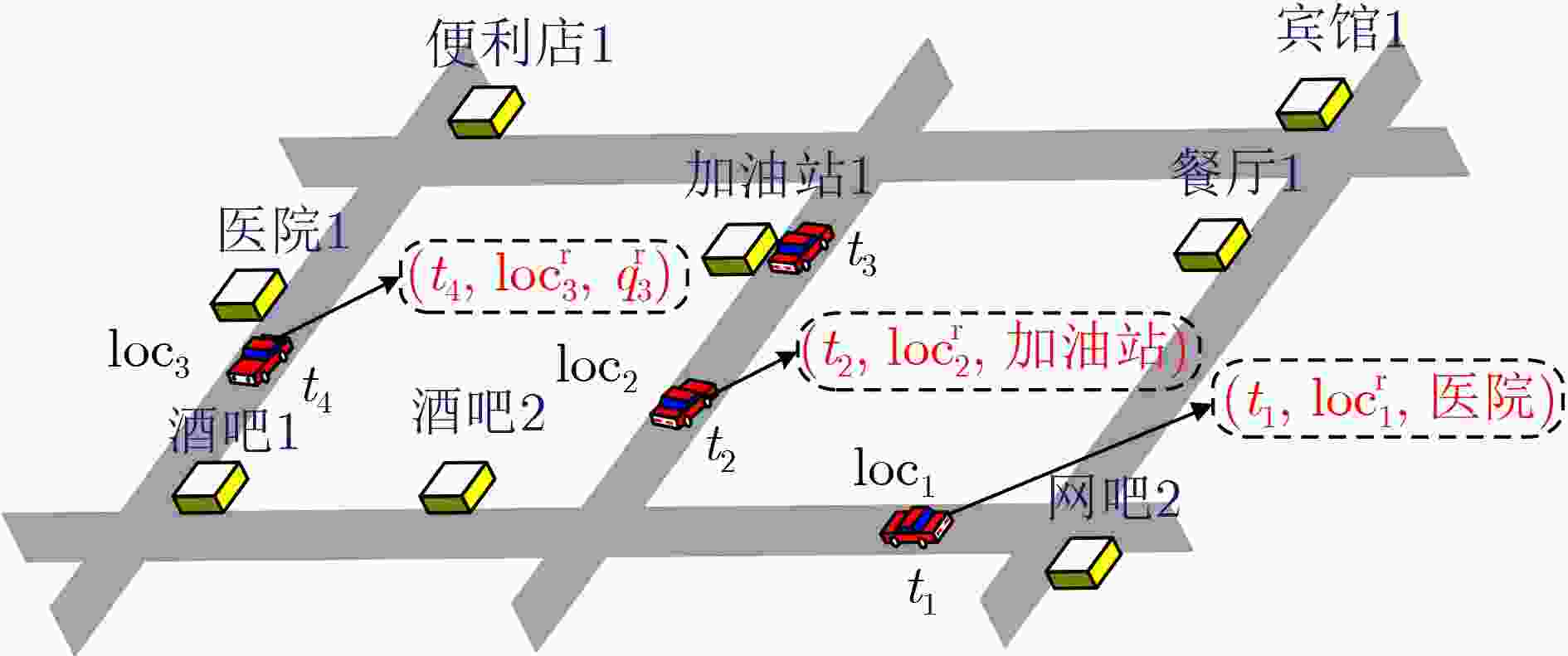
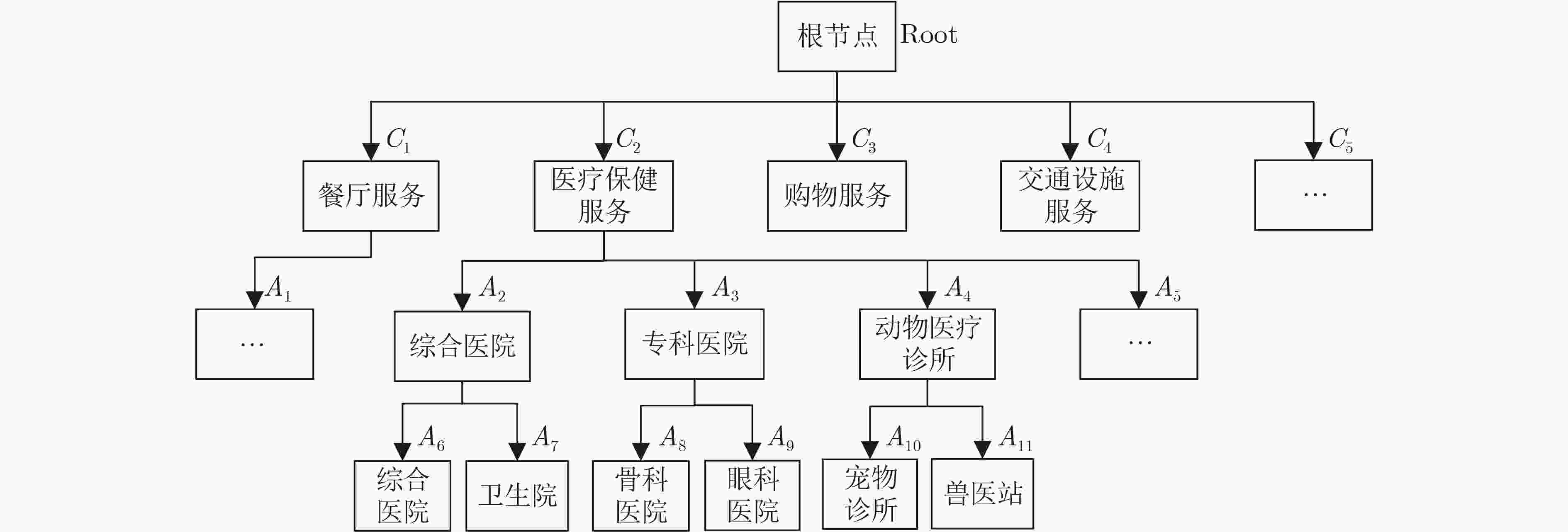
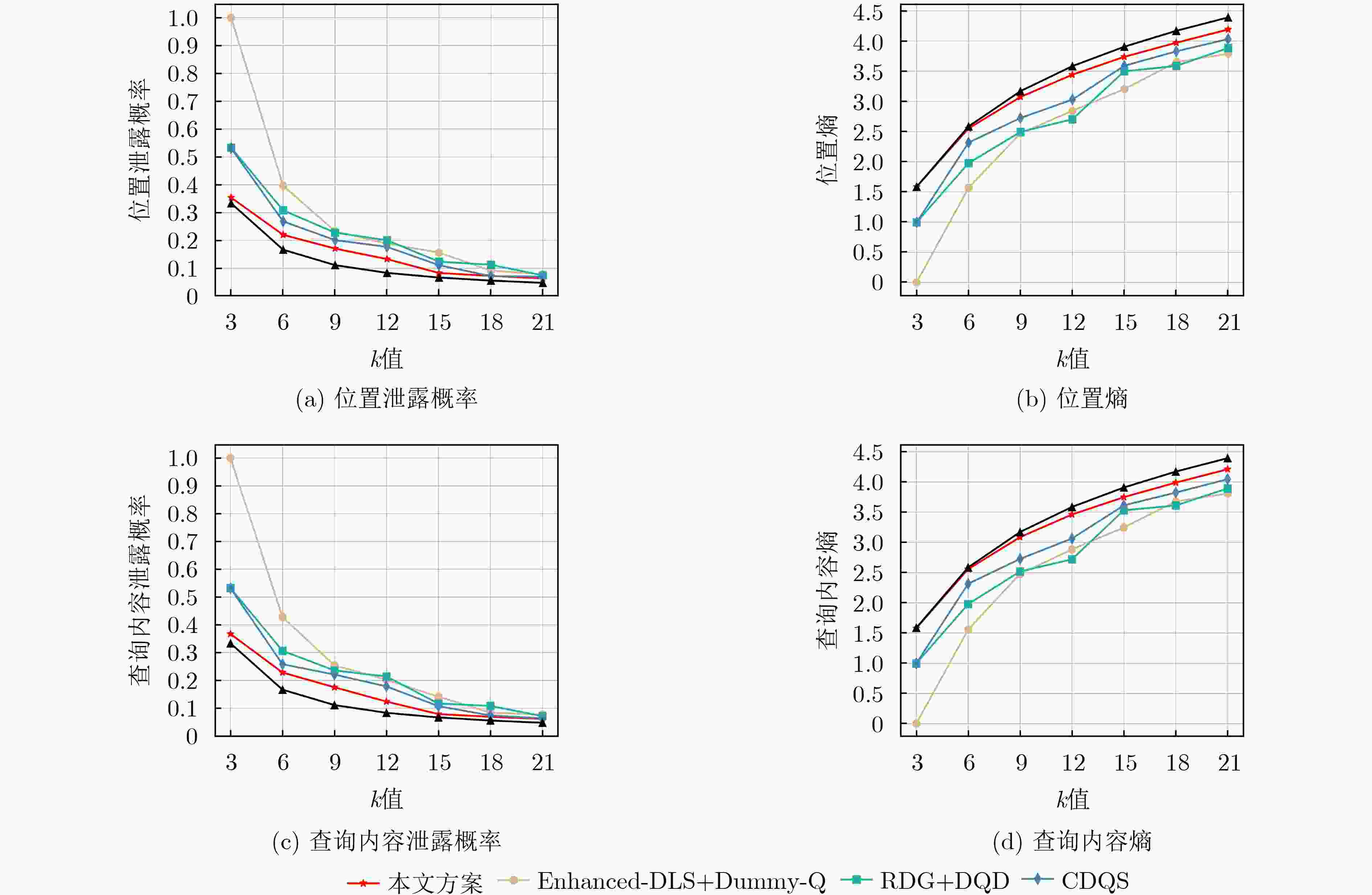
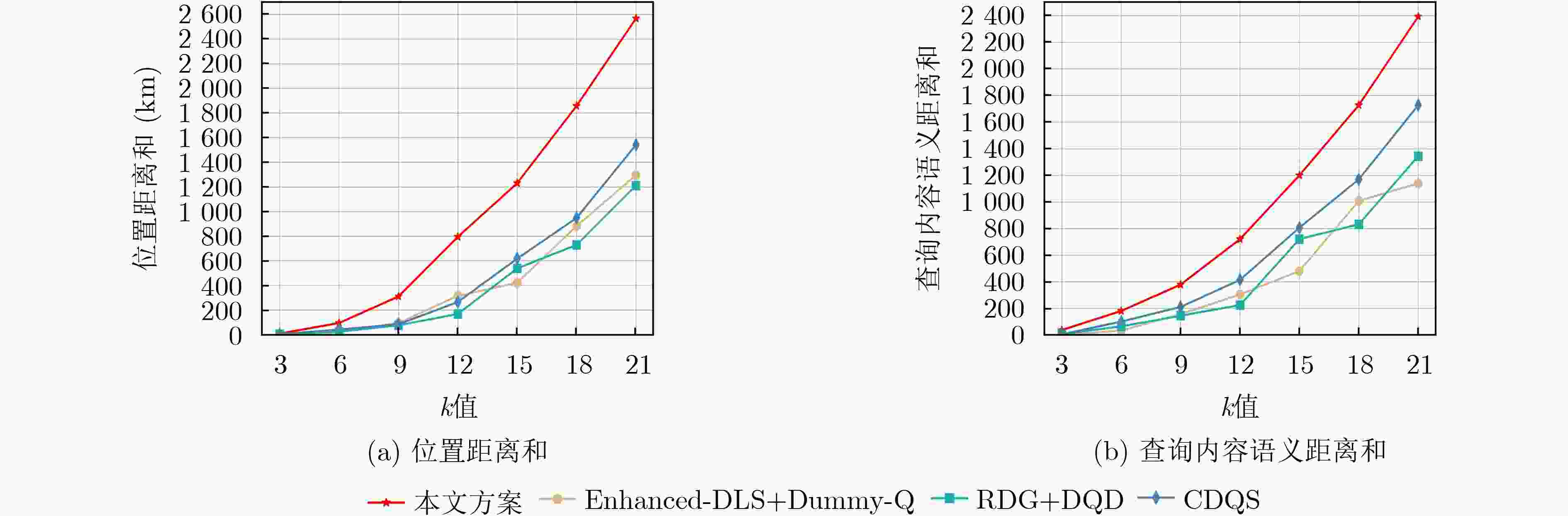
摘要: 在车联网中,基于位置的服务(LBS)的兴趣点(POI)查询被广泛用于车载应用中。但是,由于攻击者容易获取车辆位置、查询内容以及其它额外信息,单独对位置隐私或查询隐私进行保护很难保障车载用户的隐私安全,使得对位置隐私和查询隐私开展联合保护越发关键。为此,该文提出一种基于虚拟序列的位置隐私和查询隐私联合保护机制。首先根据POI查询的限制,分析位置隐私和查询隐私的相关性,运用欧几里得距离和关联规则算法对其建模描述,得到相关性判断模型;然后基于虚拟序列,根据影响隐私保护的因素和真实查询的相关性值,将联合保护转化为虚拟序列的选择问题,建立联合保护优化模型,得到匿名程度高且匿名区域大的匿名查询集,防止攻击者识别出真实查询。最后,实验结果表明,与现有方案相比,所提联合保护机制能抵御针对位置隐私和查询隐私的联合攻击(语义范围攻击、时间关联攻击和长期观察攻击),能更有效地保护用户的LBS隐私。Abstract: In vehicular networks, the Point Of Interest (POI) query is widely used in Location-Based Services (LBS) for vehicle applications. However, since the attackers can easily access the location, query content, and other information, it is difficult to protect the LBS privacy of vehicle users only using location privacy protection or query privacy protection independently. Therefore, a location privacy and query privacy joint protection scheme based on dummy sequences is proposed. According to the limitations of the POI query, the correlations between location privacy and query privacy are modelled to obtain the correlation judgment model characterized by the Euclidean distance and the association rule algorithm. Moreover, based on dummy sequences, the joint protection is transformed into the dummy sequence selection according to the factors that affect user privacy and the correlation value of real query. Then a constrained multi-objective optimization model is established to obtain the query sequence with a high level of anonymity and a big cloaking region. Experimental results demonstrate that our scheme can resist joint attacks on location privacy and query privacy and protect users’ LBS privacy more efficiently than existing schemes.
-
Key words:
- Location privacy /
- Location-Based Services (LBS) /
- Query privacy /
- Joint protection /
- Dummy sequences
-
表 1 仿真参数
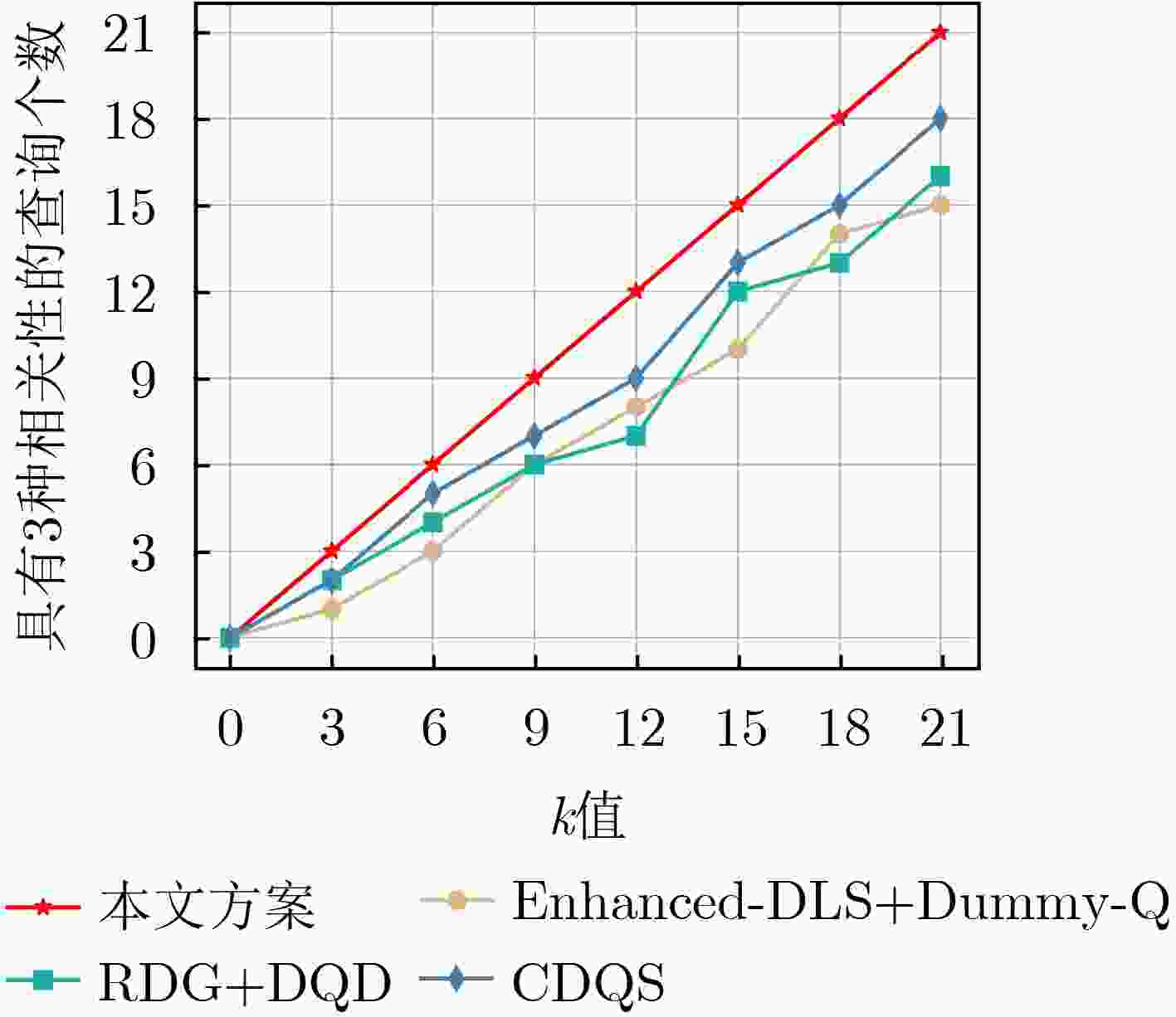
参数 符号 数值 AOR半径(km) R 3 时间段 t (8:00-9:00),(13:00-14:00),(21:00-22:00) 匿名查询集的大小 k {3,6,9,12,15,18,21} 安全距离(m) ${d_{{\text{safe}}}}$ 100 -
[1] XU Chuan, LUO Li, DING Yingyi, et al. Personalized location privacy protection for location-based services in vehicular networks[J]. IEEE Wireless Communications Letters, 2020, 9(10): 1633–1637. doi: 10.1109/LWC.2020.2999524 [2] 冯登国, 张敏, 叶宇桐. 基于差分隐私模型的位置轨迹发布技术研究[J]. 电子与信息学报, 2020, 42(1): 74–88. doi: 10.11999/JEIT190632FENG Dengguo, ZHANG Min, and YE Yutong. Research on differentially private trajectory data publishing[J]. Journal of Electronics &Information Technology, 2020, 42(1): 74–88. doi: 10.11999/JEIT190632 [3] KUANG Li, HE Shuai, FAN Yuyou, et al. T-SR: A location privacy protection algorithm based on POI query[J]. IEEE Access, 2019, 7: 59491–59503. doi: 10.1109/ACCESS.2019.2913547 [4] WANG Shengling, HU Qin, SUN Yunchuan, et al. Privacy preservation in location-based services[J]. IEEE Communications Magazine, 2018, 56(3): 134–140. doi: 10.1109/MCOM.2018.1700288 [5] LI Xingxin, ZHU Youwen, and WANG Jian. Highly efficient privacy preserving location-based services with enhanced one-round blind filter[J]. IEEE Transactions on Emerging Topics in Computing, 2021, 9(4): 1803–1814. doi: 10.1109/TETC.2019.2926385 [6] FAROUK F, ALKADY Y, and RIZK R. Efficient privacy-preserving scheme for location based services in VANET system[J]. IEEE Access, 2020, 8: 60101–60116. doi: 10.1109/ACCESS.2020.2982636 [7] SHAHAM S, DING Ming, LIU Bo, et al. Privacy preservation in location-based services: A novel metric and attack model[J]. IEEE Transactions on Mobile Computing, 2021, 20(10): 3006–3019. doi: 10.1109/TMC.2020.2993599 [8] PINGLEY A, ZHANG Nan, FU Xinwen, et al. Protection of query privacy for continuous location based services[C]. 2011 Proceedings IEEE INFOCOM, Shanghai, China, 2011: 1710–1718. [9] YADAV V K, ANDOLA N, VERMA S, et al. P2LBS: Privacy provisioning in location-based services[J]. IEEE Transactions on Services Computing, 2023, 16(1): 466–477. doi: 10.1109/TSC.2021.3123428 [10] WU Zongda, LI Guiling, SHEN Shigen, et al. Constructing dummy query sequences to protect location privacy and query privacy in location-based services[J]. World Wide Web, 2021, 24(1): 25–49. doi: 10.1007/s11280-020-00830-x [11] NIU Ben, CHEN Yahong, WANG Zhibo, et al. Eclipse: Preserving differential location privacy against long-term observation attacks[J]. IEEE Transactions on Mobile Computing, 2022, 21(1): 125–138. doi: 10.1109/TMC.2020.3000730 [12] HUA Jingyu, TONG Wei, XU Fengyuan, et al. A geo-indistinguishable location perturbation mechanism for location-based services supporting frequent queries[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(5): 1155–1168. doi: 10.1109/TIFS.2017.2779402 [13] ASUQUO P, CRUICKSHANK H, MORLEY J, et al. Security and privacy in location-based services for vehicular and mobile communications: An overview, challenges, and countermeasures[J]. IEEE Internet of Things Journal, 2018, 5(6): 4778–4802. doi: 10.1109/JIOT.2018.2820039 [14] HAN Jiawei, PEI Jian, and YIN Yiwen. Mining frequent patterns without candidate generation[J]. ACM SIGMOD Record, 2000, 29(2): 1–12. doi: 10.1145/335191.335372 [15] NYC. TLC Trip Record Data[EB/OL]. https://www1.nyc.gov/site/tlc/about/tlc-trip-record-data.page, 2022. [16] NIU Ben, LI Qinghua, ZHU Xiaoyan, et al. Achieving k-anonymity in privacy-aware location-based services[C]. IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, Canada, 2014: 754–762. [17] ZHAO Ping, LIU Wuwu, ZHANG Guanglin, et al. Preserving privacy in WiFi localization with plausible dummy locations[J]. IEEE Transactions on Vehicular Technology, 2020, 69(10): 11909–11925. doi: 10.1109/TVT.2020.3006363 [18] 百度. 百度地图[EB/OL]. https://lbsyun.baidu.com/, 2022.BAIDU. Baidu Maps[EB/OL]. https://lbsyun.baidu.com/, 2022. [19] 王洁, 王春茹, 马建峰, 等. 基于位置语义和查询概率的假位置选择算法[J]. 通信学报, 2020, 41(3): 53–61. doi: 10.11959/j.issn.1000-436x.2020061WANG Jie, WANG Chunru, MA Jianfeng, et al. Dummy location selection algorithm based on location semantics and query probability[J]. Journal on Communications, 2020, 41(3): 53–61. doi: 10.11959/j.issn.1000-436x.2020061 [20] DEB K, PRATAP A, AGARWAL S, et al. A fast and elitist multiobjective genetic algorithm: NSGA-II[J]. IEEE Transactions on Evolutionary Computation, 2002, 6(2): 182–197. doi: 10.1109/4235.996017 [21] NIU Ben, ZHU Xiaoyan, LI Weihao, et al. A personalized two-tier cloaking scheme for privacy-aware location-based services[C]. 2015 International Conference on Computing, Networking and Communications (ICNC), Garden Grove, USA, 2015: 94–98. -





 下载:
下载:


 下载:
下载:
