A Class of Combination Verification and Authentication Method for Synchronous Key Update
-
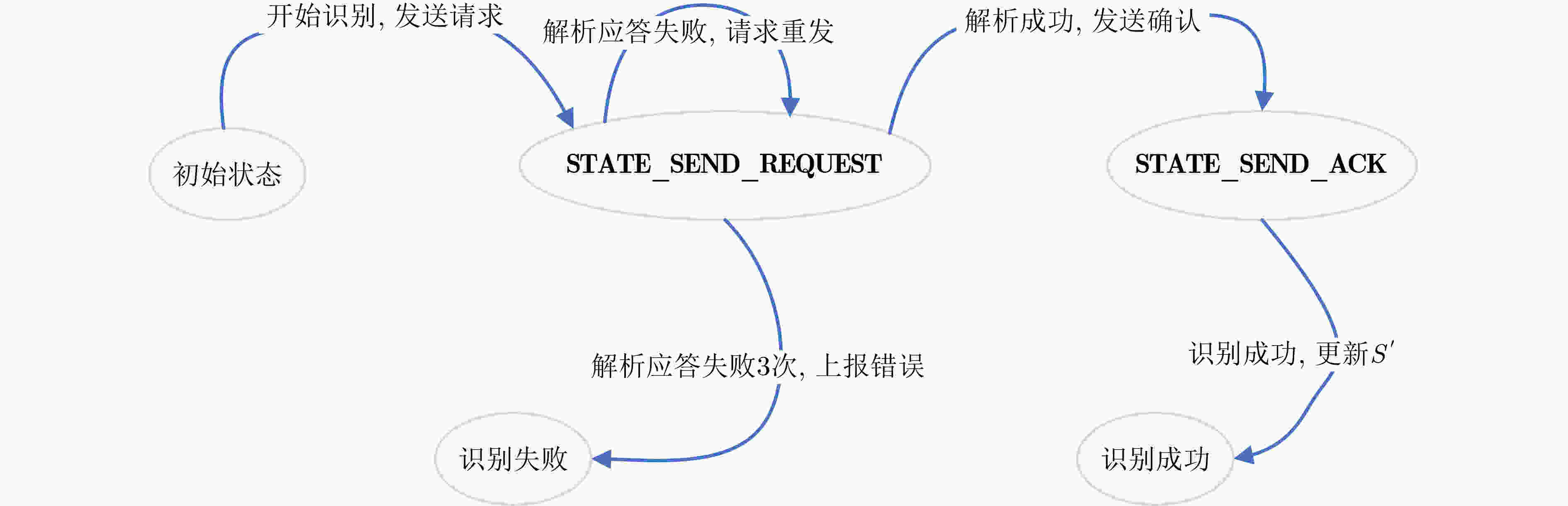
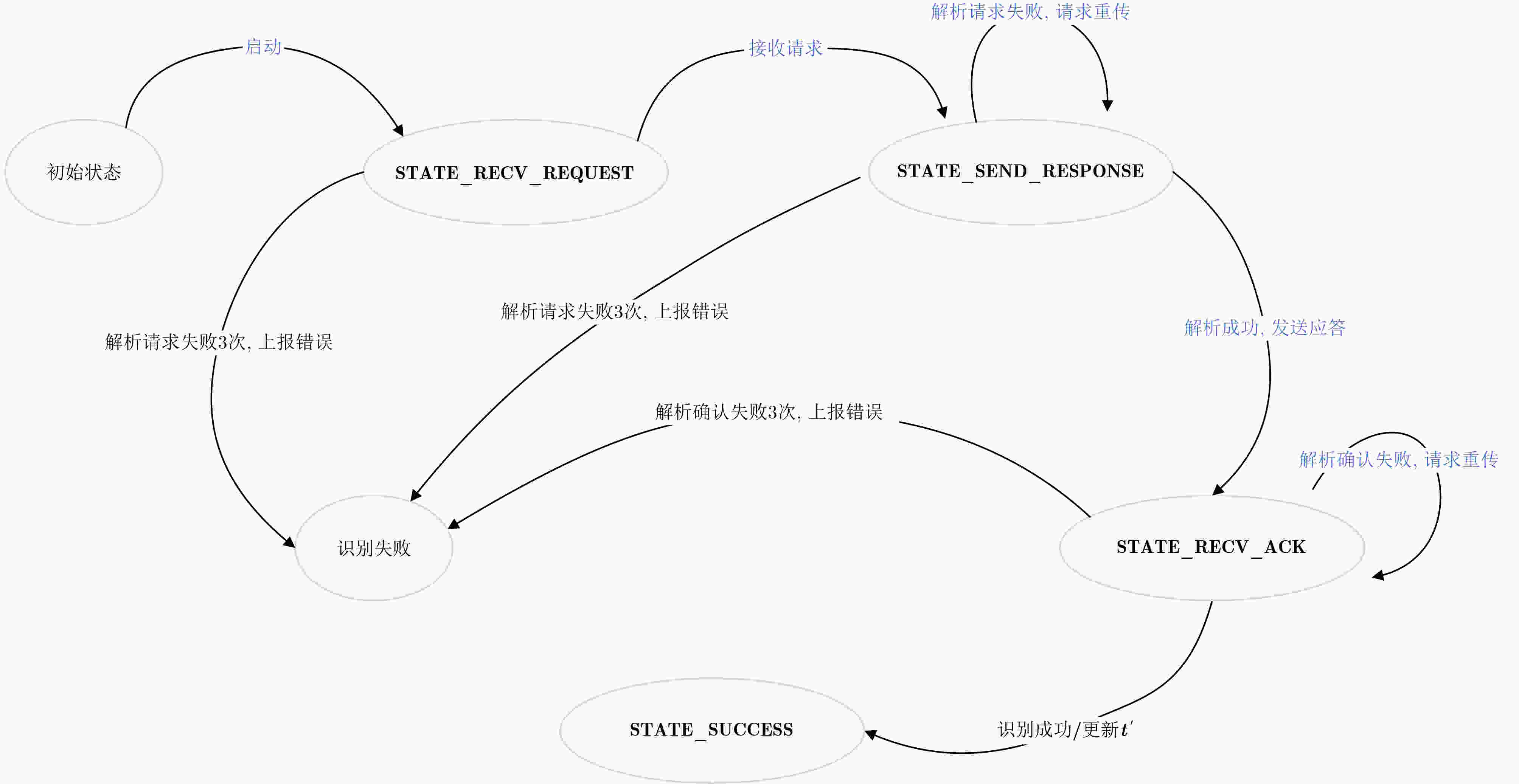
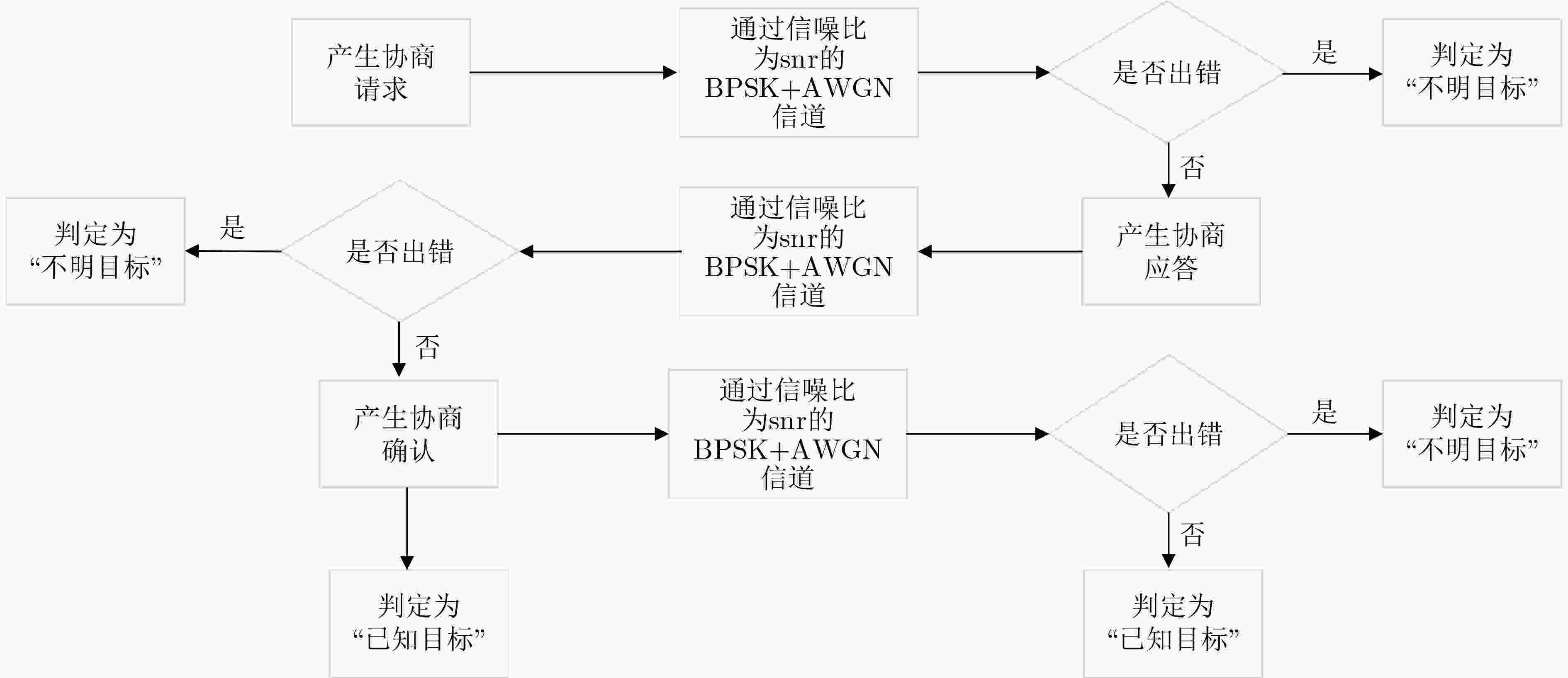
摘要: 针对一对多通报关系实体认证与密钥协商应用环境的无线目标身份识别同步认证问题,该文设计了双密钥组合校验定理,提出并证明了交互式动态认证与工作密钥同步更新定理,基于可信标识动态密钥匹配规则构建了密钥同步更新的组合校验认证模型,提出了一类密钥同步更新的组合校验认证方法,给出了双密钥组合校验、消息适度重传、模拟信道信噪比合理仿真等无线目标身份识别协议设计准则,突破了无线目标身份识别协议同步认证难的关键技术,解决了实体认证与密钥协商中实体身份动态认证、工作密钥同步更新难题。以一类无线目标身份识别协议为例,分析说明了该类方法的具体应用。基于串空间理论构造攻击方法给出了该协议的形式化证明,并通过常规攻击方法分析了该协议的实际安全性。与其他交互式密码协议同步认证设计方法相比较,该方法具有动态可认证性,由该方法设计的交互式密码协议同步认证方案,安全性高,计算量小,仅进行一次迭代运算,可应用于大规模复杂环境中的无线目标身份识别。
-
关键词:
- 密钥同步更新 /
- 动态可认证性 /
- 双密钥组合校验 /
- 基于串空间理论构造攻击方法
Abstract: In view of the problem of synchronous authentication of wireless target identification in the application environment of one-to-many notification relationship entity authentication and key agreement, a double key combination verification theorem is designed. The theorem of interactive dynamic authentication and working key synchronization uopdate is proposed and proved. Based on the dynamic key matching rule of trusted identity, a combinatorial verification authentication model of key synchronization update is constructed. A kind of key synchronous updating combinatorial verification authentication method is proposed. The design criteria of wireless target identification protocol, such as double key combination verification, moderate message retransmission, reasonable simulation of analog channel signal-to-noise ratio, are given. It breaks through the key technology of synchronization authentication in the wireless target identification protocol. The problem of dynamic authentication of entity identity and synchronous updating of working key in entity authentication and key agreement is solved. Taking a class of wireless target identification protocols as an example, the application of this kind of methods is analyzed and illustrated. The formal proof of the protocol is given by a class of constructive attack methods based on strand space theory, and the actual security of the protocol is analyzed by conventional attack methods. Compared with other design methods of synchronous authentication for interactive cryptographic protocols, this method has dynamic authentication. The synchronous authentication scheme designed by this method has the advantages of high security, less computation and only one iteration, which can be applied to wireless target identification in large-scale and complex environment. -
表 1 实体认证与密钥协商协议实现功能对照表
指标分析 分析方法机理 计算量 应用范围 安全性 基于Hash函数的检测方法 基于Hash函数采用共享密钥不断刷新机制,实现数据同步认证。 Hash杂凑运算的次数为N/2—N(N为目标数) 小型数据库 标签无法认证读写器的合法性,系统易受到重放和假冒攻击,有安全隐患。 基于Hash函数和ECC的检测方法 基于Hash函数和ECC,采用共享密钥不断刷新机制,实现数据同步认证。 Hash杂凑运算迭代1次,工作密钥通过ECC加密后再发送到对端,增加了协议运算量和存储量。 小型数据库 用于验证身份的随机数明文传输,易被截获,有安全隐患。 双密钥组合校验动态认证方法 基于对称密码体制,采用共享密钥不断刷新机制,实现数据同步认证。 MAC码运算迭代1次,工作密钥在本地参与运算,不发送,节约了协议资源开销。 大型数据库 无安全隐患 表 2 无线目标身份识别协议所用符号说明
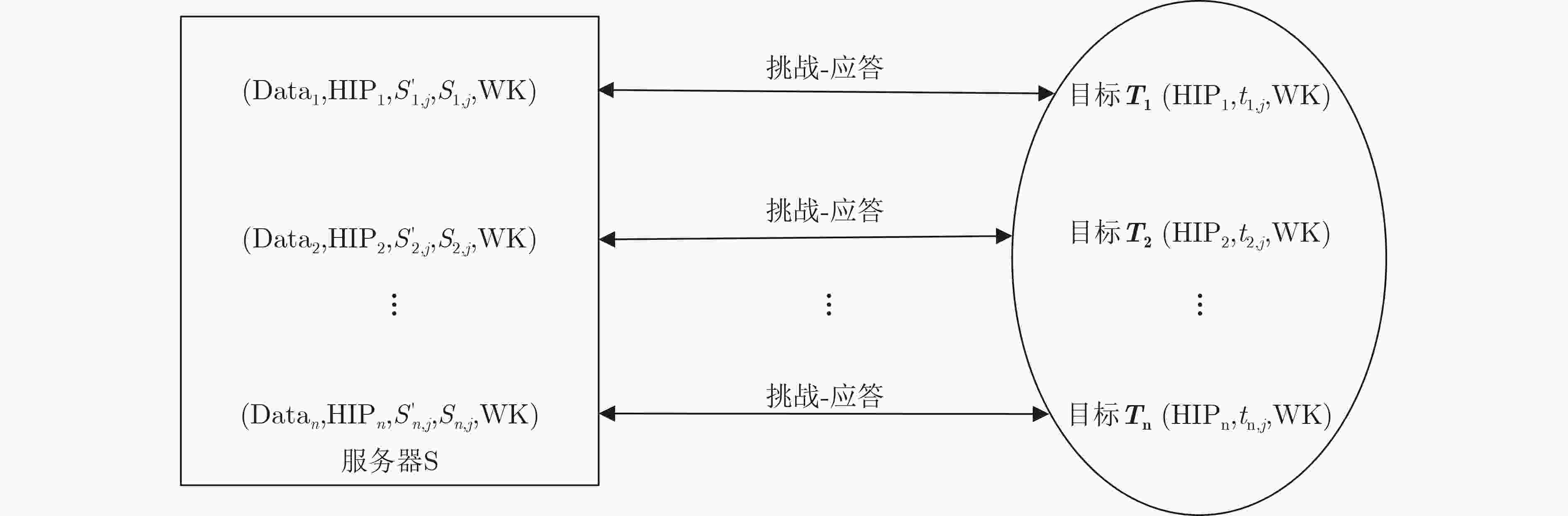
符号 含义 符号 含义 S 服务器 T 无线目标 HIPS 服务器S的可信标识 HIPT 服务器T的可信标识 Ns 服务器S产生的随机数 $N_s' $ 服务器Ns的逐比特取反 Nt 服务器T产生的随机数 $N_t' $ 服务器Nt的逐比特取反 BK 通播密钥 WKTS 服务器S与无线目标T之间的工作密钥 OPT 无线目标T的参数数据 MAC-OPT 无线目标T的参数数据认证码 MACReq 请求数据包的认证码 MACRes 应答数据包的认证码 MACAc 确认数据包的认证码 -
[1] OHKUBO M, SUZUKI K, and KINOSHITA S. Hash-chain based forward secure privacy protection scheme for low-cost RFID[C]. The Symposium on Cryptography and Information Security, Sendai, Japan, 2004: 719–724. [2] 梁焕琪. 基于Hash函数和公钥加密的RFID认证协议的研究[D]. [硕士论文], 华南理工大学, 2012.LIANG Huanqi. Research of mutual authentication protocol for RFID based on Hash function and public key[D]. [Master dissertation], South China University of Technology, 2012. [3] 刘帅. 轻量级RFID双向认证协议研究[D]. [硕士论文], 南京信息工程大学, 2021.LIU Shuai. Research on two-way authentication protocol for lightweight RFID[D]. [Master dissertation], Nanjing University of Information Science & Technology, 2021. [4] 孙学军. 基于集群架构的物联网终端动态认证仿真[J]. 计算机仿真, 2020, 37(4): 312–316. doi: 10.3969/j.issn.1006-9348.2020.04.065SUN Xuejun. Simulation of internet of things terminal dynamic authentication based on cluster architecture[J]. Computer Simulation, 2020, 37(4): 312–316. doi: 10.3969/j.issn.1006-9348.2020.04.065 [5] HURJUI C and GRAUR A. Analysis of RFID security and privacy by means of identification and authentication protocols[C]. IEEE International Joint Conference on Computational Cybernetics and Technical Informatics, Timisoara, Romania, 2010: 315–320. [6] ELKAMCHOUCHI H M, EMARAH A A M, and HAGRAS E A A. A new public key dynamic signcrypted identification (PK-DS-ID) protocol using smart cards[C]. 2007 National Radio Science Conference, Cairo, Egypt, 2007: 1–10. [7] 何烜, 王红军, 袁泉. 可证明安全的射频识别双向认证协议[J]. 空军工程大学学报:自然科学版, 2018, 19(5): 41–46. doi: 10.3969/j.issn.1009-3516.2018.05.008HE Xuan, WANG Hongjun, and YUAN Quan. Provable secure two-way authentication protocol for radio frequency identification[J]. Journal of Air Force Engineering University:Natural Science Edition, 2018, 19(5): 41–46. doi: 10.3969/j.issn.1009-3516.2018.05.008 [8] 敬安奎. 基于区块链技术的车联网分层认证机制研究与应用[D]. [硕士论文], 重庆邮电大学, 2021.JING Ankui. Research and application of hierarchical authentication mechanism for VANETs based on blockchain technology[D]. [Master dissertation], Chongqing University of Posts and Telecommunications, 2021. [9] 潘梦函. 面向天地一体化信息网络的认证技术研究[D]. [硕士论文], 华东师范大学, 2022.PAN Menghan. Research on authentication technology for space-earth integration network[D]. [Master dissertation], East China Normal University, 2022. [10] ZHONG Hong, HAN Shunshun, CUI Jie, et al. Privacy-preserving authentication scheme with full aggregation in VANET[J]. Information Sciences, 2019, 476: 211–221. doi: 10.1016/j.ins.2018.10.021 [11] ALI I, HASSAN A, and LI Fagen. Authentication and privacy schemes for Vehicular Ad hoc NETworks (VANETs): A survey[J]. Vehicular Communications, 2019, 16: 45–61. doi: 10.1016/j.vehcom.2019.02.002 [12] 谢永, 李香, 张松松, 等. 一种可证安全的车联网无证书聚合签名改进方案[J]. 电子与信息学报, 2020, 42(5): 1125–1131. doi: 10.11999/JEIT190184XIE Yong, LI Xiang, ZHANG Songsong, et al. An improved provable secure certificateless aggregation signature scheme for vehicular Ad Hoc networks[J]. Journal of Electronics &Information Technology, 2020, 42(5): 1125–1131. doi: 10.11999/JEIT190184 [13] 黄睿. 物联网环境下基于多因素的用户隐私保护方案研究[D]. [硕士论文], 南京信息工程大学, 2020.HUANG Rui. Research on user privacy protection scheme based on multi-factor in internet of things[D]. [Master dissertation], Nanjing University of Information Science & Technology, 2020. [14] 周倜, 王巾盈, 李梦君, 等. Kerberos协议版本的分析与比较[J]. 计算机科学, 2009, 36(2): 119–121,128. doi: 10.3969/j.issn.1002-137X.2009.02.027ZHOU Ti, WANG Jinying, LI Mengjun, et al. Analysis and comparison of the Kerberos Protocol's versions[J]. Computer Science, 2009, 36(2): 119–121,128. doi: 10.3969/j.issn.1002-137X.2009.02.027 [15] 高昀. 面向泛在物联网的轻量安全通信协议研究[D]. [硕士论文], 华东师范大学, 2022.GAO Yun. Research on secure lightweight communication protocol for ubiquitous IoT[D]. [Master dissertation], East China Normal University, 2022. [16] FÁBREGA F J T, HERZOG J C, and GUTTMAN J D. Strand spaces: Proving security protocols correct[J]. Journal of Computer Security, 1999, 7(2/3): 191–230. doi: 10.3233/JCS-1999-72-304 [17] 陈海强, 韦文娟, 王留洋, 等. 基于周期分层重排构造的速率兼容凿孔极化码算法[J]. 电子学报, 2021, 49(6): 1125–1131. doi: 10.12263/DZXB.20190937CHEN Haiqiang, WEI Wenjuan, WANG Liuyang, et al. An algorithm for rate-compatible punctured polar codes based on hierarchical permutation structure[J]. Acta Electronica Sinica, 2021, 49(6): 1125–1131. doi: 10.12263/DZXB.20190937 [18] 王建华, 张岚. 检测类型缺陷的形式化构造攻击方法[J]. 密码学报, 2021, 8(6): 1058–1073. doi: 10.13868/j.cnki.jcr.000496WANG Jianhua and ZHANG Lan. A formal construction attack method for detecting type defects[J]. Journal of Cryptologic Research, 2021, 8(6): 1058–1073. doi: 10.13868/j.cnki.jcr.000496 [19] ELKAMCHOUCHI H M, EMARAH A A M, and HAGRAS E A A. A new public key signcrypted challenge response identification (PKS-CR-ID) protocol using smart cards[C]. The 2006 International Conference on Computer Engineering and Systems, Cairo, Egypt, 2006: 244–249. -





 下载:
下载:

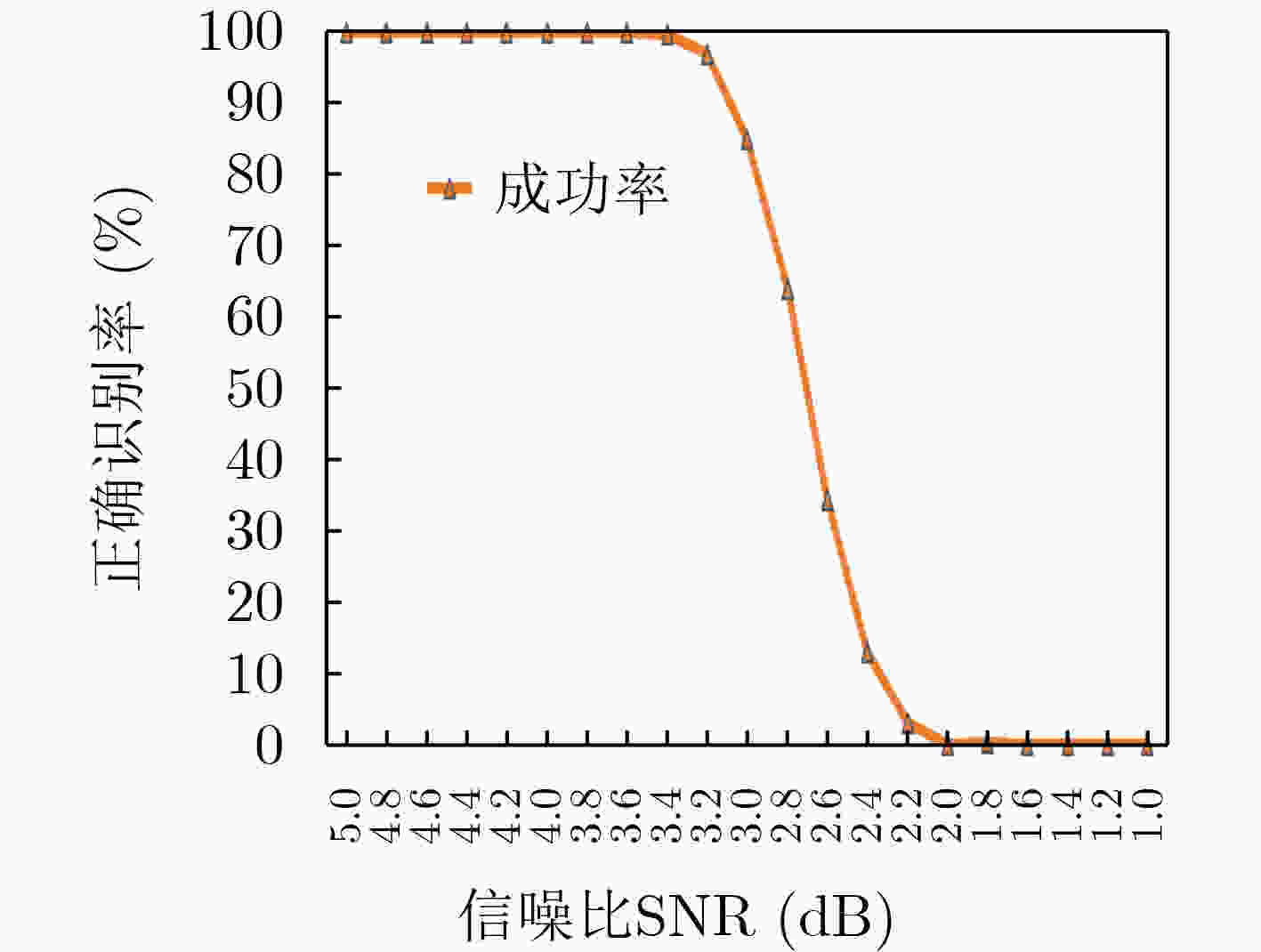
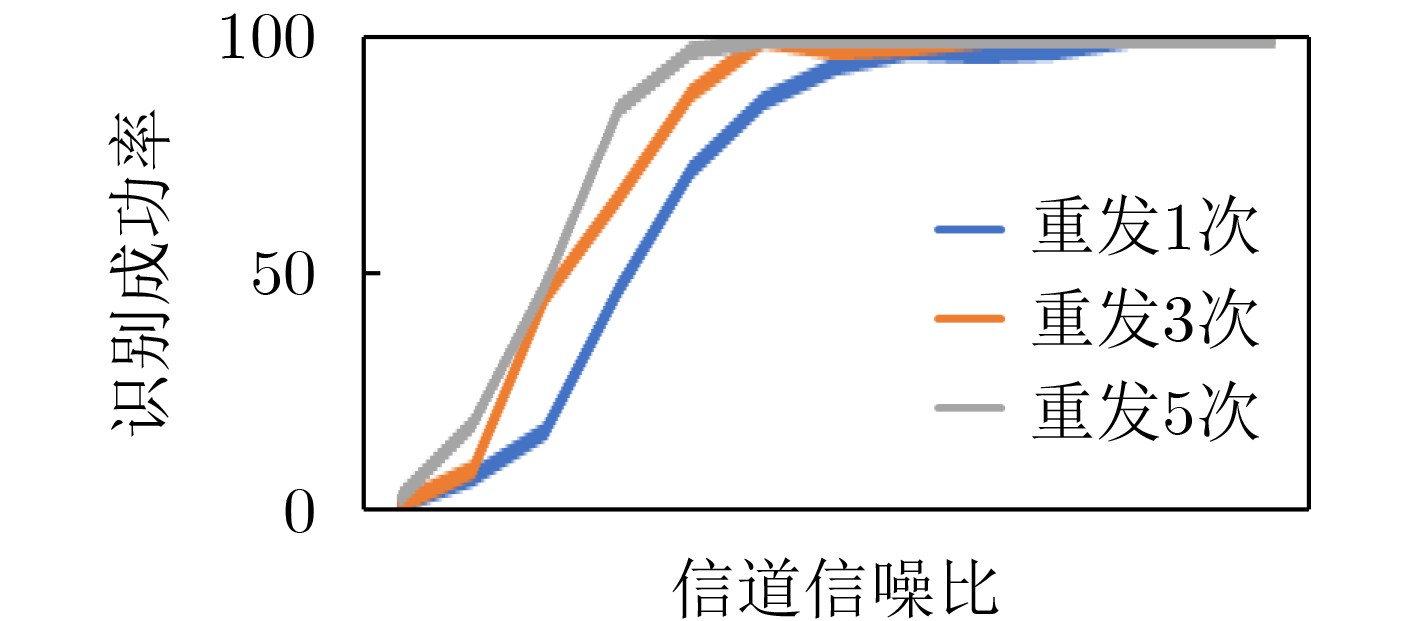


 下载:
下载:
