CertificateLess Pairing-Free SignCryption for Network Coding
-
摘要: 网络编码允许中间节点对数据包先编码再转发,提高了系统的鲁棒性并节约网络资源。实际应用中网络编码容易受到污染攻击,鉴于此,该文提出网络编码环境下无双线性对的无证书签密(NC-CLPFSC)。NC-CLPFSC通过同态哈希函数防御污染攻击,而且还避免了密钥托管和证书管理,同时降低了计算和通信成本。Abstract: Network coding allows the intermediate nodes to encode and forward the data packets, so it improves the system robustness and saves the network resources. Pollution attacks are inevitable for network coding in applications. In view of this, CertificateLess Pairing-Free SignCryption for Network Coding (NC-CLPFSC) is proposed. NC-CLPFSC uses the homomorphic Hash function to resist the pollution attacks; Moreover, it avoids the key escrow and certificate management, and it reduces the computation and communication cost.
-
表 1 各密码操作的计算时间(ms)
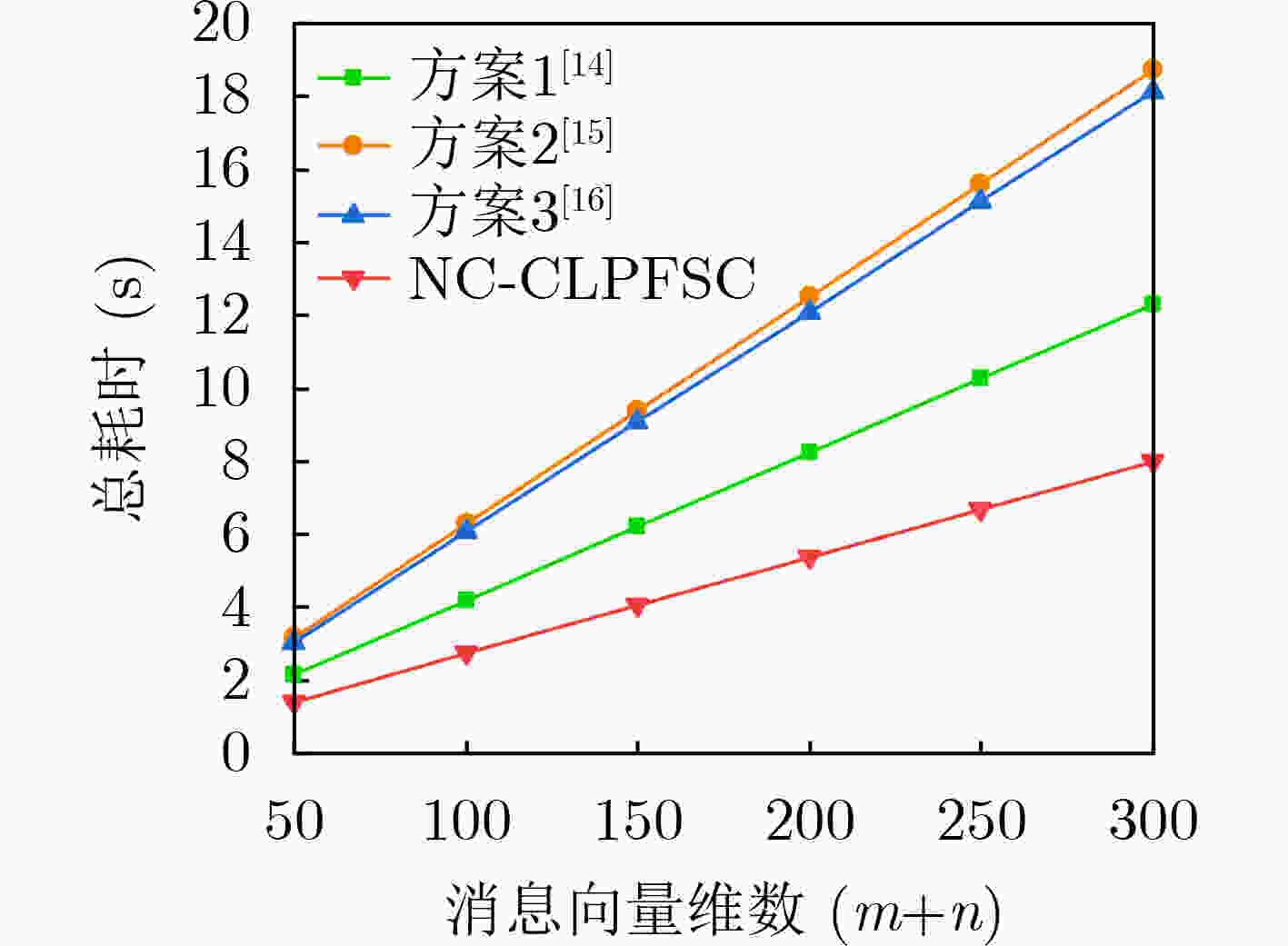
符号 执行操作 所需时间 Tec 1次指数运算 4.77 Tbp 1次双线性对运算 14.77 TH 1次哈希运算 12.02 Tmul 1次标量乘运算 0.02 表 2 分段耗时比较(ms)
-
[1] AHLSWEDE R, CAI Ning, LI S Y R, et al. Network information flow[J]. IEEE Transactions on Information Theory, 2000, 46(4): 1204–1216. doi: 10.1109/18.850663 [2] IQBAL M A, DAI Bin, HUANG Benxiong, et al. Survey of network coding-aware routing protocols in wireless networks[J]. Journal of Network and Computer Applications, 2011, 34(6): 1956–1970. doi: 10.1016/j.jnca.2011.07.012 [3] 周秀媛, 王彩芬, 罗海. 基于RSA的多源网络编码签名方案[J]. 计算机工程与设计, 2012, 33(5): 1752–1756. doi: 10.3969/j.issn.1000-7024.2012.05.016ZHOU Xiuyuan, WANG Caifen, and LUO Hai. RSA-based signature scheme for multi-source network coding[J]. Computer Engineering and Design, 2012, 33(5): 1752–1756. doi: 10.3969/j.issn.1000-7024.2012.05.016 [4] YAN Wenjie, YANG Mingxi, LI Layuan, et al. Short signature scheme for multi-source network coding[J]. Computer Communications, 2012, 35(3): 344–351. doi: 10.1016/j.comcom.2011.10.012 [5] WU Chenhuang and CHEN Zhixiong. A new efficient certificateless signcryption scheme[C]. 2008 International Symposium on Information Science and Engineering, Shanghai, China, 2008: 661–664. [6] SELVI S S D, VIVEK S S, and RANGAN C P. Cryptanalysis of certificateless signcryption schemes and an efficient construction without pairing[C]. 5th International Conference on Information Security and Cryptology, Beijing, China, 2010: 75–92. [7] 陈虹, 赵悦, 肖成龙, 等. 可证安全的无对运算的无证书签密方案[J]. 计算机应用研究, 2019, 36(3): 907–910,917. doi: 10.19734/j.issn.1001-3695.2017.09.0937CHEN Hong, ZHAO Yue, XIAO Chenglong, et al. Certificateless signcryption scheme of verifiable security without pairing[J]. Application Research of Computers, 2019, 36(3): 907–910,917. doi: 10.19734/j.issn.1001-3695.2017.09.0937 [8] 周彦伟, 杨波, 王青龙. 安全的无双线性映射的无证书签密机制[J]. 软件学报, 2017, 28(10): 2757–2768. doi: 10.13328/j.cnki.jos.005150ZHOU Yanwei, YANG Bo, and WANG Qinglong. Secure certificateless signcryption scheme without bilinear pairing[J]. Journal of Software, 2017, 28(10): 2757–2768. doi: 10.13328/j.cnki.jos.005150 [9] 高改梅, 彭新光, 秦泽峰. 无双线性映射的无证书签密方案[J]. 中北大学学报:自然科学版, 2019, 40(2): 118–125. doi: 10.3969/j.issn.1673-3193.2019.02.005GAO Gaimei, PENG Xinguang, and QIN Zefeng. Certificateless signcryption scheme without bilinear pairing[J]. Journal of North University of China (Natural Science Edition), 2019, 40(2): 118–125. doi: 10.3969/j.issn.1673-3193.2019.02.005 [10] RAM M, TYAGI S, KUMAR A, et al. Analysis of signature reliability of ring-shaped network system[J]. International Journal of Quality & Reliability Management, 2022, 39(3): 804–814. doi: 10.1108/IJQRM-04-2021-0113 [11] YU Huifang and WANG Weike. Certificateless network coding ring signature scheme[J]. Security and Communication Networks, 2021, 2021: 8029644. doi: 10.1155/2021/8029644 [12] HO T, MEDARD M, KOETTER R, et al. A random linear network coding approach to multicast[J]. IEEE Transactions on Information Theory, 2006, 52(10): 4413–4430. doi: 10.1109/TIT.2006.881746 [13] 俞惠芳, 杨波. 使用ECC的身份混合签密方案[J]. 软件学报, 2015, 26(12): 3174–3182. doi: 10.13328/j.cnki.jos.004819YU Huifang and YANG Bo. Identity-based hybrid signcryption scheme using ECC[J]. Journal of Software, 2015, 26(12): 3174–3182. doi: 10.13328/j.cnki.jos.004819 [14] WU Bin, WANG Caifen, and YAO Hailong. A certificateless linearly homomorphic signature scheme for network coding and its application in the IoT[J]. Peer-to-Peer Networking and Applications, 2021, 14(2): 852–872. doi: 10.1007/s12083-020-01028-8 [15] 俞惠芳, 高新哲. 多源网络编码同态环签名方案研究[J]. 信息网络安全, 2019, 19(2): 36–42. doi: 10.3969/j.issn.1671-1122.2019.02.005YU Huifang and GAO Xinzhe. Homomorphic ring signature scheme technology for multi-source network coding[J]. Netinfo Security, 2019, 19(2): 36–42. doi: 10.3969/j.issn.1671-1122.2019.02.005 [16] 杨文山. 网络编码中的椭圆曲线多重签名方案[J]. 信息安全与通信保密, 2022(8): 112–120. doi: 10.3969/j.issn.1009-8054.2022.08.013YANG Wenshan. Elliptic curve multi-signature scheme for network coding[J]. Information Security and Communications Privacy, 2022(8): 112–120. doi: 10.3969/j.issn.1009-8054.2022.08.013 -





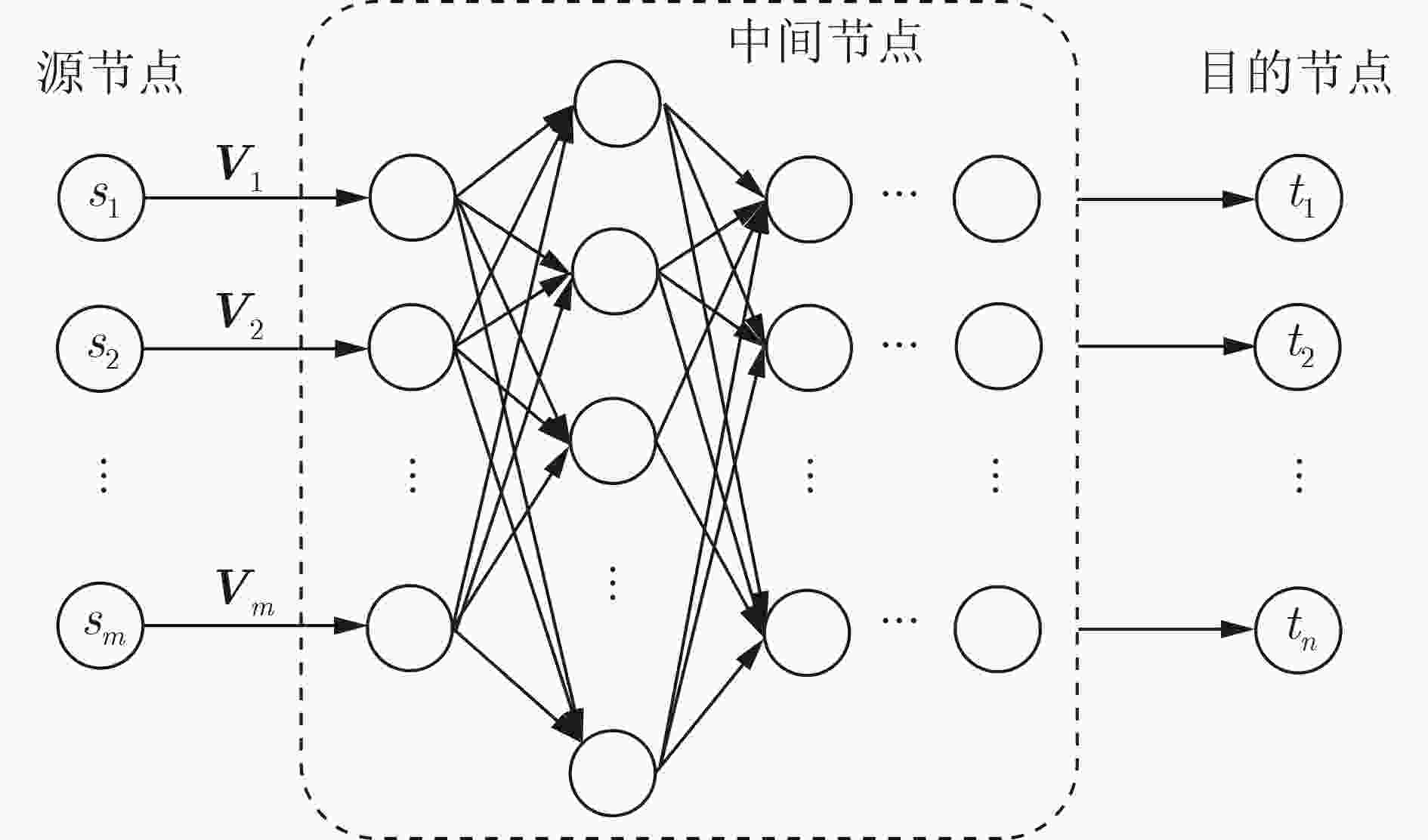
 下载:
下载:
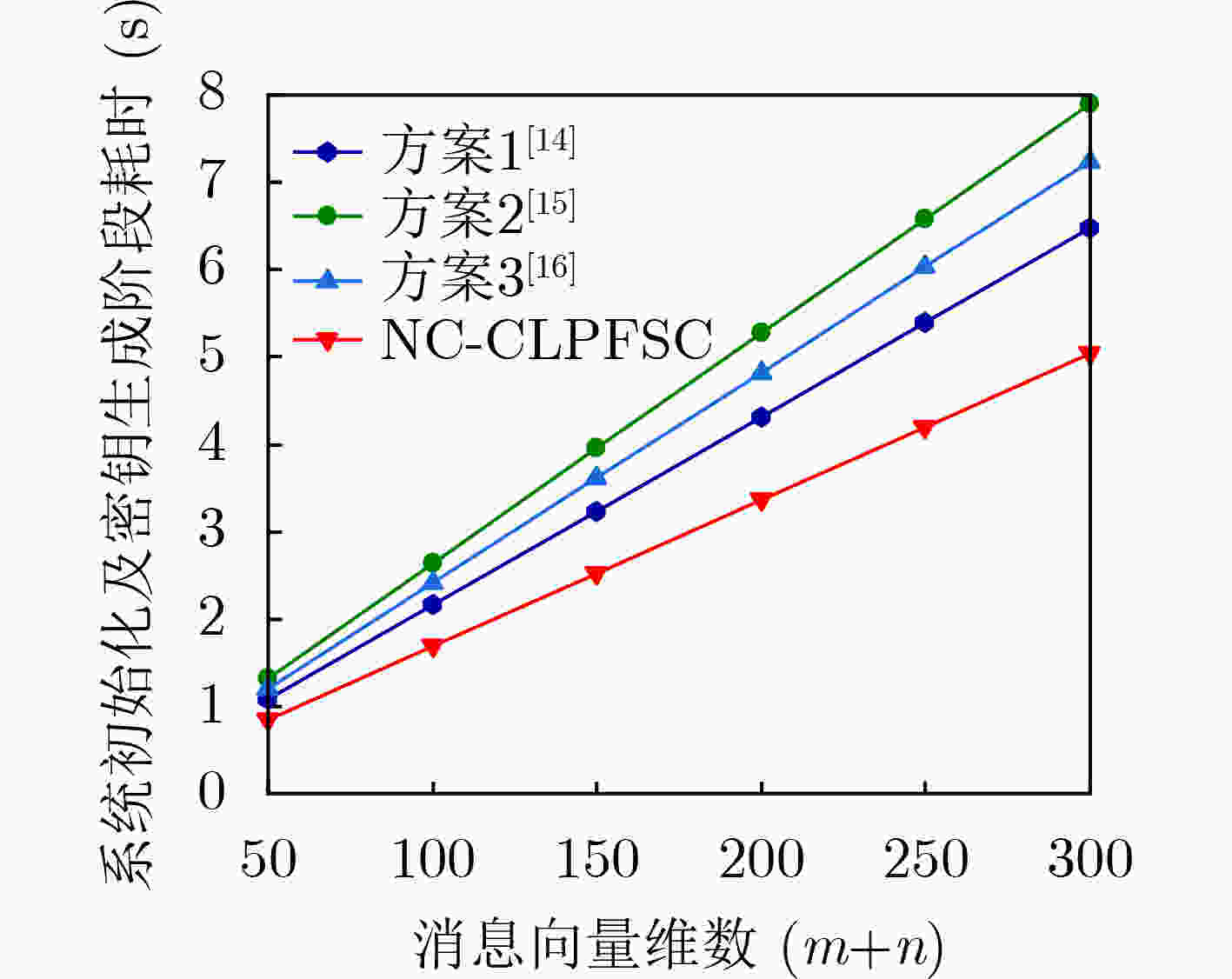
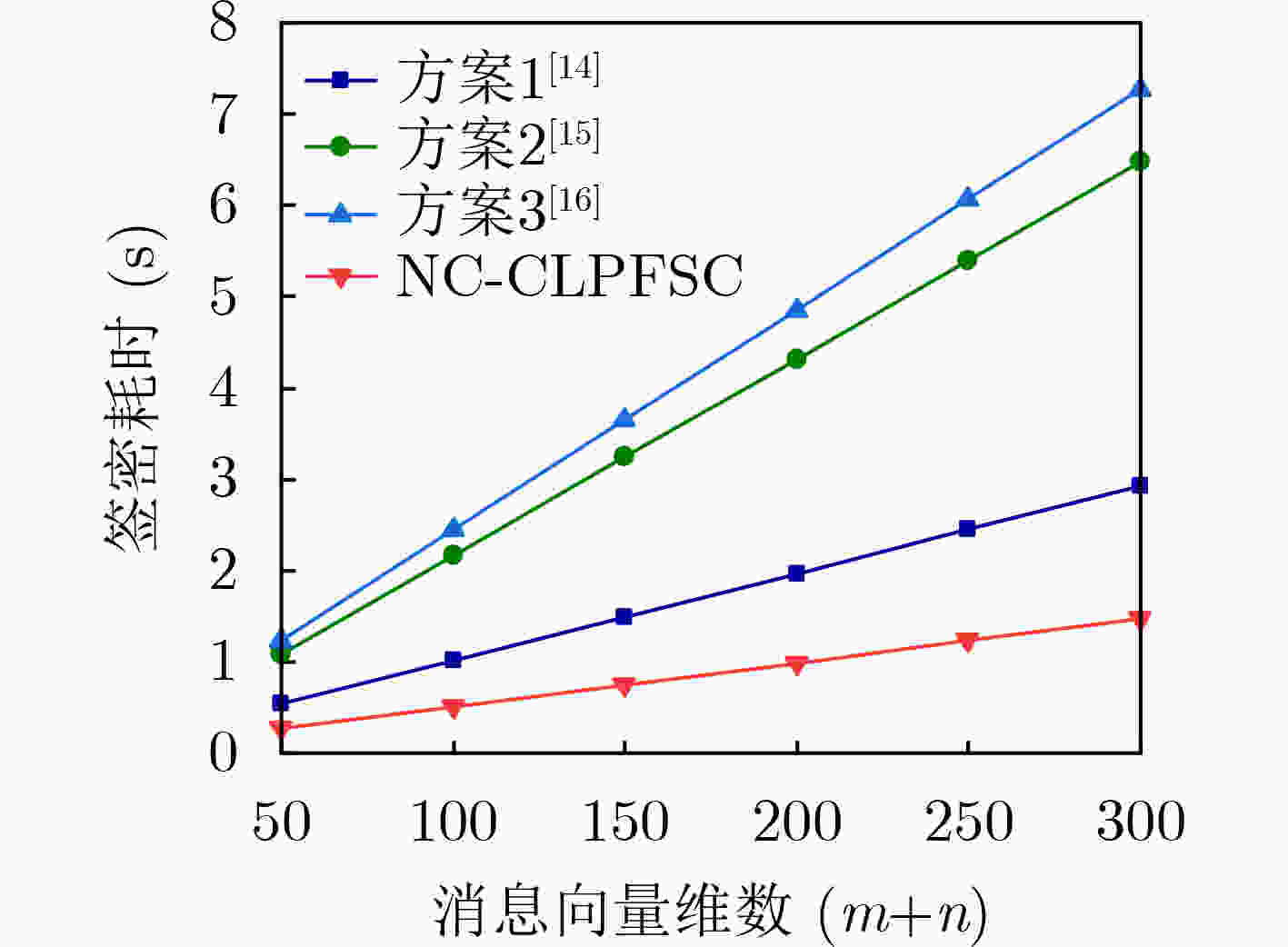
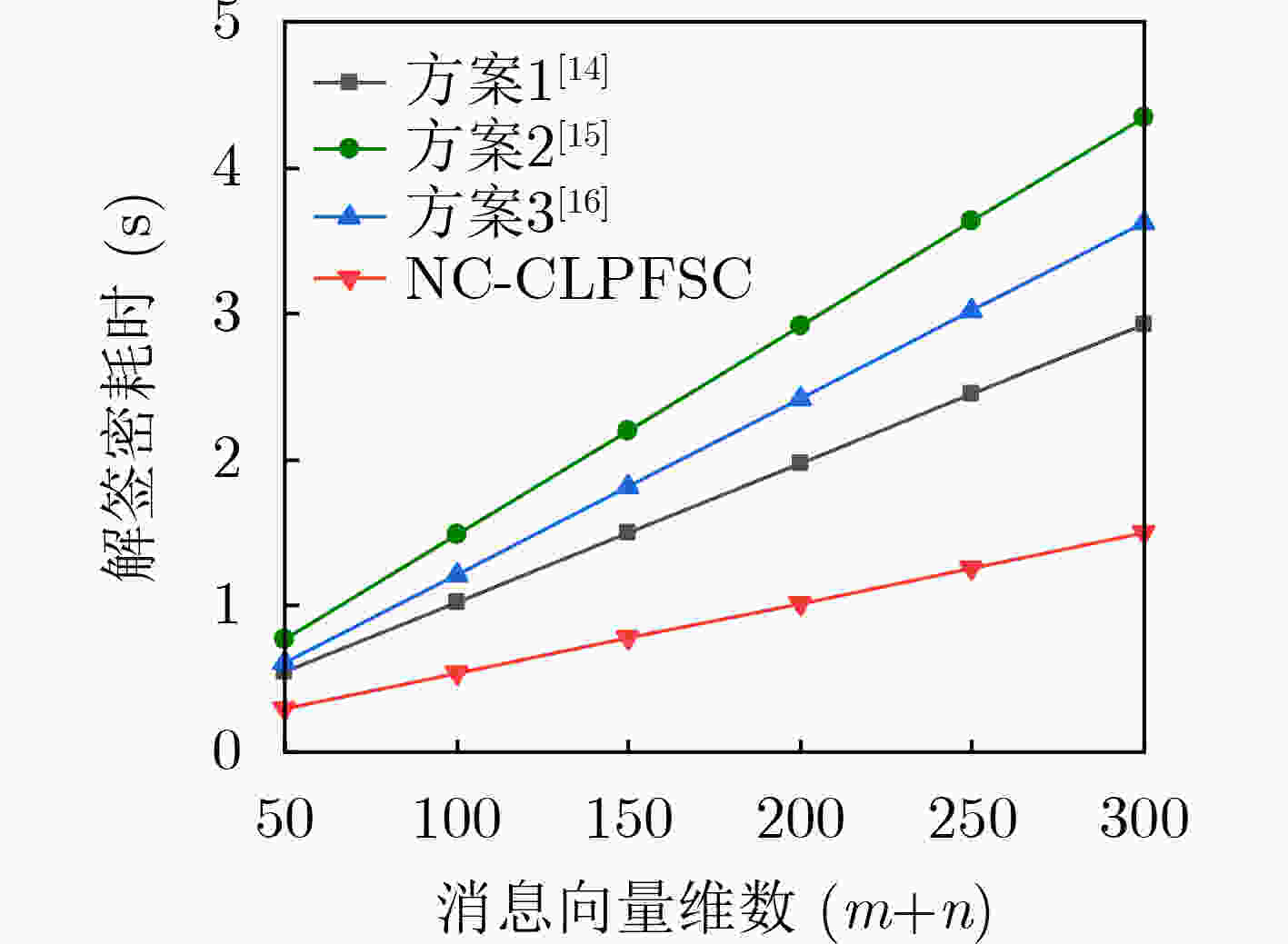


 下载:
下载:
