Preview-supported Copyright Image Sharing
-
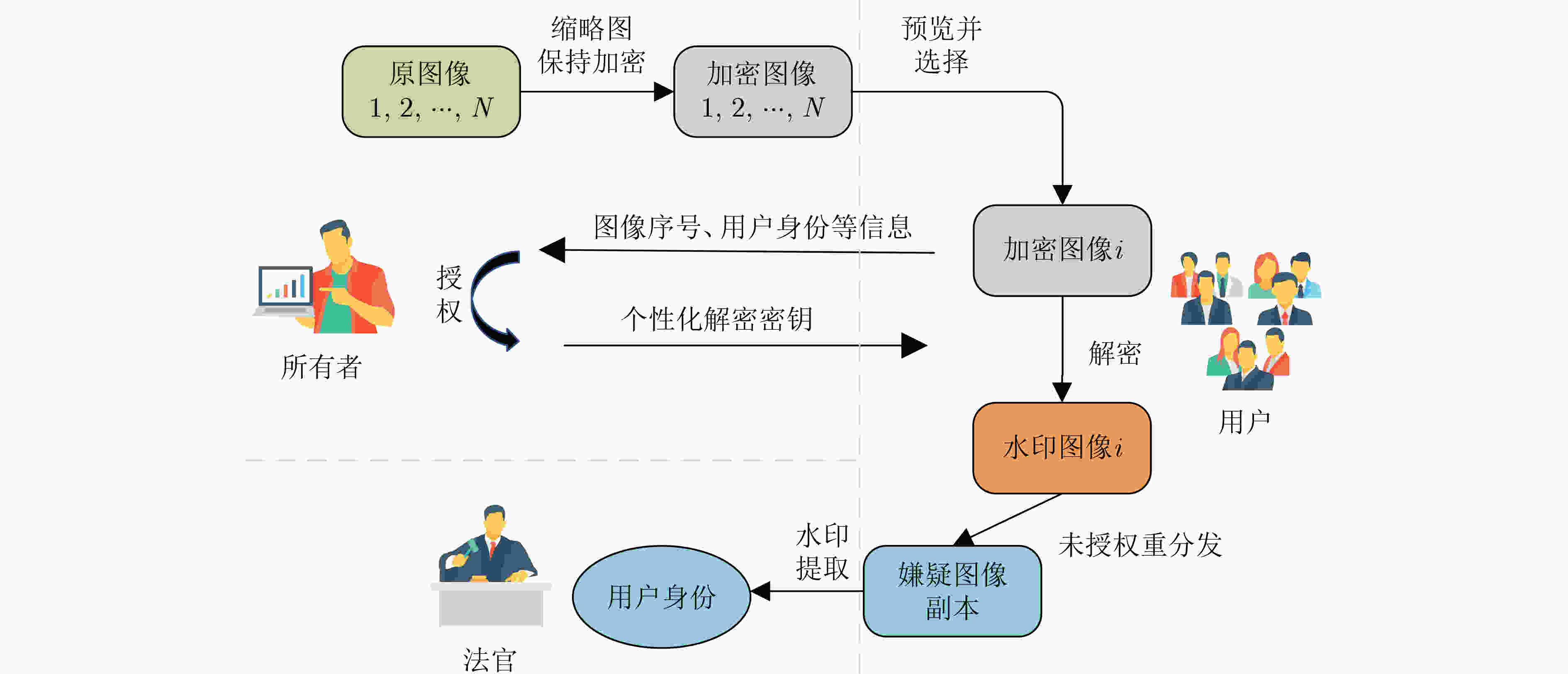
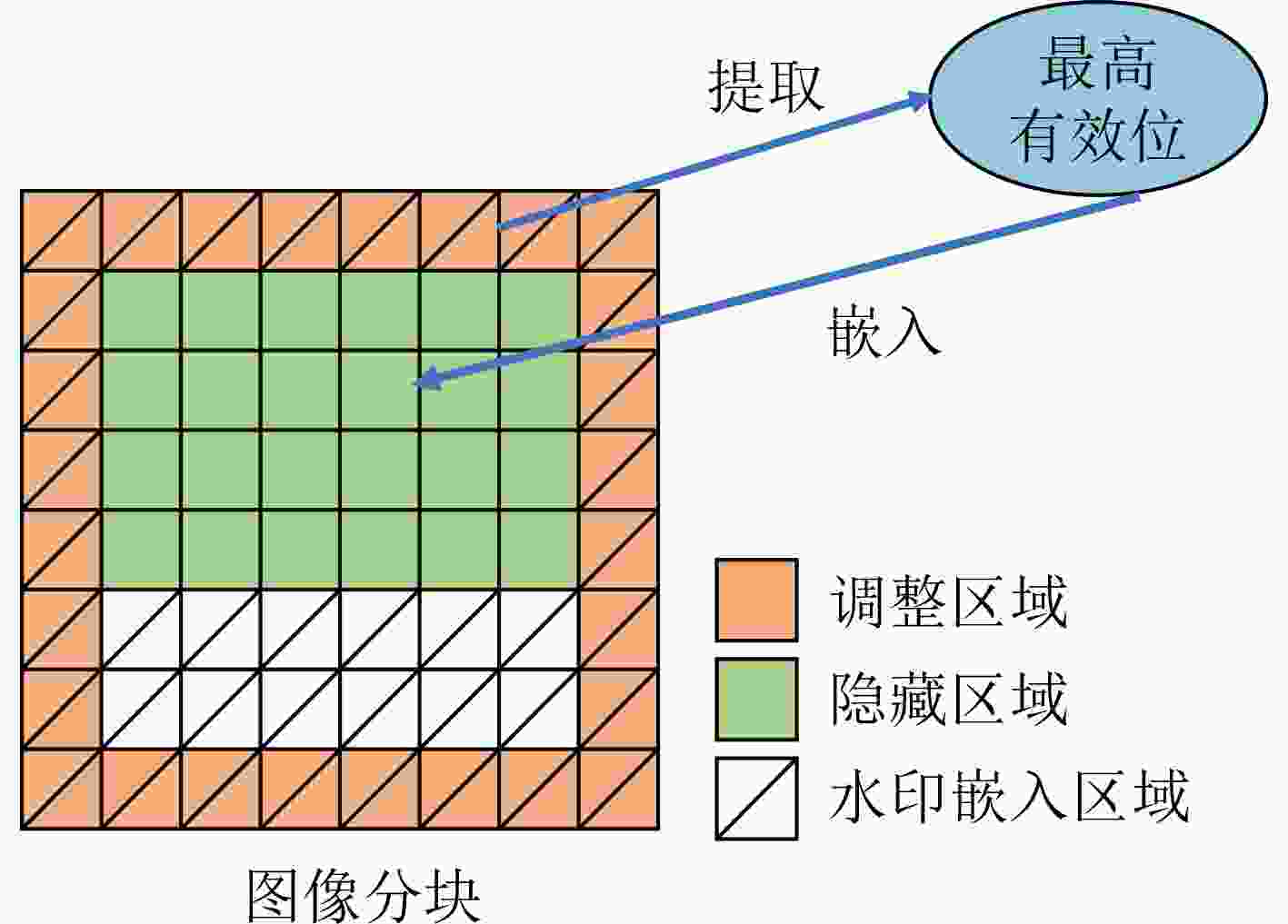
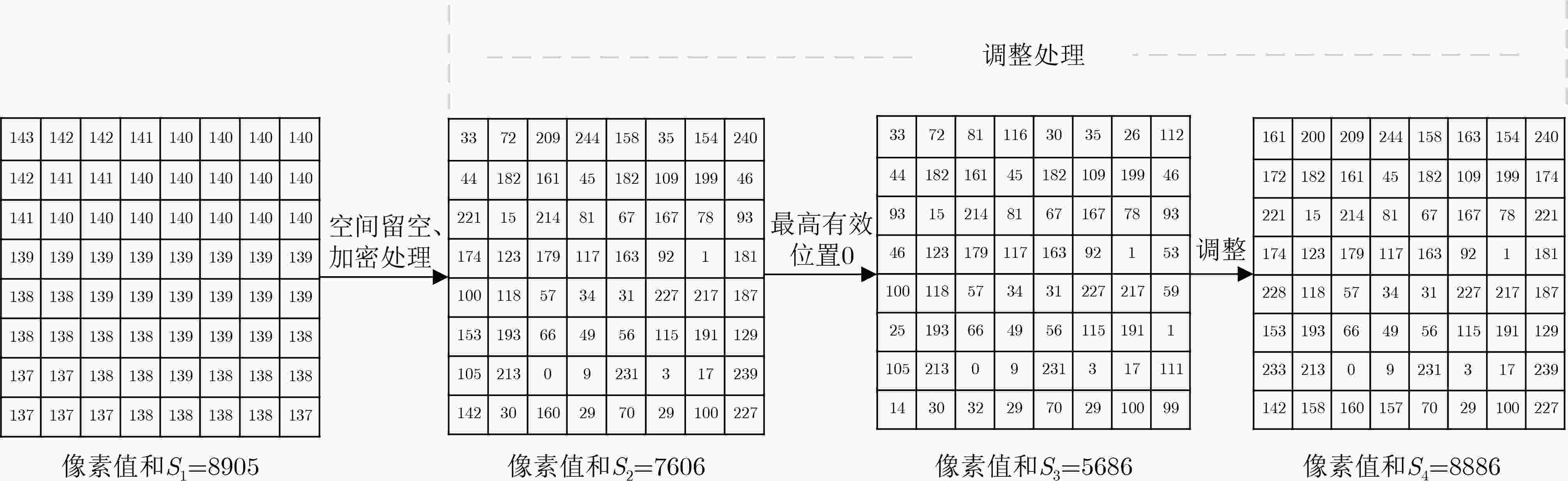
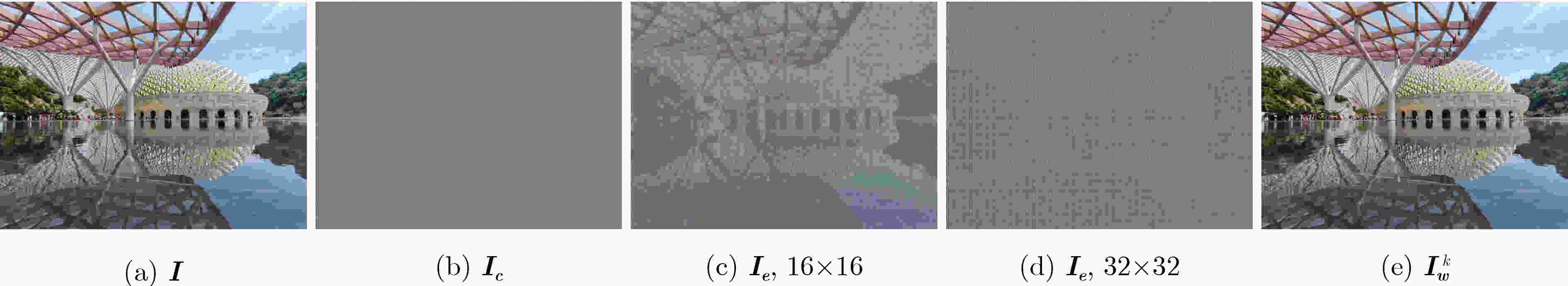
摘要: 针对数字水印技术均不考虑版权图像共享场景中用户的预览需求,以及软件控制方法和附加信息方法的局限性,该文提出一个支持直接从加密图像预览原图像部分视觉内容的版权图像共享方案。为此,将缩略图保持加密的思想引入到用户端嵌入的水印方案中,通过像素调整在加密图像上呈现原图像内容的模糊版本。用于调整的像素位被事先以信息隐藏的方法嵌入隐藏区域中,以保证解密的正确性。此外,用户水印被在解密的同时嵌入到图像中,用于实现对未授权重分发行为的追踪。这样一来,不仅满足了共享过程中用户的预览需求还同时保护了图像的版权。理论分析和实验测试的结果展现了所提方案的安全性、可行性、高效性和鲁棒性。Abstract: In view of the fact that digital watermarking technology does not consider the preview needs of users in copyright image sharing scenarios, as well as the limitations of software control method and additional information method, a copyright image sharing scheme that supports previewing part of the visual content of the original image directly from the encrypted image is proposed. To this end, the idea of thumbnail preserving encryption is introduced into the user-side embedded watermarking scheme, and a blurred version of the original image content is presented on the encrypted image through pixel adjustment. The pixel bits to be adjusted are embedded into the hidden area by means of information hiding in advance to ensure the correctness of decryption. Moreover, the user watermark is embedded into the image at the same time of decryption, which is used to track the unauthorized redistribution behavior. In this way, not only the preview needs of the user during the sharing process is met, but also the copyright of the image is protected. The results of theoretical analysis and experimental tests demonstrate the security, feasibility, efficiency, and robustness of the proposed scheme.
-
Key words:
- Digital watermarking /
- Image encryption /
- Data hiding /
- Error-correcting codes
-
表 1 嵌入容量测试(bit)
嵌入容量 P = 0.516×16 P = 0.524×24 P = 0.532×32 P = 0.616×16 P = 0.624×24 P = 0.632×32 P = 0.716×16 P = 0.724×24 P = 0.732×32 总共 7271627 7980867 8347396 8310384 9431922 10016959 9349242 10883018 11686490 所需 7704471 4436131 3460688 7778008 5077061 3871760 7845654 5180320 3992396 剩余 –432844 3544736 4886708 532376 4354861 6145199 1503588 5702698 7694094 -
[1] CELIK M U, LEMMA A N, KATZENBEISSER S, et al. Lookup-table-based secure client-side embedding for spread-spectrum watermarks[J]. IEEE Transactions on Information Forensics and Security, 2008, 3(3): 475–487. doi: 10.1109/TIFS.2008.926988 [2] 钟桦, 刘芳, 焦李成. 基于图像特征的易损水印技术[J]. 电子与信息学报, 2003, 25(11): 1482–1487.ZHONG Hua, LIU Fang, and JIAO Licheng. A novel fragile watermark technique based on image feature[J]. Journal of Electronics and Information Technology, 2003, 25(11): 1482–1487. [3] RHAYMA H, MAKHLOUFI A, HAMAM H, et al. Semi-fragile watermarking scheme based on perceptual hash function (PHF) for image tampering detection[J]. Multimedia Tools and Applications, 2021, 80(17): 26813–26832. doi: 10.1007/s11042-021-10886-0 [4] 张天骐, 周琳, 梁先明, 等. 基于Blob-Harris特征区域和NSCT-Zernike的鲁棒水印算法[J]. 电子与信息学报, 2021, 43(7): 2038–2045. doi: 10.11999/JEIT200164ZHANG Tianqi, ZHOU Lin, LIANG Xianming, et al. A robust watermarking algorithm based on Blob-Harris and NSCT- Zernike[J]. Journal of Electronics &Information Technology, 2021, 43(7): 2038–2045. doi: 10.11999/JEIT200164 [5] VALIZADEH A and WANG Z J. An improved multiplicative spread spectrum embedding scheme for data hiding[J]. IEEE Transactions on Information Forensics and Security, 2012, 7(4): 1127–1143. doi: 10.1109/TIFS.2012.2199312 [6] CHEN B and WORNELL G W. Achievable performance of digital watermarking systems[C]. IEEE International Conference on Multimedia Computing and Systems, Florence, Italy, 1999: 13–18. [7] TẠ M T and GIANG N D. Robust watermarking method using QIM with VSS for image copyright protection[J]. Journal of Research and Development on Information & Communication Technology, 2021, 2021(1): 28–40. doi: 10.32913/mic-ict-research.v2021.n1.971 [8] PATEL H A and SHAH D B. Digital watermarking system performance using QIM techniques and wavelet transforms[M]. GOYAL D, CHATURVEDI P, NAGAR A K, et al. Proceedings of Second International Conference on Smart Energy and Communication. Singapore: Springer, 2021: 699–711. [9] COX I J, KILIAN J, LEIGHTON F T, et al. Secure spread spectrum watermarking for multimedia[J]. IEEE Transactions on Image Processing, 1997, 6(12): 1673–1687. doi: 10.1109/83.650120 [10] MAIRGIOTIS A K, GALATSANOS N P, and YANG Yongyi. New additive watermark detectors based on a hierarchical spatially adaptive image model[J]. IEEE Transactions on Information Forensics and Security, 2008, 3(1): 29–37. doi: 10.1109/TIFS.2007.916290 [11] CANNONS J and MOULIN P. Design and statistical analysis of a hash-aided image watermarking system[J]. IEEE Transactions on Image Processing, 2004, 13(10): 1393–1408. doi: 10.1109/TIP.2004.834660 [12] PIVA A, BIANCHI T, and DE ROSA A. Secure client-side ST-DM watermark embedding[J]. IEEE Transactions on Information Forensics and Security, 2010, 5(1): 13–26. doi: 10.1109/TIFS.2009.2038761 [13] WRIGHT C V, FENG Wuchi, and LIU Feng. Thumbnail-preserving encryption for JPEG[C]. The 3rd ACM Workshop on Information Hiding and Multimedia Security, Portland, United States, 2015: 141–146. [14] MAROHN B, WRIGHT C V, FENG Wuchi, et al. Approximate thumbnail preserving encryption[C]. The 2017 on Multimedia Privacy and Security, Dallas, United States, 2017: 33–43. [15] ZHANG Yushu, ZHAO Ruoyu, XIAO Xiangli, et al. HF-TPE: High-fidelity thumbnail-preserving encryption[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2022, 32(3): 947–961. doi: 10.1109/TCSVT.2021.3070348 [16] TAJIK K, GUNASEKARAN A, DUTTA R, et al. Balancing image privacy and usability with thumbnail-preserving encryption[C]. Network and Distributed Systems Security (NDSS) Symposium 2019, San Diego, United States, 2019: 295. [17] ZHAO Ruoyu, ZHANG Yushu, XIAO Xiangli, et al. TPE2: Three-pixel exact thumbnail-preserving image encryption[J]. Signal Processing, 2021, 183: 108019. doi: 10.1016/j.sigpro.2021.108019 [18] 侯兴旺, 赵若宇, 张玉书. 一种精确缩略图保持的图像加密方案[J]. 计算机工程与科学, 2022, 44(1): 60–67. doi: 10.3969/j.issn.1007-130X.2022.01.007HOU Xingwang, ZHAO Ruoyu, and ZHANG Yushu. An exact thumbnail-preserving image encryption scheme[J]. Computer Engineering &Science, 2022, 44(1): 60–67. doi: 10.3969/j.issn.1007-130X.2022.01.007 [19] TIAN Jun. Reversible data embedding using a difference expansion[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2003, 13(8): 890–896. doi: 10.1109/TCSVT.2003.815962 [20] WANG Yaomin and HE Wenguang. High capacity reversible data hiding in encrypted image based on adaptive MSB prediction[J]. IEEE Transactions on Multimedia, 2022, 24: 1288–1298. doi: 10.1109/TMM.2021.3062699 [21] WU Youqing, XIANG Youzhi, GUO Yutang, et al. An improved reversible data hiding in encrypted images using parametric binary tree labeling[J]. IEEE Transactions on Multimedia, 2020, 22(8): 1929–1938. doi: 10.1109/TMM.2019.2952979 [22] BIANCHI T and PIVA A. TTP-free asymmetric fingerprinting based on client side embedding[J]. IEEE Transactions on Information Forensics and Security, 2014, 9(10): 1557–1568. doi: 10.1109/TIFS.2014.2340581 -






 下载:
下载:
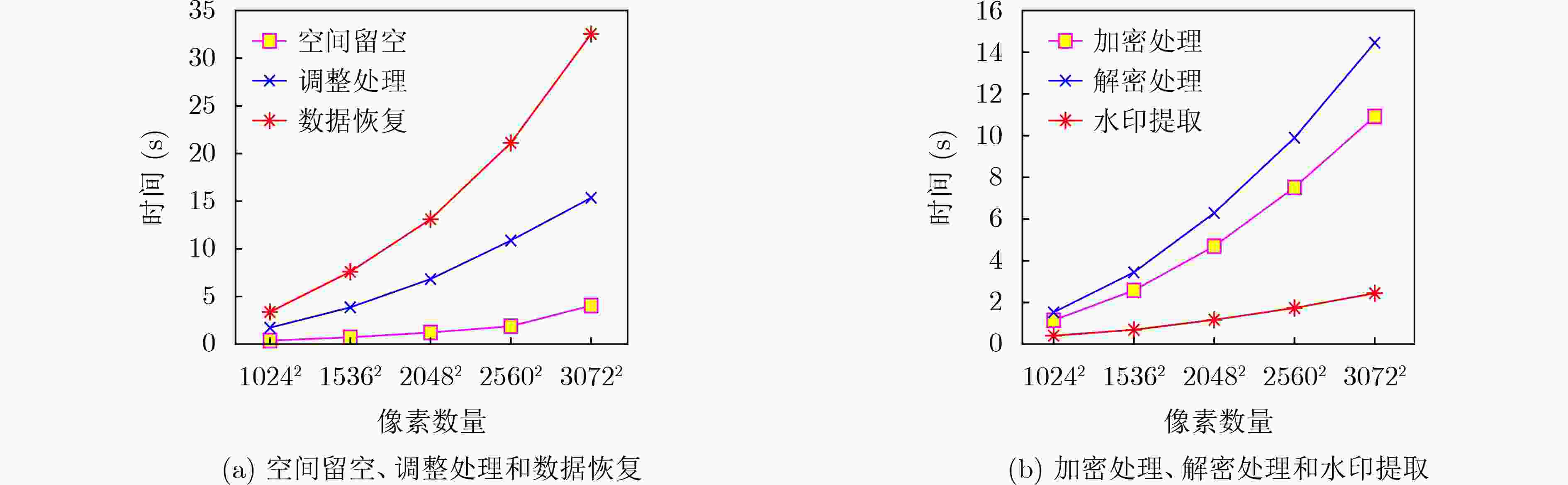



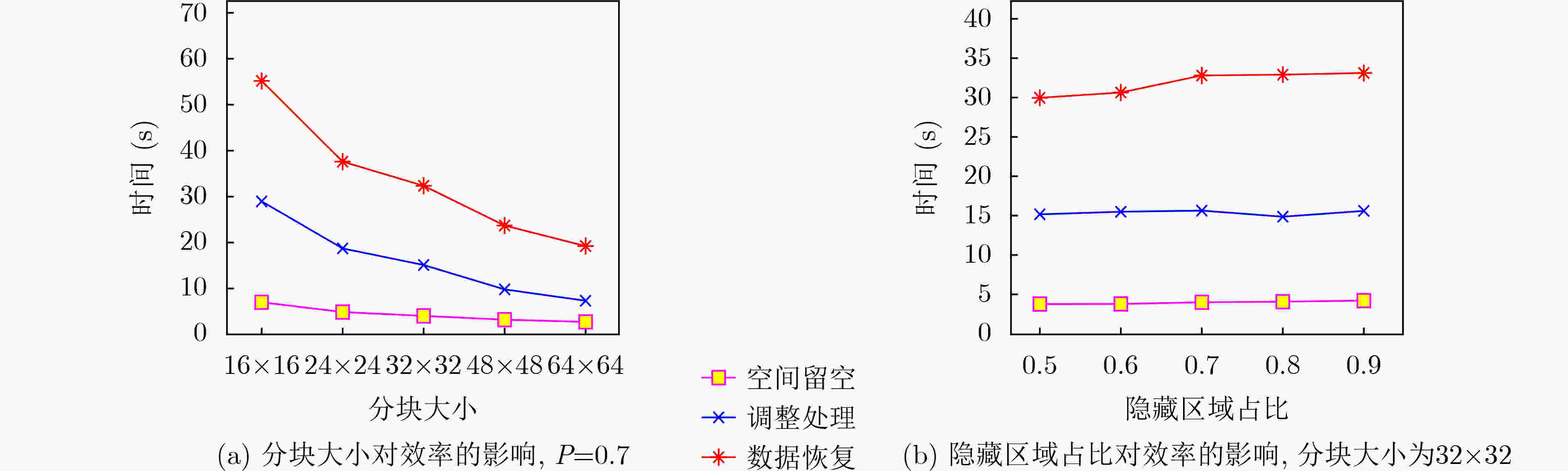
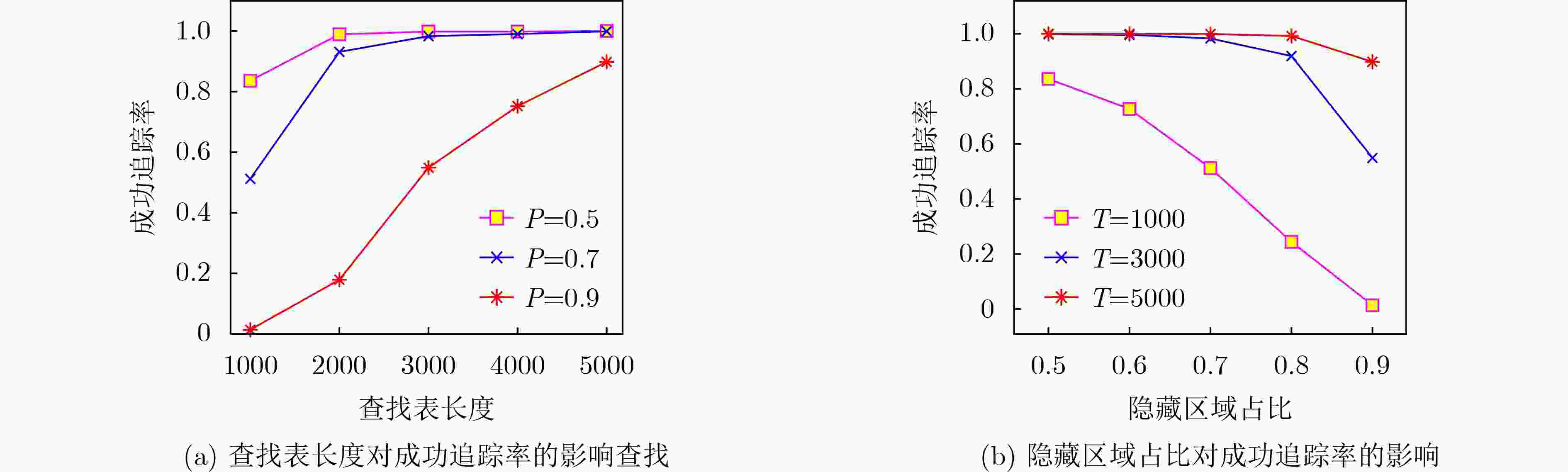


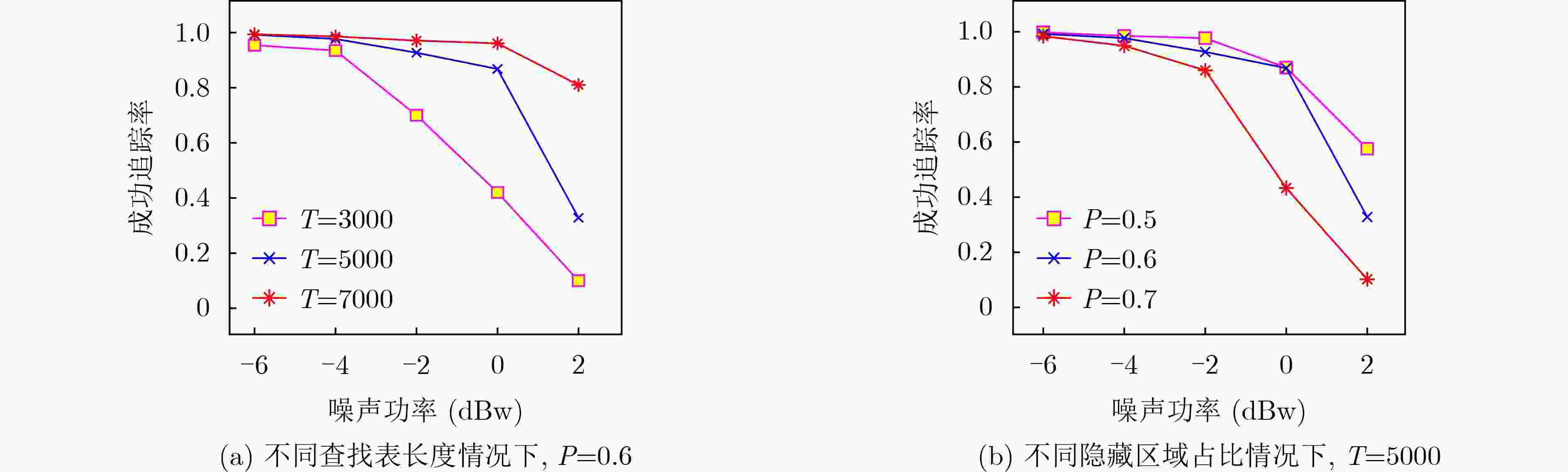




 下载:
下载:
