Linear Discriminant Analysis Algorithm for Detecting Hardware Trojans Delay
-
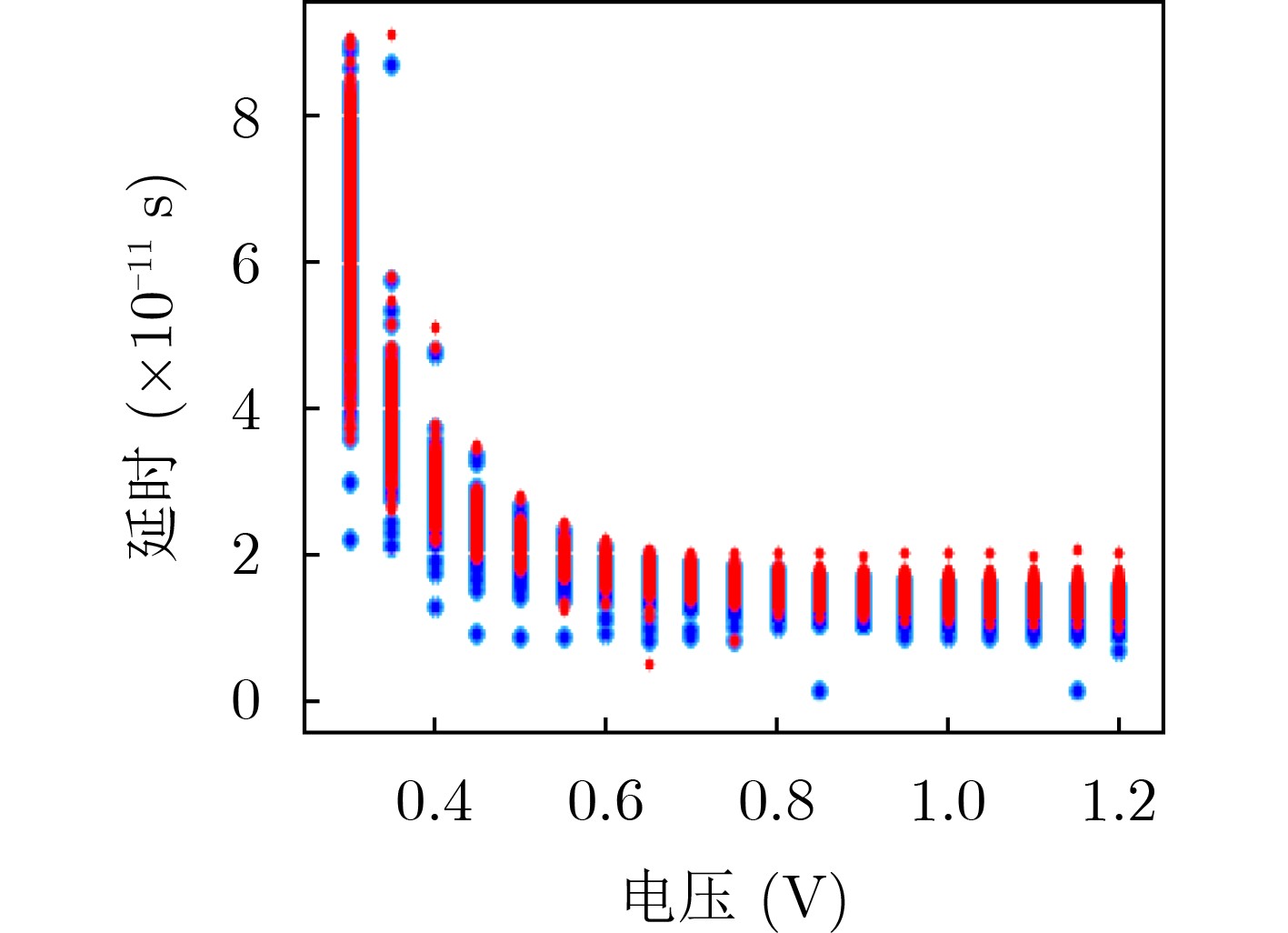
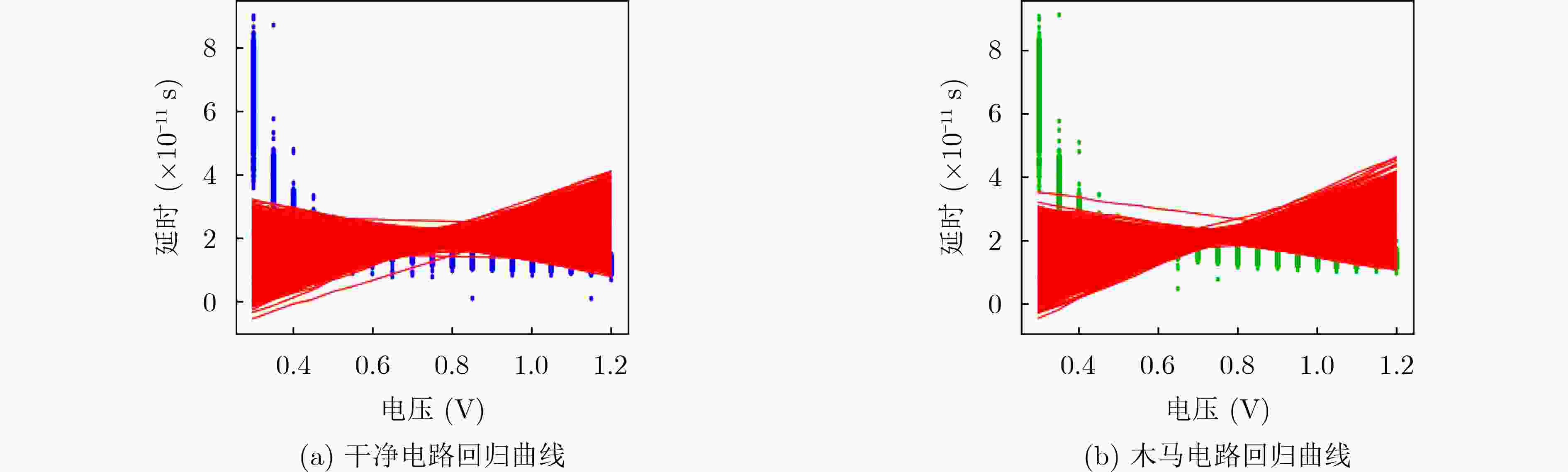
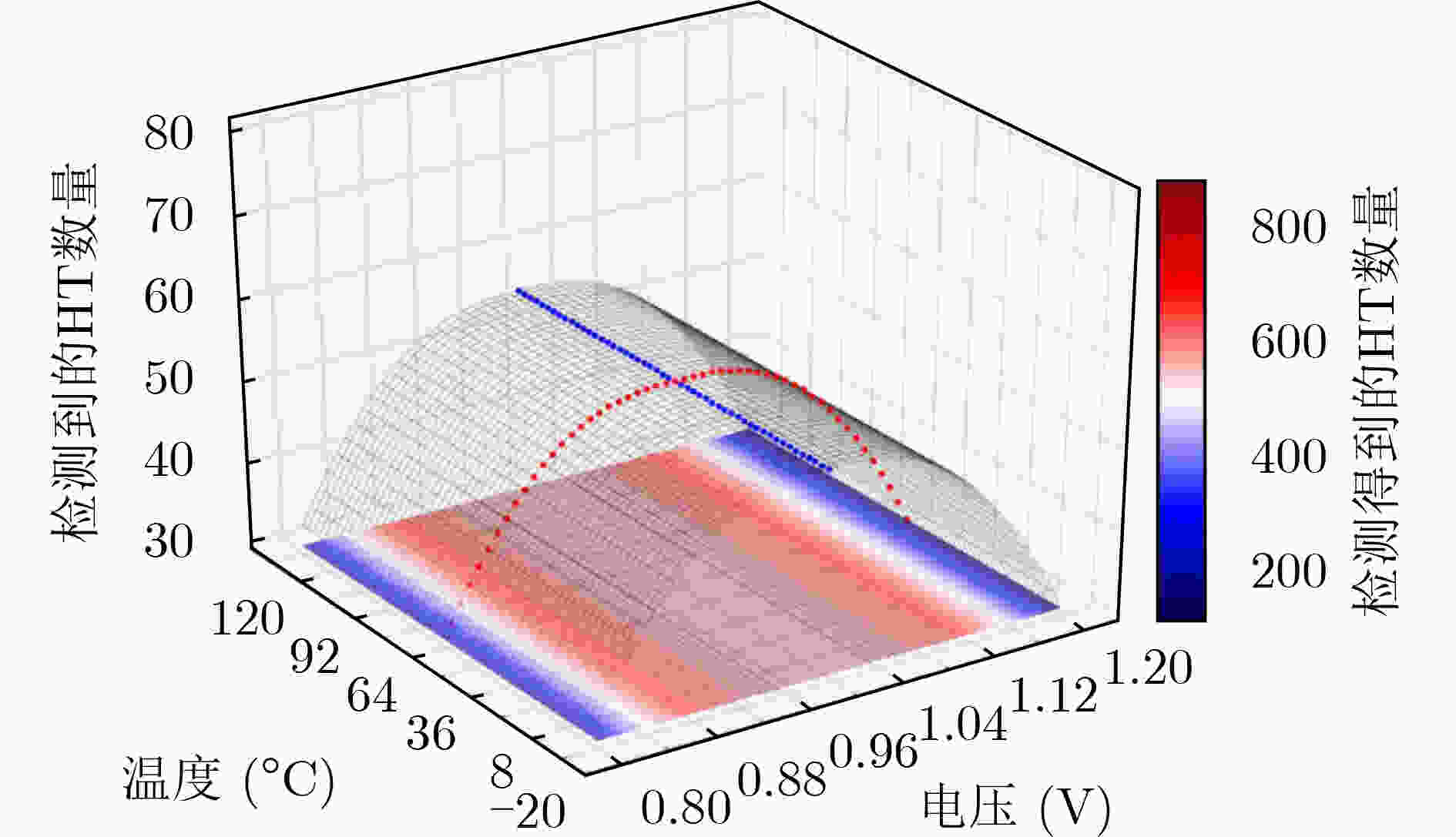
摘要: 针对芯片生产链长、安全性差、可靠性低,导致硬件木马防不胜防的问题,该文提出一种针对旁路信号分析的木马检测方法。首先采集不同电压下电路的延时信号,通过线性判别分析(LDA)分类算法找出延时差异,若延时与干净电路相同,则判定为干净电路,否则判定有木马。然后联合多项式回归算法对木马延时特征进行拟合,基于回归函数建立木马特征库,最终实现硬件木马的准确识别。实验结果表明,提出的LDA联合线性回归(LR)算法可以根据延时特征识别木马电路,其木马检测率优于其他木马检测方法。更有利的是,随着电路规模的增大意味着数据量的增加,这更便于进行数据分析与特征提取,降低了木马检测难度。通过该方法的研究,对未来工艺极限下识别木马电路、提高芯片安全性与可靠性具有重要的指导作用。Abstract: To solve the security problems of long chip production chain, poor security and low reliability, leading to prevent Hardware Trojan (HT) detection, an HT detection method based on bypass signal analysis is proposed, by means of Linear Discriminant Analysis (LDA) classification algorithm to find the difference in time delay so as to distinguish HT. Then, the polynomial regression algorithm is used to fit the delay feature of the Trojan, and the feature library of the Trojan is established based on the regression function. The experimental results show that the proposed LDA combined with linear regression algorithm can identify HT circuits according to the delay feature, and its HT detection rate is better than other methods. Moreover, it reduces the difficulty of Trojan horse detection as the scale of the circuit increases. Through the research of this method, it has an important guiding role in identifying HT circuits and improving chip security and reliability.
-
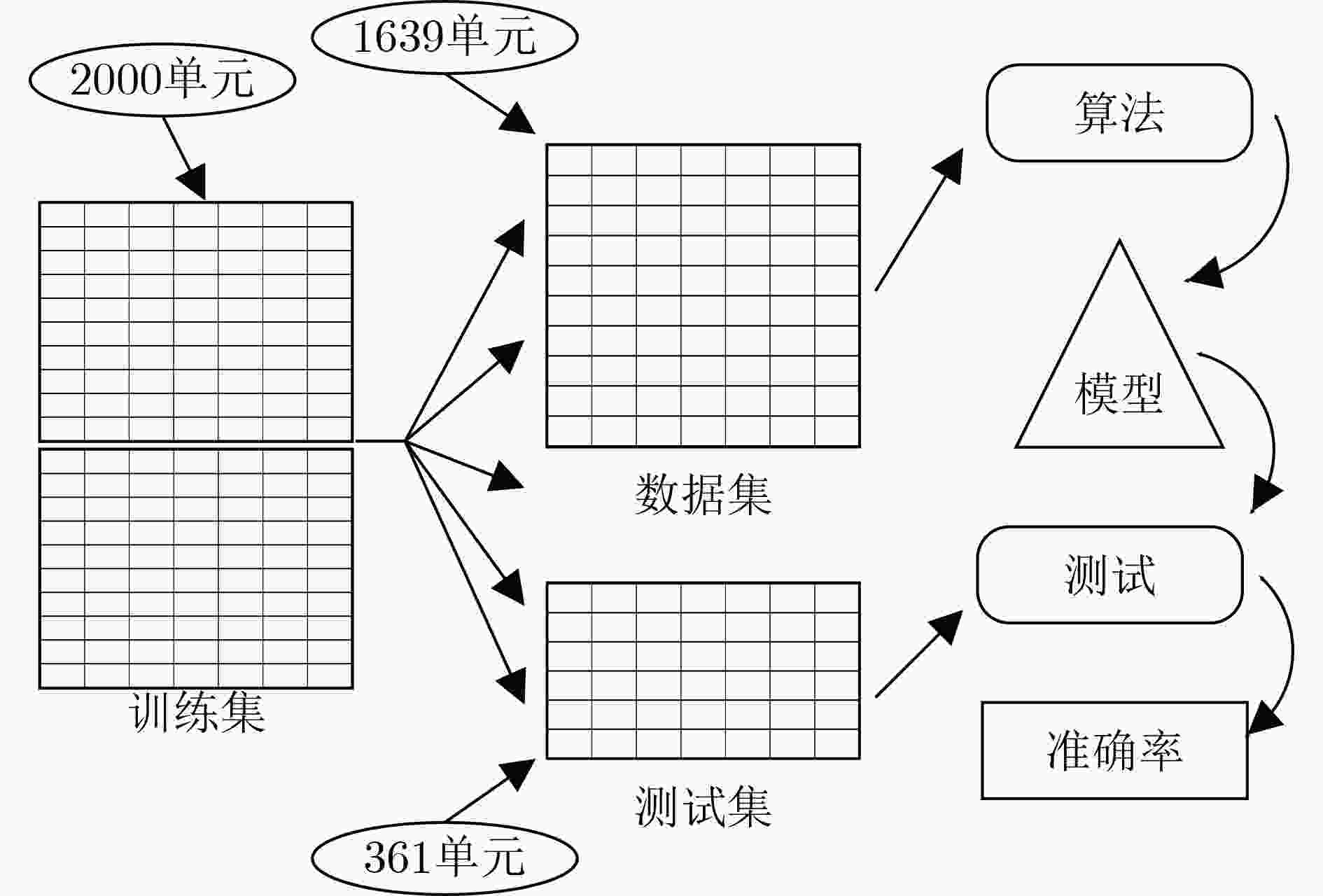
算法1 LDA 算法 输入:带标签的原始向量 输出:矩阵积 循环执行如下操作 1. 计算数据集中不同类别的多维平均向量。 2. 计算矩阵(类间和类内矩阵)。 3. 计算矩阵的特征向量和相应的特征值。 4. 对特征向量进行递减特征值排序,选择特征值最大的K个特
征向量,形成D×K维矩阵W。5. 使用这个 D×K 特征向量矩阵将模式转换到新的子空间。 6. 对矩阵求积:Y=X×W(其中X是表示n个模式的n×D维矩
阵,Y是新子空间中变换后的n×k维模式)。结束 算法2 线性回归算法 输入:训练数据集和样本特征向量 输出:计算多项式的值 y=w·x+b 对于每一个参数w和b执行如下操作 1. 前向传递:计算损失函数 L 2. 向后传递:计算相对于 w 的梯度 G1的损失函数 3. 根据G1更新参数 4. 惩罚项:计算相对于w的梯度G2的损失函数 5. 根据G2更新参数 结束 表 1 测试台数据
基准电路 门数量 电路面积(μm2) 功率(W) AES 10610 163×163 0.0732 MIPS 8661 195×195 0.0494 RS Decoder 23224 394×394 0.12 JPEG Encoder 269970 1094×1094 1.4675 表 2 本文识别率与以往技术的比较(%)
基准电路 LTPD
(μW/μm2)GNJ[16] BSC[17] LPA[18] ML[19] 本文方法 AES 0.148 8.0 2.0 2.2 2.7 3.0 0.223 26.5 19.1 15.4 16.34 31.4 0.279 31.2 43.5 54.4 67.2 86.5 0.369 64.9 77.6 89.9 86.7 96.7 0.443 90.8 96.5 98.5 99.5 100 MIPS 0.154 5.6 8.0 11.7 19.7 32.5 0.231 10.8 16.5 23.3 39.5 60.6 0.308 17.7 26.0 40.1 62.6 81.8 0.384 27.6 39.4 58.2 77.8 91.1 0.463 39.3 55.9 73.7 88.5 92.4 RS Decoder 0.062 3.7 4.8 4.3 7.5 9.8 0.092 3.7 4.8 4.3 7.5 9.8 0.122 4.8 7.3 9.1 13.4 21.2 0.156 6.1 9.3 12.5 22.2 36.2 0.218 10.1 12.8 20.9 38.1 57 JPEG Encoder 0.004 1.5 2.0 2.0 3.1 3.2 0.015 3.3 7.5 7.8 8.0 8.0 0.026 4.5 10.5 11.1 13.0 15.0 0.037 10.3 15.5 20.6 21.2 25.8 0.048 11.1 18.5 30.3 45.6 50.1 -
[1] AHMED A, FARAHMANDI F, ISKANDER Y, et al. Scalable hardware Trojan activation by interleaving concrete simulation and symbolic execution[C]. Proceedings of 2018 IEEE International Test Conference, Phoenix, USA, 2018: 1–10. [2] HAIDER S K, JIN Chenglu, AHMAD M, et al. Advancing the state-of-the-art in hardware Trojans detection[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 16(1): 18–32. doi: 10.1109/TDSC.2017.2654352 [3] 明小满. 中国集成电路的发展现状与发展建议[J]. 通讯世界, 2017(4): 273–274. doi: 10.3969/j.issn.1006-4222.2017.04.200MING Xiaoman. The development status and development suggestions of China's integrated circuits[J]. Telecom World, 2017(4): 273–274. doi: 10.3969/j.issn.1006-4222.2017.04.200 [4] ZHOU Bin, ZHANG Wei, THAMBIPILLAI S, et al. Cost-efficient acceleration of hardware Trojan detection through fan-out cone analysis and weighted random pattern technique[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2016, 35(5): 792–805. doi: 10.1109/TCAD.2015.2460551 [5] SONG Tai, NI Tianming, HUANG Zhengfeng, et al. Valid test pattern identification for VLSI adaptive test[J]. Integration, 2022, 82: 1–6. doi: 10.1016/j.vlsi.2021.08.009 [6] CHAKRABORTY R S, NARASIMHAN S, and BHUNIA S. Hardware Trojan: Threats and emerging solutions[C]. Proceedings of 2009 IEEE International High Level Design Validation and Test Workshop, San Francisco, USA, 2009: 166–171. [7] SABRI M, SHABANI A, and ALIZADEH B. SAT-based integrated hardware Trojan detection and localization approach through path-delay analysis[J]. IEEE Transactions on Circuits and Systems II:Express Briefs, 2021, 68(8): 2850–2854. doi: 10.1109/TCSII.2021.3074549 [8] 许强, 蒋兴浩, 姚立红, 等. 硬件木马检测与防范研究综述[J]. 网络与信息安全学报, 2017, 3(4): 1–13. doi: 10.11959/j.issn.2096-109x.2017.00160XU Qiang, JIANG Xinghao, YAO Lihong, et al. Overview of the detection and prevention study of hardware Trojans[J]. Chinese Journal of Network and Information Security, 2017, 3(4): 1–13. doi: 10.11959/j.issn.2096-109x.2017.00160 [9] 尹勇生, 汪涛, 陈红梅, 等. 硬件木马技术研究进展[J]. 微电子学, 2017, 47(2): 233–238. doi: 10.13911/j.cnki.1004-3365.2017.02.021YIN Yongsheng, WANG Tao, CHEN Hongmei, et al. Study on hardware Trojan technology[J]. Microelectronics, 2017, 47(2): 233–238. doi: 10.13911/j.cnki.1004-3365.2017.02.021 [10] 李莹, 陈岚, 佟鑫. 指令级功耗特征的硬件木马检测高效机器学习(英文)[J]. 中国科学院大学学报, 2021, 38(4): 494–502. doi: 10.7523/j.issn.2095-6134.2021.04.008LI Ying, CHEN Lan, and TONG Xin. Efficient machine learning methods for hardware Trojan detection using instruction-level power character[J]. Journal of University of Chinese Academy of Sciences, 2021, 38(4): 494–502. doi: 10.7523/j.issn.2095-6134.2021.04.008 [11] HU Wei, CHANG C H, SENGUPTA A, et al. An overview of hardware security and trust: Threats, countermeasures, and design tools[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2021, 40(6): 1010–1038. doi: 10.1109/TCAD.2020.3047976 [12] 倪林, 李少青, 马瑞聪, 等. 硬件木马检测与防护[J]. 数字通信, 2014, 41(1): 59–63,68. doi: 10.3969/j.issn.1005-3824.2014.01.016NI Lin, LI Shaoqing, MA Ruicong, et al. Hardware Trojans detection and protection[J]. Digital Communication, 2014, 41(1): 59–63,68. doi: 10.3969/j.issn.1005-3824.2014.01.016 [13] 詹慕文. 基于衬底电流传感器的安全芯片防激光错误注入攻击研究[D]. [硕士论文], 湖北大学, 2021.ZHAN Muwen. Research on the security chip based on bulk current sensor against laser fault injection attack[D]. [Master dissertation], Hubei University, 2021. [14] 李雄伟, 徐璐, 张阳, 等. 面向硬件木马检测的旁路信号特征选择方法[J]. 计算机工程与应用, 2017, 53(21): 258–262. doi: 10.3778/j.issn.1002-8331.1605-0149LI Xiongwei, XU Lu, ZHANG Yang, et al. Side channel signals feature selection method oriented to hardware Trojan detection[J]. Computer Engineering and Applications, 2017, 53(21): 258–262. doi: 10.3778/j.issn.1002-8331.1605-0149 [15] SHENDE R and AMBAWADE D D. A side channel based power analysis technique for hardware Trojan detection using statistical learning approach[C]. Proceedings of the 2016 13th International Conference on Wireless and Optical Communications Networks, Hyderabad, India, 2016: 1–4. [16] SALMANI H. Gradual-N-justification (GNJ) to reduce false-positive hardware Trojan detection in gate-level netlist[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2022, 30(4): 515–525. doi: 10.1109/TVLSI.2022.3143349 [17] NGUYEN L N, YILMAZ B B, PRVULOVIC M, et al. A novel golden-chip-free clustering technique using backscattering side channel for hardware Trojan detection[C]. Proceedings of 2020 IEEE International Symposium on Hardware Oriented Security and Trust, San Jose, USA, 2020: 1–12. [18] STERN A, MEHTA D, TAJIK S, et al. SPARTA: A laser probing approach for Trojan detection[C]. Proceedings of 2020 IEEE International Test Conference, Washington, USA, 2020: 1–10. [19] KURIHARA T, HASEGAWA K, and TOGAWA N. Evaluation on hardware-Trojan detection at gate-level IP cores utilizing machine learning methods[C]. Proceedings of the 2020 IEEE 26th International Symposium on On-Line Testing and Robust System Design, Napoli, Italy, 2020: 1–4. -





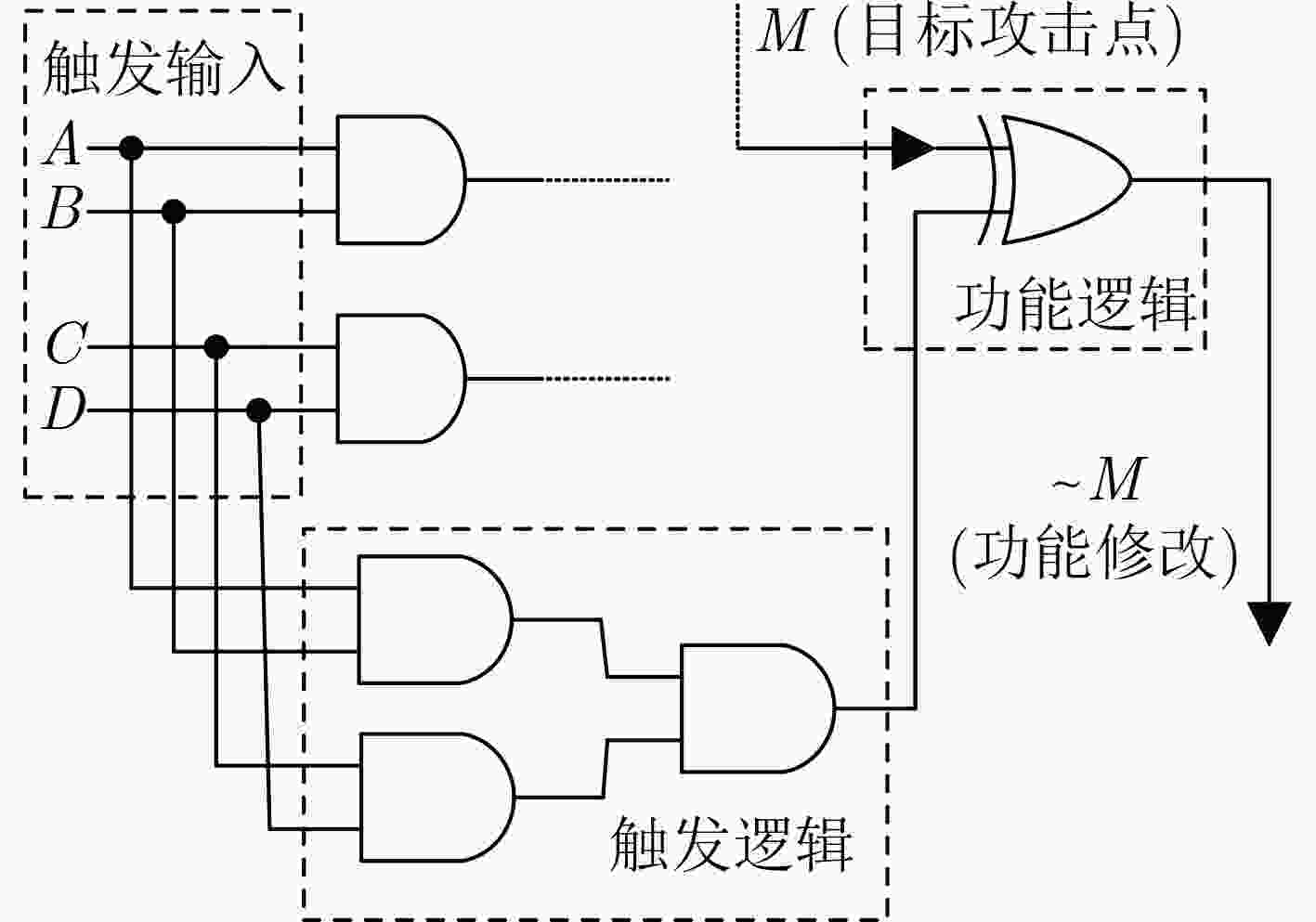
 下载:
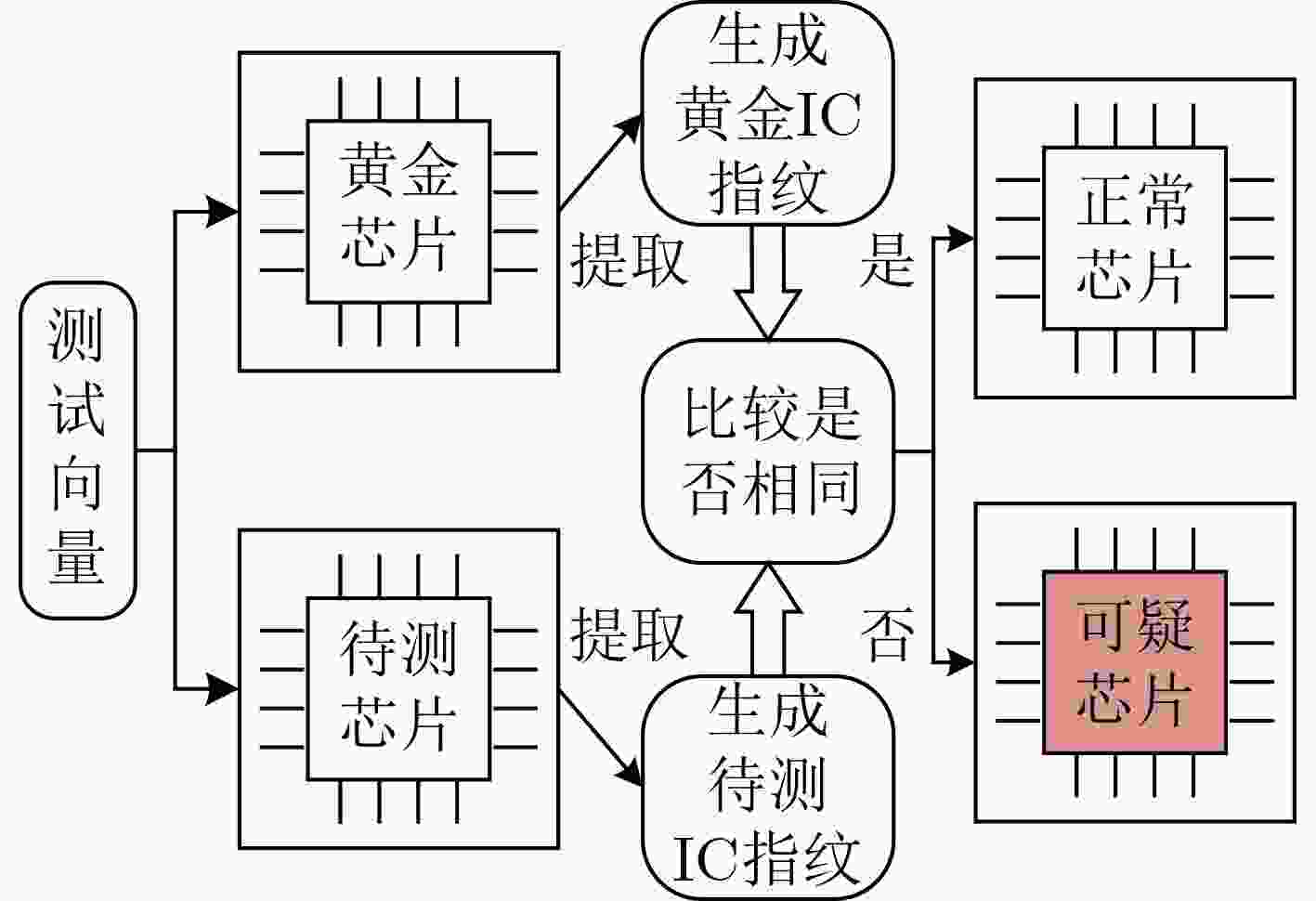
下载:
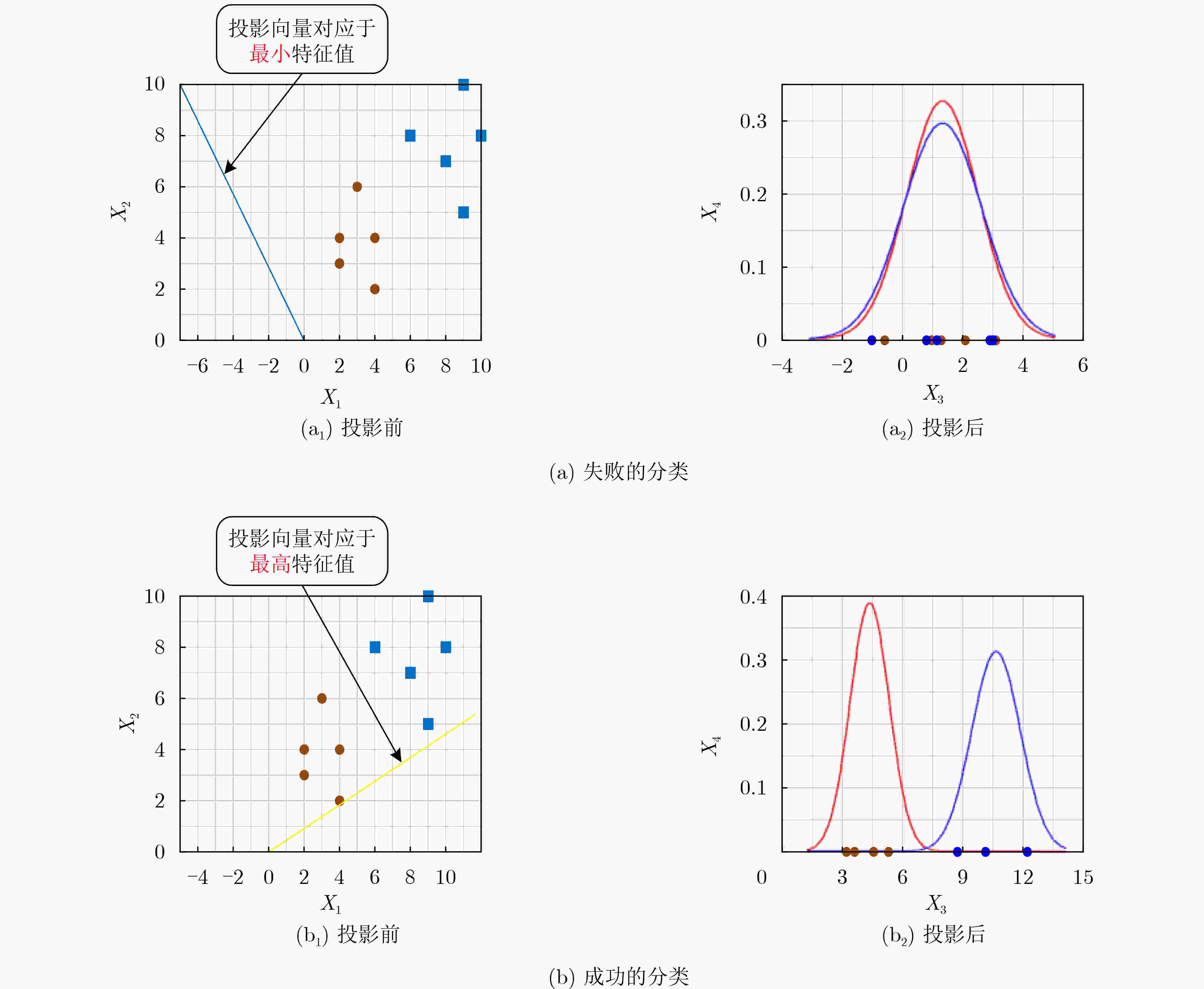

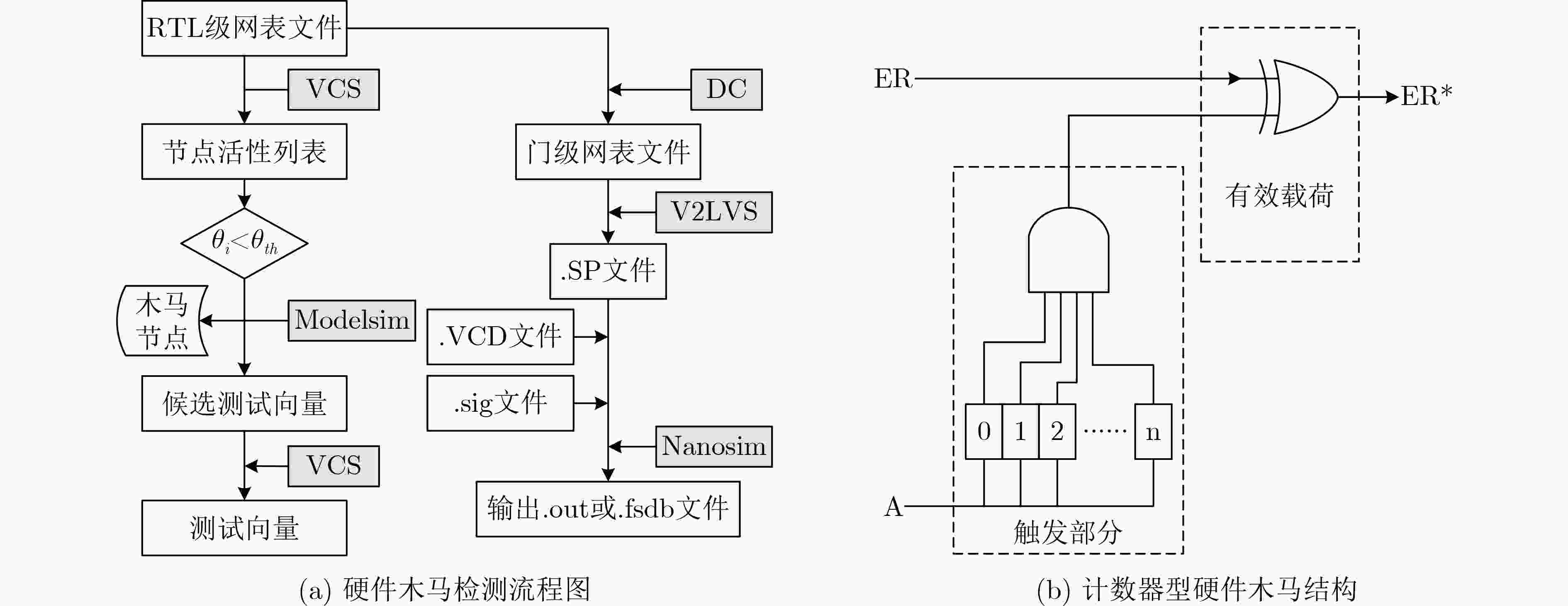


 下载:
下载:
