| [1] |
RASHEED A A, MAHAPATRA R N, and HAMZA-LUP F G. Adaptive group-based zero knowledge proof-authentication protocol in vehicular Ad Hoc networks[J]. IEEE Transactions on Intelligent Transportation Systems, 2020, 21(2): 867–881. doi: 10.1109/TITS.2019.2899321
|
| [2] |
RASHEED A A, MAHAPATRA R N, VAROL C, et al. Exploiting zero knowledge proof and Blockchain towards the enforcement of anonymity, data integrity and privacy (ADIP) on IoT[J]. IEEE Transactions on Emerging Topics in Computing, To be published.
|
| [3] |
LIN Wanxue, ZHANG Xuefei, CUI Qimei, et al. Blockchain based unified authentication with zero-knowledge proof in heterogeneous MEC[C]. 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Montreal, Canada, 2021: 1–6.
|
| [4] |
刘雪艳, 王力, 郇丽娟, 等. 车联网环境下无证书匿名认证方案[J]. 电子与信息学报, 2022, 44(1): 295–304. doi: 10.11999/JEIT201069LIU Xueyan, WANG Li, HUAN Lijuan, et al. Certificateless anonymous authentication scheme for internet of vehicles[J]. Journal of Electronics &Information Technology, 2022, 44(1): 295–304. doi: 10.11999/JEIT201069
|
| [5] |
FENG Xia, SHI Qichen, XIE Qingqing, et al. P2BA: A privacy-preserving protocol with batch authentication against semi-trusted RSUs in vehicular Ad Hoc networks[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 3888–3899. doi: 10.1109/TIFS.2021.3098971
|
| [6] |
SONG Jian, HARN P W, SAKAI K, et al. An RFID zero-knowledge authentication protocol based on quadratic residues[J]. IEEE Internet of Things Journal, 2021, 9(4): 12813–12824. doi: 10.1109/JIOT.2021.3138557
|
| [7] |
ROSE S, BORCHERT O, MITCHELL S, et al. Zero trust architecture[R]. NIST SP-800-207, 2020.
|
| [8] |
TEERAKANOK S, UEHARA T, and INOMATA A. Migrating to zero trust architecture: Reviews and challenges[J]. Security and Communication Networks, 2021, 2021: 9947347. doi: 10.1155/2021/9947347
|
| [9] |
CHEN Baozhan, QIAO Siyuan, ZHAO Jie, et al. A security awareness and protection system for 5G smart healthcare based on zero-trust architecture[J]. IEEE Internet of Things Journal, 2021, 8(13): 10248–10263. doi: 10.1109/JIOT.2020.3041042
|
| [10] |
SHAH S W, SYED N F, SHAGHAGHI A, et al. LCDA: Lightweight continuous device-to-device authentication for a zero trust architecture (ZTA)[J]. Computers & Security, 2021, 108: 102351. doi: 10.1016/j.cose.2021.102351
|
| [11] |
LIU Yizhi, HAO Xiaohan, REN Wei, et al. A blockchain-based decentralized, fair and authenticated information sharing scheme in zero trust internet-of-things[J]. IEEE Transactions on Computers, To be published.
|
| [12] |
中国信息通信研究院, 奇安信科技集团股份有限公司. 零信任技术[R]. 2020.China Academy of Information and Communications Technology, QI-ANXIN Technology Group Inc. Zero-Trust Technology[R]. 2020.
|
| [13] |
中国信息通信研究院云计算与大数据研究所, 腾讯云计算(北京)有限公司. 数字化时代-零信任安全蓝皮报告[R]. 2021.Institute of Cloud Computing and Big Data, China Academy of Information and Communication Technology, Tencent Cloud Computing (Beijing) Co.LTD. The Digital Age - Zero Trust Security Blue Report [R].2021.
|
| [14] |
BHARGAVA A, VERMA S, CHAURASIA B K, et al. Computational trust model for Internet of Vehicles[C]. 2017 Conference on Information and Communication Technology (CICT), Gwalior, India, 2017: 1–5.
|
| [15] |
HAO Min, YE Dongdong, WANG Siming, et al. URLLC resource slicing and scheduling for trustworthy 6G vehicular services: A federated reinforcement learning approach[J]. Physical Communication, 2021, 49: 101470. doi: 10.1016/j.phycom.2021.101470
|
| [16] |
GOLDWASSER S, MICALI S, and RACKOFF C. The knowledge complexity of interactive proof systems[J]. SIAM Journal on Computing, 1989, 18(1): 186–208. doi: 10.1137/0218012
|
| [17] |
BLUM M, DE SANTIS A, MICALI S, et al. Noninteractive zero-knowledge[J]. SIAM Journal on Computing, 1991, 20(6): 1084–1118. doi: 10.1137/0220068
|
| [18] |
清华大学智能产业研究院, 百度Apollo. 面向自动驾驶的车路协同关键技术与展望[R]. 2021.Institute of Intelligent Industry, Tsinghua University, Baidu Apollo. Key Technologies and Prospects of Vehicle-Road Cooperation for Autonomous Driving [R]. 2021.
|
| [19] |
中华人民共和国国家质量监督检验检疫总局, 中国国家标准化管理委员会. GB/T 32918.1-2016 信息安全技术 SM2椭圆曲线公钥密码算法 第1部分: 总则[S]. 北京: 中国标准出版社, 2017.General Administration of Quality Supervision, Inspection and Quarantine of the People's Republic of China, Standardization Administration of the People's Republic of China. GB/T 32918.1-2016 Information security technology-public key cryptographic algorithm SM2 based on elliptic curves-Part 1: General[S]. Beijing: Standards Press of China, 2017.
|
| [20] |
WANG Siming, HUANG Xumin, YU Rong, et al. Permissioned blockchain for efficient and secure resource sharing in vehicular edge computing[J]. arXiv: 1906.06319, 2019.
|
| [21] |
HUANG Xumin, YU Rong, YE Dongdong, et al. Efficient workload allocation and user-centric utility maximization for task scheduling in collaborative vehicular edge computing[J]. IEEE Transactions on Vehicular Technology, 2021, 70(4): 3773–3787. doi: 10.1109/TVT.2021.3064426
|
| [22] |
LIANG Jinwen, QIN Zheng, XIAO Sheng, et al. Efficient and secure decision tree classification for cloud-assisted online diagnosis services[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(4): 1632–1644. doi: 10.1109/TDSC.2019.2922958
|
| [23] |
ZHOU Zhenyu, LIAO Haijun, ZHAO Xiongwen, et al. Reliable task offloading for vehicular fog computing under information asymmetry and information uncertainty[J]. IEEE Transactions on Vehicular Technology, 2019, 68(9): 8322–8335. doi: 10.1109/TVT.2019.2926732
|





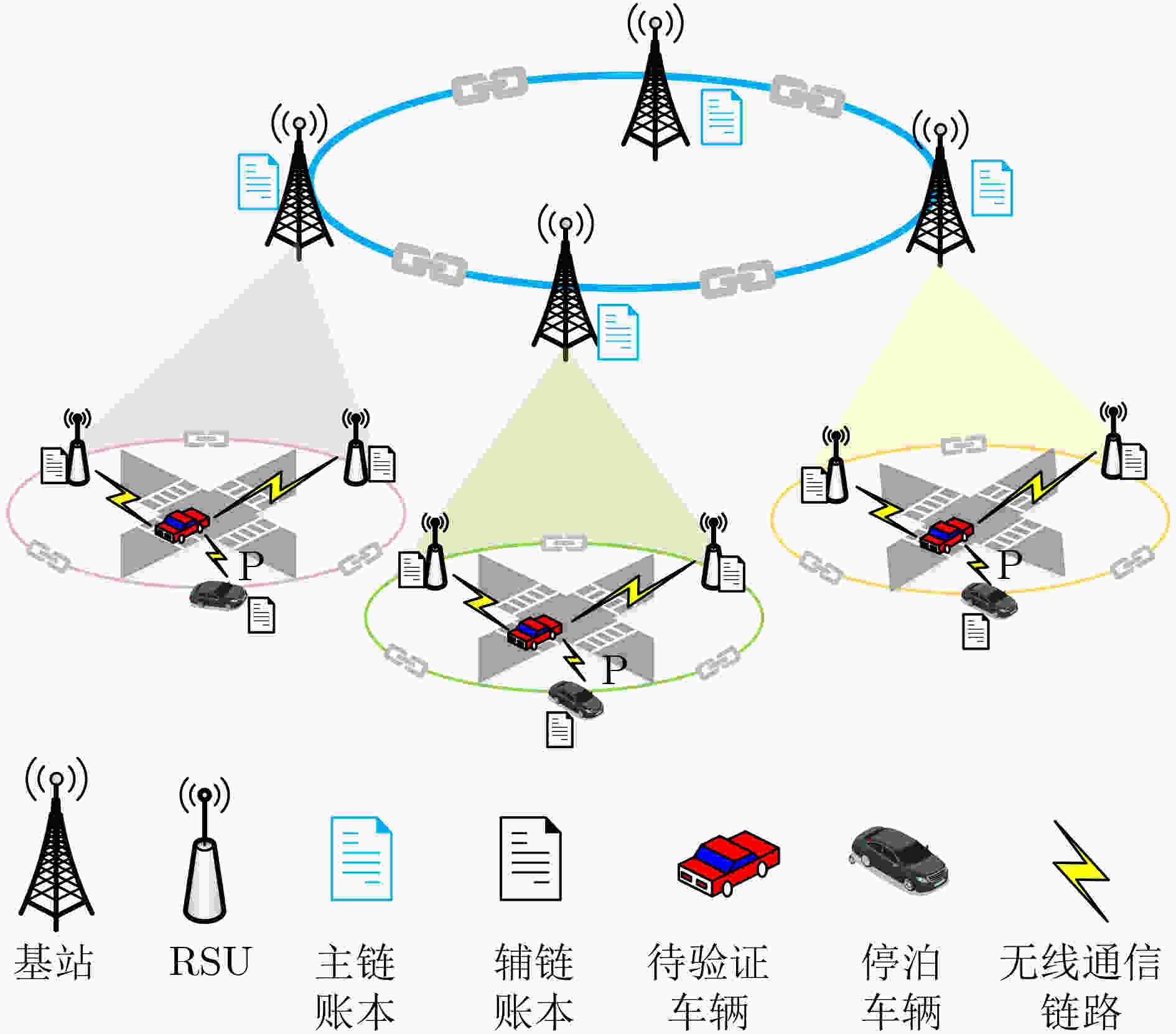
 下载:
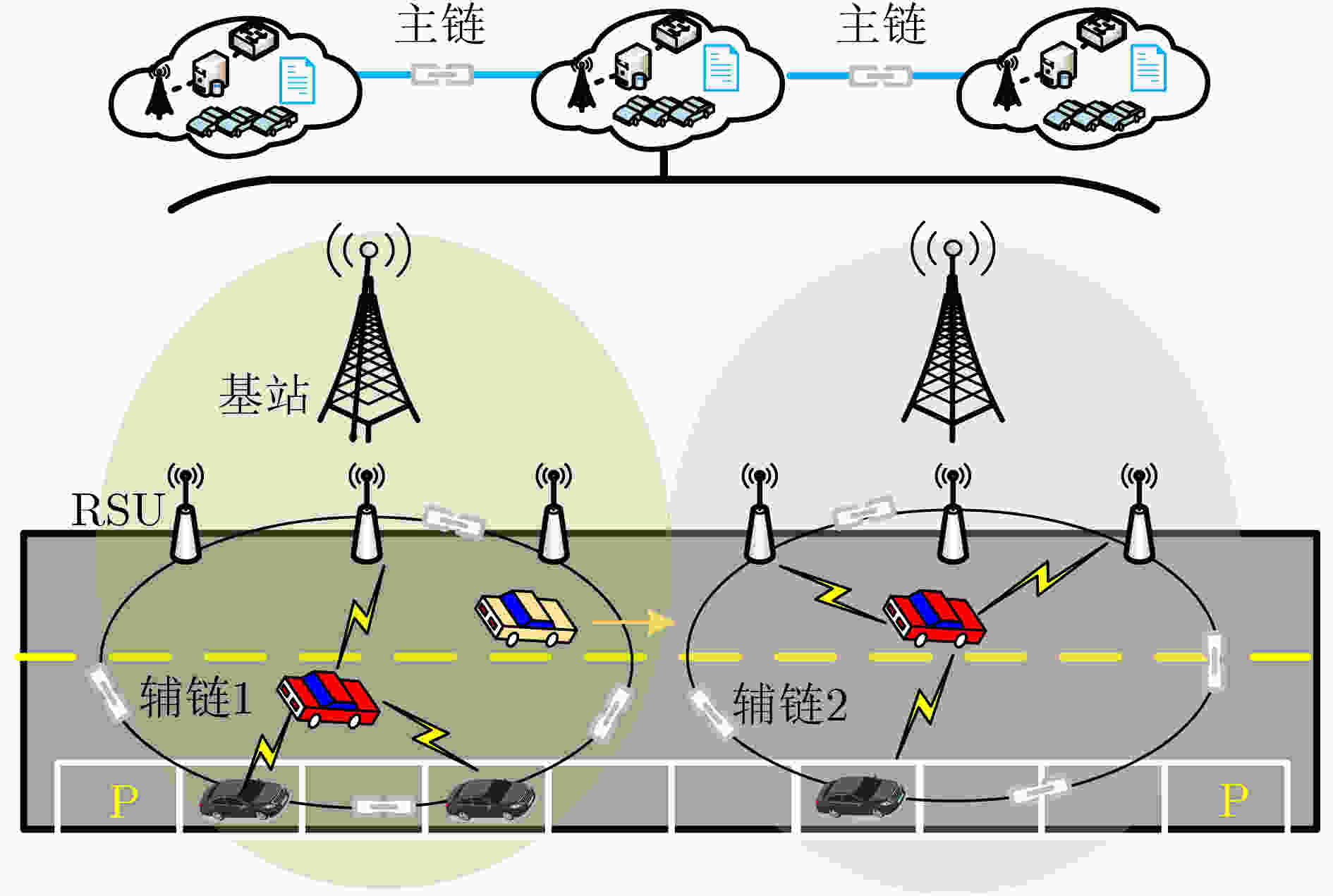
下载:

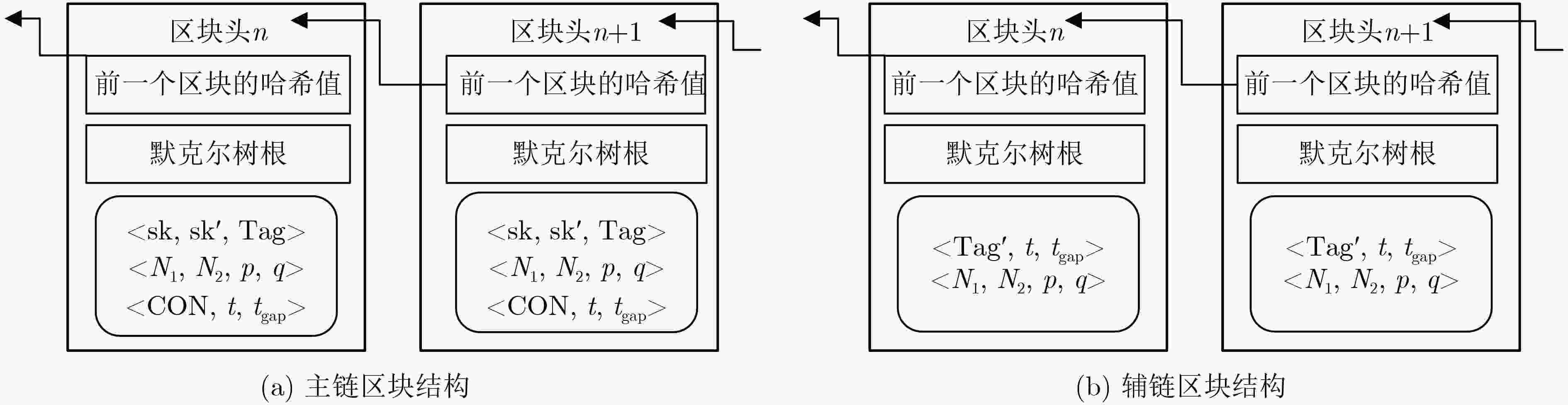


 下载:
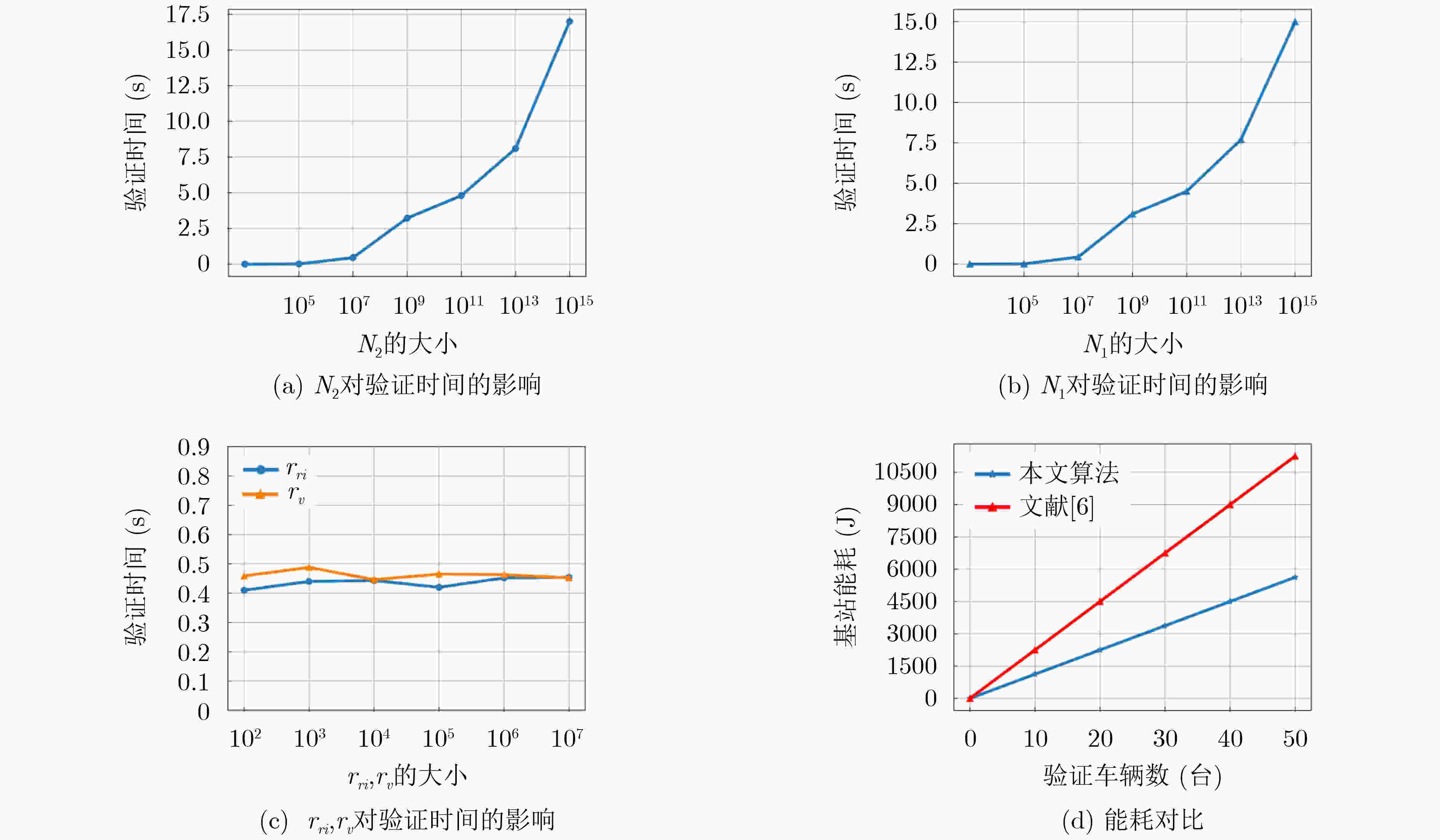
下载:
