Decentralized Group Key Management Scheme in Hierarchical Unmanned Aerial Vehicle Network
-
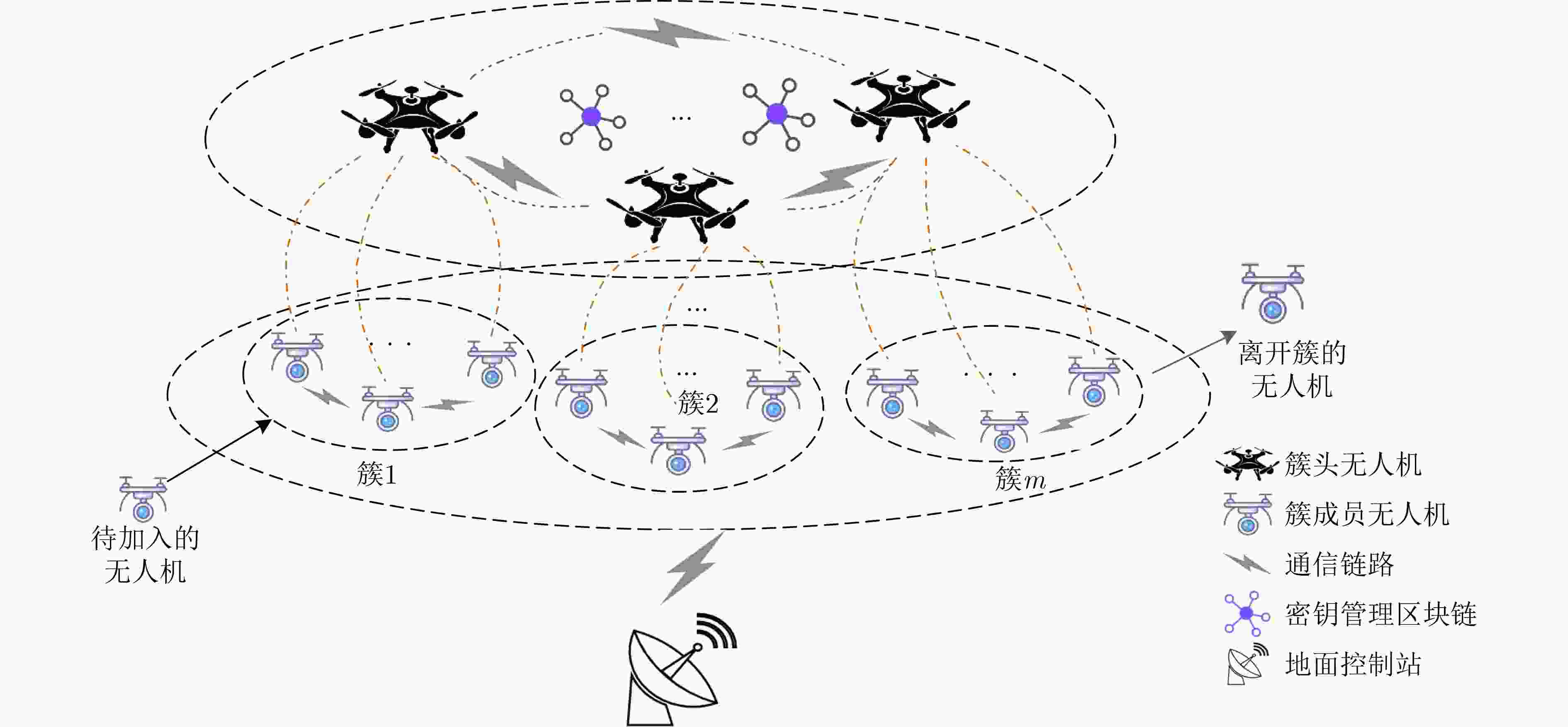
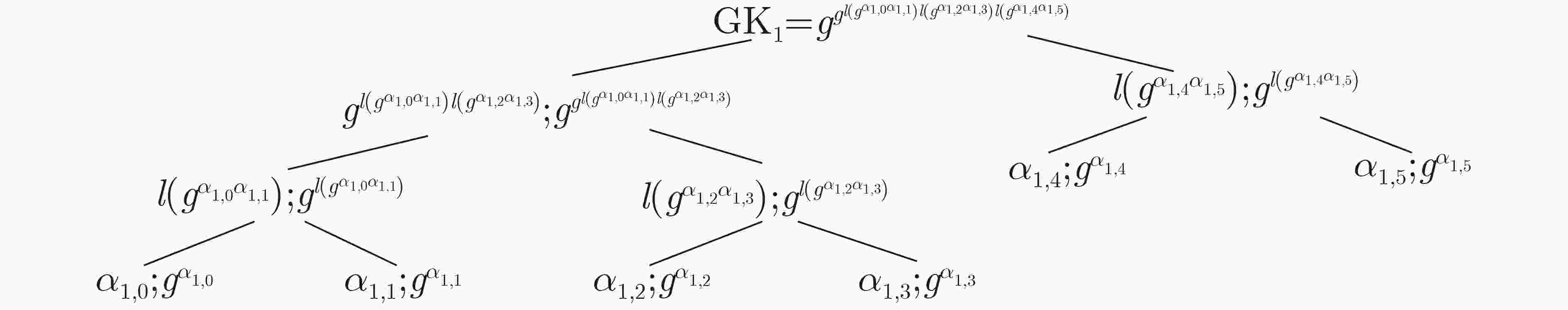
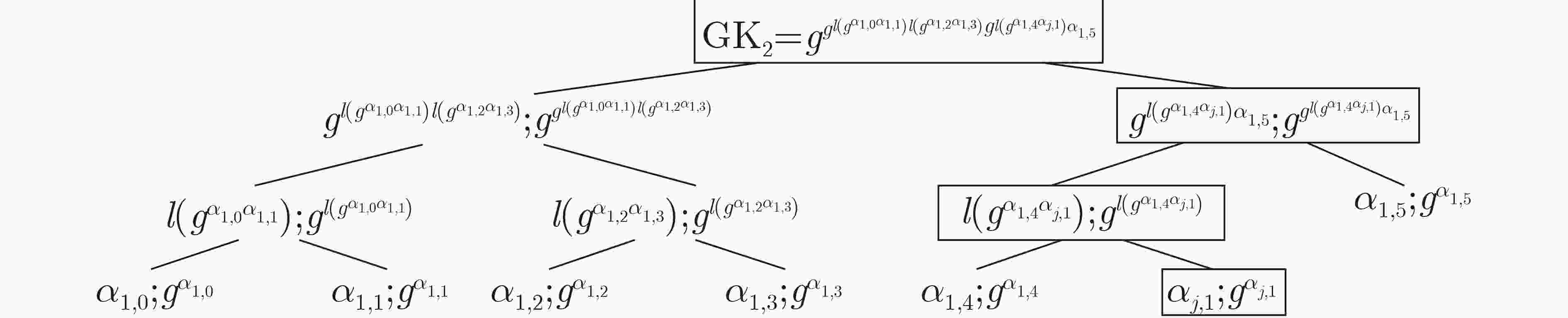
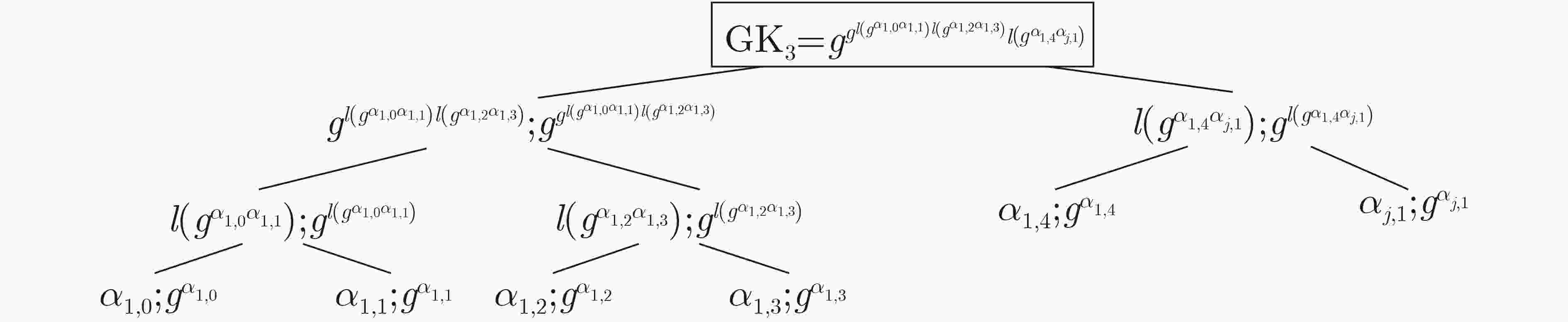
摘要: 为解决现有分层无人机(UAV)网络中群组密钥管理存在的单点故障问题,群组成员离线导致整个群组无法计算、及时更新组密钥的问题,该文提出一种支持异步计算的去中心群组密钥管理方案。该方案采用异步棘轮树(ART)协议实现对群组密钥的预部署,各成员能对组密钥进行异步计算、自主更新;利用区块链技术的去中心化特性解决了单点故障问题,提高了群组密钥管理的透明性与公平性。性能评估表明,与同类方案相比,该方案中的簇成员无人机具有较低的计算开销和通信开销,适合应用于分层无人机网络环境。Abstract: To address the single point failure of group key management in the existing hierarchical Unmanned Aerial Vehicle (UAV) network, and the incapability of timely group key calculation and update caused by offline group members, a decentralized group key management scheme that supports asynchronous computing is proposed. The Asynchronous Ratchet Tree (ART) protocol is adopted to realize the pre-deployment of the group key, in which asynchronous calculation and autonomous update of the group key can be performed by each member. The decentralization feature of the blockchain technology is employed to solve the single point failure problem, which improves the transparency and fairness of group key management. The performance evaluation shows that, compared with existing schemes, the cluster member UAV in this scheme has lower computational overhead and communication overhead, and are suitable for application in a hierarchical UAV network environment.
-
表 1 无人机节点构建ART的算法复杂度
操作 簇头无人机节点 簇成员无人机节点 初始群组密钥生成 $O(n{\log _2}n)$ $ O({\log _2}n) $ 加入 $ O({\log _2}n) $ $ O({\log _2}n) $ 离开 $ O({\log _2}n) $ $ O({\log _2}n) $ 更新 $ O({\log _2}n) $ $ O({\log _2}n) $ 表 2 密码原语操作运行时间(ms)
操作原语 原语描述 PC端运行时间 ${T_{\exp }}$ 模幂操作时间 2.418 ${T_h}$ SHA256操作时间 0.027 ${T_{ {{\rm{bp}}} } }$ 双线性配对操作时间 6.233 ${T_{ {{\rm{mul}}} } }$ 标量乘法操作时间 0.016 ${T_{\text{pa-acc}} }$ 椭圆曲线点加操作时间 0.0016 ${T_{ {{\rm{inv}}} } }$ 模逆操作时间 0.175 ${T_{\text{pa-bp}} }$ 双线性配对点加操作时间 0.073 表 3 群组密钥计算开销对比(ms)
方案 初始群组密钥计算 更新 加入 退出 文献[17] $(5n + 5){T_{\exp }} = 72.540$ $ (7 + 5n){T_{\exp }} = 77.376 $ $ 23{T_{\exp }} = 55.614 $ $ (5n - 6){T_{\exp }} = 45.942 $ 文献[20] $ \begin{gathered} {T_{bp}} + 3{T_{{\rm{mul}} }} + {T_{\rm{inv}}} + 4{T_h} \\ (n + 1){T_{{text{{pa}-bp}}}} = 58.866 \\ \end{gathered} $ -- $4{T_{{\rm{bp}}} } + {T_{\rm{inv} } } = 25.107$ $4{T_{{\rm{bp}}} } + {T_{\rm{inv} } } = 25.107$ 文献[22] $\begin{gathered} 4{T_{{\rm{bp}}} } + 3{T_{{\rm{exp}}} } + (2n - 1){T_{ {\rm{mul} } } } \\ + {T_h} + 4{T_{{\text{pa-acc}}} } = 34.421 \\ \end{gathered}$ -- -- -- 本文方案 $ (2h - 1){T_{\exp }} = 12.090 $ $ (2h - 1){T_{\exp }} = 12.090 $ $ (2h - 1){T_{\exp }} = 12.090 $ $ (2h - 1){T_{\exp }} = 12.090 $ (注:“--”表示不支持该操作) -
[1] ZENG Yong, ZHANG Rui, and LIM T J. Wireless communications with unmanned aerial vehicles: Opportunities and challenges[J]. IEEE Communications Magazine, 2016, 54(5): 36–42. doi: 10.1109/MCOM.2016.7470933 [2] ZHANG Naijian, JIANG Qi, LI Long, et al. An efficient three-factor remote user authentication protocol based on BPV-FourQ for Internet of Drones[J]. Peer-to-Peer Networking and Applications, 2021, 14(5): 3319–3332. doi: 10.1007/s12083-021-01130-5 [3] 贺蕾, 马建峰, 魏大卫. 面向无人机网络的属性代理签名方案[J]. 通信学报, 2021, 42(11): 87–96. doi: 10.11959/j.issn.1000-436x.2021210HE Lei, MA Jianfeng, and WEI Dawei. Attribute-based proxy signature scheme for unmanned aerial vehicle networks[J]. Journal on Communications, 2021, 42(11): 87–96. doi: 10.11959/j.issn.1000-436x.2021210 [4] 何道敬, 杜晓, 乔银荣, 等. 无人机信息安全研究综述[J]. 计算机学报, 2019, 42(5): 1076–1094. doi: 10.11897/SP.J.1016.2019.01076HE Daojing, DU Xiao, QIAO Yinrong, et al. A survey on cyber security of unmanned aerial vehicles[J]. Chinese Journal of Computers, 2019, 42(5): 1076–1094. doi: 10.11897/SP.J.1016.2019.01076 [5] 陈瑶, 梁加红, 邹顺, 等. 无人机Ad Hoc网络拓扑控制算法研究[J]. 计算机仿真, 2010, 27(7): 33–37. doi: 10.3969/j.issn.1006-9348.2010.07.009CHEN Yao, LIANG Jiahong, ZOU Shun, et al. Topology control algorithm for UAV Ad Hoc networks[J]. Computer Simulation, 2010, 27(7): 33–37. doi: 10.3969/j.issn.1006-9348.2010.07.009 [6] MEHTA S, SHARMA P, and KOTECHA K. A survey on various cluster head election algorithms for MANET[C]. 2011 Nirma University International Conference on Engineering, Ahmedabad, India, 2011: 1–6. [7] 游文静, 董超, 吴启晖. 大规模无人机自组网分层体系架构研究综述[J]. 计算机科学, 2020, 47(9): 226–231. doi: 10.11896/jsjkx.190900164YOU Wenjing, DONG Chao, and WU Qihui. Survey of layered architecture in large-scale FANETs[J]. Computer Science, 2020, 47(9): 226–231. doi: 10.11896/jsjkx.190900164 [8] 姜奇, 杨雪, 王金花, 等. 面向车联网的抗设备捕获认证密钥协商协议[J]. 中国科学: 信息科学, 2022, 52(12): 2351–2350. doi: 10.1360/SSI-2021-0379JIANG Qi, YANG Xue, WANG Jinhua, et al. Device capture resilient authentication and key agreement protocol for IoV[J]. Scientia Sinica Informationis, 2022, 52(12): 2351–2350. doi: 10.1360/SSI-2021-0379 [9] RAFAELI S and HUTCHISON D. A survey of key management for secure group communication[J]. ACM Computing Surveys, 2003, 35(3): 309–329. doi: 10.1145/937503.937506 [10] WONG C K, GOUDA M, and LAM S S. Secure group communications using key graphs[J]. IEEE/ACM Transactions on Networking, 2000, 8(1): 16–30. doi: 10.1109/90.836475 [11] WALLNER D, HARDER E, and AGEE R. Key management for multicast: Issues and architectures[R]. RFC 2627, 1999. [12] HARNEY H and HARDER E. “Logical key hierarchy protocol, ” Internet Eng. Task Force, Fremont, CA, USA, Internet Draft, Rep. , Apr. 1999[EB/OL]. https://datatracker.ietf.org/doc/html/draft-harneysparta-lkhp-sec-00, 1999. [13] KUNG Y H and HSIAO H C. GroupIt: Lightweight group key management for dynamic IoT environments[J]. IEEE Internet of Things Journal, 2018, 5(6): 5155–5165. doi: 10.1109/JIOT.2018.2840321 [14] MITTRA S. Iolus: A framework for scalable secure multicasting[J]. ACM SIGCOMM Computer Communication Review, 1997, 27(4): 277–288. doi: 10.1145/263109.263179 [15] BURMESTER M and DESMEDT Y. A secure and efficient conference key distribution system[C]. Workshop on the Theory and Application of Cryptographic Techniques, Perugia, Italy, 1994: 275–286. [16] KIM Y, PERRIG A, and TSUDIK G. Tree-based group key agreement[J]. ACM Transactions on Information and System Security, 2004, 7(1): 60–96. doi: 10.1145/984334.984337 [17] ERMIŞ O, BAHTIYAR Ş, ANARIM E, et al. A key agreement protocol with partial backward confidentiality[J]. Computer Networks, 2017, 129: 159–177. doi: 10.1016/j.comnet.2017.09.008 [18] COHN-GORDON K, CREMERS C, GARRATT L, et al. On ends-to-ends encryption: Asynchronous group messaging with strong security guarantees[C]. The 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, Canada, 2018: 1802–1819. [19] WRIGHT C S. Bitcoin: A peer-to-peer electronic cash system[EB/OL].https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3440802, 2008. [20] ZHANG Qikun, WANG Bingli, ZHANG Xiaosong, et al. Blockchain-based dynamic group key agreement protocol for Ad Hoc network[J]. Chinese Journal of Electronics, 2020, 29(3): 447–454. doi: 10.1049/cje.2020.02.020 [21] TAÇYILDIZ Y B, ERMIŞ O, GÜR G, et al. Dynamic group key agreement for resource-constrained devices using blockchains[C]. ACNS 2020 Satellite Workshops on Applied Cryptography and Network Security Workshops, Rome, Italy, 2020: 58–76. [22] ZHANG Qikun, LI Yongjiao, WANG Ruifang, et al. Blockchain-based asymmetric group key agreement protocol for internet of vehicles[J]. Computers & Electrical Engineering, 2020, 86: 106713. doi: 10.1016/j.compeleceng.2020.106713 [23] LARIMER D. Delegated proof-of-stake (DPOS)[EB/OL]. https://bitcointalk.org/index.php?topic=558316.0, 2014. [24] TAN Yawen, LIU Jiajia, and KATO N. Blockchain-based key management for heterogeneous flying Ad Hoc network[J]. IEEE Transactions on Industrial Informatics, 2021, 17(11): 7629–7638. doi: 10.1109/TII.2020.3048398 -





 下载:
下载:





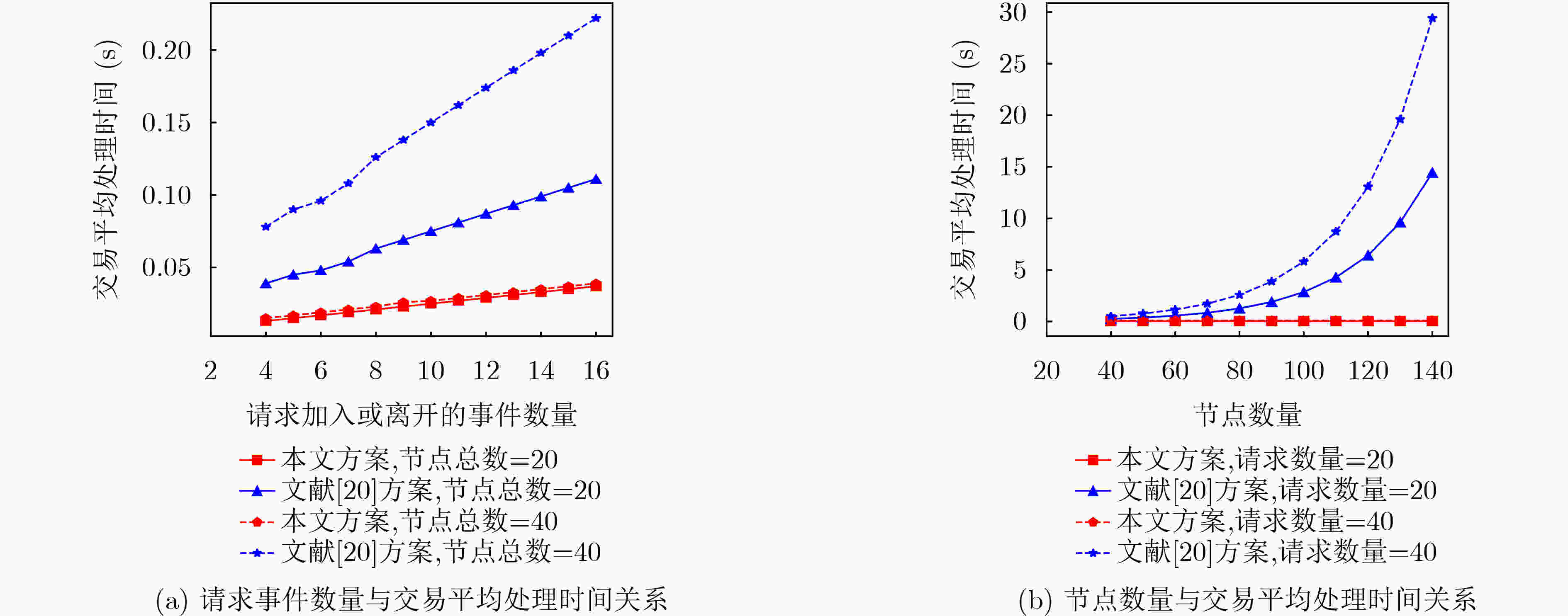


 下载:
下载:
