Endogenous Security Mechanism of Vehicle Network Based on Dynamic Heterogeneous Redundancy
-
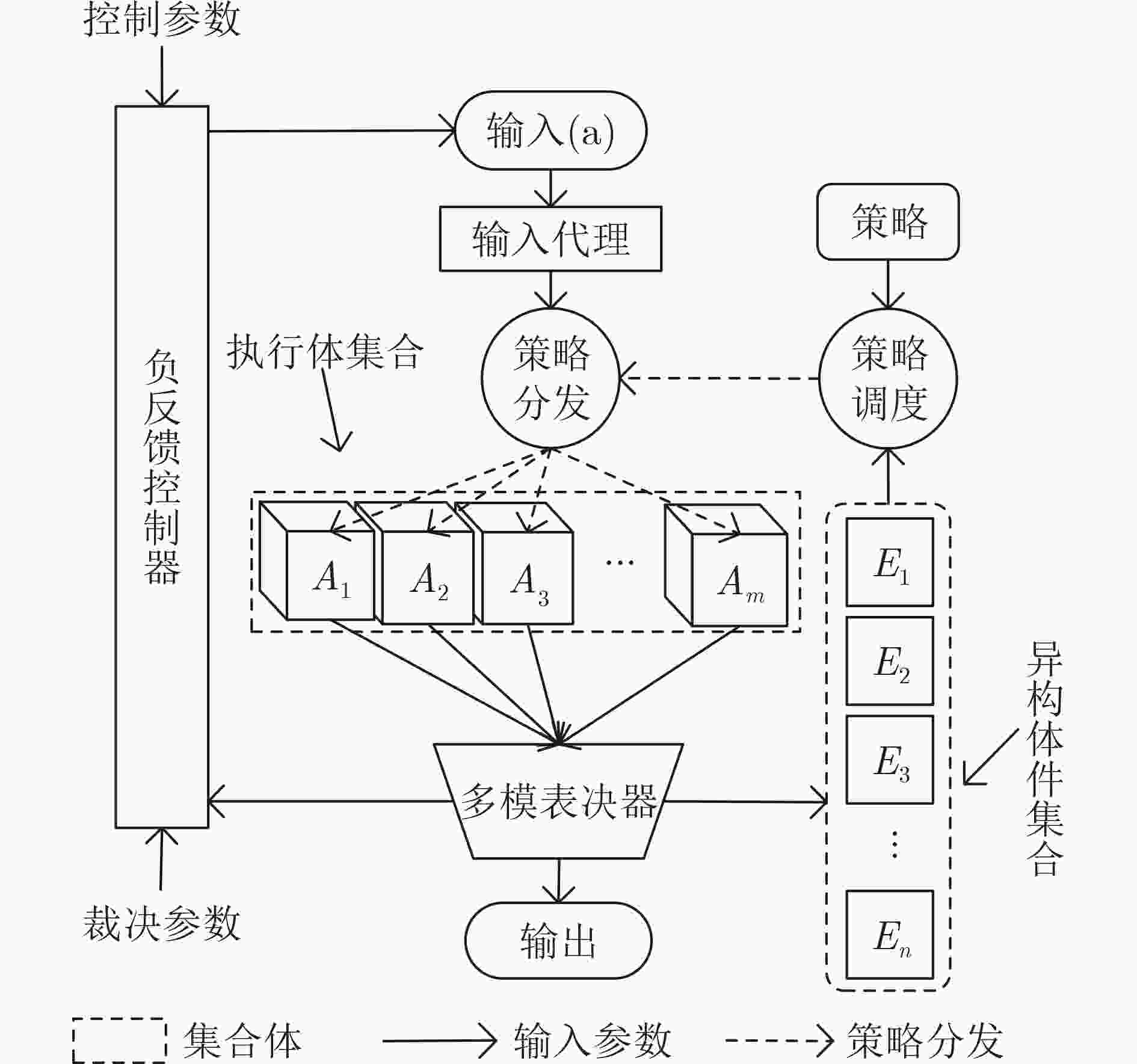
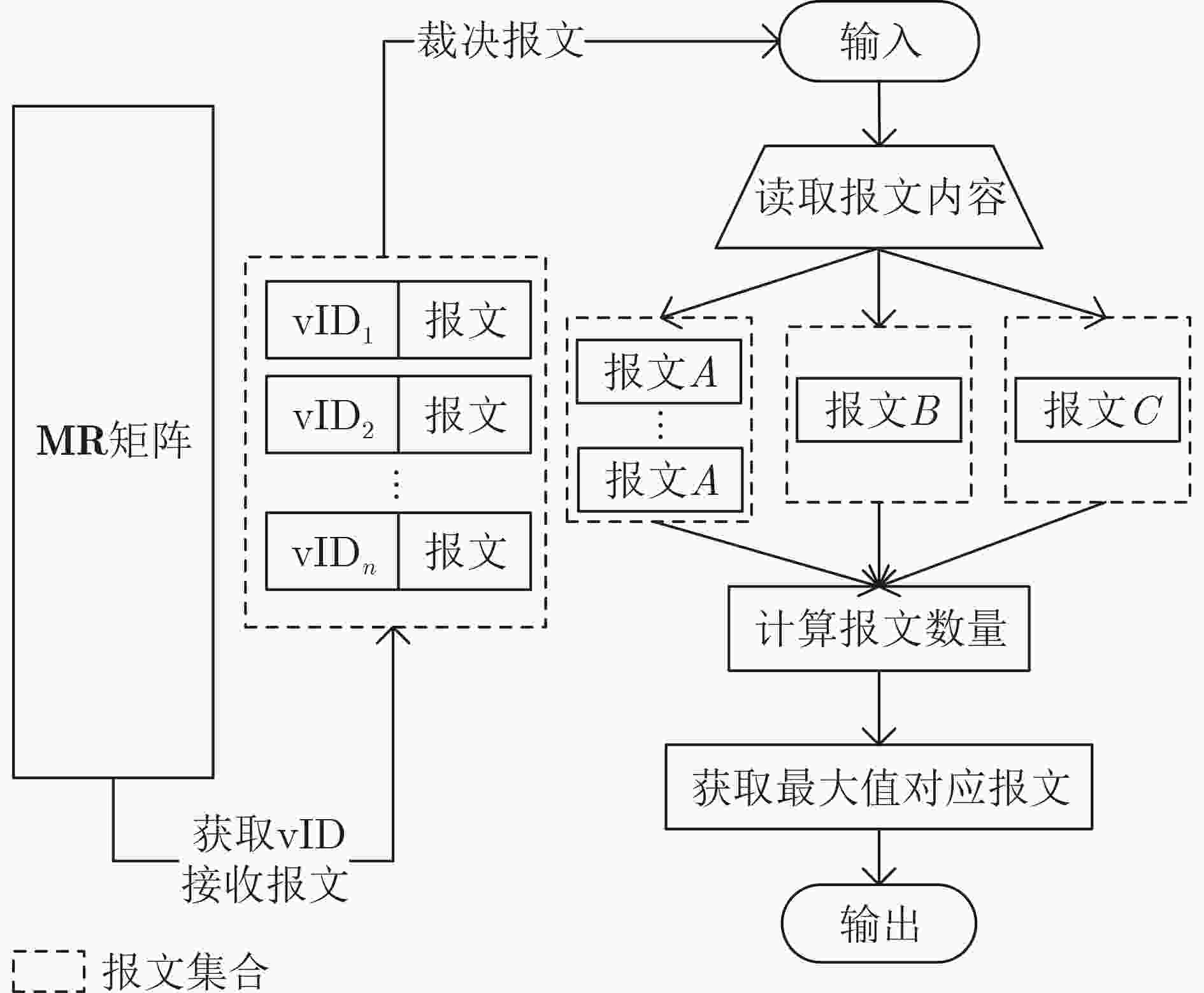
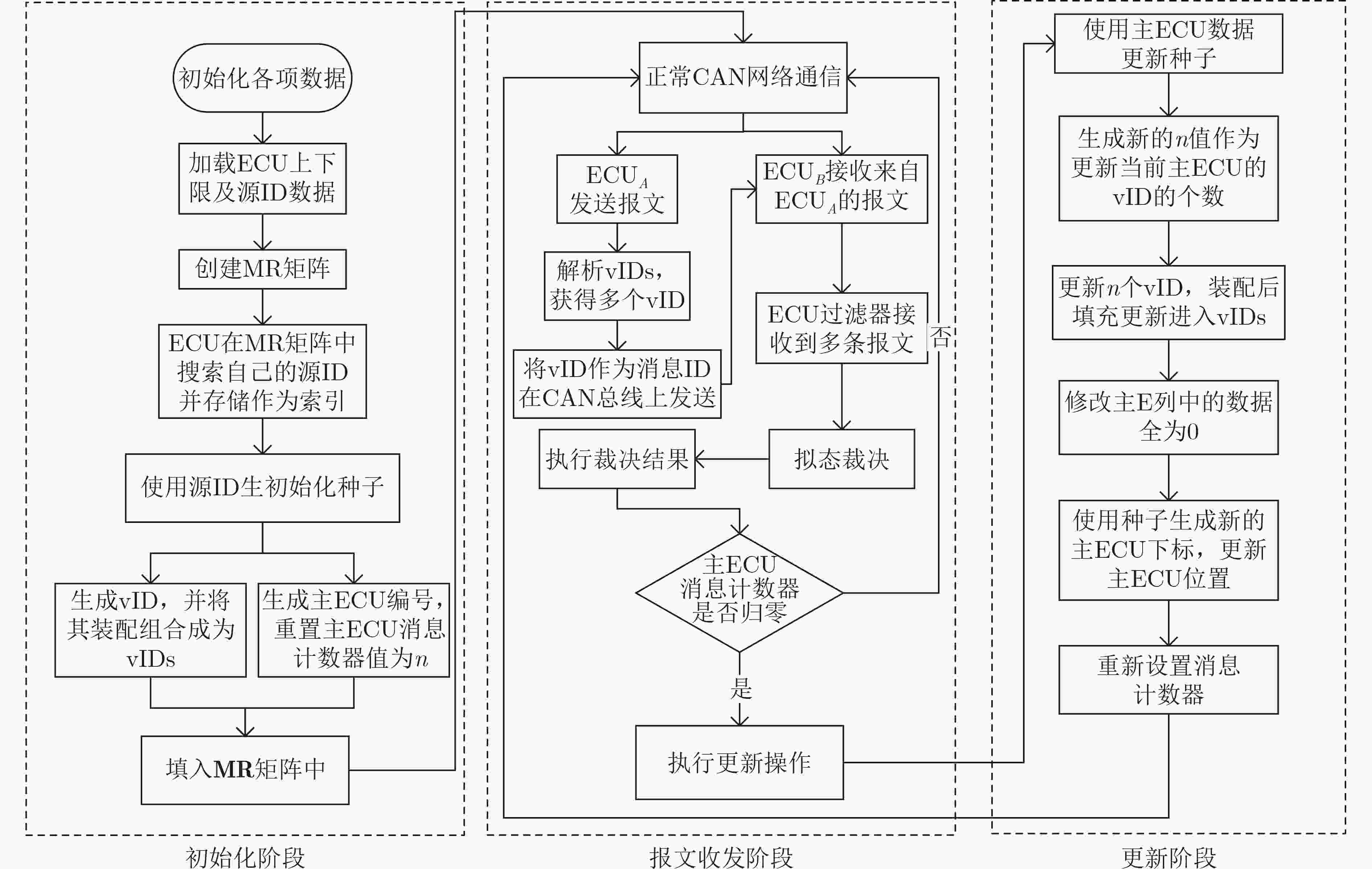
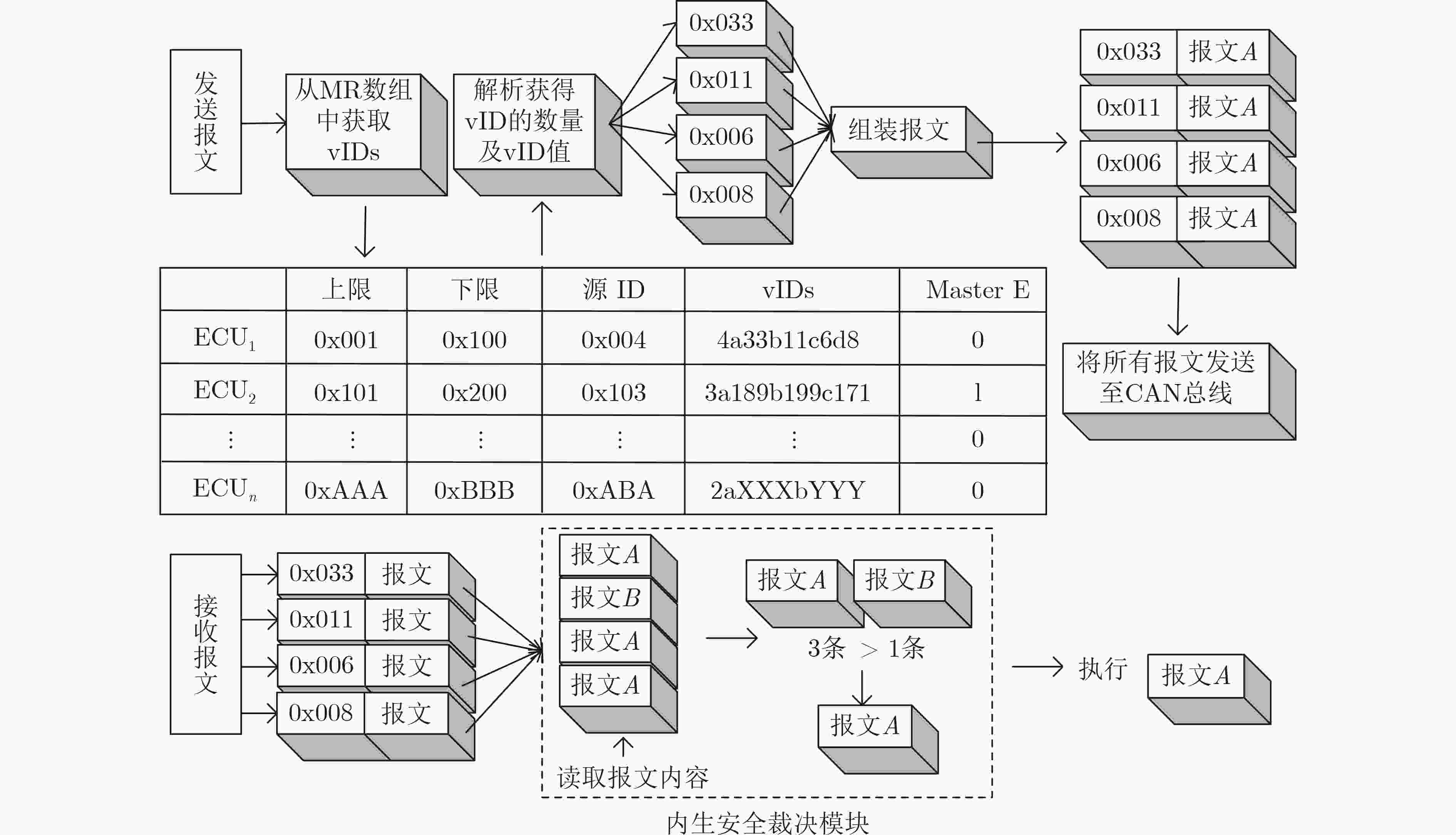
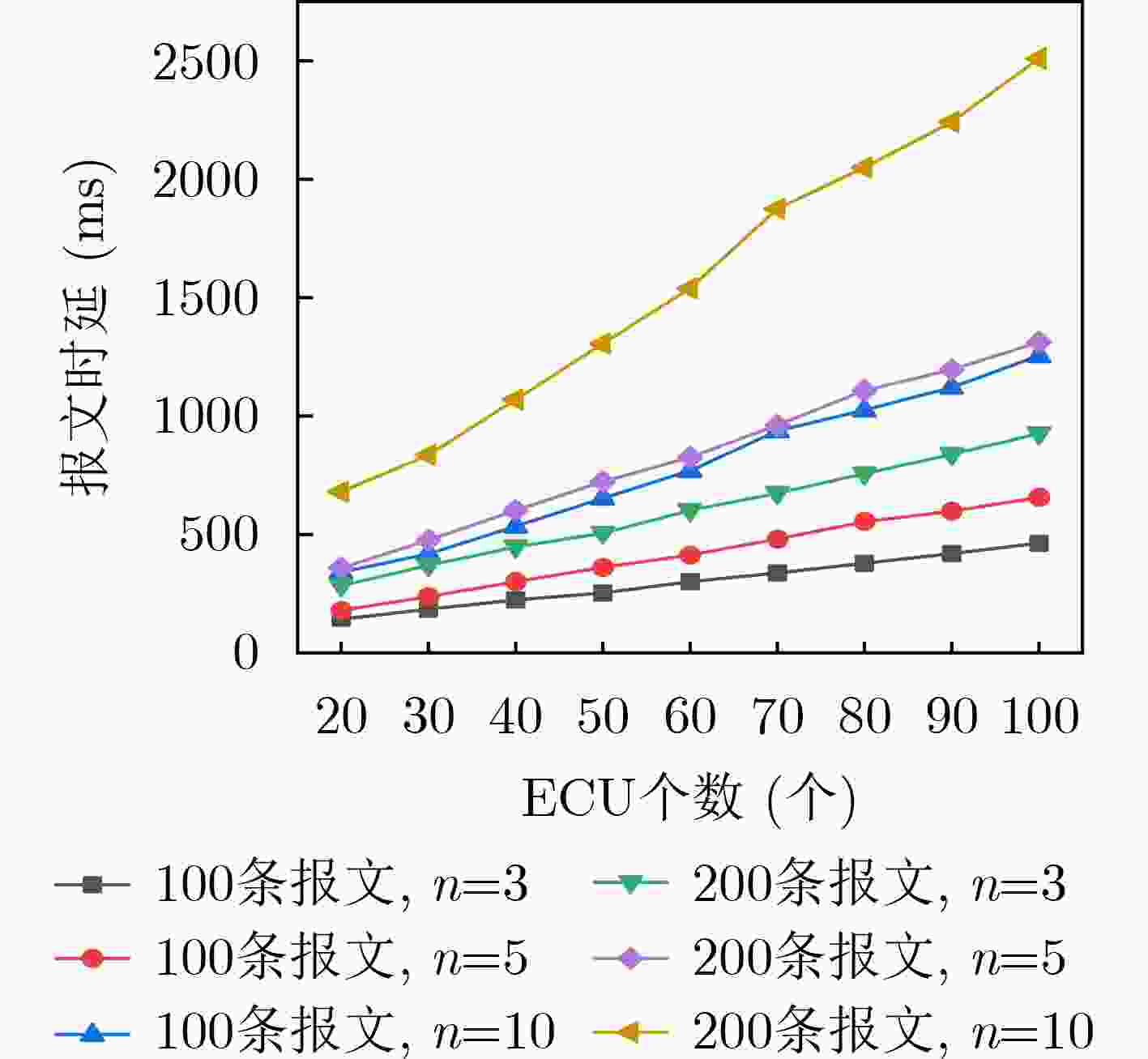
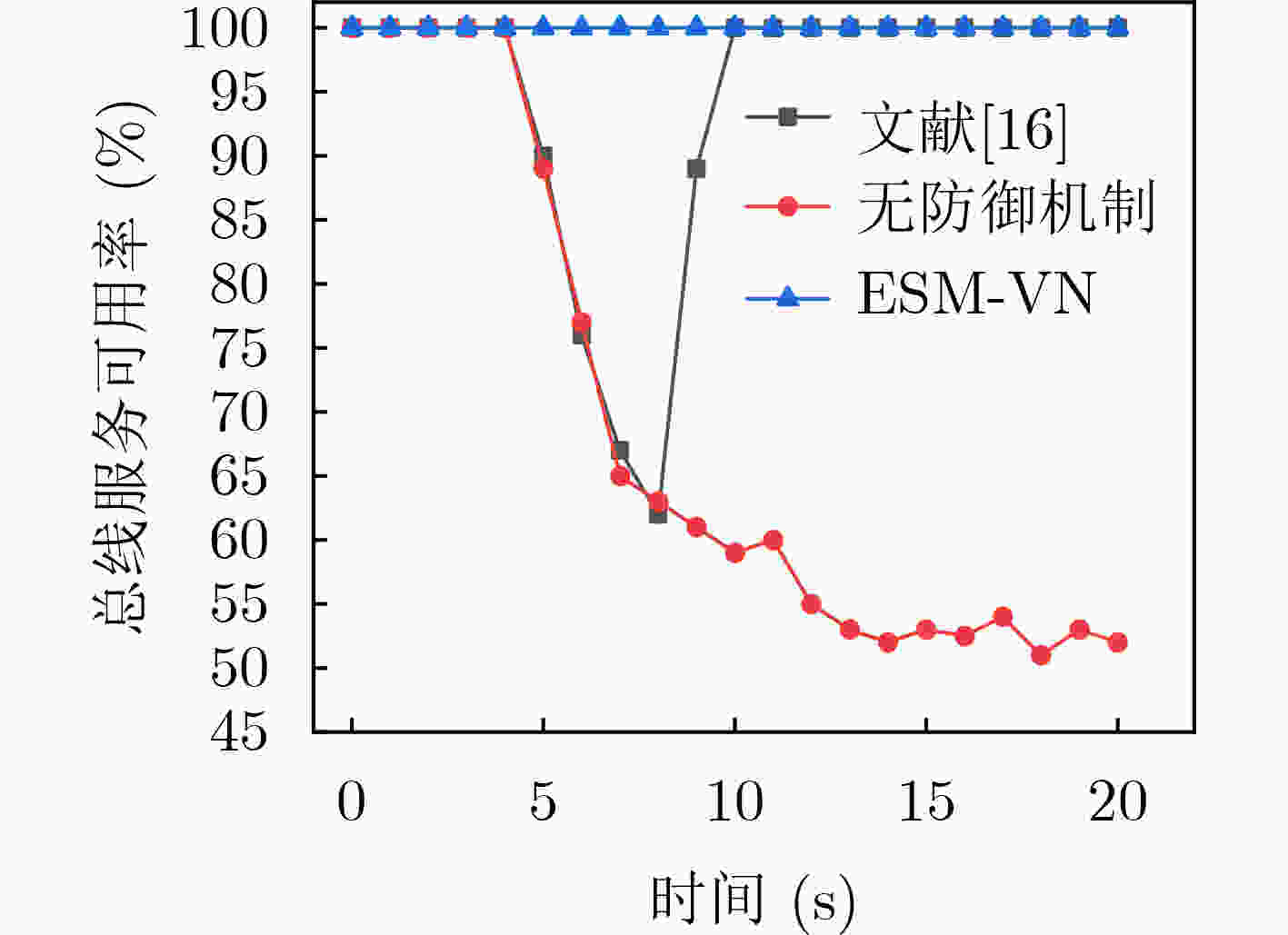
摘要: 针对车载网络通信报文容易被捕获重放的问题,该文提出一种基于动态异构冗余(DHR)架构的车载网络内生安全机制(ESM-VN)。首先,对车载网络重放攻击进行建模分析,总结重放攻击依赖的车载网络特征;然后结合网络空间内生安全理论,设计车载网络通信报文动态异构冗余的实现机制,通过拟态裁决和负反馈机制实现攻击感知与主动防御的协调统一。实验结果表明,相比于传统车载网络防御方法,该文所提机制能够在至少降低50%报文响应时延的同时,有效提高车载网络对重放攻击的防御能力。Abstract: To address the problem that in-vehicle cyber communication messages are easily captured, an Endogenous Security Mechanism for in-Vehicle Networks (ESM-VN) based on Dynamic Heterogeneous Redundancy (DHR) architecture is proposed. Firstly, the model of vehicle in network replay attack is analyzed, the network characteristics of replay attack are summarized. Then, the implementation mechanism of DHR of vehicle network communication message is designed by using the theory of network space endogenous security to realize the coordination and unification of attack perception and active defense through dynamic adjudication and negative feedback mechanism. Analysis and simulation results show that compared with the traditional in-vehicle network defense method, the proposed mechanism can reduce the response delay by at least 50% and improve effectively the defense capability of in-vehicle network against replay attack.
-
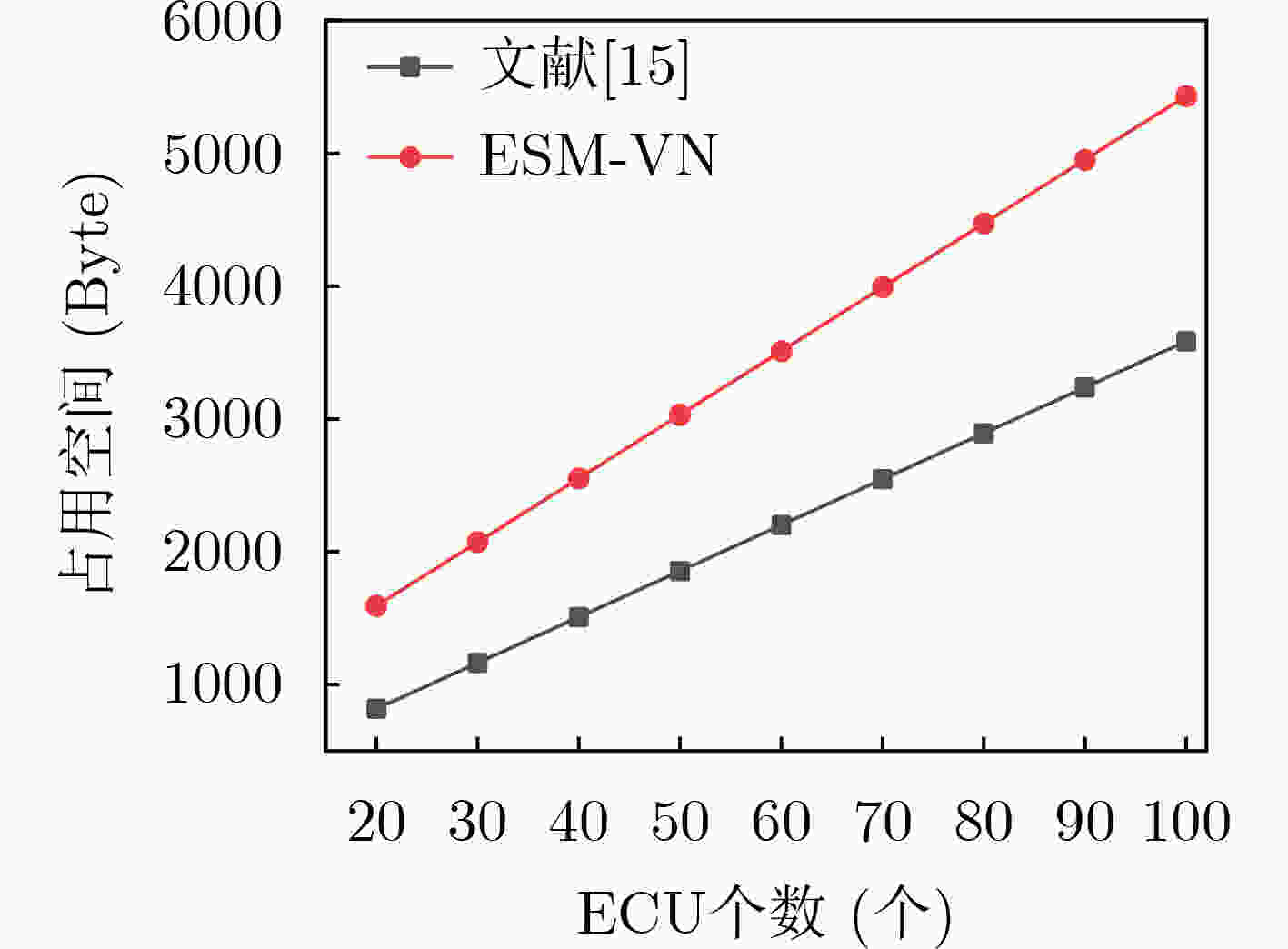
表 1 单节点占用空间对比(Byte)
ECU数量(个) 20 100 文献[15] 835.1 3519 ESM-VN 1523 5451 表 2 全节点空间对比(Byte)
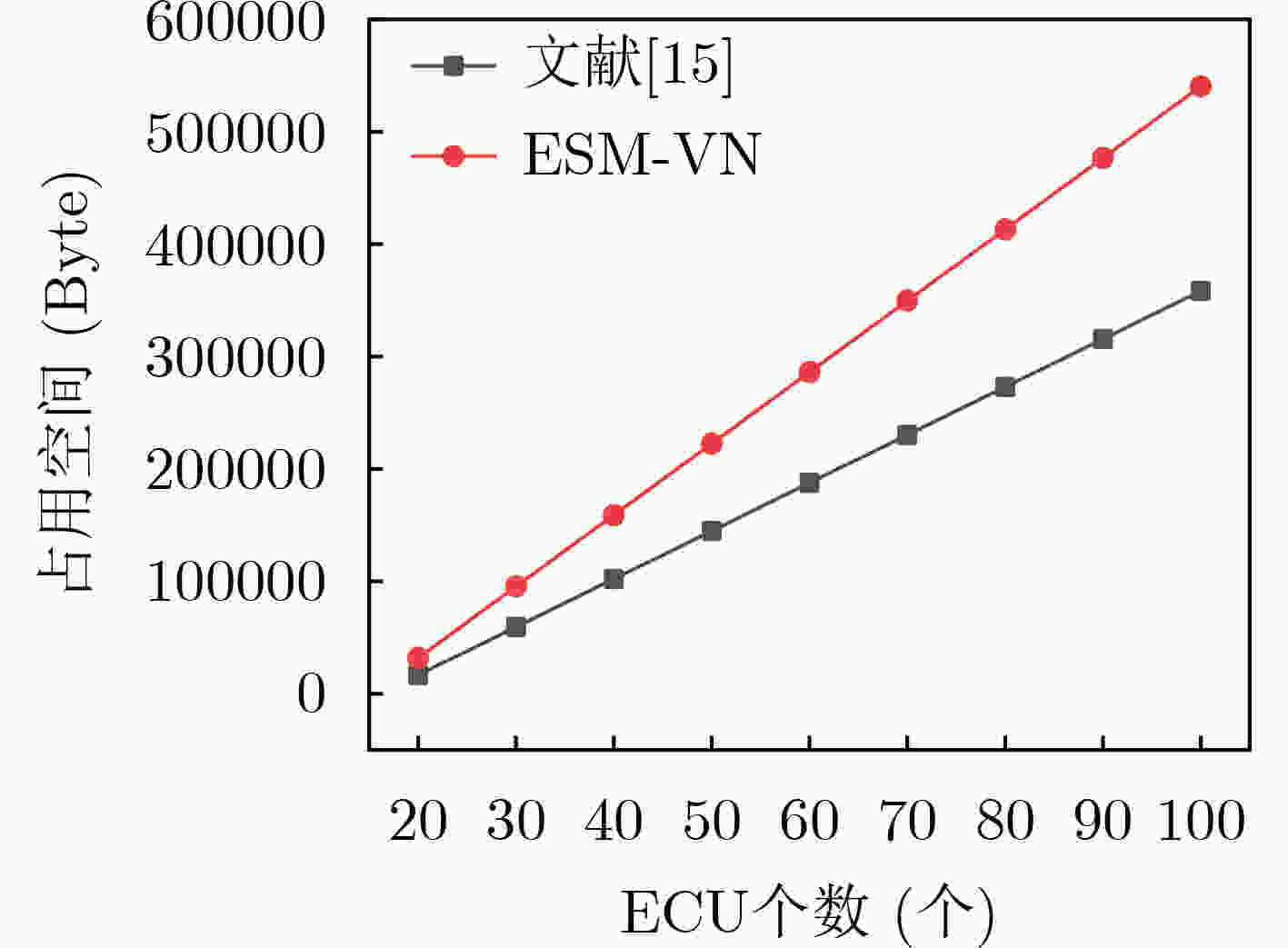
防御机制 20个ECU占用空间 100个ECU占用空间 文献[15] 16354 350178 ESM-VN 31157 543134 -
[1] 张林, 李琳, 张树祥. 车载网络安全的系统设计研究及关键技术开发[J]. 汽车电器, 2021(3): 19–25. doi: 10.13273/j.cnki.qcdq.2021.03.009ZHANG Lin, LI Lin, and ZHANG Shuxiang. Vehicle network safety system design and key technology development[J]. Auto Electric Parts, 2021(3): 19–25. doi: 10.13273/j.cnki.qcdq.2021.03.009 [2] 郑志超, 南金瑞, 南江峰. 车载网络CAN FD总线的应用前景和技术研究[J]. 现代电子技术, 2021, 44(1): 5–9. doi: 10.16652/j.issn.1004-373x.2021.01.002ZHENG Zhichao, NAN Jinrui, and NAN Jiangfeng. Research on application prospect and technology of CAN FD bus of vehicle network[J]. Modern Electronics Technique, 2021, 44(1): 5–9. doi: 10.16652/j.issn.1004-373x.2021.01.002 [3] Upstream Security. Upstream security's 2021 global automotive cybersecurity report[EB/OL]. https://upstream.auto/2021report/, 2021. [4] CUI Jin, LIEW L S, SABALIAUSKAITE G, et al. A review on safety failures, security attacks, and available countermeasures for autonomous vehicles[J]. Ad Hoc Networks, 2019, 90: 101823. doi: 10.1016/j.adhoc.2018.12.006 [5] GMIDEN M, GMIDEN M H, and TRABELSI H. Cryptographic and intrusion detection system for automotive CAN bus: Survey and contributions[C]. The 16th International Multi-Conference on Systems, Signals & Devices (SSD), Istanbul, Turkey, 2019: 158–163. [6] CUI Jin, SABALIAUSKAITE G, LIEW L S, et al. Collaborative analysis framework of safety and security for autonomous vehicles[J]. IEEE Access, 2019, 7: 148672–148683. doi: 10.1109/ACCESS.2019.2946632 [7] OH I, KIM T, YIM K, et al. A novel message-preserving scheme with format-preserving encryption for connected cars in multi-access edge computing[J]. Sensors, 2019, 19(18): 3869. doi: 10.3390/s19183869 [8] KANG M J and KANG J W. Intrusion detection system using deep neural network for in-vehicle network security[J]. PLoS One, 2016, 11(6): e0155781. doi: 10.1371/journal.pone.0155781 [9] 贾先锋, 宁玉桥, 武智. 网联汽车车载网络通讯的安全分析[J]. 汽车实用技术, 2021, 46(9): 14–19. doi: 10.16638/j.cnki.1671-7988.2021.09.005JIA Xianfeng, NING Yuqiao, and WU Zhi. Safety analysis of network communication in automobile[J]. Automobile Applied Technology, 2021, 46(9): 14–19. doi: 10.16638/j.cnki.1671-7988.2021.09.005 [10] 董琛. 车辆CAN总线入侵检测系统的研究与实现[D]. [硕士论文], 北京交通大学, 2019.DONG Chen. Research and implementation of intrusion detection system for in-vehicle CAN bus[D]. [Master dissertation], Beijing Jiaotong University, 2019. [11] 谭凯. 汽车CAN总线安全性模糊测试技术研究[D]. [硕士论文], 哈尔滨工业大学, 2020.TAN Kai. Research on fuzz testing technology of vehicle can bus security[D]. [Master dissertation], Harbin Institute of Technology, 2020. [12] PATSAKIS C, DELLIOS K, and BOUROCHE M. Towards a distributed secure in-vehicle communication architecture for modern vehicles[J]. Computers & Security, 2014, 40: 60–74. doi: 10.1016/j.cose.2013.11.003 [13] WOLF M and GENDRULLIS T. Design, implementation, and evaluation of a vehicular hardware security module[C]. The 14th International Conference on Information Security and Cryptology, Seoul, Korea, 2011: 302–318. [14] WOO S, MOON D, YOUN T Y, et al. CAN ID Shuffling Technique (CIST): Moving target defense strategy for protecting in-vehicle CAN[J]. IEEE Access, 2019, 7: 15521–15536. doi: 10.1109/ACCESS.2019.2892961 [15] BROWN R, MARTI A, JENKINS C, et al. Dynamic Address Validation Array (DAVA): A moving target defense protocol for CAN bus[C]. The 7th ACM Workshop on Moving Target Defense, New York, USA, 2020: 11–19. [16] YOON S, CHO J H, KIM D S, et al. Poster: Address shuffling based moving target defense for in-vehicle software-defined networks[C]. The 25th Annual International Conference on Mobile Computing and Networking, Los Cabos, Mexico, 2019: 103. [17] HU Hongchao, WU Jiangxing, WANG Zhenpeng, et al. Mimic defense: A designed-in cybersecurity defense framework[J]. IET Information Security, 2018, 12(3): 226–237. doi: 10.1049/iet-ifs.2017.0086 [18] 邬江兴. 网络空间内生安全——拟态防御与广义鲁棒控制[M]. 北京: 科学出版社, 2020: 587–588.WU Jiangxing. Cyberspace Mimic Defense—Generalized Robust Control and Endogenous Security[M]. Beijing: Science Press, 2020: 587–588. [19] 邬江兴. 网络空间拟态防御研究[J]. 信息安全学报, 2016, 1(4): 1–10. doi: 10.19363/j.cnki.cn10-1380/tn.2016.04.001WU Jiangxing. Research on cyber mimic defense[J]. Journal of Cyber Security, 2016, 1(4): 1–10. doi: 10.19363/j.cnki.cn10-1380/tn.2016.04.001 [20] 普黎明. 拟态云服务架构及关键技术研究[D]. [博士论文], 战略支援部队信息工程大学, 2021.PU Liming. Research on the key technologies of mimic cloud service architecture[D]. [Ph. D. dissertation], PLA Strategic Support Force Information Engineering University, 2021. -





 下载:
下载:


 下载:
下载:
