Collaborative Trustworthy Framework for Edge Computing
-
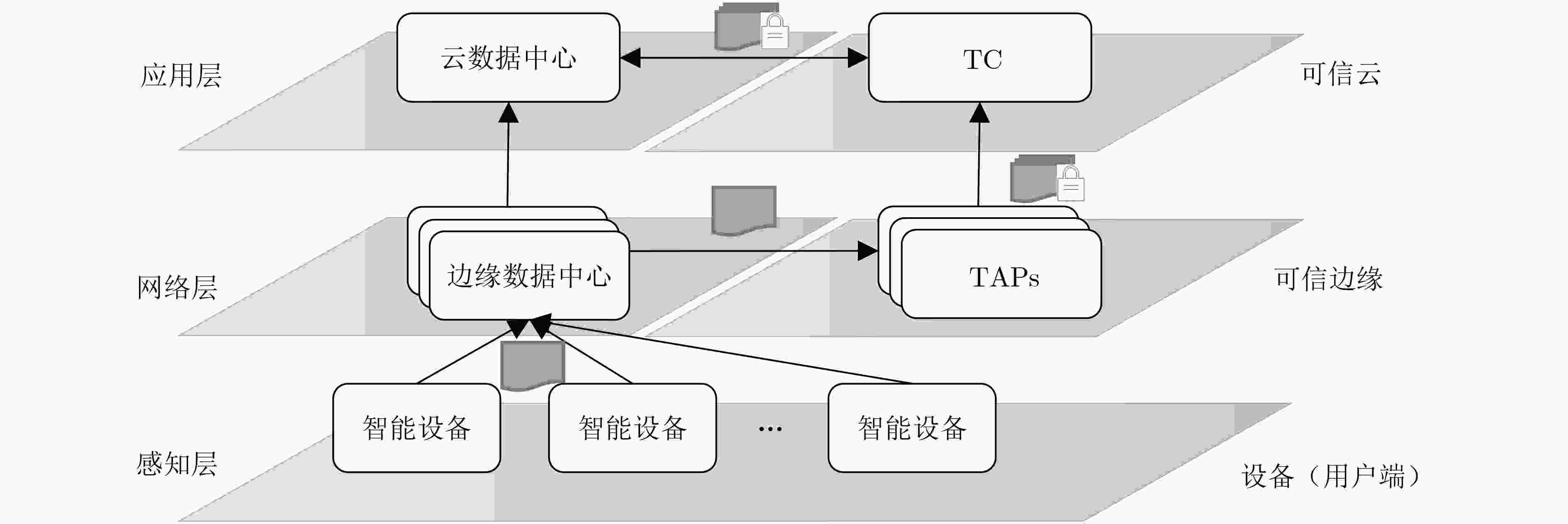
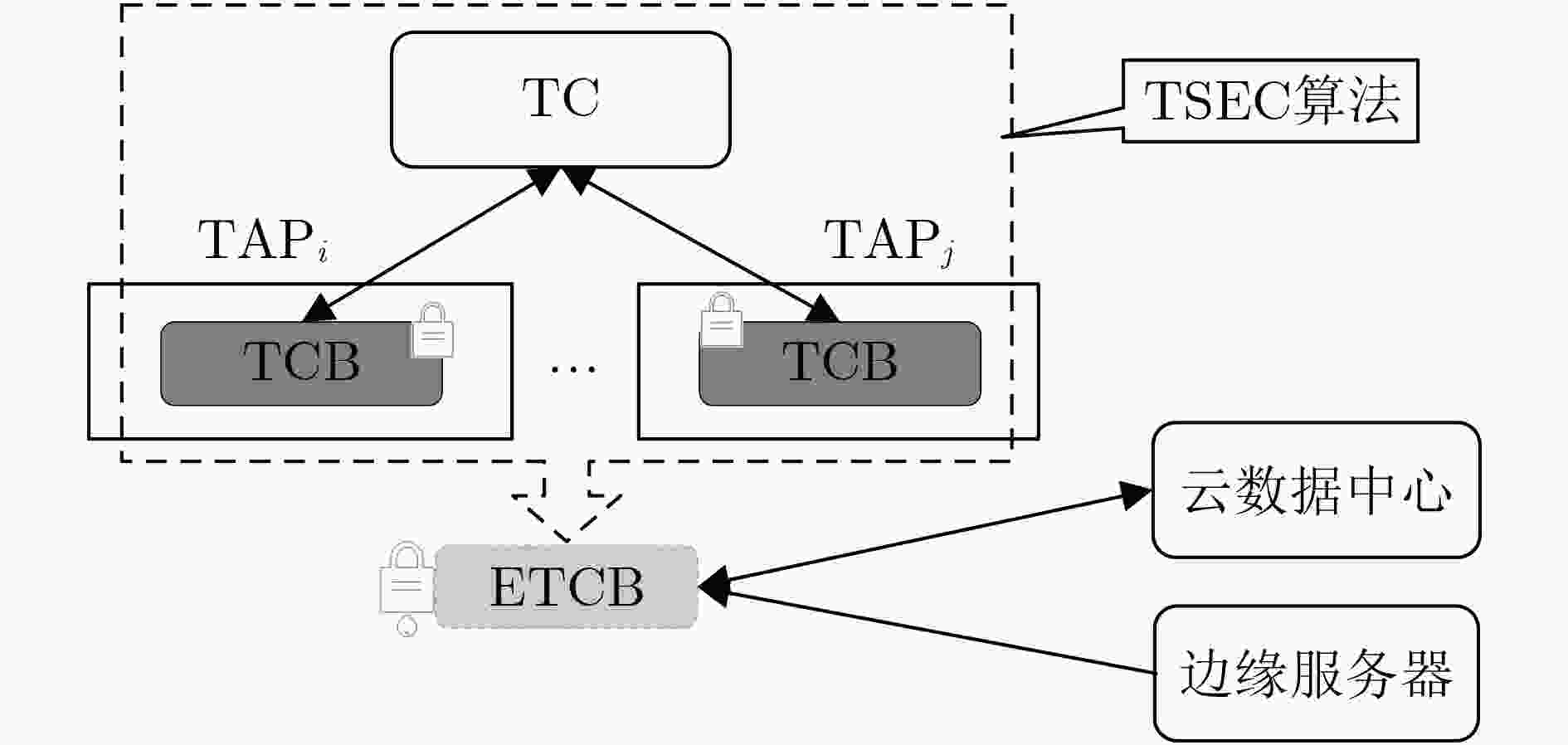
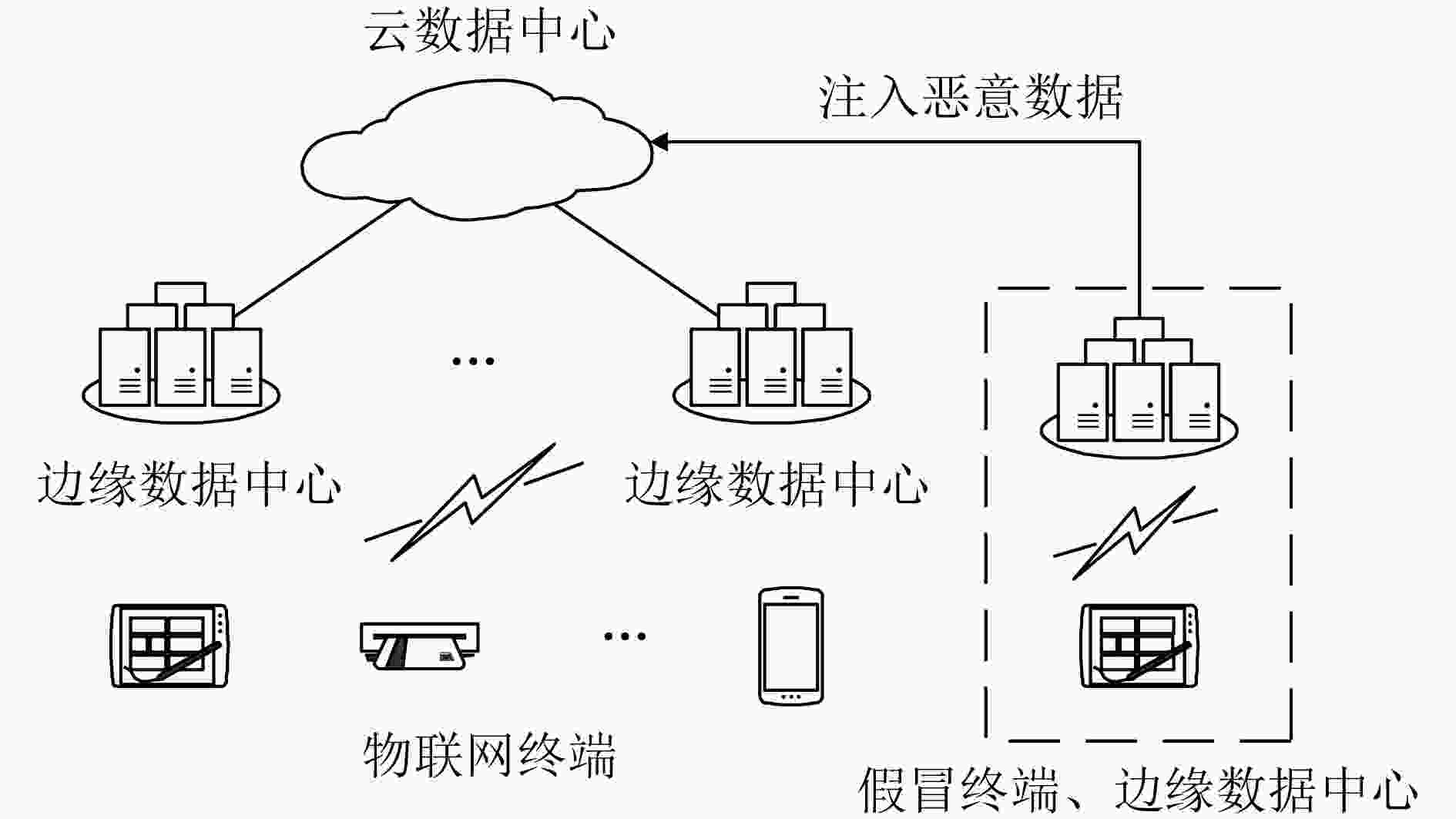
摘要: 在边缘计算环境中,边缘节点种类多样,分布范围广,工作环境差异大,这使得数据安全保障变得非常复杂,难以对其传输数据的可信性进行有效评价,从而影响整个边缘计算环境的安全性。针对上述问题,基于可信计算中密封密钥及群数字签名技术,该文提出边缘可信计算基(ETCB)的概念,并给出了构建ETCB的算法集,设计了面向边缘计算的可信数据验证协议,并对算法正确性和协议安全性进行了证明。该框架结合可信计算技术的优势,在不改变原有边缘计算模式的前提下,实现了数据的分布式可信验证。Abstract: In the edge computing environment, the edge nodes have various kinds, wide distribution range and great differences in working environment, which makes the data security guarantee become very complicated. It is difficult to evaluate the credibility of the data transmitted by nodes effectively, thus affecting the security of the entire edge computing environment. To solve the problem, a novel collaborative trustworthy framework for edge computing is presented in the paper. By using the advantage of trusted computing technology, the concept of Trusted Computing Base for Edge computing (ETCB) is introduced, algorithms of the constructing ETCB are given and a trusted data validation protocol for the edge computing is designed. Meanwhile, the correctness of the algorithms and the security analysis of the protocol are also given. The framework can realize the distributed trusted verification of data without changing the original edge computing mode.
-
表 1 Setup算法
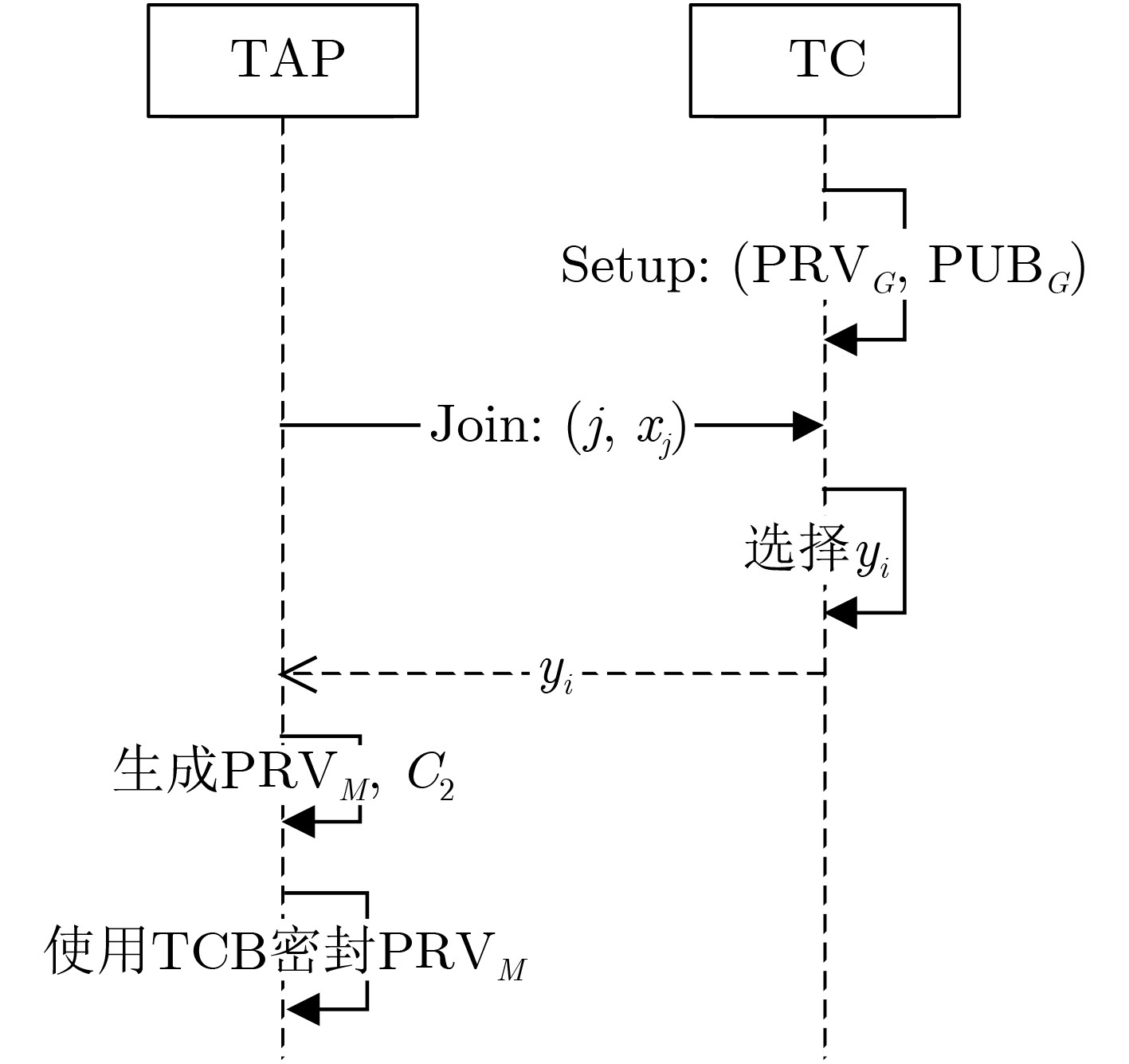
算法1:Setup 随机选取一个大素数p,随机选取一个生成元$g \in G $和$x \in Z_p^* $,
计算$h= g^x$,TAP簇公钥PUBG=(p, g, h),簇私钥PRVG=(p, g, x) 表 2 Join算法
算法2:Join 随机选取一个大素数p,随机选取一个生成元$g \in G$和$x \in Z_p^* $,计算$h= g^x $, TAP簇公钥PUBG=(p, g, h),簇私钥PRVG=(p, g, x) 假定B为新加入TAP簇进行数据可信认证的TAP,其身份标识为j,B选择$x_j=Z^*_p$,TC选择$y_j=Z_p^*$并发送给B。 B的私钥为${\rm{PRV} }_{{M} }=(y_j, h^{y_j}, x_j)$,同时计算 $C_2=h^{y_j}x_j $ (1) 执行Seal(PRVM) = ( {PRVM}s, MAC(PCR0, PCR1, ···)),将B的私钥密封,使其不可迁移,不可复制,只能在B内部使用,由TAP中的
TCB采用硬件的方式保证其可信性。表 3 Sign算法
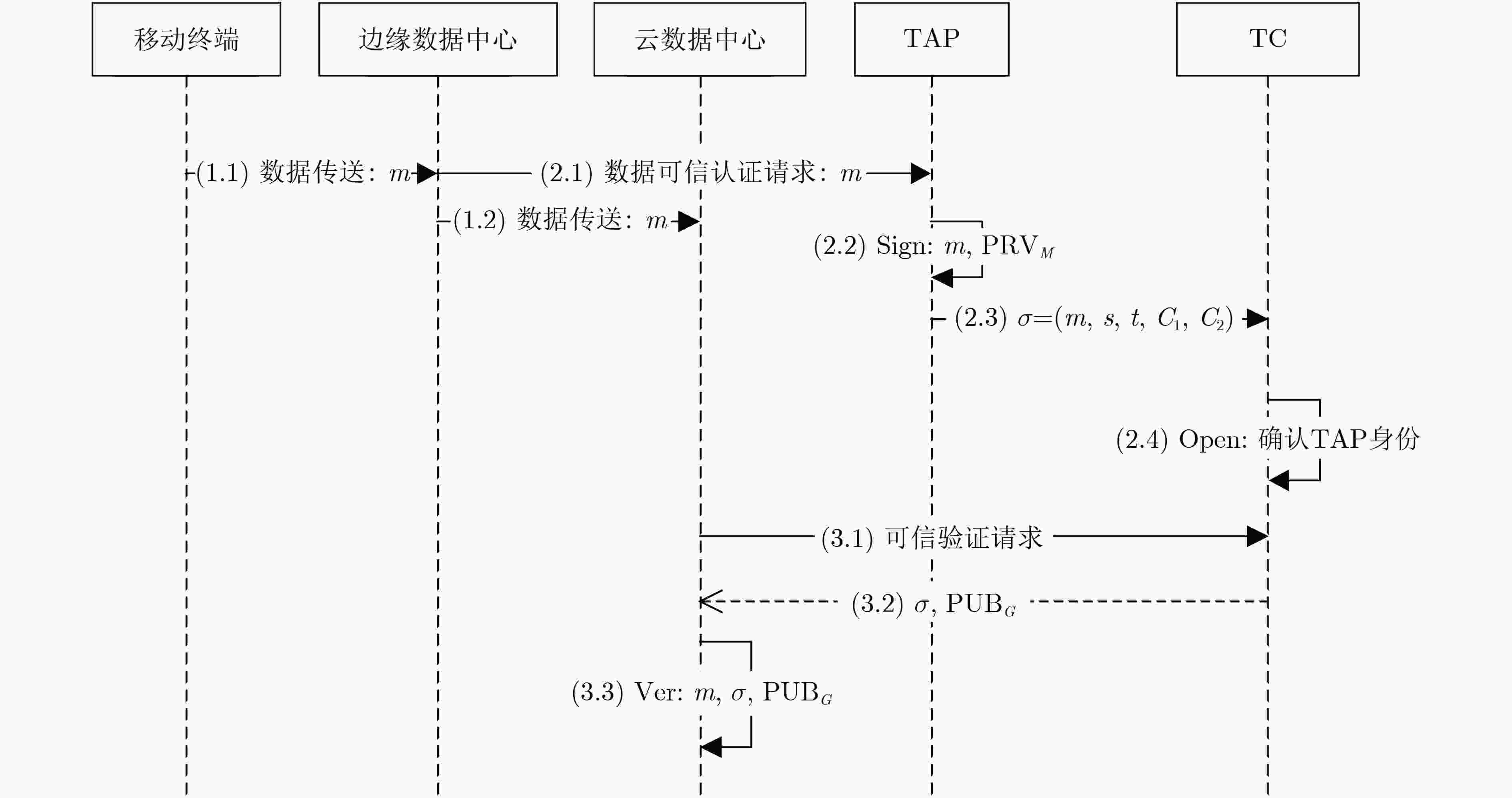
算法3:Sign 执行Unseal ( { PRVM }s, MAC(PCR0, PCR1, ···)) = PRVM释放成员私钥。 选择随机数k,其满足gcd(k, p–1)=1,计算 t=gkmod p (2) s=k–1(H(m)–t·yj)mod(p–1) (3) $C_1=g^{y_j} $ (4) 其中m为待认证的数据,生成的可信认证数据为 $\sigma = (m,s,t,{C_1},{C_2})\$ (5) 表 4 Ver算法
算法4:Ver 云数据中心收到数据及可信认证数据后,分别计算 gH(m) (6) $C_1^t{ {\cdot} }{ { {t} }^{ {s} } } { {\rm{mod} }\;{\rm{p}} }$ (7) 若两者结果相同,则收到的数据已通过某一TAP的可信认证,状态可信;否则判定数据为不可信状态。验证过程只使用PUBG和收到可信
认证数据,TAP的隐私信息也不会泄露给云数据中心。表 5 Open算法
算法5:Open TC执行 ${x_j} = {C_2}/C_1^x $ (8)
可以得到进行数据可信认证TAP的私钥,从而确定认证者。 -
[1] 施巍松, 孙辉, 曹杰, 等. 边缘计算: 万物互联时代新型计算模型[J]. 计算机研究与发展, 2017, 54(5): 907–924. doi: 10.7544/issn1000-1239.2017.20160941SHI Weisong, SUN Hui, CAO Jie, et al. Edge computing—an emerging computing model for the internet of everything era[J]. Journal of Computer Research and Development, 2017, 54(5): 907–924. doi: 10.7544/issn1000-1239.2017.20160941 [2] 张佳乐, 赵彦超, 陈兵, 等. 边缘计算数据安全与隐私保护研究综述[J]. 通信学报, 2018, 39(3): 1–21. doi: 10.11959/j.issn.1000-436x.2018037ZHANG Jiale, ZHAO Yanchao, CHEN Bing, et al. Survey on data security and privacy-preserving for the research of edge computing[J]. Journal on Communications, 2018, 39(3): 1–21. doi: 10.11959/j.issn.1000-436x.2018037 [3] XIAO Yinhao, JIA Yizhen, LIU Chunchi, et al. Edge computing security: State of the art and challenges[J]. Proceedings of the IEEE, 2019, 107(8): 1608–1631. doi: 10.1109/JPROC.2019.2918437 [4] ROMAN R, LOPEZ J, and MAMBO M. Mobile edge computing, fog et al. : A survey and analysis of security threats and challenges[J]. Future Generation Computer Systems, 2018, 78: 680–698. doi: 10.1016/j.future.2016.11.009 [5] 黄坚会, 沈昌祥, 谢文录. TPCM三阶三路安全可信平台防护架构[J]. 武汉大学学报:理学版, 2018, 64(2): 109–114. doi: 10.14188/j.1671-8836.2018.02.002HUANG Jianhui, SHEN Changxiang, and XIE Wenlu. The TPCM 3P3C defense architecture of safety and trusted platform[J]. Journal of Wuhan University:Natural Science Edition, 2018, 64(2): 109–114. doi: 10.14188/j.1671-8836.2018.02.002 [6] 何欣枫, 田俊峰, 刘凡鸣. 可信云平台技术综述[J]. 通信学报, 2019, 40(2): 154–163. doi: 10.11959/j.issn.1000-436x.2019035HE Xinfeng, TIAN Junfeng, and LIU Fanming. Survey on trusted cloud platform technology[J]. Journal on Communications, 2019, 40(2): 154–163. doi: 10.11959/j.issn.1000-436x.2019035 [7] WANG Tian, LUO Hao, ZHENG Xi, et al. Crowdsourcing mechanism for trust evaluation in CPCS based on intelligent mobile edge computing[J]. ACM Transactions on Intelligent Systems and Technology, 2019, 10(6): 62. doi: 10.1145/3324926 [8] 乐光学, 戴亚盛, 杨晓慧, 等. 边缘计算可信协同服务策略建模[J]. 计算机研究与发展, 2020, 57(5): 1080–1102.YUE Guangxue, DAI Yasheng, YANG Xiaohui, et al. Model of trusted cooperative service for edge computing[J]. Journal of Computer Research and Development, 2020, 57(5): 1080–1102. [9] MISHRA D, DHARMINDER D, YADAV P, et al. A provably secure dynamic ID-based authenticated key agreement framework for mobile edge computing without a trusted party[J]. Journal of Information Security and Applications, 2020, 55: 102648. doi: 10.1016/j.jisa.2020.102648 [10] KANG Baoyuan, HAN Yanbao, QIAN Kun, et al. Analysis and improvement on an authentication protocol for IoT-enabled devices in distributed cloud computing environment[J]. Mathematical Problems in Engineering, 2020, 2020: 1970798. doi: 10.1155/2020/1970798 [11] HUANG Huihui, LU Siqi, WU Zehui, et al. An Efficient Authentication and Key Agreement Protocol for IoT-enabled Devices in Distributed Cloud Computing Architecture[J]. EURASIP Journal on Wireless Communications and Networking, 2021, 2021: 150. doi: 10.1186/s13638-021-02022-1 [12] PSARAS I. Decentralised edge-computing and IoT through distributed trust[C]. The 16th Annual International Conference on Mobile Systems, Applications, and Services, Munich, Germany, 2018: 505–507. [13] CUI Laizhong, YANG Shu, CHEN Ziteng, et al. A decentralized and trusted edge computing platform for internet of things[J]. IEEE Internet of Things Journal, 2020, 7(5): 3910–3922. doi: 10.1109/JIOT.2019.2951619 [14] GUO Shaoyong, DAI Yao, GUO Song, et al. Blockchain meets edge computing: Stackelberg game and double auction based task offloading for mobile blockchain[J]. IEEE Transactions on Vehicular Technology, 2020, 69(5): 5549–5561. doi: 10.1109/TVT.2020.2982000 [15] 宁振宇, 张锋巍, 施巍松. 基于边缘计算的可信执行环境研究[J]. 计算机研究与发展, 2019, 56(7): 1441–1453. doi: 10.7544/issn1000-1239.2019.20180522NING Zhenyu, ZHANG Fengwei, and SHI Weisong. A study of using TEE on edge computing[J]. Journal of Computer Research and Development, 2019, 56(7): 1441–1453. doi: 10.7544/issn1000-1239.2019.20180522 [16] 王冠, 袁华浩. 基于可信根服务器的虚拟TCM密钥管理功能研究[J]. 信息网络安全, 2016(4): 17–22.WANG Guan and YUAN Huahao. Research of virtual trusted cryptography module's secret key management based on the trusted root server[J]. Netinfo Security, 2016(4): 17–22. [17] ARMANDO A, BASIN D, BOICHUT Y, et al. The AVISPA tool for the automated validation of internet security protocols and applications[C]. The 17th International Conference on Computer Aided Verification, Edinburgh, UK, 2005: 281–285. [18] VIGANÒ L. Automated security protocol analysis with the AVISPA tool[J]. Electronic Notes in Theoretical Computer Science, 2006, 155: 61–86. doi: 10.1016/j.entcs.2005.11.052 -





 下载:
下载:
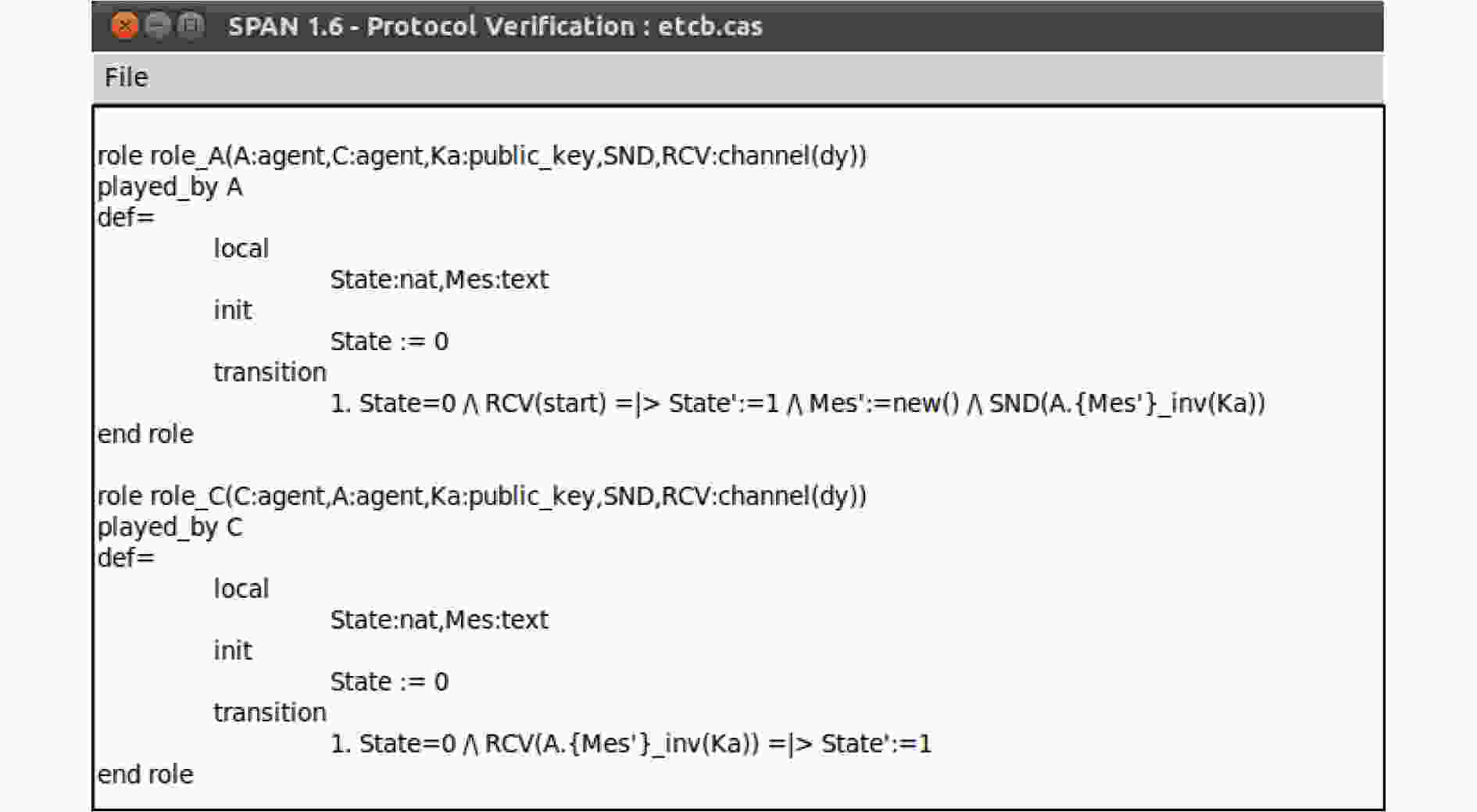
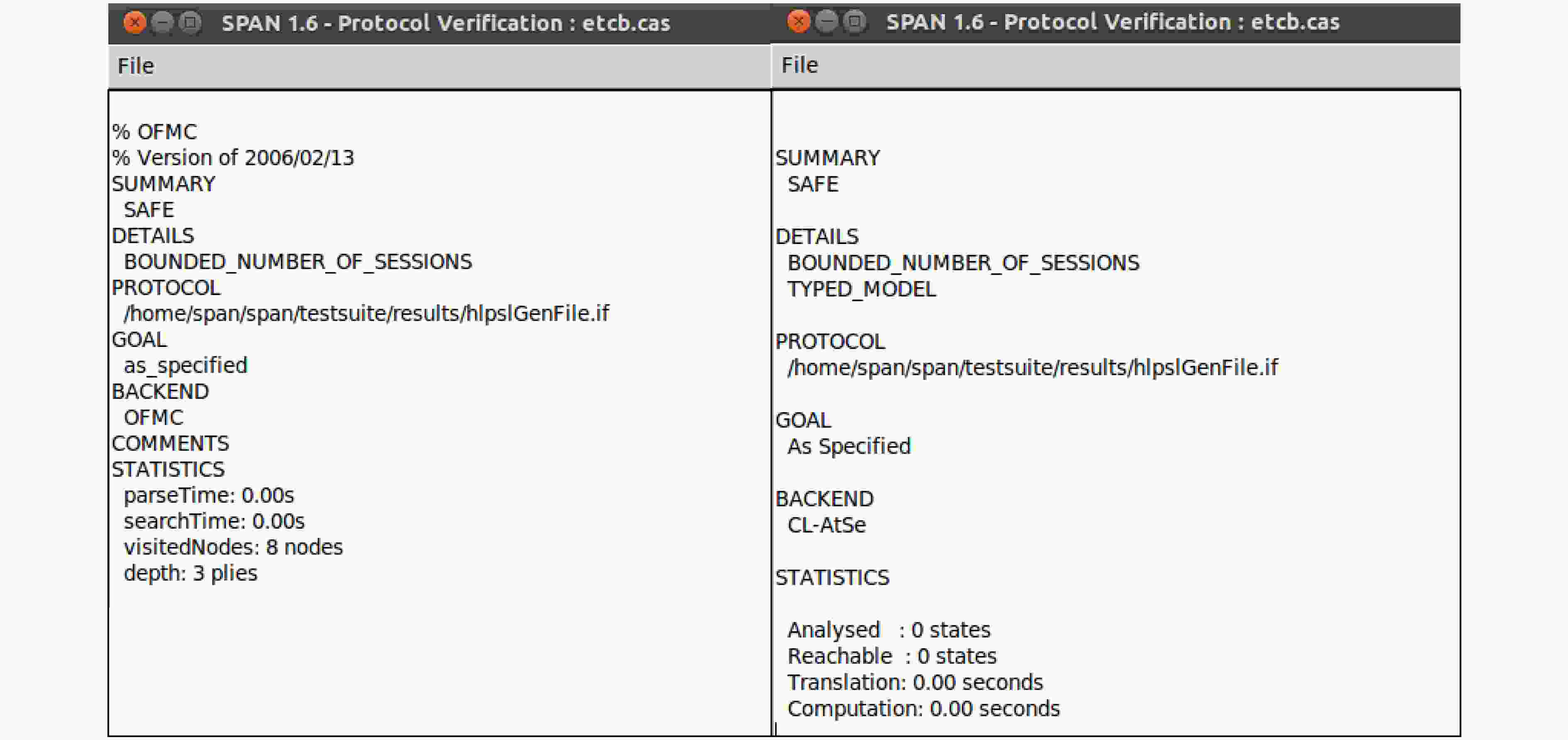


 下载:
下载:
