Efficient Privacy Preserving Authentication Scheme for Online E-invoice Service
-
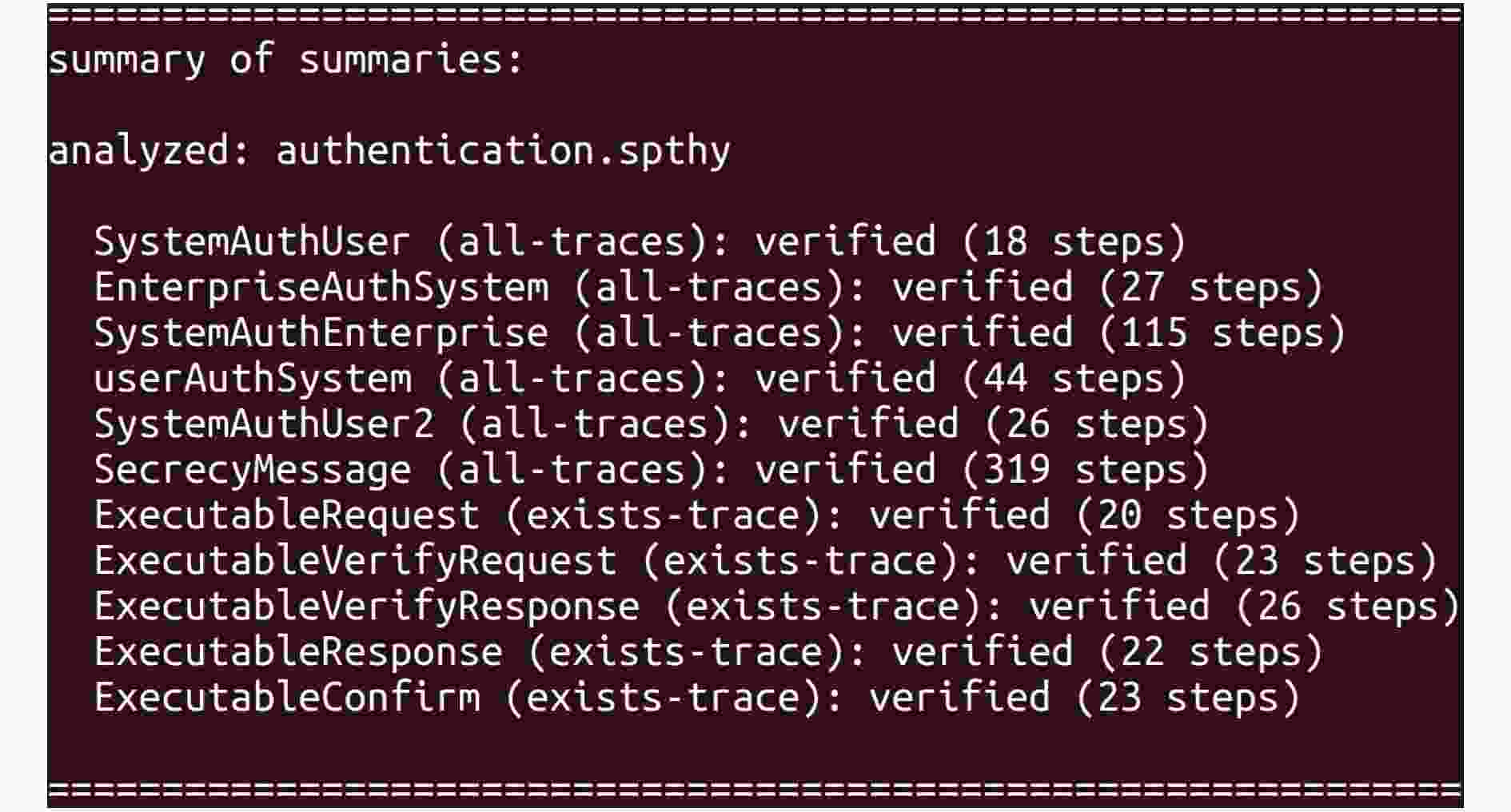
摘要: 近年来,发票形式由传统的纸质凭据向电子凭据转变。相比于开具纸质凭据,在线开具电子凭据具有流程简化、成本降低以及便于存储等优势。但是,如何保证在线开具电子凭据服务中实体身份的合法性以及身份信息的隐私性是当前研究的重点问题。为了解决此问题,利用预共享密钥机制,该文提出一种隐私保护在线开具电子凭据的认证方案。在此方案中,合法用户与企业完成交易后可以本地在线发起开票申请,国家税务总局的电子凭据系统成功核验实体身份和交易信息后可为该用户提供电子凭据。安全和性能分析结果表明提出方案可以在耗费较少认证开销的情况下提供鲁棒的安全属性。Abstract: In recent years, the form of invoice has changed from the traditional paper invoice to e-invoice. Compared with issuing paper invoice, there are the advantages of simpler process, lower cost, and easier storage for online issuing e-invoice. However, how to ensure the legitimacy of user identity and the privacy of identity information in online issuing e-invoice service is the focus issue of current research. In order to solve this issue, by using the pre- shared key mechanism, a privacy preserving authentication scheme for online issuing e-invoice is proposed. By this scheme, a legitimate user who has completed a transaction with an enterprise can initiate an e-invoice request locally and online, and the e-invoice system of the State Administration of taxation can provide the user with e-invoices after verifying the identity information and transaction information successfully. Security and performance analysis results show that the proposed scheme can provide robust security properties with less authentication overhead.
-
Key words:
- Network /
- E-invoice /
- Authentication /
- Privacy preserving
-
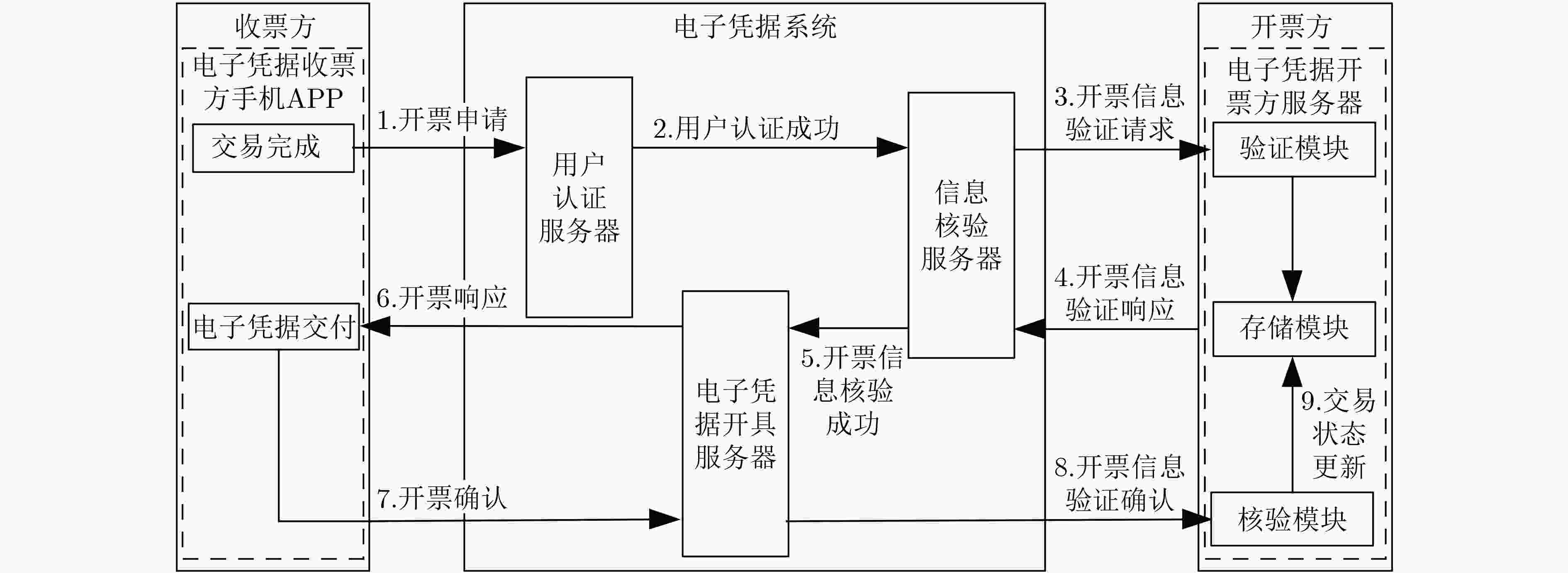
表 1 符号定义
符号 定义 符号 定义 $q/Z_q^*$ 大素数/模q的正整数集合 $ {M_j}/{m_j} $ 开票方的企业信息/开票方存储的订单交易信息 $E/G$ 椭圆曲线$E$上的循环群$G$ $ {h_{\text{1}}}/{h_{\text{2}}} $ $ {(0,1)^*} \to {(0,1)^l}/{(0,1)^*} \to {(0,1)^k} $ $P$ 循环群$G$的生成元 $ {f_{\text{1}}} $ ${(0,1)^*}\xrightarrow{ {{\rm{key}}} }{(0,1)^l}$ $ {K_{\text{e}}} $ 电子凭据系统主密钥 $ {\text{bind}} $ 身份证信息与人脸信息的绑定函数 $ {\text{sk/pk}} $ 电子凭据系统私钥/公钥 $ {\text{KDF}} $ $ {(0,1)^*} \to {(0,1)^l} $ ${{\rm{eID}}_i}/{{\rm{HID}}_i}$ 收票方用户i的身份证信息/匿名身份标识信息 $ {\text{ENC/DEC}} $ 对称加密/解密函数 $ {K_i}/{B_i} $ 收票方用户i的长期共享密钥/人脸信息 $ {\text{Gen/Rep}} $ 模糊提取生成/再生函数 $ {\alpha _i}/{\beta _i} $ 人脸信息相关的随机字符串/辅助字符串 $ || $ 连接符 ${{\rm{sID}}_j}/{K_j}$ 开票方j的企业标识/长期共享密钥 $ \oplus $ 异或操作 $ {t_{{\text{i0}}}}/{t_{{\text{j0}}}}/{t_i}/{t_{{\text{ej}}}}/{t_j} $ 时间戳 $ \cdot $ 椭圆曲线上的点乘操作 $ {M_i}/{m_i}/{M_{\text{e}}} $ 收票方的订单交易信息/订单编号信息/电子凭据信息 表 2 计算开销
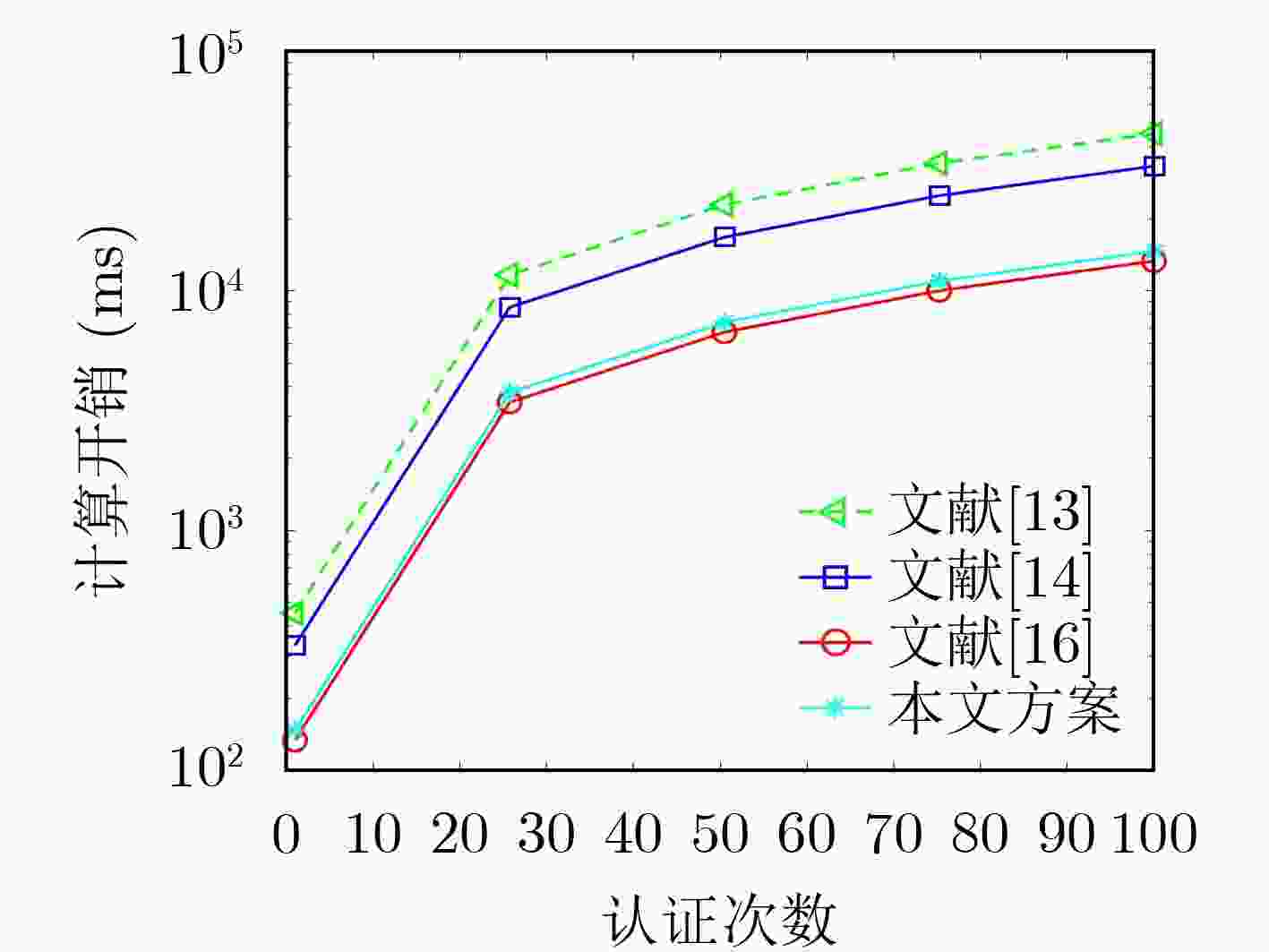
方案 开具电子凭据认证过程(ms) 文献[13] $ 22{T_{\text{h}}} + 6{T_{\text{p}}}{\text{ + }}{T_{\text{r}}}{\text{ = }}452.56 $ 文献[14] $19{T_{\text{h}}} + 3{T_{\text{p}}}{\text{ + 8}}{T_{\text{s}}}{\text{ + }}{T_{\text{r}}}{\text{ = }}331.42$ 文献[16] $16{T_{\text{h}}} + 4{T_{\text{c}}}{\text{ + }}{T_{\text{e}}}{\text{ + }}{T_{{\text{crt}}}}{\text{ = }}133.08$ 本文方案 $27{T_{\text{h}}} + 8{T_{\text{s}}}{\text{ + }}{T_{\text{r}}}{\text{ = }}146.18$ -
[1] 王玢. 电子发票系统与企业会计信息系统的协同对接研究[D]. [硕士论文], 首都经济贸易大学, 2017.WANG Fen. Study on synergy effect between E-invoice system and enterprise’s accounting system[D]. [Master dissertation], Capital University of Economics and Business, 2017. [2] 徐丽军, 刘馨月. 关于电子发票推行的安全性问题研究[J]. 辽宁经济, 2018(7): 90–91. doi: 10.14041/j.cnki.1003-4617.2018.07.040XU Lijun and LIU Xinyue. Research on the security of electronic invoice[J]. Liaoning Economy, 2018(7): 90–91. doi: 10.14041/j.cnki.1003-4617.2018.07.040 [3] 张庆胜, 刘海法. 基于区块链的电子发票系统研究[J]. 信息安全研究, 2017, 3(6): 516–522. doi: 10.3969/j.issn.2096-1057.2017.06.005ZHANG Qingsheng and LIU Haifa. Research of electronic invoice system based on block chain[J]. Journal of Information Security Research, 2017, 3(6): 516–522. doi: 10.3969/j.issn.2096-1057.2017.06.005 [4] 李涛, 杜晓平, 杜晓媛, 等. 基于“互联网+”的发票一体化管理平台[J]. 国网技术学院学报, 2019, 22(4): 48–51. doi: 10.3969/j.issn.1008-3162.2019.04.014LI Tao, DU Xiaoping, DU Xiaoyuan, et al. Invoice integrated management platform based on "Internet Plus"[J]. Journal of State Grid Technology College, 2019, 22(4): 48–51. doi: 10.3969/j.issn.1008-3162.2019.04.014 [5] 郝天新, 王海翔. 网络发票技术解决方案[J]. 现代电信科技, 2011, 41(10): 67–71. doi: 10.3969/j.issn.1002-5316.2011.10.024HAO Tianxin and WANG Haixiang. Technology solution for online invoicing[J]. Modern Science &Technology of Telecommunications, 2011, 41(10): 67–71. doi: 10.3969/j.issn.1002-5316.2011.10.024 [6] JAIN S and ASADULLAH A M. Aggregating bills and invoices on cloud for anytime anywhere access: A sustainable system[C]. The 3rd International Conference on Services in Emerging Markets, Mysore, India, 2012: 1–5. [7] CHU Hongyang, CHAI Yueting, LIU Yi, et al. A novel E-Invoice Framework towards data-oriented taxation system[C]. The IEEE 18th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Hsinchu, China, 2014: 242–246. [8] ZHANG Wei. Online invoicing system based on QR code recognition and cloud storage[C]. The 2nd IEEE Advanced Information Management, Communicates, Electronic and Automation Control Conference (IMCEC), Xi'an, China, 2018: 2576–2579. [9] ŠPANIĆ D, RISTIĆ D, and VRDOLJAK B. An electronic invoicing system[C]. The 11th International Conference on Telecommunications, Graz, Austria, 2011: 149–156. [10] CHOI Y, LEE D, KIM J, et al. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography[J]. Sensors, 2014, 14(6): 10081–10106. doi: 10.3390/s140610081 [11] HE Debiao, KUMAR N, and CHILAMKURTI N. A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks[J]. Information Sciences, 2015, 321: 263–277. doi: 10.1016/j.ins.2015.02.010 [12] CHANG C C and LE H D. A provably secure, efficient, and flexible authentication scheme for Ad hoc wireless sensor networks[J]. IEEE Transactions on Wireless Communications, 2016, 15(1): 357–366. doi: 10.1109/TWC.2015.2473165 [13] LI Xiong, NIU Jianwei, BHUIYAN M Z A, et al. A robust ECC-based provable secure authentication protocol with privacy preserving for industrial internet of things[J]. IEEE Transactions on Industrial Informatics, 2018, 14(8): 3599–3609. doi: 10.1109/TII.2017.2773666 [14] LI Xiong, PENG Jieyao, OBAIDAT M S, et al. A secure three-factor user authentication protocol with forward secrecy for wireless medical sensor network systems[J]. IEEE Systems Journal, 2020, 14(1): 39–50. doi: 10.1109/JSYST.2019.2899580 [15] CUI Jie, ZHANG Xiaoyu, ZHONG Hong, et al. Extensible conditional privacy protection authentication scheme for secure vehicular networks in a multi-cloud environment[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 1654–1667. doi: 10.1109/TIFS.2019.2946933 [16] XU Guoai, WANG Feifei, ZHANG Miao, et al. Efficient and provably secure anonymous user authentication scheme for patient monitoring using wireless medical sensor networks[J]. IEEE Access, 2020, 8: 47282–47294. doi: 10.1109/ACCESS.2020.2978891 [17] YANG Qingyou, XUE Kaiping, XU Jie, et al. AnFRA: Anonymous and fast roaming authentication for space information network[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(2): 486–497. doi: 10.1109/TIFS.2018.2854740 [18] WANG Feifei, XU Guoai, and XU Guosheng. A provably secure anonymous biometrics-based authentication scheme for wireless sensor Networks Using Chaotic Map[J]. IEEE Access, 2019, 7: 101596–101608. doi: 10.1109/ACCESS.2019.2930542 [19] QI Mingping, CHEN Jianhua, and CHEN Yitao. A secure biometrics-based authentication key exchange protocol for multi-server TMIS using ECC[J]. Computer Methods and Programs in Biomedicine, 2018, 164: 101–109. doi: 10.1016/j.cmpb.2018.07.008 [20] The Tamarin Team. Tamarin-Prover manual security protocol analysis in the symbolic model[EB/OL]. https://tamarin-prover.github.io/manual/tex/tamarin-manual.pdf, 2021. [21] BASIN D, CREMERS C, KIM T H J, et al. Design, analysis, and implementation of ARPKI: An attack-resilient public-key infrastructure[J]. IEEE Transactions on Dependable and Secure Computing, 2018, 15(3): 393–408. doi: 10.1109/TDSC.2016.2601610 [22] ROY S, CHATTERJEE S, DAS A K, et al. Chaotic map-based anonymous user authentication scheme with user biometrics and fuzzy extractor for crowdsourcing internet of things[J]. IEEE Internet of Things Journal, 2018, 5(4): 2884–2895. doi: 10.1109/JIOT.2017.2714179 [23] SRINIVAS J, DAS A K, KUMAR N, et al. Cloud centric authentication for wearable healthcare monitoring system[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 17(5): 942–956. doi: 10.1109/TDSC.2018.2828306 [24] National Institute of Standards and Technology. SP 800-57 Recommendation for key management, part 1: General (Revised 4)[S]. National Institute of Standards and Technology, 2016. [25] National Institute of Standards and Technology. SP 800-56A Recommendation for pair-wise key establishment schemes using discrete logarithm cryptography (Revision 2)[S]. National Institute of Standards and Technology, 2013. -





 下载:
下载:


 下载:
下载:
