Certificateless Anonymous Authentication Scheme for Internet of Vehicles
-
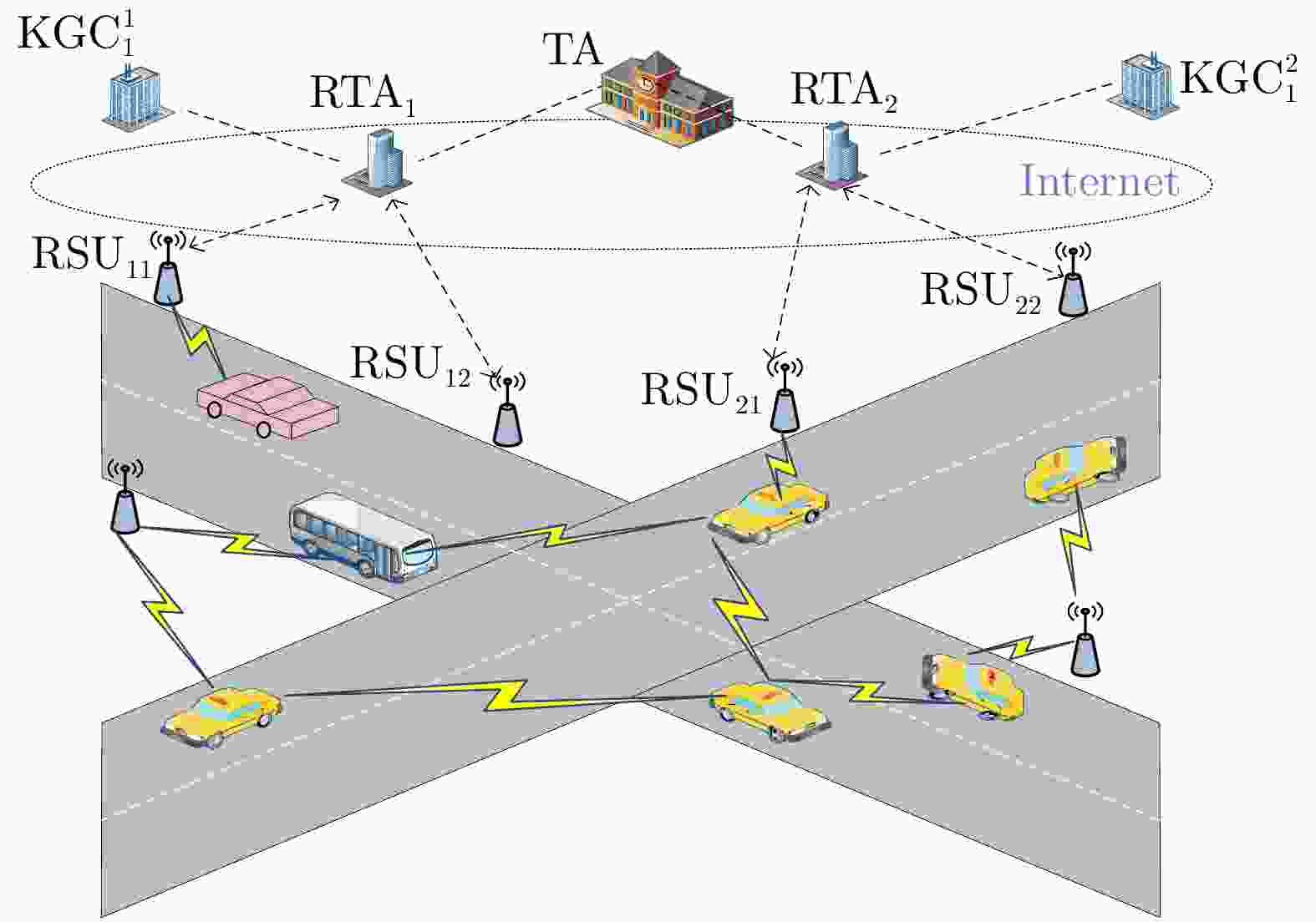
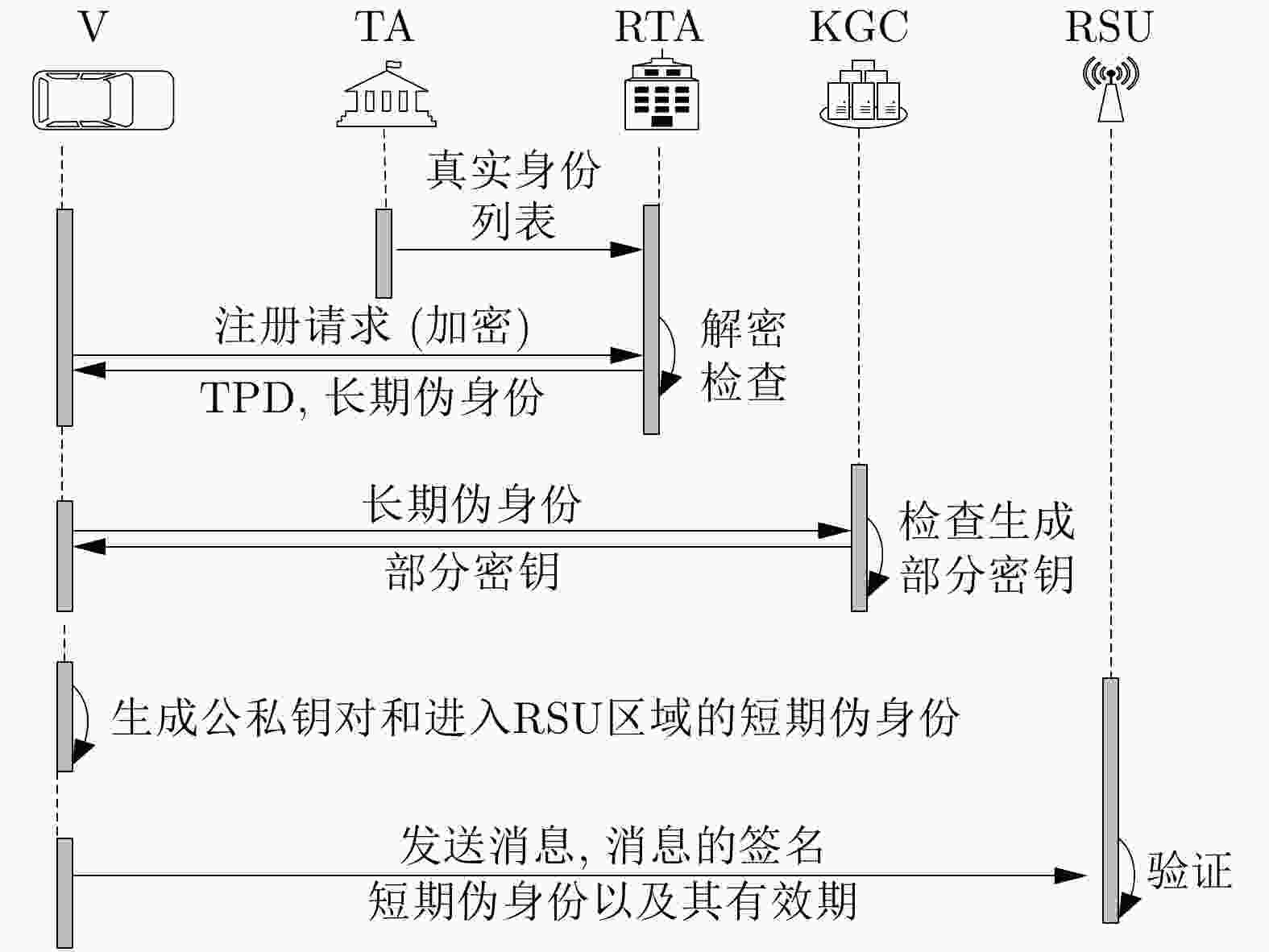
摘要: 通过信息共享,车联网(IoV)为车辆提供各种应用,以提高道路安全和交通效率。然而,车辆之间的公开通信导致了车辆隐私泄露和各种攻击。因而,安全且保护隐私的信息共享方法是非常必要的,并且对车辆间通信的安全性和保密性提出了更高的要求,所以该文提出了一种支持批量验证的非线性对的无证书匿名认证方案。在该方案中,首先,采用无证书签名机制避免了证书管理和密钥托管问题;其次结合区域管理局生成的长期伪身份和自己生成的短期伪身份保证车辆的强匿名性和签名的新鲜性,避免路侧单元计算伪身份造成的身份泄露和时延;再次,采用无对的聚合签名提供批验证,减少车联网环境中路侧单元的计算量;最后,当发生恶意事件时,区域管理局可以追踪车辆的真实身份并由可信中心撤销该用户。安全性证明和分析表明,该方案具有高的安全性,并满足完整性、可追踪性、匿名性、可撤销性等安全要求。将该方案与现有的方案进行了比较,效率分析表明该方案更有效。Abstract: Through information sharing, the Internet of Vehicles (IoV) provides various applications for vehicles to improve road safety and traffic efficiency. However, the open communication between vehicles lead to vehicle privacy leakage and various attacks. Therefore, information sharing methods with security and privacy protection are very necessary, so a pairing-free and certificateless anonymous authentication scheme supporting batch authentication is proposed. In this scheme, firstly, the problem of certificate management and key escrow can be avoided by using the certificateless signature; Secondly, the combination of the long-term pseudo-identity generated by the regional authority and the short-term pseudo-identity generated by itself, the strong anonymity of vehicle and the freshness of signature are guaranteed, and the identity disclosure and the communication delay caused by Road-side-unit computing pseudo identity are avoided; Thirdly, the aggregating signature without pairing is used to provide batch verification, which reduces greatly the computational burden of RSUs in vehicle network environment; Finally, when a malicious event occurs, the Regional Trusted Authority (RTA) can track the real identity of the vehicle. Security proof and analysis show that, the scheme has high security, and meets the security requirements.
-
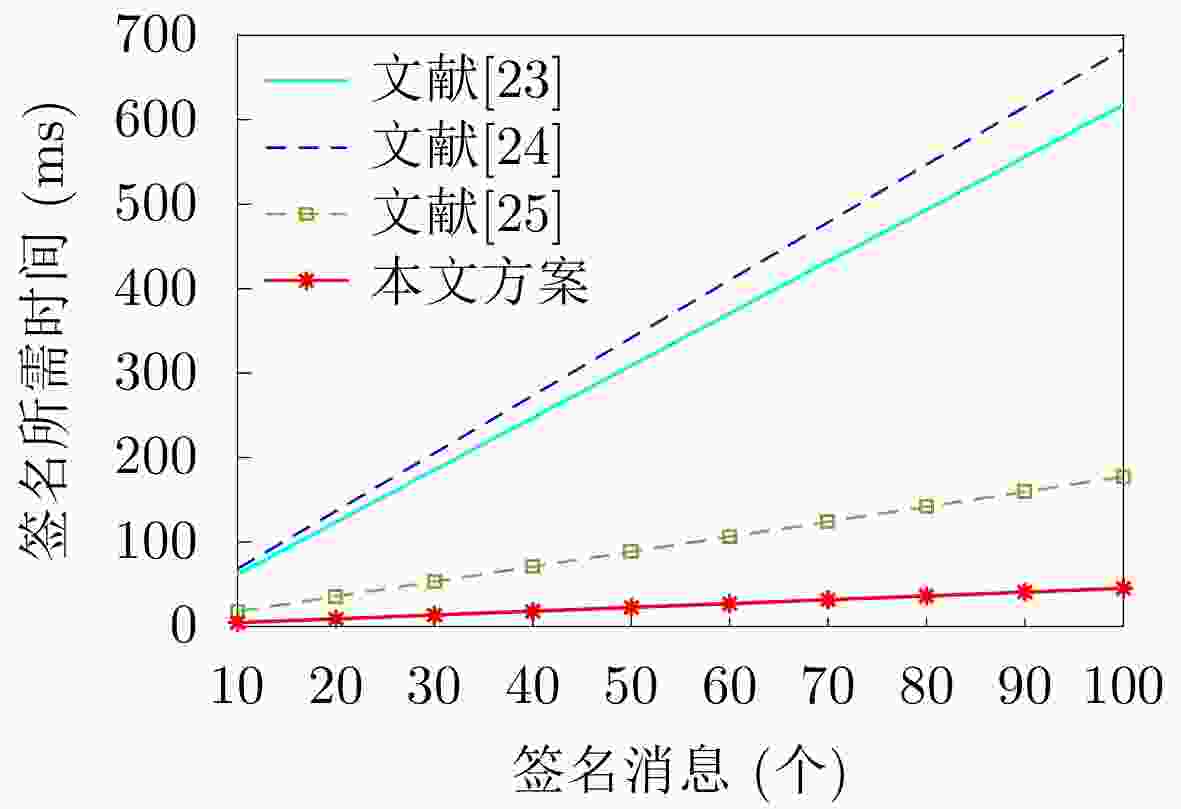
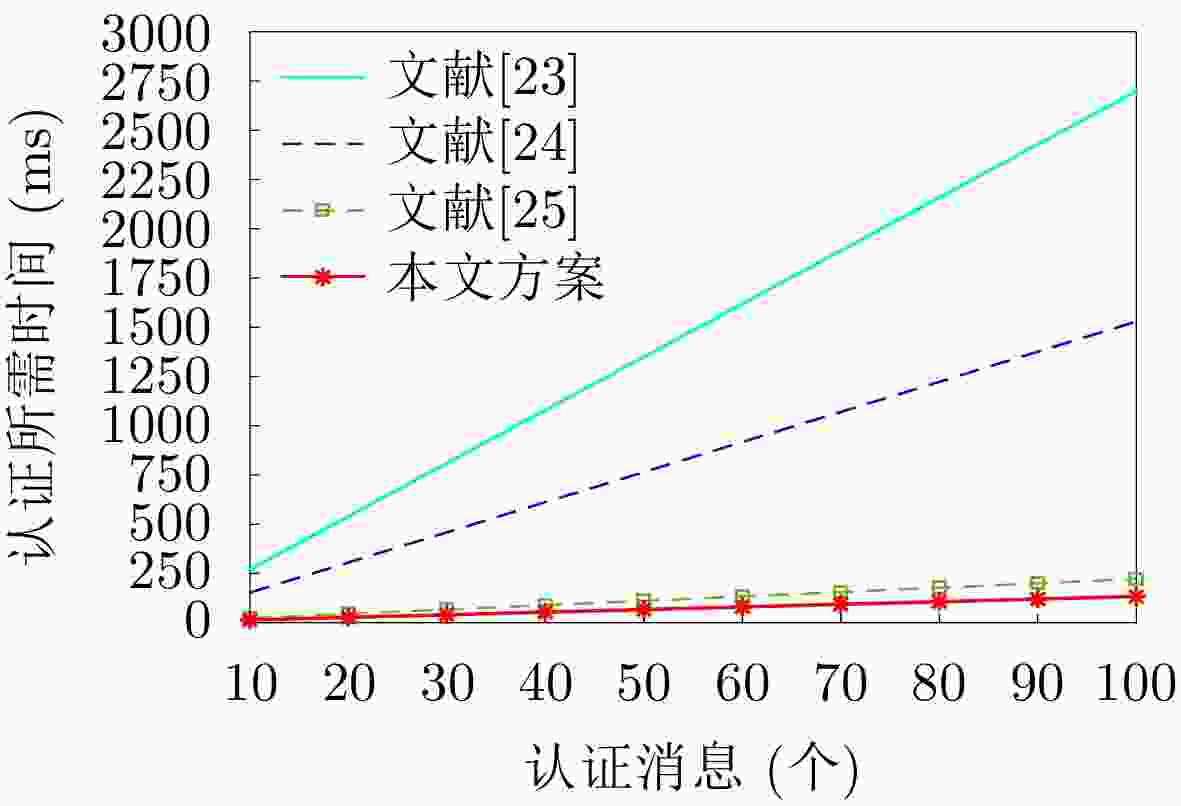
表 1 计算运行时间对比
方案 签名 验证 文献[23]
文献[24]${\rm{4}}{T_{{\rm{SM - }}{{\rm{G}}_{\rm{1}}}}} + {T_{{\rm{MTPH}}}} + 2{T_{{\rm{PA - }}{{\rm{G}}_{\rm{1}}}}}$
${\rm{4}}{T_{{\rm{SM - }}{{\rm{G}}_{\rm{1}}}}}$$4{T_{{\rm{BP}}}} + 3{T_{{\rm{SM - }}{{\rm{G}}_{\rm{1}}}}} + 2{T_{{\rm{MTPH}}}}$
${\rm{4}}{T_{{\rm{SM - }}{{\rm{G}}_{\rm{1}}}}} + 2{T_{{\rm{BP}}}}$文献[25] ${\rm{2}}{T_{{\rm{SM - G}}}}$ ${\rm{5}}{T_{{\rm{SM - G}}}}{\rm{ + 3}}{T_{{\rm{PA - G}}}}$ 本文方案 ${T_{{\rm{SM - G}}}} + 2{T_{{\rm{MM}}}}$ ${\rm{3}}{T_{{\rm{SM - G}}}}$ -
[1] SUTRALA A K, BAGGA P, DAS A. K, et al. On the design of conditional privacy preserving batch verification-based authentication scheme for Internet of Vehicles deployment[J]. IEEE Transactions on Vehicular Technology, 2020, 69(5): 5535–5548. doi: 10.1109/TVT.2020.2981934 [2] 谭富元. 车联网环境下高效安全认证方案的研究[D]. [硕士论文], 重庆邮电大学, 2018.TAN Fuyuan. Research on efficient and secure authentication scheme in vehicular Ad-Hoc network[D]. [Master dissertation], Chongqing University of Posts and Telecommunications, 2018. [3] LIN Xiaodong, SUN Xiaoting, HO P H, et al. GSIS: A secure and privacy-preserving protocol for vehicular communications[J]. IEEE Transactions on Vehicular Technology, 2007, 56(6): 3442–3456. doi: 10.1109/tvt.2007.906878 [4] SUN Yipin, LU Rongxing, LIN Xiaodong, et al. An efficient pseudonymous authentication scheme with strong privacy preservation for vehicular communications[J]. IEEE Transactions on Vehicular Technology, 2010, 59(7): 3589–3603. doi: 10.1109/tvt.2010.2051468 [5] RAYA M and HUBAUX J P. Securing vehicular ad hoc networks[J]. Journal of Computer Security, 2007, 15(1): 39–68. doi: 10.3233/jcs-2007-15103 [6] ZHANG Chenxi, LU Rongxing, LIN Xiongdong, et al. An efficient Identity-Based batch verification scheme for vehicular sensor networks[C]. IEEE INFOCOM 2008-The 27th Conference on Computer Communications, Phoenix, USA, 2008: 246–250. [7] LO N W and TSAI J L. An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks without pairings[J]. IEEE Transactions on Intelligent Transportation Systems, 2016, 17(5): 1319–1328. doi: 10.1109/tits.2015.2502322 [8] LIU Yawei, HE Zongjian, ZHAO Shengjie, et al. An efficient anonymous authentication protocol using batch operations for VANETs[J]. Multimedia Tools and Applications, 2016, 75(24): 17689–17709. doi: 10.1007/s11042-016-3614-9 [9] WANG Yimin, ZHONG Hong, XU Yan, et al. Efficient extensible conditional privacy-preserving authentication scheme supporting batch verification for VANETs[J]. Security and Communication Networks, 2016, 9(18): 5460–5471. doi: 10.1002/sec.1710 [10] TZENG S F, HORNG S J, LI Tianrui, et al. Enhancing security and privacy for identity-based batch verification scheme in VANETs[J]. IEEE Transactions on Vehicular Technology, 2017, 66(4): 3235–3248. doi: 10.1109/tvt.2015.2406877 [11] HU Xiaoming, WANG Jian, XU Huajie, et al. Secure and Pairing-free Identity-based Batch Verification Scheme in Vehicle Ad-hoc Networks[M]. HUANG Deshuang, HAN K, and HUSSAIN A. Intelligent Computing Methodologies. Cham: Springer, 2016: 11–20. [12] GAMAGE C, GRAS B, CRISPO B, et al. An identity-based ring signature scheme with enhanced privacy[C]. 2006 Securecomm and Workshops, Baltimore, USA, 2006: 1–5. doi: 10.1109/seccomw.2006.359554. [13] JIANG Shunrong, ZHU Xiaoyan, and WANG Liangmin. An efficient anonymous batch authentication scheme based on HMAC for VANETs[J]. IEEE Transactions on Intelligent Transportation Systems, 2016, 17(8): 2193–2204. doi: 10.1109/tits.2016.2517603. [14] SUN Jinyuan, ZHANG Chi, and FANG Yuguang. An ID-based framework achieving privacy and non-repudiation in vehicular ad hoc networks[C]. Proceedings of IEEE Military Communications Conference, Orlando, USA, 2007: 1–7. doi: 10.1109/milcom.2007.4454834. [15] BAEK J, STEINFELD R, and ZHENG Yuliang. Formal proofs for the security of Signcryption[J]. Journal of Cryptology, 2007, 20(2): 203–235. doi: 10.1007/s00145-007-0211-0 [16] AL-RIYAM S S and PATERSON K G. Certificateless public key cryptography[C]. The 9th International Conference on the Theory and Application of Cryptology and Information Security, Taipei, China, 2003: 452–473. [17] SONG Jun, ZHUANG Yanyan, PAN Jianping, et al. Certificateless secure upload for drive-thru internet[C]. 2011 IEEE International Conference on Communications (ICC), Kyoto, Japan, 2011: 1–6. doi: 10.1109/icc.2011.5962528. [18] SONG Jun, HE Chunjiao, ZHANG Lei, et al. Toward an RSU-unavailable lightweight certificateless key agreement scheme for VANETs[J]. China Communications, 2014, 11(9): 93–103. doi: 10.1109/cc.2014.6969774 [19] HORNG S J, TZENG S F, HUANG P H, et al. An efficient certificateless aggregate signature with conditional privacy-preserving for vehicular sensor networks[J]. Information Sciences, 2015, 317: 48–66. doi: 10.1016/j.ins.2015.04.033 [20] 王大星, 滕济凯. 车载网中可证安全的无证书聚合签名算法[J]. 电子与信息学报, 2018, 40(1): 11–17. doi: 10.11999/JEIT170340WANG Daxing and TENG Jikai. Probably secure certificateless aggregate signature algorithm for vehicular Ad Hoc network[J]. Journal of Electronics &Information Technology, 2018, 40(1): 11–17. doi: 10.11999/JEIT170340 [21] 杨小东, 麻婷春, 陈春霖, 等. 面向车载自组网的无证书聚合签名方案的安全性分析与改进[J]. 电子与信息学报, 2019, 41(5): 1265–1270. doi: 10.11999/JEIT180571YANG Xiaodong, MA Tingchun, CHEN Chunlin, et al. Security analysis and improvement of certificateless aggregate signature scheme for vehicular Ad Hoc network[J]. Journal of Electronics &Information Technology, 2019, 41(5): 1265–1270. doi: 10.11999/JEIT180571 [22] POINTCHEVAL D and STERN J. Security arguments for digital signatures and blind signatures[J]. Journal of Cryptology, 2000, 13(3): 361–396. doi: 10.1007/s001450010003 [23] KUMAR P, KUMARI S, SHARMA V, et al. Secure CLS and CL-AS schemes designed for VANETs[J]. The Journal of Supercomputing, 2019, 75(6): 3076–3098. doi: 10.1007/s11227-018-2312-y [24] JIANG Haobin, HUA Lei, and WAHAB L. SAES: A self-checking authentication scheme with higher efficiency and security for VANET[J]. Peer-to-Peer Networking and Applications, 2021, 14(2): 528–540. doi: 10.1007/s12083-020-00997-0 [25] GAYATHRI N B, THUMBUR G, REDDY P V, et al. Efficient pairing-free certificateless authentication scheme with batch verification for vehicular Ad-hoc networks[J]. IEEE Access, 2018, 6: 31808–31819. doi: 10.1109/ACCESS.2018.2845464 -





 下载:
下载:


 下载:
下载:
