| [1] |
ZETTER K. Countdown to Zero Day[M]. ZETTER K. Countdown to Zero Day: Stuxnet and the Launch of the World’s First Digital Weapon. Broadway Books, 2015.
|
| [2] |
Cnbeta. 卡巴斯基透露有黑客同时利用Windows 10和Chrome零日漏洞发动攻击[EB/OL]. http://cnnvd.org.cn/web/xxk/yjxwById.tag?id=11,170, 2019.
|
| [3] |
Cnbeta. 网络安全研究人员发现新漏洞: 或成另一个WannaCry[EB/OL]. http://cnnvd.org.cn/web/xxk/yjxwById.tag?id=8,486, 2017.
|
| [4] |
SUN Xiaoyan, DAI Jun, LIU Peng, et al. Using Bayesian networks for probabilistic identification of zero-day attack paths[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(10): 2506–2521. doi: 10.1109/TIFS.2018.2821095
|
| [5] |
SUN Xiaoyan, DAI Jun, LIU Peng, et al. Using Bayesian Networks to Fuse Intrusion Evidences and Detect Zero-day Attack Paths[M]. WANG Lingyu, JAJODIA S, and SINGHAL A. Network Security Metrics. Cham: Springer, 2017.
|
| [6] |
DIRO A A and CHILAMKURTI N. Distributed attack detection scheme using deep learning approach for internet of things[J]. Future Generation Computer Systems, 2018, 82: 761–768. doi: 10.1016/j.future.2017.08.043
|
| [7] |
KIM J Y, BU S J, and CHO S B. Zero-day malware detection using transferred generative adversarial networks based on deep Autoencoders[J]. Information Sciences, 2018, 460/461: 83–102. doi: 10.1016/j.ins.2018.04.092
|
| [8] |
张瑜, 潘小明, LIU Qingzhong, 等. APT攻击与防御[J]. 清华大学学报: 自然科学版, 2017, 57(11): 1127–1133. doi: 10.16511/j.cnki.qhdxxb.2017.21.024ZHANG Yu, PAN Xiaoming, LIU Qingzhong, et al. APT attacks and defenses[J]. Journal of Tsinghua University:Science &Technology, 2017, 57(11): 1127–1133. doi: 10.16511/j.cnki.qhdxxb.2017.21.024
|
| [9] |
ZHANG Mengyuan, WANG Lingyu, JAJODIA S, et al. Network diversity: A security metric for evaluating the resilience of networks against zero-day attacks[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(5): 1071–1086. doi: 10.1109/TIFS.2016.2516916
|
| [10] |
VALDEZ J S, GUEVARA P, AUDELO J, et al. Numerical approaching of SIR epidemic model for propagation of computer worms[J]. IEEE Latin America Transactions, 2015, 13(10): 3452–3460. doi: 10.1109/TLA.2015.7387254
|
| [11] |
顾海俊, 蒋国平, 夏玲玲. 基于状态概率转移的SIRS病毒传播模型及其临界值分析[J]. 计算机科学, 2016, 43(S1): 64–67.GU Haijun, JIANG Guoping, and XIA Lingling. SIRS epidemic model and its Threshold based on state transition probability[J]. Computer Science, 2016, 43(S1): 64–67.
|
| [12] |
王刚, 陆世伟, 胡鑫, 等. 潜伏机制下网络病毒传播SEIQRS模型及稳定性分析[J]. 哈尔滨工业大学学报, 2019, 51(5): 131–137. doi: 10.11918/j.issn.0367-6234.201805136WANG Gang, LU Shiwei, HU Xin, et al. Network virus spreading SEIQRS model and its stability under escape mechanism[J]. Journal of Harbin Institute of Technology, 2019, 51(5): 131–137. doi: 10.11918/j.issn.0367-6234.201805136
|
| [13] |
王刚, 陆世伟, 胡鑫, 等. “去二存一”混合机制下的病毒扩散模型及稳定性分析[J]. 电子与信息学报, 2019, 41(3): 709–716. doi: 10.11999/JEIT180381WANG Gang, LU Shiwei, HU Xin, et al. Virus propagation model and stability under the hybrid mechanism of “Two-go and One-live”[J]. Journal of Electronics &Information Technology, 2019, 41(3): 709–716. doi: 10.11999/JEIT180381
|
| [14] |
WANG Xu, NI Wei, ZHENG Kangfeng, et al. Virus propagation modeling and convergence analysis in large-scale networks[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(10): 2241–2254. doi: 10.1109/TIFS.2016.2581305
|
| [15] |
WANG Lei, YAO Changhua, YANG Yuqi, et al. Research on a dynamic virus propagation model to improve smart campus security[J]. IEEE Access, 2018, 6: 20663–20672. doi: 10.1109/ACCESS.2018.2817508
|
| [16] |
秦李, 黄曙光, 陈骁. 病毒传播下的因特网级联故障模型构建与仿真[J]. 计算机应用研究, 2016, 33(4): 1228–1231, 1235. doi: 10.3969/j.issn.1001-3695.2016.04.059QIN Li, HUANG Shuguang, and CHEN Xiao. Model and simulation for cascading failure on internet based on virus propagation[J]. Application Research of Computers, 2016, 33(4): 1228–1231, 1235. doi: 10.3969/j.issn.1001-3695.2016.04.059
|
| [17] |
巩永旺, 宋玉蓉, 蒋国平. 移动环境下网络病毒传播模型及其稳定性研究[J]. 物理学报, 2012, 61(11): 110205. doi: 10.7498/aps.61.110205GONG Yongwang, SONG Yurong, and JIANG Guoping. Epidemic spreading model and stability of the networks in mobile environment[J]. Acta Physica Sinica, 2012, 61(11): 110205. doi: 10.7498/aps.61.110205
|






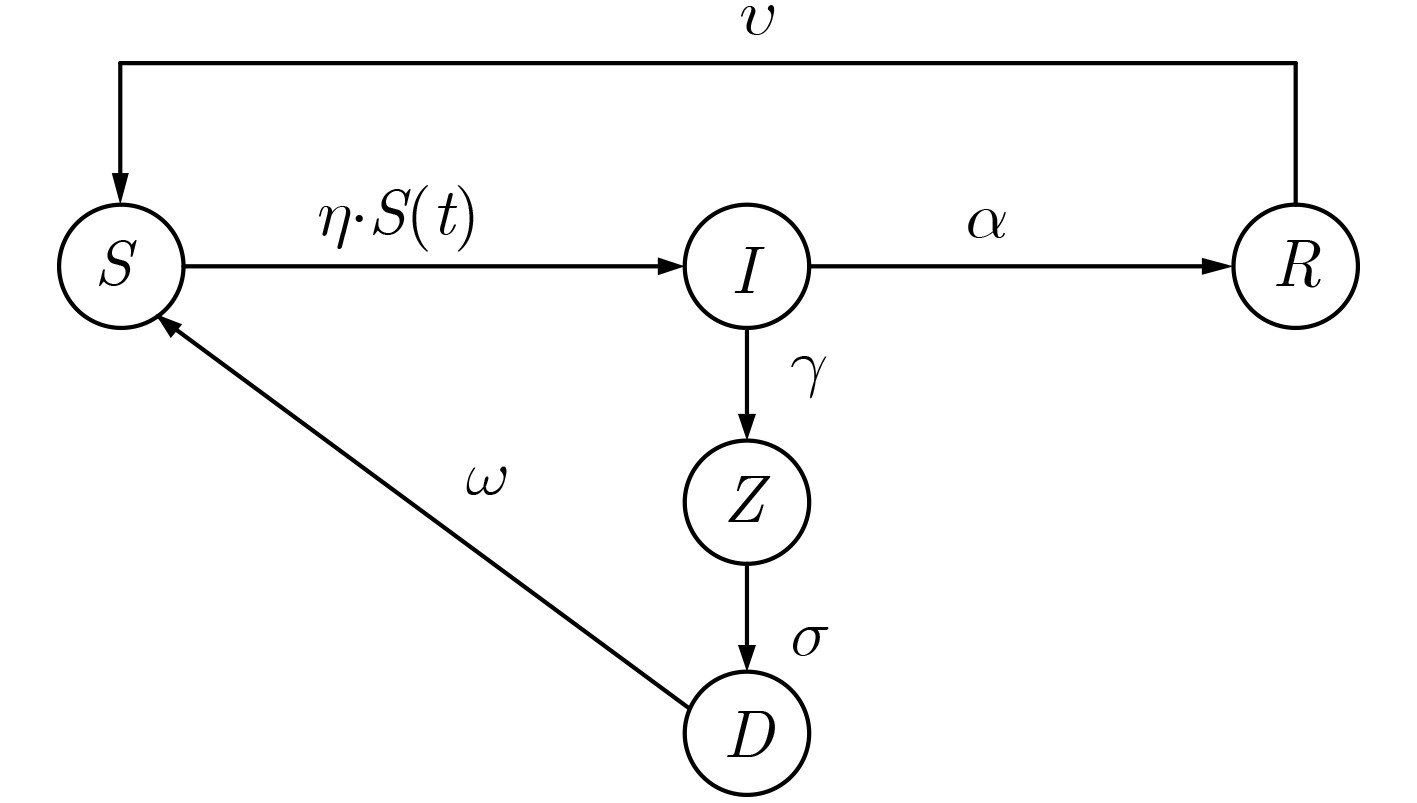
 下载:
下载:
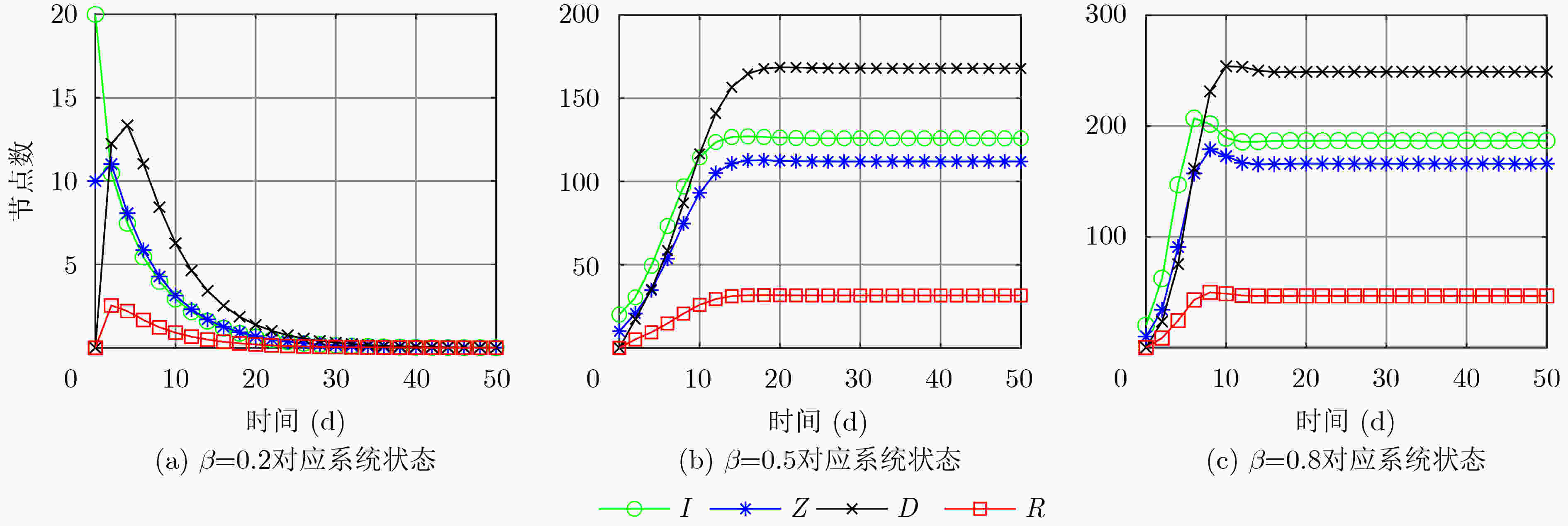

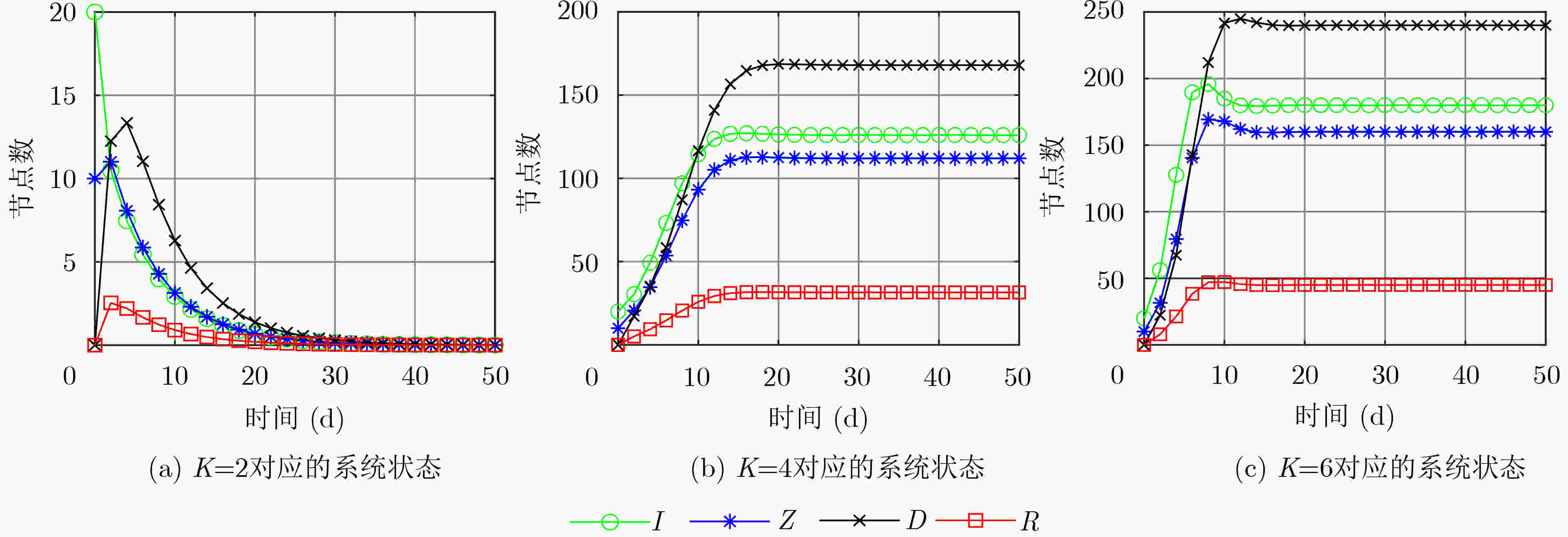

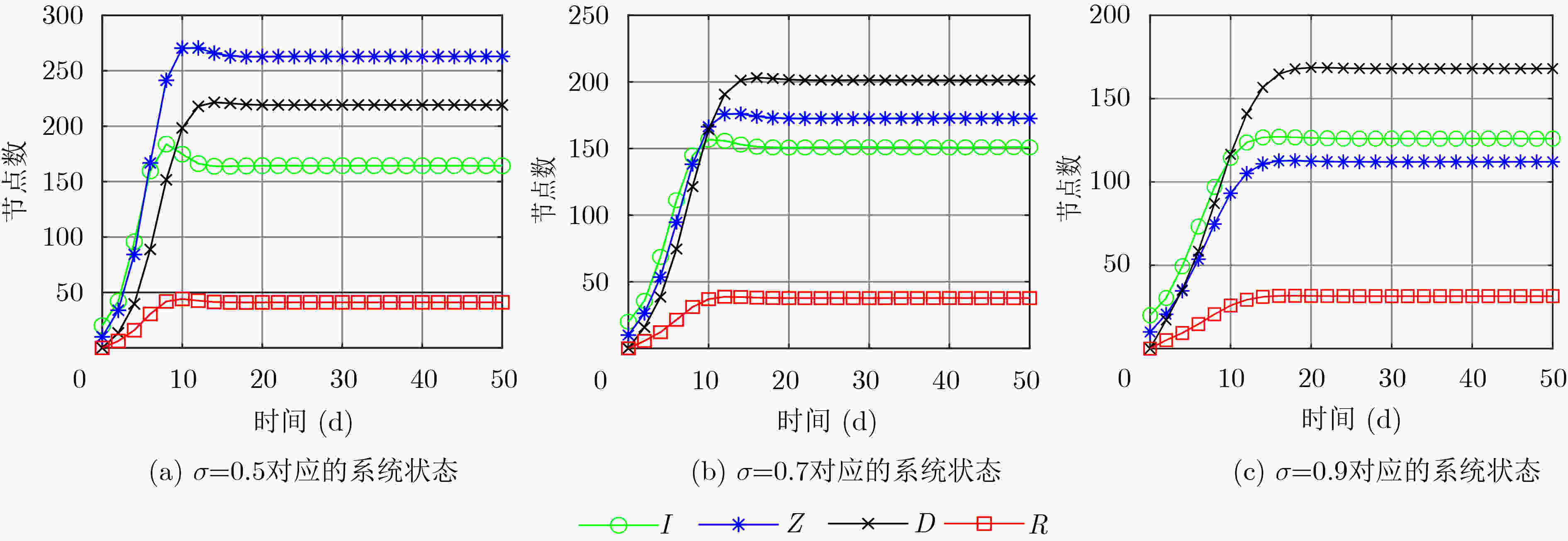



 下载:
下载:
