Research on Laser Injection Attack for AES Based on Micro-Controller Unit
-
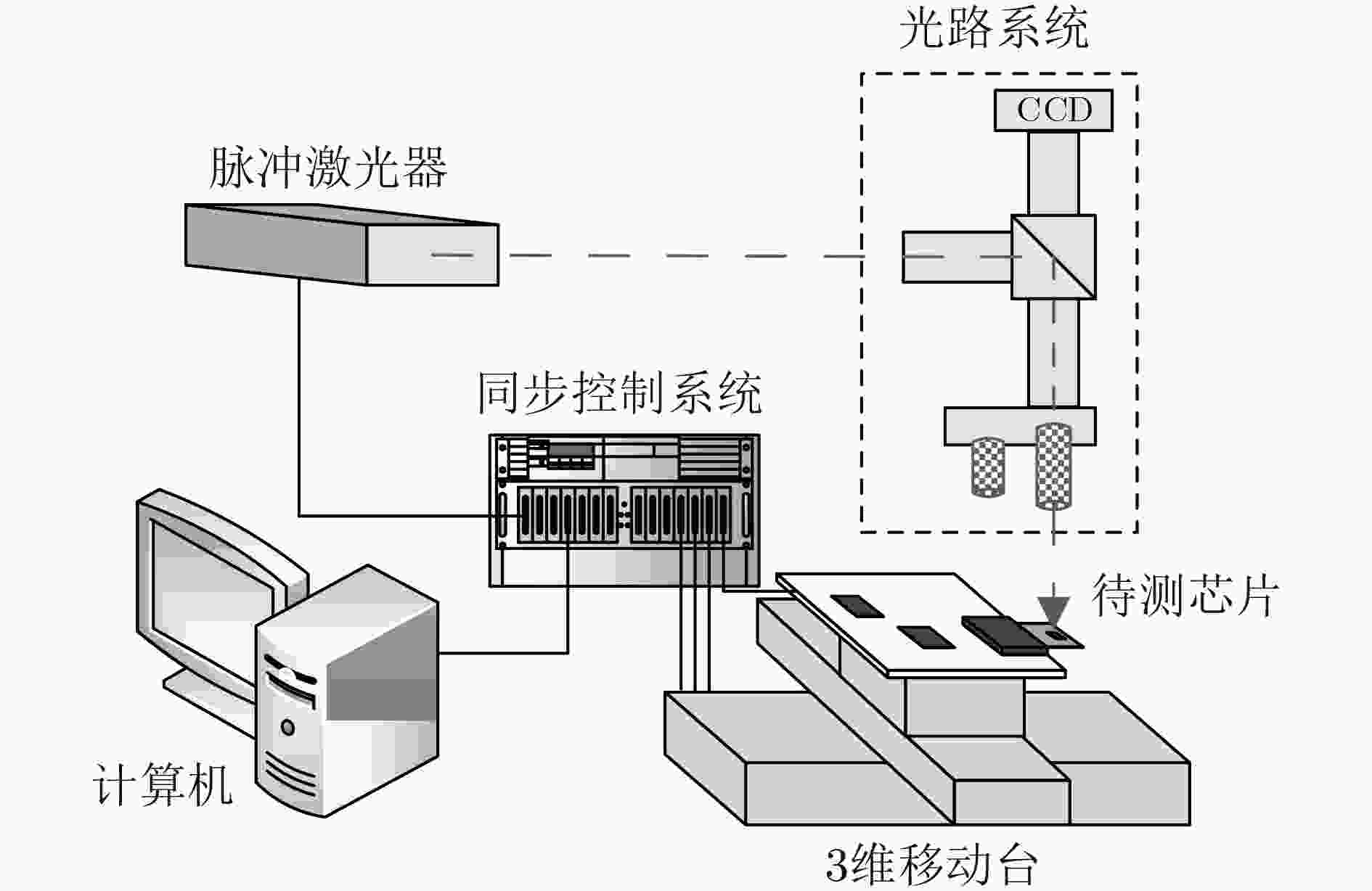
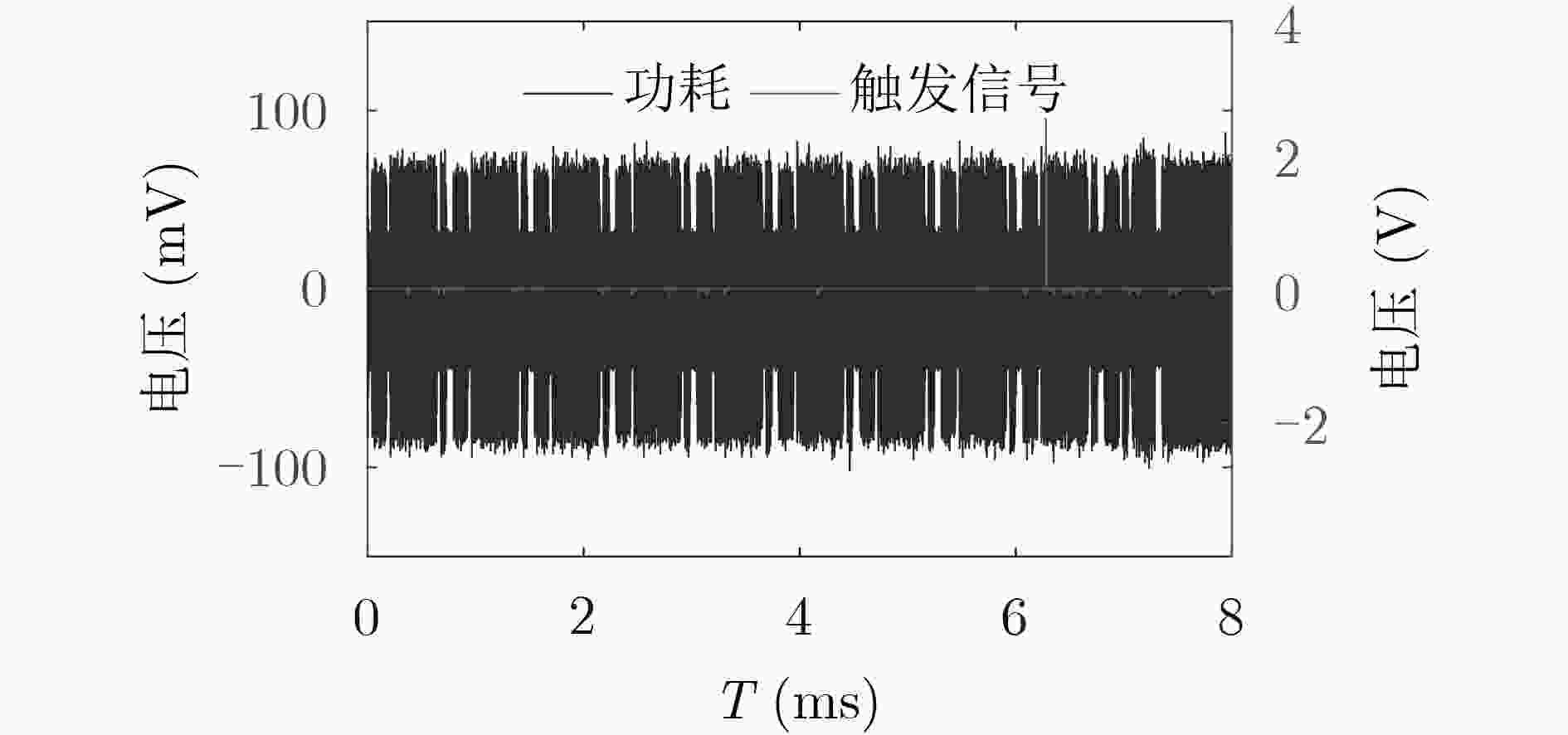
摘要: 密码设备面临故障攻击的威胁,针对密码芯片的故障攻击手段研究是密码学和硬件安全领域的重要研究方向。脉冲激光具有较好的时空分辨性,是一种准确度较高的故障攻击手段。该文详细描述了激光注入攻击的原理和方法,以集成AES-128算法的微控制器(MCU)为例实施了激光注入攻击实验。实验以微控制器的SRAM为攻击目标,分别成功实现了差分故障攻击和子密钥编排攻击,恢复了其16 Byte的完整密钥,其中后一种攻击是目前首次以激光的手段实现。研究表明,激光注入攻击能准确定位关键数据存放的物理位置,并能在任意的操作中引入错误,实现单比特的数据翻转,满足故障攻击模型的需求。激光注入攻击能在较短时间内完成自动攻击和密文收集,攻击过程贴近真实场景,对密码芯片具有极大的威胁。Abstract: The security of cryptosystem is threatened by fault attacks, and implementation of fault attacks for crypto chips become an important research direction in the field of cryptography and hardware security. The pulse laser is a method with high accuracy for its high temporal-spatial resolution. In this paper, the principle and method of laser injection attacks are described in detail, and experiments are carried out on a Micro-Controller Unit (MCU) with AES-128 algorithm as an example. The SRAMs of the MCU are taken as the attack targets. Differential fault attack and the subkey expansion attack are successfully implemented, and the 16 Byte complete keys are recovered respectively. The latter attack is first implemented by the laser. The research shows that laser injection attack has many benefits to meet the requirements of fault attack models, including accurate location of critical data, error injection in any operation, and generation of single bit flip. The laser injection attacks and ciphertext collection can be completed automatically in a short time in a nearly real-life scenario, which has a great threat to the crypto chips.
-
Key words:
- Fault attack /
- Micro-Controller Unit (MCU) /
- Advanced Encryption Standard (AES) /
- Laser injection /
- SRAM
-
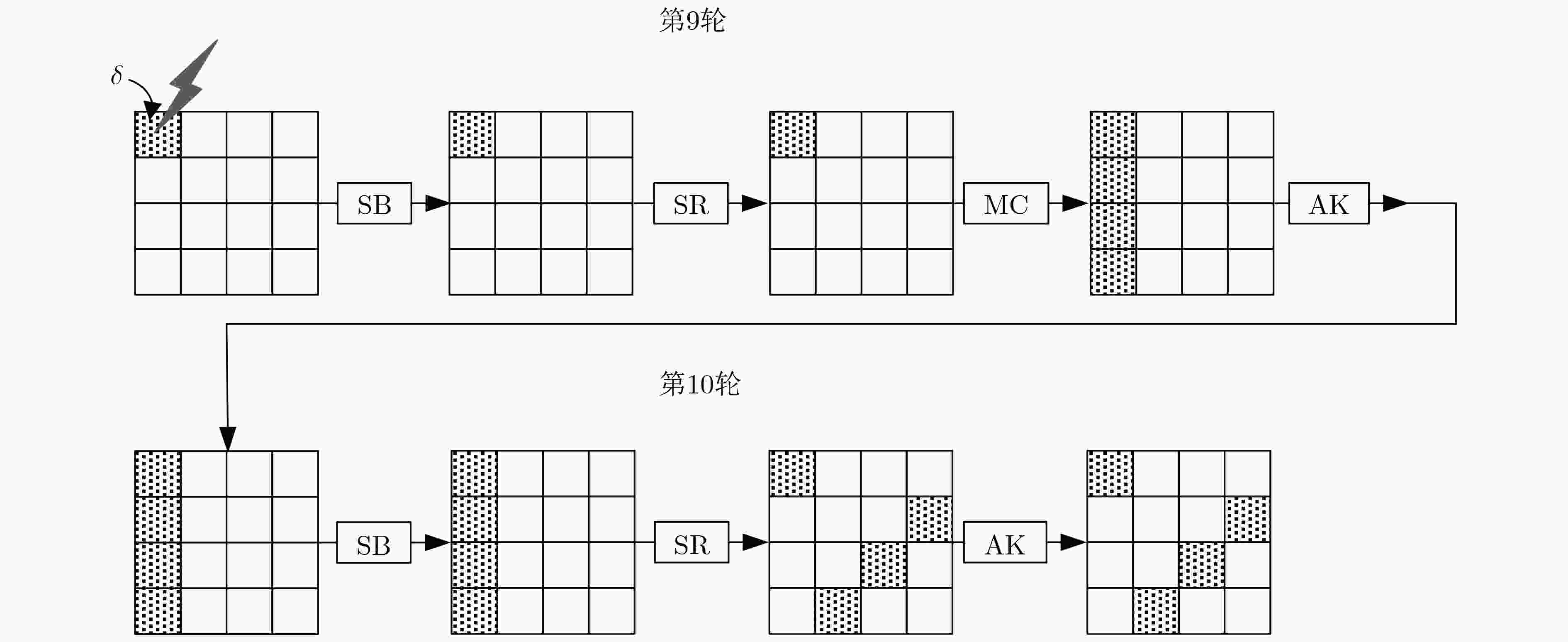
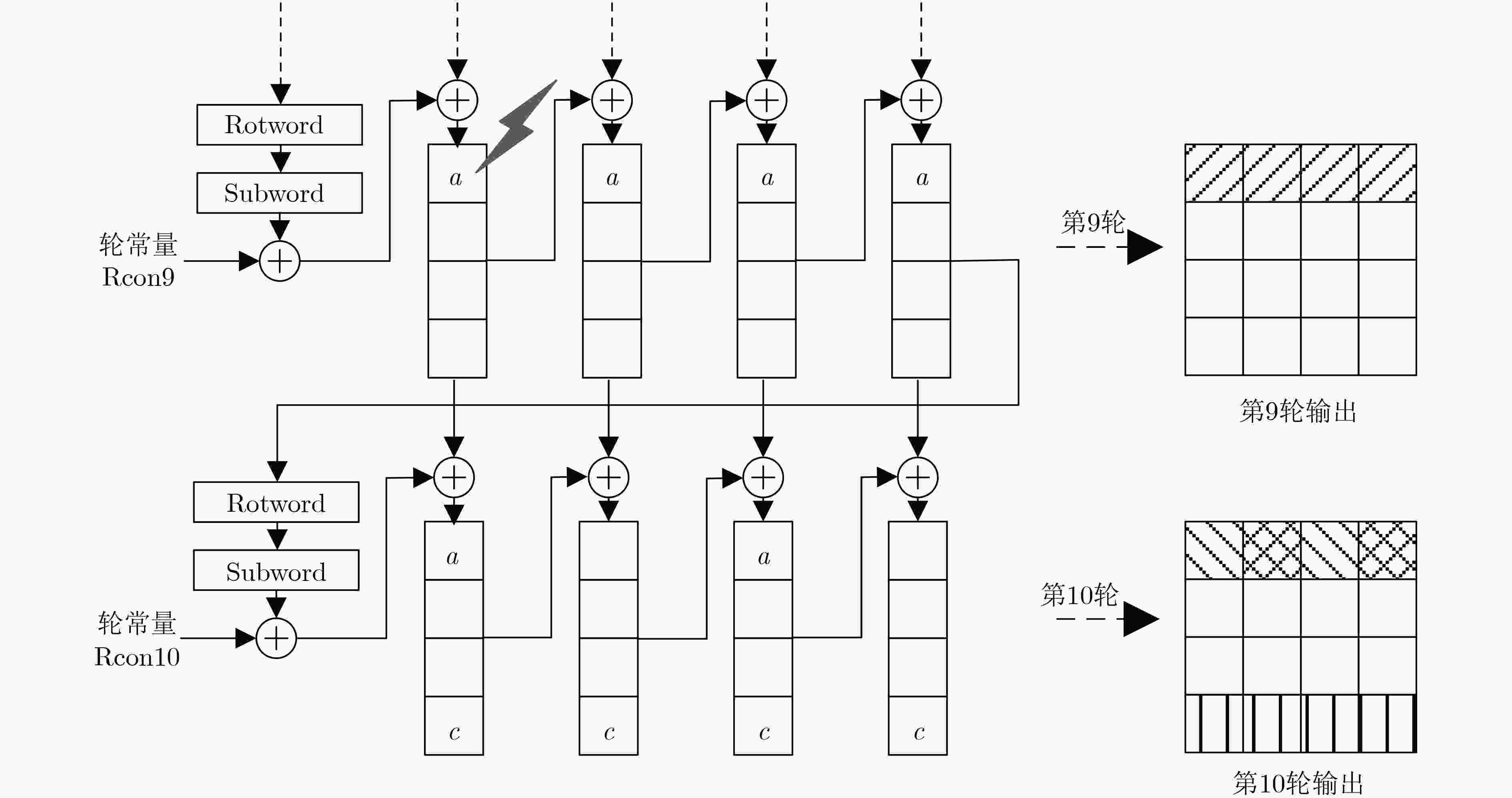
表 1 攻击第9轮输入的字节位置及恢复的密钥字节
输入错误
字节位置恢复字密钥字节 密文对
数目最终候
选值(0x)10 $K_0^{10},K_7^{10},K_{10}^{10},K_{13}^{10}$ 3 13, 17, A7, 2B 3 $K_{\rm{1}}^{10},K_{\rm{4}}^{10},K_{{\rm{11}}}^{10},K_{{\rm{14}}}^{10}$ 4 11, E3, 8B, 30 7 $K_2^{10},K_5^{10},K_8^{10},K_{15}^{10}$ 4 1D, 94, F3, C5 11 $K_3^{10},K_6^{10},K_9^{10},K_{12}^{10}$ 4 7F, 4A, 07, 4D 表 2 经步骤(1)筛选后的候选值情况
$K_{\rm{7}}^{10}$ $K_{{\rm{15}}}^{10}$ ${a_1}$ ${a_{\rm{2}}}$ 1 0x17 0xC5 0x20 0x20 2 0x53 0xC3 0x77 0x9C 表 3 经步骤(2)筛选后的候选值情况
$K_{\rm{7}}^{10}$ $K_{{\rm{11}}}^{10}$ $K_{{\rm{15}}}^{10}$ ${a_1}$ ${a_{\rm{2}}}$ 候选 0x17 0x8B 0xC5 0x20 0x20 表 4 经步骤(3)筛选后的候选值情况
$K_{\rm{3}}^{10}$ $K_{\rm{7}}^{10}$ $K_{{\rm{11}}}^{10}$ $K_{{\rm{15}}}^{10}$ ${a_1}$ ${a_{\rm{2}}}$ 候选 0x7F 0x17 0x8B 0xC5 0x20 0x20 -
[1] 陈华, 习伟, 范丽敏, 等. 密码产品的侧信道分析与评估[J]. 电子与信息学报, 2020, 42(8): 1836–1845. doi: 10.11999/JEIT190853CHEN Hua, XI Wei, FAN Limin, et al. Side channel analysis and evaluation on cryptographic products[J]. Journal of Electronics &Information Technology, 2020, 42(8): 1836–1845. doi: 10.11999/JEIT190853 [2] 王安, 葛婧, 商宁, 等. 侧信道分析实用案例概述[J]. 密码学报, 2018, 5(4): 383–398. doi: 10.13868/j.cnki.jcr.000249WANG An, GE Jing, SHANG Ning, et al. Practical cases of side-channel analysis[J]. Journal of Cryptologic Research, 2018, 5(4): 383–398. doi: 10.13868/j.cnki.jcr.000249 [3] DUSART P, LETOURNEUX G, and VIVOLO O. Differential fault analysis on A. E. S[C]. The 1st International Conference on Applied Cryptography and Network Security, Kunming, China, 2003: 293–306. doi: 10.1007/978-3-540-45203-4_23. [4] PIRET G and QUISQUATER J J. A differential fault attack technique against SPN structures, with application to the AES and KHAZAD[C]. The 5th International Workshop on Cryptographic Hardware and Embedded Systems, Cologne, Germany, 2003: 77–88. doi: 10.1007/978-3-540-45238-6_7. [5] KIM C H and QUISQUATER J J. New differential fault analysis on AES key schedule: Two faults are enough[C]. The 8th International Conference on Smart Card Research and Advanced Applications, London, UK, 2008: 48–60. doi: 10.1007/978-3-540-85893-5_4. [6] TUNSTALL M, MUKHOPADHYAY D, and ALI S. Differential fault analysis of the advanced encryption standard using a single fault[C]. The 5th IFIP WG 11.2 International Conference on Information Security Theory and Practice: Security and Privacy of Mobile Devices in Wireless Communication, Heraklion, Crete, Greece, 2011: 224–233. doi: 10.1007/978-3-642-21040-2_15. [7] LIAO Nan, CUI Xiaoxin, LIAO Kai, et al. Improving DFA attacks on AES with unknown and random faults[J]. Science China Information Sciences, 2017, 60(4): 042401. doi: 10.1007/s11432-016-0071-7 [8] ZHANG Fan, LOU Xiaoxuan, ZHAO Xinjie, et al. Persistent fault analysis on block ciphers[J]. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2018, 2018(3): 150–172. doi: 10.13154/tches.v2018.i3.150-172 [9] GRUBER M and SELMKE B. Differential fault attacks on KLEIN[C]. The 10th International Workshop on Constructive Side-Channel Analysis and Secure Design, Darmstadt, Germany, 2019: 80–95. doi: 10.1007/978-3-030-16350-1_6. [10] VAFAEI N, BAGHERI N, SAHA S, et al. Differential fault attack on SKINNY block cipher[C]. The 8th International Conference on Security, Privacy, and Applied Cryptography Engineering, Kanpur, India, 2018: 177–197. doi: 10.1007/978-3-030-05072-6_11. [11] 袁庆军, 张勋成, 高杨, 等. 轻量级分组密码PUFFIN的差分故障攻击[J]. 电子与信息学报, 2020, 42(6): 1519–1525. doi: 10.11999/JEIT190506YUAN Qingjun, ZHANG Xuncheng, GAO Yang, et al. Differential fault attack on the lightweight block cipher PUFFIN[J]. Journal of Electronics &Information Technology, 2020, 42(6): 1519–1525. doi: 10.11999/JEIT190506 [12] 王如燕. 针对AES结构的差分故障分析方法效率改进研究[D]. [硕士论文], 南京航空航天大学, 2019. doi: 10.27239/d.cnki.gnhhu.2019.001818.WANG Ruyan. Research on efficiency improvement of differential fault analysis for AES structure[D]. [Master dissertation], Nanjing University of Aeronautics and Astronautics, 2019. doi: 10.27239/d.cnki.gnhhu.2019.001818. [13] AGOYAN M, DUTERTRE J M, MIRBAHA A P, et al. Single-bit DFA using multiple-byte laser fault injection[C]. 2010 IEEE International Conference on Technologies for Homeland Security, Waltham, USA, 2010: 113–119. doi: 10.1109/THS.2010.5655079. [14] ROSCIAN C, DUTERTRE J M, and TRIA A. Frontside laser fault injection on cryptosystems – Application to the AES’ last round[C]. 2013 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Austin, USA, 2013: 119–124. doi: 10.1109/HST.2013.6581576. [15] COURBON F, LOUBET-MOUNDI P, FOURNIER J J A, et al. Increasing the efficiency of laser fault injections using fast gate level reverse engineering[C]. 2014 IEEE International Symposium on Hardware-oriented Security and Trust (HOST), Arlington, USA, 2014: 60–63. doi: 10.1109/HST.2014.6855569. [16] BREIER J, JAP D, and CHEN C N. Laser-based Fault Injection on Microcontrollers[M]. PATRANABIS S and MUKHOPADHYAY D. Fault Tolerant Architectures for Cryptography and Hardware Security. Singapore: Springer, 2018: 81–100. doi: 10.1007/978-981-10-1387-4_5. [17] ZHANG Fan, ZHANG Yiran, JIANG Huilong, et al. Persistent fault attack in practice[J]. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2020, 2020(2): 172–195. doi: 10.13154/tches.v2020.i2.172-195 [18] 王红胜, 纪道刚, 张阳, 等. 针对RSA-CRT数字签名的光故障攻击研究[J]. 电子设计工程, 2015, 23(6): 12–15. doi: 10.14022/j.cnki.dzsjgc.2015.06.004WANG Hongsheng, JI Daogang, ZHANG Yang, et al. Optical fault attack on RSA-CRT signatures[J]. Electronic Design Engineering, 2015, 23(6): 12–15. doi: 10.14022/j.cnki.dzsjgc.2015.06.004 [19] 朱磊, 陈力颖. 低成本eSIM芯片抗激光故障注入攻击的防护设计[J]. 电子元器件与信息技术, 2019, 3(11): 7–10. doi: 10.19772/j.cnki.2096-4455.2019.11.004ZHU Lei and CHEN Liying. Protection design of low cost eSIM chip against laser fault injection attack[J]. Electronic Component and Information Technology, 2019, 3(11): 7–10. doi: 10.19772/j.cnki.2096-4455.2019.11.004 [20] RODRIGUEZ J, BALDOMERO A, MONTILLA V, et al. LLFI: Lateral laser fault injection attack[C]. 2019 Workshop on Fault Diagnosis and Tolerance in Cryptography, Atlanta, USA, 2019: 41–47. doi: 10.1109/FDTC.2019.00014. [21] YUCE B, SCHAUMONT P, and WITTEMAN M. Fault attacks on secure embedded software: Threats, design, and evaluation[J]. Journal of Hardware and Systems Security, 2018, 2(2): 111–130. doi: 10.1007/s41635-018-0038-1 [22] 王沛晶. 集成电路奇偶校验故障注入检测方法研究[D]. [硕士论文], 天津大学, 2018. doi: 10.27356/d.cnki.gtjdu.2018.002203.WANG Peijing. Research on parity code-based fault detection of integrated circuit against fault injection attack[D]. [Master dissertation], Tianjin University, 2018. doi: 10.27356/d.cnki.gtjdu.2018.002203. -





 下载:
下载:





 下载:
下载:
