Searchable Encryption Scheme Supporting Policy Hiding and Constant Ciphertext Length
-
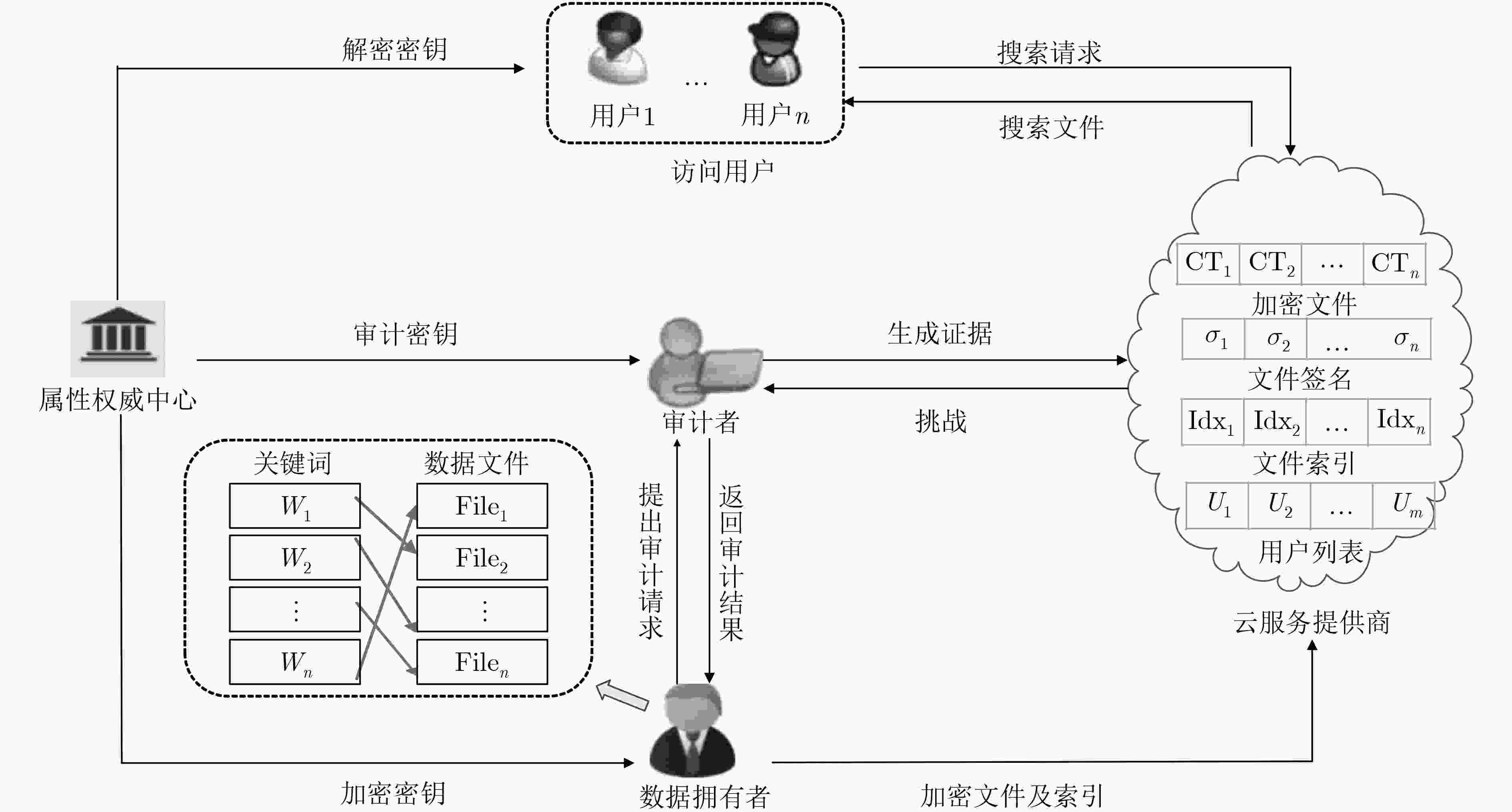
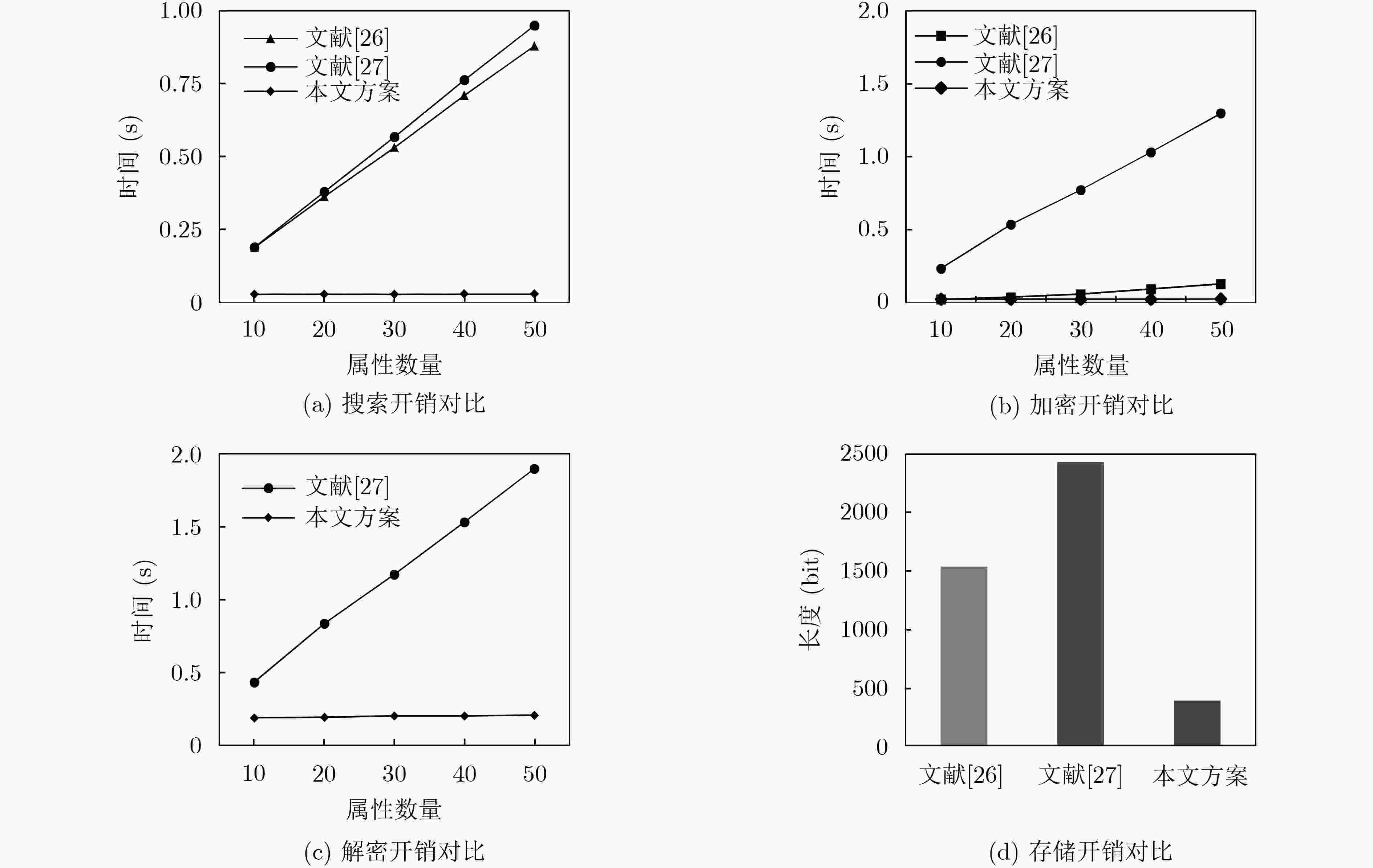
摘要: 属性加密体制是实现云存储中数据灵活访问控制的关键技术之一,但已有的属性加密方案存在密文存储开销过大和用户隐私泄露等问题,并且不能同时支持云端数据的公开审计。为了解决这些问题,该文提出一个新的可搜索属性加密方案,其安全性可归约到q-BDHE问题和CDH问题的困难性。该方案在支持关键词搜索的基础上,实现了密文长度恒定;引入策略隐藏思想,防止攻击者获取敏感信息,确保了用户的隐私性;通过数据公开审计机制,实现了云存储中数据的完整性验证。与已有的同类方案相比较,该方案有效地降低了数据的加密开销、关键词的搜索开销、密文的存储成本与解密开销,在云存储环境中具有较好的应用前景。Abstract: The Attribute-Based Encryption (ABE) mechanism is one of the key technologies for implementing flexible access control of data in cloud storage. However, the existing ABE schemes have some problems, such as too much ciphertext storage overhead and user privacy leakage, and unsupported public auditing of cloud data. To solve these problems, a new searchable ABE scheme is proposed, and its security can be reduced to the difficulty of q-BDHE (q –decisional Bilinear Diffie-Hellman Exponent) problem and CDH (Computational Diffie-Hellman) problem. The proposed scheme achieves a constant ciphertext length on the basis of supporting keyword search. By introducing strategies to hide ideas, it prevents attackers from obtaining sensitive information and ensures the privacy of users. And the integrity of the data in cloud storage is verified through data public audit mechanism. Compared with the existing similar schemes, this scheme greatly reduces the data encryption overhead, keyword search overhead, ciphertext storage cost and decryption cost, which has a good application prospect to the cloud storage environment.
-
表 1 计算开销对比
表 2 存储开销对比
方案 属性权威中心 数据拥有者 访问用户 云服务提供商 文献[20] $2\left| {{Z_P}} \right|$ $(2{n_a} + 1)\left| {{G_1}} \right|$ ${n_k}\left| {{G_1}} \right|{\rm{ + }}\left| {{Z_p}} \right|$ $3\left| {{G_1}} \right| + \left| {{G_T}} \right|$ 文献[26] $({n_\omega } + 2)\left| {{Z_P}} \right|$ $({n_a} + 1)\left| {{G_1}} \right|$ $(2{n_k} + 1)\left| {{G_1}} \right| + \left| {{Z_P}} \right|$ $(2{n_\omega } + 1)\left| {{G_1}} \right| + \left| {{G_T}} \right|$ 文献[27] $\left| {{G_1}} \right| + \left| {{Z_P}} \right|$ ${n_a}\left| {{G_1}} \right| + \left| {{Z_P}} \right|$ $({n_k} + 1)\left| {{G_1}} \right|{\rm{ + }}\left| {{G_T}} \right|$ $({n_\omega } + 2)\left| {{G_1}} \right| + \left| {{G_T}} \right|$ 本文方案 $({n_\omega } + 2)\left| {{Z_P}} \right|$ ${n_a}\left| {{G_1}} \right|{\rm{ + }}{n_a}\left| {{G_T}} \right|$ ${n_k}\left| {{G_1}} \right|{\rm{ + }}\left| {{G_T}} \right|$ $2\left| {{G_1}} \right| + \left| {{G_T}} \right|$ -
ZHANG Jindan, WANG Baocang, HE Debiao, et al. Improved secure fuzzy auditing protocol for cloud data storage[J]. Soft Computing, 2019, 23(10): 3411–3422. doi: 10.1007/s00500-017-3000-1 ZHANG Yinghui, YANG Menglei, ZHENG Dong, et al. Efficient and secure big data storage system with leakage resilience in cloud computing[J]. Soft Computing, 2018, 22(23): 7763–7772. doi: 10.1007/s00500-018-3435-z BETHENCOURT J, SAHAI A, and WATERS B. Ciphertext-policy attribute-based encryption[C]. The 2007 IEEE Symposium on Security and Privacy, Berkeley, USA, 2007: 321–334. doi: 10.1109/SP.2007.11. WATERS B. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization[C]. The 14th International Conference on Practice and Theory in Public Key Cryptography Conference on Public Key Cryptography, Taormina, Italy, 2011: 53–70. doi: 10.1007/978-3-642-19379-8_4. ROUSELAKIS Y and WATERS B. Practical constructions and new proof methods for large universe attribute-based encryption[C]. The 2013 ACM SIGSAC Conference on Computer & Communications Security, New York, USA, 2013: 463–474. doi: 10.1145/2508859.2516672. CHEUNG L and NEWPORT C. Provably secure ciphertext policy abe[C]. The 14th ACM Conference on Computer and Communications Security, Alexandria, USA, 2007: 456–465. doi: 10.1145/1315245.1315302. LAI Junzuo, DENG R H, and LI Yingjiu. Expressive CP-ABE with partially hidden access structures[C]. The 7th ACM Symposium on Information, Computer and Communications Security, New York, USA, 2012: 18–19. doi: 10.1145/2414456.2414465. NISHIDE T, YONEYAMA K, and OHTA K. Attribute-based encryption with partially hidden encryptor-specified access structures[C]. The 6th International Conference on Applied Cryptography and Network Security, New York, USA, 2008: 111–129. doi: 10.1007/978-3-540-68914-0_7. 应作斌, 马建峰, 崔江涛. 支持动态策略更新的半策略隐藏属性加密方案[J]. 通信学报, 2015, 36(12): 178–189. doi: 10.11959/j.issn.1000-436x.2015327YING Zuobin, MA Jianfeng, and CUI Jiangtao. Partially policy hidden CP-ABE supporting dynamic policy updating[J]. Journal on Communications, 2015, 36(12): 178–189. doi: 10.11959/j.issn.1000-436x.2015327 PHUONG T V X, YANG Guomin, and SUSILO W. Hidden ciphertext policy attribute-based encryption under standard assumptions[J]. IEEE transactions on Information Forensics and Security, 2016, 11(1): 35–45. doi: 10.1109/TIFS.2015.2475723 XU Runhua and LANG Bo. A CP-ABE scheme with hidden policy and its application in cloud computing[J]. International Journal of Cloud Computing, 2015, 4(4): 279–298. doi: 10.1504/IJCC.2015.074224 ZHOU Zhibin, HUANG Dijiang, and WANG Zhijie. Efficient privacy-preserving ciphertext-policy attribute based-encryption and broadcast encryption[J]. IEEE Transactions on Computers, 2015, 64(1): 126–138. doi: 10.1109/TC.2013.200 LAI Junzuo, DENG R H, and LI Yingjiu. Fully secure cipertext-policy hiding CP-ABE[C]. The 7th International Conference on Information Security Practice and Experience, Guangzhou, China, 2011: 24–39. doi: 10.1007/978-3-642-21031-0_3. EMURA K, MIYAJI A, NOMURA A, et al. A ciphertext-policy attribute-based encryption scheme with constant ciphertext length[C]. The 5th International Conference on Information Security Practice and Experience, Xi’an, China, 2009: 13–23. doi: 10.1007/978-3-642-00843-6_2. HERRANZ J, LAGUILLAUMIE F, and RÀFOLS C. Constant size ciphertexts in threshold attribute-based encryption[C]. The 13th International Conference on Practice and Theory in Public Key Cryptography, Paris, France, 2010: 19–34. doi: 10.1007/978-3-642-13013-7_2. GE Aijun, ZHANG Rui, CHEN Cheng, et al. Threshold ciphertext policy attribute-based encryption with constant size ciphertexts[C]. The 17th Australasian Conference on Information Security and Privacy, Wollongong, Australia, 2012: 336–349. doi: 10.1007/978-3-642-31448-3_25. ZHANG Yinghui, ZHENG Dong, CHEN Xiaofeng, et al. Computationally efficient ciphertext-policy attribute-based encryption with constant-size ciphertexts[C]. The 8th International Conference on Provable Security, Hong Kong, China, 2014: 259–273. doi: 10.1007/978-3-319-12475-9_18. 安立峰, 范运东, 付钰. 支持策略隐藏且固定密文长度的属性基加密方案[J]. 通信技术, 2018, 51(1): 156–164. doi: 10.3969/j.issn.1002-0802.2018.01.028AN Lifeng, FAN Yundong, and FU Yu. Attribute-based encryption scheme with hidden policy and constant length ciphertext[J]. Communications Technology, 2018, 51(1): 156–164. doi: 10.3969/j.issn.1002-0802.2018.01.028 KUMAR G S and KRISHNA A S. Privacy Sustaining Constant Length Ciphertext-policy Attribute-based Broadcast Encryption[M]. WANG J, REDDY G, PRASAD V, et al. Soft Computing and Signal Processing. Singapore: Springer, 2019: 313–324. 赵志远, 朱智强, 王建华, 等. 属性可撤销且密文长度恒定的属性基加密方案[J]. 电子学报, 2018, 46(10): 2391–2399. doi: 10.3969/j.issn.0372-2112.2018.10.012ZHAO Zhiyuan, ZHU Zhiqiang, WANG Jianhua, et al. Attribute-based encryption with attribute revocation and constant-size ciphertext[J]. Acta Electronica Sinica, 2018, 46(10): 2391–2399. doi: 10.3969/j.issn.0372-2112.2018.10.012 SUSILO W, YANG Guomin, GUO Fuchun, et al. Constant-size ciphertexts in threshold attribute-based encryption without dummy attributes[J]. Information Sciences, 2018, 429: 349–360. doi: 10.1016/j.ins.2017.11.037 孙瑾, 王小静, 王尚平, 等. 支持属性撤销的可验证多关键词搜索加密方案[J]. 电子与信息学报, 2019, 41(1): 53–60. doi: 10.11999/JEIT180237SUN Jin, WANG Xiaojing, WANG Shangping, et al. Verifiable multi-keyword search encryption scheme with attribute revocation[J]. Journal of Electronics &Information Technology, 2019, 41(1): 53–60. doi: 10.11999/JEIT180237 牛淑芬, 谢亚亚, 杨平平, 等. 加密邮件系统中基于身份的可搜索加密方案[J]. 电子与信息学报, 2020, 42(7): 1803–1810. doi: 10.11999/JEIT190578NIU Shufen, XIE Yaya, YANG Pingping, et al. Identity-based searchable encryption scheme for encrypted email system[J]. Journal of Electronics &Information Technology, 2020, 42(7): 1803–1810. doi: 10.11999/JEIT190578 BELGUITH S, KAANICHE N, LAURENT M, et al. Phoabe: Securely outsourcing multi-authority attribute based encryption with policy hidden for cloud assisted IOT[J]. Computer Networks, 2018, 133: 141–156. doi: 10.1016/j.comnet.2018.01.036 苏金树, 曹丹, 王小峰, 等. 属性基加密机制[J]. 软件学报, 2011, 22(6): 1299–1315. doi: 10.3724/SP.J.1001.2011.03993SU Jinshu, CAO Dan, WANG Xiaofeng, et al. Attribute-based encryption schemes[J]. Journal of Software, 2011, 22(6): 1299–1315. doi: 10.3724/SP.J.1001.2011.03993 QIU Shuo, LIU Jiqiang, SHI Yanfeng, et al. Hidden policy ciphertext-policy attribute-based encryption with keyword search against keyword guessing attack[J]. Science China Information Sciences, 2017, 60(5): 052105. doi: 10.1007/s11432-015-5449-9 刘振华, 周佩琳, 段淑红. 支持关键词搜索的属性代理重加密方案[J]. 电子与信息学报, 2018, 40(3): 683–689. doi: 10.11999/JEIT170448LIU Zhenhua, ZHOU Peilin, and DUAN Shuhong. Attribute-based proxy re-encryption scheme with keyword search[J]. Journal of Electronics &Information Technology, 2018, 40(3): 683–689. doi: 10.11999/JEIT170448 -





 下载:
下载:


 下载:
下载:
