Research on Target Failure Link Location Method in Inter-domain Routing System Cascading Failure
-
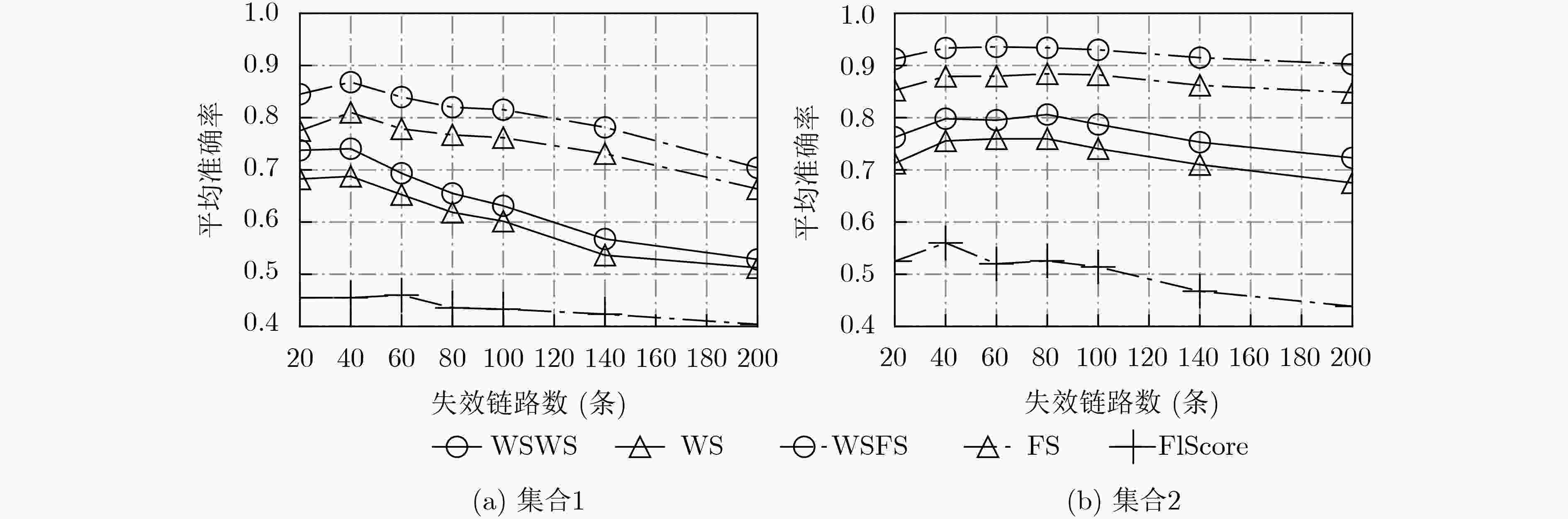
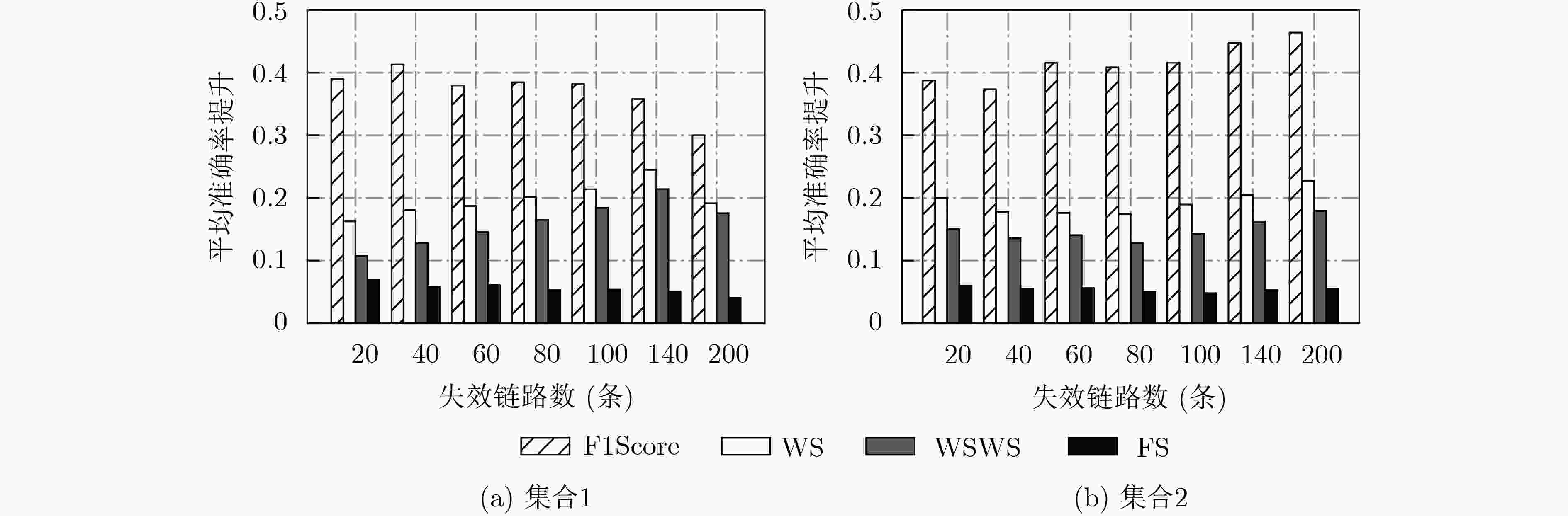
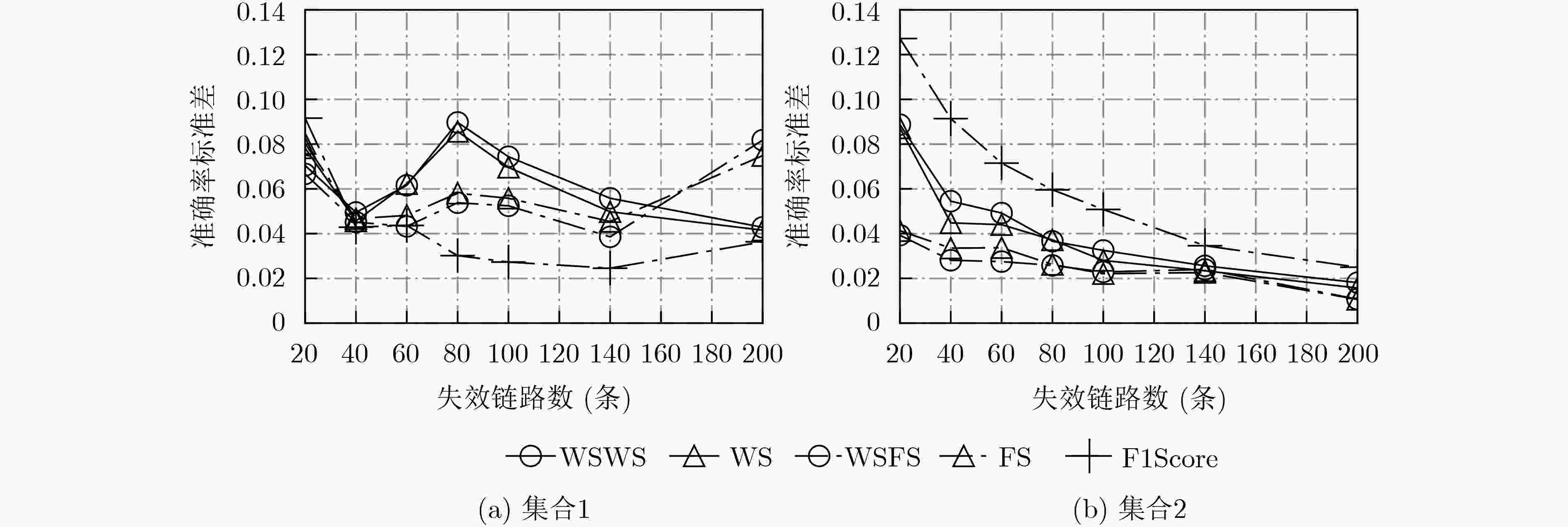
摘要: 协同跨平面会话中断攻击(CXPST)通过反复对多条目标关键链路实施低速率拒绝服务攻击(LDoS)造成域间路由系统的级联失效,从而导致互联网的崩溃。在攻击发生的初期,准确定位受攻击的关键链路并进行针对性防御可遏制级联失效的发生。现有定位方法研究主要基于单源假设,没有考虑多条目标链路同时失效对路径撤回的影响,定位准确度受限。针对上述问题,该文提出一种基于加权统计匹配得分的多失效链路定位方法(WSFS),以级联失效攻击目标链路选择策略作为推断基础,将撤销路径长度的倒数作为权重对评分进行加权。基于实际网络拓扑和有利点位置的级联失效攻击仿真实验结果表明,WSFS比目前最优方法平均准确率可提升5.45%。实验结果证明WSFS相比于其他定位方法更适合应对域间路由系统级联失效下的目标失效链路定位问题。Abstract: Coordinated Cross Plane Session Termination (CXPST) repeatedly implements Low rate Denial of Service (LDoS) attacks on multiple target critical links, causing the cascading failure of the inter-domain routing system and the collapse of the internet. In the early stages of an attack, accurately locating the critical link under attack and carrying out targeted defense can prevent the occurrence of cascading failures. The research on existing locating methods is mainly based on the single-source hypothesis, and does not consider the impact of simultaneous failure of multiple target links on path withdrawal, so the locating accuracy is limited. To solve the above problems, a locating method is proposed based on Weighted Statistical Fit Score (WSFS). Using the target link selection strategy of cascading failure attack as inferring basis, scores are weighted by the reciprocal of the length of the withdrawal paths. The simulation results based on the actual network topology and vantage point location show that WSFS can improve the average accuracy rate by 5.45% compared with the current optimal method. Experimental results prove that WSFS is more suitable for locating target failure links in inter-domain routing system cascading failure than other locating methods.
-
表 1 单失效链路定位方法的对比分析
表 2 各链路的WS值
链路 WS值 CD 1.00 AC 0.75 BC 0.75 DE 0.50 DF 0.25 EG 0.25 -
REKHTER Y, LI T, and HARES S. IETF RFC 4271 A border gateway protocol 4 (BGP-4)[S]. 2006. SERMPEZIS P, KOTRONIS V, DAINOTTI A, et al. A survey among network operators on BGP prefix hijacking[J]. ACM SIGCOMM Computer Communication Review, 2018, 48(1): 64–69. doi: 10.1145/3211852.3211862 BUTLER K, MCDANIEL P, and AIELLO W. Optimizing BGP security by exploiting path stability[C]. The 13th ACM Conference on Computer and Communications Security, Alexandria, USA, 2006: 298–310. SCHUCHARD M, THOMPSON C, HOPPER N, et al. Taking routers off their meds: Why assumptions of router stability are dangerous[C]. The 19th Network and Distributed System Security Symposium, San Diego, USA, 2012. DENG Wenping, ZHU Peidong, LU Xicheng, et al. On Evaluating BGP routing stress attack[J]. Journal of Communications, 2010, 5(1): 13–22. SCHUCHARD M, MOHAISEN A, FOO KUNE D, et al. Losing control of the internet: Using the data plane to attack the control plane[C]. The 17th ACM Conference on Computer and Communications Security, Chicago, USA, 2010: 726–728. LI Heshuai, ZHU Junhu, QIU Han, et al. The new threat to internet: DNP attack with the attacking flows strategizing technology[J]. International Journal of Communication Systems, 2015, 28(6): 1126–1139. doi: 10.1002/dac.2748 ZHANG Ying, MAO Z M, WANG J. Low-Rate TCP-targeted DoS attack disrupts internet routing[C]. 2007 Network and Distributed System Security Symposium, San Diego, USA, 2007. 郑皓, 陈石, 梁友. 关于“数字大炮”网络攻击方式及其防御措施的探讨[J]. 计算机研究与发展, 2012, 49(S1): 69–72.ZHENG Hao, CHEN Shi, and LIANG You. How the cyber weapon “Digital Ordnance” works and its precautionary measures[J]. Journal of Computer Research and Development, 2012, 49(S1): 69–72. 邱菡, 李玉峰, 兰巨龙, 等. 域间路由系统的级联失效攻击及检测研究[J]. 中国科学: 信息科学, 2017, 47(12): 1715–1729. doi: 10.1360/N112016-00259QIU Han, LI Yufeng, LAN Julong, et al. Research on cascading failure attack and detection of inner-domain routing system[J]. Scientia Sinica Informationis, 2017, 47(12): 1715–1729. doi: 10.1360/N112016-00259 QIU Han, ZHU Huihu, LI Yufeng, et al. FD-SP: A method for predicting cascading failures of inter-domain routing system[C]. The 4th IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 2018: 290–295. GUO Yi, DUAN Haixin, CHEN Jikun, et al. MAF-SAM: An effective method to perceive data plane threats of inter domain routing system[J]. Computer Networks, 2016, 110: 69–78. doi: 10.1016/j.comnet.2016.09.017 ZHANG Mingwei, LI Jun, and BROOKS S. I-Seismograph: Observing, measuring, and analyzing internet earthquakes[J]. IEEE/ACM Transactions on Networking, 2017, 25(6): 3411–3426. doi: 10.1109/TNET.2017.2748902 ZENG Ziyi, ZHU Junhu, QIU Han, et al. SM-RC: A new security measurement method for inter-domain routing system[J]. IEEE Access, 2019, 7: 108189–108199. doi: 10.1109/ACCESS.2019.2927712 CAESAR M, SUBRAMANIAN L, and KATZ R H. Towards localizing root causes of BGP dynamics[R]. UCB/CSD-04-1302, 2003. FELDMANN A, MAENNEL O, MAO Z M, et al. Locating Internet routing instabilities[J]. ACM SIGCOMM Computer Communication Review, 2004, 34(4): 205–218. doi: 10.1145/1030194.1015491 JAVED U, CUNHA I, CHOFFNES D, et al. PoiRoot: Investigating the root cause of interdomain path changes[J]. ACM SIGCOMM Computer Communication Review, 2013, 43(4): 183–194. doi: 10.1145/2534169.2486036 GLASS K, COLBAUGH R, and PLANCK M. Automatically identifying the sources of large Internet events[C]. 2010 IEEE International Conference on Intelligence and Security Informatics, Vancouver, Canada, 2010: 108–113. VENTORIM COMARELA G. On the dynamics of interdomain routing in the Internet[D]. [Ph. D. dissertation], Boston University, 2017. HOLTERBACH T, VISSICCHIO S, DAINOTTI A, et al. Swift: Predictive fast reroute[C]. 2017 Conference of the ACM Special Interest Group on Data Communication, Los Angeles, USA, 2017: 460–473. CAIDA. BGP AS links[EB/OL]. http://as-rank.caida.org. RIPE. RIS raw data[EB/OL]. https://www.ripe.net/analyse/internet-measurements/routing-information-service-ris/ris-raw-data, 2019. -






 下载:
下载:


 下载:
下载:
