A Switching Authentication Protocol of Terminal Node for Fog Computing
-
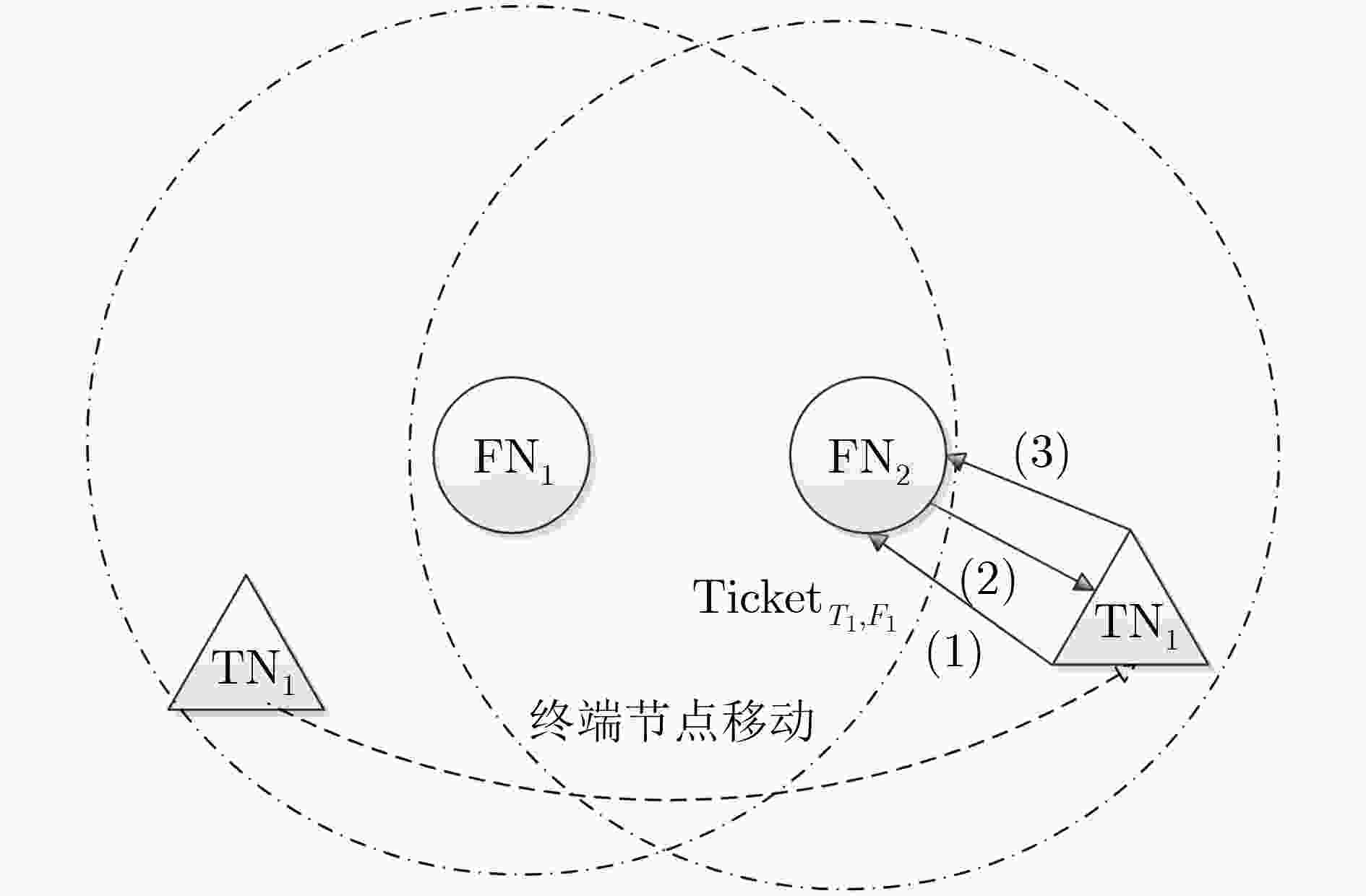
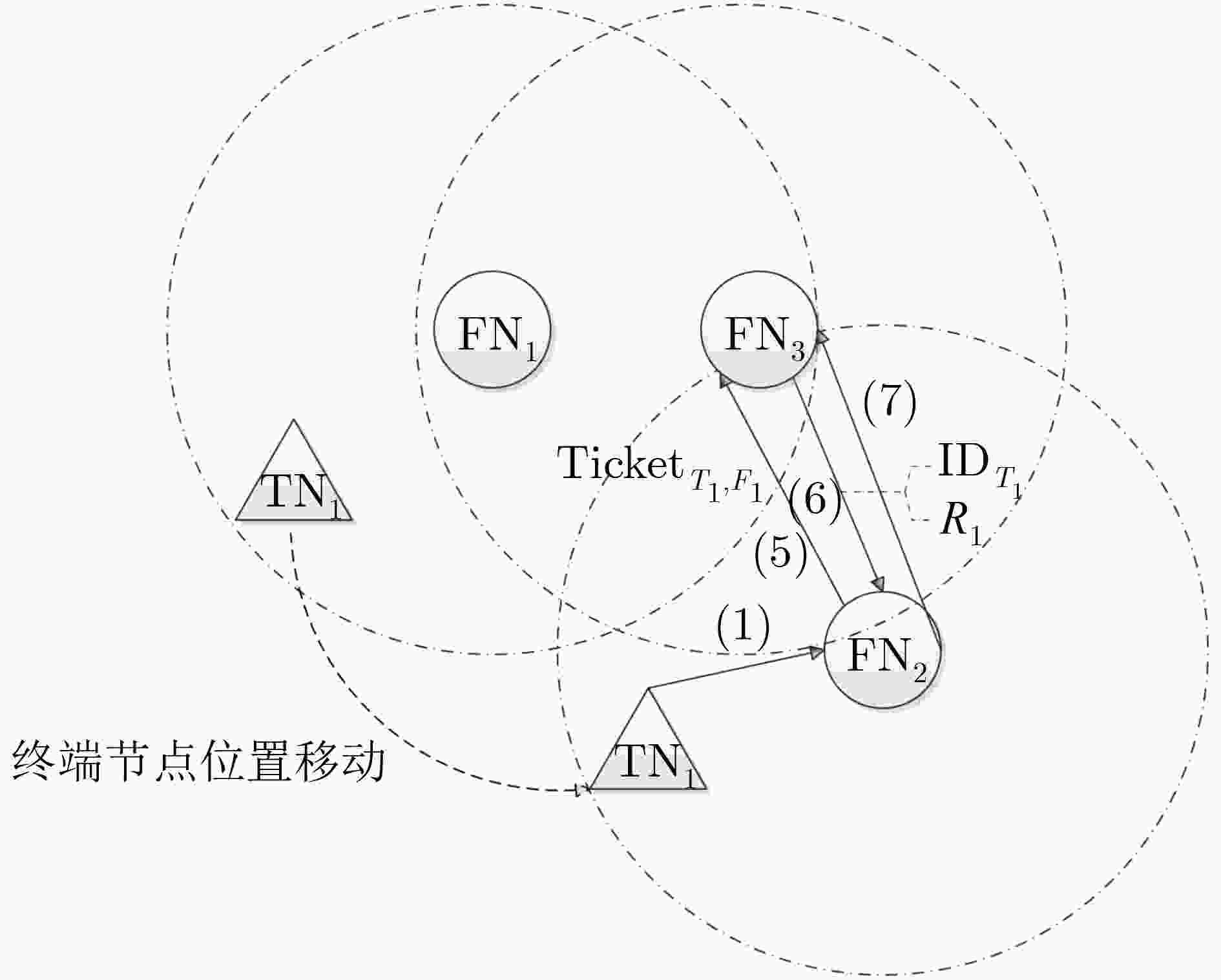
摘要: 针对当前雾计算环境下终端节点的切换认证协议在存储量、计算量和安全性等方面还存在缺陷,该文提出一种高效的终端节点切换认证协议。在该协议中,采用双因子组合公钥(TF-CPK)和认证Ticket相结合的方式,实现雾节点和终端节点的相互认证和会话密钥协商。安全性和性能分析结果表明,该协议支持不可跟踪性,可以抵抗众多已知攻击和安全威胁,且具有较小的系统开销。Abstract: In order to solve the problem that the switching authentication protocol of terminal nodes in fog computing has some defects in storage, compute and security, an efficient terminal node switching authentication protocol is proposed. In this protocol, mutual authentication and session key agreement between the fog nodes and terminal nodes are realized by the combination of Two Factors Combined Public Key(TF-CPK) and authentication ticket. The security and performance analysis results show that the protocol supports untraceability, which can resist numerous known attacks and security threats, and has a smaller system overhead.
-
表 1 初始化认证通信跳数比较表
表 2 切换重认证通信跳数比较表
表 3 初始化认证和切换重认证计算开销比较表
运算种类 初始化认证 切换重认证 对称加密/解密 3 2 非对称加密/解密 1 0 签名或验证 1 0 哈希运算 3 2 -
王颖, 王懿, 陈文瑛, 等. 一种面向分布式分析的雾计算架构及其在电网安全风险评估中的应用[J]. 自动化与仪器仪表, 2016(9): 128–130, 132. doi: 10.14016/j.cnki.1001-9227.2016.09.128WANG Ying, WANG Yi, CHEN Wenying, et al. A fog computing infrastructure for distributed analytics and its application in risk assessment to power grid[J]. Automation &Instrumentation, 2016(9): 128–130, 132. doi: 10.14016/j.cnki.1001-9227.2016.09.128 IBRAHIM M H. Octopus: An edge-fog mutual authentication scheme[J]. International Journal of Network Security, 2016, 18(6): 1089–1101. YI Shanhe, QIN Zhengrui, and Li Qun. Security and privacy issues of fog computing: A survey[C]. The 10th International Conference on Wireless Algorithms, Systems, and Applications, Qufu, China, 2015: 685–695. doi: 10.1007/978-3-319-21837-3_67. 张海波, 程妍, 刘开健, 等. 车联网中整合移动边缘计算与内容分发网络的移动性管理策略[J]. 电子与信息学报, 2020, 42(6): 1444–1451. doi: 10.11999/JEIT190571ZHANG Haibo, CHENG Yan, LIU Kaijian, et al. The mobility management strategies by integrating mobile edge computing and CDN in vehicular networks[J]. Journal of Electronics &Information Technology, 2020, 42(6): 1444–1451. doi: 10.11999/JEIT190571 MUKHERJEE M, MATAM R, SHU Lei, et al. Security and privacy in fog computing: Challenges[J]. IEEE Access, 2017, 5: 19293–19304. doi: 10.1109/ACCESS.2017.2749422 NI Jianbing, ZHANG Kuan, LIN Xiaodong, et al. Securing fog computing for internet of things applications: Challenges and solutions[J]. IEEE Communications Surveys & Tutorials, 2018, 20(1): 601–628. doi: 10.1109/COMST.2017.2762345 黄彬, 刘广钟, 徐明. 基于簇的无线传感器网络安全节点认证协议[J]. 计算机工程, 2016, 42(7): 117–122, 128. doi: 10.3969/j.issn.1000-3428.2016.07.020HUANG Bin, LIU Guangzhong, and XU Ming. Security authentication protocol for nodes in wireless sensor networks based on clusters[J]. Computer Engineering, 2016, 42(7): 117–122, 128. doi: 10.3969/j.issn.1000-3428.2016.07.020 HAN K, KIM K, and SHON T. Untraceable mobile node authentication in WSN[J]. Sensors, 2010, 10(5): 4410–4429. doi: 10.3390/s100504410 HAN K, SHON T, and KIM K. Efficient mobile sensor authentication in smart home and WPAN[J]. IEEE Transactions on Consumer Electronics, 2010, 56(2): 591–596. doi: 10.1109/TCE.2010.5505975 IBRIQ J and MAHGOUB I. A hierarchical key establishment scheme for wireless sensor networks[C]. The 21st International Conference on Advanced Information Networking and Applications, Niagara Falls, Canada, 2007: 210–219. doi: 10.1109/AINA.2007.14. FANTACCI R, CHITI F, and MACCARI L. Fast distributed bi-directional authentication for wireless sensor networks[J]. Security and Communication Networks, 2008, 1(1): 17–24. doi: 10.1002/sec.1 房帅磊. 层次化无线传感器网络移动节点认证技术研究[D]. [硕士论文], 西安电子科技大学, 2011.FANG Shuailei. Study on mobile nodes authentication in hierarchical wireless sensor networks[D]. [Master dissertation], Xidian University, 2011. 南湘浩. CPK密码体制与网际安全[M]. 北京: 国防工业出版社, 2008: 23–28.NAN Xianghao. CPK-Crypotosystem and Cyber Security[M]. Beijing: National Defense Industry Press, 2008: 23–28. 张鑫, 杨晓元, 朱率率. 移动网络可信匿名认证协议[J]. 计算机应用, 2016, 36(8): 2231–2235. doi: 10.11772/j.issn.1001-9081.2016.08.2231ZHANG Xin, YANG Xiaoyuan, and ZHU Shuaishuai. Trusted and anonymous authentication protocol for mobile networks[J]. Journal of Computer Applications, 2016, 36(8): 2231–2235. doi: 10.11772/j.issn.1001-9081.2016.08.2231 KARLOF C, SASTRY N, and WAGNER D. TinySec: A link layer security architecture for wireless sensor networks[C]. The 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, USA, 2004: 3–5. LEE H R, CHOI Y J, and KIM H W. Implementation of TinyHash based on hash algorithm for sensor network[C]. The World Academy of Science, Engineering and Technology, Saint Louis, USA, 2005: 135–139. -





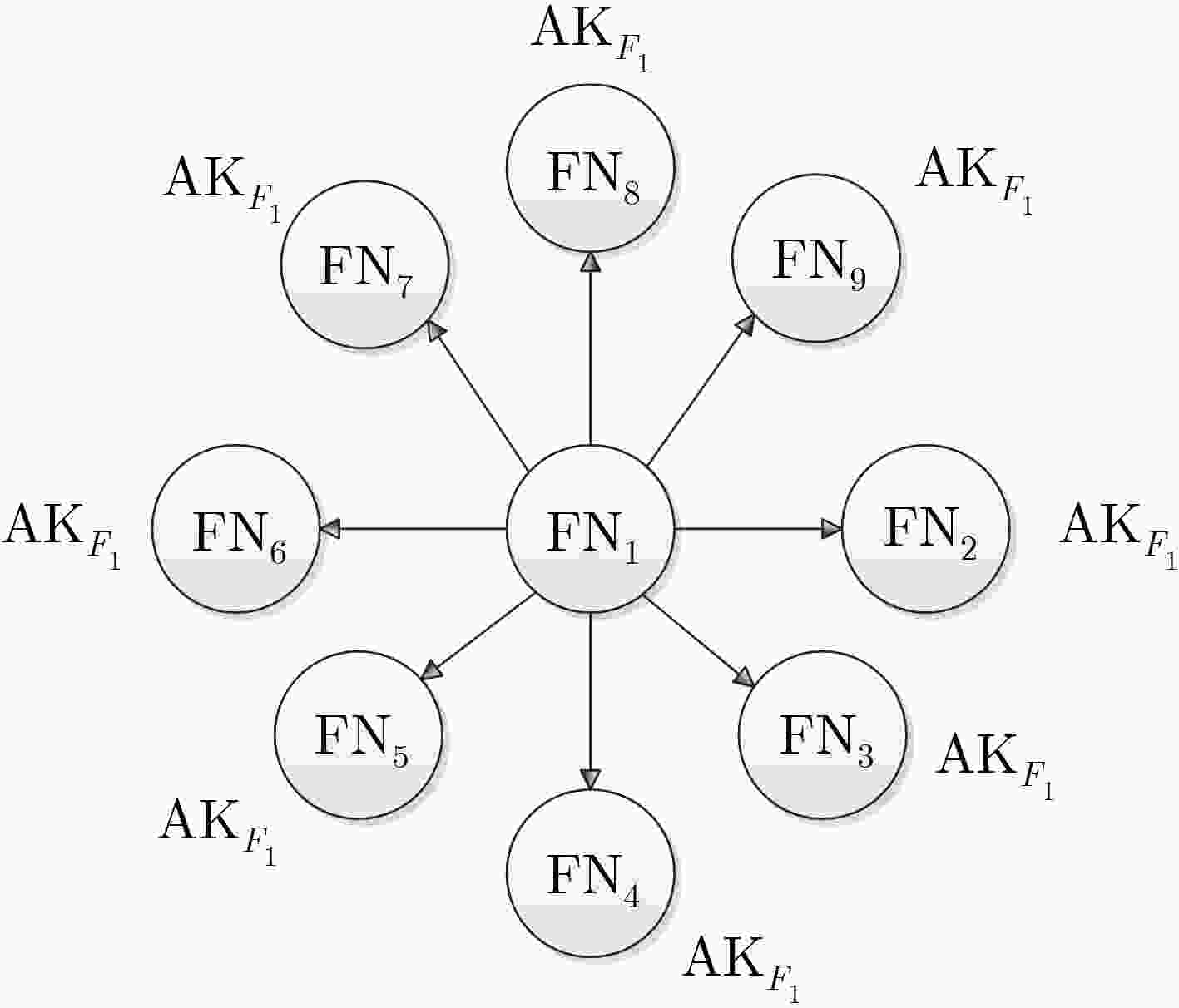


 下载:
下载:
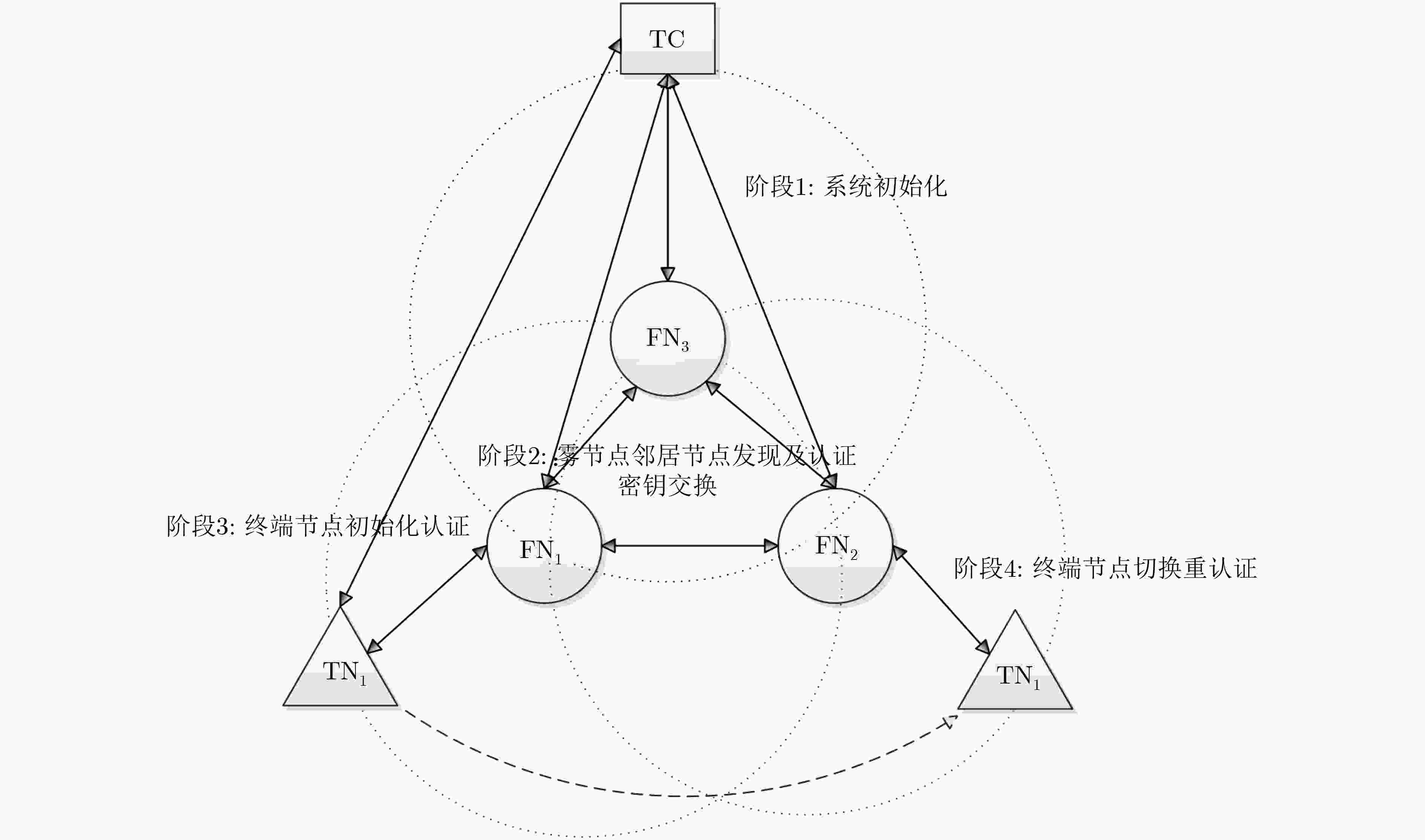


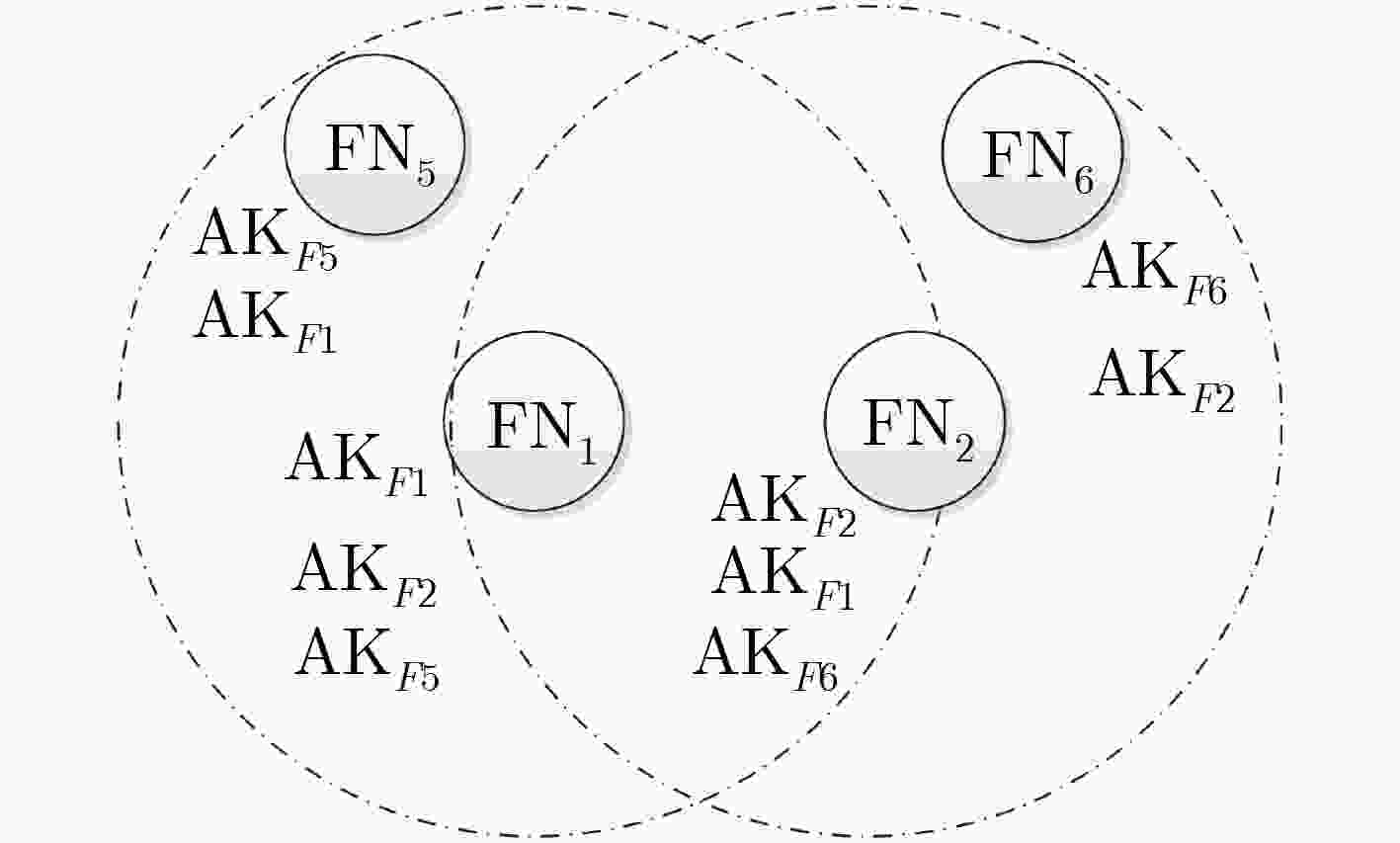
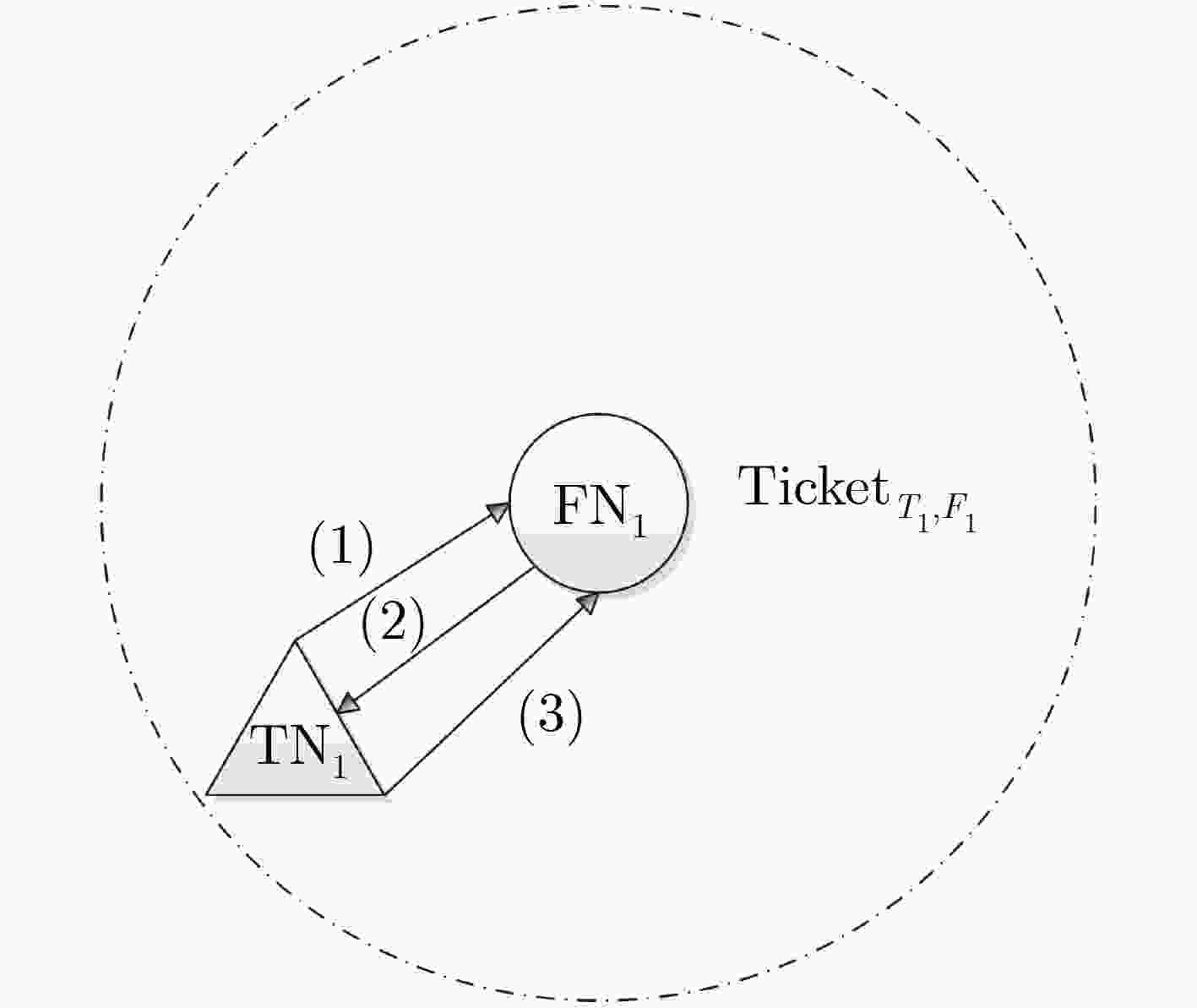






 下载:
下载:
