Fast Public Key Searchable Encryption Scheme against Internal Keyword Guessing Attack in Cloud Environment
-
摘要:
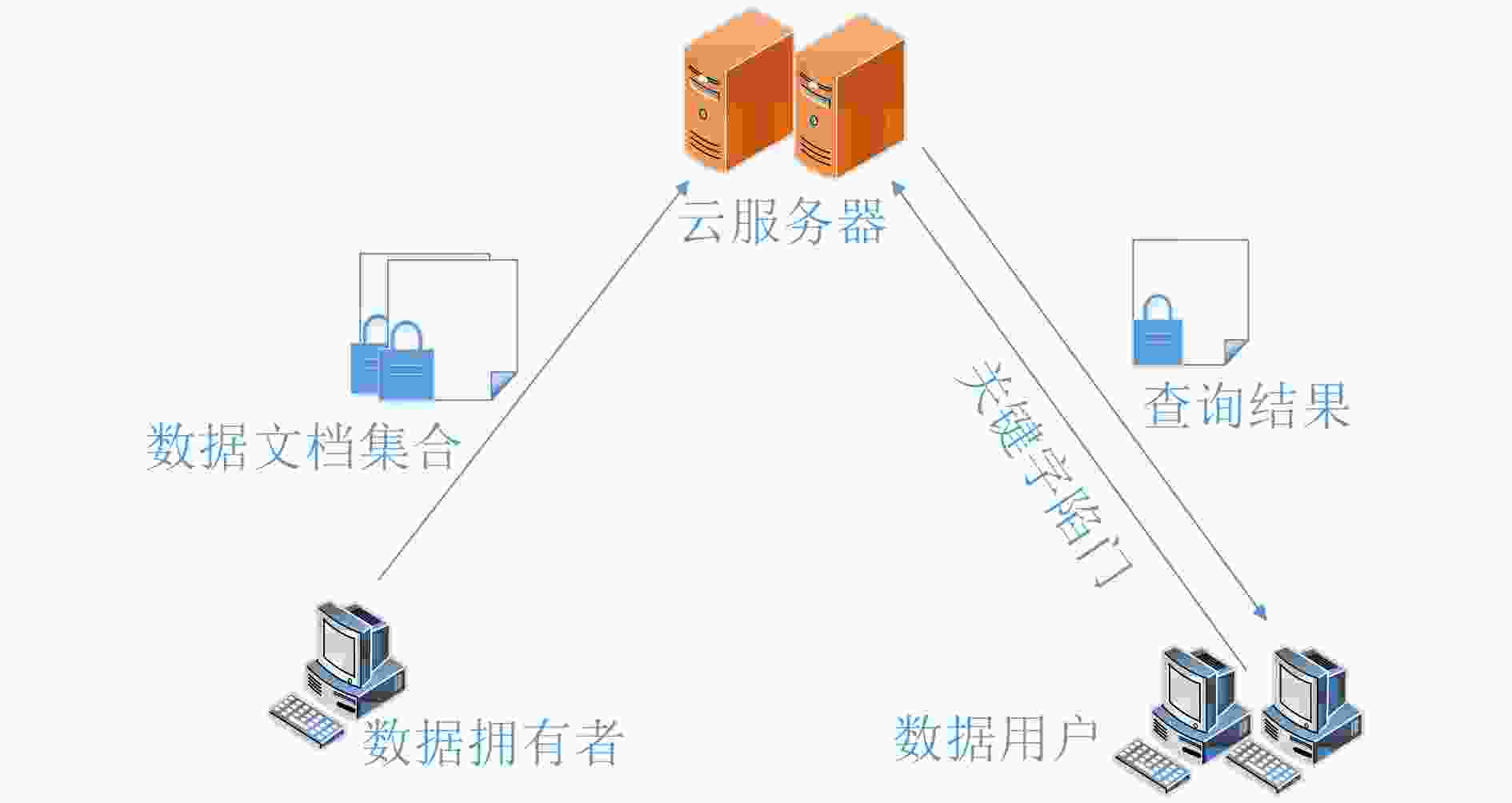
随着云计算的发展,以密文检索为核心的安全和搜索性能问题成为研究的重点。在传统的加密方案中,大多只解决了抵御外部关键字猜测攻击问题,往往忽视了诚实且好奇的云服务器问题。为了提高密文安全性,该文提出快速搜索的抵御内部关键字攻击方案。首先,引入高效的加密倒排索引结构的公钥密文搜索方案,实现关键字的并行搜索任务。其次,在构建密文倒排索引时加入数据拥有者的私钥抵御恶意云服务器的关键字攻击。与传统的公钥可搜索加密相比,该方案在很大程度上增强了搜索系统的安全性和搜索效率。
Abstract:With the development of cloud computing, the security and search performance of ciphertext retrieval has become the focus of research. In the traditional encryption schemes, most of them only solve the problem of defending against external keyword guessing attacks but ignore the honest and curious cloud server. In order to improve the security of ciphertext, an inside keyword attack scheme based on inverted index is proposed. Firstly, the private key of the data owner is added to resist the keyword attack of the malicious cloud server when the ciphertext inversion index is built. Secondly, an efficient public key ciphertext search scheme of parallel encryption index structure is introduced to realize the parallel search task of keywords. Compared with the traditional public key searchable encryption, the proposed scheme enhances greatly the security and search efficiency of the search system.
-
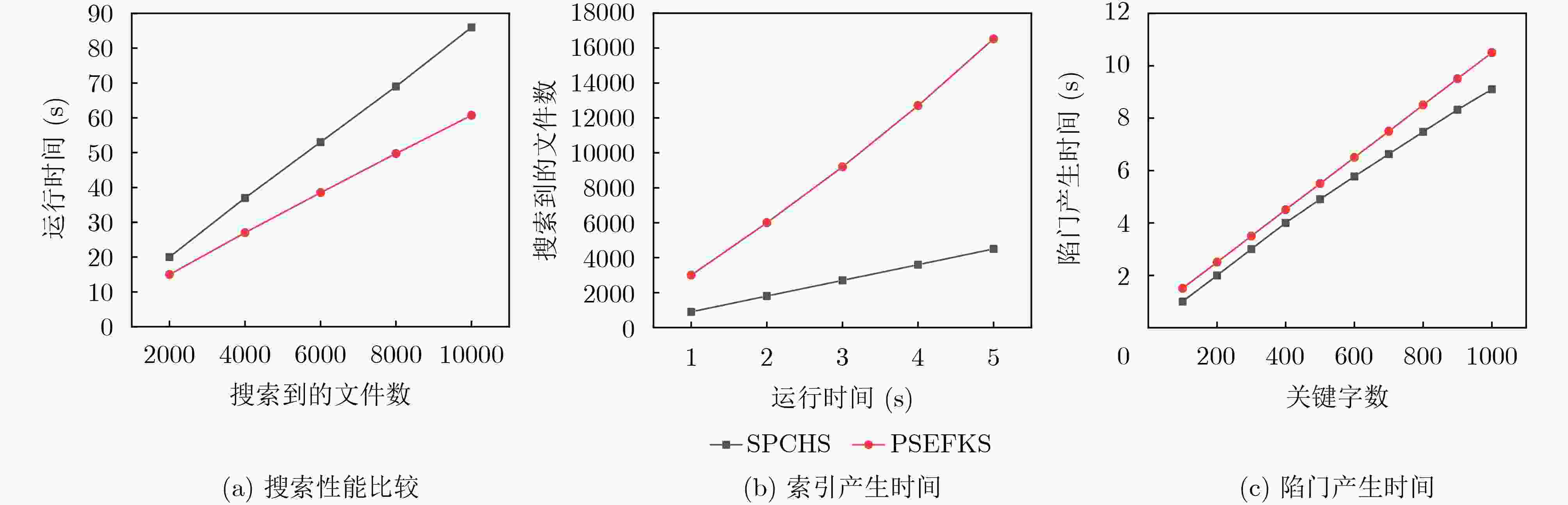
表 1 性能分析
初始化 索引 陷门 搜索 Boneh 2E 2E+2H+P E+H H+P Shao (n+3)E 9E+3H+3P 2E 5E+H+4P SPCHS 2E 3E+H+2P E+H 2P PSEFKS 2E 2E+H+P E+H+P E+H+P 表 2 安全性对比
Boneh Shao SPCHS PSEFKS 密文不可区分 是 是 是 是 陷门不可区分 否 是 是 是 抗外部攻击 是 是 是 是 抗内部攻击 否 是 否 是 -
李经纬, 贾春福, 刘哲理, 等. 可搜索加密技术研究综述[J]. 软件学报, 2015, 26(1): 109–128. doi: 10.13328/j.cnki.jos.004700LI Jingwei, JIA Chunfu, LIU Zheli, et al. Survey on the searchable encryption[J]. Journal of Software, 2015, 26(1): 109–128. doi: 10.13328/j.cnki.jos.004700 SONG D X, WAGNER D, and PERRIG A. Practical techniques for searches on encrypted data[C]. 2000 IEEE Symposium on Security and Privacy, Berkeley, USA, 2000: 44–55. doi: 10.1109/SECPRI.2000.848445. 李双, 徐茂智. 基于属性的可搜索加密方案[J]. 计算机学报, 2014, 37(5): 1017–1024. doi: 10.3724/SP.J.1016.2014.01017LI Shuang and XU Maozhi. Attribute-based public encryption with keyword search[J]. Chinese Journal of Computers, 2014, 37(5): 1017–1024. doi: 10.3724/SP.J.1016.2014.01017 BONEH D, DI CRESCENZO G, OSTROVSKY R, et al. Public key encryption with keyword search[C]. International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2004: 506–522. doi: 10.1007/978-3-540-24676-3_30. 董晓蕾, 周俊, 曹珍富. 可搜索加密研究进展[J]. 计算机研究与发展, 2017, 54(10): 2107–2120. doi: 10.7544/issn1000-1239.2017.20170627DONG Xiaolei, ZHOU Jun, and CAO Zhenfu. Research advances on secure searchable encryption[J]. Journal of Computer Research and Development, 2017, 54(10): 2107–2120. doi: 10.7544/issn1000-1239.2017.20170627 FANG Liming, SUSILO W, GE Chunpeng, et al. Public key encryption with keyword search secure against keyword guessing attacks without random oracle[J]. Information Sciences, 2013, 238: 221–241. doi: 10.1016/j.ins.2013.03.008 SUN Lixue, XU Chunxiang, ZHANG Mingwu, et al. Secure searchable public key encryption against insider keyword guessing attacks from indistinguishability obfuscation[J]. Science China Information Sciences, 2018, 61(3): 038106. doi: 10.1007/s11432-017-9124-0 BYUN J W, RHEE H S, PARK H A, et al. Off-line keyword guessing attacks on recent keyword search schemes over encrypted data[C]. 3rd VLDB Workshop on Secure Data Management, Seoul, South Korea, 2006: 75–83. doi: 10.1007/11844662_6. WANG Bing, SONG Wei, LOU Wenjing, et al. Inverted index based multi-keyword public-key searchable encryption with strong privacy guarantee[C]. 2015 IEEE Conference on Computer Communications, Hong Kong, China, 2015: 2092–2100. doi: 10.1109/INFOCOM.2015.7218594. PENG Yanguo, CUI Jiangtao, PENG Changgen, et al. Certificateless public key encryption with keyword search[J]. China Communications, 2014, 11(11): 100–113. doi: 10.1109/CC.2014.7004528 DING Shugeng, LI Yidong, ZHANG Jianhui, et al. An efficient and privacy-preserving ranked fuzzy keywords search over encrypted cloud data[C]. 2016 International Conference on Behavioral, Economic and Socio-cultural Computing, Durham, USA, 2016: 1–6. doi: 10.1109/BESC.2016.7804500. RHEE H S, PARK J H, SUSILO W, et al. Trapdoor security in a searchable public-key encryption scheme with a designated tester[J]. Journal of Systems and Software, 2010, 83(5): 763–771. doi: 10.1016/j.jss.2009.11.726 YAU W C, HENG S H, and GOI B M. Off-line keyword guessing attacks on recent public key encryption with keyword search schemes[C]. The 5th International Conference on Autonomic and Trusted Computing, Oslo, Norway, 2008: 100–105. doi: 10.1007/978-3-540-69295-9_10. DU Minxin, WANG Qian, HE Meiqi, et al. Privacy-preserving indexing and query processing for secure dynamic cloud storage[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(9): 2320–2332. doi: 10.1109/TIFS.2018.2818651 SHAO Zhiyi and YANG Bo. On security against the server in designated tester public key encryption with keyword search[J]. Information Processing Letters, 2015, 115(12): 957–961. doi: 10.1016/j.ipl.2015.07.006 张玉磊, 文龙, 王浩浩, 等. 多用户环境下无证书认证可搜索加密方案[J]. 电子与信息学报, 2020, 42(5): 1094–1101. doi: 10.11999/JEIT190437ZHANG Yulei, WEN Long, WANG Haohao, et al. Certificateless authentication searchable encryption scheme for multi-user[J]. Journal of Electronics &Information Technology, 2020, 42(5): 1094–1101. doi: 10.11999/JEIT190437 SAITO T and NAKANISHI T. Designated-senders public-key searchable encryption secure against keyword guessing attacks[C]. 2017 5th International Symposium on Computing and Networking, Aomori, 2017: 496–502. 杜瑞忠, 李明月, 田俊峰, 等. 基于倒排索引的可验证混淆关键字密文检索方案[J]. 软件学报, 2019, 30(8): 2362–2374.DU Ruizhong, LI Mingyue, TIAN Junfeng, et al. Verifiable obfuscated keyword ciphertext retrieval scheme based on inverted index[J]. Journal of Software, 2019, 30(8): 2362–2374. XU Peng, TANG Xiaolan, WANG Wei, et al. Fast and parallel keyword search over public-key ciphertexts for cloud-assisted IoT[J]. IEEE Access, 2017, 5: 24775–24784. doi: 10.1109/ACCESS.2017.2771301 LYNN B. PBC Library[DB/OL]. https://crypto.stanford.edu/pbc/. -





 下载:
下载:
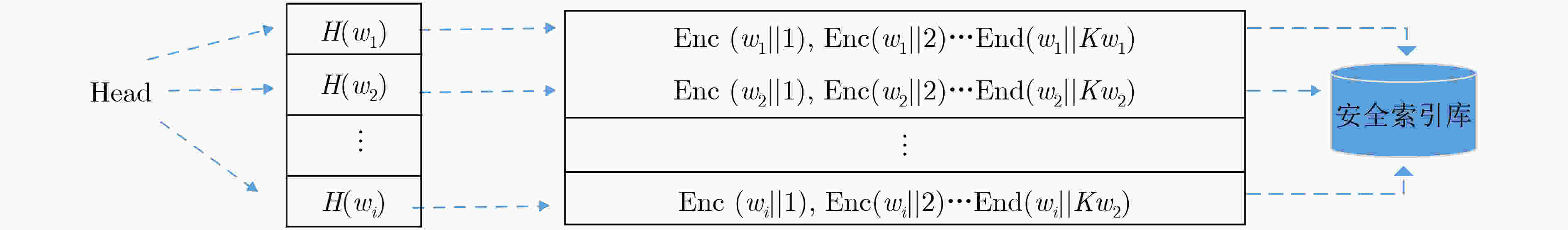
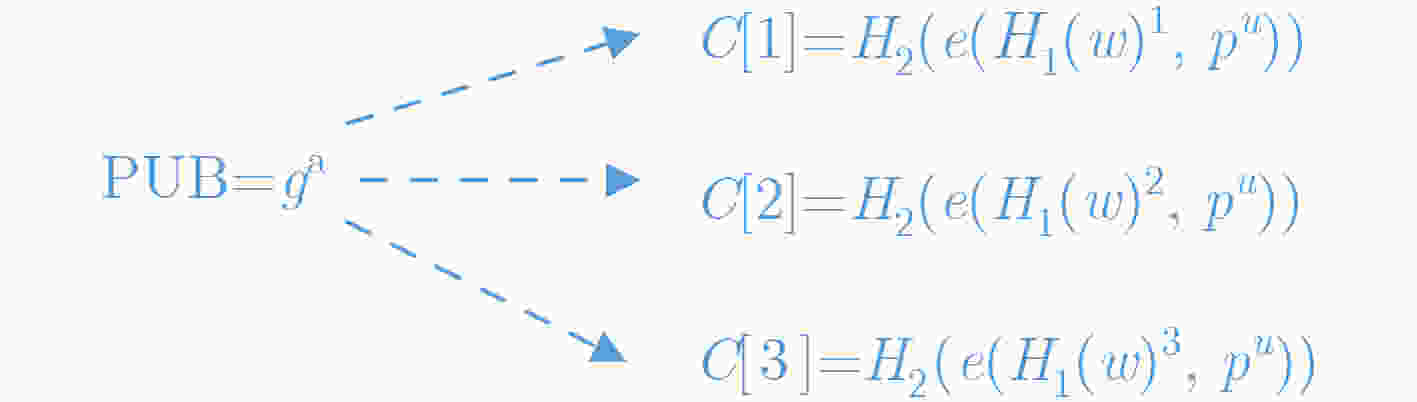
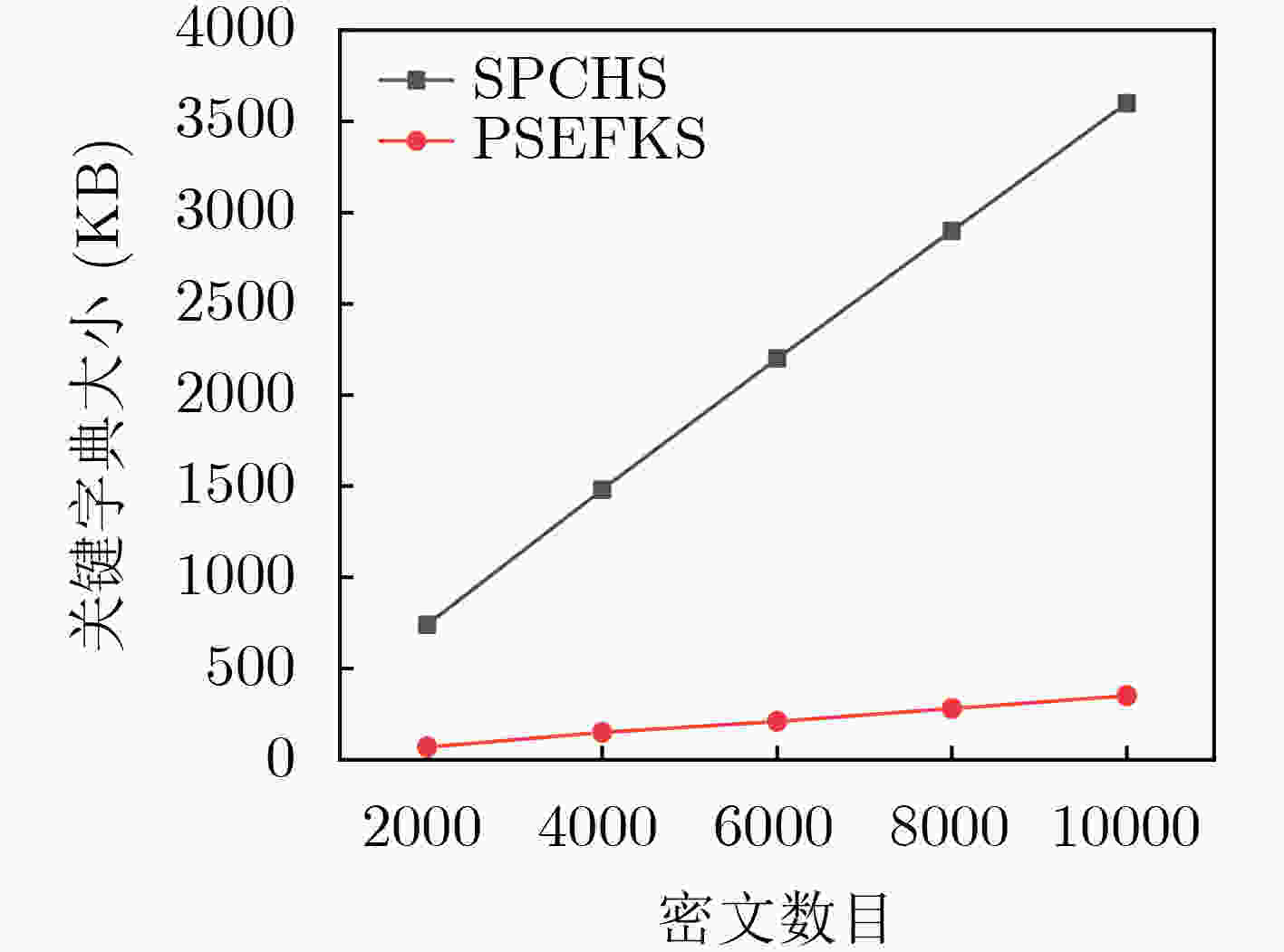


 下载:
下载:
