Joint Secure Routing and Power Optimization Algorithm for Wireless Ad Hoc Networks
-
摘要:
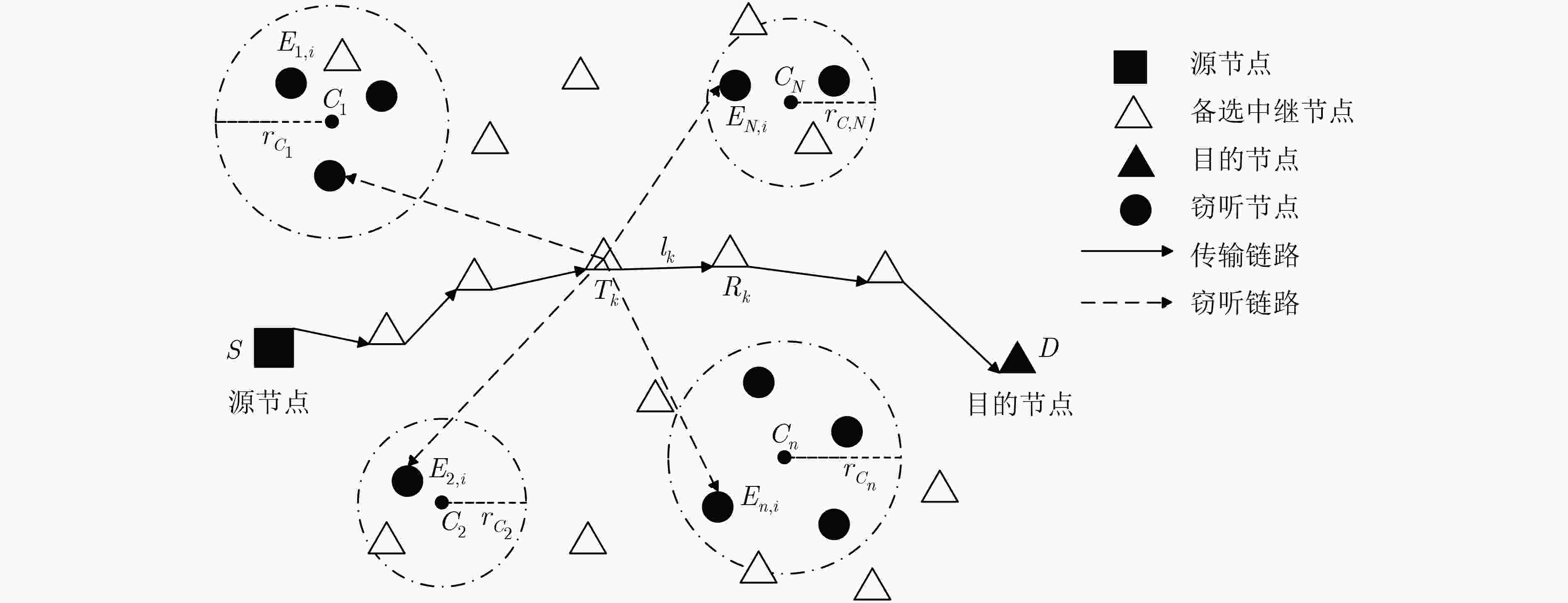
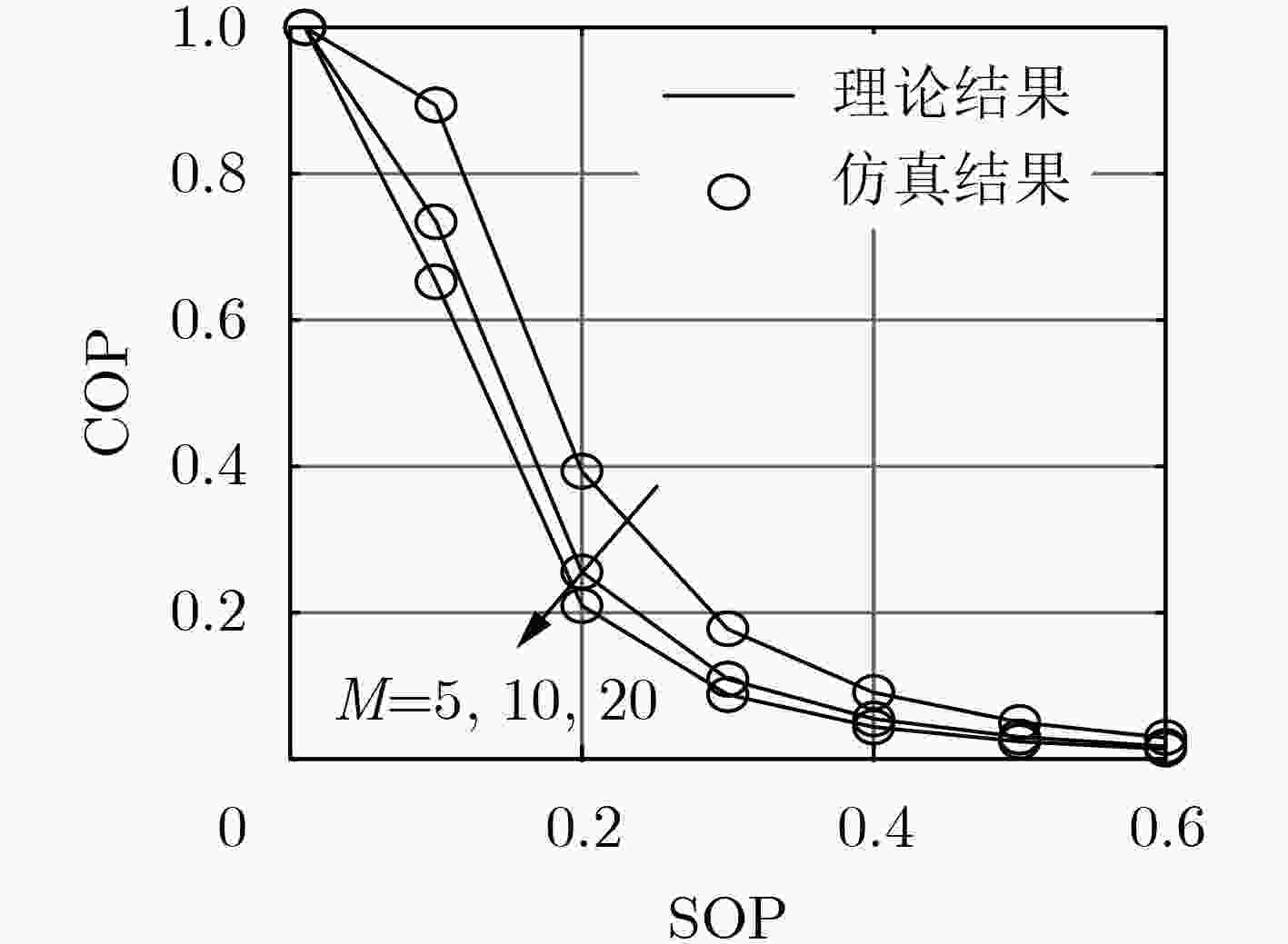
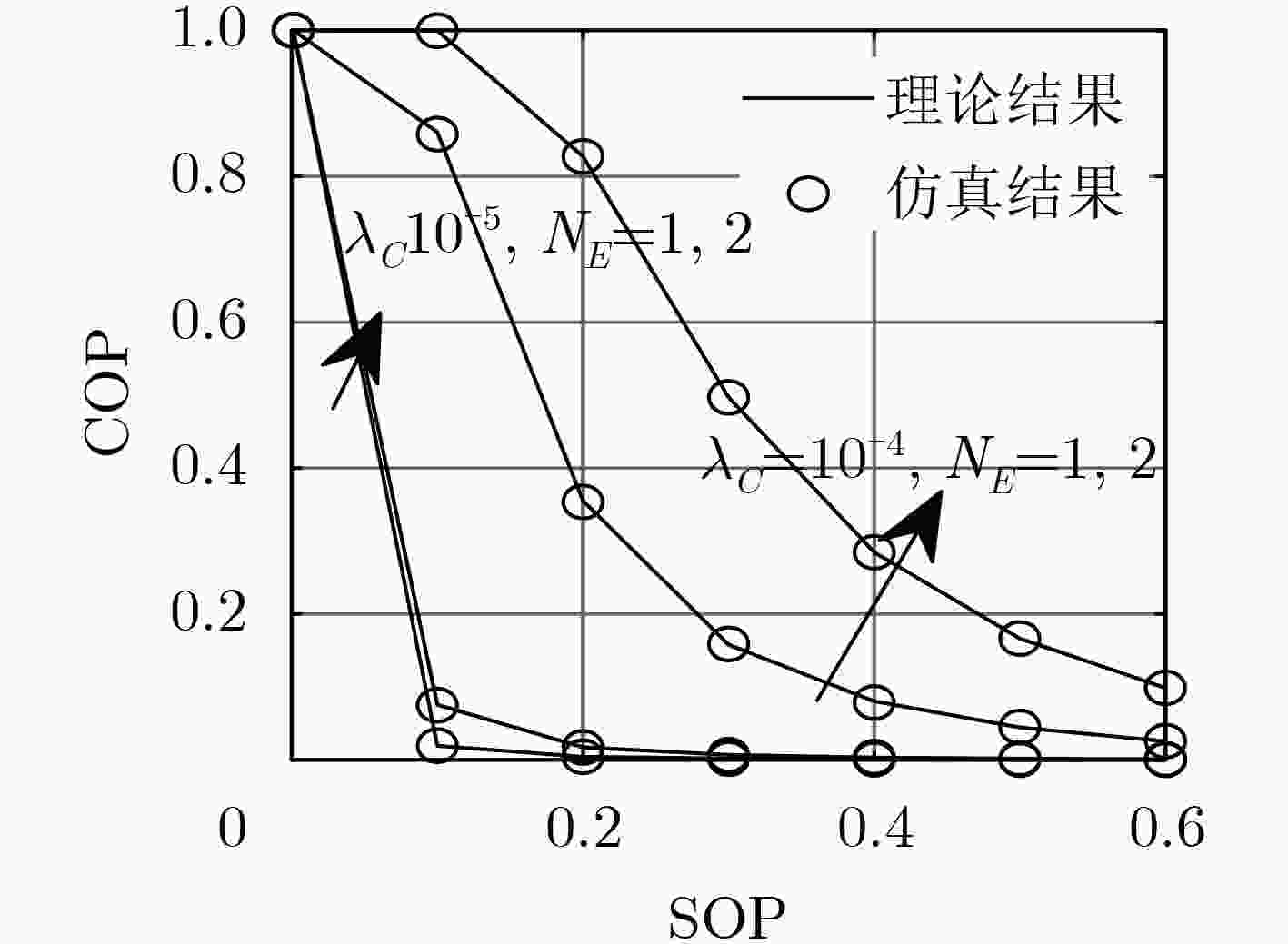
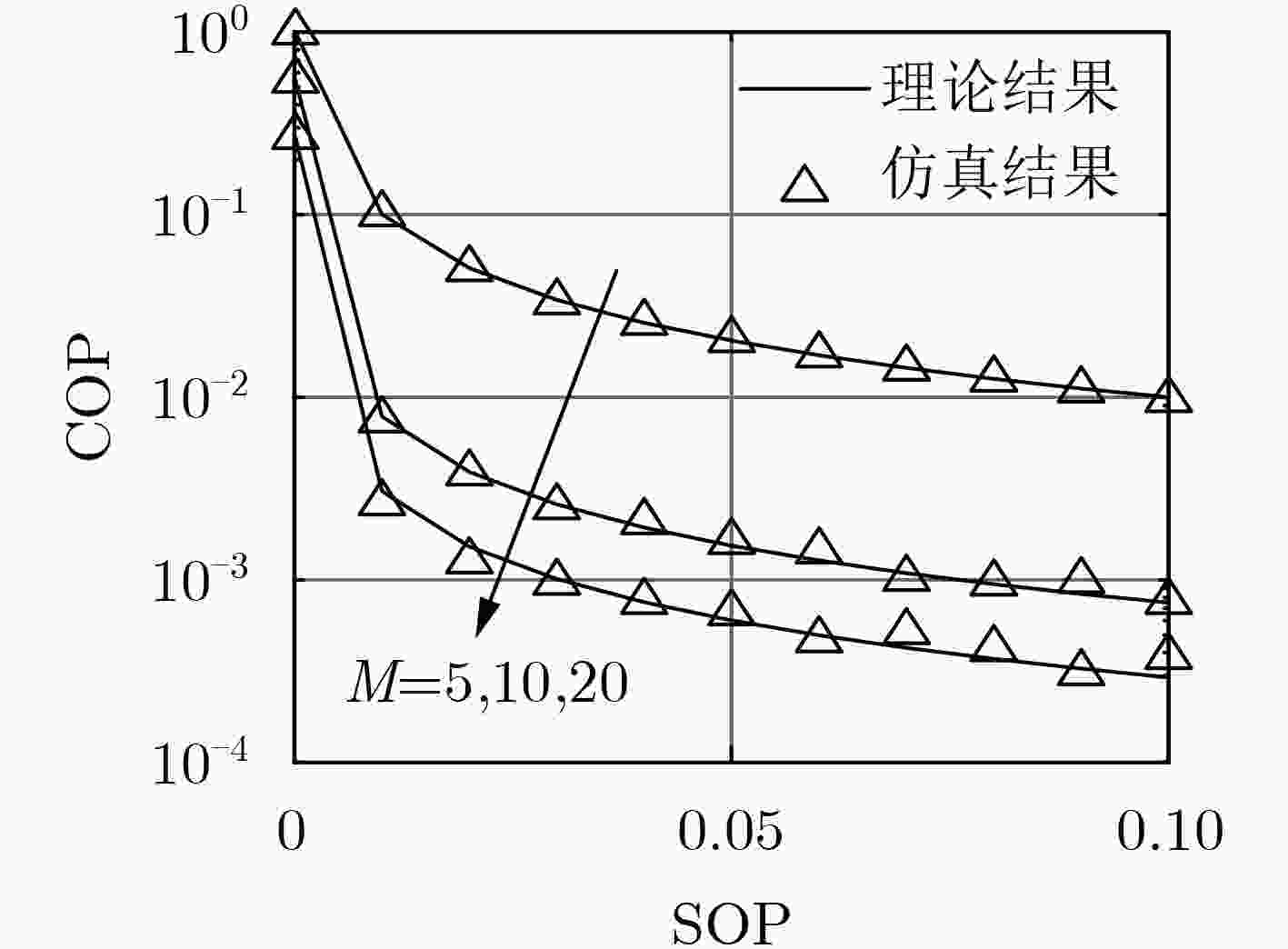
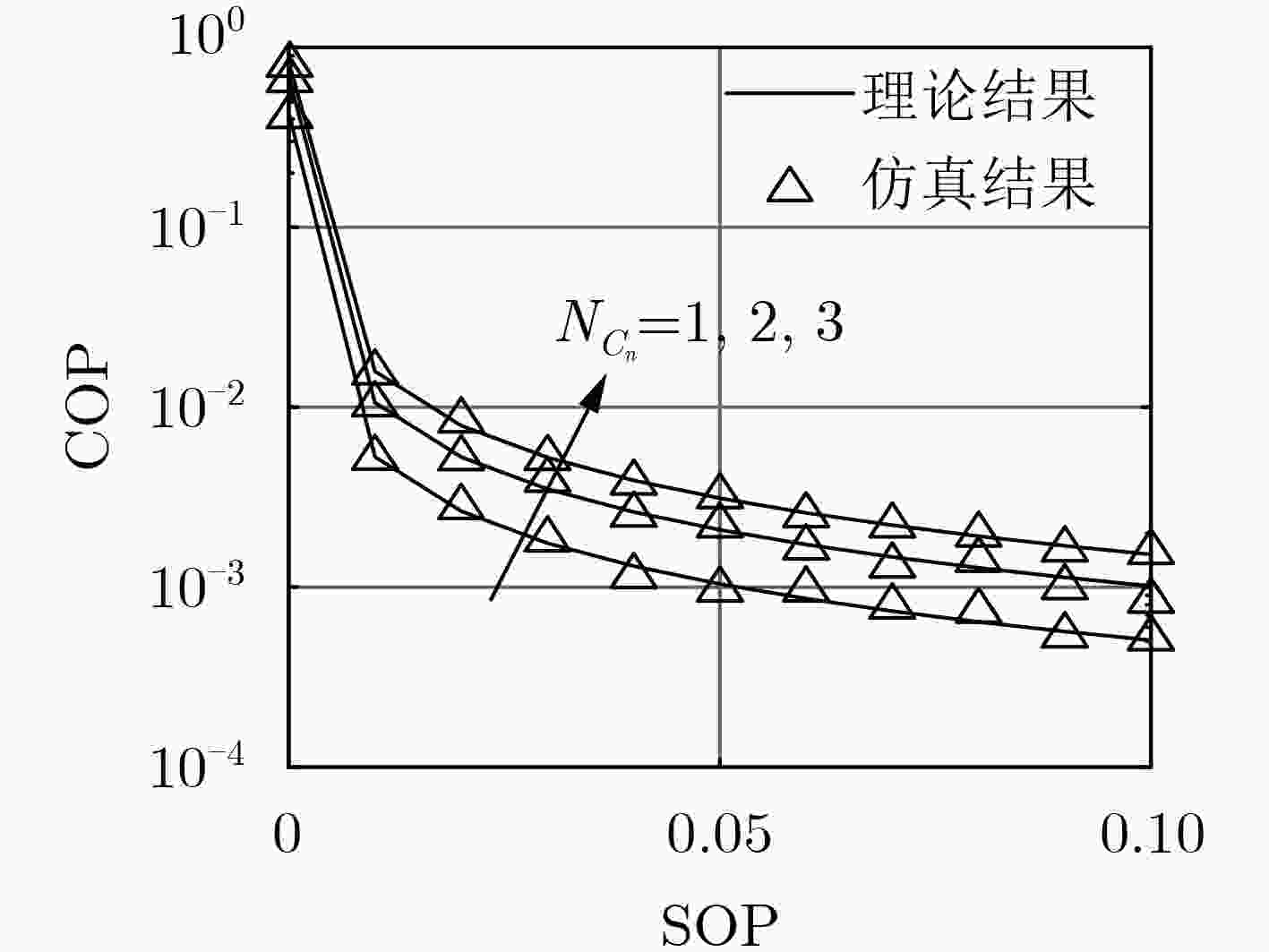
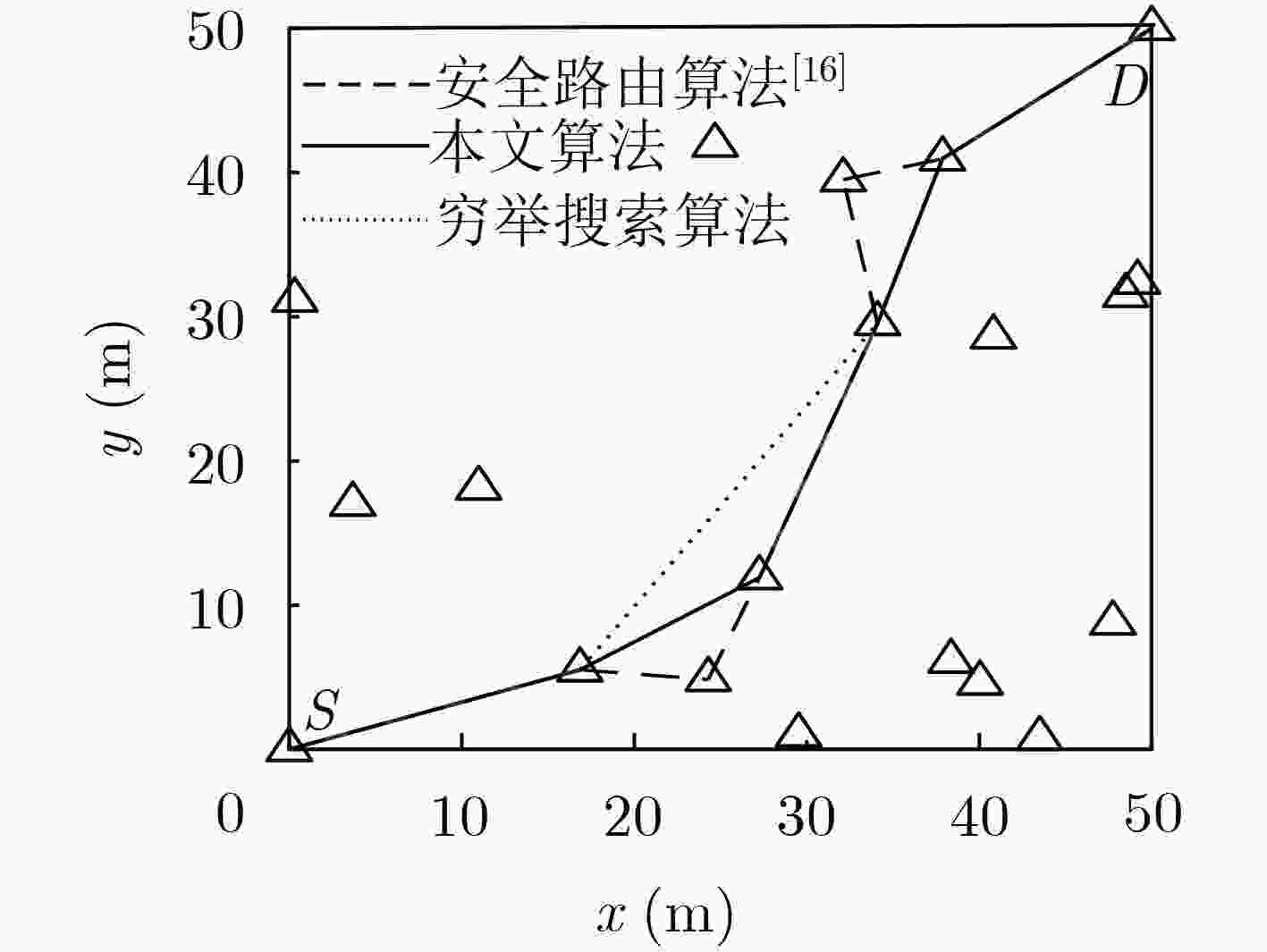
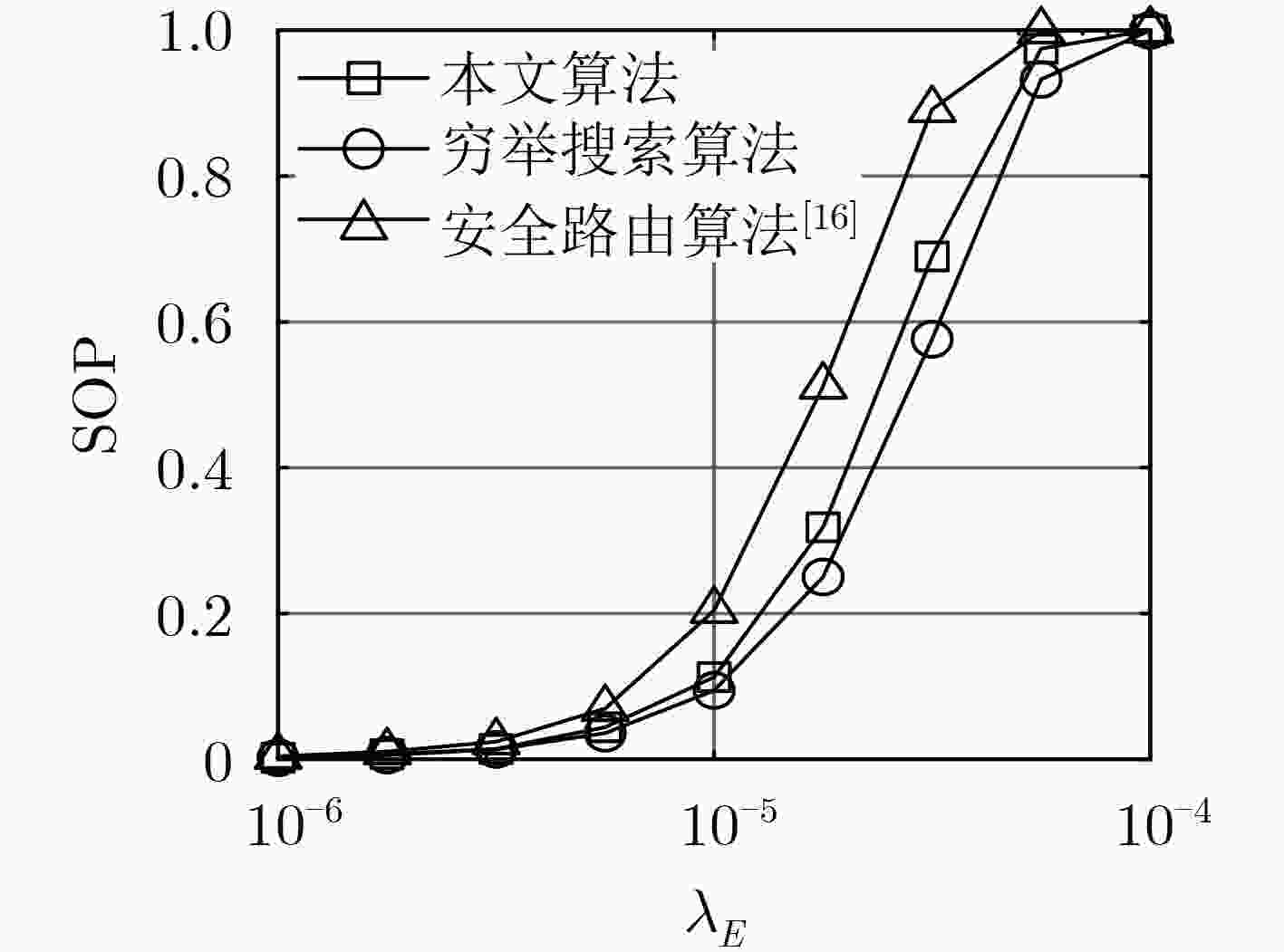
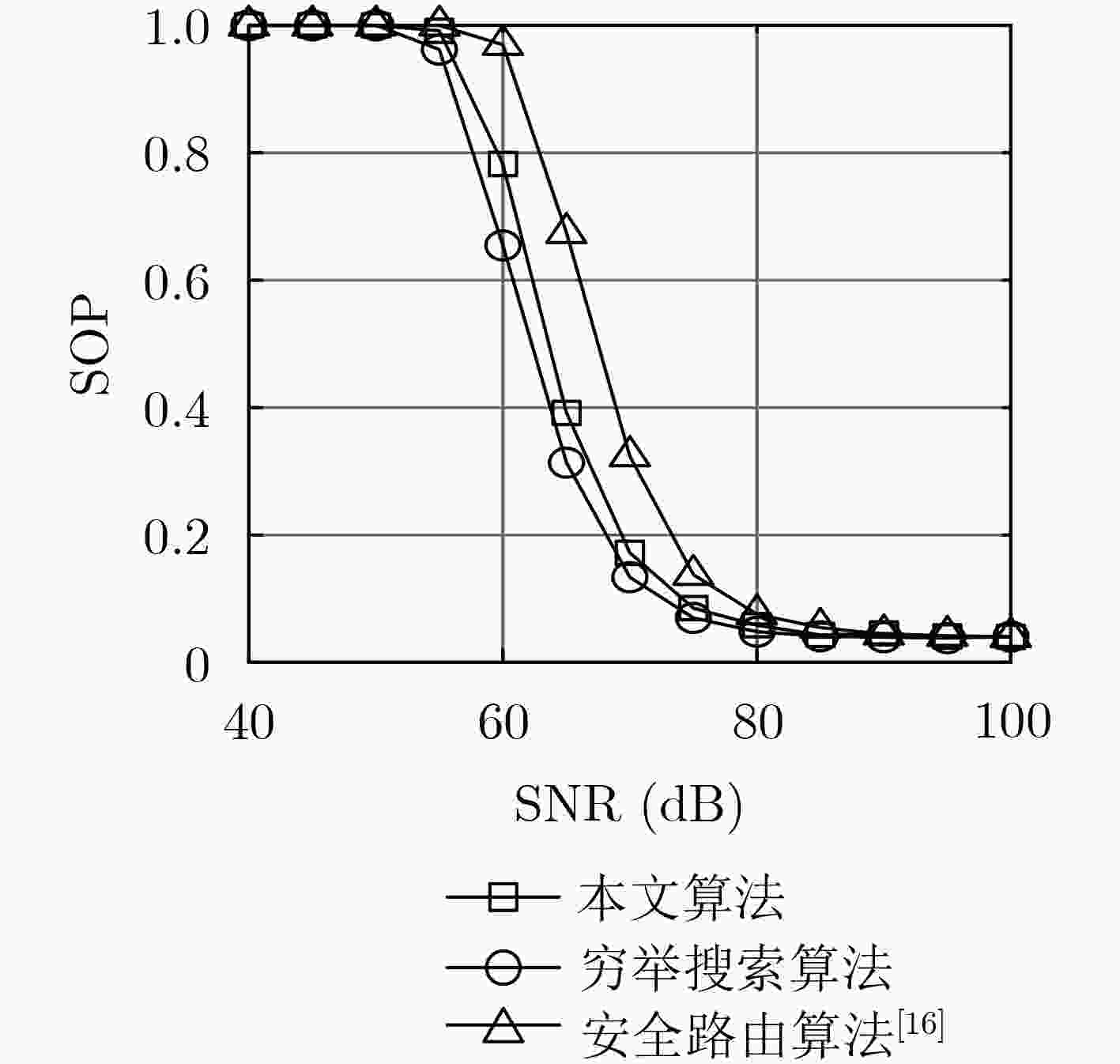
针对无线自组织网络在窃听环境中的安全传输问题,该文提出了一种无线多跳自组织网络的联合安全路由和功率优化算法。首先,在窃听者服从泊松簇过程(PCP)这一假设下推导得到了系统安全中断概率(SOP)和连接中断概率(COP)的表达式;然后以安全中断概率约束下的连接中断概率最小为准则,针对给定路径推导得到了源与各跳中继的最优传输功率,并进一步获得了源与目的节点间的最优路由。仿真结果表明,该文所提系统安全中断概率和连接中断概率的表达式与蒙特卡洛仿真结果相符,所提算法可获得与穷举搜索方法接近的安全性能,显著优于传统方法。
Abstract:A joint security routing and power optimization algorithm for wireless multi-hop Ad hoc network is proposed in an eavesdropping environment. Firstly, the Secrecy Outage Probability (SOP) and expressions of Connection Outage Probability (COP) are derived under the assumption that the distribution of the eavesdroppers follows the Poisson Cluster Process (PCP). Then, in view of minimizing COP with the constraint of SOP, the optimal transmission power of each hop is derived for any given path. Based on that, the optimal route from the source to the destination is obtained. The simulations on COP and SOP show that the derived theoretical results agree well with the Monte-Carlo simulations. It is also shown that the security performance of the proposed algorithm is close to that of exhaustive searching, and also outperforms the traditional method.
-
表 1 父节点位置未知情况下的功率优化和路由选择算法
输入:信噪比阈值${\gamma _c}$和${\gamma _e}$,安全中断概率约束$\zeta $; 输出:最优路由${\varPi ^ * }$,最优传输功率$P_{{T_k}}^ * $; (1) 计算${({\varphi _k})^{{{\rm{2}} / {(2 + \alpha )}}}}$,并对传输距离进行赋值; (2) 用Dijkstra算法获得最优路由${\varPi ^ * }$; (3) 利用式(20)对最优路由上的各跳计算相应的最优传输功率
$P_{{T_k}}^ * $;(4) 返回${\varPi ^ * }$, $P_{{T_k}}^ * $。 表 2 父节点位置已知情况下的功率优化和路由选择算法
输入:网络相关信息,信噪比阈值${\gamma _c}$和${\gamma _e}$,安全中断概率约束$\zeta $; 输出:最优路由${\varPi ^ * }$,最优传输功率$P_{{T_k}}^ * $; (1) 将网络中任意两合法节点间的距离赋值为${\varphi _k}$,将各合法节点
到各窃听者簇的距离用${w_n}$进行赋值;(2) 建立矩阵${{M}} \in {\mathbb{R}^{(M + 2) \times (M + 2)}}$,将矩阵${{M}}$的第$i$行第$j$列元
素用$\dfrac{ { {\gamma _c} } }{ { {\gamma _e} } }d_{i,j}^\alpha \displaystyle\sum\limits_{n = 1}^N {\dfrac{1}{ {d_{i,{C_n} }^\alpha } } }$进行赋值;(3) 初始时,路由节点集合${\cal{R} } = \{ {{S} }\}$; (4) 依据$k = \arg \min ({{M} }({{S} },{R_k}){\rm{ + } }{{M} }({R_k},{{D} }))$寻找${{S} } - {R_k} - {{D} }$
距离最小的中继${R_k}$,并将其加入集合${\cal{R}}$;(5) 依据${{M} }({{S} },{R_k}) \!=\! \mathop {\min }\limits_{ {R_n},{R_n} \in {\cal{M} } } ({{M} }({{S} },{R_k}),{{M} }({{S} },{R_n}) \!+\!{{M} }({R_n},$
${R_k})) $判断是否存在其他备选中继节点使得距离缩短,若存在
则将${R_n}$加入集合${\cal{R}}$,否则不变;(6) 与步骤(5)类似,依次判断整条链路中每一跳是否存在其他备
选中继节点使得该跳距离缩短,若存在则将该中继加入集合
${\cal{R}}$,否则不变;(7) 重复步骤(6),直到整条路由的距离不再减少时,遍历结束并
得到最优路由${\varPi ^ * }$;(8) 利用式(22)对最优路由上的每一跳计算相应的最优传输功
率$P_{{T_k}}^ * $;(9) 返回${\varPi ^ * }$, $P_{{T_k}}^ * $。 -
BURMESTER M and YASINSAC A. Security Issues in Ad-Hoc Networks[M]. New York: Springer, 2008: 89–105. 金梁, 宋昊天, 钟州, 等. 多用户大规模MIMO自适应安全传输策略[J]. 电子与信息学报, 2018, 40(6): 1468–1475. doi: 10.11999/JEIT170974JIN Liang, SONG Haotian, ZHONG Zhou, et al. Adaptive secure transmission strategy for multiuser massive MIMO[J]. Journal of Electronics &Information Technology, 2018, 40(6): 1468–1475. doi: 10.11999/JEIT170974 YOU Li, WANG Jiaheng, WANG Wenjin, et al. Secure multicast transmission for massive MIMO with statistical channel state information[J]. IEEE Signal Processing Letters, 2019, 26(6): 803–807. doi: 10.1109/LSP.2019.2900940 LUN Dong, ZHU Han, PETROPULU A P, et al. Improving wireless physical layer security via cooperating relays[J]. IEEE Transactions on Signal Processing, 2010, 58(3): 1875–1888. doi: 10.1109/TSP.2009.2038412 CHRAITI M, GHRAYEB A, ASSI C, et al. On the Achievable secrecy diversity of cooperative networks with untrusted relays[J]. IEEE Transactions on Communication, 2018, 66(1): 39–53. doi: 10.1109/TCOMM.2017.2755654 YANG Zilong and DONG Min. Low-complexity coordinated relay beamforming design for multi-cluster relay interference networks[J]. IEEE Transactions on Wireless Communications, 2019, 18(4): 2215–2228. doi: 10.1109/TWC.2019.2901477 SHENG Zhichao, TUAN H D, DUONG T Q, et al. Beamforming optimization for physical layer security in MISO wireless networks[J]. IEEE Transactions on Signal Processing, 2018, 66(14): 3710–3723. doi: 10.1109/TSP.2018.2835406 洪涛, 张更新. 人工噪声辅助的物理层安全信号峰均功率比减低算法[J]. 电子与信息学报, 2018, 40(6): 1426–1432. doi: 10.11999/JEIT170739HONG Tao and ZHANG Gengxin. Peak-to-average power ratio reduction algorithm of artificial-noise-aided secure signal[J]. Journal of Electronics &Information Technology, 2018, 40(6): 1426–1432. doi: 10.11999/JEIT170739 ZHANG Wei, CHEN Jian, KUO Yonghong, et al. Artificial-noise-aided optimal beamforming in layered physical layer security[J]. IEEE Communications Letters, 2019, 23(1): 72–75. doi: 10.1109/LCOMM.2018.2881182 SAAD W, ZHOU Xiangyun, MAHAM B, et al. Tree formation with physical layer security considerations in wireless multi-hop networks[J]. IEEE Transactions on Wireless Communications, 2012, 11(11): 3980–3991. doi: 10.1109/TWC.2012.091812.111923 LEE J H. Optimal power allocation for physical layer security in multi-hop DF relay networks[J]. IEEE Transactions on Wireless Communications, 2016, 15(1): 28–38. doi: 10.1109/TWC.2015.2466091 XU Yang, LIU Jia, TAKAHASHI O, et al. SOQR: Secure optimal QoS routing in wireless ad hoc networks[C]. 2017 IEEE Wireless Communications and Networking Conference, San Francisco, USA, 2017: 1–6. doi: 10.1109/WCNC.2017.7925687. YAO Jianping and LIU Yuan. Secrecy rate maximization with outage constraint in multihop relaying networks[J]. IEEE Communications Letters, 2018, 22(2): 304–307. doi: 10.1109/LCOMM.2017.2768513 WANG Huiming, ZHANG Yan, NG D W K, et al. Secure routing with power optimization for Ad-Hoc networks[J]. IEEE Transactions on Communications, 2018, 66(10): 4666–4679. doi: 10.1109/TCOMM.2018.2835478 SAHA C, AFSHANG M, and DHILLON H S. Poisson cluster process: Bridging the gap between PPP and 3GPP HetNet models[C]. 2017 Information Theory and Applications Workshop, San Diego, USA, 2017: 1–9. doi: 10.1109/ITA.2017.8023448. CHEN Gaojie, COON J P, and TAJBAKHSH S E. Secure routing for multihop ad hoc networks with inhomogeneous eavesdropper clusters[J]. IEEE Transactions on Vehicular Technology, 2018, 67(11): 10660–10670. doi: 10.1109/TVT.2018.2866977 STOYAN D, CHIU S N, KENDALL W S, et al. Stochastic Geometry and Its Applications[M]. 3rd ed. Chichester: John Wiley & Sons, 2013: 171–175. -





 下载:
下载:

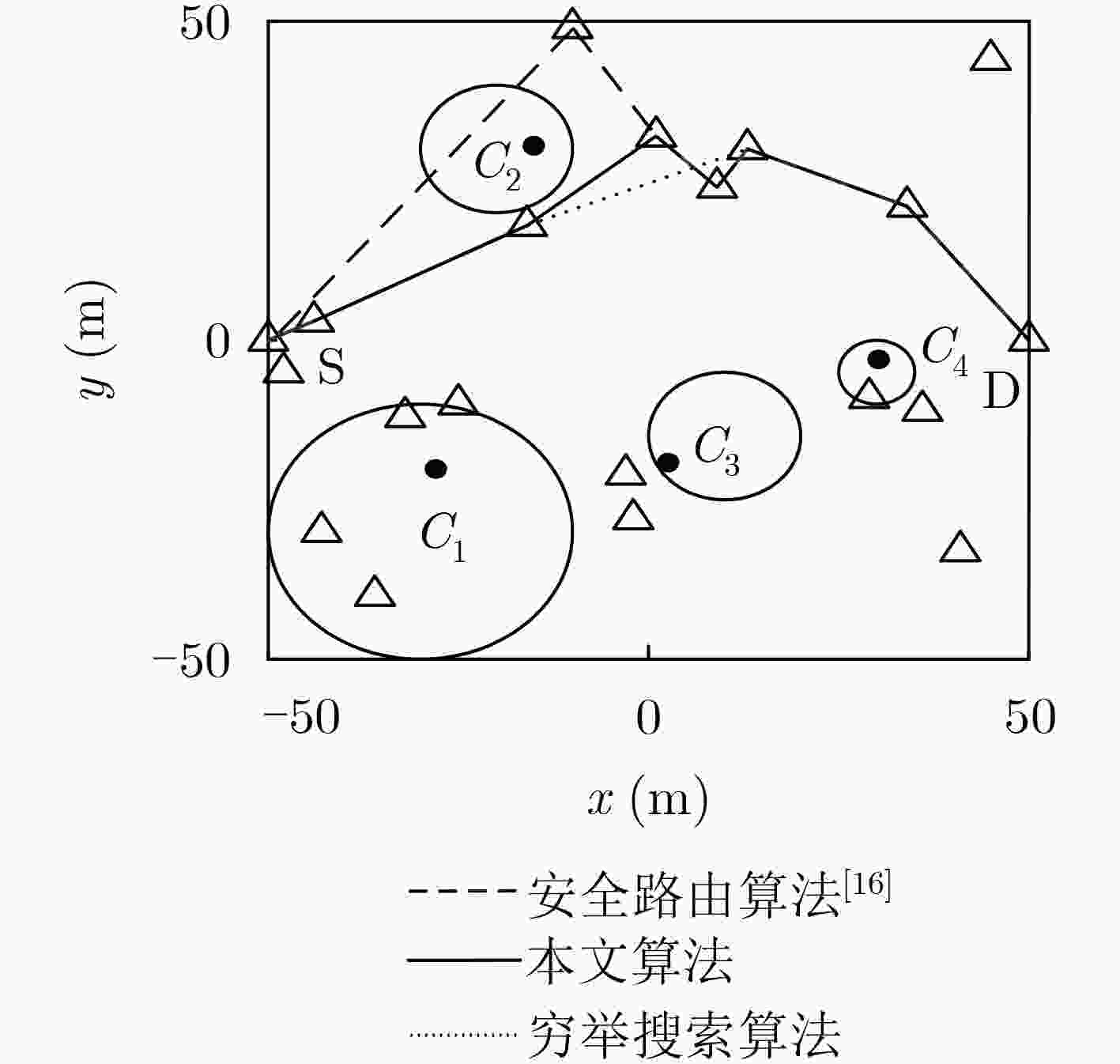
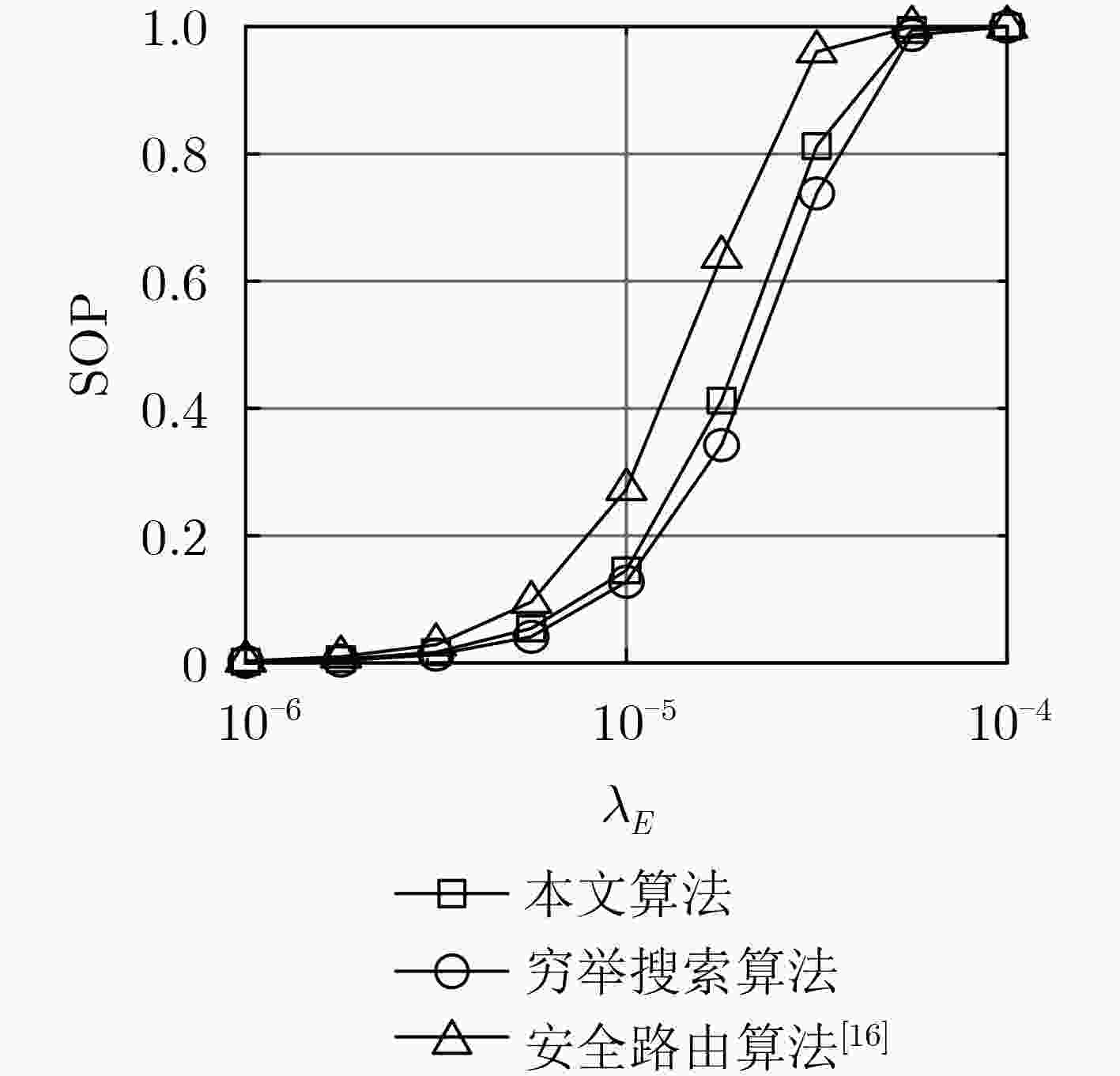

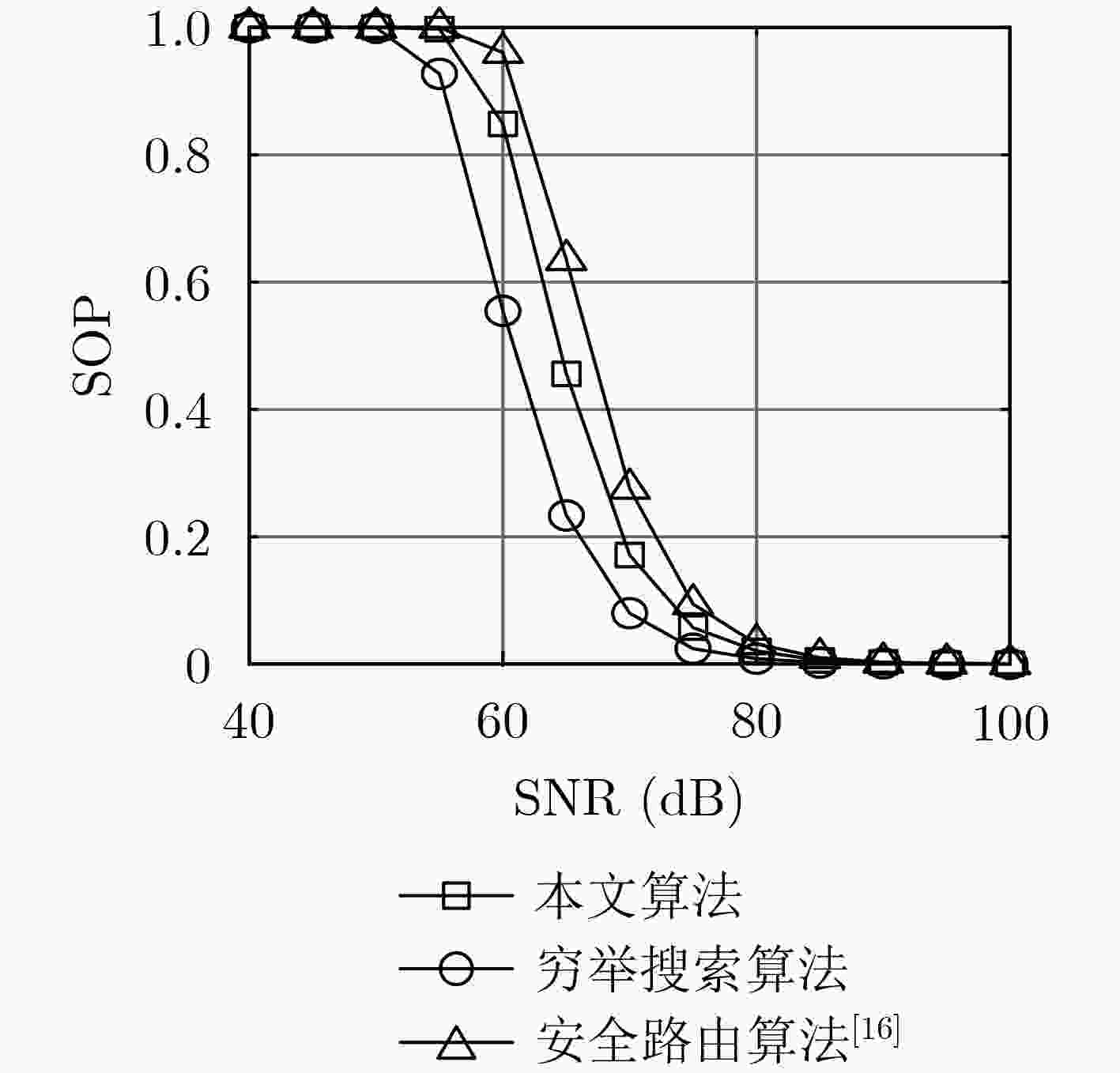


 下载:
下载:
