Optical Image Encryption Based on Spiral Phase Transform and Generalized Fibonacci Chaos
-
摘要:
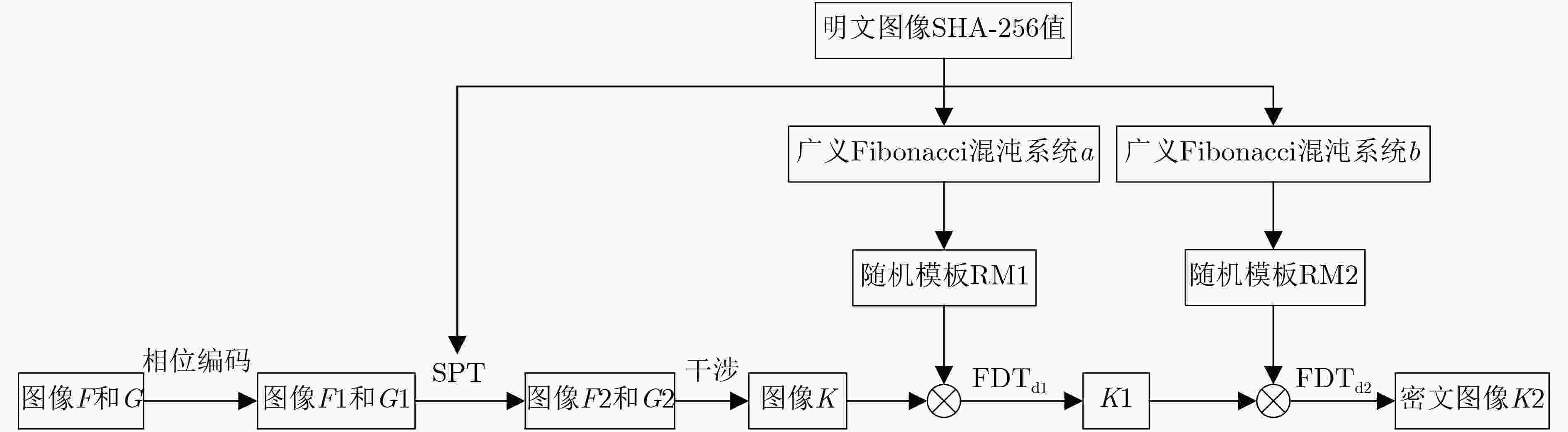
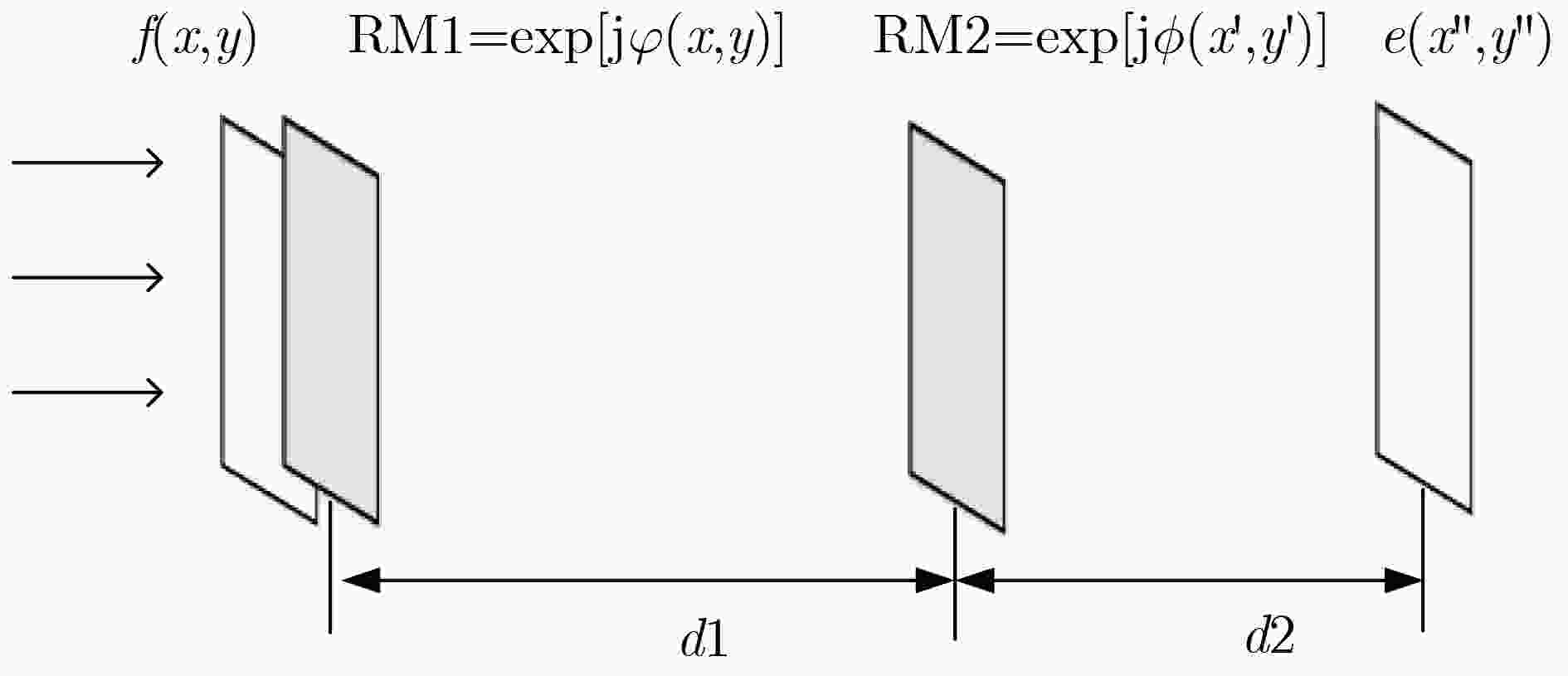
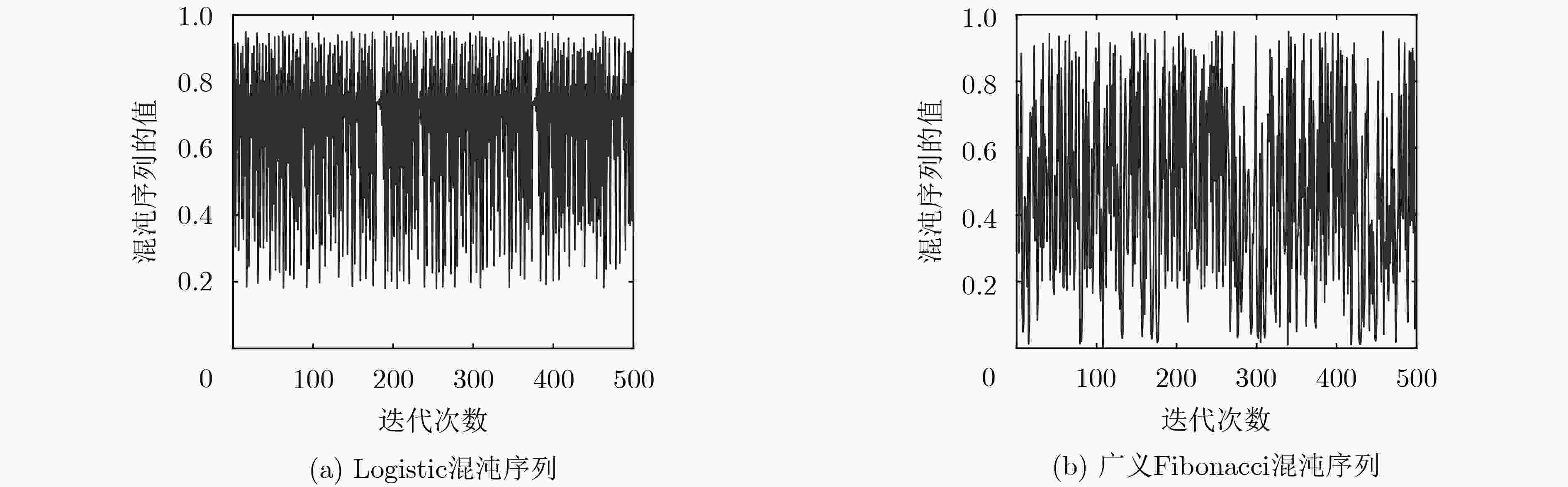
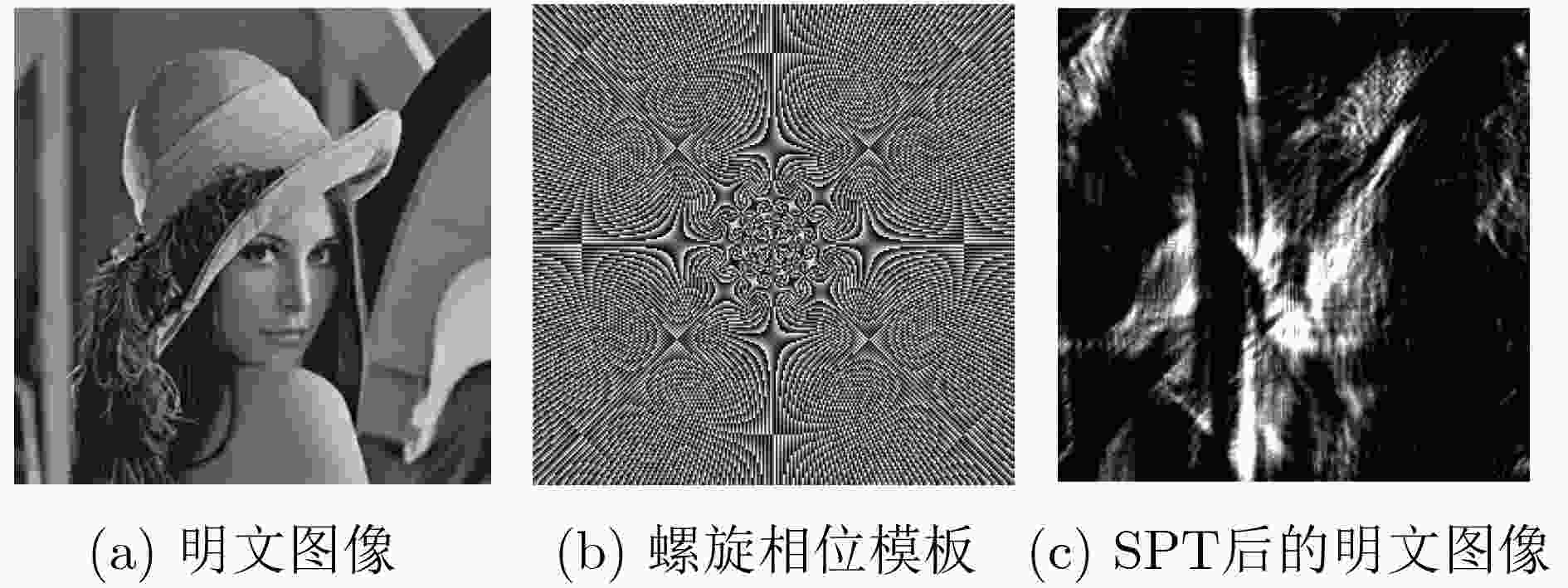
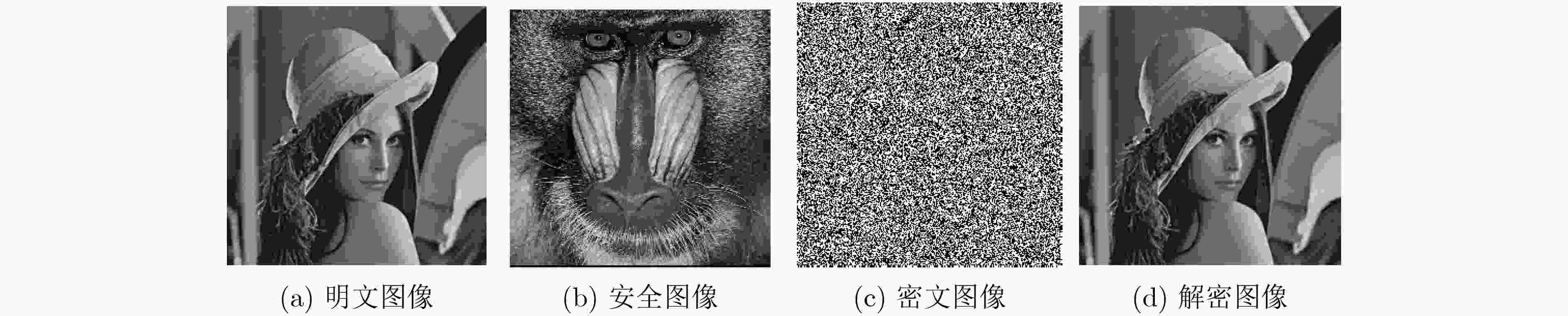
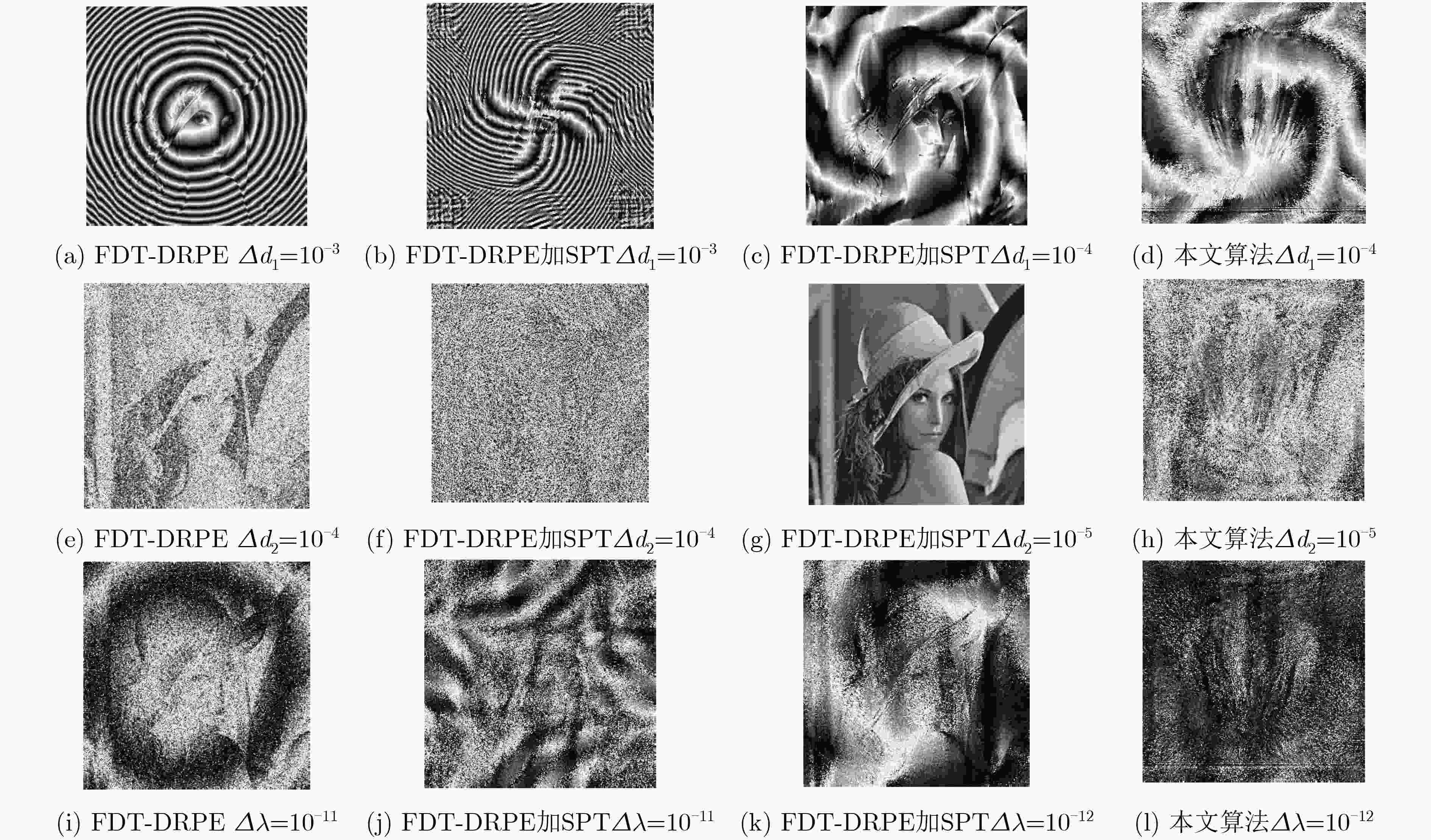
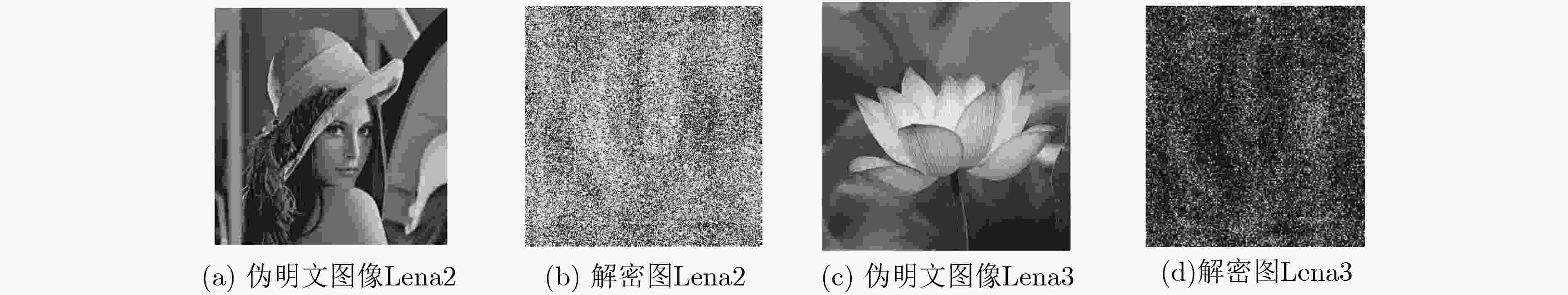
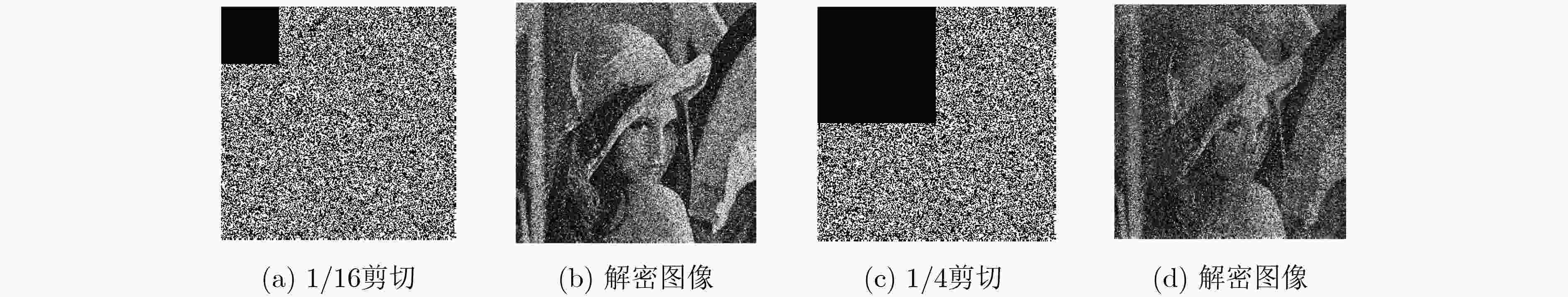
为了解决光学加密技术中混沌序列分布不均匀,抗选择明文攻击能力弱以及菲涅尔域双随机相位编码系统对第1个衍射距离不敏感等问题,该文基于螺旋相位变换和新型广义Fibonacci混沌系统,提出一种光学图像加密算法。在菲涅尔域的双随机相位编码中对明文图像进行相位编码和螺旋相位变换,克服系统对第1块随机模板和衍射距离不敏感的缺陷,提高光学密钥敏感性。添加安全图像与明文进行加权干涉,进一步提高光学密钥敏感性和密钥维度。构造可产生均匀混沌序列的广义Fibonacci混沌系统生成随机模板,解决密钥体积过大分发传递困难问题,克服Logistic混沌分布不均匀的缺点,提高密钥传输效率及密钥敏感性。同时用明文哈希值SHA-256生成混沌初值和螺旋相位变换参数,使得密钥流随明文自适应变化,达到“一次一密”的效果,提高算法抵抗选择明文攻击能力和明文敏感性,雪崩效应更强。实验对比表明该算法明文及密钥敏感性高,密钥空间大,鲁棒性好,能有效抵御各种攻击,是一种高安全性的光学图像加密方法。
-
关键词:
- 光学图像加密 /
- 广义Fibonacci混沌 /
- 螺旋相位变换 /
- 菲涅尔变换 /
- 一次一密
Abstract:In this paper, an optical image encryption algorithm based on spiral phase transform and new generalized fibonacci chaotic system is proposed to solve the problems of the Fresnel domain double random phase coding system is insensitive to the first diffraction distance, uneven distribution of chaotic sequences and weak resistance to choice plaintext attack. The plaintext image is encoded as phase information and spiral phase transformed to overcame the insensitivity of the first random phase template and diffraction distance of the Fresnel diffraction transform-double random phase encoding system. The sensitivity of the optical keys is improved. The weighted interference between secure image and plaintext image is added to further increase the sensitivity of the optical keys and dimension of key . A generalized Fibonacci chaotic system, which could generate uniform sequences, is constructed to generate phase templates to overcame uneven distribution of logistic chaos and improve the efficiency of key transmission and the sensitivity of the keys. The chaotic initial value and parameters of spiral phase transform are related to SHA-256. It makes the keys change with the plaintext and achieved the effect of “one encryption at a time”, and enhanced the sensitivity of the plaintext and the ability of the resistance to choice plaintext attack and avalanche effect.Experimental comparison shows that this method can effectively increase the plaintext sensitivity and key sensitivity. This method’ robustness and the key space are sufficiently secure. It is a high security optical image encryption method.
-
表 1 NPCR和UACI值对比
表 2 性能对比结果
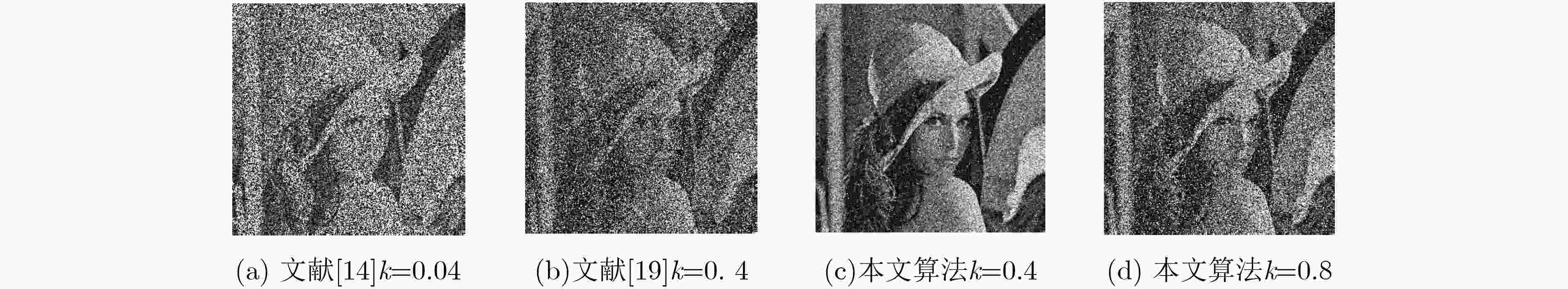
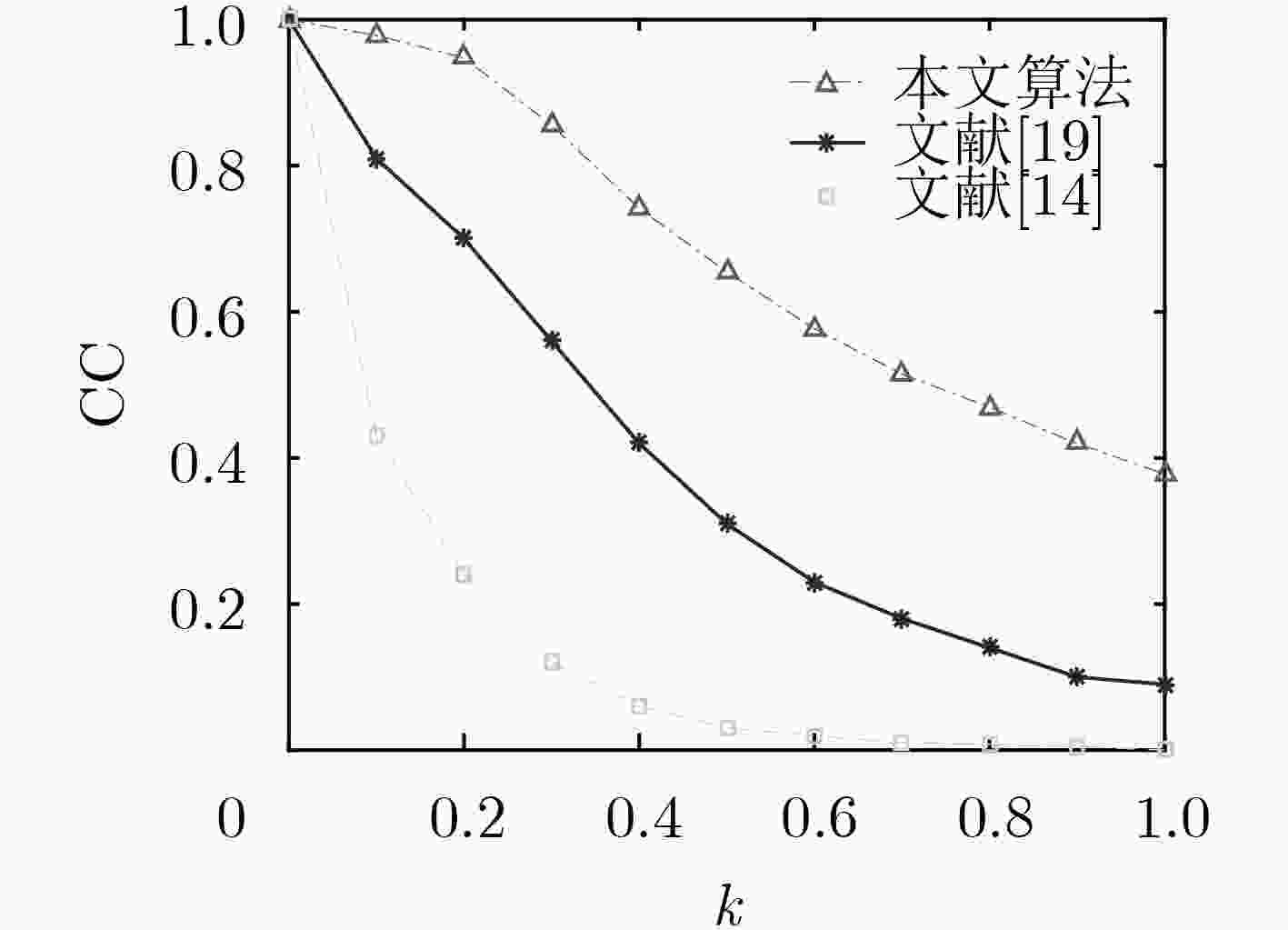
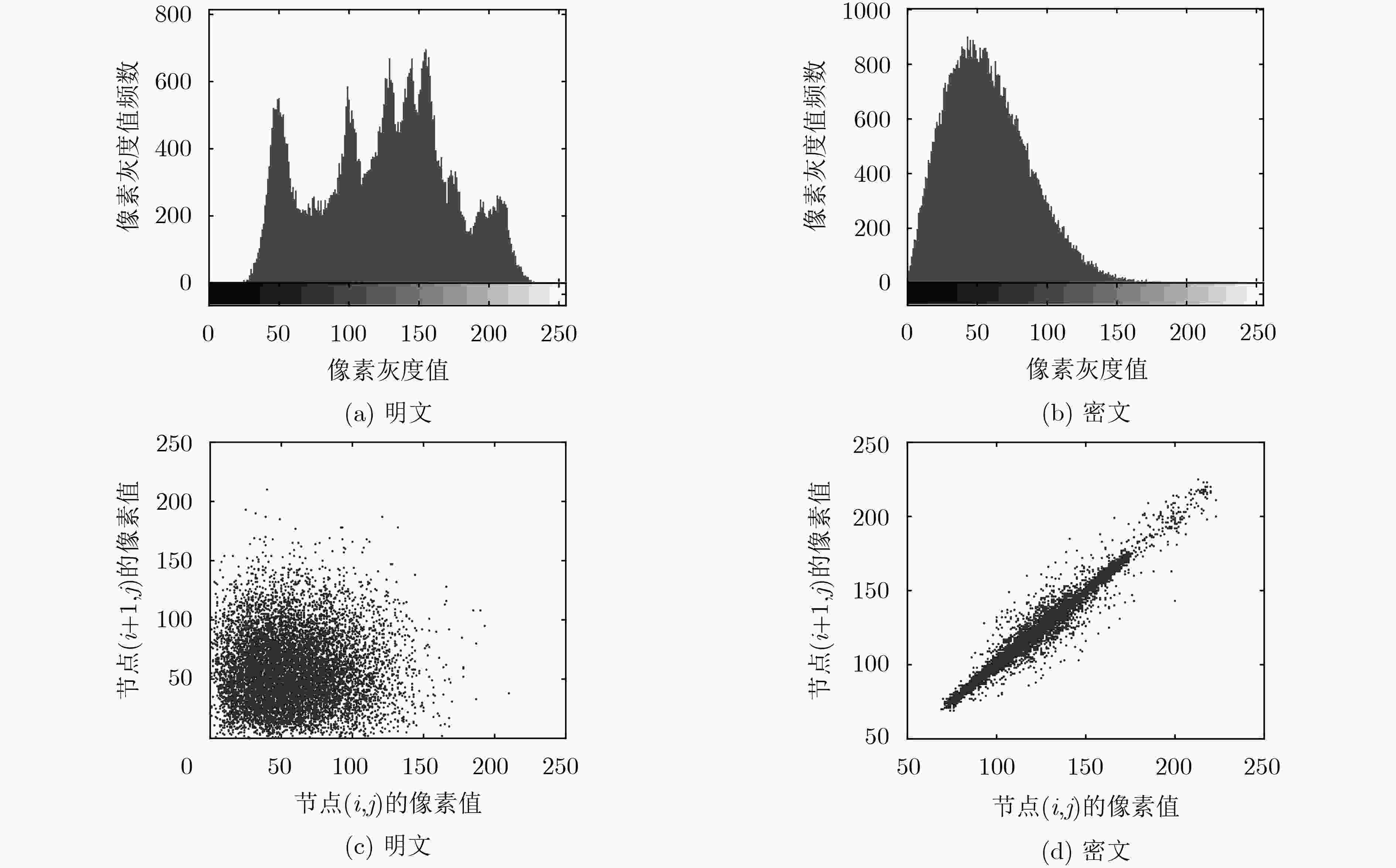
比较项 文献[19] 文献[14] 本文算法 相邻像素相关性 水平 0.0001 0.0334 -0.0036 垂直 0.0014 0.0248 0.0004 对角 0.0014 0.0288 -0.0082 光学密钥敏感性 ${d_1}$ ${10^{{\rm{ - }}3}}$ ${10^{{\rm{ - 4}}}}$ ${10^{{\rm{ - 4}}}}$ ${d_2}$ ${10^{{\rm{ - 4}}}}$ ${10^{{\rm{ - 5}}}}$ ${10^{{\rm{ - 5}}}}$ $\lambda $ ${10^{{\rm{ - 11}}}}$ ${10^{{\rm{ - 9}}}}$ ${10^{{\rm{ - 12}}}}$ 抵御选择明文攻击 否 是 是 是否依赖于明文 否 是 是 密钥空间 ${10^{{\rm{114}}}}$ ${10^{203}}$ ${10^{300}}$ -
WANG Qu, XIONG Deping, ALFALOU A, et al. Optical image encryption method based on incoherent imaging and polarized light encoding[J]. Optics Communications, 2018, 415: 56–63. doi: 10.1016/j.optcom.2018.01.018 LI Xiaowei, ZHAO Min, XING Yan, et al. Designing optical 3D images encryption and reconstruction using monospectral synthetic aperture integral imaging[J]. Optics Express, 2018, 26(9): 11084–11099. doi: 10.1364/OE.26.011084 LI Chengqing, ZHANG Yun, and XIE E Y. When an attacker meets a cipher-image in 2018: A year in review[J]. arXiv: 1903.11764, 2019. REFREGIER P and JAVIDI B. Optical image encryption based on input plane and Fourier plane random encoding[J]. Optics Letters, 1995, 20(7): 767–769. doi: 10.1364/OL.20.000767 SITU G, PEDRINI G, and OSTEN W. Strategy for cryptanalysis of optical encryption in the Fresnel domain[J]. Applied Optics, 2010, 49(3): 457–462. doi: 10.1364/AO.49.000457 PENG Xiang, ZHANG Peng, WEI Hengzheng, et al. Known-plaintext attack on optical encryption based on double random phase keys[J]. Optics Letters, 2006, 31(8): 1044–1046. doi: 10.1364/OL.31.001044 彭翔, 张鹏, 位恒政, 等. 双随机相位加密系统的已知明文攻击[J]. 物理学报, 2006, 55(3): 1130–1136. doi: 10.3321/j.issn:1000-3290.2006.03.021PENG Xiang, ZHANG Peng, WEI Hengzheng, et al. Known-plaintext attack on double phase encoding encryption technique[J]. Acta Physica Sinica, 2006, 55(3): 1130–1136. doi: 10.3321/j.issn:1000-3290.2006.03.021 LIU Xiaoli, WU Jiachen, HE Wenqi, et al. Vulnerability to ciphertext-only attack of optical encryption scheme based on double random phase encoding[J]. Optics Express, 2015, 23(15): 18955–18968. doi: 10.1364/OE.23.018955 QIN Wan and PENG Xiang. Asymmetric cryptosystem based on phase-truncated Fourier transforms[J]. Optics Letters, 2010, 35(2): 118–120. doi: 10.1364/OL.35.000118 WANG Yong, QUAN Chenggen, and TAY C J. Optical color image encryption without information disclosure using phase-truncated Fresnel transform and a random amplitude mask[J]. Optics Communications, 2015, 344: 147–155. doi: 10.1016/j.optcom.2015.01.045 WANG Yong, QUAN Chenggen, and TAY C J. Improved method of attack on an asymmetric cryptosystem based on phase-truncated Fourier transform[J]. Applied Optics, 2015, 54(22): 6874–6881. doi: 10.1364/AO.54.006874 RAJPUT S K and NISHCHAL N K. Known-plaintext attack-based optical cryptosystem using phase-truncated Fresnel transform[J]. Applied Optics, 2013, 52(4): 871–878. doi: 10.1364/AO.52.000871 WANG Yong, QUAN Chenggen, and TAY C J. Asymmetric optical image encryption based on an improved amplitude-phase retrieval algorithm[J]. Optics and Lasers in Engineering, 2016, 78: 8–16. doi: 10.1016/j.optlaseng.2015.09.008 刘禹佳, 徐熙平, 徐嘉鸿, 等. 基于矢量运算和副像相位掩模的遥感图像加密技术[J]. 光子学报, 2019, 48(2): 0210002. doi: 10.3788/gzxb20194802.0210002LIU Yujia, XU Xiping, XU Jiahong, et al. Remote sensing image encryption using vector operations and secondary image phase masks[J]. Acta Photonica Sinica, 2019, 48(2): 0210002. doi: 10.3788/gzxb20194802.0210002 常杰. 基于分数傅里叶变换的双图像光学加密技术研究[D]. [硕士论文], 哈尔滨工程大学, 2013.CHANG Jei. Research on double image optical encryption in the fractional Fourier-domain[D]. [Master dissertation], Harbin Engineering University, 2013. 朱薇, 杨庚, 陈蕾, 等. 基于小波变换和改进双随机相位编码的多图像加密算法[J]. 南京邮电大学学报: 自然科学版, 2014, 34(5): 87–92.ZHU Wei, YANG Geng, CHEN Lei, et al. Multiple-image encryption based on wavelet transform and improved double random phase encoding[J]. Journal of Nanjing University of Posts and Telecommunications:Natural Science, 2014, 34(5): 87–92. 孙杰. 基于多混沌系统的双图像光学加密算法[J]. 光学技术, 2017, 43(3): 279–283.SUN Jie. Double optical images encryption method based on chaotic systems[J]. Optical Technique, 2017, 43(3): 279–283. 张博, 龙慧, 江沸菠. 基于相干叠加与模均等矢量分解的光学图像加密算法[J]. 电子与信息学报, 2018, 40(2): 438–446. doi: 10.11999/JEIT170489ZHANG Bo, LONG Hui, and JIANG Feibo. Optical image encryption algorithm based on coherent superposition and equal modulus vector decomposition[J]. Journal of Electronics &Information Technology, 2018, 40(2): 438–446. doi: 10.11999/JEIT170489 朱薇, 杨庚, 陈蕾, 等. 基于混沌的改进双随机相位编码图像加密算法[J]. 光学学报, 2014, 34(6): 0607001. doi: 10.3788/AOS201434.0607001ZHU Wei, YANG Geng, CHEN Lei, et al. An improved image encryption algorithm based on double random phase encoding and chaos[J]. Acta Optica Sinica, 2014, 34(6): 0607001. doi: 10.3788/AOS201434.0607001 陈志刚, 梁涤青, 邓小鸿, 等. Logistic混沌映射性能分析与改进[J]. 电子与信息学报, 2016, 38(6): 1547–1551.CHEN Zhigang, LIANG Diqing, DENG Xiaohong, et al. Performance analysis and improvement of Logistic chaotic mapping[J]. Journal of Electronics &Information Technology, 2016, 38(6): 1547–1551. LI Chengqing, LIN Dongdong, LÜ Jinhu, et al. Cryptanalyzing an image encryption algorithm based on autoblocking and electrocardiography[J]. IEEE MultiMedia, 2018, 25(4): 46–56. doi: 10.1109/MMUL.2018.2873472 HU Xubo, YANG Xiangbo, and LIU Songhao. Optical transmission through generalized third-order Fibonacci multilayers[J]. Modern Physics Letters B, 2014, 28(16): 1450129. doi: 10.1142/S0217984914501292 SINGH R K, KUMAR B, SHAW D K, et al. Level by level image compression-encryption algorithm based on quantum chaos map[J]. Journal of King Saud University - Computer and Information Sciences, 2018, S1319157817304123. doi: 10.1016/j.jksuci.2018.05.012 LARKIN K G, BONE D J, and OLDFIELD M A. Natural demodulation of two-dimensional fringe patterns. I. General background of the spiral phase quadrature transform[J]. Journal of the Optical Society of America A, 2001, 18(8): 1862–1870. doi: 10.1364/JOSAA.18.001862 LU Yuzhen, LI R, and LU Renfu. Fast demodulation of pattern images by spiral phase transform in structured-illumination reflectance imaging for detection of bruises in apples[J]. Computers and Electronics in Agriculture, 2016, 127: 652–658. doi: 10.1016/j.compag.2016.07.012 ZHANG Yushu and XIAO Di. Double optical image encryption using discrete Chirikov standard map and chaos-based fractional random transform[J]. Optics and Lasers in Engineering, 2013, 51(4): 472–480. doi: 10.1016/j.optlaseng.2012.11.001 -





 下载:
下载:


 下载:
下载:
