|
LIU Yiliang, CHEN H H, and WANG Liangmin. Physical layer security for next generation wireless networks: Theories, technologies, and challenges[J]. IEEE Communications Surveys & Tutorials, 2017, 19(1): 347–376. doi: 10.1109/COMST.2016.2598968
|
|
YANG Enhui and WU Xinwen. Information-theoretically secure key generation and management[C]. 2017 IEEE International Symposium on Information Theory, Aachen, Germany, 2017: 1529–1533.
|
|
MAURER U M. Secret key agreement by public discussion from common information[J]. IEEE Transactions on Information Theory, 1993, 39(3): 733–742. doi: 10.1109/18.256484
|
|
ZHU Xiaojun, XU Fengyuan, NOVAK E, et al. Using wireless link dynamics to extract a secret key in vehicular scenarios[J]. IEEE Transactions on Mobile Computing, 2017, 16(7): 2065–2078. doi: 10.1109/TMC.2016.2557784
|
|
HASSANA A A, STARKB W E, HERSHEYC J E, et al. Cryptographic key agreement for mobile radio[J]. Digital Signal Processing, 1996, 6(4): 207–212. doi: 10.1006/dspr.1996.0023
|
|
KITAURA A, SUMI T, TACHIBANA K, et al. A Scheme of private key agreement based on delay profiles in uwb systems[C]. 2006 IEEE Sarnoff Symposium, Princeton, USA, 2006: 1–6.
|
|
MADISEH M G, NEVILLE S W, and MCGUIRE M L. Applying beamforming to address temporal correlation in wireless channel characterization-based secret key generation[J]. IEEE Transactions on Information Forensics and Security, 2012, 7(4): 1278–1287. doi: 10.1109/TIFS.2012.2195176
|
|
HUANG Pengfei and WANG Xudong. Fast secret key generation in static wireless networks: A virtual channel approach[C]. 2013 Proceedings IEEE INFOCOM, Turin, Italy, 2013: 2292–2300.
|
|
CHEN Dajiang, QIN Zhen, MAO Xufei, et al. SmokeGrenade: An efficient key generation protocol with artificial interference[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(11): 1731–1745. doi: 10.1109/TIFS.2013.2278834
|
|
GOLLAKOTA S and KATABI D. Physical layer wireless security made fast and channel independent[C]. 2011 Proceedings IEEE INFOCOM, Shanghai, China, 2011: 1125–1133.
|
|
LI Guyue, HU Aiqun, ZHANG Junqing, et al. Security analysis of a novel artificial randomness approach for fast key generation[C]. 2017 IEEE Global Communications Conference, Singapore, 2017: 1–6.
|
|
LOU Yangming, JIN Liang, ZHONG Zhou, et al. Secret key generation scheme based on MIMO received signal spaces[J]. Scientia Sinica Informationis, 2017, 47(3): 362–373. doi: 10.1360/N112016-00001
|
|
ZHANG Junqing, DUONG T Q, MARSHALL A, et al. Key generation from wireless channels: A review[J]. IEEE Access, 2016, 4: 614–626. doi: 10.1109/ACCESS.2016.2521718
|
|
COVER T and THOMAS J. Elements of information theory[M]. Boston: John Wiley & Sons, 2012: 33–34.
|
|
PASOLINI G and DARDARI D. Secret key generation in correlated multi-dimensional Gaussian channels[C]. 2014 IEEE International Conference on Communications, Sydney, Australia, 2014: 2171–2177.
|
|
YE Chunxuan, REZNIK A, and SHAH Y. Extracting secrecy from jointly Gaussian random variables[C]. 2006 IEEE International Symposium on Information Theory, Seattle, USA, 2006: 2593–2597.
|
|
ROE G. Quantizing for minimum distortion (Corresp.)[J]. IEEE Transactions on Information Theory, 1964, 10(4): 384–385. doi: 10.1109/TIT.1964.1053693
|
|
ZHAN Furui, YAO Nianmin, GAO Zhenguo, et al. Efficient key generation leveraging wireless channel reciprocity for MANETs[J]. Journal of Network and Computer Applications, 2018, 103: 18–28. doi: 10.1016/j.jnca.2017.11.014
|
|
WONG C W, WONG T F, and SHEA J M. Secret-Sharing LDPC codes for the BPSK-constrained Gaussian wiretap channel[J]. IEEE Transactions on Information Forensics and Security, 2011, 6(3): 551–564. doi: 10.1109/TIFS.2011.2139208
|
|
ZHANG Shengjun, JIN Liang, LOU Yangming, et al. Secret key generation based on two-way randomness for TDD-SISO system[J]. China Communications, 2018, 15(7): 202–216. doi: 10.1109/CC.2018.8424614
|
|
BENNETT C H, BRASSARD G, CREPEAU C, et al. Generalized privacy amplification[J]. IEEE Transactions on Information Theory, 1995, 41(6): 1915–1923. doi: 10.1109/18.476316
|
|
ZENG X and DURRANI T S. Estimation of mutual information using copula density function[J]. Electronics Letters, 2011, 47(8): 493–494. doi: 10.1049/el.2011.0778
|





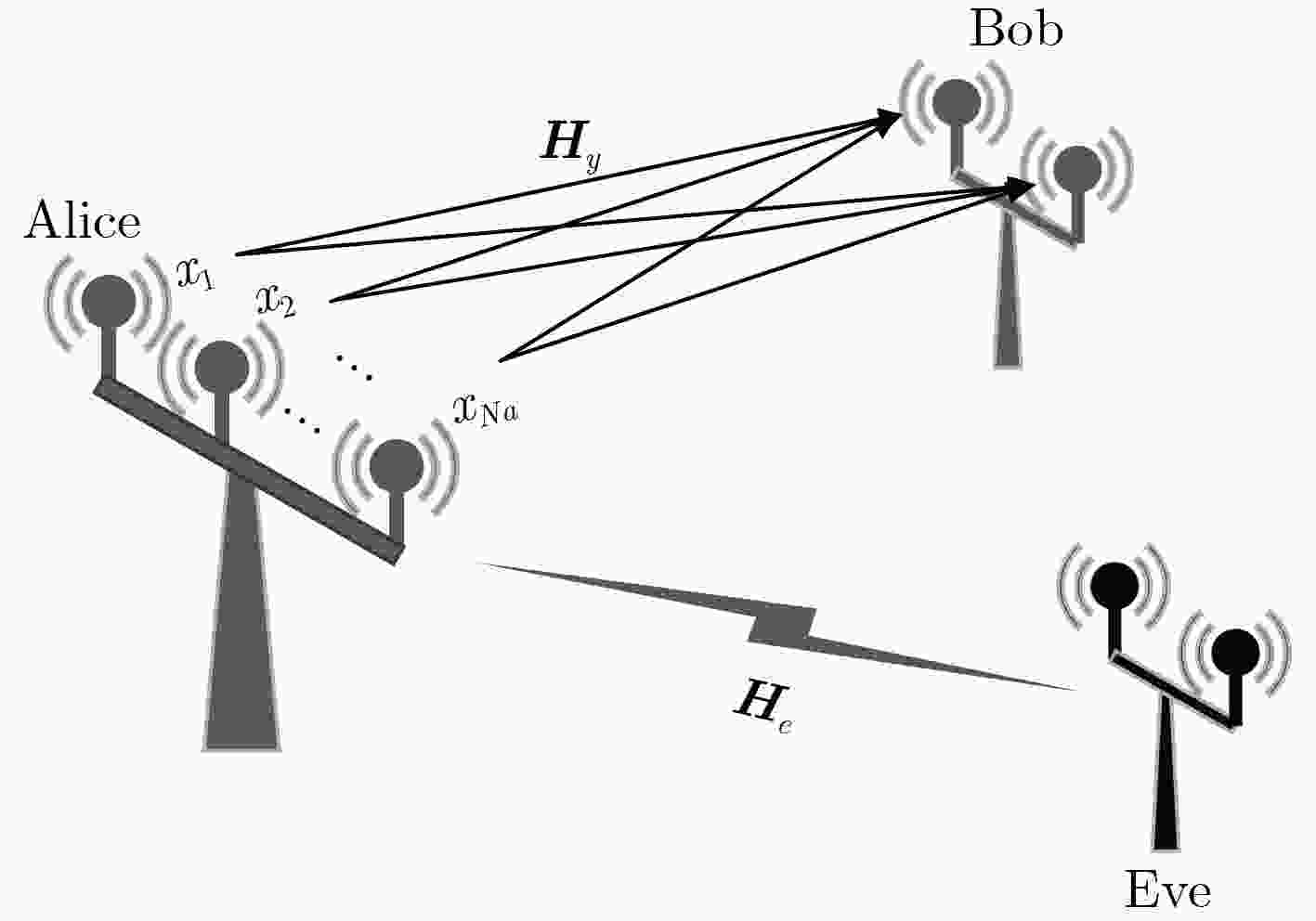
 下载:
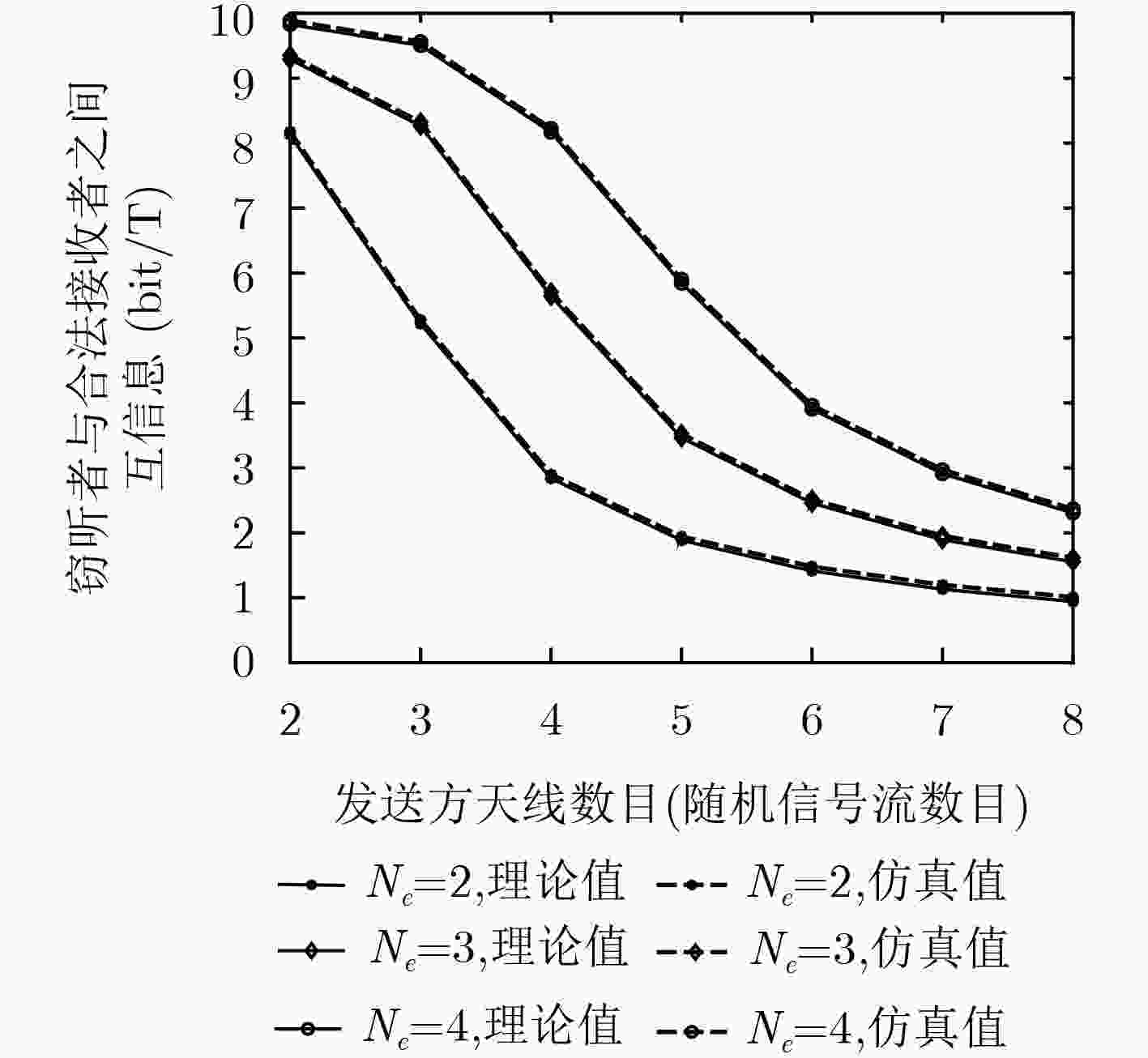
下载:
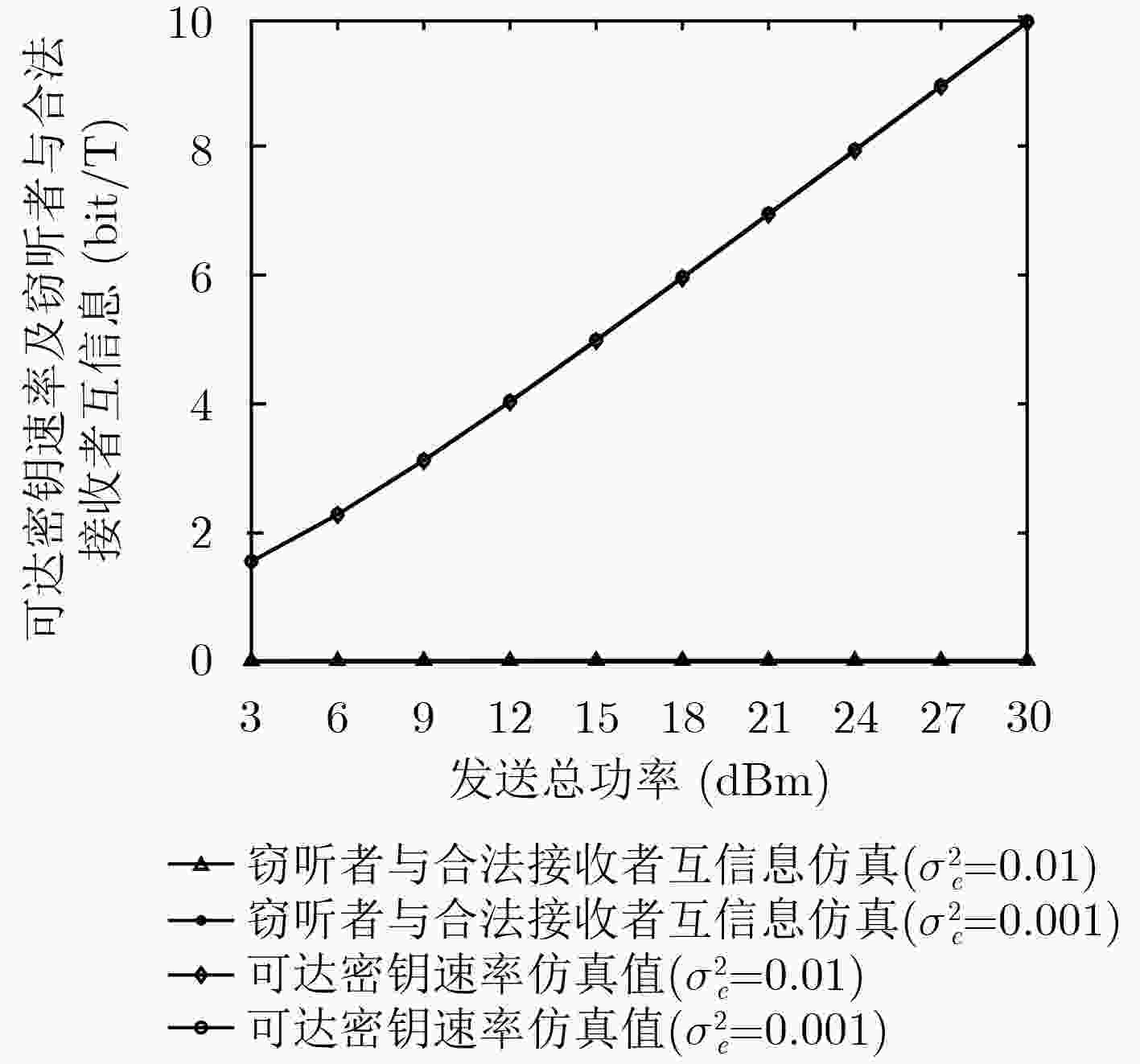

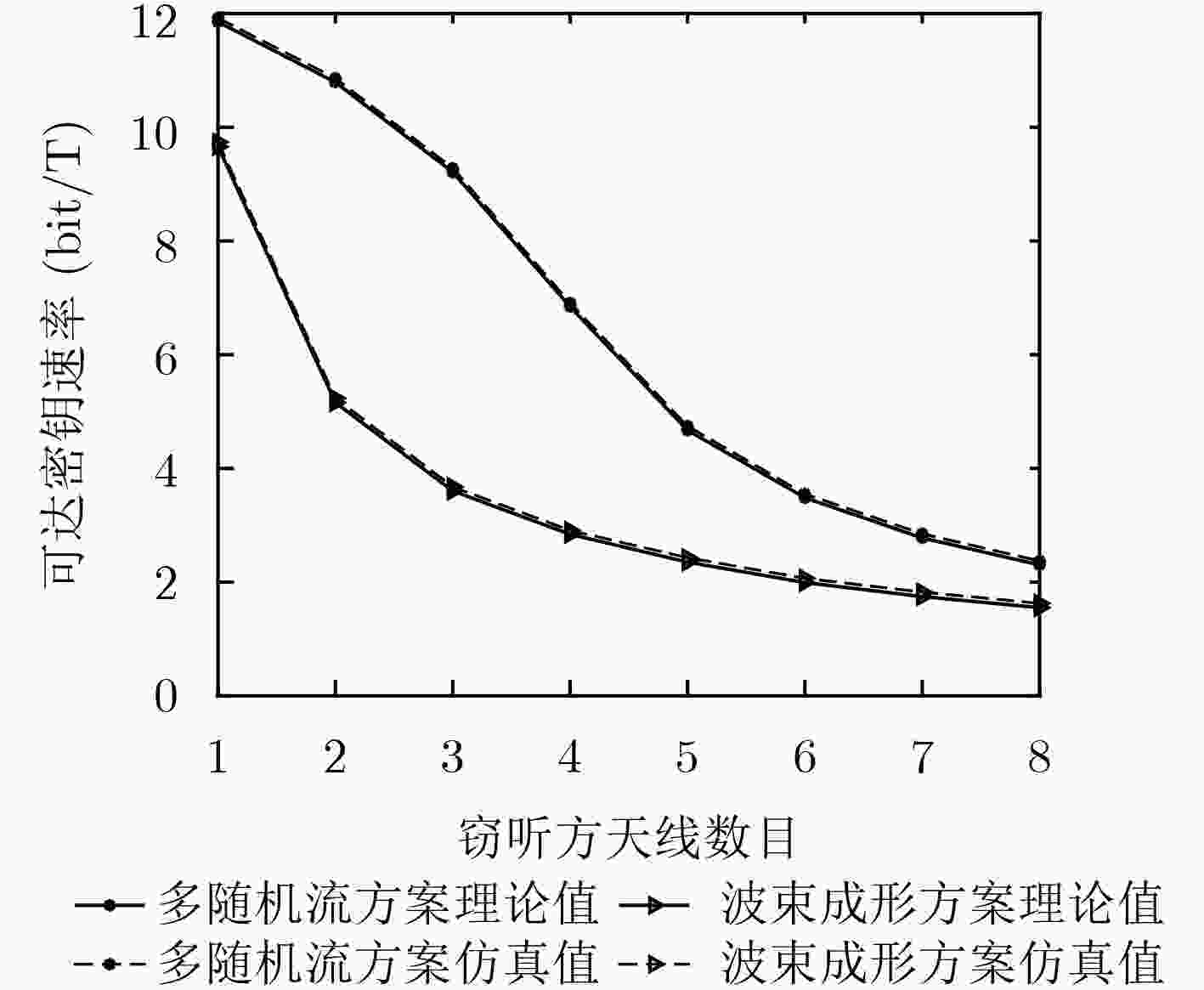
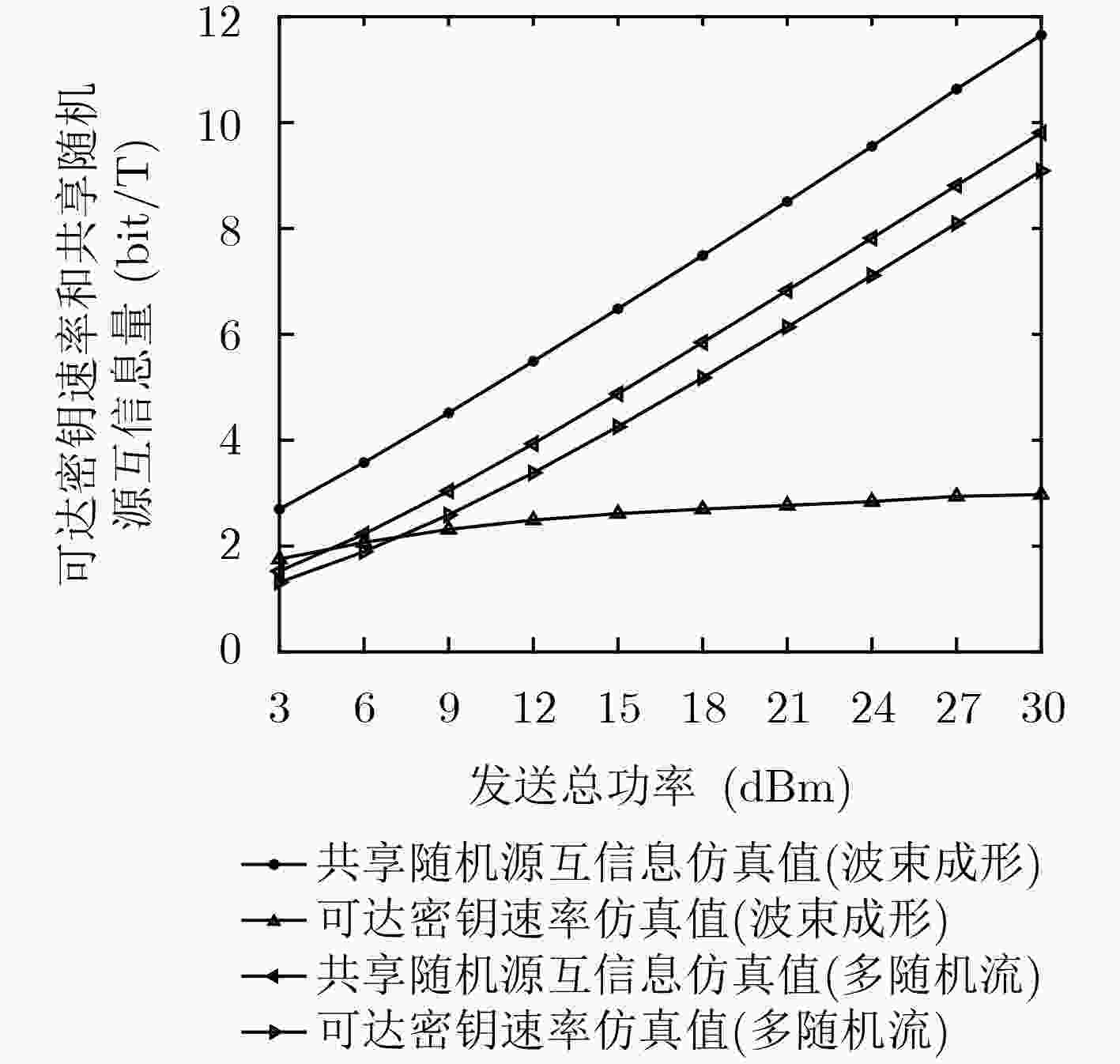
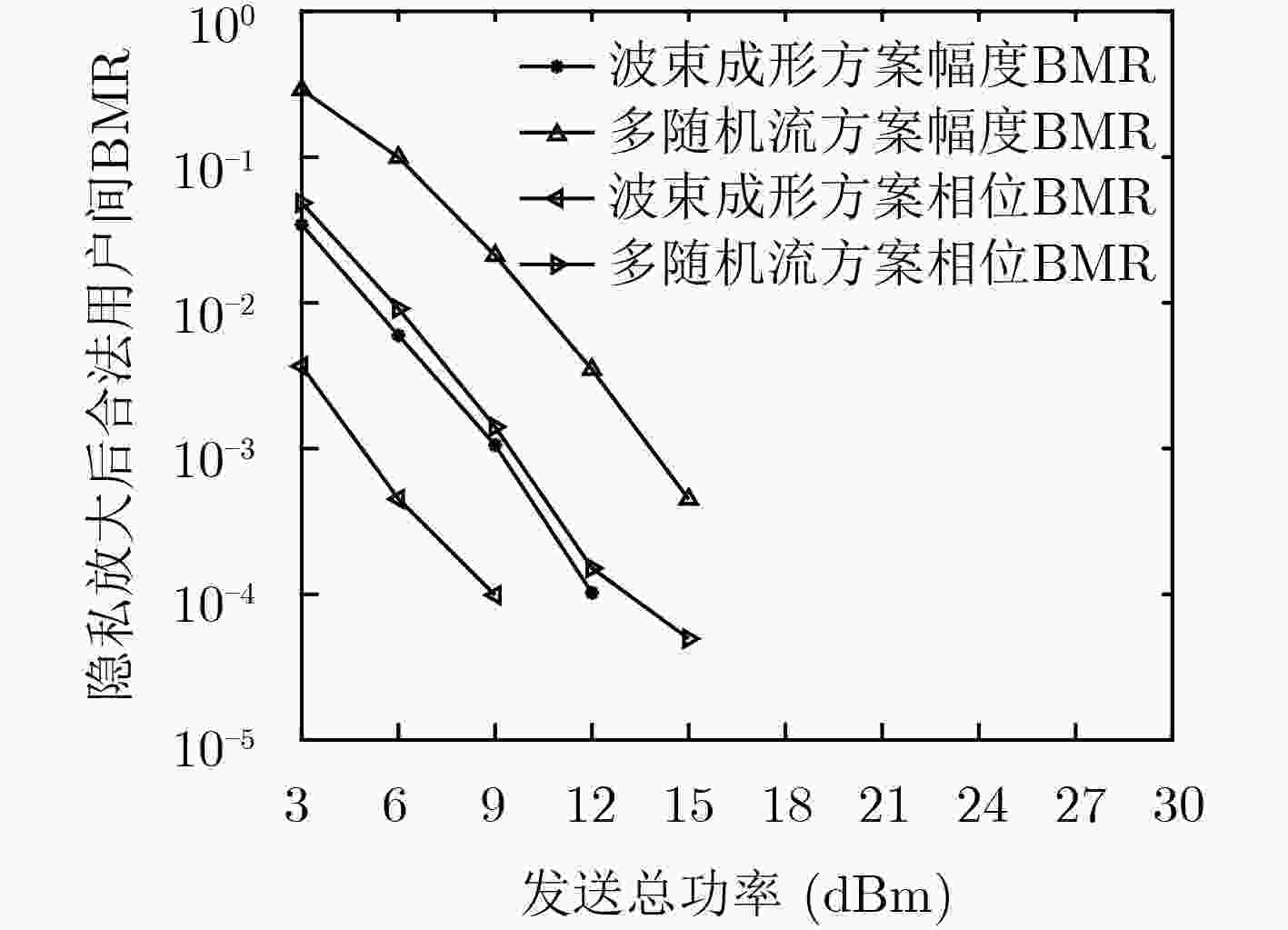
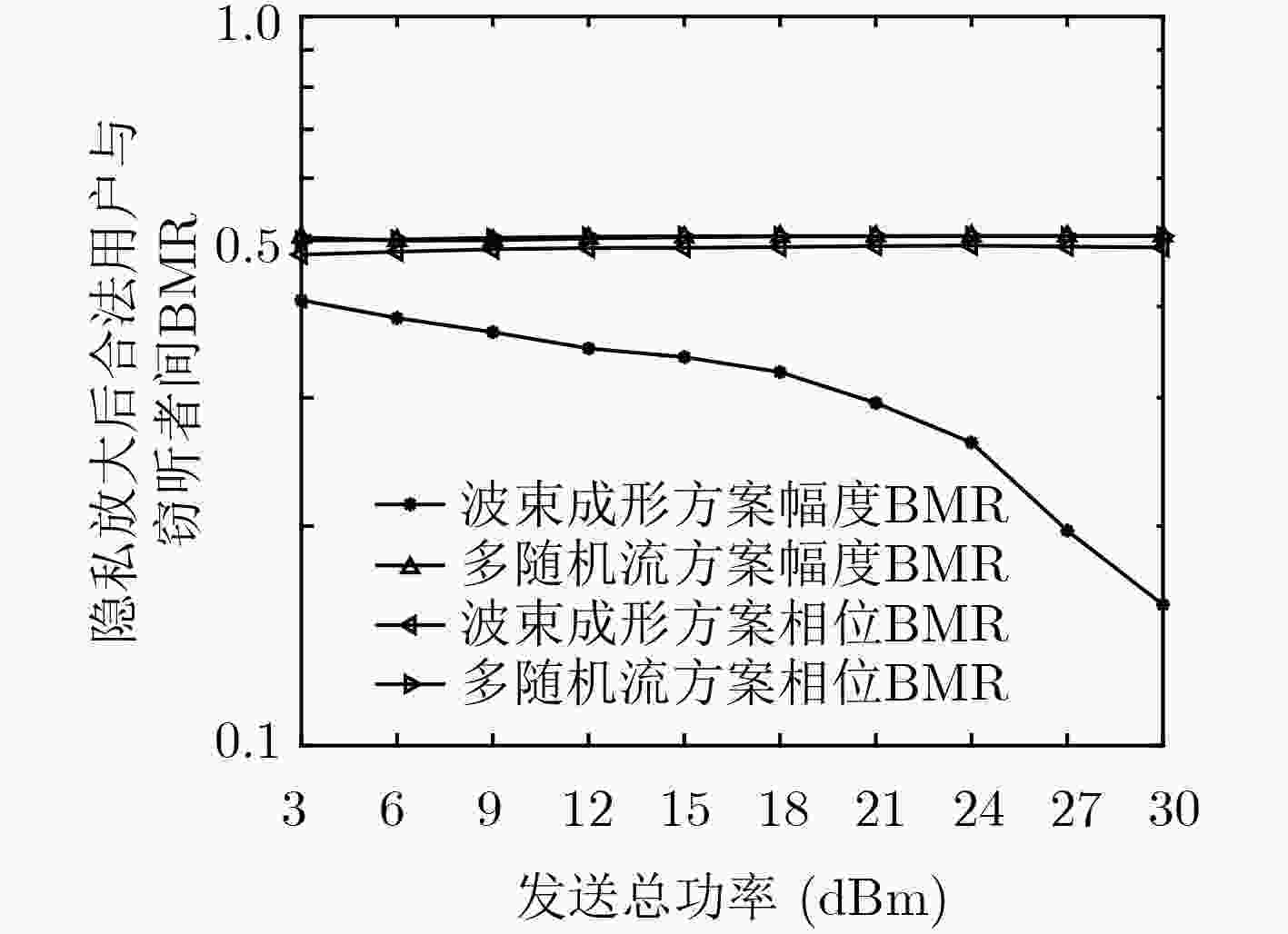


 下载:
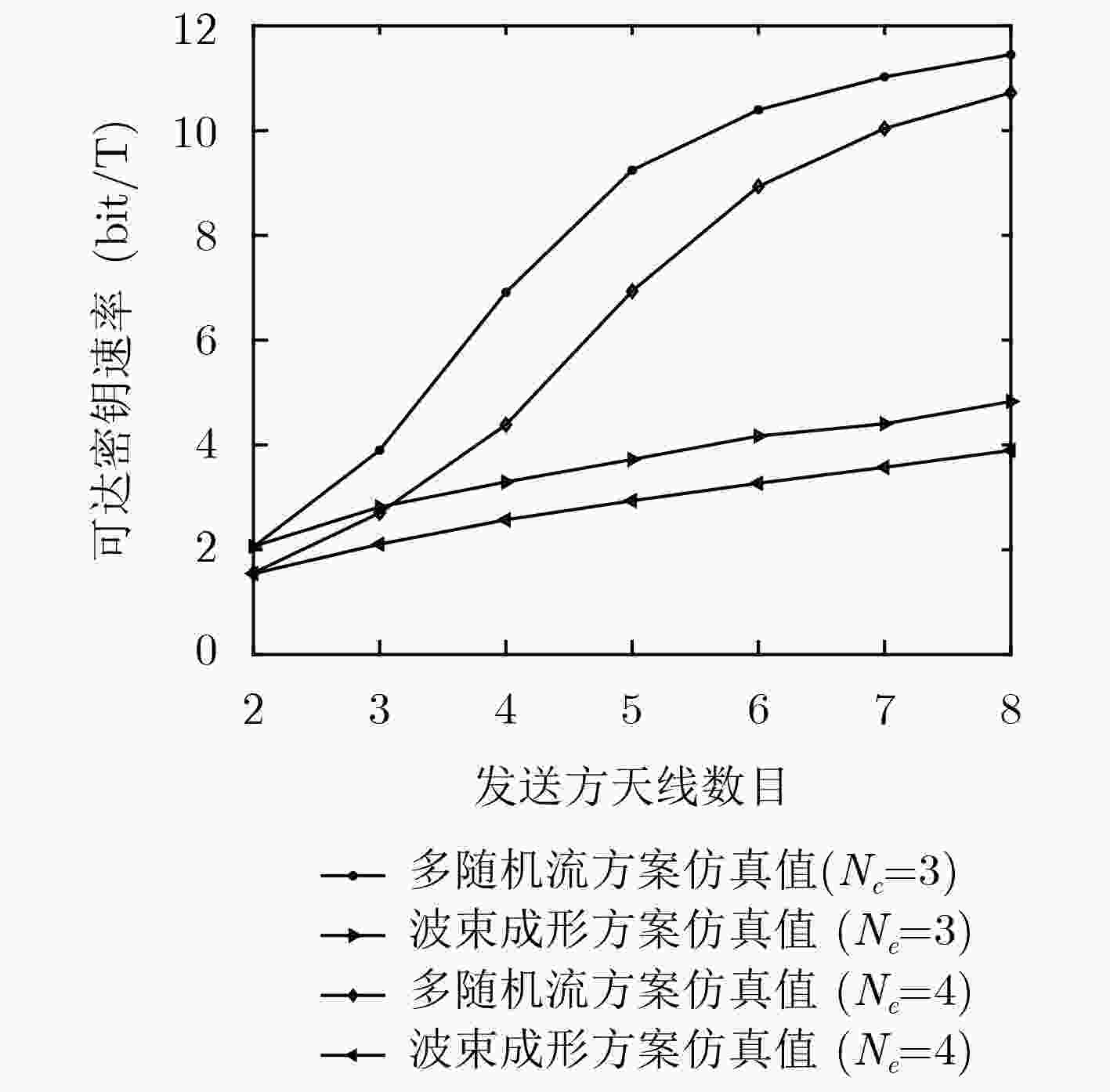
下载:
