Efficient Offline/Online Attribute Based Encryption with Verifiable Outsourced Decryption
-
摘要: 属性基加密可以为雾-云计算中的数据提供机密性保护和细粒度访问控制,但雾-云计算系统中的移动设备难以承担属性基加密的繁重计算负担。为解决该问题,该文提出一种可验证外包解密的离线/在线属性基加密方案。该方案能够实现离线/在线的密钥生成和数据加密,同时支持可验证外包解密。然后,给出方案的选择明文攻击的安全证明和可验证性的安全证明。之后,该文将转换阶段所需双线性对的计算量降为恒定常数。最后,从理论和实验两方面对所提方案进行性能分析,实验结果表明该方案是有效且实用的。Abstract: Attribute based encryption can provide data confidentiality protection and fine-grained access control for fog-cloud computing, however mobile devices in fog cloud computing system are difficult to bear the burdensome computing burden of attribute based encryption. In order to address this problem, an offline/online ciphertext-plicy attribute-based encryption scheme is presented with verifiable outsourced decryption based on the bilinear group of prime order. It can realize the offline/online key generation and data encryption. Simultaneously, it supports the verifiable outsourced decryption. Then, the formal security proofs of its selective chosen plaintext attack security and verifiability are provided. After that, the improved offline/online ciphertext-plicy attribute-based encryption scheme with verifiable outsourced decryption is presented, which reduces the number of bilinear pairings from linear to constant in the transformation phase. Finally, the efficiency of the proposed scheme is analyzed and verified through theoretical analysis and experimental simulation. The experimental results show that the proposed scheme is efficient and practical.
-
Key words:
- Attributed-based encryption /
- Offline/online /
- Outsourced decryption /
- Verifiability
-
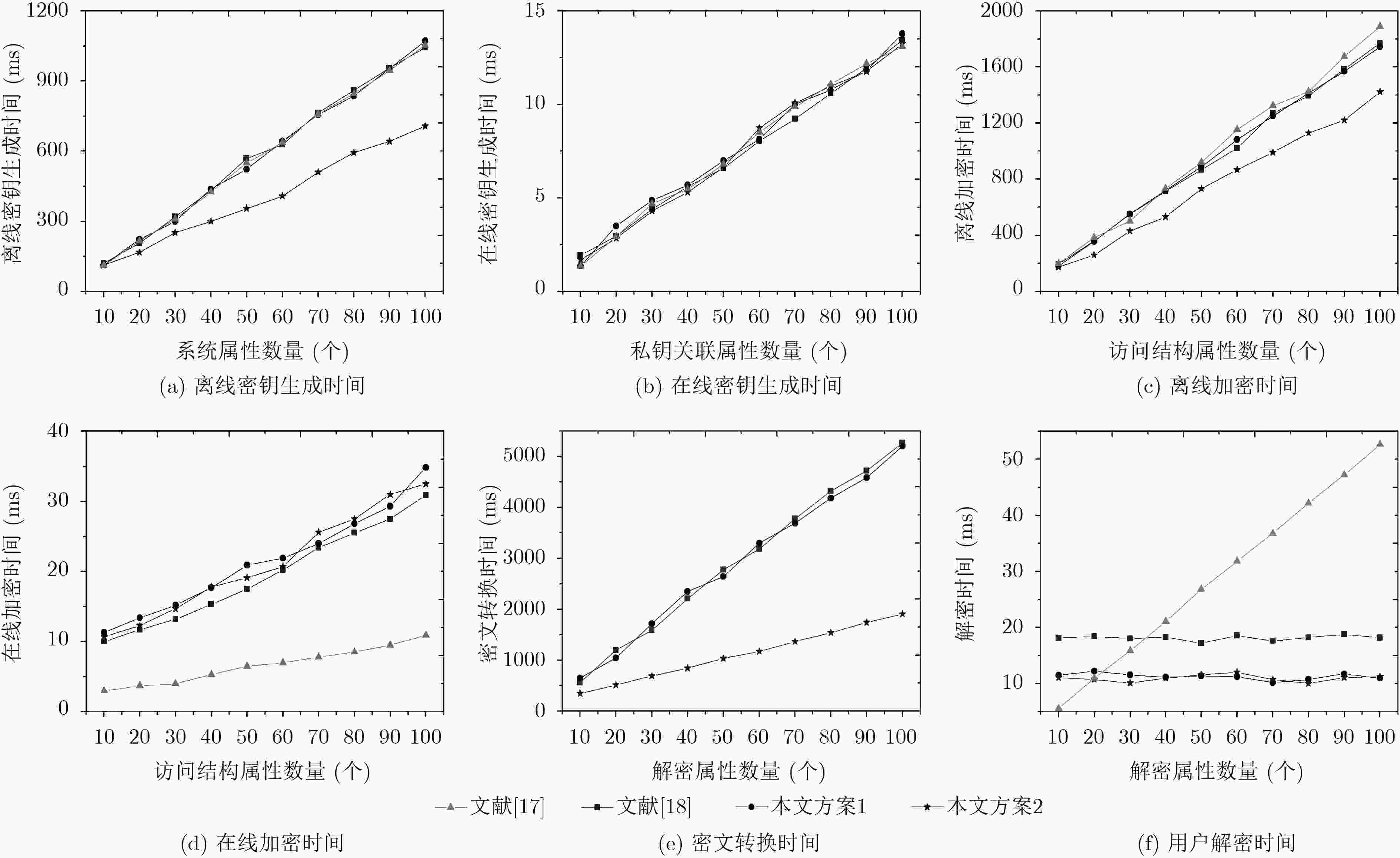
表 1 计算效率对比分析
算法 文献[17]方案 文献[18]方案 3OVD-CP-ABE I3OVD-CP-ABE 密钥生成 离线 $(3s{\rm{ + }}4){E_G} + (s{\rm{ + 1}}){\rm{Mul}}$ $(3s{\rm{ + }}4){E_G} + (s{\rm{ + 1}}){\rm{Mul}}$ $(3s{\rm{ + }}4){E_G} + (s{\rm{ + 1}}){\rm{Mul}}$ $(2s{\rm{ + 5}}){E_G} + (s{\rm{ + 1}}){\rm{Mul}}$ 在线 $s{\rm{Mul}}$ $s{\rm{Mul}}$ $s{\rm{Mul}}$ $s{\rm{Mul}}$ 加密 离线 $(5l{\rm{ + 1}}){E_G} + 1{E_{{G_T}}} + 2l{\rm{Mul}}$ $(5l{\rm{ + 1}}){E_G} + 1{E_{{G_T}}} + 2l{\rm{Mul}}$ $(5l{\rm{ + 1}}){E_G} + 1{E_{{G_T}}} + 2l{\rm{Mul}}$ $(4l{\rm{ + 2}}){E_G} + 1{E_{{G_T}}} + 2l{\rm{Mul}}$ 在线 0 $2{E_G}{\rm{ + }}{\rm{Mul}}$ $3H$ $3H$ 解密 外包 — $\begin{gathered} (2y{\rm{ + 1}}){E_{{G_T}}} + y{E_{{G_T}}} \\ {\rm{ + }}(3y{\rm{ + 2}})P + 2y{\rm{Mul}} \\ \end{gathered} $ $\begin{gathered} (2y{\rm{ + 1}}){E_{{G_T}}} + y{E_{{G_T}}} \\ {\rm{ + }}(3y{\rm{ + 2}})P + 2y{\rm{Mul}} \\ \end{gathered} $ $(5y{\rm{ + 5}}){E_G}{\rm{ + 10}}P{\rm{ + 4}}y{\rm{Mul}}$ 用户 $\begin{gathered} (2y{\rm{ + 1}}){E_{{G_T}}} + y{E_{{G_T}}} \\ {\rm{ + }}(3y{\rm{ + 2}})P + 2y{\rm{Mul}} \\ \end{gathered} $ $2{E_G} + 1{E_{{G_T}}} + {\rm{Mul}}$ $1{E_{{G_T}}}{\rm{ + }}3H$ $1{E_{{G_T}}}{\rm{ + }}3H$ -
KHAN S, PARKINSON S, and QIN Yongrui. Fog computing security: A review of current applications and security solutions[J]. Journal of Cloud Computing, 2017, 6(1): 19–41 doi: 10.1186/s13677-017-0090-3 SAHAI A and WATERS B. Fuzzy identity-based encryption[C]. Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 2005: 457–473. doi: 10.1007/11426639_27. GOYAL V, PANDEY O, SAHAI A, et al. Attribute-based encryption for fine-grained access control of encrypted data[C]. Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, USA, 2006: 89–98. doi: 10.1145/1180405.1180418. BETHENCOURT J, SAHAI A, and WATERS B. Ciphertext-policy attribute-based encryption[C]. Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, USA, 2007: 321–334. doi: 10.1109/SP.2007.11. GREEN M, HOHENBERGER S, and WATERS B. Outsourcing the decryption of ABE ciphertexts[C]. Proceedings of the 20th USENIX Conference on Security, San Francisco, USA, 2011: 34. LAI Junzuo, DENG R H, GUAN Chaowen, et al. Attribute-based encryption with verifiable outsourced decryption[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(8): 1343–1354 doi: 10.1109/TIFS.2013.2271848 ZHAO Zhiyuan and WANG Jianhua. Verifiable outsourced ciphertext-policy attribute-based encryption for mobile cloud computing[J].KSII Transactions on Internet and Information Systems, 2017, 11(6): 3254–3272 doi: 10.3837/tiis.2017.06.024 FAN Kai, WANG Junxiong, WANG Xin, et al. A secure and verifiable outsourced access control scheme in fog-cloud computing[J]. Sensors, 2017, 17(7): 1695–1710 doi: 10.3390/s17071695 LI Jiguo, SHA Fengjie, ZHANG Yichen, et al. Verifiable outsourced decryption of attribute-based encryption with constant ciphertext length[J]. Security and Communication Networks, 2017, 2017: 1–11 doi: 10.1155/2017/3596205 ZHANG Rui, MA Hui, and LU Yao. Fine-grained access control system based on fully outsourced attribute-based encryption[J]. Journal of Systems and Software, 2017, 125(3): 344–353 doi: 10.1016/j.jss.2016.12.018 EVEN S, GOLDREICH O, and MICALI S. On-line/off-line digital signatures[C]. Proceedings of the Conference on the Theory and Application of Cryptology, Santa Barbara, USA, 1989: 263–275. doi: 10.1007/0-387-34805-0_24. LIU J K, BAEK J, ZHOU Jianying, et al. Efficient online/offline identity-based signature for wireless sensor network[J]. International Journal of Information Security, 2010, 9(4): 287–296 doi: 10.1007/s10207-010-0109-y GUO Fuchun, MU Yi, and CHEN Zhide. Identity-based online/offline encryption[C]. Proceedings of the International Conference on Financial Cryptography and Data Security, Cozumel, Mexico, 2008: 247–261. doi: 10.1007/978-3-540-85230-8_22. LIU J K and ZHOU Jianying. An efficient identity-based online/offline encryption scheme[C]. Proceedings of the International Conference on Applied Cryptography and Network Security, Paris-Rocquencourt, France, 2009: 156–167. doi: 10.1007/978-3-642-01957-9_10. CHOW S S M, LIU J K, and ZHOU Jianying. Identity-based online/offline key encapsulation and encryption[C]. Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, Hong Kong, China, 2011: 52–60. doi: 10.1145/1966913.1966922. ROUSELAKIS Y and WATERS B. Practical constructions and new proof methods for large universe attribute-based encryption[C]. Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, Berlin, Germany, 2013: 463–474. doi: 10.1145/2508859.2516672. HOHENBERGER S and WATERS B. Online/offline attribute-based encryption[C]. Proceedings of the International Workshop on Public Key Cryptography, Buenos Aires, Argentina, 2014: 293–310. doi: 10.1007/978-3-642-54631-0_17. LIU Zechao, JIANG Z L, WANG Xuan, et al. Offline/online attribute-based encryption with verifiable outsourced decryption[J]. Concurrency and Computation:Practice and Experience, 2017, 29(7): 1–17 doi: 10.1002/cpe.3915 -





 下载:
下载:


 下载:
下载:
