Artificial Noise Aided Secure Transmission in Dense Heterogeneous Cellular Networks with Imperfect Channel State Information
-
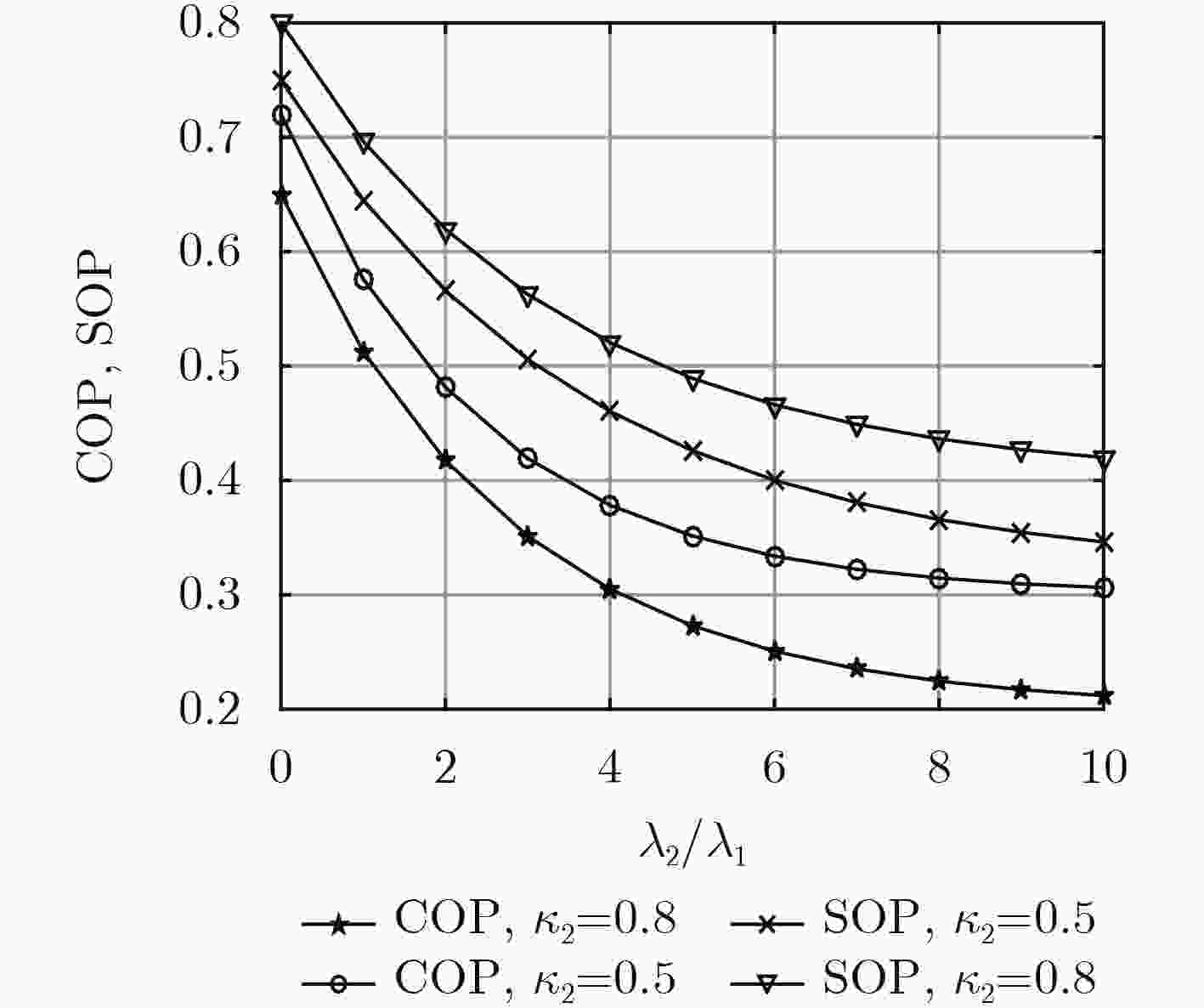
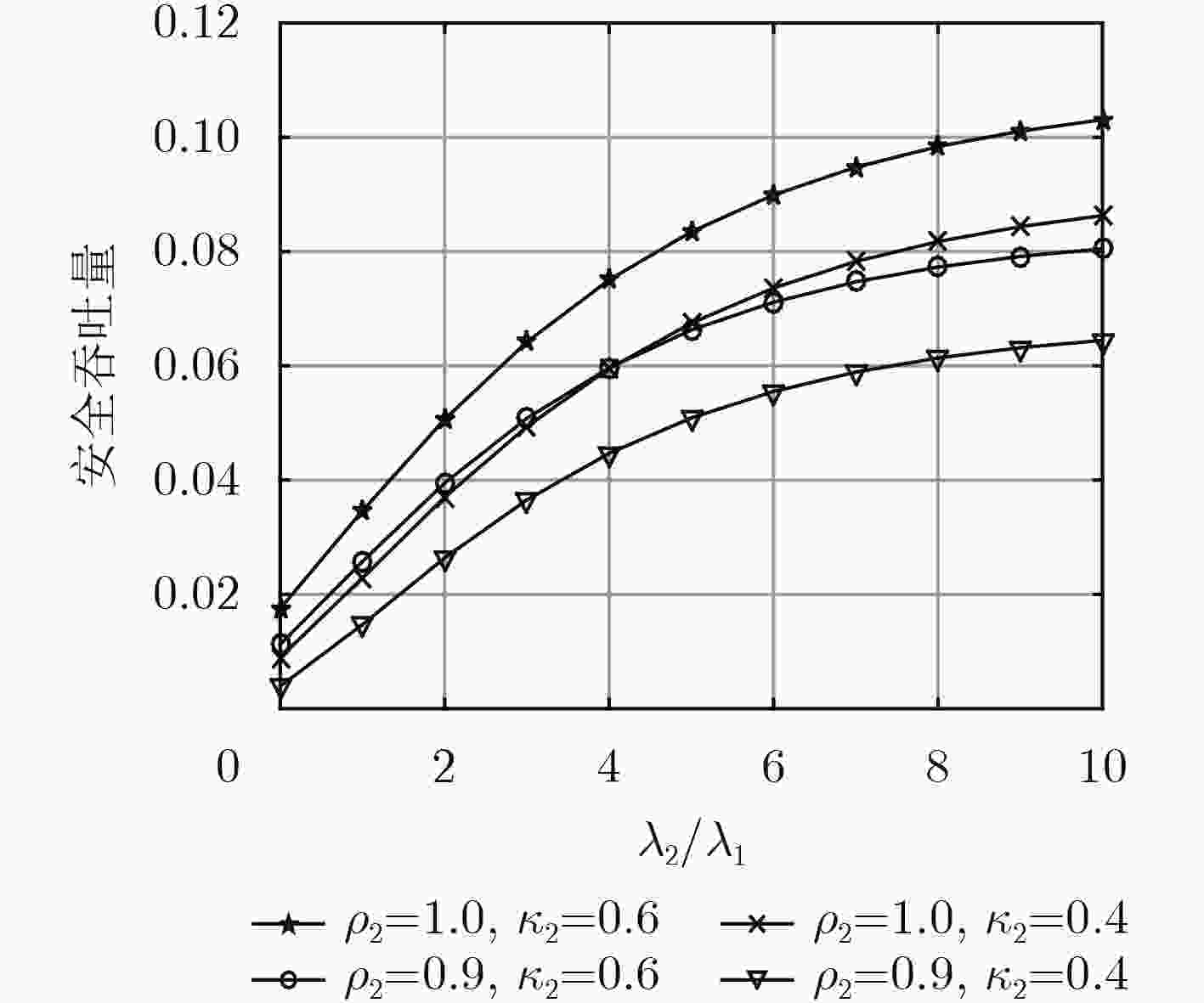
摘要: 针对密集异构蜂窝网在非理想信道状态信息条件下的安全传输问题,该文分析了人工噪声对通信的可靠性和安全性的影响,在此基础上提出功率分配优化模型,在不同信道估计精度条件下给出了最优的功率分配因子。首先,考虑信道估计误差对合法信号传输以及人工噪声泄露的影响,推导了典型通信链路的连通中断概率和安全中断概率。然后,在安全性和可靠性约束条件下建立功率分配优化模型以最大化系统安全吞吐量,并通过K维联合搜索算法得到每层网络的最优功率分配因子。最后,仿真结果表明系统设置最优功率分配因子时,人工噪声方案可提升约15%的安全吞吐量。Abstract: To ensure secure transmission in dense heterogeneous cellular networks with imperfect Channel State Information (CSI), the influence of Artificial Noise (AN) on secure and reliable communication is analyzed, and a power split factor optimization model is presented to obtain the optimal value under different channel estimation accuracy. First, the connection outage probability and secrecy outage probability are deduced by considering the influence of channel estimation error on signal transmission and AN leakage. Then, a power split factor optimization model is presented, which maximizes the secrecy throughput subject to the security and reliability requirements. A K-dimensional search method is employed to solve the optimal power split factor of each tier. Finally, the numerical results verify that the AN transmission scheme with optimal power split factor can increase secrecy throughput by about 15%.
-
表 1 功率分配因子最优值搜素算法
(1) 输入:K, ${\rho _i}$, ${\alpha _i}$, ${P_i}$, ${\lambda _i}$, ${\lambda _e}$, ${R_b}$, ${R_s}$, ${\partial _1}$, ${\partial _2}$, $\Delta {\kappa _1},\Delta {\kappa _2}, ·\!·\!· ,\Delta {\kappa _K}$; (2) 初始化: ${C_1} = {\rm{1}}/\Delta {\kappa _1}, ·\!·\!· ,{C_K} = {\rm{1}}/\Delta {\kappa _K}$, ${\xi ^ \circ } = 0$; (3) for ${c_i} = 1:{C_i}\;$do (4) 计算 ${\mathcal{A}_i}$, $P_{\rm co}^i$和 $P_{\rm so}^i$,在约束条件 $P_{\rm co}^i \le {\partial _1},\;\;P_{\rm so}^i \le {\partial _2}$下更新集 合 $\left( {{{\hat \kappa }_1},{{\hat \kappa }_2}, ·\!·\!· ,{{\hat \kappa }_K}} \right)$; (5) end for (6) 设置 $\varOmega $为集合 $\left( {{{\hat \kappa }_1},{{\hat \kappa }_2}, ·\!·\!· ,{{\hat \kappa }_K}} \right)$中的元素数量,
$\varOmega = {\rm{Card}}\left( {{{\hat \kappa }_1}} \right),$ ${\rm{Card}}\left( {{{\hat \kappa }_2}} \right), ·\!·\!· , = {\rm{Card}}\left( {{{\hat \kappa }_K}} \right)$(7) for $\omega = 1:\varOmega $ do (8) 将集合 $\left( {{{\hat \kappa }_1},{{\hat \kappa }_2}, ·\!·\!· ,{{\hat \kappa }_K}} \right)$中的元素 $\kappa _1^\omega ,\kappa _2^\omega , ·\!·\!· ,\kappa _K^\omega $代入式(21)计算 $\xi $; (9) 当 $\xi > {\xi ^ \circ }$时,令 ${\xi ^ \circ } = \xi $, $\kappa _1^* = \kappa _1^\omega ,\kappa _2^\omega , ·\!·\!· ,\kappa _K^* = \kappa _K^\omega $; (10) end for (11) 输出:最优值 $\kappa _1^*,\kappa _2^*, ·\!·\!· ,\kappa _K^*$。 -
YANG Xiaobin and FAPOJUWO A O. Coverage probability analysis of heterogeneous cellular networks in rician/rayleigh fading environments[J]. IEEE Communications Letters, 2015, 19(7): 1197–1200 doi: 10.1109/LCOMM.2015.2430346 BLOCH M and BARROS J. Physical-layer Security: From Information Theory to Security Engineering[M]. Cambridge: Cambridge University Press, 2011: 290–308. YANG Nan, WANG Lifeng, GERACI G, et al. Safeguarding 5G wireless communication networks using physical layer security[J]. IEEE Communications Magazine, 2015, 53(4): 20–27 doi: 10.1109/MCOM.2015.7081071 GOEL S and NEGI R. Guaranteeing secrecy using artificial noise[J]. IEEE Transactions on Wireless Communication, 2008, 7(6): 2180–2189 doi: 10.1109/TWC.2008.060848 ZHANG Xi, ZHOU Xiangyun, and MCKAY M. Enhancing secrecy with multi-antenna transmission in wireless Ad hoc networks[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(11): 1802–1814 doi: 10.1109/TIFS.2013.2279842 CAI Yueming, XU Xiaoming, and YANG Weiwei. Secure transmission in the random cognitive radio networks with secrecy guard zone and artificial noise[J]. IET Communications, 2016, 10(15): 1904–1913 doi: 10.1049/iet-com.2016.0117 ZHONG Zhihao, LUO Wenyu, PENG Jianhua, et al. Secrecy performance analysis of cooperative transmission and cooperative jamming for multi-tier heterogeneous cellular networks[J]. SCIENTIA SINICA INformationis China Information Sciences, 2016, 46(1): 33–48 doi: 10.1360/N112015-00174 WANG Chao and WANG Huiming. Opportunistic jamming for enhancing security stochastic geometry modeling and analysis[J]. IEEE Transactions on Vehicular Technology, 2016, 65(12): 10213–10217 doi: 10.1109/TVT.2016.2536621 ZHENG Tongxing and WANG Huiming. Optimal power allocation for artificial noise under imperfect csi against spatially random eavesdroppers[J]. IEEE Transactions on Vehicular Technology, 2016, 65(10): 8812–8817 doi: 10.1109/TVT.2015.2513003 WANG Huiming, WANG Chao, ZHENG Tongxing, et al. Impact of artificial noise on cellular networks: A stochastic geometry approach[J]. IEEE Transactions on Wireless Communications, 2016, 15(11): 7390–7404 doi: 10.1109/TWC.2016.2601903 LI Si, LI Qiang, and SHAO Shihai. Robust secrecy beamforming for full-duplex two-way relay networks under imperfect channel state information[J]. Science China Information Sciences, 2018, 61(2): 022307 doi: 10.1007/S11432-017-9110-X CAO Weifeng, ZOU Yulong, and YANG Zhen. Joint source-relay selection for improving wireless physical layer security[C]. 2016 IEEE Global Communications Conference, Singapore, 2017: 1–5. CAI Yunlong, SHI Qingjiang, CHAMPAGNE B, et al. Joint transceiver design for secure downlink communications over an amplify-and-forward MIMO relay[J]. IEEE Transactions on Communications, 2017, 65(9): 3691–3704 doi: 10.1109/TCOMM.2017.2708110 WANG Huiming, ZHENG Tongxing, YUAN Jinhong, et al. Physical layer security in heterogeneous cellular networks[J]. IEEE Transactions on Communications, 2016, 64(3): 1204–1219 doi: 10.1109/TCOMM.2016.2519402 GRADSHTEYN I, RYZHIK I, JEFFREY A, et al. Table of Integrals, Series, and Products[M]. New York, USA, Academic, 2007. -





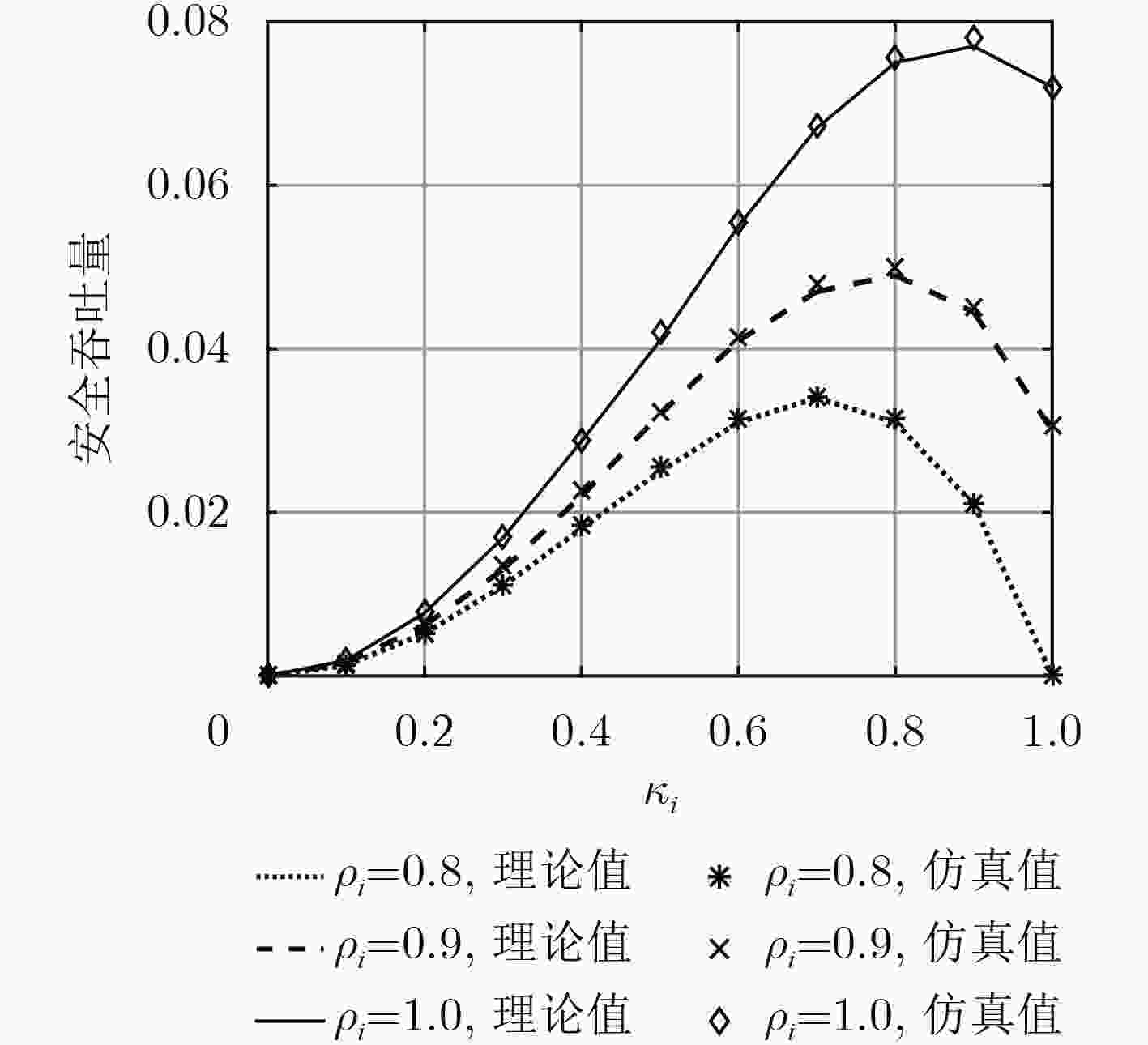
 下载:
下载:
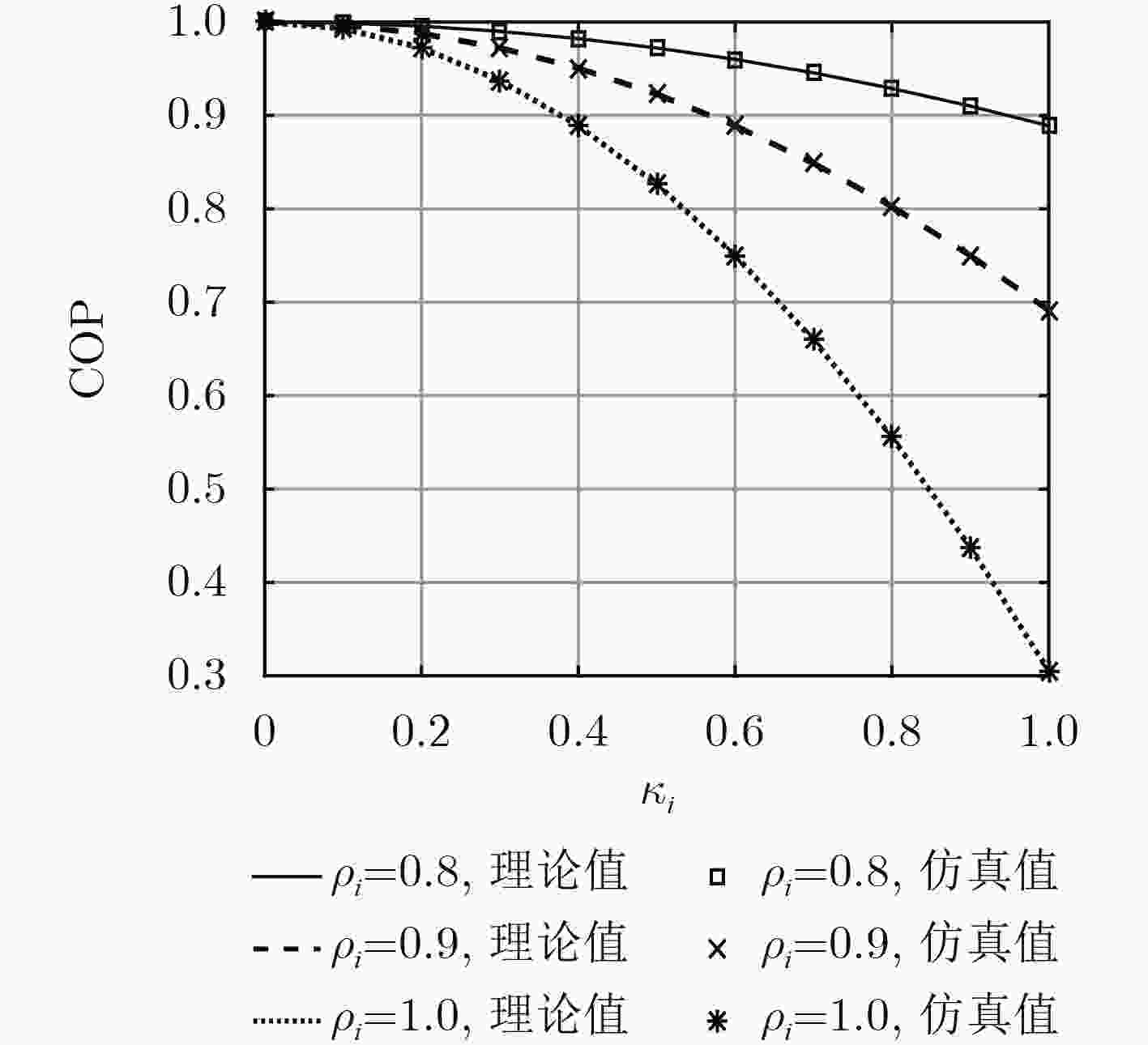
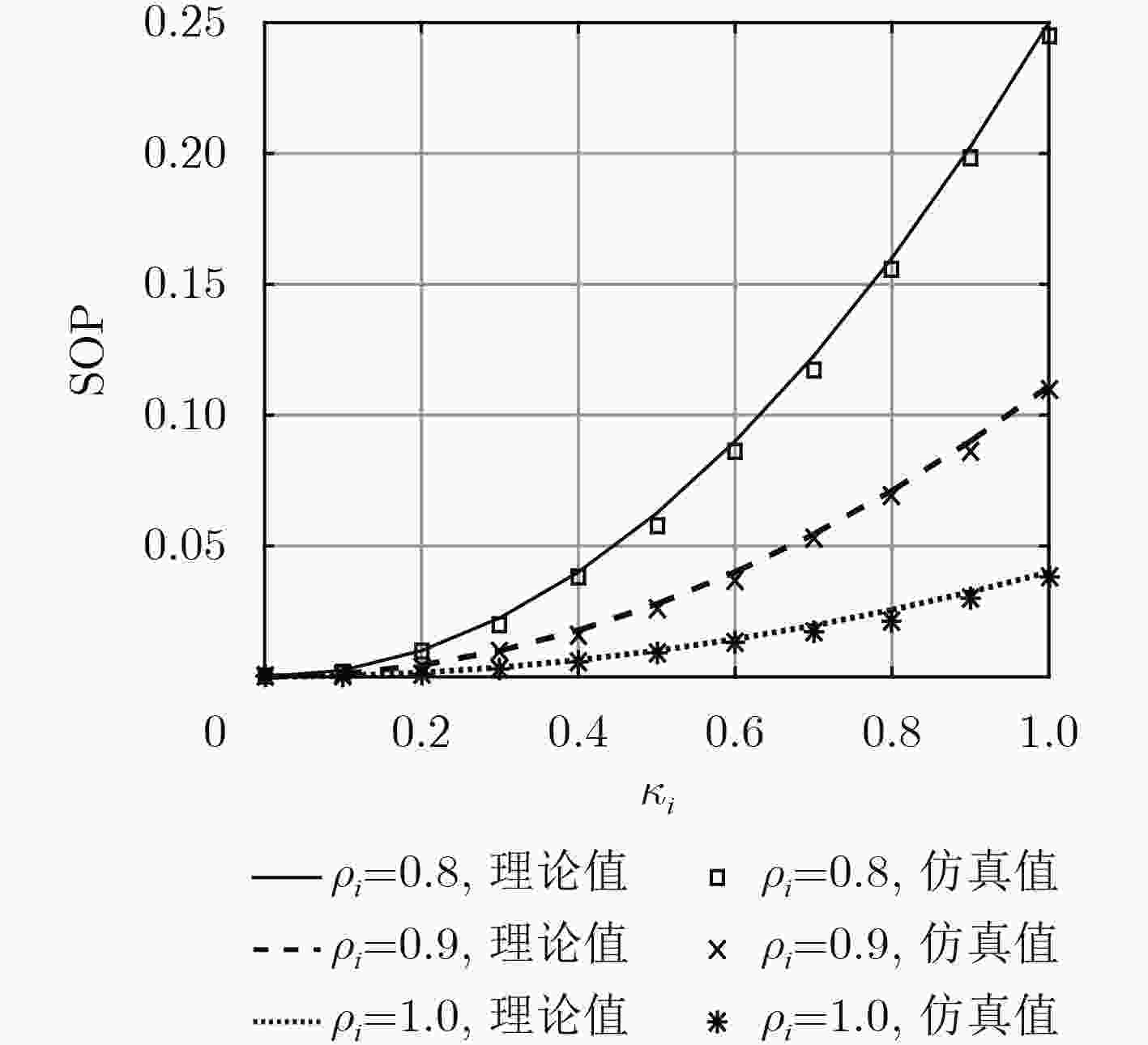
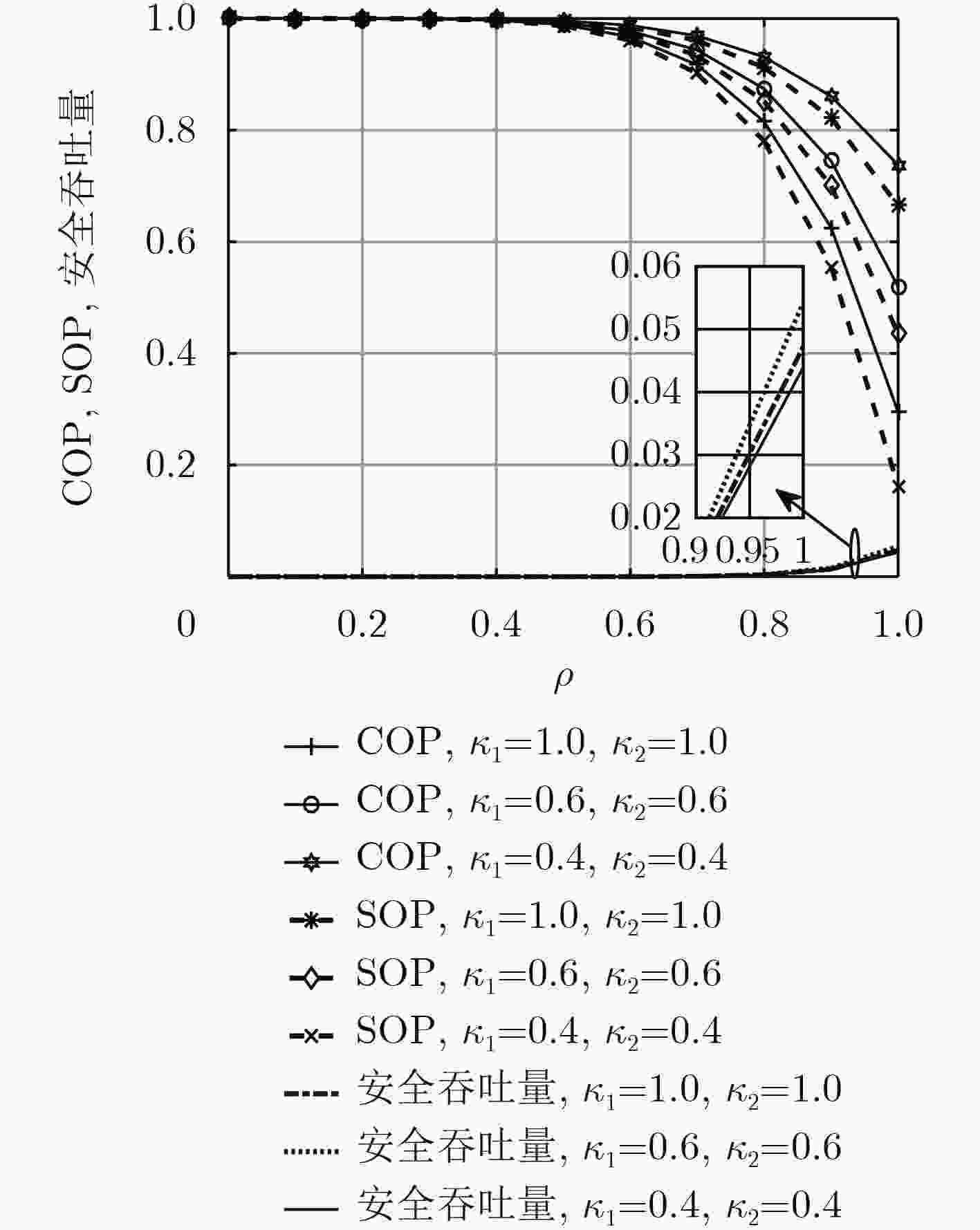



 下载:
下载:
