Packet Forwarding Authentication Mechanism Based on Cipher Identification in Software-defined Network
-
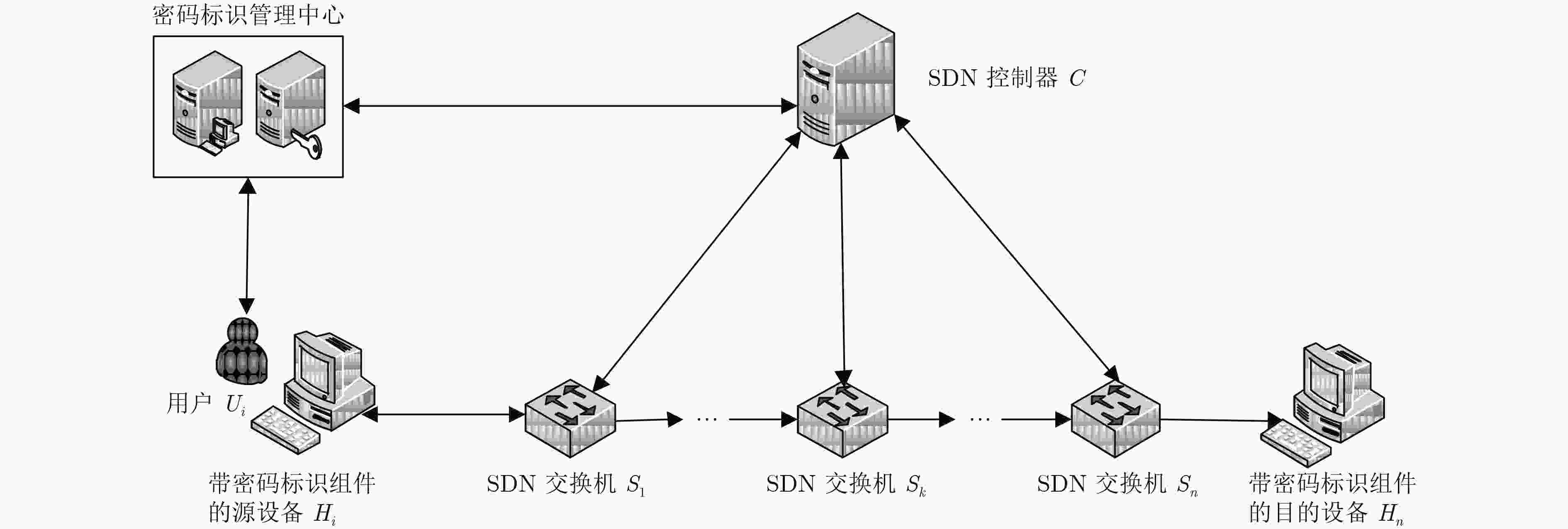
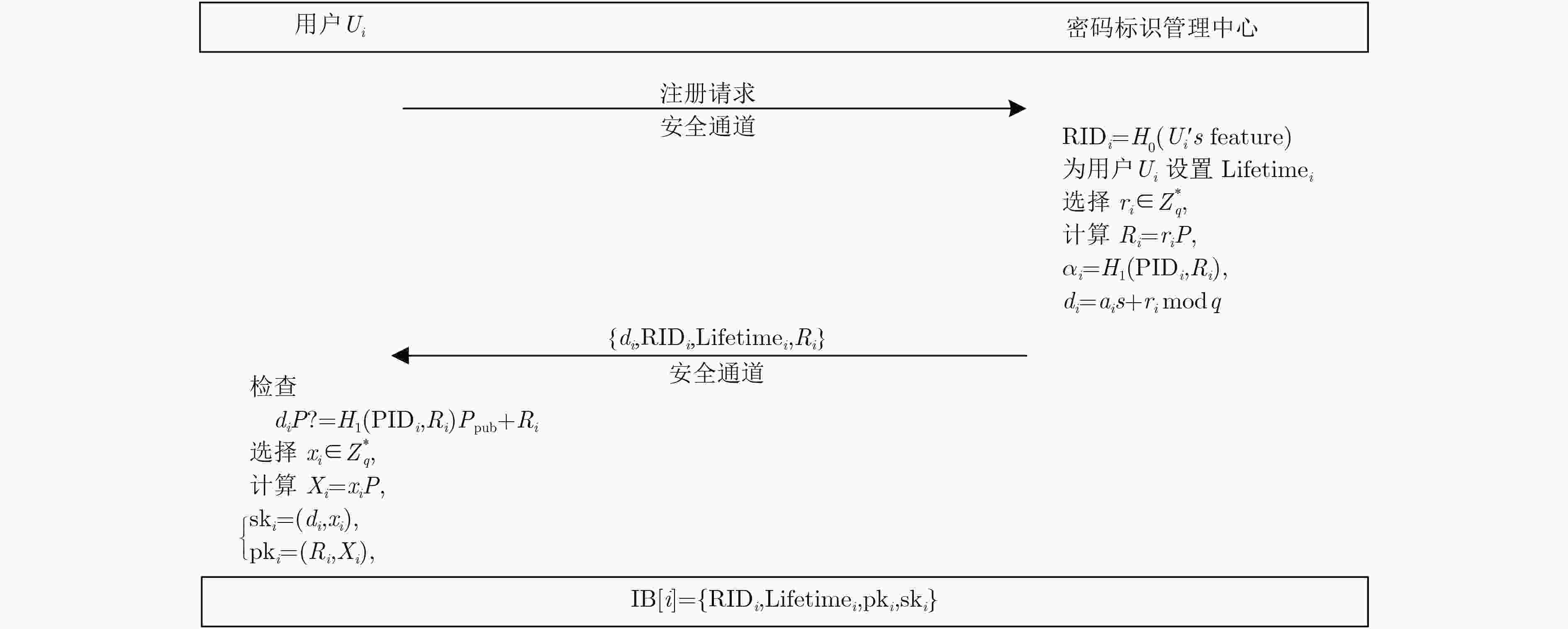
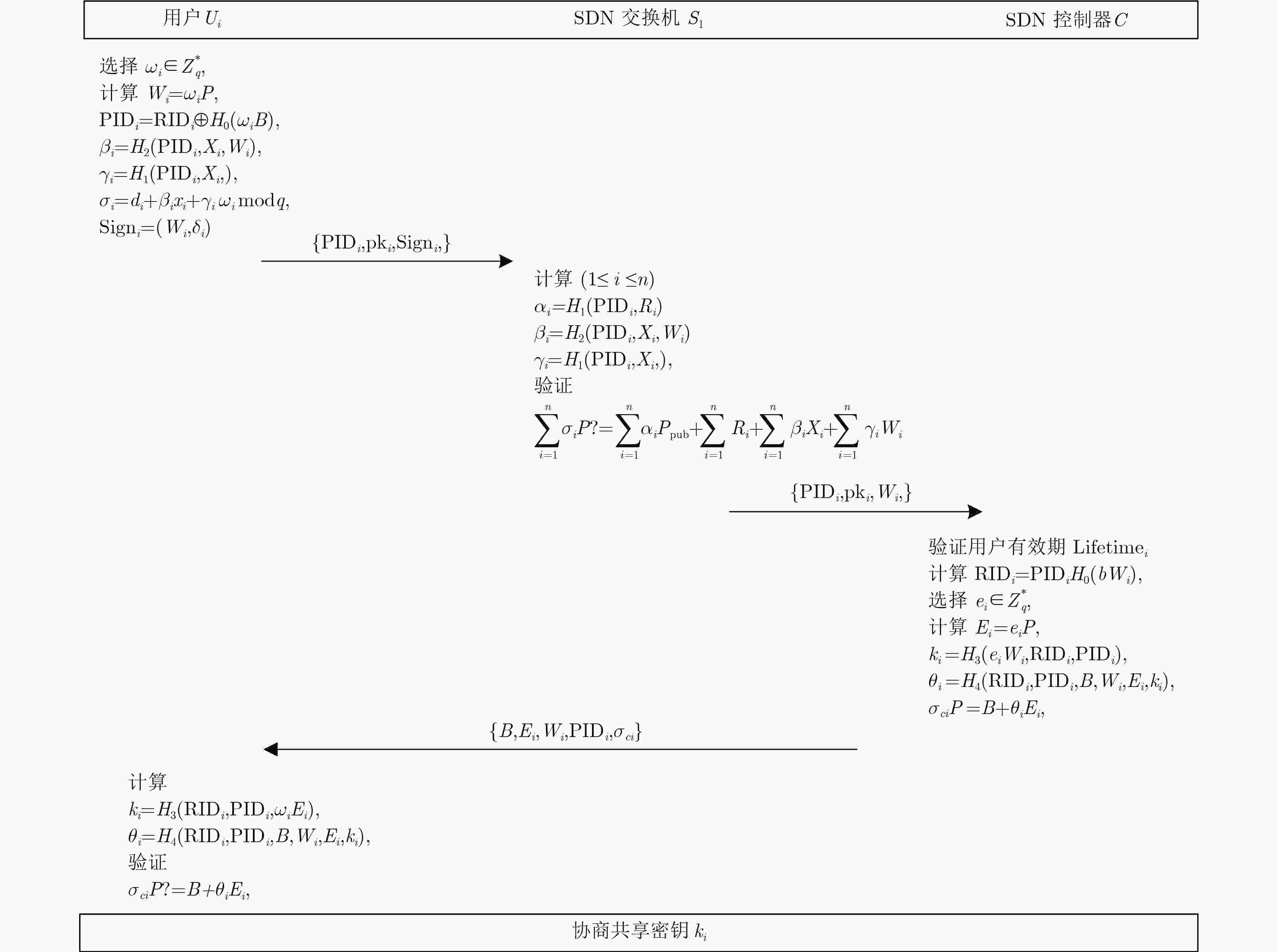
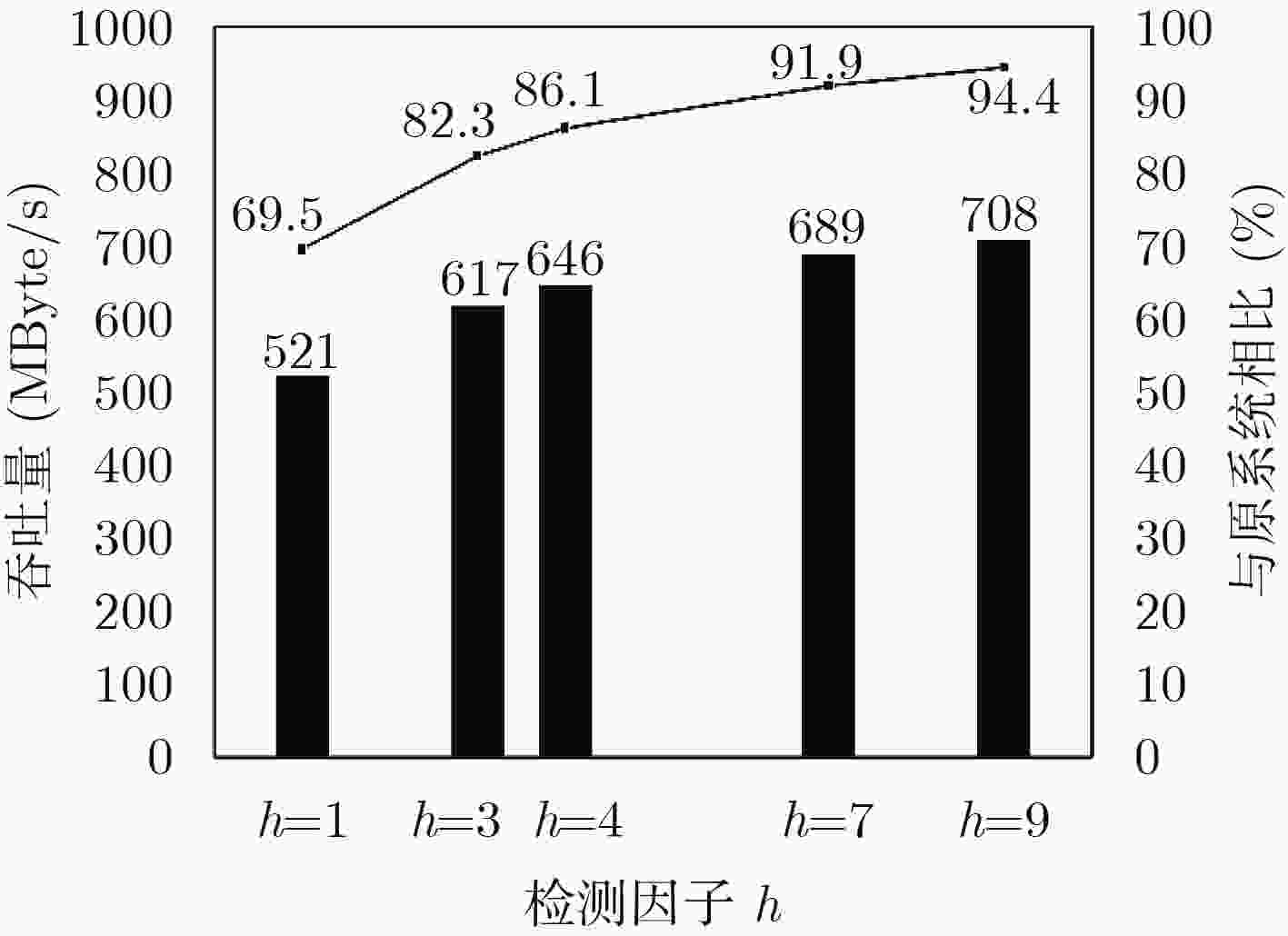
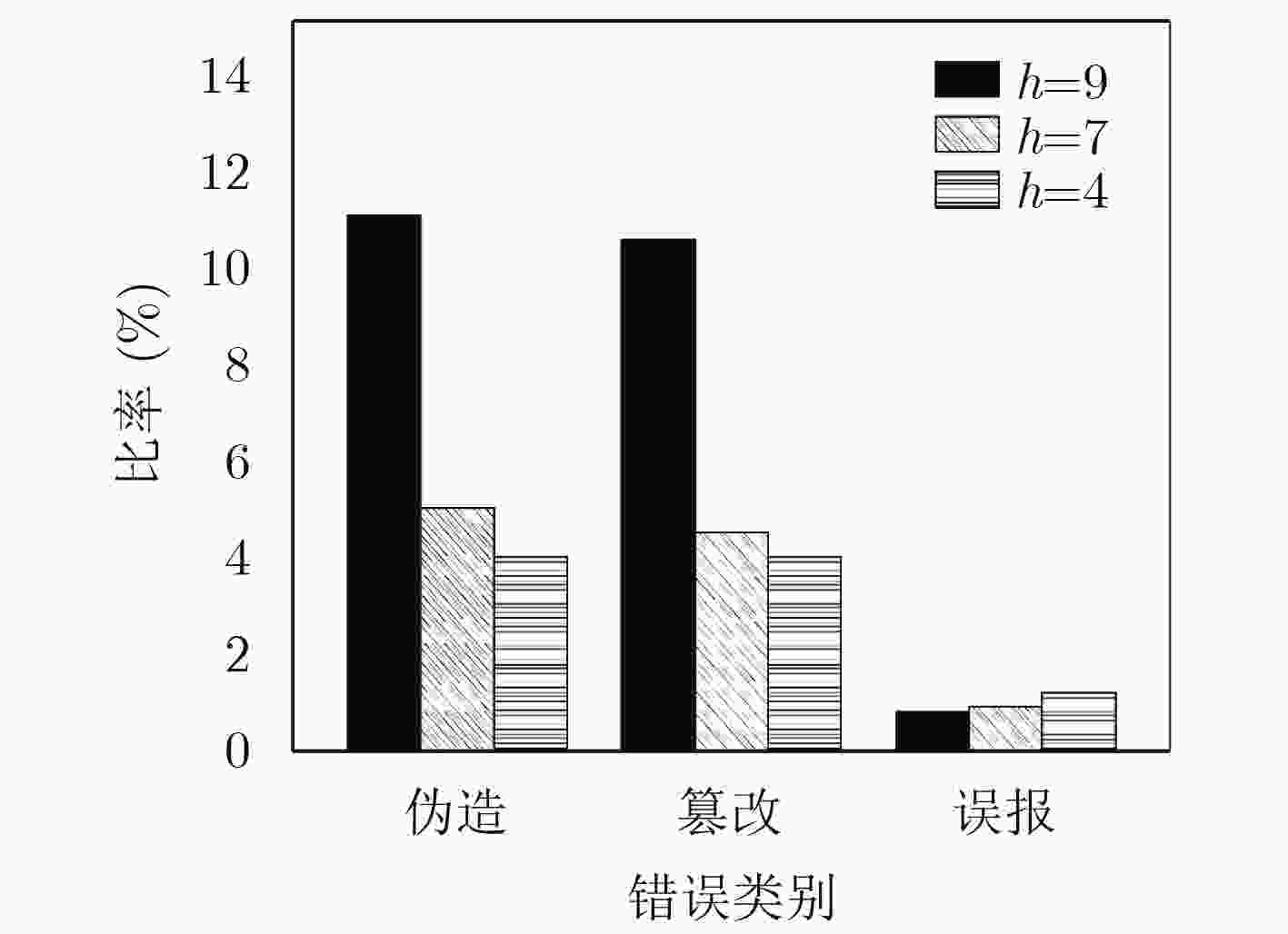
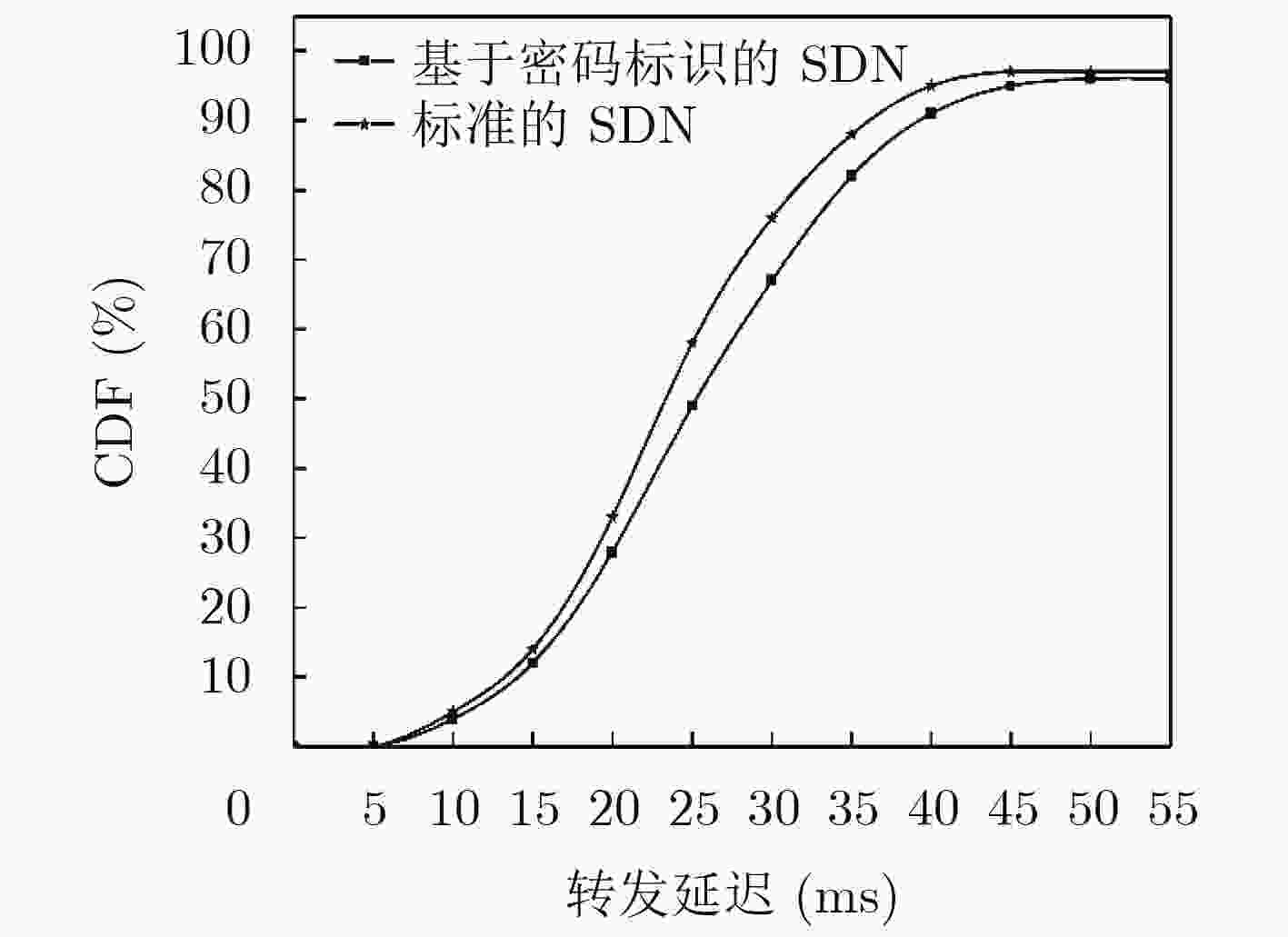
摘要: 针对软件定义网络(SDN)中缺乏安全高效的数据来源验证机制问题,该文提出基于密码标识的报文转发验证机制。首先,建立基于密码标识的报文转发验证模型,将密码标识作为IP报文进出网络的通行证。其次,设计SDN批量匿名认证协议,将SDN控制器的验证功能下放给SDN交换机,由SDN交换机进行用户身份验证和密码标识验证,快速过滤伪造、篡改等非法报文,提高SDN控制器统一认证与管理效率,同时可为用户提供条件隐私保护。提出基于密码标识的任意节点报文抽样验证方案,任何攻击者无法通过推断采样来绕过报文检测,确保报文的真实性的同时降低其处理延迟。最后,进行安全性分析和性能评估。结果表明该机制能快速检测报文伪造和篡改及抵抗ID分析攻击,但同时引入了大约9.6%的转发延迟和低于10%的通信开销。Abstract: To deal with the lack of a secure and efficient data source authentication mechanism in Software-Defined Network (SDN), a packet forwarding authentication mechanism based on cipher identification is proposed. Firstly, a packet forwarding authentication model based on cipher identification is established, where the cipher identification is identified as a passport of IP packets entering and leaving the network. Secondly, the SDN batch anonymous authentication protocol is designed to decentralize the authentication function of the SDN controller to the SDN switch. The SDN switch performs user authentication and cipher identification verification, and quickly filters forgery, falsification, and other illegal packets to improve the unified authentication and management efficiency of the SDN controller, while providing users with the conditions of privacy protection. Thirdly, a scheme for sampling and verifying packets based on cipher identification in any node is proposed, where any attacker can not bypass the packet detection by inferring the sample, to ensure the authenticity of the packet while reducing its processing delay. Finally, safety analysis and performance evaluation are conducted. The results show that this mechanism can quickly detect packet falsification and tampering and resist ID analysis attacks, but at the same time it introduces about 9.6% forwarding delay and less than 10% communication overhead.
-
表 1 任意节点报文抽样验证流表项生成算法
算法1 任意节点报文抽样验证流表项生成算法 输入:未匹配报文 ${P_i}$;检测因子h 输出:流表项;组表项;共享密钥 ${k_i}$ (1) ${\rm{PID}}_i \leftarrow {\rm{getPID}}\left( {{P_i}} \right)$; (2) ${\rm{SwitchID}} \leftarrow {\rm{getSwitchID}}\left( {{P_i}} \right)$; (3) ${\rm{SrcIP}}_i \leftarrow {\rm{getSrcIP}}\left( {{P_i}} \right)$; (4) ${\rm{RID}}_i \leftarrow {\rm{PID}}_i \oplus {H_0}\left( {b{W_i}} \right)$; (5) get ${\rm{Lifetime}}_i,{k_i}$ by querying ${L_c}$ according to ${\rm{RID}}_i$; (6) $\alpha = {\rm{ValidityCheck}}\left( {{\rm{Lifetime}}_i} \right)$; (7) if $\alpha = = 0$ /* ${\rm{RID}}_i$失效*/ (8) setFlowEntry (SwitchID; SrcIPi; drop); (9) else /* ${\rm{RID}}_i$有效*/ (10) select an optimized ${{\rm Path}_i}$ for unmatched packet ${P_i}$; (11) ${L_i} \leftarrow {\rm{getLength}}\left( {{\rm{Path}}_i} \right)$; (12) randomly select $x \in Z_q^ * $; (13) $k \leftarrow x\bmod {L_i}$; (14) for $j = {1_{}}{;_{}}j \le {L_i}_{}{;_{}}j + + $ (15) SwitchID $ \leftarrow {\rm{getSwitchID}}\left( {{\rm{Path}}\left( j \right)} \right)$; (16) if $j \ne k$ (17) setFlowEntry(SwitchID; Ci; Forward);/* ${C_i}$为匹配域
*/(18) else (19) SwitchID $ \leftarrow {\rm{getSwitchID}}\left( {{\rm{Path}}\left( k \right)} \right)$; (20) setFlowEntry(SwitchID; Ci; Group);/* ${C_i}$为匹配域*/ (21) setGroupTable(SwitchID; select; h; Forward,Verify-
MAC);(22) send ${k_i}$ to SwitchID by TLS; (23) end if (24)end if 表 2 交换机与主机数目表
网络符号 说明 网络拓扑结构 Fattree 核心交换机数目 64 聚集交换机数目 128 边界交换机数目 128 主机数目 512 表 3 认证开销
方案 参与方数量 通信开销 用户计算开销 SDN控制器(服务器)计算开销 SDN交换机计算开销 文献[18] 2 3|G|+4|ID|+2 $|Z_q^*|$ 7 ${T_{\rm em}}$+2 ${T_{\rm ea}}$ 5 ${T_{\rm em}}$+2 ${T_{\rm ea}}$ $\left( {3n + 1} \right){T_{\rm em}}$+ $\left( {4n - 1} \right){T_{\rm ea}}$ 文献[19] 2 2|G|+4|ID|+4 $|Z_q^*|$ 7 ${T_{\rm em}}$+ ${T_{\rm ea}}$ 7 ${T_{\rm em}}$+ ${T_{\rm ea}}$ – 本文方案 3 5|G|+3|ID|+2 $|Z_q^*|$ 5 ${T_{\rm em}}$+ ${T_{\rm ea}}$ 2 ${T_{\rm em}}$ – 注:“–”表示不存在该项,n为单位时间SDN交换机收到用户数目 -
MCKEOWN N. Software-defined networking[C]. IEEE International Conference on Computer Communications, Rio de Janeiro, Brazil, 2009: 30–32. NUNES B, MENDONCA M, NGUYEN X, et al. A survey of software-defined networking: Past, present, and future of programmable networks[J]. IEEE Communications Surveys&Tutorials, 2014, 16(3): 1617–1634 doi: 10.1109/SURV.2014.012214.00180 王蒙蒙, 刘建伟, 陈杰, 等. 软件定义网络: 安全模型、机制及研究进展[J]. 软件学报, 2016, 27(4): 969–992 doi: 10.13328/j.cnki.jos.005020WANG Mengmeng, LIU Jianwei, CHEN Jie, et al. Software defined networking: Security model, threats and mechanism[J]. Journal of Software, 2016, 27(4): 969–992 doi: 10.13328/j.cnki.jos.005020 LIU Hongqiang, WU Xin, ZHANG Ming, et al. zUpdate: Updating data center networks with zero loss[J]. Computer Communication Review, 2013, 43(4): 411–422 doi: 10.1145/2486001.2486005 LI Dan, SHANG Yunfei, and CHEN Congjie. Software defined green data center network with exclusive routing[C]. IEEE International Conference on Computer Communications, Toronto, Canada, 2014: 1743–1751. DHAWAN M, PODDAR R, MAHAJAN K, et al. SPHINX: Detecting security attacks in software-defined networks[C]. Network and Distributed System Security Symposium, San Diego, USA, 2015: 1–15. 李杰, 吴建平, 徐恪, 等. Hidasav: 一种层次化的域间真实源地址验证方法[J]. 计算机学报, 2012, 35(1): 85–100 doi: 10.3724/SP.J.1016.2012.00085LI Jie, WU Jianping, XU Ke, et al. An hierarchical inter-domain authenticated source address validation solution[J]. Chinese Journal of Computers, 2012, 35(1): 85–100 doi: 10.3724/SP.J.1016.2012.00085 YAO Guang, BI Jun, and XIAO Peiyao. Source address validation solution with OpenFlow/NOX architecture[C]. IEEE International Conference on Network Protocols, Vancouver, Canada, 2011: 7–12. 孙鹏. 面向SDN的源地址验证方法研究[J]. 电光与控制, 2016, 23(3): 49–53 doi: 10.3969/j.issn.1671-637X.2016.03.012SUN Peng. Source address validation methods based on SDN[J]. Electronics Optics&Control, 2016, 23(3): 49–53 doi: 10.3969/j.issn.1671-637X.2016.03.012 LIU Bingyang, BI Jun, and ZHOU Yu. Source address validation in software defined networks[C]. ACM Conference on SIGCOMM, Florianópolis, Brazil, 2016: 595–596. KIM H, BASESCU C, JIA L, et al. Lightweight source authentication and path validation[C]. ACM Conference on SIGCOMM, Chicago, USA, 2014: 271–282. TAKAYUKI S, CHRISTOS P, TAEHO L, et al. SDNsec: Forwarding accountability for the SDN data plane[C]. International Conference on Computer Communication and Networks, Hawaii, USA, 2016: 1–10. 陈越, 贾洪勇, 谭鹏许, 等. 基于流认证的IPv6接入子网主机源地址验证[J]. 通信学报, 2013, 34(1): 171–178 doi: 10.3969/j.issn.1000-436x.2013.01.019CHEN Yue, JIA Hongyong, TAN Pengxu, et al. Host’s source address verification based on stream authentication in the IPv6 access subnet[J]. Journal of Communications, 2013, 34(1): 171–178 doi: 10.3969/j.issn.1000-436x.2013.01.019 董平, 秦雅娟, 张宏科. 支持普适服务的一体化网络研究[J]. 电子学报, 2007, 35(4): 599–606DONG Ping, QIN Yajuan, and ZHANG Hongke. Research on universal network supporting pervasive services[J]. Acta Electronica Sinica, 2007, 35(4): 599–606 FARINACCI D, MEYER D, ZWIEBEL J, et al. The locator/id separation protocol (LISP) for multicast environments[S]. Internet Draft, draft-farinacci-lisp-15.txt, 2011. 许芷岩, 吴黎兵, 李莉, 等. 无线漫游认证中可证安全的无证书聚合签名方案[J]. 通信学报, 2017, 38(7): 123–130 doi: 10.11959/j.issn.1000-436x.2017152XU Zhiyan, WU Libing, LI Li, et al. Provably secure certificateless aggregate signature scheme in wireless roaming authentication[J]. Journal of Communications, 2017, 38(7): 123–130 doi: 10.11959/j.issn.1000-436x.2017152 HORNG S, TZENG S, PAN Y, et al. b-SPECS+: batch verification for secure pseudonymous authentication in VANET[J]. IEEE Transactions on Information Forensics&Security, 2013, 8(11): 1860–1875 doi: 10.1109/TIFS.2013.2277471 谢永, 吴黎兵, 张宇波, 等. 面向车联网的多服务器架构的匿名双向认证与密钥协商协议[J]. 计算机研究与发展, 2016, 53(10): 2323–2333 doi: 10.7544/issn1000-1239.2016.20160428XIE Yong, WU Libing, ZHANG Yubo, et al. Anonymous mutual authentication and key agreement protocol in multi-server architecture for VANETs[J]. Journal of Computer Research and Development, 2016, 53(10): 2323–2333 doi: 10.7544/issn1000-1239.2016.20160428 周彦伟, 杨波, 张文政. 一种改进的无证书两方认证密钥协商协议[J]. 计算机学报, 2017, 40(5): 1181–1191 doi: 10.11897/SP.J.1016.2017.01181ZHOU Yanwei, YANG Bo, and ZHANG Wenzheng. An improved two-party authenticated certificateless key agreement protocol[J]. Chinese Journal of Computers, 2017, 40(5): 1181–1191 doi: 10.11897/SP.J.1016.2017.01181 -





 下载:
下载:


 下载:
下载:
