Random Addition-chain Based Countermeasure Against Side-channel Attack for Advanced Encryption Standard
-
摘要:
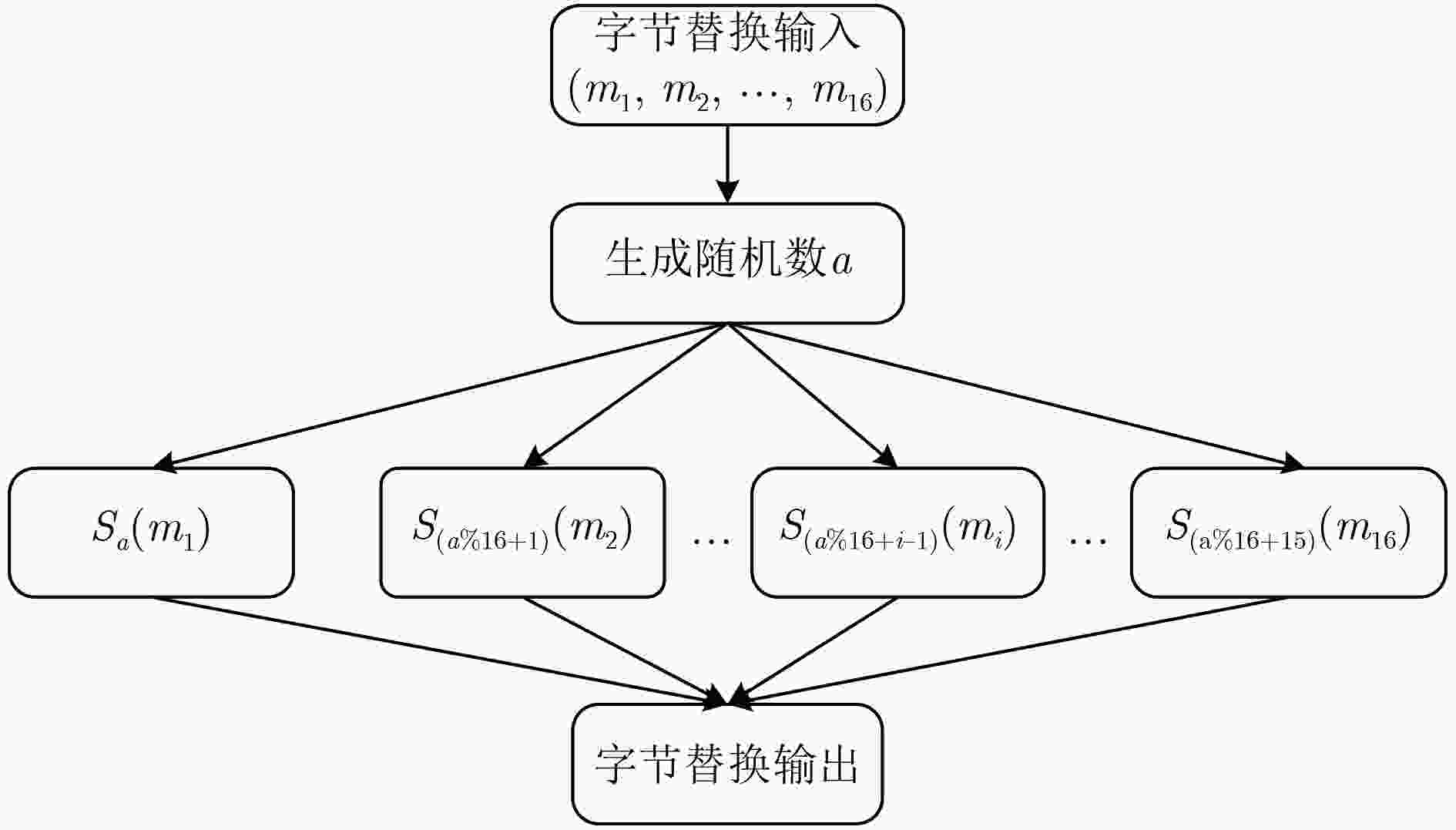
侧信道攻击已经对高级加密标准(AES)的硬件安全造成严重威胁,如何抵御侧信道攻击成为目前亟待解决的问题。字节替换操作作为AES算法中唯一的非线性操作,提高其安全性对整个加密算法有重要意义。该文提出一种基于随机加法链的AES抗侧信道攻击对策,该对策用随机加法链代替之前固定的加法链来实现有限域GF(28)上的乘法求逆操作,在此基础上研究随机加法链对算法安全性和有效性方面的影响。实验表明,所提随机加法链算法比之前固定的加法链算法在抵御侧信道攻击上更加安全、有效。
Abstract:Side channel attacks have serious threat to the hardware security of Advanced Encryption Standard (AES), how to resist the side channel attack becomes an urgent problem. Byte substitution operation is the only nonlinear operation in AES algorithm, so it is very important for the whole encryption algorithm to improve its security. In this paper, a countermeasure against side-channel attack is proposed based on random addition-chain for AES by replacing the fixed addition-chain with random addition-chain to realize the inverse operation of multiplication in a finite field GF(28). The impact of the random addition-chain on the security and effectiveness of the algorithm is studied. Experimental results show that the proposed random addition-chain based algorithm is more secure and effective than the previous fixed addition-chain based algorithms in defending against side channel attacks.
-
表 1 16条不同功耗特性的加法链
序号 加法链路径 (1) 1→2→4→8→16→32→64→80→84→168→252→254 (2) 1→2→4→8→16→32→64→80→84→86→168→254 (3) 1→2→4→8→16→32→48→50→100→200→250→254 (4) 1→2→4→8→16→32→48→50→100→102→204→254 (5) 1→2→4→8→16→32→48→50→54→100→200→254 (6) 1→2→4→8→16→32→40→80→84→168→252→254 (7) 1→2→4→8→16→32→40→80→84→86→168→254 (8) 1→2→4→8→16→32→40→42→84→126→127→254 (9) 1→2→4→8→16→32→40→42→43→84→ 127→254 (10) 1→2→4→8→16→32→36→72→144→216→252→254 (11) 1→2→4→8→16→24→40→50→100→200→250→254 (12) 1→2→4→8→16→24→48→50→100→102→204→254 (13) 1→2→4→8→16→24→48→50→54→100→200→254 (14) 1→2→4→8→16→24→28→56→112→224→252→254 (15) 1→2→4→8→16→24→28→56→112→113→226→254 (16) 1→2→4→8→16→24→28→30→56→112→224→254 表 2 随机数生成算法
将包含1~16的数组完全打乱 输入:a[16]={1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16} 输出:1~16随机排列后的数组 (1)srand((unsigned)time(NULL))/*随机数发生器的初始函数*/ (2)int i,j,temp (3)for i from 16 to 1 do /*i 从16递减到1 */ (4)j=rand()%(i+1) /*生成0~i的随机数*/ (5)Temp=a[j] /*交换数组中第i+1个数和第j+1个数*/ (6)a[j]=a[i] (7)a[i]=temp (8)end for 表 3 不同方案的不同模块的面积比较
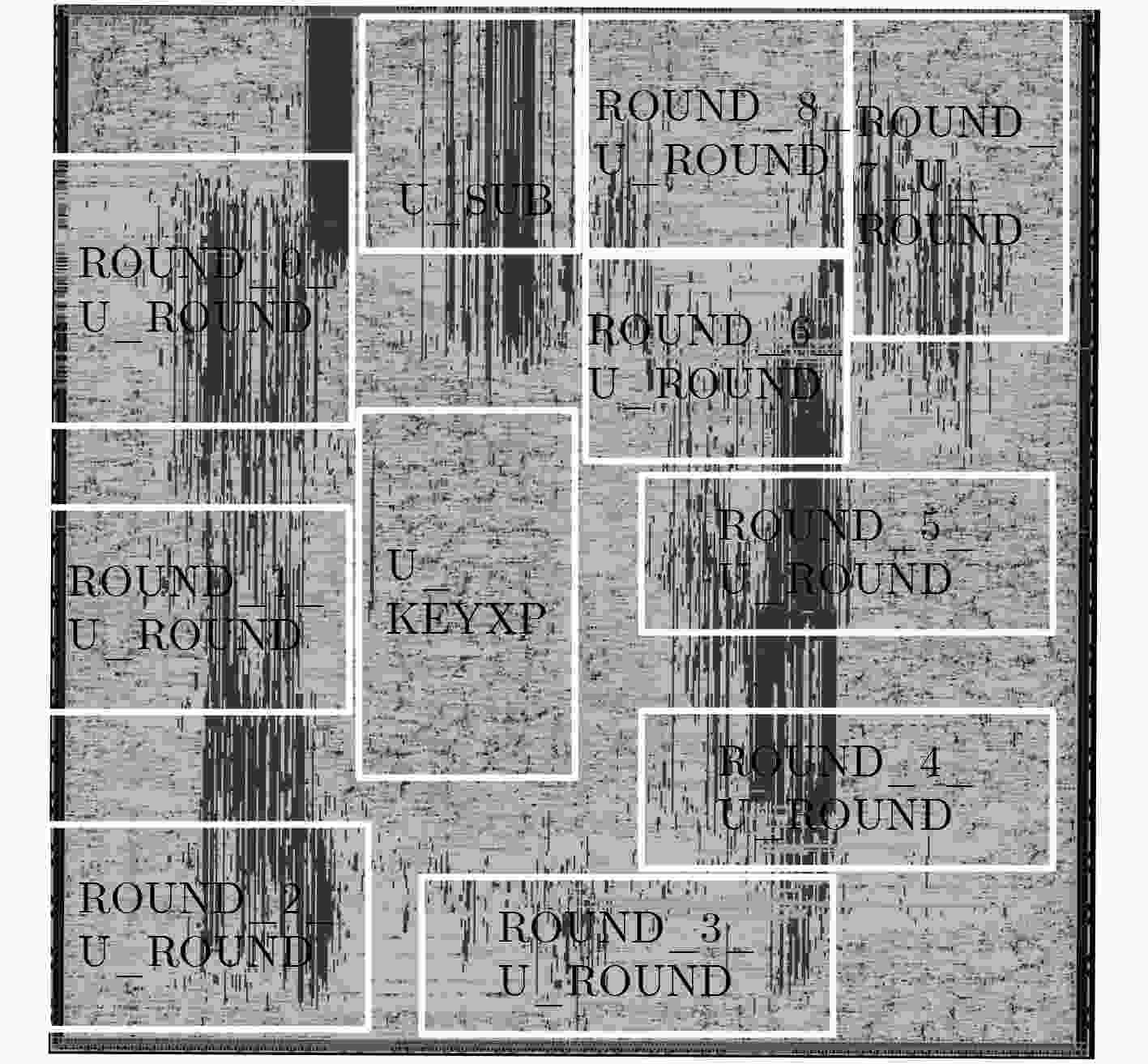
方案 组合面积(kGE) 非组合面积(kGE) 网络互连面积(kGE) 总面积(kGE) 字节替换 行移位 列混合 密钥加 密钥扩展 标准AES 1067 32 149 66 1190 854 46 3404 文献[7]方案 2179 32 149 66 2328 675 26 5441 循环调用加法链 2162 32 149 66 2320 675 20 5424 乱序调用加法链 2165 32 149 66 2344 675 21 5452 -
STANDAERT F X. Introduction to Side-channel Attacks[M]. Secure Integrated Circuits and Systems, Boston: Springer, 2010: 27–42. CORON J S. Higher order masking of look-up tables[C]. 33rd Annual International Conference on the Theory and Applications of Cryptographic Techniques, Copenhagen, Denmark, 2014: 441–458. 刘国强, 金晨辉. 一类动态S盒的构造与差分性质研究[J]. 电子与信息学报, 2014, 36(1): 74–81. doi: 10.3724/SP.J.1146.2013.00416LIU Guoqiang and JIN Chenhui. Investigation on construction and differential property of a class of dynamic S-box[J]. Journal of Electronics &Information Technology, 2014, 36(1): 74–81. doi: 10.3724/SP.J.1146.2013.00416 臧鸿雁, 黄慧芳. 基于均匀化混沌系统生成S盒的算法研究[J]. 电子与信息学报, 2017, 39(3): 575–581. doi: 10.11999/JEIT160535ZANG Hongyan and HUANG Huifang. Research on algorithm of generating S-box based on uniform chaotic system[J]. Journal of Electronics &Information Technology, 2017, 39(3): 575–581. doi: 10.11999/JEIT160535 钟卫东, 孟庆全, 张帅伟, 等. 基于秘密共享的AES的S盒实现与优化[J]. 工程科学与技术, 2017, 49(1): 191–196. doi: 10.15961/j.jsuese.2017.01.025ZHONG Weidong, MENG Qingquan, ZHANG Shuaiwei, et al. Implementation and optimization of S-box on AES based on secret sharing[J]. Advanced Engineering Sciences, 2017, 49(1): 191–196. doi: 10.15961/j.jsuese.2017.01.025 张伟, 高俊雄, 王耕波, 等. 一种优化的AES算法及其FPGA实现[J]. 计算机与数字工程, 2017, 45(1): 502–505. doi: 10.3969/j.issn.1672-9722.2017.03.020ZHANG Wei, GAO Junxiong, WANG Yunbo, et al. An optimized AES algorithm and its FPGA implementation[J]. Computer &Digital Engineering, 2017, 45(1): 502–505. doi: 10.3969/j.issn.1672-9722.2017.03.020 RIVAIN M and PROUFF E. Provably secure higher-order masking of AES[C]. Cryptographic Hardware and Embedded Systems, Santa Barbara, USA, 2010: 413–427. CARLET C, GOUBIN L, PROUFF E, et al. Higher-order masking schemes for s-boxes[C]. International Conference on FAST Software Encryption, Washington, DC, USA, 2012: 366–384. ROY A and VIVEK S. Analysis and improvement of the generic higher-order masking scheme of FSE 2012[C]. Cryptographic Hardware and Embedded Systems-CHES 2013, Santa Barbara, USA, 2013: 417–434. CORON J S, PROUFF E, RIVAIN M, et al. Higher-order side channel security and mask refreshing[C]. International Workshop on Fast Software Encryption 2013, Singapore, 2013: 410–424. 王晓东. 最短加法链算法[J]. 小型微型计算机系统, 2001, 22(10): 1250–1253. doi: 10.3969/j.issn.1000-1220.2001.10.026WANG Xiaodong. Shortest addition chain algorithm[J]. Mini-Micro System, 2001, 22(10): 1250–1253. doi: 10.3969/j.issn.1000-1220.2001.10.026 刘艳萍, 李秋慧. AES算法的研究与其密钥扩展算法改进[J]. 现代电子技术, 2016, 39(10): 5–8. doi: 10.16652/j.issn.1004-373x.2016.10.002LIU Yanping and LI Qiuhui. Analysis of AES algorithm and its key extension algorithm improvement[J]. Modern Electronics Technique, 2016, 39(10): 5–8. doi: 10.16652/j.issn.1004-373x.2016.10.002 OSWALD E, MANGARD S, PRAMSTALLER N, et al. A side-channel analysis resistant description of the AES S-box[C]. International Workshop on Fast Software Encryption 2005, Paris, France, 2005: 413–423. 夏克维, 李冰. AES算法中S-box和列混合单元的优化及FPGA实现[J]. 现代电子技术, 2009, 32(24): 11–14. doi: 10.16652/j.issn.1004-373x.2009.24.029XIA Kewei and LI Bing. Optimization of S-box and Mixcolumn blocks in AES encryption algorithm and FPGA implementation[J]. Modern Electronics Technique, 2009, 32(24): 11–14. doi: 10.16652/j.issn.1004-373x.2009.24.029 崔琦, 王思翔, 段晓毅, 等. 一种AES算法的快速模板攻击方法[J]. 计算机应用研究, 2017, 34(6): 1801–1804. doi: 10.3969/j.issn.1001-3695.2017.06.045CUI Qi, WANG Sixiang, DUAN Xiaoyi, et al. Fast template DPA attack against AES algorithm[J]. Application Research of Computers, 2017, 34(6): 1801–1804. doi: 10.3969/j.issn.1001-3695.2017.06.045 王建新, 方华威, 段晓毅, 等. 基于滑动平均的能量分析攻击研究与实现[J]. 电子与信息学报, 2017, 39(5): 1256–1260. doi: 10.11999/JEIT160637WANG Jianxin, FANG Huawei, DUAN Xiaoyi, et al. Research and implementation of power analysis based on moving average[J]. Journal of Electronics &Information Technology, 2017, 39(5): 1256–1260. doi: 10.11999/JEIT160637 段晓毅, 王思翔, 崔琦, 等. 一种带掩码AES算法的高阶差分功耗分析攻击方案[J]. 计算机工程, 2017, 43(10): 120–125. doi: 10.3969/j.issn.1000-3428.2017.10.021DUAN Xiaoyi, WANG Sixiang, CUI Qi, et al. A high-order differential power analysis attack scheme with masked AES algorithm[J]. Computer Engineering, 2017, 43(10): 120–125. doi: 10.3969/j.issn.1000-3428.2017.10.021 ISHAI Y, SAHAI A, and WAGNER D. Private circuits: Securing hardware against probing attacks[C]. CRYPTO 2003: Advances in Cryptology – CRYPTO, Santa Barbara, USA, 2003: 463–481. ZHANG Xinmiao and PARHI K K. High-speed VLSI architectures for the AES algorithm[J]. IEEE Transactions on Very Large Scale Integration Systems, 2004, 12(9): 957–967. doi: 10.1109/TVLSI.2004.832943 JUNGK B, STÖTTINGER M, GAMPE J, et al. Side-channel resistant AES architecture utilizing randomized composite field representations[C]. International Conference on Field-Programmable Technology, Seoul, Korea, 2012: 125–128. BONNECAZE A, LIARDET P, and VENELLI A. AES side-channel countermeasure using random tower field constructions[J]. Designs, Codes and Cryptography, 2013, 69(3): 331–349. doi: 10.1007/s10623-012-9670-x -





 下载:
下载:



 下载:
下载:
