|
李杰, 宫二玲, 孙志强, 等. 下一代机载网络技术评述[J]. 指挥与控制学报, 2015, 1(3): 351–356. DOI: JCC.CN.2015.00351.LI Jie, GONG Erling, SUN Zhiqiang, et al.. An overview of next generation airborne networks[J]. Journal of Command and Control, 2015, 1(3): 351–356. DOI: JCC.CN.2015.00351.
|
|
梁一鑫, 程光, 郭晓军, 等. 机载网络体系结构及其协议栈研究进展[J]. 软件学报, 2016, 27(1): 96–111.DOI: 10.13328/j.cnki.jos.004925.LIANG Yixin, CHENG Guang, GUO Xiaojun, et al.. Research progress on architecture and protocol stack of the airborne network[J]. Journal of Software, 2016, 27(1): 96–111. DOI: 10.13328/j.cnki.jos.004925.
|
|
SHANTHI K and MURUGAN D. Pair-wise key agreement and hop-by-hop authentication protocol for MANET[J]. Wireless Networks, 2016, 23(4): 1–9.DOI: 10.1007/s11276-015-1191-x.
|
|
PHUNG P H and MINH Q T. DASSR: A distributed authentication scheme for secure routing in wireless ad-hoc networks[C]. International Conference on Future Data and Security Engineering. Can Tho, Vietnam, 2016: 219–236.
|
|
DONG Ying, SUI Aifeng, YIU S M, et al.. Providing distributed certificate authority service in cluster-based mobile ad hoc networks[J]. Computer Communications, 2007, 30(11/12): 2442–2452. doi: 10.1016/j.comcom.2007.04.011.
|
|
韩磊, 刘吉强, 赵佳, 等. 移动ad hoc网络分布式轻量级CA 密钥管理方案[J].四川大学学报(工程科学版), 2011, 43(6): 133–139.DOI: 10.15961/j.jsuese.2011.06.021.HAN Lei, LIU Jiqiang, ZHAO Jia, et al..Distributed lite CA key management scheme in mobile ad hoc networks[J].Journal of Sichuan University (Engineering Science Edition), 2011, 43(6): 133–139. doi: 10.15961/j.jsuese.2011.06.021.
|
|
DATKO B. Supporting secure, ad hoc joins for tactical networks[R]. Maryland: United States Naval Academy Trident Scholar Project Report, 2002.
|
|
CAPKUN S, NUTTYAN L, and HUBAUX J P. Self-organized public-key management for mobile ad hoc networks[J]. IEEE Transactions on Mobile Computing, 2003, 2(1): 52–64. DOI: 10.1109/TMC.2003.1195151.
|
|
RAFSANJANI M K and SHOJAIEMEHR B. Improvement of self-organized public key management for MANET[J]. Journal of American Science, 2012, 8(1): 197–202.
|
|
JANANI V S and MANIKANDAN M S K. Trust-based hexagonal clustering for efficient certificate management scheme in mobile ad hoc networks[R]. Sadhana, 2016.
|
|
OMAR M, BOUFAGHES H, MAMMERI L, et al.. Secure and reliable certificate chains recovery protocol for mobile ad hoc networks[J]. Journal of Network & Computer Applications, 2016, 62(C): 153-162. DOI: 10.1016/j.jnca.2016.01.007
|
|
SHAMIR. Identity-based cryptosystems and signature schemes[J]. LNCS, 1984, 21(2): 47–53.DOI: 10.1007/3-540-39568-7 5.
|
|
BONEH D and FRANKLIN M. Identity-based encryption from the weil pairing[C]. International Cryptology Conference on Advances in Cryptology. Santa Barbara, USA, 2001: 213–229.
|
|
曹丹, 王小峰, 王飞, 等. SA-IBE: 一种安全可追责的基于身份加密方案[J].电子与信息学报, 2011, 33(12): 2922–2928.DOI: 10.3724/SP.J.1146.2011.00399.CAO Dan, WANG Xiaofeng, WANG Fei, et al.. SA-IBE: A secure and accountable identity-based encryption scheme[J] Journal of Electronics & Information Technology, 2011, 33(12): 2922–2928. doi: 10.3724/SP.J.1146.2011.00399.
|
|
ZHANG Tao, YUE Kang, and YAN Jinkui. A distributed anonymous authentication scheme for mobile ad hoc network from bilinear maps[C]. International Conference on Mechatronic Science, Electric Engineering and Computer. Jilin, China, 2011: 314–318.
|
|
NARAYANA V L and BHARATHI C R. Identity based cryptography for mobile ad hoc networks[J]. Journal of Theoretical and Applied Information Technology, 2017, 95(5): 1173–1182.
|
|
罗长远, 李伟, 邢洪智, 等. 空间网络中基于身份的分布式密钥管理研究[J].电子与信息学报, 2010, 32(1): 183–188.DOI: 10.3724/SP.J.1146.2009.00461.LUO Changyuan, LI Wei, XING Hongzhi, et al.. Research on identity-based distributed key management in space network[J]. Journal of Electronics & Information Technology, 2010, 32(1): 183–188. doi: 10.3724/SP.J.1146.2009.00461.
|
|
XIA Pengrui, WU Meng, WANG Kun, et al. Identity-based fully distributed certificate authority in an OLSR MANET[C]. International Conference on Wireless Communications, Networking and Mobile Computing. Dalian, China, 2008: 1–4.
|
|
任艳丽, 蔡建兴, 黄春水, 等.基于身份加密中可验证的私钥生成外包算法[J].通信学报, 2015, 36(11): 61-66. DOI: 10.11959/j.issn.1000-436x.2015233.REN Yanli, CAI Jianxing, HUANG Chunshui, et al.. Verifiable outsourcing private key generation algorithm in an identity-based encryption scheme[J]. Journal of Communications, 2015, 36(11): 61–66. DOI: 10.11959/j.issn.1000-436x.2015233.
|
|
李慧贤, 庞辽军, 王育民. 适合ad hoc网络无需安全信道的密钥管理方案[J].通信学报, 2010, 31(1): 112–117.LI Huixian, PANG Liaojun, and WANG Yumin. Key management scheme without secure channel for ad hoc networks[J]. Journal of Communications, 2010, 31(1): 112–117.
|





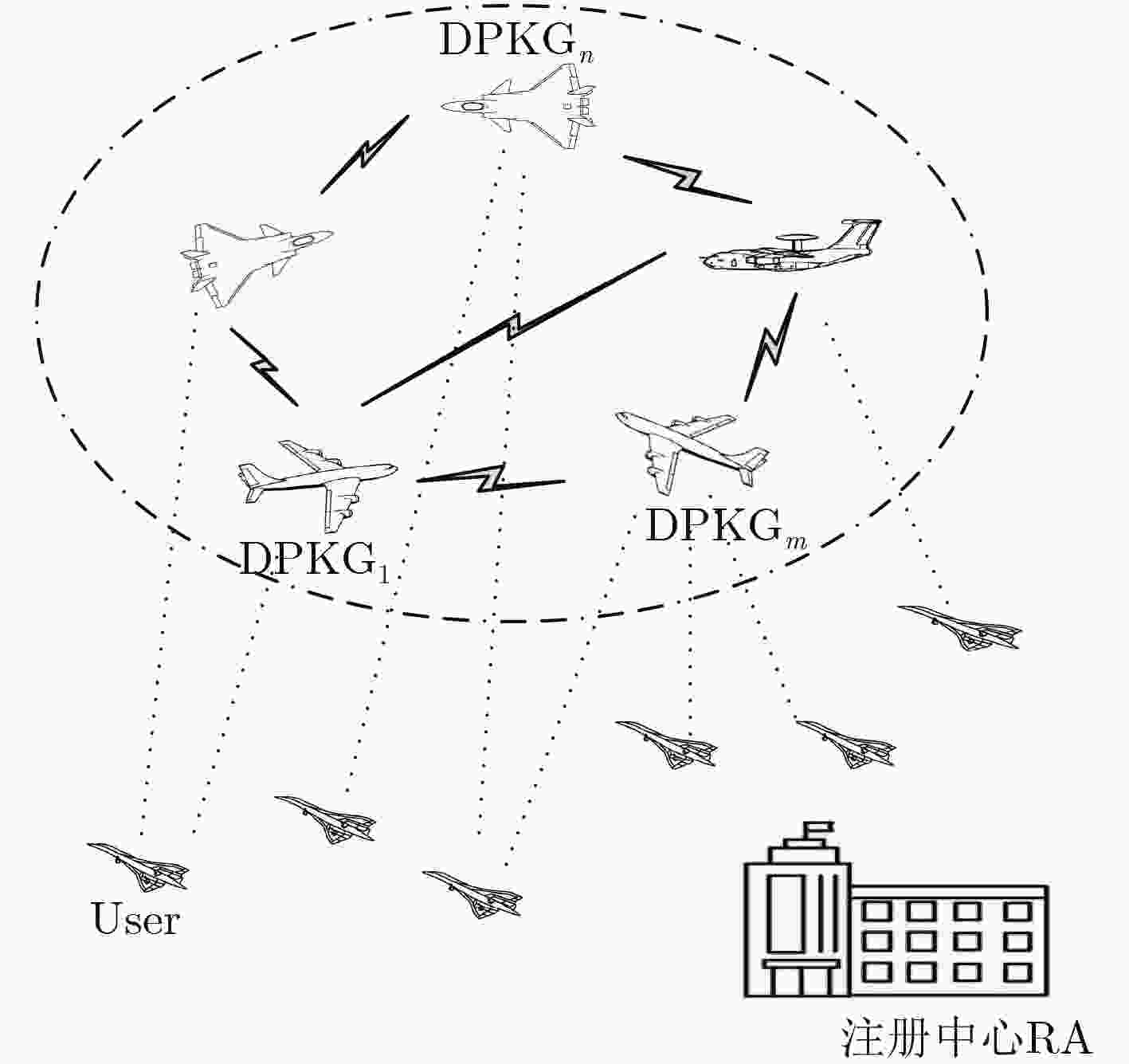
 下载:
下载:
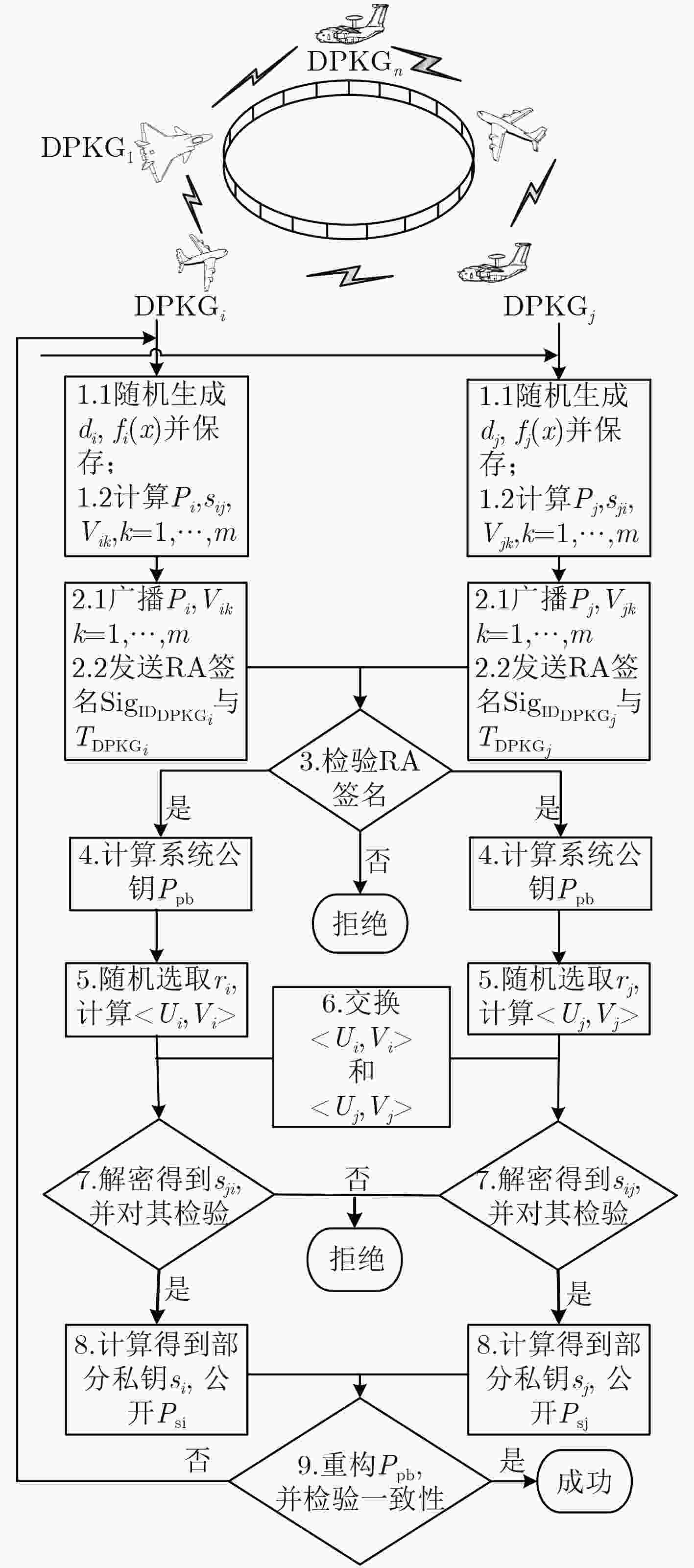
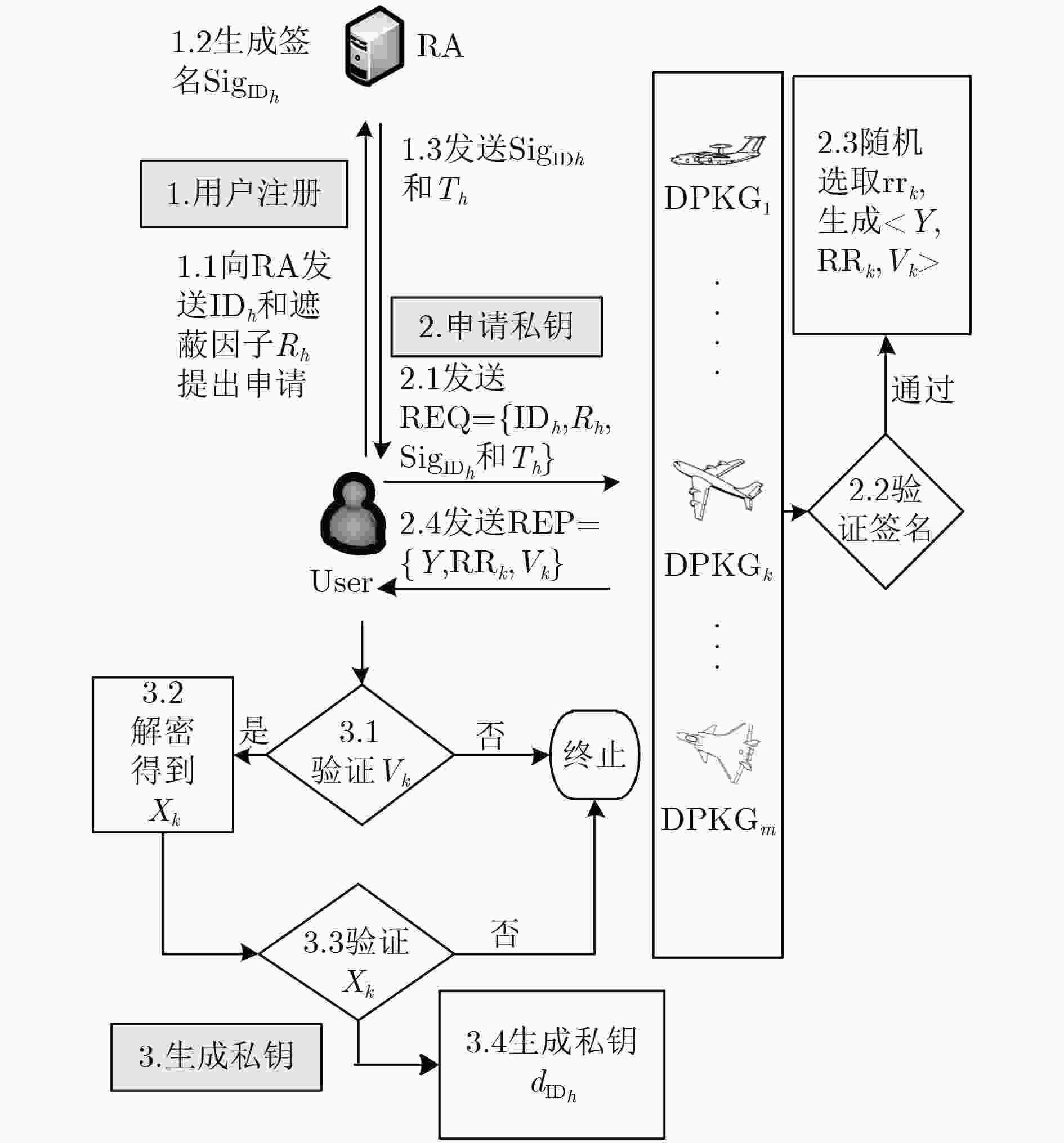


 下载:
下载:
