|
ZOU Yulong, ZHU Jia, WANG Xinbin, et al. A survey on wireless security: Technical challenges, recent advances, and future trends[J]. Proceedings of the IEEE, 2016, 104(9): 1727–1765 doi: 10.1109/JPROC.2016.2558521
|
|
XIAO Shuaifang, GUO Yunfei, HUANG Kaizhi, et al. High-rate secret key generation aided by multiple relays for Internet of things[J]. Electronics Letters, 2017, 53(17): 1198–1200 doi: 10.1049/el.2017.2346
|
|
ZHANG Yingxian, YANG Zhen, LIU Aijun, et al. Secure transmission over the wiretap channel using polar codes and artificial noise[J]. IET Communications, 2017, 11(3): 377–384 doi: 10.1049/iet-com.2016.0429
|
|
白慧卿, 金梁, 肖帅芳, 等. 多天线系统中面向物理层安全的极化编码方法[J]. 电子与信息学报, 2017, 39(11): 2587–25931 doi: 10.11999/JEIT170068BAI Huiqing, JIN Liang, XIAO Shuaifang, et al. Polar codes for physical layer security in multi-antenna systems[J]. Journal of Electronics&Information Technology, 2017, 39(11): 2587–25931 doi: 10.11999/JEIT170068
|
|
OZAROW L H and WYNER A D. Wire-tap channel II[J]. AT&T Bell System Technical Journal, 1984, 63(10): 2135–2137.
|
|
CASSITO Y and BANDIC Z. Low complexity wiretap codes with security and error-correction guarantees [C]. IEEE Information Theory Workshop, Dublin, Ireland, 2010: 1–5.
|
|
BELFIORE J C and OGGIER F. Lattice codes design for the Rayleigh fading wire-tap channel [C]. IEEE International Conference on Communications Workshops, Kyoto, Japan, 2011: 1–5.
|
|
ARIKAN E. Channel polarization: A method for constructing capacity-achieving codes for symmetry binary-input memoryless channels[J]. IEEE Transactions on Information Theory, 2009, 55(7): 3051–3073 doi: 10.1109/TIT.2009.2021379
|
|
MAHDAVIFAR H and VARDY A. Achieving the secrecy capacity of wiretap channels using polar codes[J]. IEEE Transactions on Information Theory, 2011, 57(10): 6428–6443 doi: 10.1109/TIT.2011.2162275
|
|
SASOGLU E and VARDY A. A new polar coding scheme for strong security on wiretap channels[C]. IEEE Internationnal Symposium on Information Theory Proceedings (ISIT), Istanbul, Turkey, 2013: 1117–1121.
|
|
MIRGHASEMI H and BELFIORE J. The un-polarized bit-channels in the wiretap polar coding scheme [C]. International Conference on Wireless Communications, Vehicular Technology, Information Theory and Aerospace & Electronic Systems, Manchester, Denmark, 2014: 1-5.
|
|
SERRANO R B, THOBABEN R, ANDERSSON M, et al. Polar codes for cooperative relaying[J]. IEEE Transactions on Communications, 2012, 60(11): 3263–3273 doi: 10.1109/TCOMM.2012.081412.110266
|
|
DUO Bin, WANG Peng, LI Yonghui, et al. Secure transmission for relay-eavesdropper channels using polar coding [C]. IEEE International Conference on Communications, Sydney, Australia, 2014: 2197–2202.
|
|
DUO Bin, ZHONG Xiaoling, and GUO Yong. Practical polar code construction for degraded multiple-relay networks[J]. China Communications, 2017, 14(4): 127–139 doi: 10.1109/CC.2017.7927571
|
|
KARAS D S, PAPPI K N, and KARAGIANNIDIS G K. Smart decode-and-forward relaying with polar codes[J]. IEEE Wireless Communications Letters, 2014, 3(1): 62–65 doi: 10.1109/WCL2013.111213.130639
|
|
SOLIMAN T, YANG F, EJAZ S, et al. Decode and forward polar coding scheme for receive diversity: A relay partially perfect retransmission for half-duplex wireless relay channels[J]. IET Communications, 2017, 11(2): 185–191 doi: 10.1049/iet-com.2016.0915
|
|
SI Hongbo, KOYLUOGLU O O, and VISHWANATH S. Hierarchical polar coding for achieving secrecy over state-dependent wiretap channels without any instantaneous CSI[J]. IEEE Transactions on Communications, 2016, 64(9): 3609–3623 doi: 10.1109/TCOMM.2016.2592523
|





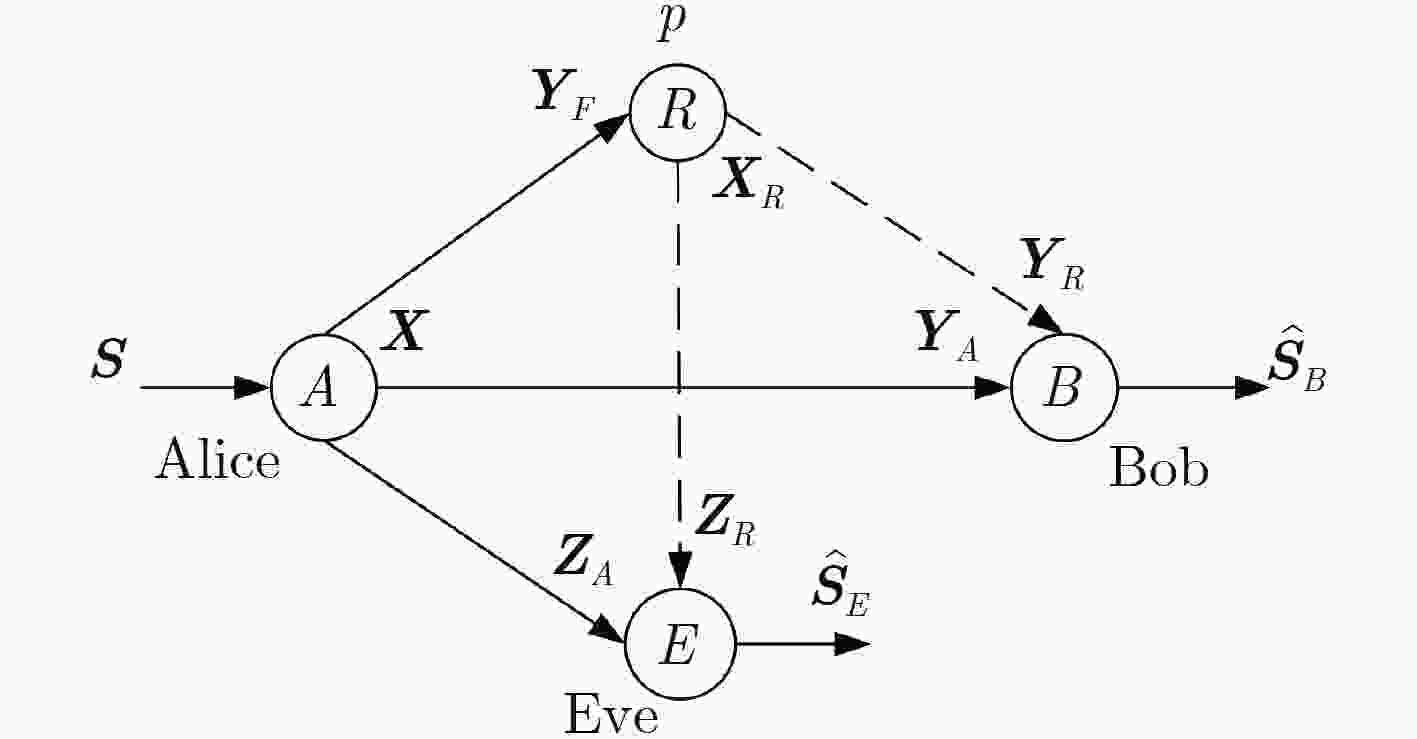
 下载:
下载:
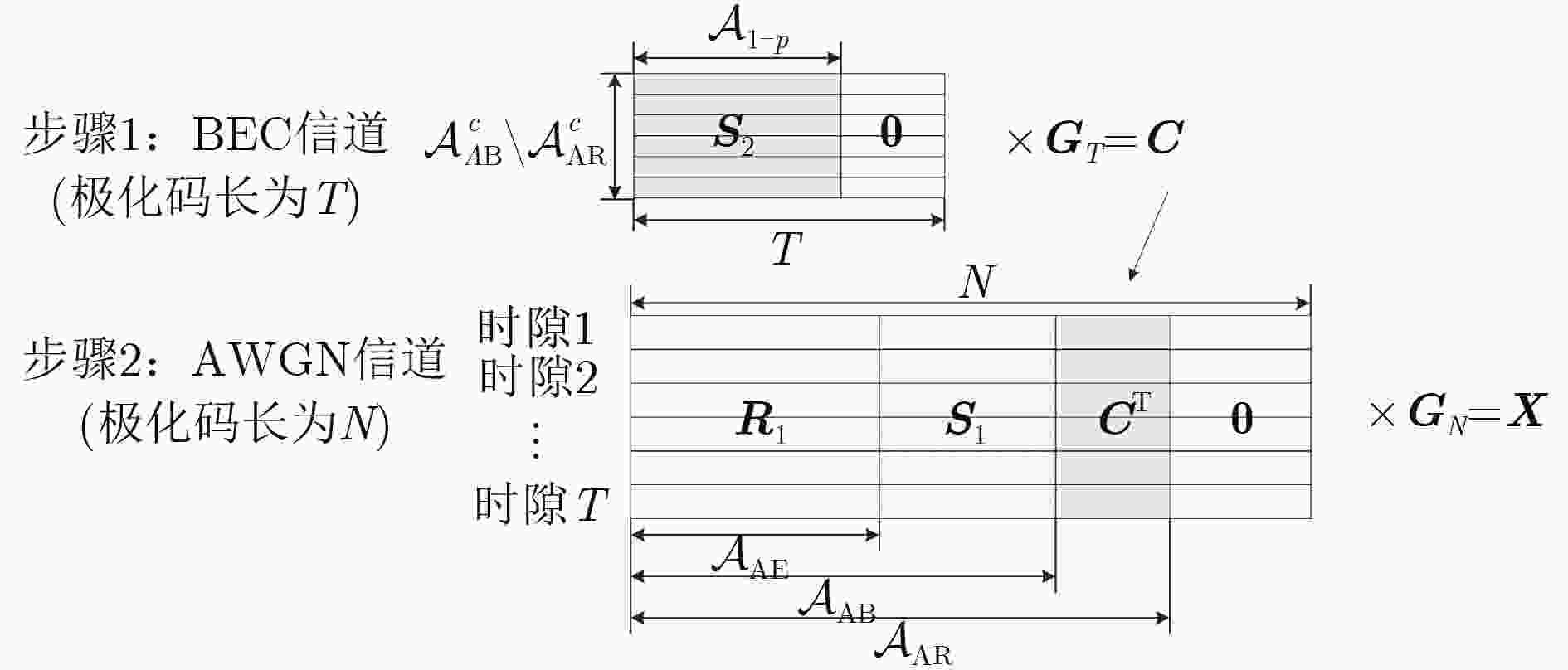
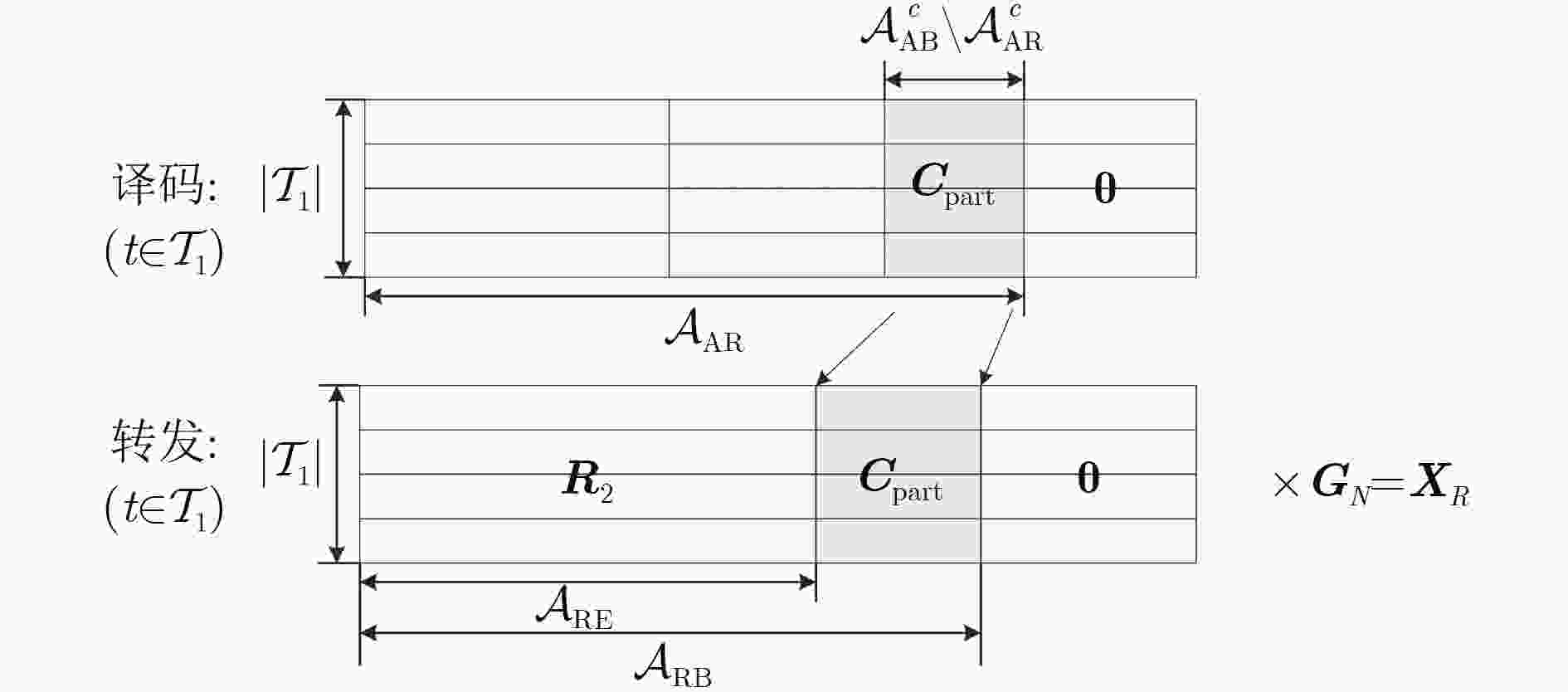

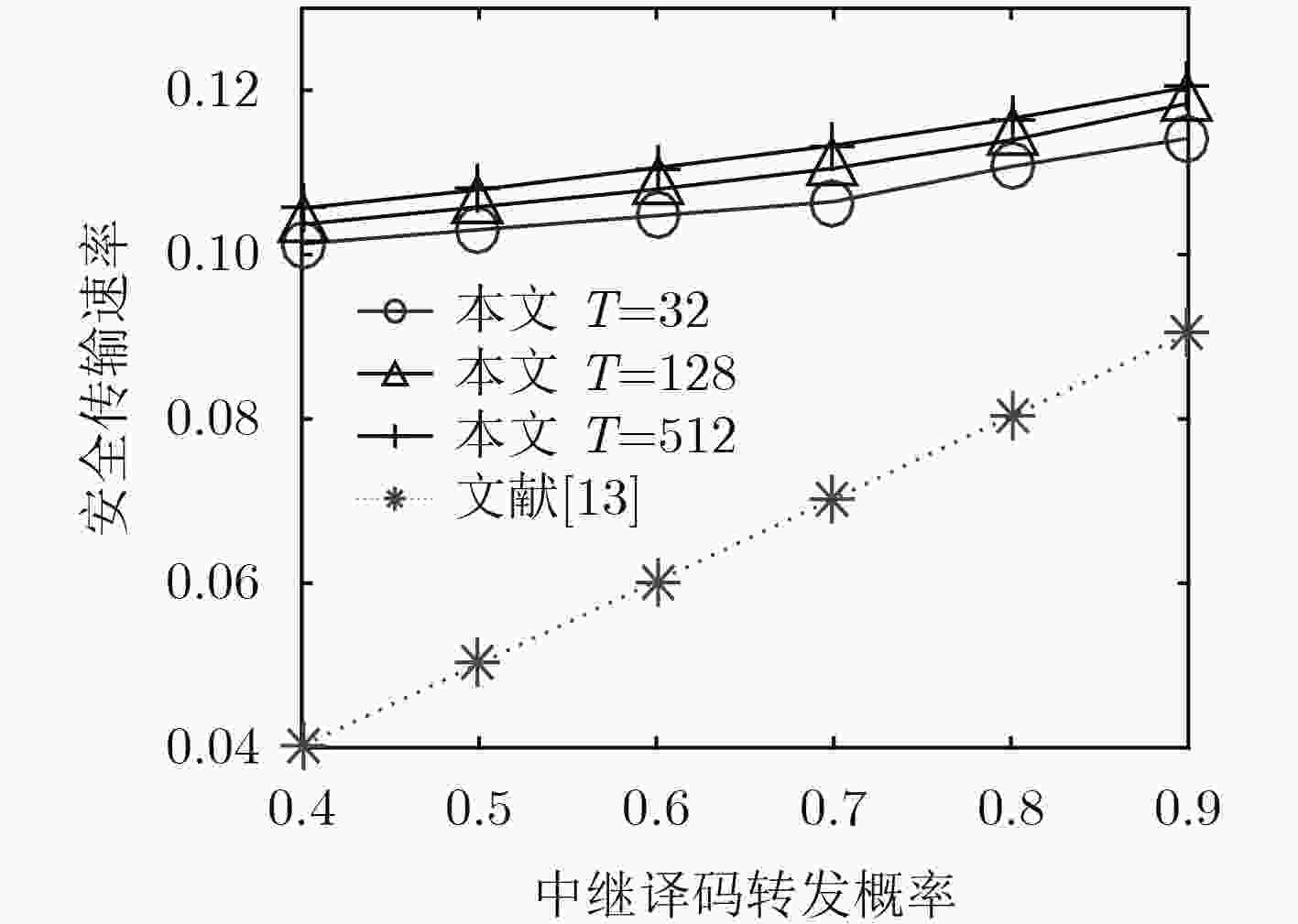

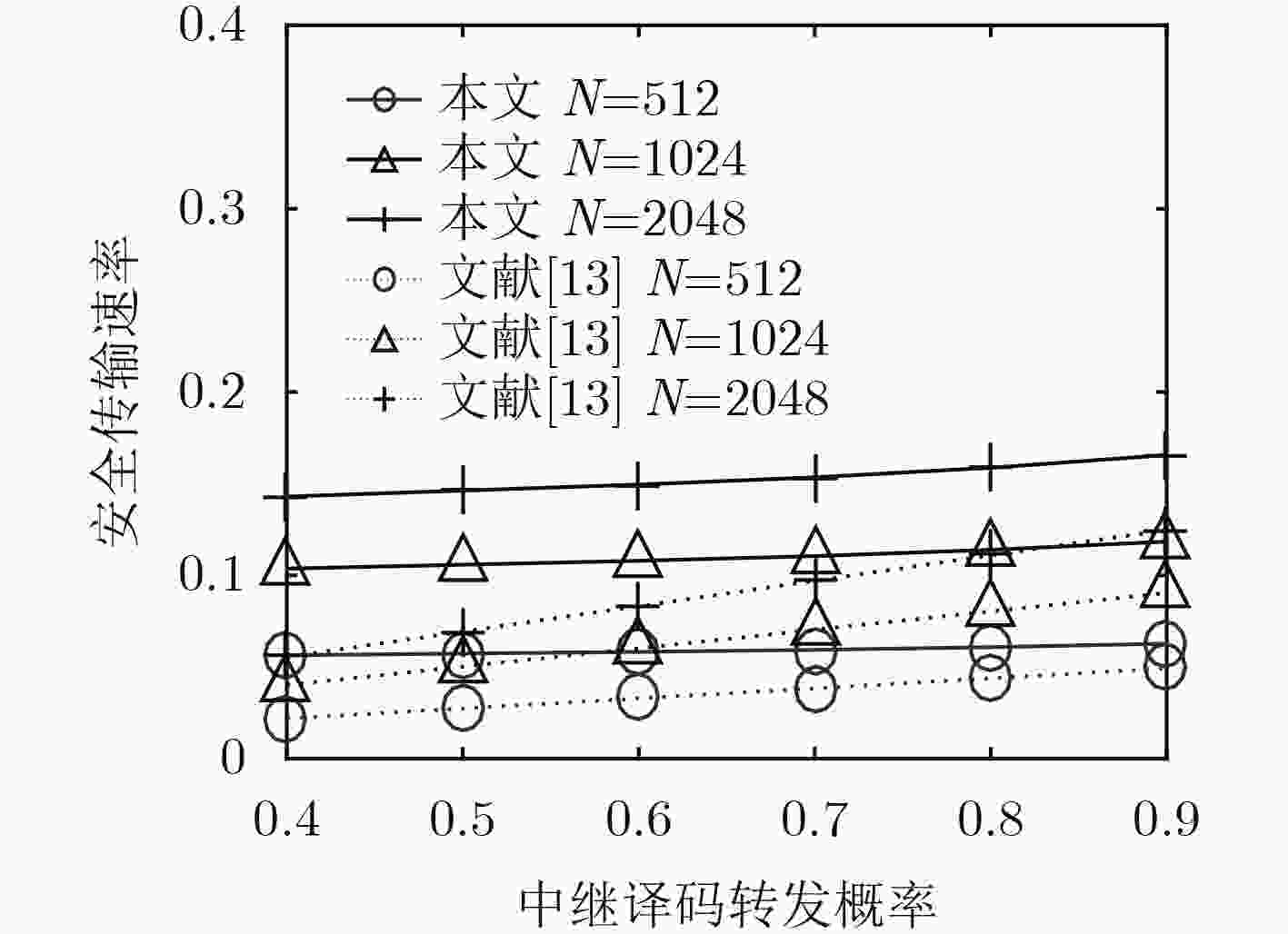
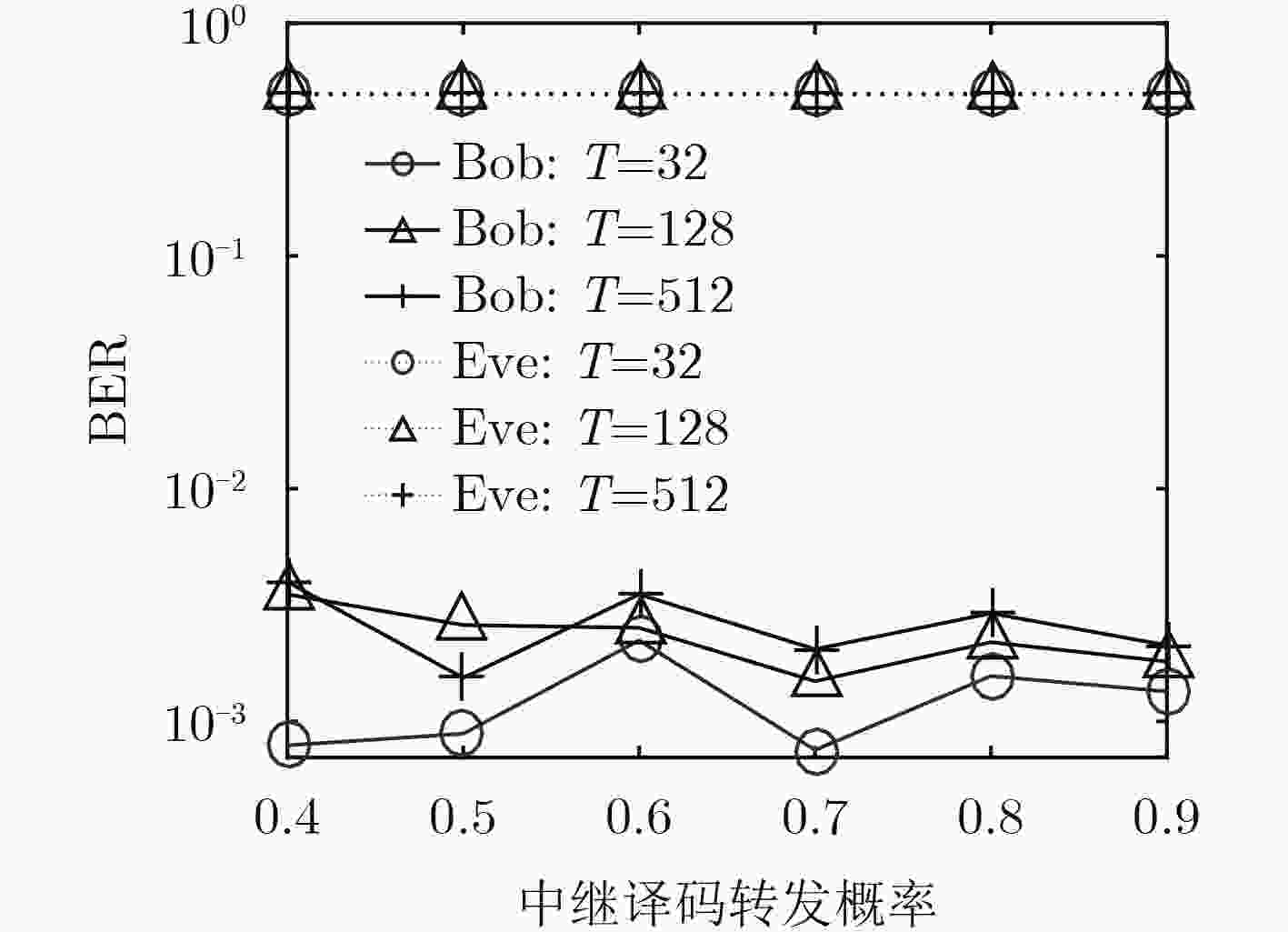


 下载:
下载:
