Privacy Preserving Method Based on Location Service in Personalized Search
-
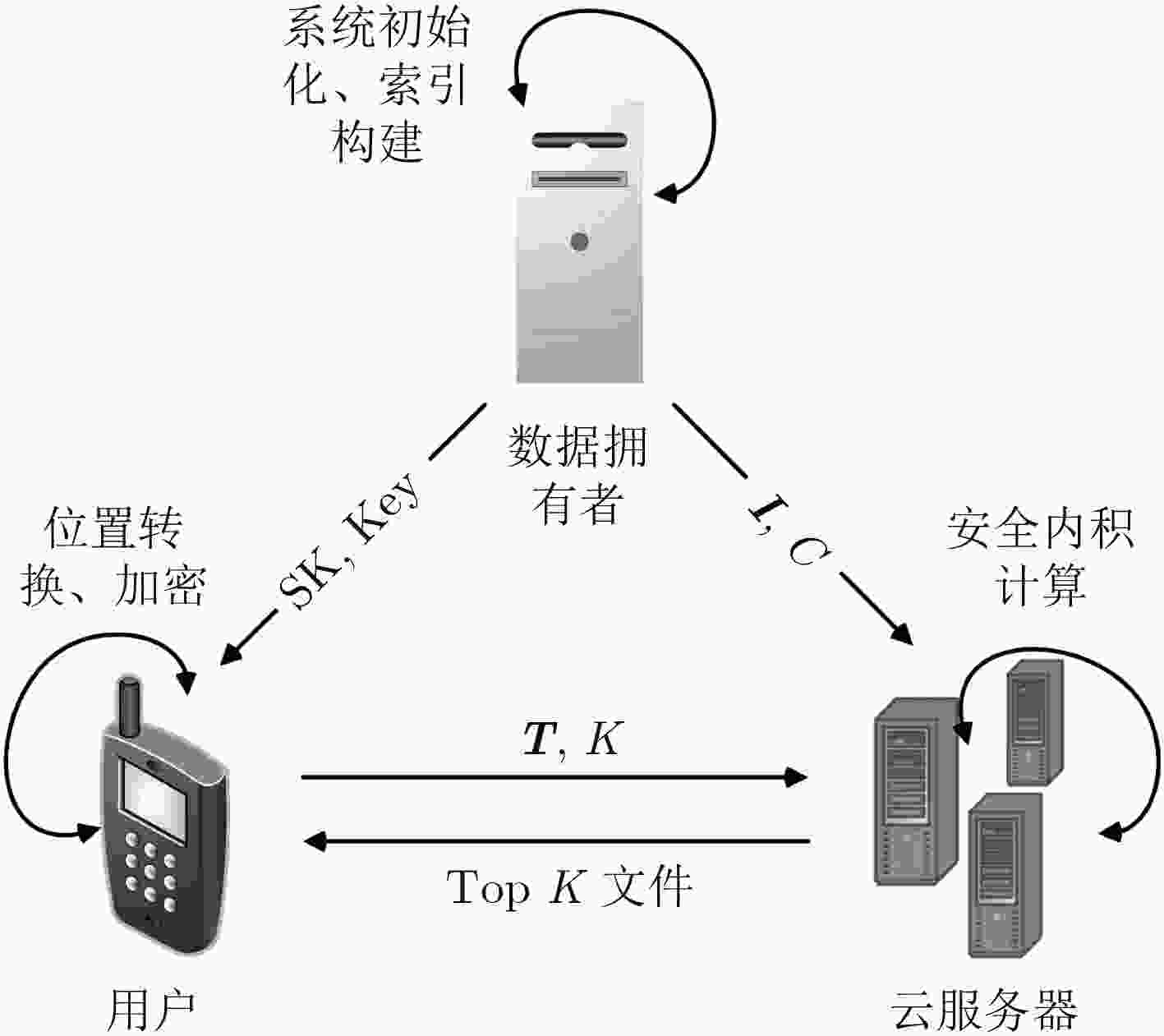
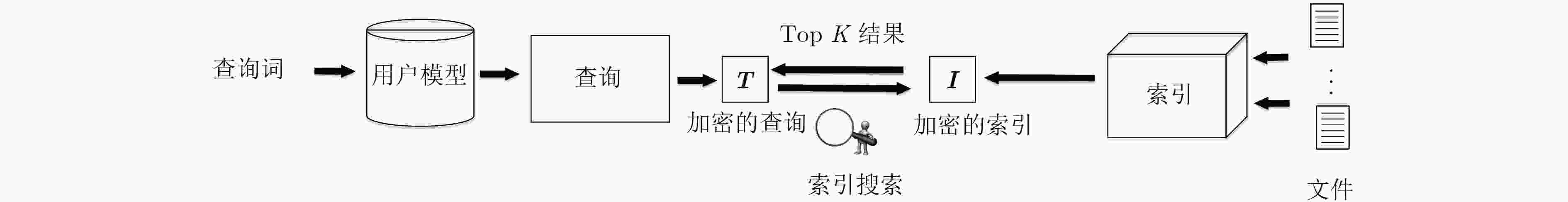
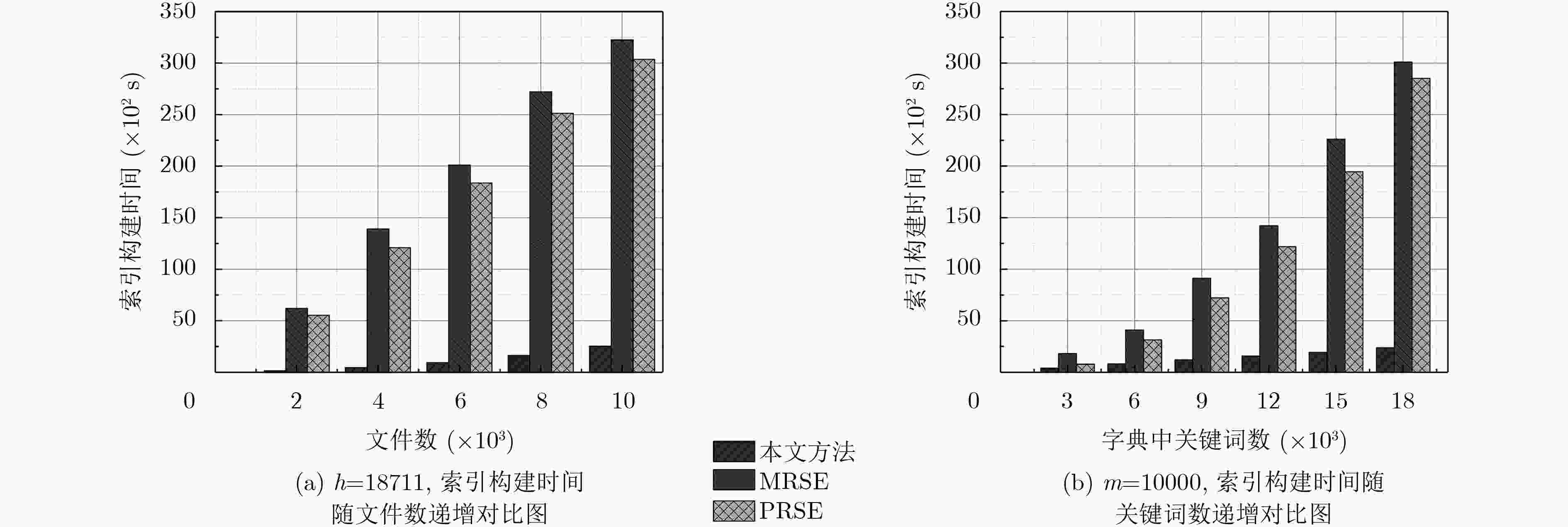
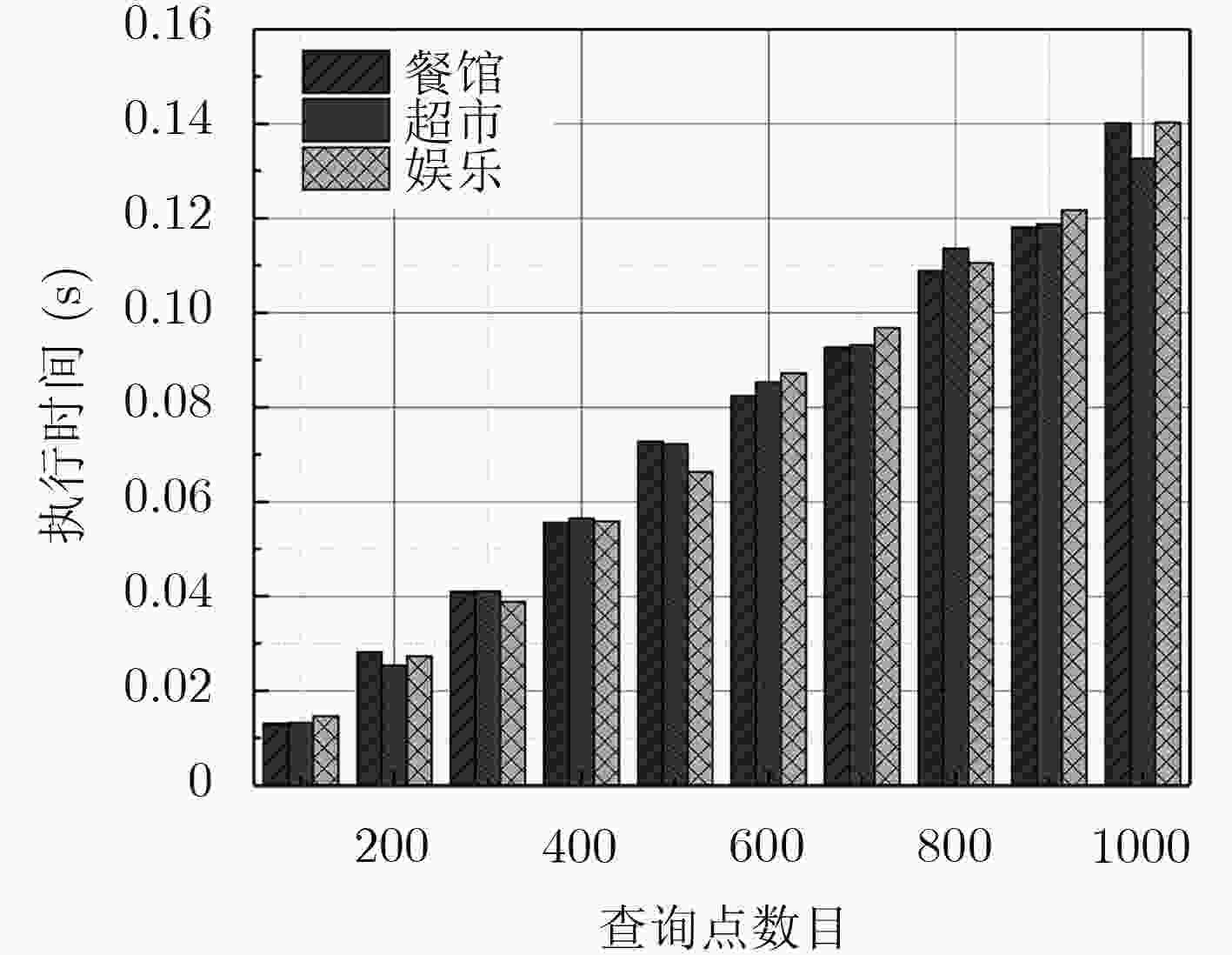
摘要: 在基于位置服务的个性化搜索中,利用可信第三方服务器以及对等节点是保护用户隐私的主要方法,但在现实生活中,它们却是不完全可信的。为了解决这一问题,该文提出一种个性化搜索中基于位置服务的隐私保护方法。该方法通过转换用户的位置信息,并根据用户的查询类型生成用户模型,进而形成带有用户位置信息的查询矩阵,然后利用矩阵加密用户的查询,隐藏查询矩阵中的用户信息,最后根据安全内积计算返回相关性得分最高的前K个查询文件给用户。安全性分析表明该方法能有效地保护用户的查询隐私和位置隐私,通过分析与实验表明,该方法大幅度地缩短了索引构建时间,降低了通信开销,同时为用户提供了基于位置的个性化搜索结果,一定程度上解决了移动设备屏幕小带来的弊端。Abstract: For personalized search based on location service, the trusted third-party server and peer node are used as the main method for privacy preserving. However, entirely trusted third-party server or peer node does not exist in real life. In order to address this problem, a method of privacy preserving on the location of mobile users is proposed when using personalized search. The method is used to convert the user’s location information into distance information and generate the user model according to the user’s query type, forming a query matrix with user location information, then the matrix is used to encrypt the user’s query and conceal the user information in the query matrix. Finally, according to the calculation of the security inner product, the K file with the highest relevance score is returned to the user. It is evident from the security analysis that the proposed method can effectively protect the user’s query privacy and location privacy. The analysis and experimental results show that the proposed method can greatly shorten the time of index construction and reduce the communication overhead. While providing users with location based personalized search results, the method is able to remedy the defects of small-screen mobile devices.
-
Key words:
- Privacy preserving /
- Personalized search /
- Location conversion /
- Security inner product
-
表 1 该文中的相关符号描述
符号 描述 符号 描述 SK 密钥 $K$ 用户提交的参数 $K$ ${{p}}$ 明文索引 $a$ 大于0的随机数 ${{I}}$ 加密后的索引 ${{R}}(i,:)$ 与第 $i$个文件的相关性得分 $C$ 加密后的文件 ${{s}}$ 分裂指示器 ${{q}}$ 用户模型或用户查询 $h$ 字典中的总关键词数 ${{U}}$ 用户模型 $m$ 文件数量 ${{T}}$ 加密后的查询矩阵 ${{G}}$ 查询点的综合评分矩阵 $n$ 真实的关键词数 $t$ 随机生成的关键词数 表 2 索引构建过程
算法 索引构建过程 输入: ${{G}},{{s}},m,{{M}}_1^{\rm{T}},{{M}}_2^{\rm{T}}$ 输出: ${{I}}$ (1) $p={\rm{diag}}({G});$ (2) $h = n + t;$ (3) ${{tp}} = {\rm{rand(1,1)*ones(1,}}t{\rm{);}}$ (4) for $i = 1:m$ do (5) ${{{p}}^ * }(i,:) = [{{p}}(i,:){\rm{ }}{{tp}}];$ (6) ${{r}} = {\rm{rand}}(1,h);$ (7) for $j = 1:h$ do (8) if ${{s}}(j) = = 1$ then (9) ${{p}}'(i,j) = {{r}}(1,j);$ (10) ${{p}}''(i,j) = {{{p}}^ * }(i,j) - {{p}}'(i,j);$ (11) else (12) ${{p}}'(i,j) = {{p}}''(i,j) = {{{p}}^ * }(i,j);$ (13) end if (14) end for (15) end for (16) ${{I}} = [{{p}}'{{M}}_1^{\rm{T}},{{p}}''{{M}}_2^{\rm{T}}]$ (17) return ${{I}}$ -
LU Rongxing, LIN Xiaodong, LIANG Xiaohui, et al.. A dynamic privacy-preserving key management scheme for location-based services in VANETs[J]. IEEE Transactions on Intelligent Transportation Systems, 2012, 13(1): 127–139. DOI: 10.1109/TITS.2011.2164068. YU Rong, KANG Jiawen, HUANG Xumin, et al.. MixGroup: Accumulative pseudonym exchanging for location privacy enhancement in vehicular social networks[J]. IEEE Transactions on Dependable and Secure Computing, 2016, 13(1): 93–105. DOI: 10.1109/TDSC.2015.2399291. 张少波, 刘琴, 王国军. 基于网格标识匹配的位置隐私保护方法[J]. 电子与信息学报, 2016, 38(9): 2173–2179. DOI: 10.11999/JEIT160350.ZHANG Shaobo, LIU Qin, and WANG Guojun. The method of location privacy protection based on grid identifier matching[J]. Journal of Electronics & Information Technology, 2016, 38(9): 2173–2179. DOI: 10.11999/JEIT160350. DU Qing, XIE Haoran, CAI Yi, et al.. Folksonomy-based personalized search by hybrid user profiles in multiple levels[J]. Neurocomputing, 2016, 204(C): 142–152. DOI: 10.1016/j.neucom.2015.10.135. ZHOU Dong, WU Xuan, ZHAO Wenyu, et al.. Query expansion with enriched user profiles for personalized search utilizing folksonomy data[J]. IEEE Transactions on Knowledge & Data Engineering, 2017, 29(7): 1536–1548. DOI: 10.1109/TKDE.2017.2668419. PENG Tao, LIU Qin, and WANG Guojun. Enhanced location privacy preserving scheme in location-based services [J]. IEEE Systems Journal, 2017, 11(1): 219–230. DOI: 10.1109/JSYST.2014.2354235. PAN Xiao, XU Jianliang, and MENG Xiaofeng. Protecting location privacy against location-dependent attacks in mobile services[J]. IEEE Transactions on Knowledge & Data Engineering, 2012, 24(8): 1506–1519. DOI: 10.1109/TKDE.2011.105. HWANG R H, HSUEH Y L, and CHUNG H W. A novel time-obfuscated algorithm for trajectory privacy protection [J]. IEEE Transactions on Services Computing, 2014, 7(2): 126–139. DOI: 10.1109/TSC.2013.55. NIU Ben, LI Qinghua, ZHU Xiaoyan, et al.. Enhancing privacy through caching in location-based services[C]. Proceedings of the IEEE Conference on Computer Communications (INFOCOM). Hong Kong, China, 2015: 1017–1025. CHOR B, GOLDREICH O, KUSHILEVITZ E, et al.. Private information retrieval[C]. Proceedings of the 36th Annual Symposium on Foundations of Computer Science, Washington, USA, 1995: 41–50. LI Xiangyang and JUNG T. Search me if you can: Privacy-preserving location query service[C]. Proceedings of the IEEE International Conference on Computer Communications (INFOCOM). Turin, Italy, 2013: 2760–2768. FU Zhangjie, REN Kui, SHU Jiangang, et al.. Enabling personalized search over encrypted outsourced data with efficiency improvement[J]. IEEE Transactions on Parallel & Distributed Systems, 2016, 27(9): 2546–2559. DOI: 10.1109/TPDS.2015.2506573. ZHAO Feng, YAN Fengwei, JIN Hai, et al.. Personalized mobile searching approach based on combining content-based filtering and collaborative filtering[J]. IEEE Systems Journal, 2017, 11(1): 324–332. DOI: 10.1109/JSYST.2015.2472996. LEUNG W T, LEE D L, and LEE W C. PMSE: A personalized mobile search engine[J]. IEEE Transactions on Knowledge & Data Engineering, 2013, 25(4): 820–834. DOI: 10.1109/TKDE.2012.23. WONG Waikit, CHEUNG W L, KAO Ben, et al. Secure kNN computation on encrypted databases[C]. ACM SIGMOD International Conference on Management of Data. ACM, Providence, USA, 2009: 139–152. 罗恩韬, 王国军. 移动社交网络中一种朋友发现的隐私安全保护策略[J]. 电子与信息学报, 2016, 38(9): 2165–2172. DOI: 10.11999/JEIT151479.LUO Entao and WANG Guojun. A novel friends matching privacy preserving strategy in mobile social networks[J]. Journal of Electronics & Information Technology, 2016, 38(9): 2165–2172. DOI: 10.11999/JEIT151479. ZHANG Qiang, LIU Qin, and WANG Guojun. A privacy-preserving hybrid cooperative searching scheme over outsourced cloud data[C]. Security, Privacy, and Anonymity in Computation, Communication, and Storage. Zhangjiajie, China, 2016: 265–278. CAO Ning, WANG Cong, LI Ming, et al.. Privacy-preserving multi-keyword ranked search over encrypted cloud data[J]. IEEE Transactions on Parallel and Distributed Systems, 2014, 25(1): 222–233. DOI: 10.1109/TPDS.2013.45. -





 下载:
下载:
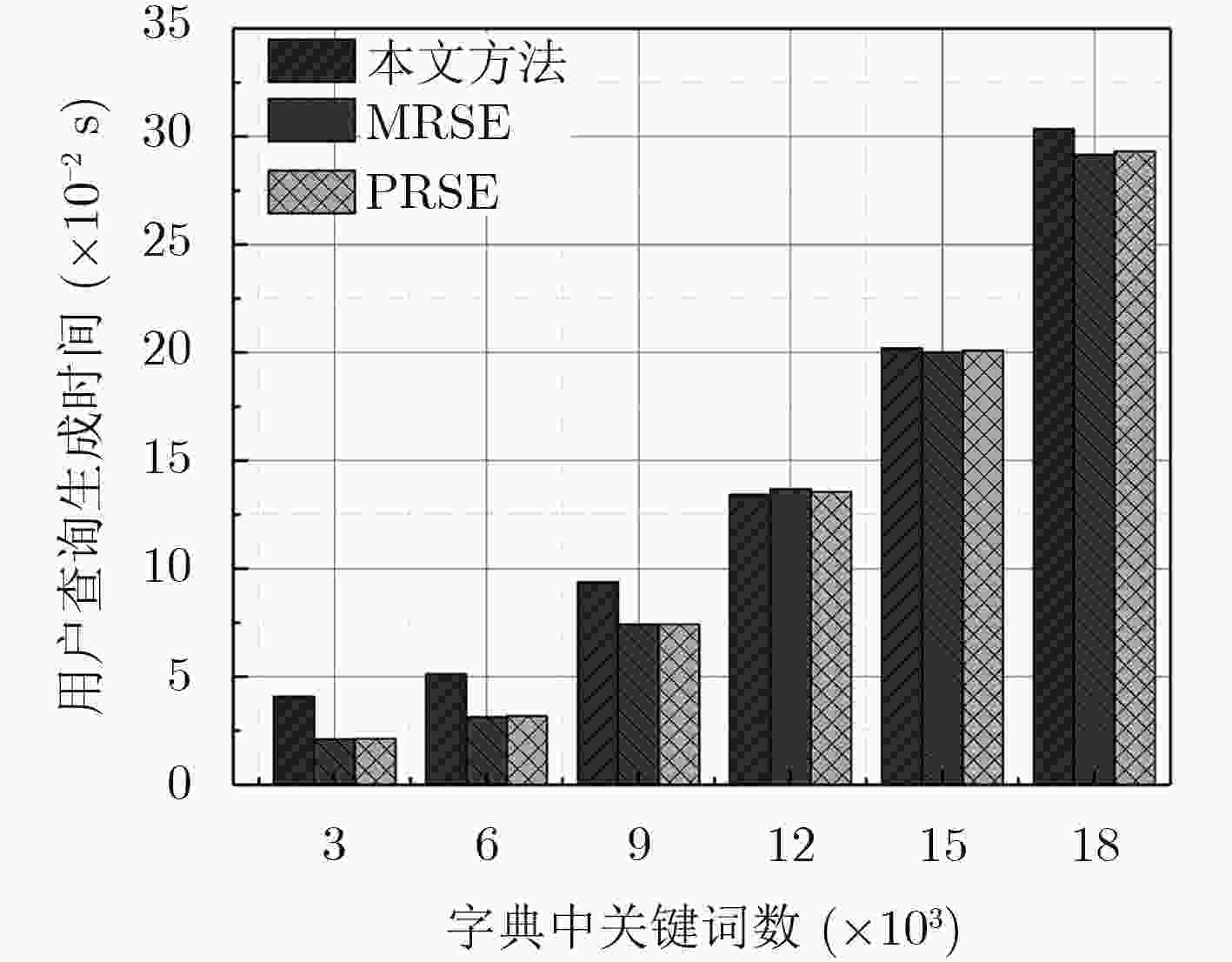
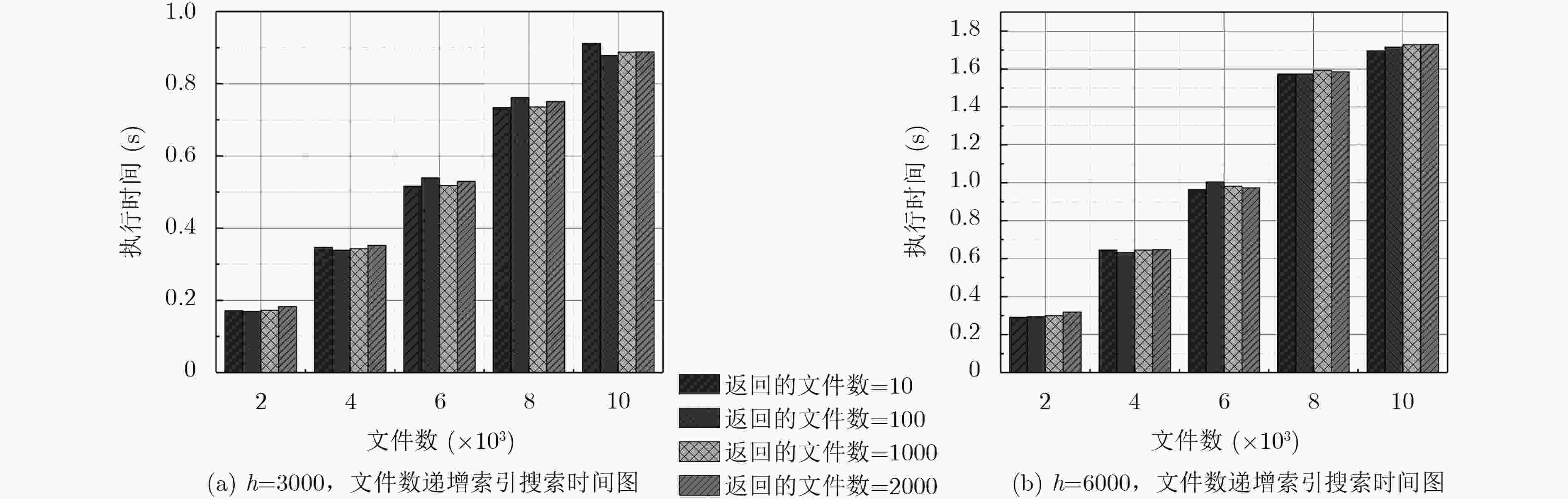


 下载:
下载:
