| [1] |
冯晨, 王慧明. 面向5G的短包物理层安全通信[J]. 中国科学: 信息科学, 2021, 51(9): 1507–1523. doi: 10.1360/SSI-2020-0397.FENG Chen and WANG Huiming. Secure physical layer short-packet communication for 5G[J]. Scientia Sinica Informationis, 2021, 51(9): 1507–1523. doi: 10.1360/SSI-2020-0397.
|
| [2] |
周小波, 于辉, 彭旭, 等. 智能反射面辅助及人工噪声增强的无线隐蔽通信[J]. 电子与信息学报, 2022, 44(7): 2392–2399. doi: 10.11999/JEIT211618.ZHOU Xiaobo, YU Hui, PENG Xu, et al. Wireless covert communications based on intelligent reflecting surface aided and artificial noise enhanced[J]. Journal of Electronics & Information Technology, 2022, 44(7): 2392–2399. doi: 10.11999/JEIT211618.
|
| [3] |
WAN Zhang, HUANG Kaizhi, XU Xiaoming, et al. RIS-assisted integration of communications and security: Protocol, prototyping, and field trials[J]. IEEE Internet of Things Journal, 2024, 11(16): 26877–26887. doi: 10.1109/JIOT.2024.3390677.
|
| [4] |
WAN Zheng, LIU Kexin, CHEN Yajun, et al. Resource allocation for STAR-RIS-assisted MIMO physical-layer key generation[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 10328–10338. doi: 10.1109/TIFS.2024.3488509.
|
| [5] |
FENG Chen, WANG Huiming, and POOR H V. Reliable and secure short-packet communications[J]. IEEE Transactions on Wireless Communications, 2022, 21(3): 1913–1926. doi: 10.1109/TWC.2021.3108042.
|
| [6] |
SONG Lulu, ZHANG Di, JIA Shaobo, et al. STAR-RIS-aided NOMA for secured xURLLC[J]. IEEE Transactions on Vehicular Technology, 2025, 74(8): 13249–13254. doi: 10.1109/TVT.2025.3556542.
|
| [7] |
WANG Zeyin, ZHANG Di, JIA Shaobo, et al. Joint security-latency design for short packet-based low-altitude communications[J]. IEEE Communications Letters, 2025, 29(6): 1401–1405. doi: 10.1109/LCOMM.2025.3563514.
|
| [8] |
LI Lintao, CHEN Wei, POPOVSKI P, et al. Reliability-latency-rate tradeoff in low-latency communications with finite-blocklength coding[J]. IEEE Transactions on Information Theory, 2025, 71(1): 360–389. doi: 10.1109/TIT.2024.3485173.
|
| [9] |
BASH B A, GOECKEL D, and TOWSLEY D. Limits of reliable communication with low probability of detection on AWGN channels[J]. IEEE Journal on Selected Areas in Communications, 2013, 31(9): 1921–1930. doi: 10.1109/JSAC.2013.130923.
|
| [10] |
YANG Weiwei, LU Xingbo, YAN Shihao, et al. Age of information for short-packet covert communication[J]. IEEE Wireless Communications Letters, 2021, 10(9): 1890–1894. doi: 10.1109/LWC.2021.3085025.
|
| [11] |
CHE Bohan, SHI Hui, LU Xingbo, et al. Covert multi-channel communication against interference-assisted proactive detection[J]. IEEE Transactions on Vehicular Technology, 2024, 73(9): 14033–14037. doi: 10.1109/TVT.2024.3394734.
|
| [12] |
LU Xingbo, YAN Shihao, YANG Weiwei, et al. Covert communication with time uncertainty in time-critical wireless networks[J]. IEEE Transactions on Wireless Communications, 2023, 22(2): 1116–1129. doi: 10.1109/TWC.2022.3201872.
|
| [13] |
FAN Hongbin, YANG Weiwei, SHI Hui, et al. Covert communication in underlay multi-antenna cognitive radio networks[J]. IEEE Transactions on Cognitive Communications and Networking, 2025, 11(3): 1493–1507. doi: 10.1109/TCCN.2024.3475369.
|
| [14] |
FOROUZESH M, AZMI P, KUHESTANI A, et al. Covert communication and secure transmission over untrusted relaying networks in the presence of multiple wardens[J]. IEEE Transactions on Communications, 2020, 68(6): 3737–3749. doi: 10.1109/TCOMM.2020.2978206.
|
| [15] |
FOROUZESH M, AZMI P, KUHESTANI A, et al. Joint information-theoretic secrecy and covert communication in the presence of an untrusted user and warden[J]. IEEE Internet of Things Journal, 2021, 8(9): 7170–7181. doi: 10.1109/JIOT.2020.3038682.
|
| [16] |
WEN Yingkun, LIU Lei, LI Junhuai, et al. A covert jamming scheme against an intelligent eavesdropper in cooperative cognitive radio networks[J]. IEEE Transactions on Vehicular Technology, 2023, 72(10): 13243–13254. doi: 10.1109/TVT.2023.3277457.
|
| [17] |
ZHOU Xiaobo, YONG Jiang, XIA Tingting, et al. Intelligent reflecting surface-aided secure and covert communications[J]. China Communications, 2024, 21(9): 1–10. doi: 10.23919/JCC.fa.2023-0567.202409.
|
| [18] |
LIU Pengpeng, LI Zan, SI Jiangbo, et al. Joint information-theoretic secrecy and covertness for UAV-Assisted wireless transmission with finite blocklength[J]. IEEE Transactions on Vehicular Technology, 2023, 72(8): 10187–10199. doi: 10.1109/TVT.2023.3254882.
|
| [19] |
MAO Haobin, LIU Yanming, XIAO Zhenyu, et al. Energy efficient defense against cooperative hostile detection and eavesdropping attacks for AAV-aided short-packet transmissions[J]. IEEE Transactions on Vehicular Technology, 2025, 74(2): 3082–3095. doi: 10.1109/TVT.2024.3483256.
|
| [20] |
WANG Chao, LI Zan, ZHANG Haibin, et al. Achieving covertness and security in broadcast channels with finite blocklength[J]. IEEE Transactions on Wireless Communications, 2022, 21(9): 7624–7640. doi: 10.1109/TWC.2022.3160051.
|
| [21] |
ZHANG Tongxing, WANG Huiming, NG D W K, et al. Multi-antenna covert communications in random wireless networks[J]. IEEE Transactions on Wireless Communications, 2019, 18(3): 1974–1987. doi: 10.1109/TWC.2019.2900915.
|
| [22] |
YAN Shihao, HE Biao, ZHOU Xiangyun, et al. Delay-intolerant covert communications with either fixed or random transmit power[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(1): 129–140. doi: 10.1109/TIFS.2018.2846257.
|
| [23] |
HE Biao, YAN Shihao, ZHOU Xiangyun, et al. On covert communication with noise uncertainty[J]. IEEE Communications Letters, 2017, 21(4): 941–944. doi: 10.1109/LCOMM.2016.2647716.
|
| [24] |
LEHMANN E L and ROMANO J P. Testing Statistical Hypotheses[M]. Switzerland: Springer, 2022: 709–712. doi: 10.1007/978-3-030-70578-7.
|
| [25] |
HU Jinsong, YAN Shihao, ZHOU Xiaobo, et al. Covert communications without channel state information at receiver in IoT systems[J]. IEEE Internet of Things Journal, 2020, 7(11): 11103–11114. doi: 10.1109/JIOT.2020.2994441.
|
| [26] |
YANG Wei, SCHAEFER R F, and POOR H V. Finite-blocklength bounds for wiretap channels[C]. 2016 IEEE International Symposium on Information Theory, Barcelona, Spain, 2016: 3087–3091. doi: 10.1109/ISIT.2016.7541867.
|
| [27] |
WANG Yuntian, ZHOU Xiaobo, ZHUANG Zhihong, et al. UAV-enabled secure communication with finite blocklength[J]. IEEE Transactions on Vehicular Technology, 2020, 69(12): 16309–16313. doi: 10.1109/TVT.2020.3042791.
|





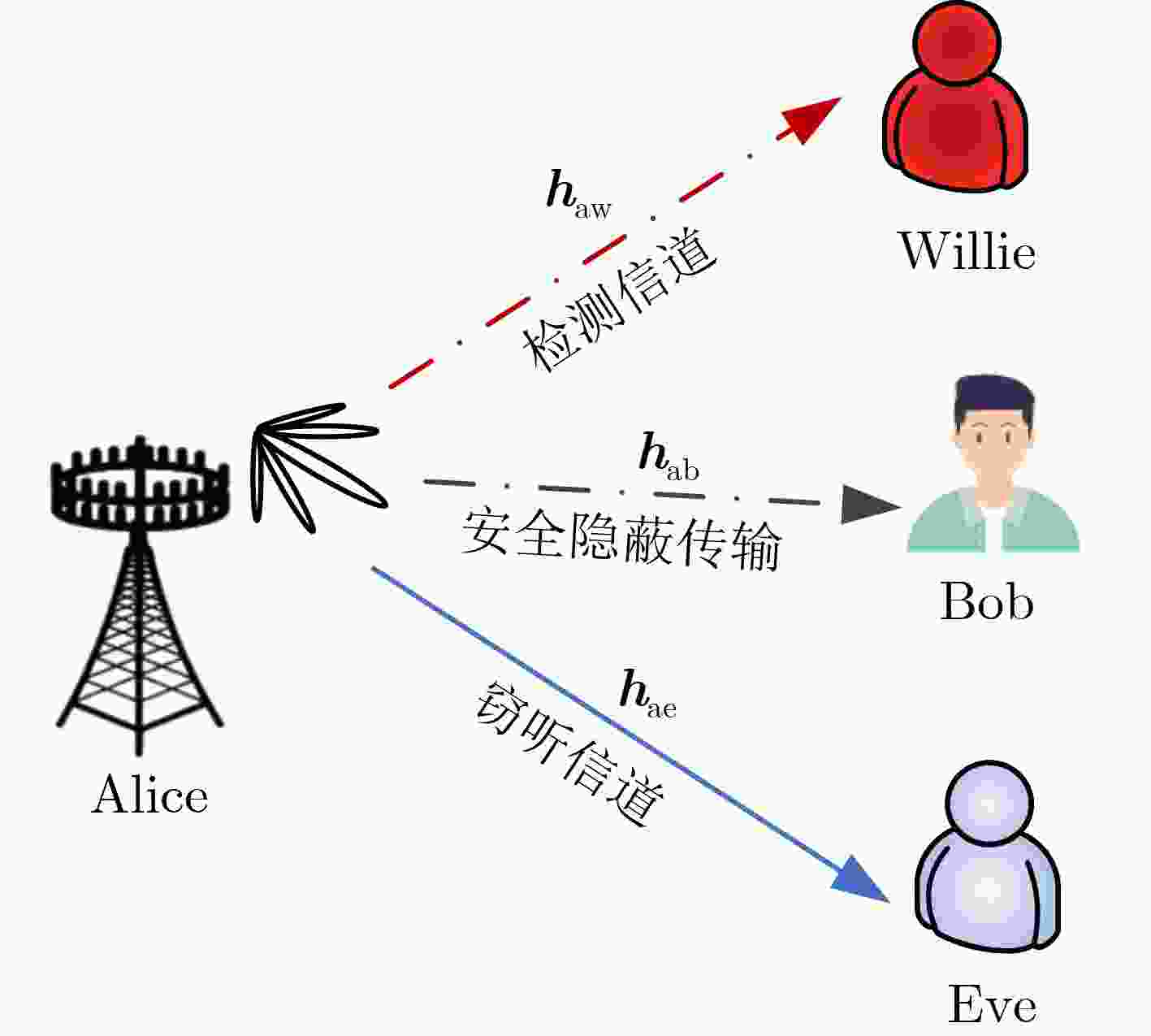
 下载:
下载:
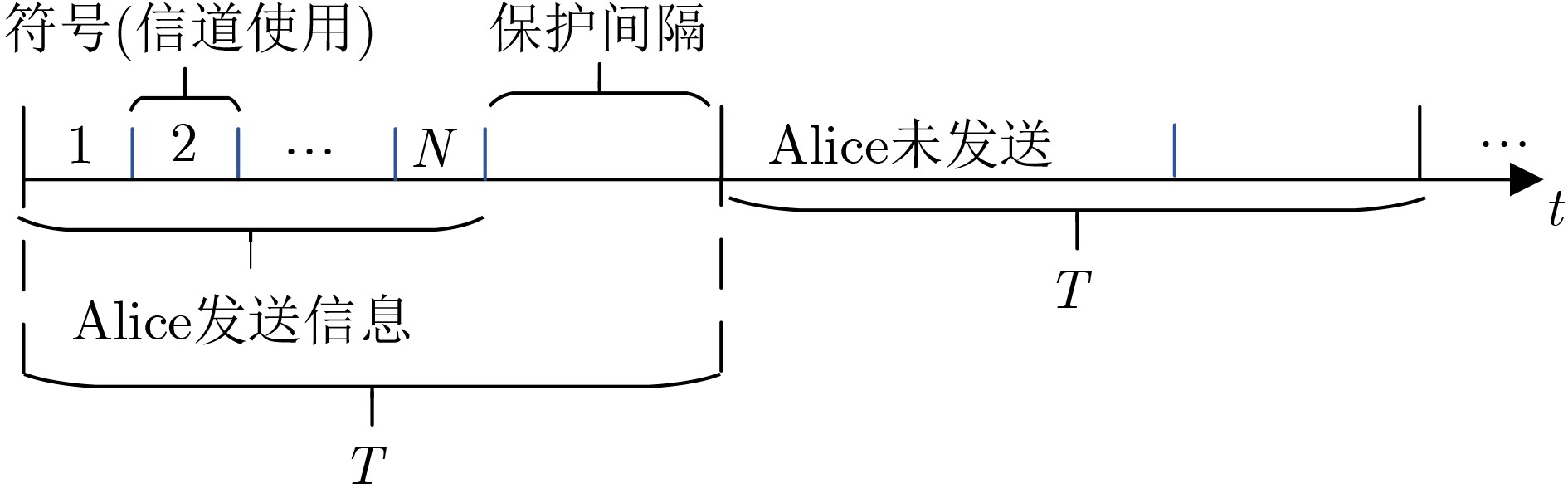
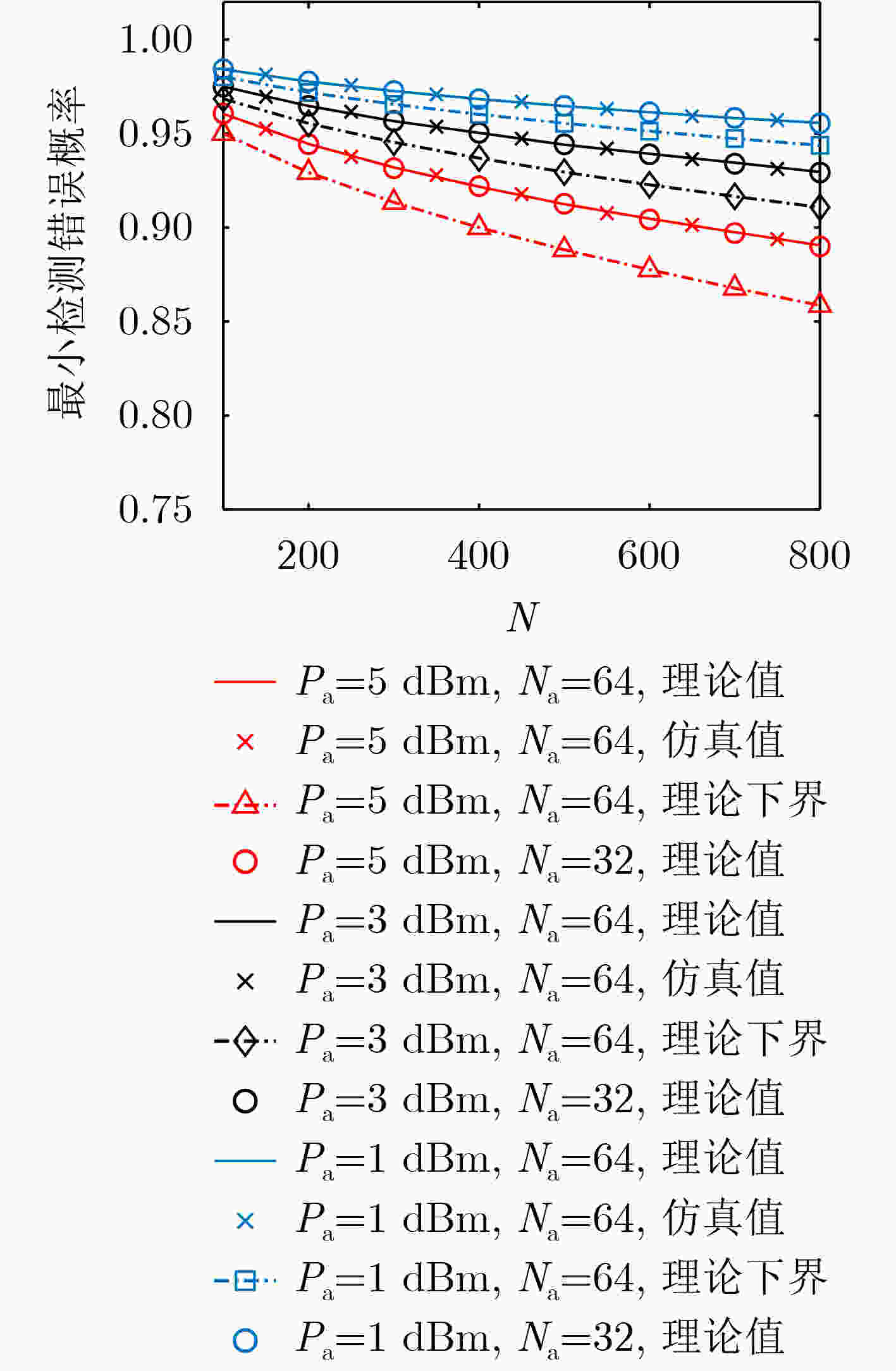
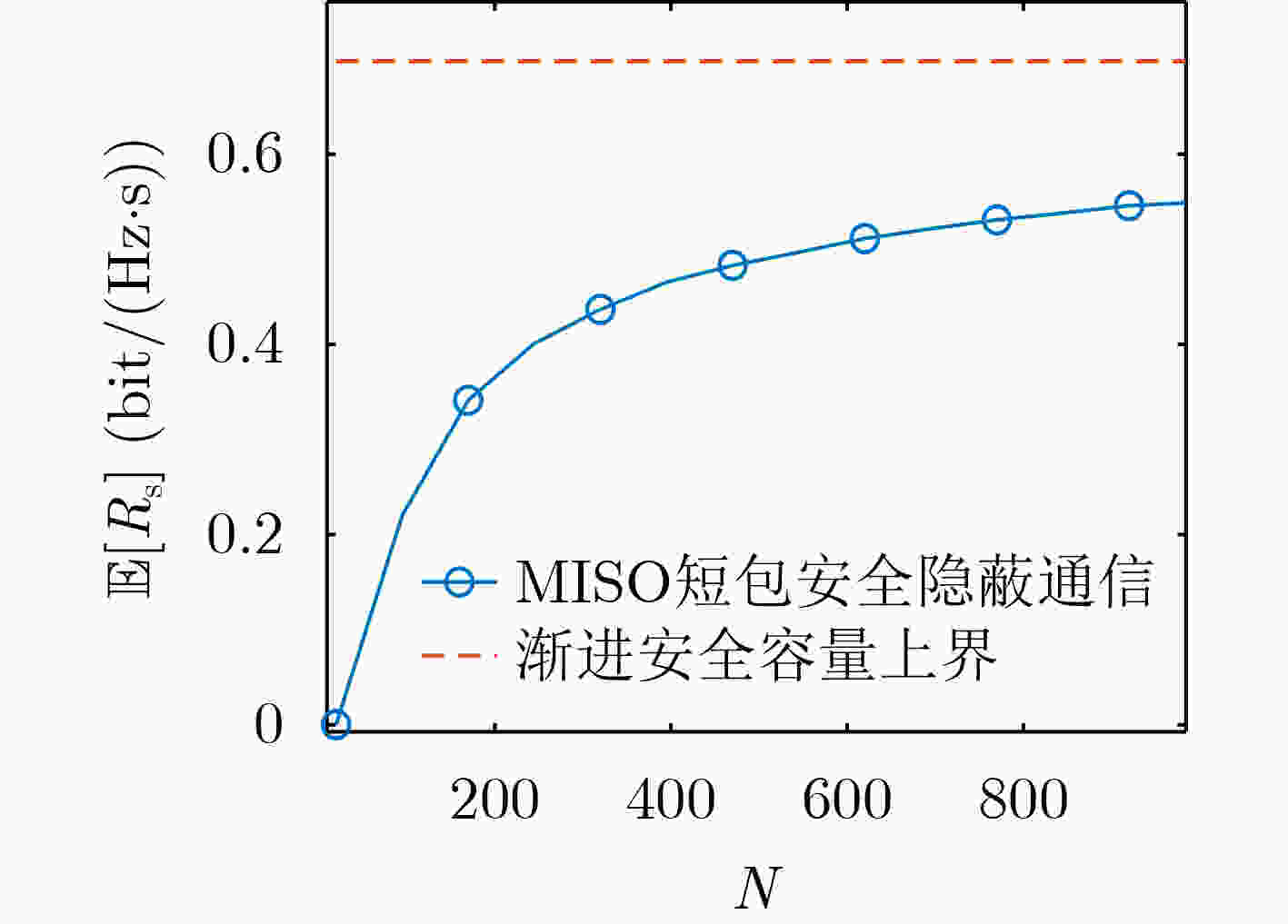


 下载:
下载:
